Introduction
Analysis of the Business Process of Outsourcing
Information Security Management Systems (ISMS) and Categorization of Data
Objectives of the study
Scope of the study
Methodology of the Study
Limitation
Company Overview
Company Analysis
7 Amco Enterprise Limited's bankers include Eastern Bank Limited (EBL) and Social Islami Bank (SIBL), which allows the company to efficiently and securely manage financial transactions related to its recruitment services. The company's memberships, partnerships and commitment to its clients and job seekers have allowed it to establish itself as a trusted and reliable recruitment agency in Bangladesh (Amco Enterprise Limited company profile, n.d.).
Company vision
Overall, Amco Enterprise Limited has demonstrated a strong track record of success in the international recruitment and placement industry, with a focus on providing professional and ethical services that meet the unique needs of each client.
Company mission
Management Hierarchy
Service offered
SWOT analysis
The article "Assessing the Effectiveness and Efficiency of an ISO-based Information Security Management System evaluates ISO 27001-based ISMSs. Under the direction of the CEO, each employee must commit to information security as part of their ability to enforce these regulations. This policy lays the foundation for managing information security across the organization and demonstrates management support.
It is the policy of the Information Security Team to report any incident involving information or IT security, as well as any other suspected violations of this policy. The Information Security Team will adhere to the Organization's recommendations for security incident escalation and reporting, and any data breach involving compromised personal information will be subsequently notified in accordance with the procedure. In accordance with SOA 2 dated June 26, 2018, the Information Security Management System (ISMS) includes a wide variety of operations, including data entry, processing, collection and verification.
Variables such as the number of interconnected systems, the potential for harm from those connections, the importance or sensitivity of the information source, and the needs of information security regulations all affect how often risks must be observed. If the allegations are proven to be true, the Information Security Team will respond in accordance with protocols established to handle incidents of this nature. Information Security Management System (ISMS) standards are defined in the only worldwide standard that can be audited, and that standard is ISO 27001.
An assessment of the effectiveness and efficiency of an information security management system based on the ISO 27001 standard. Have you received any training or education on information security management systems (ISMS) or data categorization in your current organization.
Related Literature review
Internship Experience
Position, Duties, and Responsibilities
Other than completing the tasks given to me by the trainers, my obligations as an intern were not very challenging.
Contribution to Departmental Functions
Evaluation
Skills Applied
New skills developed
Application of academic knowledge
The Information Security and Safety Manager oversees information security and provides guidance on how best to implement policies. Whether administered in-house or by a third party, all of Amco's information resources fall under the purview of Information Security Risk Management. Executives, systems engineers, stakeholders, and IT administrators must work with the appropriate Information Security Office to execute the information risk mitigation program.
To address the security breach or potential risk, an incident response team will be assembled and will operate under the direction of the CEO. As a result, the utilization of traditional cost-effectiveness assessments to support the certification of an information security. A company that has achieved this certification is able to claim that it uses the most up-to-date and effective information security processes.
What steps can individuals take to increase their awareness of information security best practices and contribute to a culture of security in their organization?
Data Evaluation and Interpretation
The Sorting and Categorizing of Data
To find out the level of sensitivity associated with a certain category of information, the first thing to do is to determine what kind of protection is required for that information. If there is information that varies significantly in terms of the degree of sensitivity included within the same system or termination, that information should be classified at the most sensitive level possible. Data protected by federal, state or local authorities, or by voluntarily set criteria such as the General Data Protection Regulation.
Name, phone number, account number, any part of a date (other than year) that is directly related to a person, such as date of birth, date of employment, date of discharge, or any other unique range, characteristic, code or combination that can be used to identify a person. All information that is legally protected as private or that is protected as confidential by contract, except for any other information that Amco Enterprise Ltd. Any information that is confidential or intended only for use by Amco Enterprise employees who are properly authorized to access such information.
The term "public information" refers to any information that is available to the general public and has no legal restrictions imposed on either its access or its use in any way.
Scope of ISMS
20 and evaluating security needs and threats is greatly enhanced by the Information Security Advisory Panel, which consists of supervisors from all major business units. Engagement with professional interest groups on the protection of sensitive information in project management. It is crucial to keep the company's reputation intact through accurate representation and use of official documents.
The need for periodic review, including compliance reviews of use and maintenance review of the policy.
Handling of the Risks Associated with Information Security
24 The Information Resource Risk Classification Policy applies universally to all types of information resources, including those used for data storage, analysis and transmission. Based on the data classification policy, information sources are classified according to their functions, susceptibility and level of exposure to risk. Controls will be evaluated in accordance with the above framework and implemented based on risk analysis.
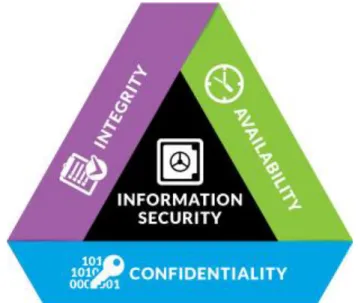
A documented risk analysis method is used to identify, define and prioritize risks based on the confidentiality, integrity and availability of information sources. In the event that the security measures taken for an information resource do not meet a certain security standard, risks are recognized and evaluated based on the following three factors: the possibility that the prospective risk will occur as well as the nature of the threat , the effectiveness or vulnerability of the existing security mechanisms, and the likely degree of consequence. The level of urgency and sensitivity of the measures is also increased in accordance with the type and extent of the occurrence.
Overall, risk mitigation is an essential component of information security, and the knowledge and skills I gained through my internship helped me realize how important it is to the process of protecting precious data resources.
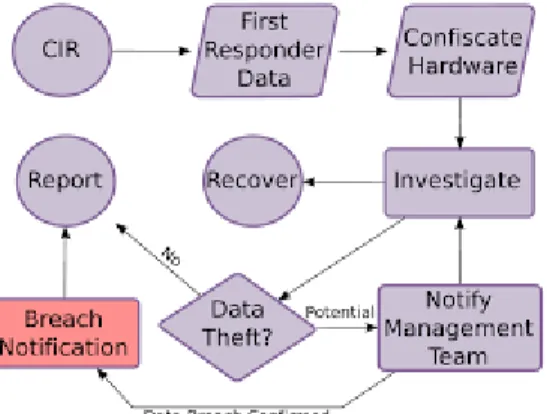
System for Responding to Data Breaches
Observing unusual system behavior, which may indicate the presence of a virus or other form of malicious activity. Mistakes made by people that compromise information technology security or violate IT standards, such as keeping passwords on a computer that is accessible to multiple users. Causes damage to the physical components of information technology equipment such as computers and storage devices.
These channels are monitored by the Information Security Team, who also conduct investigations into any reported incidents to determine whether or not a security breach or exposure has occurred.
Confirmed violation
Although Amco has not yet achieved ISO 27001 certification, the organization is already experiencing positive effects. ISO 27001 accreditation is the international benchmark for effective information asset management and can help businesses avoid devastating revenue losses due to data breaches. Therefore, if an ISMS certified to ISO 27001 is adopted, then the company continues to be secure and it also shows that the company has taken significant security, which is a good signal as it helps in recruiting customers.
The purpose of ISO 27001 certification is to ensure that organizations meet business, legal, contractual and regulatory requirements by choosing appropriate security measures that are proportionate to the level of risk associated with protecting information. The company's current size is the result of implementing ISMS throughout the organization and pursuing ISO 27001 certification. The audit required to obtain the ISO 27001 accreditation has not yet been carried out on Amco Enterprise Limited.
Maintenance of logs: Amco maintains logs and tracking of organization-owned devices, but this was not considered significant until recently when the organization became aware of the ISO 27001 certification requirements.
Findings of the Study
Advantages of Embracing ISMS Awareness
It is possible to quantitatively predict and monitor anticipated losses that could arise due to potential risks to the operation of the existing information system. It is possible to improve the organization's resources in terms of their consistency, productivity, efficiency and reliability. Despite the obvious advantages that have been mentioned above, it is possible that the companies that receive the certificate will not be immediately visible.
31 management system can be dangerous and it can be difficult to monitor and manage both tangible and intangible measures that can be further obtained. Amco security has improved significantly, making data stored within the organization and on its server much more secure. Although maintenance costs have increased, risks have been reduced and the organization now has adequate legal remedies and measures in place for potential incidents such as data breaches.
This growth can be attributed not only to strong customer performance, but also to the recent uptake of ISMS awareness.
Advantages of Obtaining an ISO 27001 Certification
32 company's successful journey, and once Amco has achieved ISO 27001 certification, it is on track to become a major player in the outsourcing market in Bangladesh and beyond. Adjustment of structure and focus: This standard enables companies to be more productive, as it clearly outlines the duties for managing the risks associated with information security. However, Amco must prioritize this issue to ensure the privacy of its customers' data and speed up the process by which it will be awarded ISO 27001.
If this does not change, the efforts of the past months would have been in vain, both in terms of achieving ISO 27001 certification and developing an efficient ISMS. Retrieved from University of Pittsburgh, Information Technology: https://www.technology.pitt.edu/help-desk/how-to-documents/guide-identifying-personally-identifiable-information-pii". Retrieved from https:// www.smartlockr.io: https://www.smartlockr.io/en/blog/cost-of-a-data-breach.
Are there any specific policies or procedures in place in your organization to ensure the security of different categories of data.
Recommendation & Conclusion
Appendix
Questionnaires
Progress Report