To effectively execute this phase, the systems analyst meets with other members of the organization to outline the problems, opportunities, and objectives. The systems analyst must also create a series of maps of the locations that are part of the proposed system. During the phase, the system that was recommended and approved at the end of the analysis phase is designed.
The systems analyst uses the previously collected information to create a logical design of the information system. The maintenance phase, on the other hand, costs more time and money; it is comparable in size to the part of the iceberg that is below the surface.
Network Modelling
With careful and accurate analysis and design, the time and cost of the maintenance phase can be minimized.
Feasibility Studies
Capacity Planning
Creating a Baseline
Network Manager Skills
Planning
2 Planning
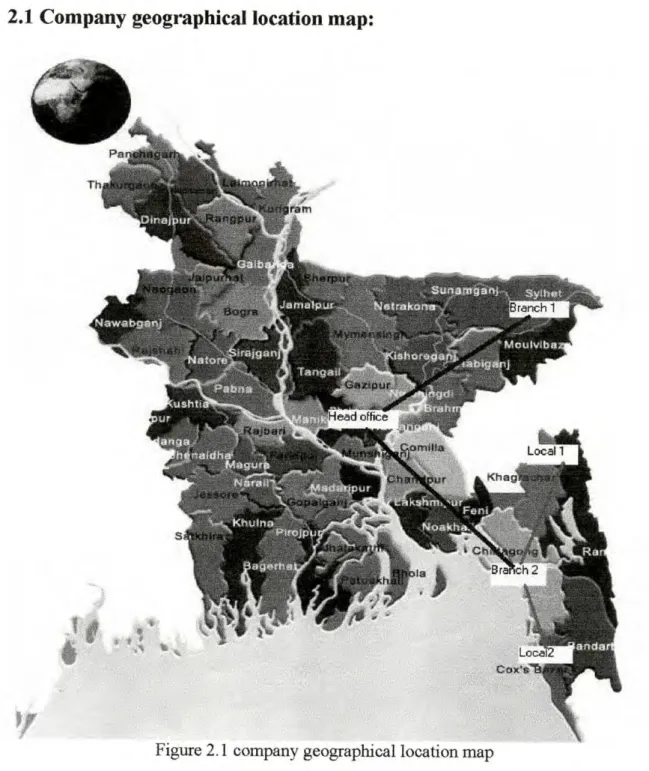
Company geographical location map
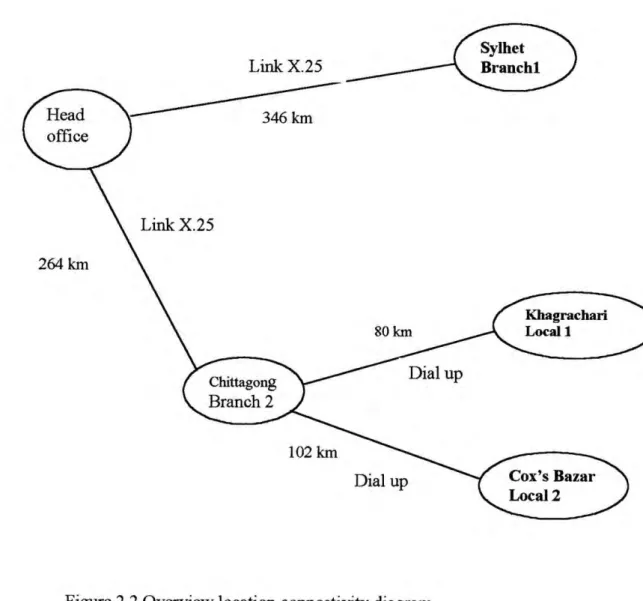
Overview location connectivity diagram
Head office 0001' plan
Head office
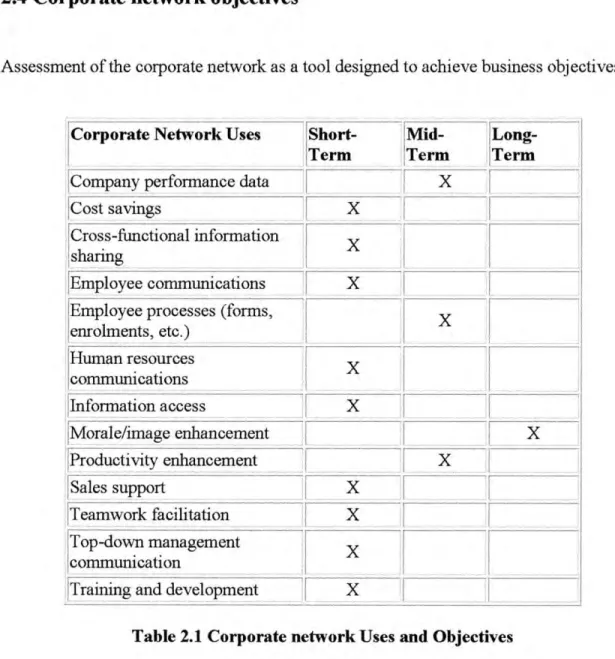
- COI"porate network objectives
- Audience Identification
- Communication Strategies
- Products
- Services
- Communications
- Transactions
- Support Requirements
- Security
- Analysis
These are the real tactical elements of the intranet that will need to be built so that it can be functional and serve specific needs. Products can also be tools that employees can use to do their jobs, which are different from other parts of the intranet. Certain components of the intranet will provide a direct service to the individual employee using it.
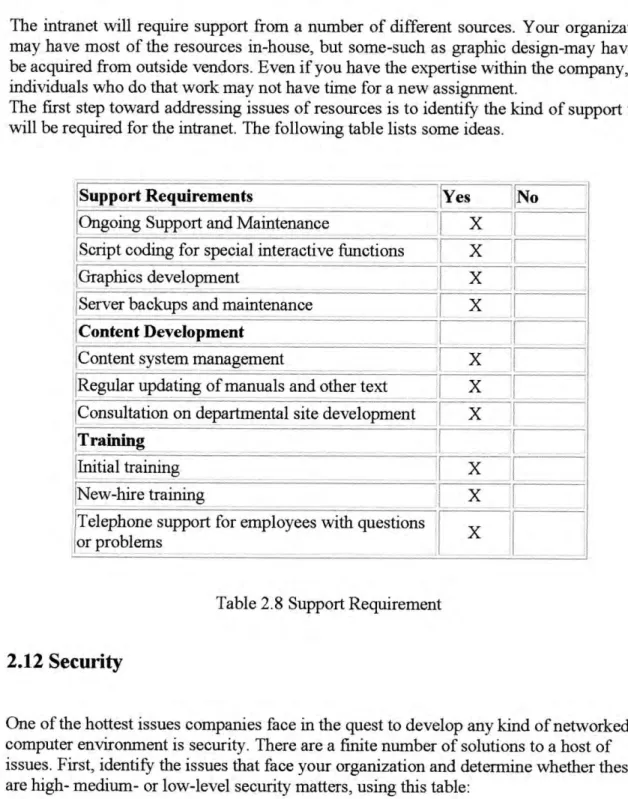
Finally, the parts of the intranet are identified in which data is actually sent from the client to the server to complete some type of transaction. The first step toward addressing resource issues is identifying the type of support that will be required for the intranet.
3 Analyses
Internet
Between the two extremes are networks that are superficially simple but technically complex, and those that are superficially complex but technically simple.
Intr'anet
At the other end of the spectrum, a WAN can comprise many different systems and LANs, all interconnected using a variety of techniques, including standard telephone lines, packet-switched networks, and ISDN connections. To protect sensitive company information and to ensure that hackers do not damage computer systems and data, security barriers called firewalls protect the intranet from the Internet. Firewall technology uses a combination of routers, servers, and other hardware and software to allow people on the intranet to use Internet resources and prevent outsiders from accessing the intranet.
Many intranets must connect to "legacy systems" hardware and databases that were built before an intranet was built. A common way is to use CGI scripts to access the database information and pour that data into H1ML-formatted text, making it accessible to a web browser. Information sent across an intranet is sent to the correct destination by routers, which examine each TCPIIP packet for the IF address and determine the packet's destination.
If the packet is to be delivered to an address on the same subnetwork of the intranet from which it was sent, the packet may be delivered directly without having to go through other routers. If it needs to be sent to another subnetwork on the intranet, it will be sent to a different internal router address. If the packet is to be sent to a destination outside the intranet, in other words, to an Internet destination, the packet is sent to a router that connects to the Internet.
Topologies
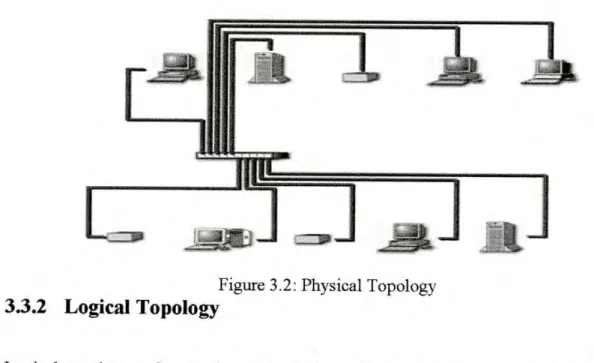
- Physical Topologies
- Logical Topology
- Common LAN Topologies
Logical topology refers to the method that a media access protocol uses to determine device priority. It creates a simple view of the basic network structure so that a determination can be made about the order in which devices transmit. Advances in broadcast media also led to an improvement in LAN media access protocols.
Ring Topology
Unidirectional links connect the sending side of one device to the receiving side of another device. The only advantage of the ring topology is that it uses shorter network lengths and uses fewer cables. The main disadvantage is that a cable break between devices affects the entire LAN (only in Token Ring Standard).
Star Topology
In a star topology, each station is connected to a central hub or concentrator that functions as a multi-port repeater. The main advantage of the star topology is that a cable break typically affects only one workstation.
Topology Comparison
Protocol
Open Systems Interconnection (OSI) Reference Model
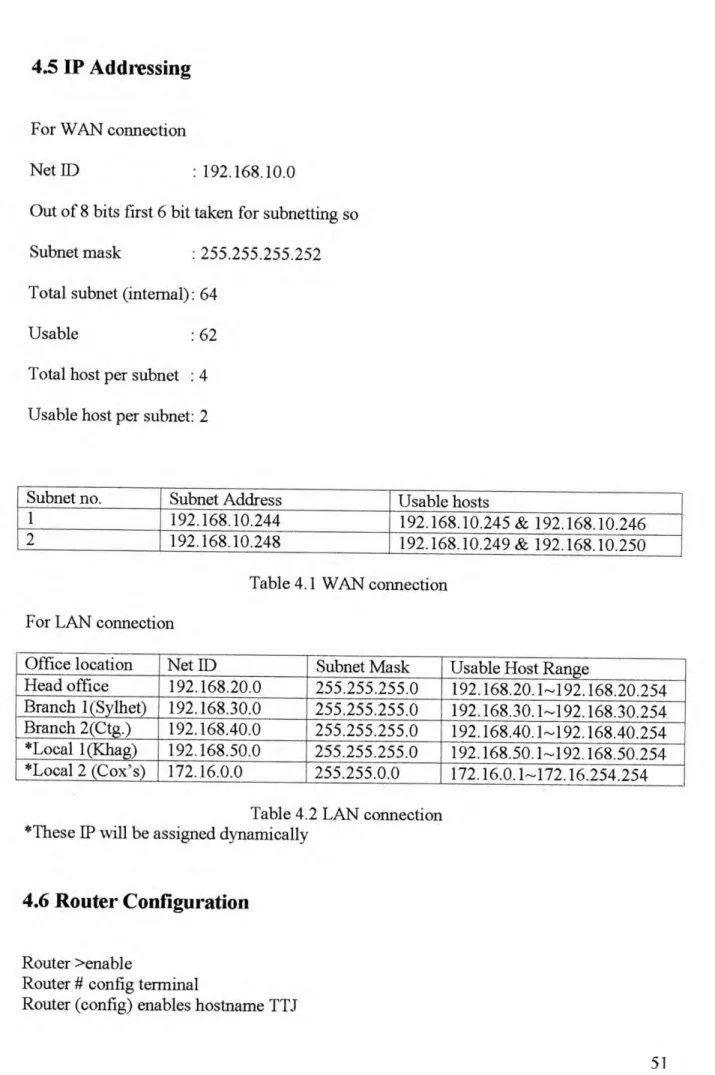
IP Addressing
The network ID in the address consists of a certain number of bits starting from the left. 00001010 would be an IP address that has the same network ID but a different host ID. The network ID consists of the first 16 bits to the left and the host ID consists of the nex1 16 bits.
00010010 would be an IP address that has the same network ID but a different host ID. Network !D consists of the first 24 leftmost bits and host !D consists of the next 8 bits. If a certain bit is part of the network ID, we write an I to the corresponding bit of the subnet mask.
If a particular bit is part of the host ID, we write a 0 in the corresponding bit of the subnet mask. Note that the two IP addresses below are on the same network segment, as their bits corresponding to an 'I' in the subnet mask are identical. The network ID consists of the first 16 bits on the left, and the host !D consists of the next 16 bits.
Note that the two IP addresses below are on the same network segment because the bits corresponding to a '1' in the subnet mask are identical. The network ID consists of the first 24 bits on the left and the host ID consists of the next 8 bits. Note that the two IP addresses below are on the same network segment because the bits corresponding to an 'I' in the subnet mask are identical.
Subnetting
That is, the two hosts must have identical bits in the network ID and subnet ID. In the above subnet network, there are 16 bits in the network ID and 5 bits in the subnet ID. So we write an 'I' for each of these bits in the subnet mask and a '0' for each bit in the host ID.
Note that each 'l' in the subnet mask corresponds to a bit that both IF addresses must have identical. Given two IP addresses and a subnet mask, we can therefore compare the binary bits that correspond to those with an 'I' in the subnet mask. Another way to calculate this is to note that in the example we have three bits and each bit can have two possible values.
In general, the total number of subnets will be (2 A S) - 2, where S is the number of bits in the subnet ill. Note that each 'I' in the subnet mask corresponds to a bit that both IF addresses must have identical. Another way to calculate this is to note that in the example we have three bits and each bit can have two possible values.
In general, the total number of subnets will be (2A S) - 2, where S is the number of bits in the subnet. Recall that we previously discovered that for this subnet, the last two bytes in the IF address should have a decimal value somewhere between 32.1 and 63.254. 1O.240.0.z, but we don't accept it because it matches all I's in the subnet ill.
Software Products
To get your answers quickly during the exam, you should use a table that you wrote during the astronomy tutorial. This isolates the upper layers from the communication requirements with the specific hardware present in a machine. This allows all application and server programs to run identically regardless of the brands of hardware installed on a machine.
The software installed on a workstation
- Driver Software
- Application Software
- Server Software
- File and print Server
- Email server
- Web server
- Administrating recol'd keeping system
- Cost estimation
- Designing
A corporate office should also only purchase the capabilities they need or expect to need in the future. The corporate office should investigate the free alternative before spending money on commercial products. For example, if the corporate office decides to standardize on Internet e-mail, they should choose an e-mail client such as Eudora that supports Internet e-mail.
For this reason, the corporate office must purchase fast machines to use as servers. If an employee already has experience with one of the choices, the corporate office can save time and money by not having to train a server administrator in a new product. This can also cost a lot of money and requires the corporate office to support a UNIX system.
Server programs called software gateways will translate between most of the different email protocols, but a corporate office can save money and avoid problems by standardizing on a single protocol. Unfortunately, these email servers cannot handle a large number of users and the performance of the servers slows down after a few hundred email accounts are in use. A UNIX machine acts as a mail server for the corporate office that requires better performance, although this is not recommended unless a corporate office has a UNIX machine that has a different purpose or absolutely requires higher performance. The wide variety of choices allows a corporate office a lot of freedom in choosing the web server.
Most administrative systems operate in one or two environments; centralized or distributed. In a centralized environment, a central computer stores all information, often in the administrative part of the company's office. If we compare the costs incurred by the corporate office to decide to manage the record keeping system. While preparing budgets, the corporate office will need a cost estimate for the corporate office network.

4 Designing
Hierarchical network design
Logical Design
Bandwidth requiJoement
Device Selection
- Router Selection
- Switch Selection
Selection Issues
- Hub Selection
- IP Addressing
- Router Configuration
- IP Connectivity
- Cost Analysis
- IPLC (International Private Leased Line Circuits)
- National (Point to Point High Speed Data Circuits)
- Local (Point to Point High Speed Data Circuits)
- Installation & Testing Charges (One Time)
- Rental Charges (For 64 KBPS)
- EI Access charge from PSTN to ISPS
- Tariff for X.25 Services
- Overall Cost
- Simulation
- Conclusion
Hub selection issues include: Need for 10 Mbps or 100 Mbps on media Port density Need for management console Ease of operation Before deploying hubs, we assess which workstations require 10 Mbps and which higher-end workstations require an upgrade. Lower-end hubs provide only 10 Mbps, while mid-range hubs automatically detect Ethernet frame data rates and deliver 10 Mbps or 100 Mbps. Hubs allow for a variety of port densities and we can stack hubs to get multiples of the hub densities.
If you want a managed hub that has an integrated console, choose from the higher end hub senes. In our design, WAN connection is omitted, but if someone wants to connect them to the Internet, they can easily connect by adding a card and a real IF connection in the router. Software exporters earning 0.4 USD (Asia, . to 10 million per year in foreign currency Europe, .currency.. 5.40 Software exporters earning more than 10 million USD per year in foreign currency.
6 Conclusion