Hosneara Khatun (CSE in the Department of Computer Science and Engineering, Sonargaon University (SU), has been accepted as satisfactory in partial fulfillment of the requirements for the degree of Bachelor of Science in Computer Science and Engineering and approved as to its style and We hereby declare that the work presented in this report is the result of the research carried out by us under the supervision of Md Rafiqul Islam (Rafiq), Lecturer, Department of Computer Science and Engineering, Sonargaon University, Dhaka, Bangladesh. Starting from a historical overview, this project will provide an introduction to the underlying ideas and technologies of network design for a large group of companies.
Rafiqul Islam (Rafiq), Lecturer, Department of Computer Science and Engineering, Sonargaon University, whose warm and valuable support with best care and guidance acted as necessary refuge to carry out our project. We are also grateful to all our teachers throughout our education for introducing us to the beauty of learning. What we want to convey from the beginning is that our entire project is on top of the network configuration.
A network switch (also called switching hub, bridging hub, and by IEEE MAC bridge[1]) is network hardware that connects devices on a computer network by using packet switching to receive and forward data to the destination device. In a nutshell, a network switch is typically a Layer-2 device of the OSI model, while a router is a Layer-3 device.

Router& routing devices
Server
NETWORK SWITCH 2.1 Network Switch
ROUTER: HOW WE USE OUR ROUTER IN OUR NETWORK
What is a network route?
Static Routing
Advantage
Disadvantage
Dynamic routing
Dynamic routes are routes that change automatically over time, and the routing protocol creates and manages such routes. Page | 16 The network topology caused by this growth or by the failure of one or more network components. It is also less secure than static routing because the interfaces identified by the routing protocol send routing updates.
Routing Protocol
Routing Information Protocol (RIP) is a dynamic routing protocol that uses hop count as a routing metric to find the best path between the source and destination network. It is a distance vector routing protocol which has AD value 120 and operates on the application layer of the OSI model. Hop count is the number of routers that exist between the source and destination networks.
The path with the least number of hops is considered the best path to reach the network and is therefore included in the routing table. RIP prevents routing loops by limiting the number of hops allowed on a source-to-destination path. The maximum number of hops allowed for RIP is 15, and a hop count of 16 is considered an unreachable network.
Features of RIP
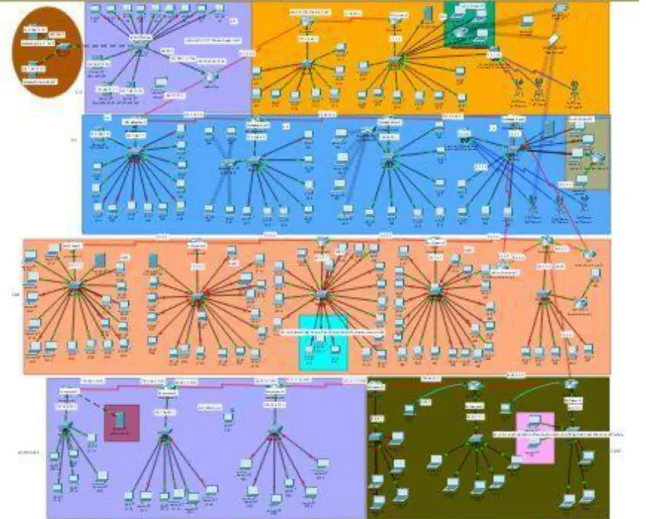
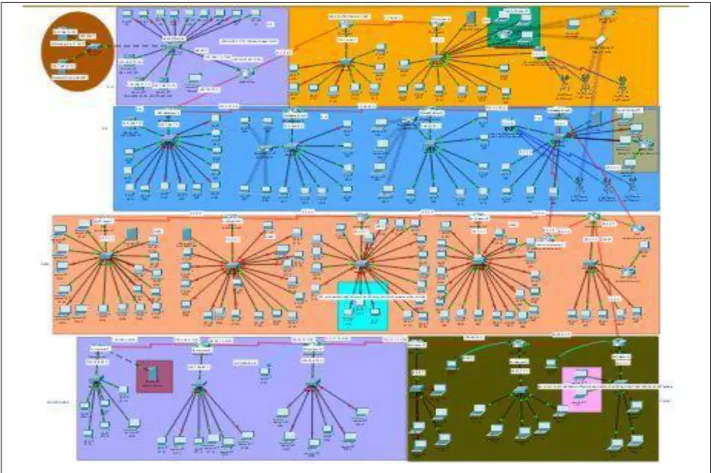
Page | 18 Now we will see how we have applied RIP to some of the routers in our network. In the head office's main router, we use RIP version 1 to connect with the other router on the network. Now we will show the running configuration of the router and describe the whole part of this.
Head Office POP
We configured the line console password and username and vty telnet password for the entire network.
Mirpur Pop-1
Mirpur pop-2
Mohakahli pop-1
This router also uses RIP and connects to Mirpur pop-1 (full network) and Mirpur pop02 office network. This is how the Mirpur branch router works, now we go to the Mohakhali branch router. Same as Mohakhali pop 2.3 is connected to their external router and also uses rip as router protocol.
Mohakhali pop-2
Mohakhali pop-3
There are three networks, once connected to Mohakhali pop-2, once pop-4 and finally connected to office network.
Mohakhali Pop-4
Kustia pop-1
So initially we test the IP address of each interface and don't shut down this entire interface.
Kustia Pop-2
Like the previous network Kushtia pop-2 also used the OSPF protocol, three are connected to the network in this one, one of this network is connected to the previous network, connected to the office network and another connected pop 3.
Kushtia pop-3
Kushtia pop-3 also contains ospf protocol, three networks also connect to this and connect three networks and the total whole network.
Kustia pop-4
It is also the easiest protocol, we created OSPF 10 and put network under area 1. In this router 4 network connected using ospf.
Kushtia pop-5
Jossore Pop-1
Radius server is very important for server based security systems that include router log username and password.
Jossore pop-2
Page | 42 First, assign ip address, use all interfaces and then use routing protocol rip version 2 with complete routing. Radius server is very important for server based security systems which includes router logging username and password so we can easily access the router with included username and password.
Khulna Pop-1
At the end we know that our router from our router description used different protocol like RIP, OSPF, EIGRP etc.
ACL: ACCESS CONTROL LIST 4.1 Definition of an Access control List
Types of ACL
Those of you familiar with ACLs probably know that there are many different types of ACLs. We have access control lists for IP version 4, for IP version 6, for IPX, for DECnet, for AppleTalk and the list goes on and on. At this point, we're responsible for IP version 4, and that's what our focus is, IP version 4.
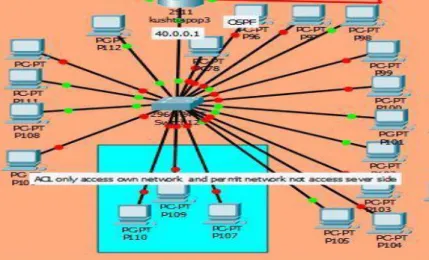
And we can divide IP version 4 access control lists into two different types, standard and extended. Kushtia pop-3 pc not only have access to own network, they are not allowed to access the server. Main rules of default acl: .. default acl only get access to own network and allow any other network or host but no access others deny network or host.
SERVER (MAIL, FTP, RADIUS, DHCP, DNS) 5.1 Definition of SERVER
- What is mail server? How its work?
- What Is FTP server? How its work?
- What Is RADIOUS server? How its work?
- What is DHCP server and how its work?
- What is DNS server and how its work?
- Web Server
- DNS Server
- FTP Server
- MAIL Server
- DHCP Server
- Radius Server
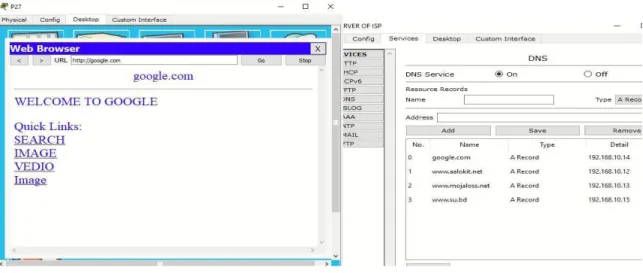
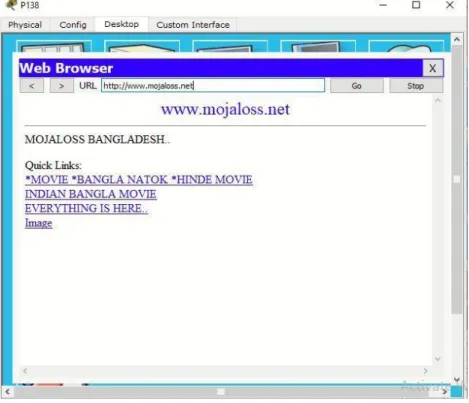
Everything connected to the Internet - laptops, tablets, mobile phones, websites - has an Internet Protocol (IP) address, which is made up of numbers. Now we browse from pc138..and the web address is www.mojaloss.net.so the result is here. Every pc or client can browse from DNS server.. it means DNS server store all domain address and ip.
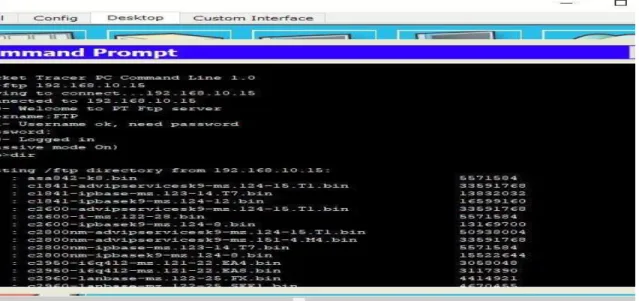
The ftp server can only access all authorized PCs or clients due to the ftp server set a username and password. DHCP servers are used for this network because all PCs under the DHCP server are automatically given IP addresses. Each DHCP server has an ip range, so each PC can ip address from ip range on DHCP server.
It has included the username and password of the entire router under the radius server, so that any computer can access the router with the username and password of the radius server. now let's look at Example.
CONCLUSION