While various analysts have explored such security issues and open questions in IoT, there is a lamentable lack of orderly investigation of security challenges in the IoT arena. In this report, we aim to bridge this gap by guiding a careful investigation of IoT security problems and issues.
List of Tables
Introduction
- General Introduction
- Motivation
- Related work
- Goal of this research work
- Outline Methodology
- Organization of the thesis
We selected the above systems based on the obtained criteria: (I) notoriety of the carriers within the product program and gadget ventures, (ii) help to expediently improve usability and quantity of trade uses, (iii) inclusion and use of structure, and is notorious in the IoT commercial center . Creators on the problems and proposed approach to overcome security issues of IoT middleware, where countless frameworks derive security properties from middleware frameworks.
Internet of things (IOT)
- Introduction
- Background History
- Characteristics of IoT
- Basic elements of IoT architecture
- Application of IoT
- IoT Framework
- AWS IoT
- ARM mbed IoT
It talks to the rest of the state of the device while it has converted into. It is indeed very suitable for the mbed operating system and can be accessed through the mbed copper library.
Application mbed Cloud
The mbed gadget connector is a web benefit that allows designers to add IoT gadgets to the cloud without having to deal with the framework [59]. In addition, the mbed device Connector provides confidence and assurance over the use of TLS/DTLS and offers a vast scope of far-reaching conventions, including CoAP/HTTP, TLS/TCP, DTLS/UDP and OMA lightweight M2M. Currently, ARM reports on mbed Cloud [60] and adds it to the IoT environment.
The commitment to provide all the security guarantees in the expressions of cryptography modules, depending on zones, key control, etc., being a SaaS, the mbed Cloud can be sent and.
In addition, it really works with rest APIs, making it easy to consolidate and travel to the various business benefits.
Hardware (ARM MCUs)
- Hardware specifications
- Security features
- Azure IoT suite
- Architecture
- Hardware specification
- Security features
- Brillo/Weave
- Architecture
In activity, mbed Device Connector is a simplified case of mbed Cloud administrations. Fruitful IP devices can talk to Azure IoT Hub immediately with the guide to force one of the supported correspondence conventions [67]. Memory footprint: memory footprint is largely SDK dependent and the convention used, regardless of the stage target (eg base ..prerequisite RAM used by the C SDK is 64KB).
The ID Vault in Azure IoT Hub provides a nice collection of tool identities and security keys.
Weave Local API Weave Cloud API
The Android HAL (Equipment Abstraction Layer) is a middleware, which bridges the gap between the equipment and the product program. It lets in Android bundles to talk to equipment explicit device managers by handling gadget calls between the portion and the best Android-based thoroughly layers.
Android HAL
Hardwar specification
Security features
Calvin
- Architecture
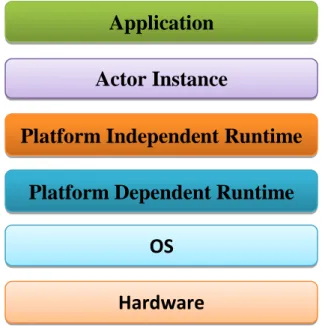
The base layer talks to the real device or device, while the second one types the working device that the device discovered. In other words, this layer supports different transport layer conventions (WiFi, BT, and i2c) and provides scene-specific key points like sensors and actuators in a uniform form to the scene-aware runtime layer. where he lives above the stage. dependent execution layer. The runtime can be arranged to grant access to different resources depending on whether a character on the screen is part of the application.
Application Actor Instance
Platform Independent Runtime Platform Dependent Runtime
OS Hardware
Security features
Approval can be attempted through a technique for differentiating the hash estimate of the input and output pieces of knowledge. Device and portals are integrated into the versatile network to access the cloud. End customers speak to the cloud and investigate the various current events of the extraordinary IoT device they have approved.
IoT devices cannot connect to the cloud via M2M inputs without going through the verification and approval forms.
Network
The approval procedure must be performed after a fruitful confirmation, as it makes use of the returned qualities as information. To the joy of our expertise, neither sandboxing nor virtualization technique is equipped in Calvin structure, as Er-Ericsson does not maintain their own cloud framework.
Cloud
HomeKit
- Architecture
Until the design display, iOS, watch OS and tvOS are the best working structures that support HomeKit capabilities. Regardless, not all private connected IoT devices can join the HomeKit organization except for a minute reprieve. HomeKit Bridges are entries that act as an intermediary between iOS applications and home robotics that do not deal with the HomeKit tradition.
The HomeKit API layer is responsible for providing interfaces to third-party developers to streamline the improvement of sharp applications and hide the versatile nature of the base layers.
For add-ons implementing HAP, no extension is required and IP (LAN, Wi-Fi) or BLE is used as the transport agreement. JSON mapping is used in HAP to exchange messages between iOS apps and HomeKit-enabled gadgets. It is far in charge of providing a consistent user interface to all Apple gadgets that share a similar record by synchronizing saved data in a shared database using iCloud [90].
Bridge MiFi cetified
BLE IP
HomeKit Accessories
Other Accessories
Hardware and specification
Subsequently, HomeKit empowers all external equipment devices that utilize Apple's MFi-authorized innovation [91] to electronically interface with the iPhone, iPad, iPod, or Apple Watch. As expressed before, to link a highlight that is generally not MFi guaranteed to the HomeKit structure, a HomeKit connection must be used to locate a typical dialect between the heterogeneous transportation conventions. The scaffold only supports ZigBee and Z-Wave conventions from the info page of the dikeddar.
Be that as it may, for HomeKit there are no basic requirements for memory size, as it mainly depends on the explicit expectation of the MCU and the elements of the stacked code.
Security Feature
Secure communications: The combination of the central pieces of iOS security design (e.g., pleasant boot, etc.) ensures that only trusted code can continue to run on Apple devices. The AES 256 encryption tradition is brought forward through an engine integrated into the DMA course between the burst accumulation and the main device memory in each device, ensuring that encryption is extremely profitable. So despite the way the correspondence goes through very attractive devices or organizations, the keys cannot be decrypted even by Apple techniques.
This decision invigorates the correspondence methodology in the event that in destiny the device is compromised and the sure period key is unhesitatingly observed, the enemy cannot decipher the correspondence.
Kura
- Architecture
- Hardware specifications
Application
Remote
Admin GUI
Delivery Network
Services
Field Protocol
Device Abstraction OSGi application container
Java SE & embedded Linux Kernel
Hardware
Security features
Ensuring that it is not tainted or confused with a report by a harmful buyer is accomplished by conducting a regular ecological compliance check by means of the welfare supervisory part. This makes it more difficult for programmers to reach the administration to recover the capture password from the device. Secure communication: SSL Manager oversees SSL authentication, accepts both private and public keys and valid stores.
The cryptographic APIs are used to encode and decipher privileged insights and methods and methodologies and to retrieve the catchphrase.
SmartThings
- Architecture
Smart apps can also continue to run in the center and in addition in the cloud depending on the physical qualities of the smart device. This decision we tend to have those gadgets cross the entryway and be part of the Smart Things cloud. Every sensory apparatus has a place with at least one or a large part of the following.
Center-related gadgets include all devices that have the common sense to combine with the Smart Things center the work of ZigBee or Z-Wave home mechanization conventions, while being LAN related.
Smarthings Cloud Backend
SmarthDevice
Smarthing Hub
Smarthings Buddy App
Wave ZigBee
Every neighborhood |LAN| PC system and cloud-related devices are willing to talk and mix through net administrations such as winding down or improvement cleaner [104]. There are two techniques for correspondence between smart apps and brilliant gadgets; (I) strategy brings in that savvy apps can perform and perform activities across avid devices and (ii) event membership where smart apps can buy into method-created events for various smart apps or brilliant devices. The availability control layer is at risk of establishing a constant and secure association between the associated devices, e.g.
The instrument type handler layer improves adaptability by holding an event or virtual photograph for each kind of smart gadget.
SmarthThings Cloud Backend Web UI and Core APIs
SmaartApp Management and Execution Subscription Processing
Device Type Haandlers Connectivity Management
Hardware specification
Security features
The most important detail required is the ability to convey using one of the perfect conventions. A capability is a basic idea inside the basic design that has a place with a legitimate layer that provides a reflection of the Smart-Device's capability. Directions are strategies or abilities to play out a few features of the clever instrument, while properties come into parameters that speak to the condition of the gadget.
When all is said and done, agreements between all building blocks of the SmartThings environment are concluded over partner SSL (Secure Sockets Layer)/TLS (Transport Layer Security convention).
Attack or threat 4.1. DoS attack
- Jamming Attack
- Blue borne attack
- Remote access using telnet
- Sybil attack
- Exploit kit
- Man in the middle attack
- Replay attack
- Ransomware
- Side channel attack
Attack Method: A jamming attack is a type of denial-of-service attack that prevents typical nodes from using a forwarding channel by jamming the channel they are transmitting on. The term telnet is similarly used to refer to product software that performs part of the conference for the user. It is important to note that the use of Endeavor units is not limited to harmful sites.
Attack Method: Cloud computing has recently been taken into account as one of the most dominant paradigms in the information and technology IT industry.
Result and comparative analysis 5.1. Aws framework
- ARM mbed
- Azure IoT suite
- Brillo/weave
- Ericsson/Calvin
- Apple homekit
- Smartthing/Samsung
- Kuru/Java
- Conclusion
The HTTPS server uses the ARM software component mbed TLS to allow secure communication. For context, a major attack last year had a power of about one terabit per second (1 Tb/sec). The entire Internet has a shared bandwidth of 200 Tb/sec. Now when we compare this to a single Google data center which has a dedicated bandwidth of 1300 Tb/sec. The cellular jamming attack is a denial of service attack that wastes power. The mobile jamming protection method operates the multi-topology scheme to reduce the mobile jamming attack so that the affected area is also reduced.
A comparative analysis of the frameworks was performed based on architecture, hardware compatibility, software requirements and security.
32] https://www.linkedin.com/pulse/thesis-ideas-internet-things-advantages-applications-manpreet-kaur/?fbclid=IwAR3DTh778bpW0xCZVHZRgcyi3gF8gPZ-. 35] https://www.linkedin.com/pulse/thesis-ideas-internet-things-advantages-applications-manpreet-kaur/?fbclid=IwAR3DTh778bpW0xCZVHZRgcyi3gF8gPZ-. 113] https://www.infoworld.com/article/2625148/intrusion-detection/hackers-using-telnet-to-athack-corporate-servers.html.
117] https://www.quora.com/How-does-the-Sybil-attack-work-How-does-it-initiate-the-attack.