This thesis/project entitled "a study on cyber security", submitted by Abdifatah Ahmed Mohamed, ID to the Department of Computer Science and Engineering, Daffodil International University, has been accepted as satisfactory in partial fulfillment of the requirements for the degree of MS in Management Information System and approved in terms of its style and content. This thesis could not have been completed by myself, a humble and happy person like me. Must seek Allah Almighty to give me the chance to go through this process. Sheak Rashed Haider Noori, Associate Professor and Associate Head, Department of CSE Daffodil International University, Dhaka for the study opportunity and for the technical assistance during the last phase of completing this thesis.
Introduction
This happened in the development of activities because the information and digital age unfolded in the rest of the 20th century for a hundred years. During the remainder of the 1960s and into the mid-1970s, automatic capability became a reality.
![Figure 2-1: Diagrammatical Representation of DoS. [1]](https://thumb-ap.123doks.com/thumbv2/filepdfnet/10823876.0/12.918.131.712.636.914/figure-2-1-diagrammatical-representation-of-dos-1.webp)
Background
Worms and other DoS attacks were some of the examples of dealing with and responding to cybersecurity attacks. Ultimately, they led to the development of the cybersecurity industry, as well as CERTs as a hub for coordinating responses.
Problem statement
Network protection should be tailored to the wishes of a unmarried company, now no longer the wishes of any other individual. For example, a small regulated company would allow accredited clients in nature for the company to be admitted to the case statistics at the same time making sure that the full net admission in it should constantly be due to personnel within the company. , in case they want to receive admission in a record from the workplace or at the same time as outside and around.
Objectives
Justification
Scope of Study
Moreover, as mentioned above, any part of the network can be vulnerable to attacks and fraudulent benefits. To determine the right way to protect a for-profit organization's assets from attackers, IT managers of such for-profit organizations understand the attacks and disruptions that can be brought to the for-profit organization's infrastructure.
Literature review
Fast access to records on the Internet is becoming an increasingly important part of expanding your business. Unauthorized network access can adversely affect transactions with customers and partners and may call into question the ability of retailers to protect private records.
Categories of security threats
Unstructured threats
Unstructured security risk is the type of risk made by a green person who tries to take advantage of getting right of passage into an organization.
Structured threats
- External threat
- Internal threat
Physical installation attack
Device communication attack
- Physical layer
- data link layer
- Network layer
- Transport layer
- Session layer
- presentation layer
- Application layer
Communication of the information interface is somehow powerless in terms of security. The primary case of the layer 2 component is the 'warfare' strategy of go around and look and arrange with default security settings. Highlighted below are the problems facing layer two of the osi demonstration and the arrangement of the problems.
It is known that the third level at the lower part of the osi model confronts the problems of protection issues and the refusal of administration assaults. Part of the security takes a chance with that influence which is the organization layer mocking of network layer bundles, course caricature and IP address mocking. The presentation layer is one of the most secure layers in many OSI models, but it is also one of the most dangerous.
The use of host-based, fully firewalled structures to coordinate traffic, software sports, and requests controlled through the use of ID systems are a way to manipulate the shortcomings of cause layers.
Reconnaissance attacks
- Access attack
- Password attacks
- Denial of Service attacks
- Worm, virus and trojan horse attacks
The deadly disease mostly spreads by discoloring different applications on a similar computer in which it resides. The laptop virus is a self-replicating malware that executes unpredictable code and places a duplicate of itself in the memory of an infected computer. Trojans can do two things at the same time they infect can be transferred and changed, and Trojan horses can attack in three ways.
The love computer virus is downright annoying as it infects all the photo documents on the compromised hard drive and turns them into new Trojan horses. And finally, the love virus is a computer virus because it spreads on the Internet by hiding in Trojan horses that are sent using the contact address of the attacked email. Make sure the community hasn't been tampered with or in the hands of malicious people.
Entering the community with the help of hackers and disgruntled employees can ruin your business.
Methodology
Chosen methodology
Requirement gathering technique
Introduction
Hardware threat mitigation
Mitigation of environmental threats
Intruders can only access the traffic flow of connected ports, for example, if an organization adopts Layer 2 switched Ethernet. By focusing on questions of ability, you can work on the overall well-being and satisfaction of the organization for well-being. Associations are proving increasingly vulnerable to digital threats due to the increasing dependence on personal computers, organizations, programs, virtual entertainment and information around the world.
The control technique you use will be predictable considering the risk and advanced firmness of the association. When you reduce the hazard, you limit the severity of the hazard and the likelihood that the hazard will occur. The threats to the company that could have an effect on the agency's activities appear to be vulnerabilities.
The importance of the monitoring and assessment process is that the organization's activities are managed appropriately and that procedures are understood and adhered to. The wishes of the commercial enterprise determine the way you broaden your commercial enterprise techniques and manage measures. The hacker may be on the other side of the world from the victim and does not know that he has been hacked.
Electrical threats mitigations
Maintenance-related threat mitigation
Neither the console nor any console port should be left open, and administrative interfaces should be closed before departure. No room is completely secure, and even if someone manages to get into a room, there's nothing preventing them from connecting to the console of a switch or a router.
Packet Sniffer attack mitigation
An anti-sniffer tool is a piece of hardware or software that can be used to identify the use of sniffers on a network.
Port scan and ping sweep attack mitigation
Access attacks mitigation
Trust exploitation attack mitigation
Man-in-the-middle attack mitigation
Denial of service attacks and mitigation
Anti-spoofing features: The likelihood of a DoS attack can be reduced by properly configuring anti-spoofing features on routers and firewalls. Anti-DoS Features: Anti-DoS (Denial of Service) measures enabled on routers and firewalls reduce the effectiveness of an attack. Limiting the number of TCPs a system can have open at the same time is a common component of DoS measures.
Filtering limits the amount of unwanted traffic that can pass through different network sections at a certain speed.
Mitigating worm attacks
Application layer attack mitigation
Securing Remote Access
Introduction
Seeking out problems before they happen
Basic risk
You should find a device near you so that you can definitely report the problem. Daffodil International University 33 Representatives should be effectively called upon to record risks and expertise issues. Risk Avoidance Risk aversion is the act of eliminating a weak part of a framework or even an actual framework.
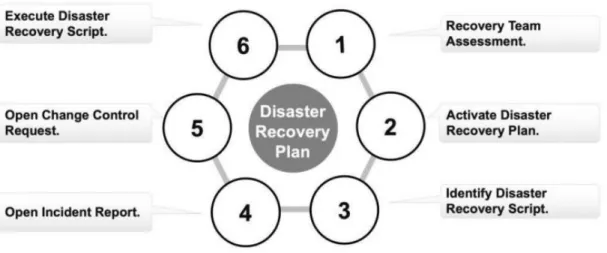
This current circumstance applies to optional schools where risk avoidance can be problematic due to how different clients access the schools network for different reasons. In order for his or her praise to be implemented, you want buy-in from the superiors. The disaster recovery plan describes the processes that want to be accompanied in the event of a disaster to protect it.
Information about the risks and controls identified through the risk assessment and analysis process is communicated using the appropriate copy of the risk assessment. For the most part, none of the insider attacks we've seen have been challenging to investigate," said Peter Vestergaard, former specialized head at Danish security consulting company Protego. Their methods, and also Network Security fundamentals, are fundamental to developing security measures. and implement to prevent Network attacks, Network security breaches are the result of secure information being released to a malicious environment.
Level of impact
Everyone’s responsibility
At the point where anyone and everyone is responsible for committee risk, all representatives really need to understand how to log professional issues. Noticeably update the risk communication board that staff should be aware of in addition to information about crisis situations in the work environment. Make notable updates by publishing a summary of hazards that staff should be aware of, along with records of workplace crisis situations.
Risk management Techniques
Reduce the Risk
Daffodil International University 34 noteworthy than others, but it can be more noteworthy if we do it.
Risk avoidance
Identify Vulnerabilities
Gather Information
Implement Recommendation
Disaster Recovery Plan
Keep Documentation Simple and Clear
Communication and Consult
Monitor and Review
Investigate anomalous activities
Control measures are movements or sports that can limit or save you from danger. The measures used depend on the danger involved and how it can be avoided without effort. The coverage and method of inspection system will be according to each business enterprise.
Measures that may be essential three hundred and sixty-five days will not be necessary the next, or they are not ok to meet the company's needs.
Summary of Risk Assessment
Computer crimes are diverse and do not always happen in front of a computer, but they are always done by a computer. Thanks to advances in technology, criminals no longer have to rob banks or go out and commit crimes. Their weapons are no longer firearms, they use mouse cursors and passwords to attack.
7] https://economictimes.indiatimes.com/definition/emotional-intelligences [8] Multiple Authors, Wireless Local Area Networks Handbook, 2005, Book.
Conclusion