Her guidance helped us find the solutions of research work and arrive at our final theory. We would like to express my sincere gratitude and appreciation to all our faculty members of the Software Engineering Department for their kind help, generous advice and support during the studies. We dedicate this dissertation to our family because of their love; affection and the devotion towards us support us for the success of our life.
We also dedicate this thesis to our teachers and especially to our mentor, because without their guidance, inspiration and dedication it would not have been possible. The conclusion of this paper is a look at how blockchain can solve the problems with the current e-voting system.
Introduction
- Problem Outline
- Motivation
- What are we studying
- Why are we interested in it
- Why should this be interesting to others
- Research Question (RQ)
- Research Design
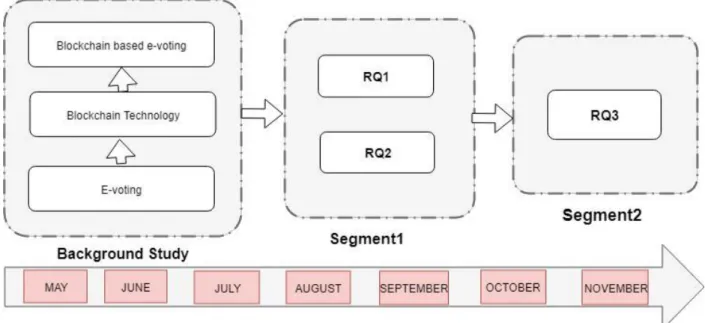
Obvious advantages of e-voting using blockchain include i) greater transparency due to open and distributed ledgers, ii) inherent anonymity, iii) security and authenticity and iv) Immutability [1]. Since blockchain is a decentralized, distributed and immutable database, we thought we could find a solution to a security issue by using blockchain technology as the basis of the e-voting system. Background study was used as input of segment 1 and segment 1 was used to answer RQ1 and RQ2.
Literature Review
- Research Method
- Search strategy
- Search string
- Search scope
- Search period
- Search method
- Inclusion/exclusion criteria
- Classification Schema
- Descriptive analysis
- Search scope results
- Time period results
- Publication type results
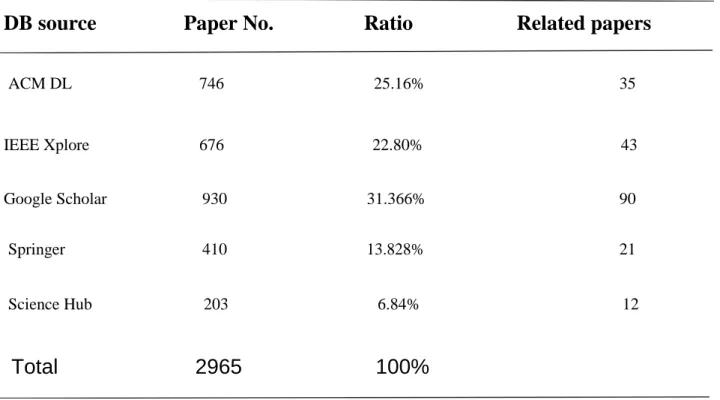
The search string must be narrowly defined to have broad coverage of the prior art. We use logical OR to connect main terms and their synonyms. The final search string is: (“Block Chain” OR “block-. We included Science Hub (https://scihub.org/), Google Scholar (https://scholar.google.com/) database to find more effective studies , which do not appear in the standard search process, regardless of how the search results will generally repeat with the search results of the selected databases.
All selected studies must include all inclusion criteria and not meet all exclusion criteria. Despite the inclusion/exclusion criteria, we still found articles that did not answer the research questions. We think we can identify the current knowledge of the e-voting system with blockchain; the final number of selected studies is sufficient.
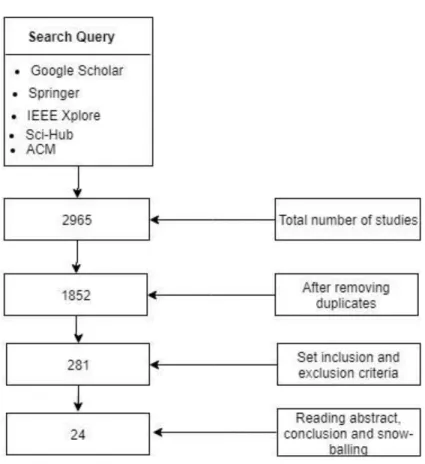
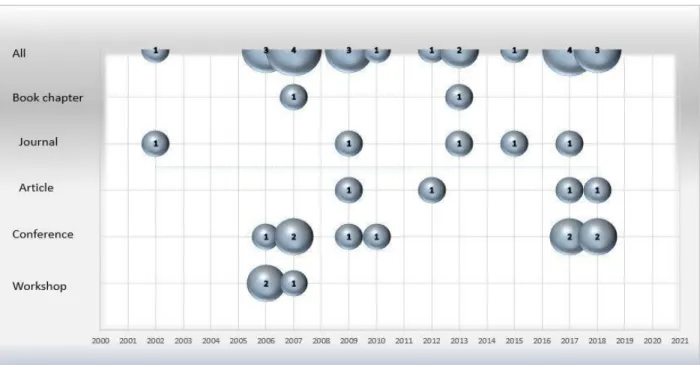
Finally, we acquired 328 selected articles after manually exploring the text based on title, abstract and keywords, to discard articles that were not related to any of the research questions, and after the snowball, we ended up with 24 relevant articles, which represent 1.412% of the original 2965. As a result of the superficial reading, a set of facets can be determined into which the papers can be classified. First, we get an overview of the results from different features of the mapping study.
As a result of the initial search process, Table 3 shows a total of 2965 articles, the number of articles per electronic database and this represents the percentage.
Background Study
- Electronic voting
- Working Method
- Analogy of e-voting system
- Why blockchain in e voting
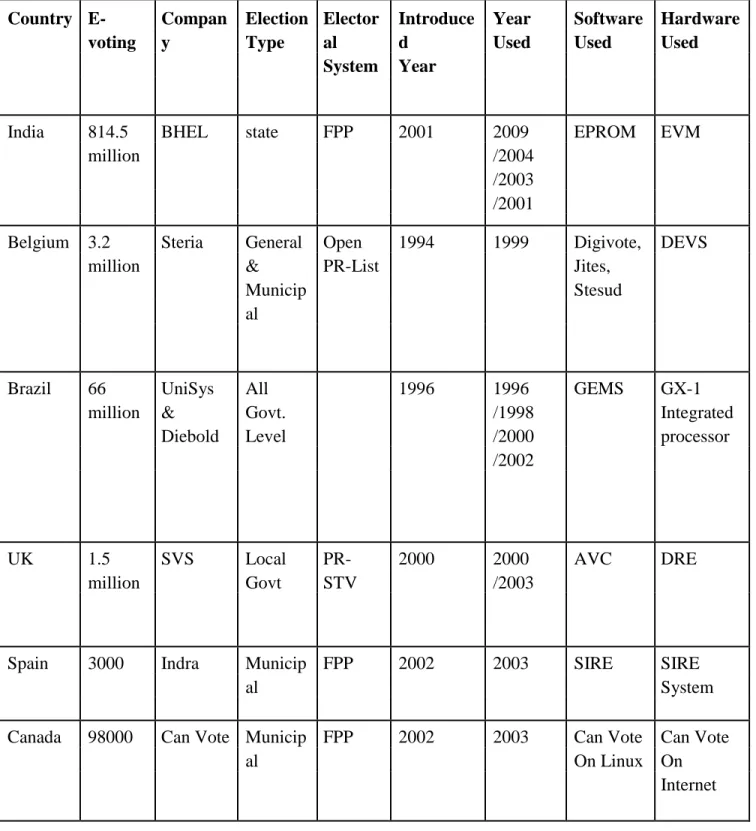
Electronic voting in favor of voters has been used since the 1960s [21], when punch card systems appeared. Estonia was the first in the world to provide electronic voting for its national elections [22]. It was not long before Switzerland was able to vote electronically for its state-wide elections [23] and by Norway for its municipal elections [24].
From Australia to India, Norway to Venezuela, more than 20 countries in the world have been involved with electronic voting systems over the past 20 years with changing reception or discharge rates [25]. The vulnerabilities behind these attacks emerge from key properties of the Internet architecture and actual individual computers. Often the character of the voter is not checked, the voting material may not be anchored and the principles for secret ballot may have been loose even in the polling stations.
Each of these nodes has their own copy of the distributed ledger that contains the full history of all transactions the system has processed. Each block has permanently recorded transaction data that is added to the blockchain [35]. Anyone who might try to decrypt the data by looking at the hash would not have the ability to work out the length of the encrypted data.
A key analysis of blockchain innovation recommends that it is a suitable foundation for electronic voting and could also potentially make electronic voting more valuable and solid [1].
Gap analysis
Drawback of Electronic voting machine
- Substituting Look-Alike CPUs
- Messing with Software before CPU Manufacture
- Substituting Look-Alike Circuit Boards
- Substituting Look-Alike Units
- Messing with Machine State
Attackers may think it is faster to develop an electrically compatible, rogue motherboard and replace it with the original. An attacker can steal votes by replacing the circuit board in the voting unit with a circuit board that responds falsely to keystrokes, or by replacing the display board in the control unit with a circuit board that reports inaccurate vote totals. The associations between these components are also trusted, so an attacker could try to embed a device between the voting unit and the control unit with the end goal of capturing the keystroke flags and replacing them with votes in favor of different candidates [20].
Voters and poll workers have no down-to-earth approach to verifying that the EVMs they use are valid, so attackers can attempt to construct identical yet rogue control devices or ballots and replace them before an election. Since the devices we analyzed have no convincing method to check the authenticity of the devices they are matched to, displacing one of the devices with a deceptive one would allow the attacker to change decision results [20 ]. Regardless of whether each segment of the framework acts correctly, attackers could in any case endeavor to control the framework by specifically accessing or controlling the internal state of the machine in ways not contemplated by its designers [20].
Manifestation Attack
- Deceptive display assault
- Clip-on Memory Manipulator Attack
The deceptive display includes a different, hidden microcontroller that blocks voice aggregates and replaces false results. To achieve this, the blank screen reads electrical signals from the control unit, which would periodically control the 7-segment LED numbers. This allows him to recognize when the control unit is trying to display the results of a decision.
It also translates the return "add to cast a vote" to determine the actual overall number of votes so that it can effectively include the non-conscientious votes. When the unscrupulous display is introduced into an EVM (perhaps months or years before the decision), the attacker must indicate which candidate will be favored, and by what margin. There are a wide variety of ways in which aggressors can send such a signal - with different types of radios, by using secret combinations of keystrokes, or even by using the number of candidates on the ballot [20].
The rotary switch selects a number from 0 to 9, and the attacker can use it to select a favored candidate in any of the first nine e-voting positions, which usually include the real national parties. When the change is set to position 1-9, the lock on the gadget performs a voting system [20]. An aggressor could also use our lock on the gadget to abuse the mysterious voice.
The device can be associated with a computer phone a sequential link, and, when the rotary switch is set to position 0, it expects instructions to read or write the EEPROM [20].
Similar models
Proposed Model
Model Structure
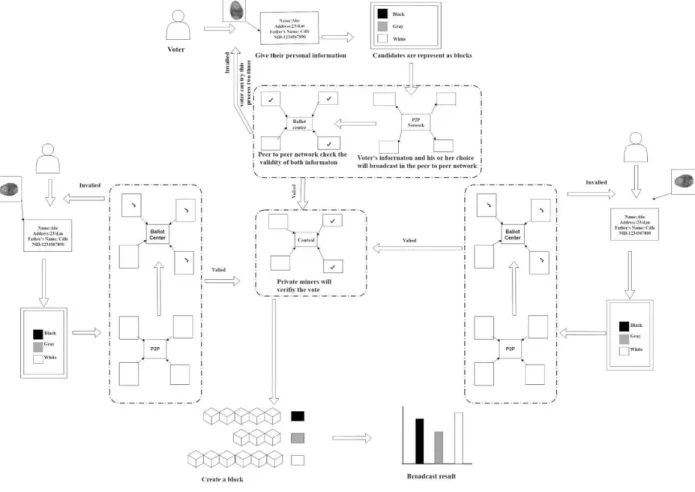
The voter's information and choice are then broadcast on the peer-to-peer network. If the information is invalid, the process returns to the beginning. The voter can attempt the process twice, after which the voter is considered a fraudster. The private miner assigned in the central network will verify the vote. They generate a voting transaction and create a block in the blockchain. After the voting process, the result is broadcast based on the candidate blockchain.
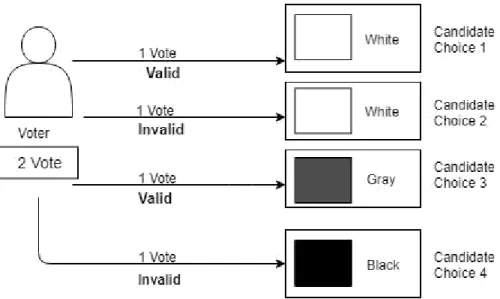
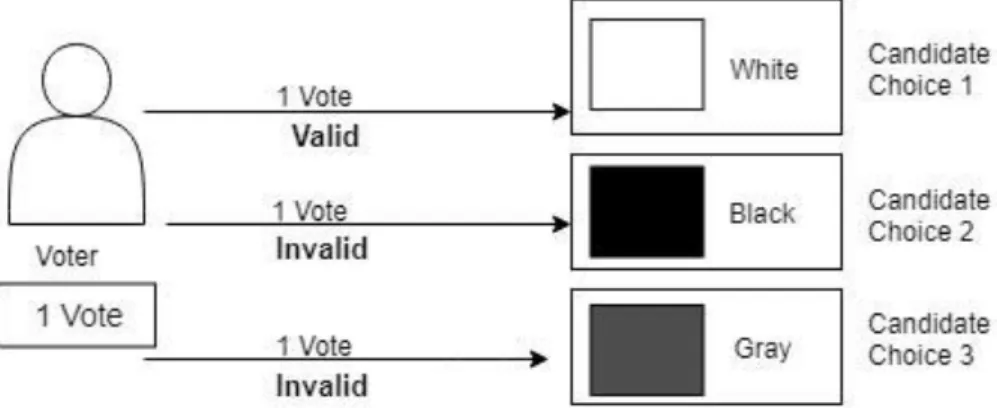
At first, the number of votes a voter can cast will be declared depending on the type of election. Each voter can cast one or more votes, depending on the type of election. If the voter has one vote to cast, he/she can only cast one vote for each candidate.
In this case, only one voting transaction will be valid and the others will be invalid. Where voters have the right to vote multiple times, the selection of candidates will be divided into lots. A voter could cast multiple votes, but not in the same column or for the same candidate.
Model Process
- Registration
- Voter registration
- Candidate Registration
- Request for Vote
- Peer to peer network
- Create a block
- Counting vote
When a person requests to be registered as a candidate, he/she must provide his/her personal information (NID number, name, age, address, party name, symbol). If the government accepts her/his request, the government miner will create a genesis block. On voting day, when voters arrive at the polling station, they submit their fingerprints in the fingerprint scanner. Then he or she has to submit their personal information such as NID and their choice from candidates to a peer-to-peer network.
In this peer-to-peer network, once the miners get the voter information and the candidate information of their choice, they will check whether the voter and candidate information is valid or not. If all information is valid, send all information to private miners and if any information is invalid, it will go back to the beginning. A voter can attempt this a maximum of three times, after which the voter will be blocked as a fraud.
When the private miners get all valid information from the voter and candidate, then process the vote for the count. After a block is created and depending on the candidate selected, the information is recorded in the corresponding Blockchain. After the voting process ends, the government authority will broadcast vote result based on candidate blockchain.
In this counting process, using the public ledger, it shows how many votes all candidates get and who wins the election.

Contribution
Due to the allocation of more miners and their distribution to voting centers and the central office, the voting time will be reduced. Time = (Current Time × Sample Block × Expected Block)/ Expected Miner However, as the number of expected miners increases, the voting processing time will decrease, but the cost will also increase. Electronic voting is a platform that provides a safe and reliable environment for voting over the Internet.
We proposed an e-voting system using blockchain that eliminates voter and candidate fraud, providing a transparent record of the votes cast and preventing the fraudulent election.