©DAFFODIL INTERNATIONAL UNIVERSITY I
Efficient Resource Allocation Algorithm for Fog of IoT
BY
Abdi Bille Abdi ID: 183-31-247
This Report Presented in Partial Ful llment of the Requirements for the Degree of Master of Science in Electronics and Telecommunication Engineering
(M.Sc. in ETE).
Supervised By Engr. Md. Zahirul Islam
Assistant Professor Department of ETE
Department of Electronics and Telecommunication Engineering Da odil International University
Dhaka, Banglad
©DAFFODIL INTERNATIONAL UNIVERSITY II
APPROVAL
©DAFFODIL INTERNATIONAL UNIVERSITY III
©DAFFODIL INTERNATIONAL UNIVERSITY IV
List of Tables
5.1 Initial parameters used in GA for multi-objective optimization problem……… 35
©DAFFODIL INTERNATIONAL UNIVERSITY V
List of Figures
2.1 Iot Architecture . . . 8
2.2 Iot Standards and Framework . . . 10
2.3 Example of an IoT System . . . 12
2.4 How IoT Works . . . 15
2.5 Iot Applications . . . 16
2.6 IoT Security and Privacy . . . 17
3.1 Smart Energy . . . 21
3.2 Edge Resource Applications . . . 22
3.3 Smart Healthcare . . . 23
4.1 SDN Based IoT Architecture . . . 26
4.2 System Flow Diagram . . . 28
4.3 Learning Asset Accessibility and Capacity . . . 29
4.4 Learning Demand Finishing Time (MTTC) from IoT Node to the Resources . . . 30
4.5 Forecasting Number of Probable Requests from IoT Nodes . . . 31
4.6 The Resource Allocation Problem and the System With Acquired Knowledge . . . 31
4.7 Predicting Resource Reliability . . . 32
5.1 Experimental Scenario . . . 36
5.2 Probability of failure of R2 Vs. Number of Allocated Requests. . . 37
5.3 Number of requests allocated to an IoT node to resource with the varying reliability of R2. The probability of failure for resources R1, R2 and R3 are (a) [.01 .1 .01] (b) [.01 .3 .01] (c) [.01 .5 .01] (d) [.01 .7 .01] (e) [.01 .8 .01] (f) [.01 .9 .01] . . . 37
©DAFFODIL INTERNATIONAL UNIVERSITY VI
5.4 Overall resource utilization in case of changing in quantity of probable requests. . . 38
5.5 Number of requests allocated to an IoT node to resource for varying expected number of requests. The requests made from N1, N2 N3 for respective cases are (a) [50 100 30] (b) [20 80 40] (c) [10 80 10] (d)
[100 100 100] (e) [200 200 200] (f) [0 0 100] . . . 39
©DAFFODIL INTERNATIONAL UNIVERSITY VII
Contents
Declaration iii
Acknowledgment ix
Abstract x
1 Introduction 1
1.1 General Introduction . . . 1
1.2 Motivation . . . 3
1.3 Related Work . . . 3
1.4 Research Objectives . . . 4
1.5 Organization of Thesis . . . 5
2 Fog of Iot 6 2.1 Introduction . . . 6
2.2 Iot Architecture . . . 7
2.3 IoT Standards and Frameworks . . . 8
2.4 History of IoT . . . 11
2.5 Why Iot is Important? . . . 12
2.6 Bene ts of IoT . . . 13
2.7 How IoT Works . . . 14
2.8 IoT Applications . . . 14
2.9 Iot Security and Privacy Issues . . . 17
2.10 The Future of IoT . . . 18
3 Resource allocation 19 3.1 Introduction . . . 19
©DAFFODIL INTERNATIONAL UNIVERSITY VIII
3.2 Energy e cient Resource allocation . . . 20
3.3 Smart Energy . . . 21
3.4 Edge Resource Allocation for Multiple Applications . . . 22
3.5 Smart Healthcare Resource Allocation . . . 22
4 Proposed solution 25 4.1 Introduction . . . 25
4.2 Proposed Method for Resource Allocation . . . 26
4.2.1 Finding Available Resources . . . 27
4.2.2 Mapping assets to IoT fog Nodes . . . 29
5 Results 34 5.1 Changing possibility of failure . . . 36
5.2 Changing quantity of probable requests . . . 37
6 Conclusion 40
©DAFFODIL INTERNATIONAL UNIVERSITY IX
Acknowledgment
Firstly, I like to forward my regard to Almighty Allah for showing me the right path while attempting the duty. The real sprit of achieving a destiny is through the path of eminence and solid discipline. I would have never achieved in nishing my job without the alliance, inspiration and assist issued to me by di erent personalities.
This thesis report would not have been manageable without the assist and di-rection of Engr. Md. Zahirul Islam, Assistant Professor, Department of Electronics and Telecommunication Engineering, Da odil International University, under whose supervision I chose this topic.
I would like to express my heartiest respect to Md. Taslim Are n, Associate Professor &
Head, Department of Electronics and Telecommunication engineering, for his kind help and also to other faculty members, the sta s of the ETE Department of Da odil International University. I must grant with due respect.
©DAFFODIL INTERNATIONAL UNIVERSITY X
Abstract
In recent years, Internet connected devices have increased signicantly. Technolo-gies such as Internet of things and cloud computing are enabling more and more devices to connect to the Internet. With rise in number of Internet connected de-vices, new computational paradigms such as edge computing and fog Computing are emerging. All these changes are making the network infrastructure very com-plex, dense and heterogeneous. In this dynamically altering and growing scenario, existing traditional network infrastructures are inadequate to fullll the growing data requirements, the network service providers need to update the infrastructure hard-ware and software parameters dynamically. They need to manage co-operation, co-ordination and co- existence among diverse network types. For this, novel self conguring resource management techniques are required. In this direction, we have presented novel methods for allocating resources at di erent levels of network in-frastructure where computational resource optimization for IoT devices has been done. IoT device density is increasing and current philosophy of processing requests at cloud is not appropriate for emerging IoT domains such as health care and real time control. We have considered to use variety of devices available at the network access layer. This includes the devices voluntarily given by users, dedicated edge servers and cloud infrastructure. The proposed system learns the optimal operating parameters during initial runs. Using the knowledge acquired in the learning phase, an integer linear programming problem is formulated to minimize the mean time to complete the request for all the IoT nodes. The solution of the formulated prob-lem provides fair resource allocation for all the IoT nodes. Later, considering the unreliable nature of the voluntary devices, the learning and formulation has been extended to incorporate probability of failure of these devices. A multi-objective optimization problem has been formulated and solved using genetic algorithm.
©DAFFODIL INTERNATIONAL UNIVERSITY 1
Chapter 1 Introduction
1.1 General Introduction
The web of things (IoT) to future progressive is considered in step in the cell inno-vation IoT administration are predicated as a key parameter for further push in the development in cell innovation it has been assessed that 30 billion cell IoT based associated gadgets will be conaveyed by 2025 and furthermore 7 billion low power wide territory (L P W A) modules are predicated to account in 2025 cell based IoT is probably going to o er assistance like help meters machines for retailing car ma-rine administration, brilliant tra c framework, tra c Information continuously to the vehicle in car part security announcing and basic and other therapeutic help in actuality IoT devices (passages sensors or installed frameworks) gave computational [2]stock piling, and system assets which permit to move the execution of IoT appli-cation to the edge of the system along these lines the methodology depicted as haze guring ( or edge registering) haze guring is an augmentation of the cloud based foundation gives processing stockpiling and system asset like cloud and advancing the usage of the IoT application close to the information source contrasted and the remote server farm, it has bit of lee way of shortening application reaction time haze hubs are scattered in topographical area and asset on them restricted contrasted and cloud between haze hubs, system round-trip time, information preparing pace and asset accessibility are still signi cant,Thus in a fog computing condition it is as yet a test to streamline in culmination time and vitality utilization of solicitation simulta-neously the vitality and time productive calculation offloading and asset designation
©DAFFODIL INTERNATIONAL UNIVERSITY 2
for IoT application which means to decreasing the vitality utilization and consum-mation time of IoT application demand improving the processing intensity of IoT device in fog [2].
Arrange elements such us portal servers, switches and switches can be regraded as mist hubs for processing reason . Fog isn’t supplant the cloud they are reciprocal to one another Predication of the internet of things (IoT) portray an amassing of conceivably enormous number of interconnected IoT clients to actualize applications found in shrewd urban communities [1]. Smart agriculture and industry in this way designating constrained asset such us range and capacity to countless IoT clients is pivotal but then complex test generally IoT clients were battery fu-eled which limits there activity time besides a signi cant number of these clients are situated in blocked o space remote zones or in unfriendly and lethal conditions hence there has been a solid development towards the utilization of vitality reaping innovations where the gadget gets vitality from large number of sustainable power source asset like sun based wind radio recurrence (RF) signals and so on explicitly procedures has been increasing more consideration because of the multiplication of transmitters that as of now exist our condition [1]. Internet of things (IoT) technol-ogy is bring numerous emerging concept into reality , among which a striking one is shrewd city with IoT based brilliant urban areas gigantic heterogeneous IoT gadget run assorted propelled administration for phenomenal insight and productivity in di erent spaces of city life to be speci c savvy city building , canny transportation ,pervasive e social insurance, keen home, savvy vitality and savvy processing plant are going to essentially improve the personal satisfaction and occupant in IoT based brilliant urban areas, IoT based shrewd urban communities are described by an enormous number of administration running over monstrous end IoT gadget just as applications facilitated in remote servers note that these administrations changing from augmented reality to accuracy human services from video based reconnaissance to water organize observing may have entirely unexpected nature of administration (Qos) necessity for instance computer generated reality has a stringent cuto and endured delay [1]. What is more the number of IoT devices in smart cities is expo-nentially growing with dissimilar attributes stationary IoT gadget as sent in various geo areas might be out tted with control full processes and colossal extra room on opposite, the battery life ,preparing force and capacity limit of profoundly portable
©DAFFODIL INTERNATIONAL UNIVERSITY 3
IoT gadgets shrewd wearable ,might be exceptionally restricted ,Given the huge measure of IoT gadgets and the enormous number of brilliant city support just as their diverse Qos prerequisite it has been a major challenge for servers to ideally assign constrained assets to all facilitated application applications for agreeable ex-ecution this issue turns out to be considerably more cut o as the IoT based keen urban communities scales up clearly running all applications on the focal cloud may e ectively prompt genuine arrange clog and execution debasement [3]. The internet of things( IoT ) is a rising correspondence worldview in which di erent physical article are out tted with little handsets for advanced correspondence and associated with the web the underlying thoughts of IoT were proposed in mid 80 s computer-ized stock framework however their commonsense acknowledge in genuine industry have as of late be rearm attributable to the improvement of the structure of lit-tle and modest specialized gadgets As well as simple access to versatile web the IoT empowers di erent applications in a wide range of areas including savvy urban communities, home car , keen matrix , medicinal services ,tra c management [3].
1.2 Motivation
In last years the IoT technology has been increasing in all over the world which more e ective and useful human internet of things IoT is new technology that in-terconnected di erent devices with the internet. The resource allocation problems seeks to nd an optimal allocation of xed amount of resource to activities so as to minimize the cost incurred the allocation . Resource scheduling supports the process of resource allocation by adding e cient scheduling of the resource for the optimal allocation the iot helps in achieving the some purpose and it possible to maintain the real time record of the resource and disseminate this information where and when required.
1.3 Related Work
Some works related IoT resource allocation further delineates the likenesses and con- trasts between energizing research and our work so far distributed computing has been broadly examined dependent on the versatile and adaptable cloud framewor
©DAFFODIL INTERNATIONAL UNIVERSITY 4
such us the asset/tra c streamlining of backhaul systems estimating methodologies of utilizing business cloud administration, administration con rmation control and planning the asset booking plans can be separated into six half breed classes contain-ing cost mindful asset planning productivity mindful asset booking vitality mindful asset planning load adjusting mindful asset booking Qos mindful asset booking, and usage mindful asset planning [4].
However loads of existing distributed computing models are intended for customary web applications what’s more haze of things, is an exceptionally encouraging guring mode wherein IoT capacities are held on request based assistance. IoT conquered its own asset limitation by utilizing virtual boundless asset in the cloud, cloud can upgrade its administration by intriguing with things in the physical world ( such us using the extent of usage ) and IoT inves-tigation additionally have been generally contemplated,for instance petal et al [5]. Exhibited adaptable design for IoT information diagnostic utilizing the idea of edge registering that o ces the computerized changes among edge and cloud contingent upon the dynamic state of the IoT foundation and application necessities. Thus et al [6]. depicted an IoT platform that help solid and ensured information dispersal and investigation ( both at the edge and cloud ) for provincial and remote regions were the remote foundation is saves , requiring long - go multi-bounce availability to remote sensors and actuators et al [4].
Proposed a fog level IoT analysis system that uses e ective information extraction innovation to lessen the measure of information that would be transmitted to the cloud and disentangles the whole transmission pro-cess , then again haze registering portrayed by stretching out distributed computing to the system edge has become popular expression to day.
1.4 Research Objectives
The main idea of the research work is resource allocation fog of iot transferring data packet over connected network save time and money.
improved communication between connected electronic devices
ability to access information from any where at any time on any device.
©DAFFODIL INTERNATIONAL UNIVERSITY 5
1.5 Organization of Thesis
This thesis contains six chapter. We explain as following chapter one: general in- troduction resource allocation fog of iot and it consist the motivation and related works research objectives and also outline methodology. (chapter two: this chapter covers all the detail fog of IoT history of IoT how it works why IoT is important bene t of IoT. IoT standards and frameworks IoT security and privacy and last the future of IoT. (chapter three: this chapter covers the resource allocation IoT. (chap-ter four: proposed solution and it shows proposed method for resource allocation nding available resource, mapping assets to IoT fog nodes. (chapter ve: shows the result of proposed solution it details results changing possibility of failure changing quantity of probable requests chapter six the last part of thesis and it concluded the thesis.
©DAFFODIL INTERNATIONAL UNIVERSITY 6
Chapter 2 Fog of Iot
2.1 Introduction
The internet of things IoT is new technology that interconnected many devices that uses di erent ways such us heath monitoring business industries and etc that uses internet the internet of things or IoT is an arrangement of interrelated registering gadgets mechanical and advanced machines Objects animals or individuals that are furnished with one of a kind identi ers (UIDs) And the ability to move data over a framework without anticipating that human should human or human to PC corre-spondence A thing in the trap of things can be a person with a heart checking embed
, a domesticated animals with a biochip transponder an auto convenient that has worked in sensors to alert the driver when tire pressure is low or some other ordinary or man- made article that can be distributed an IP address and can move data over a framework . Dynamically relationship in a combination of adventures are using IoT to work all the more productively margarine grasp customers to movement over-hauled clients administration improve fundamental initiative and addition the value business [7]. Fog computing registering expands the idea of distributed computing to the system edge, making it perfect for web of things (IoT) and di erent applications that require constant interactions.computing is decentralized guring framework in which information gure stockpiling and applications are found some place the infor-mation source and the cloud like edge registering mist registering brings the favorable circumstances and intensity of the cloud nearer to where information is made fol-lowed up on Many individuals utilize the terms of haze registering and edge guring
6
©DAFFODIL INTERNATIONAL UNIVERSITY 7
conversely on the grounds that both include carrying insight and preparing nearer to where the information made this is frequently done to improve pro ciency however it might likewise be utilized for security and consistence reasons Many web of thing applications mist processing is regularly utilized [3] its appropriated methodology tends to the requirements of IoT and modern IoT just as monstrous measure of information savvy sensors and IoT gadgets produce which will be utilized expensive and tedious to send to cloud for preparing and investigation ,mist registering lessens the transfer speed required and decrease the back and foam correspondence among sensors and the cloud which can adversely impact execution despite the fact that in-activity might be ennoying when sensors are a piece of gaming application delays in information transmission in numerous genuine world IoT situations can be perilous for instance in vehicle to vehicle correspondence framework keen lattice organization or tel medication and patient consideration condition, where millisecond meter haze guring and IoT utilizes cases additionally incorporate shrewd rail, fabricating and uses.
2.2 Iot Architecture
Considering remarkable open entryways IoT ensures, more a liations search for the thought of its things in their business structures. Nevertheless, with respect to this present reality, this awe inspiring thought shows up too tangled to perhaps be executed given the amount of devices and conditions expected to make it work[8]. Toward the day’s end, the issue of working up a reliable designing of Internet of Things unquestionably enters the stage. Among all to deal with the whole collec-tion of components impacting IoT building, it’s less complex and logically amazing to nd a strong provider of IoT courses of action [9]. This decision will basically reduce the amount of advantages spent in travel.
Disregarding the way that it’s pos-sible to comprehend the path toward making programming, the practical use of its 4 stages contains an exorbitant number of nuances and perspectives to be depicted in direct words. Thusly, use this guide for working up a suitable comprehension of what’s happening during IoT engineering however consider alluding to the au-thority to make this procedure really occur. This choice will encourage getting the
©DAFFODIL INTERNATIONAL UNIVERSITY 8
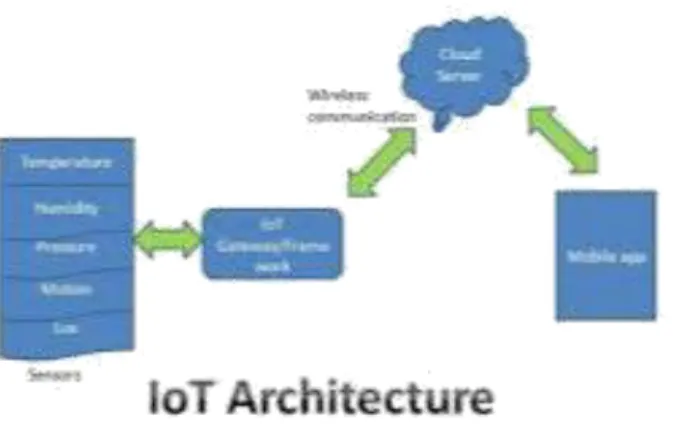
Figure 2.1: Iot Architecture
required outcome and assurance being a ful lled customer of a product improvement organization Prior to uncovering the privileged insights and giving an unmistakable structure of this activity, it’s imperative to comprehend what this idea really implies
[8]. Fundamentally, IoT design is the arrangement of various components: sensors, conventions, actuators, cloud administrations, and layers. Given its intricacy, there exist 4 phases of IoT design. Such a number is picked to consistently incorporate these di erent kinds of segments into a re ned and brought together system. Also, Internet of Things engineering layers are recognized so as to follow the consistency of the framework. This ought to likewise be thought about before the IoT engineering procedure start.
2.3 IoT Standards and Frameworks
There are a few rising IoT guidelines including:
6 LoW PAN (IPv6 over Low - Power Wireless Personal Area Networks), an open standard portrayed by the Internet Engineering Task Force (IETF). The
6 LoW PAN standard enables any low-control radio to pass on to the web, including 804.15.4, Bluetooth Low Energy and Z-Wave (for home computeri-zation).
Zig Bee, a low-control, uninformed rate remote framework used for the most part in current settings.
Zig Bee relies upon based the IEEE 802.15.4 standard.
©DAFFODIL INTERNATIONAL UNIVERSITY 9
The Zig Bee Alliance made Dot detect, the broad language for IoT that engages sharp things to work securely on any framework and see each other.
Light OS, a Unix like working structure for remote sensor frameworks. Light OS supports PDAs, wear ables, sharp collecting applications, splendid homesand Internet of Vehicles (IoV). The working system moreover lls in as a wise gadget progression stagea.
One M2M, a machine to machine organization layer that can be introduced in programming and gear to relate contraptions. The overall systematization
body, One M2M, was made to make reusable checks to enable IoT applications transversely over di erent verticals to bestow.
DDS (Data Distribution Service) was made by the Object Management Group (O M G) and is an IoT standard for constant, versatile and tip top machine-to-machine correspondence.
AMQP (Advanced Message Queuing Protocol), an open source appropriated standard for nonconcurrent illuminating by wire. AMQP engages encodedand cover operable educating among a liations and applications.
The show is used in client/server illuminating and in IoT contraption the o cials.
CoAP (Constrained Application Protocol), a show arranged by the IETF that decides how low- control gure constrained gadgets can work in the snare of
things.LoRa WAN (Long Range Wide Area Network), a show for wide zone composes, it’s planned to support colossal frameworks, for instance, sharp ur-ban territories, with an enormous number of low-control devices.IoT structures include:AWS IoT, a cloud organize for IoT released by Amazon. This structure is planned to enable insightful devices to easily relate and securely speak with
the AWS cloud and other related gadgets.ARM Mbed IoT, a phase to make applications for the IoT reliant on ARM littler scale controllers. The goal of the ARM Mbed IoT organize is to give aversatile, related and secure condition for IoT contraptions by planning Mbed mechanical assemblies and organizations.
©DAFFODIL INTERNATIONAL UNIVERSITY 10
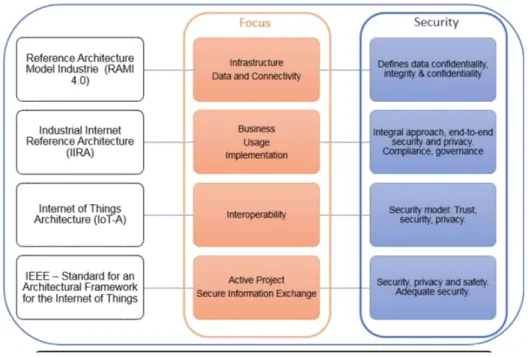
Figure 2.2: Iot Standards and Framework
Microsoft’s Azure IoT Suite, a phase that contains a great deal of organiza-tions that enables customers to work together with and get data from their IoT
devices similarly as perform various assignments over data, for instance, mul-tidimensional examination, change and aggregate, and imagine those exercises to such an extent that is proper for business. Google’s Brillo/Weave, a phase for the quick use of IoT applications.
The stage contains two basic spines: Brillo, an android-based working system for the improvement of introduced low power devices; and Weave, IoT-orchestrated correspondence show that lls in as the correspondence language between the gadget and the cloud.Calvin, an open source IoT arrange released by Ericsson planned for build-ing and regulating dispersed applications that engage gadgets chat with each other. Calvin consolidates an improvement structure for application architects similarly as a run time condition for dealing with the running application.
©DAFFODIL INTERNATIONAL UNIVERSITY 11
2.4 History of IoT
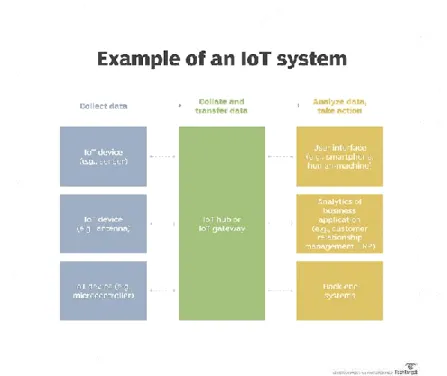
Kevin Ashton fellow benefactor of the auto ID focus at MIT originally referenced the internet of things in an introduction he made to Procter and Gamble (P and G) in 1999 needing to bring radio recurrence ID (RFID) to the consideration of P and Gs senior administration Ashton called his introduction internet of things to consolidate the cool new pattern of 1999 the web. MIT teacher Neil Gershenfeld’s book, When Things Start to Think, additionally showing up in 1999 didn’t utilize the accurate term yet gave a sensible vision of where IoT was going. IoT has progressed from the association of remote developments, scaled down scale electro mechanical structures (MEMS), little scale organizations and the web. The association has helped tear down the storage facilities between operational advancement (OT) and information development (IT), enabling unstructured machine-made data to be analyzed for bits of information to drive improvements.Although Ashton’s was the primary notice of the web of things, associated devices has been around since the 1970s, under the monikers implanted web and unavoidable computing.The rst web appliance,for case, was a Coke machine at Carnegie Mellon University in the mid 1980s. Using the web, engineers could check the status of the machine and choose if there would be an infection drink foreseeing them, should they decide to make the excursion to the machine.The rst web device, for example, was a Coke machine at Carnegie Mellon University in the mid 1980s.Using the internet,engineers could check the status of the machine and choose if there would be an infection drink foreseeing them, should they decide to make the outing to the machine.The web of things is more over a trademark extension of SCADA (supervisory control and data procurement),a class of programming application program for process controlthe get- together of data ceaselessly from remote zones to control apparatus and conditions.
SCADA systems join hardware and programming fragments. The hardware amasses and feeds data into a PC that has SCADA programming presented, where it is then arranged and showed it in a fortunate manner. The progression of SCADA is with the ultimate objective that late-age SCADA structures shaped into unique IoT systems.
©DAFFODIL INTERNATIONAL UNIVERSITY 12
Figure 2.3: Example of an IoT System
2.5 Why Iot is Important?
the internet of things helps people with living and work increasingly splendid simi-larly as supervise there lives despite o ering sharp gadget to robotize homes [10].IoT give is essential to business. IoT provides for associations a progressing research how their associations structure real work passing on bits of information into everything from the introduction of machines from to the creation system and collaborations exercises IoT engages associations to automate shapes and lessen work costs it in like manner kills waste and improves organization transport making it progressively rea-sonable amassing and movement stock similarly as o ering straightforwardness into customer transection IoT contacts every industry, including healthcare [10] money ,retail and assembling in shrewd urban areas assist residents with diminishing waste and vitality utilization and interfacing sensors are even utilized in cultivating to as-sist screen with editing and steers yields and foresee development designs All things considered, IoT is one of the most signi cant advancements of regular daily existence and it will continua to get steam as more organizations understand the capability of associated gadget to keep them aggressive .
©DAFFODIL INTERNATIONAL UNIVERSITY 13
2.6 Bene ts of IoT
The internet of things o ers a number of bene ts to organizations enabling them to Monitor their overall business processes
Improve the customer experience Save time and money
Enhance employee productivity
Integrate and adapt business models Make batter business decision
Generate more revenue
IoT encourages companies to rethink the ways they approach their businesses , industries and markets and gives them the tools to improve their business strategies [8].
Some of the advantages of IoT include :
Capacity to get to information from wherever at whatever point on any gadgets Improved correspondence between related electronic gadget
Moving data packages over a related framework puts aside time and money Robotizing assignments improves the idea of a business , bene ts and decreases the necessity for human intercession
Some disadvantage of IoT include
As the amount of related contraptions augmentations and more information shared between gadgets the potential that developer could take characterized similarly increases Endeavors may over the long haul need to oversee enormous numbers { may be even millions of IoT devices and social occasion managing the data from
every single one of those gadgets will challenges
©DAFFODIL INTERNATIONAL UNIVERSITY 14
if there is a bug in the structure its likely that each related gadgets will get degraded Since there is no worldwide standard of comparability for IOT its issue for contraptions from di erent makers to talk with one another
2.7 How IoT Works
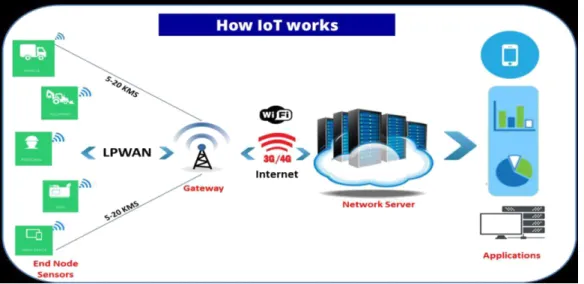
IoT biological system comprise of internet empowered savvy devices that utilization installed processors, sensors and correspondence equipment to gather send and follow up on information they obtain from their condition. IoT device share the sensor information they gather by interfacing with an IoT entryway or other edge device where information is either sent to the cloud to be examined or dissected locally.a few times these device speak with other related device and follow up on the data they get from one other the device do the greater part of the work without human intercession in spite of the fact that individuals can connect with the device for example to set them up, give them guidance or access the information, the availability, systems administration and correspondence conventions utilized with these web-empowered device to a great extent rely upon the particular IoT application conveyed, An IoT framework comprises of sensors/devices which "talk" to the cloud through some sort of availability. When the information gets to the cloud, programming forms it and afterward may choose to play out an activity, for example, sending a caution or consequently changing the sensors/devices without the requirement for the client. Be that as it may, if the client information is required or if the client basically needs to monitor the framework, a UI enables them to do as such. Any alterations or activities that the client makes are then sent the other way through the framework: from the UI, to the cloud, and back to the sensors/devices to make some sort of progress.
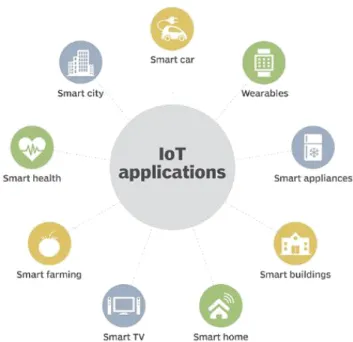
2.8 IoT Applications
There are many di erent applications of iot such as smart home, wearables, smart cities industries healthcare and more di erent applications The Internet of Things
©DAFFODIL INTERNATIONAL UNIVERSITY 15
Figure 2.4: How IoT Works
can be utilized in various parts of life, in both the private and open divisions. On account of IoT, individuals can follow things like lost pets, their home’s security frameworks, or apparatus support plan [11]. Buyers can utilize the IoT to assist them with making eatery reservations, screen their activity progress and in general wellbeing, and get coupons for a store just by righteousness of strolling by the busi-ness being referred to. Organizations can utilize IoT to screen supply chains, track clients’ ways of managing money also gather their criticism, screen and keep up stock levels, and take part in prescient upkeep of their machines and device.There are various true utilizations of the web of things, running from customer IoT and undertaking IoT to assembling and modern IoT (IIoT) [12]. IoT applications length di erent verticals, including vehicle, telecom and essentialness. In the customer seg-ment, for example, wise homes that are equipped with sharp indoor controllers quick machines and related warming lighting and electronic devices can be controlled re-motely by methods for PCs and mobile phones. Wearable devices with sensors and programming can assemble and inspect customer data, sending messages to various developments about the customers with the purpose of making customers’ lives more straightforward and progressively pleasing. Wearable gadgets are moreover used for open security - for example, improving individuals accessible as needs be’s response times during emergencies by giving streamlined courses to a region or by follow-ing advancement workers’ or re ghters’ pivotal signs at perilous destinations [13]. In medicinal services, IoT o ers numerous advantages, including the capacity to
©DAFFODIL INTERNATIONAL UNIVERSITY 16
Figure 2.5: Iot Applications
screen patients all the more near utilize the information that is produced and inves-tigate it. Emergency clinics regularly use IoT frameworks to nish assignments, for example, stock administration, for the two pharmaceuticals and medicinal instru-ments. Brilliant structures can, for example, lessen vitality costs utilizing sensors that distinguish what number of inhabitants are in a room. The temperature can change subsequently for example, turning the constrained air framework on if sen-sors perceive a social a air room is full or turning the glow down if everyone in the working environment has come all the way back. In agriculture, IoT based splendid developing systems can help screen, for instance, light, temperature, moisture and soil sogginess of yield elds using related sensors. IoT is also instrumental in mo-torizing water framework frameworks.In a splendid city IoT sensors and plans, for instance, insightful streetlights and adroit meters, can help ease tra c, safeguard essentialness, screen and address natural concerns and improve sanitation[13] .
©DAFFODIL INTERNATIONAL UNIVERSITY 17
Figure 2.6: IoT Security and Privacy
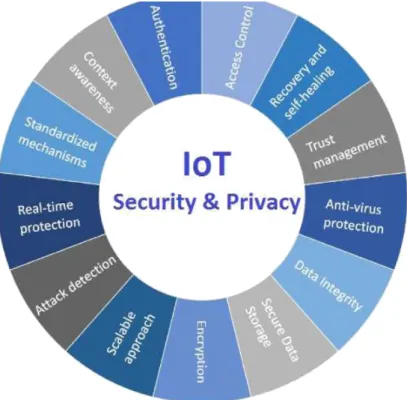
2.9 Iot Security and Privacy Issues
The internet of things partners billions of gadget to the web and incorporates the usage of billions of data coordinates all of which need toward be con rmed as a result of its expended attack surface IoT security and IoT assurance are refered to as noteworthy stress In 2016 one of the most acclaimed late IOT ambushes was mirai a botnet that attacked space name server provider DYN and cut down various locales for a widely inclusive time period in one of the best passed on renouncing of organization (DDoS) ambushes anytime seen aggressors got to the framework by mishandling de ciently checked IoT gadget considering the way that IoT gadget are solidly related all of the a software engineers needs to do is abuse one lack of protection to control all of the data rendering it unusable makers that don’t invigorate their contraption reliably or at all leave them defenseless against advanced guilty parties [14]. IoT has ended up being one of the most gigantic segments of things to come Internet with a monster impact on open action and business circumstances.
As talked about in area bigger number of IoT applications and administrations are progressively helpless to assaults or data burglary. To verify IoT against such
©DAFFODIL INTERNATIONAL UNIVERSITY 18
assaults, cutting edge innovation is required in a few zones. More in particular, veri cation, classi cation, and information uprightness are the key issues identi ed with IoT security . Con rmation is fundamental for making a relationship between two gadgets and the exchanging of some open and private keys through the center point to balance data thievery. Mystery ensures that the data inside an IoT device is gotten away unapproved substances. Data uprightness maintains a strategic distance from any man-in-the middle change to data by ensuring that the data appearing at the recipient center point is in unaltered structure and remains as transmitted by the sender. Also associated gadget regularly request that clients contribution to enter that individual data including [14]. name, ages ,addresses , telephone numbers , and even online networking accounts data that is signi cant to programmers. In any case, programmers aren’t the main danger to the web of things security and other signi cant worry for IoT clients for example organizations that make and convey buyer IoT device cloud utilize those gadget to get and cell clients individual information past releasing individual information IoT represents a hazard to basic foundation. Incorporate power transportation and budgetary assistance
2.10 The Future of IoT
There is no shortage of IoT market estimations for example a few include
Bain & company expects annual IoT revenue of hardware and software to exceed
$450 billion 2020
Mckinesy & company estimates IOT will have an $11.1 trillion impact by 2025 markit believes the number of connected IOT devices will increases 12% an- nually to reach 125 billion in 2030
Gartner assesses that 20.8 billion connected things will be in use 2020 with the total spend on IOT devices and services to reach 3.7 trillion in 2018
©DAFFODIL INTERNATIONAL UNIVERSITY 19
Chapter 3
Resource allocation
3.1 Introduction
Asset designation is the way toward appointing and overseeing resources in a way that supports un association Strategic objectives asset distribution incorporates overseeing unmistakable resources such us equipment to utilize gentler resources such us human capital. The IoT device are utilized to produced information which changes into use able data and gives applied assets to end of client this procedure is the fundamental objective of IoT thusly one of the signi cant subject in the IoT is asset distribution which points is burden adjusting and limiting operational ex-pense ,and power devouring more over the asset ought to be allocatted in such away to be adjusted e ectiveness that can build the framework execution, nature of ad-ministration (QOS) and administration level understanding (SLA) despite the fact that the asset portion is signi cant in the IoT In numerous IoT applications, for example, condition monitoring,although there is countless IoT clients, every client only generates a moderately limited quantity of information[15].
this empowers the gateway to gather information from a monstrous number of devices,some correspon-dence advances have been examined to connect those devices, a psychological radio empowered Time Division Long Term Evolution (TD-LTE) proving ground has been proposed to powerfully get to range over TV void area in .A moderately new class of correspondence conventions, described as low-control wide-region (LPWA) sys-tems, are coming to the fore as they devour lower control in the IoT device while their transmission degree covers geologically bigger area.More over, LPWA o ers
©DAFFODIL INTERNATIONAL UNIVERSITY 20
an exchange o among information transmission rate, organize inclusion and power utilization, to meet a large assortment of necessities on IoT applications .LPWA frameworks accomplish this level of inuence and separation at the cost of low in-formation transmission rate which makes it more appropriate for idleness tolerant IoT applications with smaller data requirements.The existing LPWA advances
3.2 Energy e cient Resource allocation
The productive asset allotment (RA) approaches are originally explored for stream-lining the OMA frameworks ,and they will give another level of opportunity for NOMA systems. The examinations for RA in NOMA frameworks have drawn a parcel look into considerations on the improvement of spectrum e ciency (SE) or aggregate rate [16]. In the low-complexity polynomial calculation has been proposed to approximately solve the non-curved power allotment issue. While, the authors in have examined the decoupled issue of the user grouping and power portion in the NOMA systems,where the proposed U C depends on comprehensive pursuit ap-proach with high multifaceted nature required.
As of late, inspiring to maximizing entirety rate, Lian get al have proposed one tone matching based client blending and researched control allocation problem in the intellectual radio NOMA frame-works. Further,has proposed a novel sub channel portion approach for the downlink NOMA frameworks by utilizing many-to-many matching hypothesis. All the more as of late, look into endeavors have been devoted to asset the board in di erent NOMA systems,for model, the writers in have built up a joint power allocation and sub carrier apportioning plan for a low density spreading (LDS) numerous en-trance frameworks, for example a code-domain NOMA system.Energy utilization is turning into a signi cant social and economical issue for future remote correspon-dences especially with touchy information tra c. Thus, it is imperative to address energy e ectiveness (EE) when structuring NOMA frameworks. In, vitality pro - ciency of the single-transporter FDMA framework was studied, where the vitality productivity is measured in wording of the vitality utilization gain and the vital-ity decrease gain [16].
By the by, constrained research endeavors, for example,have been dedicated to the investigation of vitality pro cient in NOMA frameworks. Fan
©DAFFODIL INTERNATIONAL UNIVERSITY 21
get all have examined vitality e cient RA in for the downlink NOMA frameworks, where, however,the proposed slope based paired pursuit control allocation algorithm requires generally high intricacy. Moreover , it has proposed the novel power allot-ment algorithms which are EE- ideal and SE-ideal individually. Recent studies have applied NOMA to future machine-to-machine communications in and to millimeter wave (mm Wave)networks Curiously, the creators of have investigated the use of NOMA method in mm Wave networks by mutually concentrating the beam form-ing, client scheduling, and control allocation.Future 5G correspondences will request assorted service types, and need to help huge availability of clients and/or devices, just as meeting the necessities for low inertness,
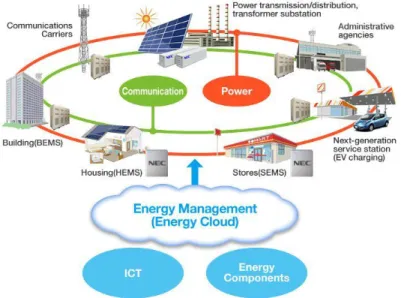
3.3 Smart Energy
Keen administration of vitality allotment and utilization, for example, brilliant me-tering, savvy lighting, and shrewd network has bunches of advantages for improving vitality productivity and saving energy cost. In addition, it can advance the use of sustainable power sources (e.g., sun powered energy and wind energy).[17] with shrewd lattices energy conveyance can be improved. These matrices likewise con-tinue gathering ongoing information which aides in disseminating power e ectively and furthermore to decrease the blackouts.
Figure 3.1: Smart Energy
©DAFFODIL INTERNATIONAL UNIVERSITY 22
3.4 Edge Resource Allocation for Multiple Applications
Gigantic information created By di erent assistance running on various IoT devices needs further preparing for applications facilitated in remote servers to accomplish rich astute capacities now the edge system relocates registering and capacity abilities closer to the nish of IoT devices and has conveyed engineering to adjust system tra c along these lines it can improve the( Q o S )of the brilliant urban communities administrations and maintain a strategic distance from tra c tops hence , the sen-sible allotment of constrained edge asset to various applications with the assorted qualities and prerequisite is especially signi cant the accompanying discourses give a few run of the mill necessities of some IoT applications for edge asset assignment the moved information may expend a gigantic sum of data transmission and vitality of the center system. On the other hand, [17] since the remote cloud is a long way from IoT clients which send application demands and anticipate the outcomes created by the information preparing in the remote cloud, the reaction time of the solicitations might be excessively long, particularly terrible for delay delicate IoT applications. Along these lines, cloudlets, which bring processing assets near IoT gadgets and IoT clients, can be utilized to mitigate the tra c load in the center system furthermore, limit the reaction time for IoT clients.
Figure 3.2: Edge Resource Applications
3.5 Smart Healthcare Resource Allocation
Peoples neglect of health and social limited medical resource lead to very urgent need for the smart healthcare wearable device carried with patients such us smart
©DAFFODIL INTERNATIONAL UNIVERSITY 23
Figure 3.3: Smart Healthcare
as bracelets and blood pressure and sugar detectors are able to monitor a variety of human health indicators while doctors can collect real time raw data through these IOT smart device therefore doctors and patients will be greatly facilitated with re-duced medical cost and enirched expirence [17] medicinal services toward the mix of Cloud and IoT doesn’t meet the prerequisites. Bringing this reconciliation with regards to medicinal services can essentially add to building pro cient human ser-vices applications for overseeing and observing emergency clinics and patients in an productive way with respect to asset sharing and cost consumptions. In view of Cloud and IoT , remote human services checking and the executives data adminis-trations can e ectively give early discovery and treatment of constant maladies that signi cantly a ect individuals’ well being. That is, IoT body sensors, implantable or wearable) assemble the necessary data from an individual, and afterward the data can be investigated and prepared in Cloud The utilization of CoT in medicinal servces area o ers new chances to restorative IT framework,[18] and can upgrade social insurance bene ts Moreover, CoT improves the social insurance forms and the nature of the genuine human services bene ts by improving the way toward social occasion patients crucial information and conveying them to a restorative focus on Cloud for capacity and handling purposes. As it were, the utilization of CoT in Body Sensor Network based human services helps during the time spent putting away -
©DAFFODIL INTERNATIONAL UNIVERSITY 24
sembled information, just as preparing and dissecting them in an adaptable style. With CoT, human services sensors can be over seen e ectively in a straight forward way just as make any managing delay sensitive human services bene ts increasingly productive To accomplish e ective social insurance administrations with respect to delay-touchy and vitality utilization, haze processing can assume an essential job by bringing down the weight on Cloud just as going about as a nearby capacity for IoT devices and its capacity to do some preparing on the information [18].
©DAFFODIL INTERNATIONAL UNIVERSITY 25
Chapter 4
Proposed solution
4.1 Introduction
Conventional IoT models interface the detecting device s to the Internet and send the produced information to a cloud asset for handling. This system functions ad-mirably for the applications where exacting postponement is not a worry. Cloud isn’t a perfect asset for the applications which require constant reactions. This is the explanation, areas, for example, media transmission, social insurance, constant control and so forth process the information closer to the birthplace in [19]. This computational worldview is named as edge registering. In [20] suggested that the edge guring needs to use every one of the assets associated at the system edge, for example, workstation, tablets, work areas, cell phones and so forth. In spite of the fact that, these devices are not constantly associated with the Internet, they can in any case be utilized astutely for di erent computational undertakings. Presently a days, devices at the system edge, for example, PCs and personal computers are by and large intentionally o ered by the proprietors for computational purposes. Efcient use of all these computational assets upgrades the general limit of the edge framework and enables it to scale. The trafc towards the center IP system can like- wise be decreased signicantly. In such manner, we have exhibited a self-arranging edge framework laid on the standards of SDN We propose a keen programming dened Edge Controller (EC) in IoT condition, which congures the foundation to use all the accessible assets efciently for information handling. This EC learns di erent parameters for asset improvement during introductory runs. In the wake of procur-
©DAFFODIL INTERNATIONAL UNIVERSITY 26
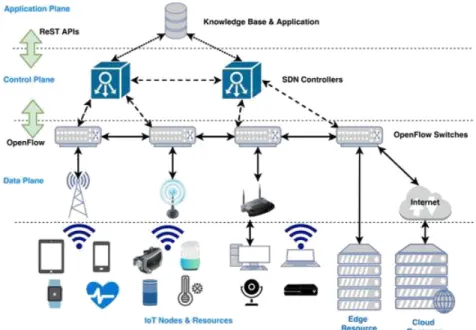
Figure 4.1: SDN Based IoT Architecture
ing sufcient data, a whole number direct programming issue for minimization of time to nish solicitations is planned and fathomed. The arrangement guarantees reason-able assignment of the solicitations to di erent assets in such away that the absolute time for demand ful llment is limited for every one of the hubs.The dependability of the deliberate assets is another signi cant issue which is canvassed in this section. Ordinarily a computational asset acknowledges a solicitation, yet can not process it in an opportune way. It might happen due to the battery blackout, planning of other higher need assignments, association restoration because of versatility and so on. Doling out idleness delicate assignments to such devices is a hazard. The plan accomplished for minimization of time to nish solicitations has been reached out to consolidate dependability measures.
A multi-target advancement issue is de ned and understood utilizing Genetic Algorithm (GA). The answer for the issue gives the distributions which dependably forward the solicitations to the accessible assets.
4.2 Proposed Method for Resource Allocation
Figure 4.1 shows the proposed framework where the IoT hubs and the assets are associated through OF switches at the information plane. OF switches are designed
©DAFFODIL INTERNATIONAL UNIVERSITY 27
by the SDN controller at control plane utilizing OF convention. On the highest point of the control plane, application plane lives. It speaks with SDN controller utilizing ReST APIs. Application plane assembles the information required for ideal asset distribution.
Utilizing the put away information, it discovers the ideal asset distribution and imparts the equivalent to EC. At long last, EC pushes proper arrangements to the OF switches.
Figure 4.2 outlines the framework stream graph. This stream outline covers every one of the means associated with learning and asset assignment. Here, the objective is to plan a framework, where the all out time to process the solicitations made by IoT hubs can be limited. So as to accomplish this goal, proposed framework experiences a learning stage.
Learning begins with social event data about accessible assets and their abilities. Utilizing this data the EC arranges the OF changes to advance every one of the solicitations made by IoT hubs to every one of the assets in a cooperative e ort (RR) design. In this procedure, EC distinguishes the postpone associated with nishing of a solicitation between an IoT hub and an asset and anticipated number of solicitations from an IoT hub. Once, the framework has required data, EC starts sending the solicitations so that the absolute time to process the solicitations made by IoT hubs is limited. This element makes our controller self-arranging. The means engaged with learning procedure have been portrayed in detail in up and coming segments.
4.2.1 Finding Available Resources
The initial move towards making the framework self-sorted out is to assemble total data about the accessible assets in the framework. Prior to booking the solicita-tions, the EC must know about the accessible assets for calculation. In various IoT condition, various hubs may utilize various systems and conventions for ad-ministration commercial and revelation. Hubs may utilize brought together or dis-seminated approaches for asset disclosure. In a Constrained ReSTful Environment (CoRE) [21] the devices use CoRE connection design 1 for asset disclosure. Hubs can likewise utilize Resource Discovery Protocol (RDP). Both the conventions bol-ster server/customer model for asset disclosure. In such concentrated design, the RDP customers (or assets) send the asset data as an all around built question to the RDP server and the server stores this data in an asset registry. The hubs searching
©DAFFODIL INTERNATIONAL UNIVERSITY 28
Figure 4.2: System Flow Diagram
for assets send inquiry to RDP server and the server reacts appropriately. Assort-ment of other assistance disclosure conventions in IoT setting can found in [21]. It is accepted that RDP question will contain most extreme capacity of the asset.The data about help instruments and asset databases is given as an arrangement to the proposed framework.
At re up, it parses the design document and arranges the OF based SDN switches in the framework to catch these asset data bundles about the accessible assets. For instance, say the devices declare their capacity by means of RDP and this data is referenced in the design. The switch stream tables are designed by the edge controller to get RDP declaration streams on referenced convention and port. The edge controller parses these streams and updates its learning base about accessible assets. On the o chance that there is a RDP server in the framework, EC sends the RDP inquiry to get data about accessible assets by means of parcel out component. It is expected that the whole framework is likewise associated with cloud assets and the EC has this data. Figure 4.3 portrays a similar thought.
©DAFFODIL INTERNATIONAL UNIVERSITY 29
Figure 4.3: Learning Asset Accessibility and Capacity
4.2.2 Mapping assets to IoT fog Nodes
When EC has the rundown of accessible assets and the most extreme solicitations they can deal with, it starts sending solicitations originating from IoT hubs to ac-cessible assets in a RR way. Before doing this, EC arranges the SDN changes to declare the default asset address for all the accessible administrations. IoT hubs searching for assets, get theories warnings and start sending solicitations to declared default entryway. The EC arranges the SDN switches so that the solicitations go to all the accessible specialist organizations individually. For diverting the solici-tations to di erent assets, switches change the goal address of a solicitation from default passage to a chose asset. For instance, a camera- prepared IoT hub needs the caught pictures to be grouped. It gets the default asset data and starts send-ing solicitations to the referenced location. Because of the switch arrangement, the goal of the solicitation changes and the primary solicitation is sent to most readily accessible picture characterization specialist co-op. The subsequent solicitation is sent to another specialist co-op. This procedure continues for ensuing solicitations in a RR way.
With the examination of solicitations and reactions EC maps the IoT hubs to the assets with di erent measurements, for example, handling delay and the quantity of anticipated solicitations from an IoT hub.
©DAFFODIL INTERNATIONAL UNIVERSITY 30
Figure 4.4: Learning Demand Finishing Time (MTTC) from IoT Node to the Resources 4.2.2.1 Learning demand nishing time
It has been just talked about that IoT condition is heterogeneous. Administration giving hub can be associated through various media get to conventions. They can have diverse handling capacities. They can be static or portable. Every one of these circumstances change the ideal opportunity for handling a solicitation. By means of sending solicitations to every one of the assets in a RR way, our controller nds out about the normal time taken for nishing a solicitation. Figure 4.4 clari es the thought pictorially. So as to locate the slipped by time in handling a solicitation, EC designs the change to send warning bundles to itself when a solicitation is sent to an asset and asset sends the reaction back.
Investigating the time contrast, EC distinguishes the postpone included. This deferral is likewise named as Mean Time to Complete (MTTC). This procedure is rehashed for each pair of IoT hub and asset.
4.2.2.2 Forecasting number of probable requests
During the time spent sending solicitations to all the accessible assets, the EC like-wise decides the quantity of expected solicitations from an IoT hubs in a term. While sending demands in a RR way, the EC gets the solicitation warning (as EC designed
©DAFFODIL INTERNATIONAL UNIVERSITY 31
Figure 4.5: Forecasting Number of Probable Requests from IoT Nodes
Figure 4.6: The Resource Allocation Problem and the System With Acquired Knowledge
the switches for learning MTTC, referenced in past subsection 4.2.2.1). The EC spares these records with a period stamp. At the point when adequate informa-tion is gathered, application plane breaks down the information and conjectures the normal number of solicitations in future. Neural systems or profound learning based time arrangement investigation methods can be utilized by the application plane to foresee the normal number of solicitations later on. Figure 4.5 clari es the equivalent.
©DAFFODIL INTERNATIONAL UNIVERSITY 32
4.2.2.3 Knowing resource reliability
Numerous elements can choose the unwavering quality of an asset. Versatility, con-trol (battery), outstanding task at hand, security and so forth are hardly any such parameters.
The unwavering quality of an asset goes down if there should arise an occurrence of low battery condition. Thus, on the o chance that it is exchanging crosswise over passageways or a client is running computational broad application right now, it is unsafe to advance a solicitation to that asset. In our investigation, the dependability of an asset is named as the quantity of reactions sent in a convenient way for each solicitation. As referenced in above area, the EC designs the change to discover the preparing postpone engaged with sending a solicitation from IoT hub to an asset. EC utilizes this planning in acknowledging dependability of an asset. In the event that the time contrast between a solicitation and reaction is in excess of an edge, it is probably not going to meet the application necessities. Henceforth, the EC lessens the unwavering quality of such an asset or at the end of the day it expands the likelihood of disappointment of that speci c asset. Genuine unwavering quality worth is determined as the proportion of auspicious sent reactions (nres) to the absolute sent solicitations (nreq) for example nres/nreq (allude Algorithm 1). A similar thought is portrayed in Figure 4.7.
Figure 4.7: Predicting Resource Reliability
©DAFFODIL INTERNATIONAL UNIVERSITY 33
©DAFFODIL INTERNATIONAL UNIVERSITY 34
Chapter 5 Results
The genetic algorithm is been used in order to solve the optimization problem. Using the function gamultiobj() in MATLAB is used to code and solve the problem. The initial con guration parameter in mentioned in Table 1. In this methodology, the arrangements are kept in three bunches. The First bunch has values with low post-ponement and high likelihood of disappointment. In opposition to that, the third group has values with high postponement and low likelihood of disappointment. In contrast to rst and third groups, the arrangements in the subsequent bunch are not outrageous. Thus, an answer from bunch 2 is picked haphazardly what’s more, the solicitations from IoT hub to the assets are designated appropriately. To con rm the proposed assignment methodology, the situation according to gure 5.1, has been held under examination. N1, N2 and N3 are three information creating IoT hubs. Handling is required on the created information. For engaging the solicitations orig-inating from IoT hubs, assets R1, R2 and R3 are accessible in the framework. R1 is a devoted edge asset and it can react to 100 solicitations for each unit time. It is stationary and has availability by means of Ethernet. It has repetitive power and capacity. Consequently, the likelihood of disappointment is exceptionally low (.01).
R3 is a cloud-associated asset. It is exceptionally adaptable and can process 500 solicitations for every unit time. The likelihood of R3’s disappointment is likewise extremely low (.01). Asset R2 is a versatile hub. It is battery fueled, associated by means of WLAN or 4G connect. When R2 is versatile, it switches crosswise over access di erent focuses. Subsequently, the unwavering quality of R3 is lesser than R1 and R3. The likelihood of disappointment for R2 is 0.1 and it can process 20
©DAFFODIL INTERNATIONAL UNIVERSITY 35
solicitations for every unit time.
Table 5.1: Initial parameters used in GA for multi-objective optimization problem
Parameter Value Details
CreationFcn @gacreationuniform Initial population is chosen with uniform distribution.
CrossoverFcn @crossoverintermediate Children are created using weighted average of parents.
CrossoverFraction 0.8 Next generation population frac-
tion.
DistanceMeasureFcn @distancecrowding, Measure distance of individuals in
’phenotype function space.
FunctionTolerance 10 4 If relative change is less than this value, the algorithm stops.
MaxGenerations 1800 Maximum iterations.
MutationFcn @mutationadaptfeasible Random changes in individu- als depend upon last success- ful/unsuccessful generation.
PopulationSize 200 Initial population size.
SelectionFcn @selectiontournament Parents for next generation are chosen by tournament of size 4
R1 is introduced near N1 and N2. In this way, N1 and N2 get fast reactions for the solicitations sent to R1. In the event that the solicitations are sent to R2 or R3, an opportunity to get the reaction increments. Correspondingly, N3 is nearer to R2, so the postpone associated with getting the reactions for R1 and R3 is higher when contrasted with R2.
The framework begins for the most part by gathering the accessible asset data. With accessible asset data close by, the EC arranges the changes to advance the solicitations in a RR way. In the learning procedure the framework not just nds out about the interim to nish demands and the normal number of solicitations from each IoT hub yet additionally, it monitors the likelihood of disappointment of an asset utilizing the algorithm 1. With this data, the application plane takes care of the multi-target enhancement issue utilizing
©DAFFODIL INTERNATIONAL UNIVERSITY 36
Figure 5.1: Experimental Scenario
GA and advances the portion to the EC. The EC gets the ideal portions from the application plane and designs the OF switches in like manner. For testing the plan following two conditions have been considered.
5.1 Changing possibility of failure
For this situation, the allotments are seen with di ering likelihood of disappointment of asset R2. As talked about already, R2 is a versatile asset and it will most likely be unable to process assigned demands in an opportune way because of conditions, for example, battery blackout, change of passageway and so forth. Consequently, it is important to comprehend the asset assignment changes with uctuating likeli-hood of disappointment of asset R2. The quantity of expected solicitations from N1, N2 and N3 are 50, 100, 30 individually. The R2’s likelihood of disappointment is changed from 0.1 to 0.9. Figure 3.17 shows the di erent assignments with expanding likelihood of disappointment of R2.
Instinctively, with the ascent in likelihood of disappointment of R2, the EC ought to advance less number of solicitations to R2. Results in gure 5.3 a rm this conduct. With the ascent in likelihood of disappoint-ment, EC moves the portions from R2 to R3. R1 is completely used, so there are no solicitation shifts from R2 to R1. Figure 5.2 portrays the quantity of dispensed solicitations to R2 and R3 with increment in R2’s likelihood of disappointment. It is
©DAFFODIL INTERNATIONAL UNIVERSITY 37
Figure 5.2: Probability of failure of R2 Vs. Number of Allocated Requests.
plainly observed than the fall in number of allotted solicitations to R2 is equivalent to distributions added to R3.
5.2 Changing quantity of probable requests
True to form number of solicitations from di erent IoT assets may uctuate after some time, application plane refreshes EC about ideal designations for a given time
Figure 5.3: Number of requests allocated to an IoT node to resource with the varying reliability of R2. The probability of failure for resources R1, R2 and R3 are
(a) [.01 .1 .01] (b) [.01 .3 .01] (c) [.01 .5 .01] (d) [.01 .7 .01] (e) [.01 .8 .01] (f) [.01 .9 .01]
37