A NEW MALWARE ATTACK PATTERN
GENERALIZATION
Robiah Y., Siti Rahayu S., Shahrin Sahib, Mohd Zaki M., Faizal M. A., Marliza R. Faculty of Information and Communication Technology
Univeristi Teknikal Malaysia Melaka, Durian Tunggal, Melaka,
Abstract— The significant threats of malware are still continuing due to their rapid distribution nature on the internet. The malware attack pattern from nine different attack scenarios have been extracted from various logs at different OSI layers such as victim logs, attacker logs and IDS alert log. These malware attack pattern are further analyzed to form the general malware attack pattern which describes the process of malware infection. This paper proposes a general attack pattern for malware in three different perspectives which is attacker, victim and victim/attacker or multi-step attack using only traditional worm variant. Hence, the general malware attack pattern can be extended into research areas in alert correlation and computer forensic investigation.
Index Terms — malware attack pattern, log, malware attack
I. INTRODUCTION
It is essential to identify the dynamic propagation of the current malware infection so as to protect us against the attack of the future malware. Their fast spreading character in exploiting the vulnerability of the operating system has threatened the services offered on the internet. Thus, there is a need to find a solution to detect and predict the propagation of the malware.
This paper propose the general malware attack pattern for detecting and predicting the malware by examining the various OSI layer’s log from the malware source and the other machine that are infected with it and investigate the evidence leave by the attacker which is considered as the attack pattern. For the purpose of this paper, the researchers have select nine scenarios: scenario A to scenario I; and used Blaster, Sasser and Lovesan.T variants during the experiment. This attack pattern is based on the fingerprint of these three variants’ attack on victim’s logs, attacker’s logs and Intrusion Detection System (IDS) alert’s log.
II. RELATED WORK
A. What is Malware?
Malware is a program that has malicious intention as mentioned by [1]. Nevertheless [2] has defined it as a generic term that encompasses viruses, Trojans, spywares and other intrusive codes. The malware implies malice of forethought by malware inventor and its intention is to destroy a system. Moreover, malware even if it has destructive consequences, is not a defect in a legitimate software program.
According to [3], generally malware is consists of three types of malware of the same level as depicted in Fig. 1 which are virus, worm and Trojan horse.
Fig. 1. General Malware Taxonomy by Karresand
For the purpose of this paper, the researchers have scope the malware to traditional worms. This is due to the fact that these types of worm are still persistent in internet as claimed by [4] and [5]; and hence they are selected for further research. According to [6], worm taxonomy can be further categorized into four types of worms which are traditional worm, e-mail worms, windows file sharing worm and hybrid worm. The most well-known traditional worms such as Blaster, Sasser, Code Red and Slammer, are the main threats to the security of the internet. Thus, the researchers have selected Blaster, Sasser and Lovesan.T variants for the experiment.
The Blaster worm launch on August, 11th 2003 infected at least 100,000 Microsoft Windows systems and cost millions in damage. In spite of cleanup efforts, an anti-worm, and a removal tool from Microsoft, the worm persists [6]. Meanwhile, Sasser was first noticed to spread on April 30th, 2004 and then Lovesan.T is another name for Blaster with variant T has been found on 21st April 2004 and has similar scanning characteristics with Sasser but different malware code. Most of these computer worms affect computers running vulnerable versions of Windows XP and Windows 2000 and have the potential to generate the multi-step attack which can increase the recovery cost of the infected system and would initiate serious cyber crimes.
Blaster worms spreads by exploiting DCOM RPC vulnerability in Microsoft Windows as described in Microsoft Security Bulletin MS03-026. The worms scan
port 135 on random subnets in sequential or random order, and the target are the discovered systems. The exploit code opens a backdoor on TCP port 4444 and instructing them to download and execute the file MSBLAST.EXE from a remote system via Trivial File Transfer Protocol (TFTP) on UDP
port 69 to the %WinDir%\system32 directory of the infected system and execute it as stated by [7]. The goal of the Blaster attacker is to make the system unstable by terminating the RPC services and causes the system to reboot. Meanwhile, Sasser spreads it code by exploiting a buffer overflows in the component known as LSASS (Local Security Authority Subsystem Service) on the affected operating systems. This malware scans different ranges of IP addresses and connects to victim’s computers primarily through TCP port 445 and it may also spread through port
An attack pattern is a method to cause an exploit against software used by attackers as stated by [8]. It is a systematic explanation of the attack goals and attack strategies for defending against attack. Moreover [9] has described that an attack pattern as the steps in a generic attack, while [10] has clarify the term attack pattern as the attack steps, attack goal, pre-conditions and post-conditions of an attack. Thus, an attack pattern is recognized as one of the important element to protect from any potential attack. Subsequently, [11] and [12] have discussed on issues related to how the attack is performed, the attack goals, how to defences against the attack and how to trace once it has occurred. Nevertheless, based on the research, the victim’s perspective is not considered as the focus is on the attacker’s perspective only. Thus, in this research, the researchers has proposed the attack patterns that focus on the attacker’s, victim’s and attacker/victim’s (multi-step) perspectives to present a logical perception on how the attack is accomplished and the effect caused by the attack.
III. ATTACK SCENARIO
In this experiment, nine attack scenarios: scenario A to scenario I are designed using the framework which consists of four phases: Network Environment Setup, Attack Activation, Log Collection and Log Analysis as described in [13]. The attack scenario A, B, C for Blaster attack can be referred to [14] and scenario D, E, F for Sasser attack can be referred to [15]. Each attack scenario is attained through thorough log analysis.
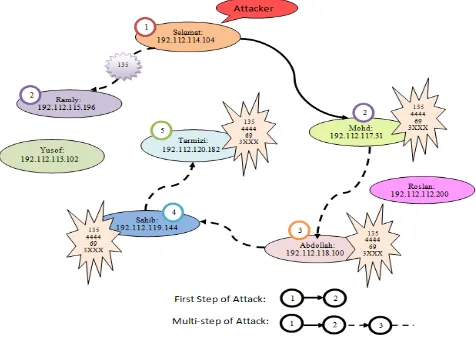
Fig. 2 Lovesan.T attack in scenario G which consists of first step and multi-step of attack
The diverse logs involve in this analysis are divided into two categories which are host logs and network logs. The host logs categories: personal firewall log, security log, system log, application log and network logs categories: alert log by IDS. The sample of scenario G for Lovesan.T attack is as shown in Fig. 2 where the analysis of scenario G shows that the Lovesan.T attack is activated in Selamat and this host has successfully exploited hosts Mohd, but partially has exploited Ramly. Subsequently, hosts Mohd which has been previously exploited by Selamat has organized an attack on host Abdollah and this attack is called multi-step attack. Later on, Abdollah attacks Sahib and then Sahib attacks
Tarmizi.
In this attack scenario, the hosts that are marked with
135, 4444, 69 and 3xxx shows that it has been successfully exploited by the attacker and this host has been infected. In this case, port 3xxx is port 3033 and it is the communication port use between Selamat and Mohd. Port 3xxx is generated randomly by this variant as it can be any number from 3000 to 3999. Hence, similar to Sasser.B’s attack, the researcher has decided to call this port as 3xxx. Meanwhile, those marks with port 135 shows the attacker is trying to communicate with the victims by scanning the victim’s IP address.
IV. ANALYSISANDFINDINGS
The nine attack scenarios are further analysed and the example of the detail analysis can be referred to [13] and [14] and the findings from this analysis are used as the primary guideline in developing the general malware attack pattern. These attack patterns are constructed in three different perspectives: attacker, victim and victim/attacker or multi-step attack. The details of these perspectives are elaborated in the following sub-sections.
A. Analysis of General Malware Attack Pattern in Attacker Perspective
In the attacker perspective, there is significant attack pattern found in the analysis of this general malware’s attacker pattern and its summary is shown in TABLE I.
TABLE I
Summary on general malware’s attacker pattern (attributes found=√, attributes not found=nil)
General General
With reference to TABLE I, the data detected in attacker’spersonal firewall log for all malware’s scenario have similar log attributes which are action, protocol and destination port. Therefore, the generalized log attributes for scan and exploits attack steps are action, protocol and destination port.
necessarily generated once it is being infected by the malware, unless the device is restarted. Hence, the generalized log attributes for both logs are event id and event message. In the IDS alert log, the data detected in all malware’s scenario are similar, thus the generalized log attributes are error message and source IP address.
B.
Analysis of Malware Attack Pattern in Victim PerspectiveIn victim perspective, there is significant attack pattern found in the analysis of this general malware’s victim pattern and the summary of the victim pattern is shown in TABLE II and the details are discussed.
TABLE II
Summary on general malware’s victim pattern (attributes found=√, attributes not found=nil)
General General
With reference to TABLE II, all of the logs involved:
personal firewall log, security log, system log, application log and IDS alert log have the similar log attributes detected as in the general malware’s attacker pattern. Therefore, the log attributes selected for this general victim pattern are
action, protocol, destination port, event id, image filename, event message, error message, source IP address, and destination IP address.
C. Analysis Of Malware Attack Pattern in Multi-Step (Victim/Attacker) Perspective
The multi-step attacker’s data have been detected in all malware’s scenario. The summary of the general multi-step attacker pattern is represented in TABLE III and the details of the multi-step attacker’s logs are discussed.
TABLE III
Summary on general malware’s multi-step attacker (victim/attacker) pattern
(attributes found=√, attributes not found=nil)
General General
All of the logs involved: personal firewall log, security log, system log, application log and IDS alert log in TABLE III have the similar log attributes detected as in the general malware’s victim pattern except for attributes found in the IDS alert log. In the IDS alert log, the attributes for the victim attack pattern are destination IP address and
destination port whereas the attribute for multi-step attacker pattern is source IP address only. Therefore, log attributes selected for this general multi-step attacker pattern are
action, protocol, destination port, event id, image filename, event message, error message, source IP address, and destination IP address.
In this analysis, the researcher has identified the attributes involved in the victim, attacker and multi-step attacker pattern. These findings are further used to construct the proposed general malware’s attacker pattern.
V. PROPOSED GENERAL MALWARE
ATTACK PATTERN
The general attack pattern for malware is designed based on the finding from the attack pattern analysis done on Blaster.A, Sasser.B and Lovesan.T. In constructing the general malware’s attack pattern, the researcher has decided to segregate the logs into two categories which are called
primary log and secondary log. In primary log, all of the information gathered from this log is pre-requisite. From this log, the researcher can determine the perspective of the attacker without gathering the information from the
For the secondary log, most of the log gathered from
security log, system log, application log and IDS alert log
are not necessarily the main factor to determine the perspective of the attacker. This secondary log is considered as supportive information to the researcher [16] and not necessarily true in case of alert gathered from IDS alert log. Sometime the alert from IDS can turn into false positive or false negative alarm. In case of security log,system log and
application log; all of these logs are not necessarily generated once it is being infected by malware; unless the device is restarted, then only the log is generated. Hence, this secondary log is more or less unreliable in certain situation, but act as supportive information in determining the attacker’s perspective. The following section describes the details on the primary and secondary log involved in the attacker, victim and multi-step attacker pattern.
This research proposed the general malware attack pattern based on victim, attacker and multi-step point of view. The following section describes the details.
A. General Attacker Pattern
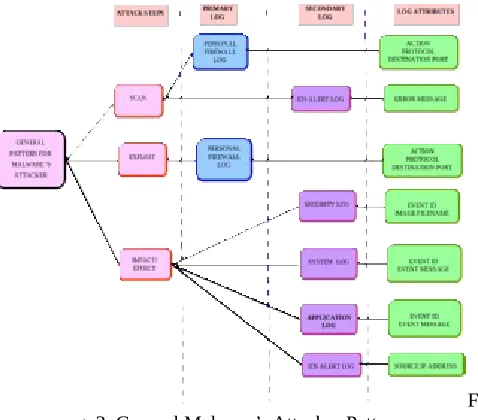
Based on the finding from general Blaster.A, Sasser.B and Lovesan.T malware’s attacker analysis, the overall malware’s attacker pattern is generalized in Fig. 3.
Fi g. 3 General Malware’s Attacker Pattern
In primary log, the scanning and exploiting activity can only be found in personal firewall log. These logs have the general attributes of action, protocol and destination port. Meanwhile, in secondary log, on host level, the impact can be found in security log, system log and application log. These logs have the general attributes of event id, image filename and event message. Consequently, on network level, both scanning activity and its impact/effect can be found in IDS alert log and the general attributes are error message and source IP address correspondingly.
B. General Victim Pattern
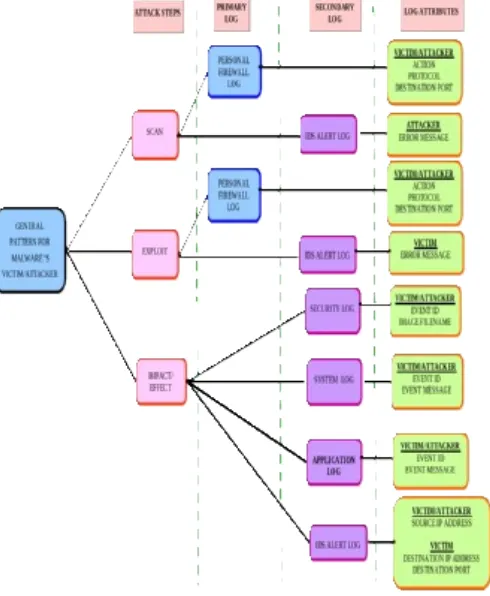
In general malware’s pattern for victim as depicted in Fig. 4; the finding is based on the discussion in analysis of general malware’s victim perspective.
Fig. 4 General Malware’s Victim Pattern
With reference to Fig. 4, the log files and attributes for the scan, exploit and impact/effect attack steps are similarly found in general malware’s pattern for the attacker in Fig. 3. The only main difference is on the network level where the alarm’s general attribute found in IDS alert log are source IP address, destination IP address and destination port. Moreover, this alarm is found during exploiting and impact/effect activities compared to scanning and exploiting activities found in general malware’s attack pattern.
C. General Multi-step (Victim/Attacker/) Pattern
Fig. 5 General Malware’s Multi-Step Attacker Pattern
The considered attributes are only destination IP address and
destination port for victim; and error message and source IP address for multi-step attacker (victim/attacker) pattern. The general malware’s victim and attacker pattern are used for developing a basic malware’s attack model, while the general multi-step attacker pattern is used to develop multi-step malware’s attack model which will be further discussed in next section.
VI. CONCLUSIONSANDFUTUREWORKS
In this paper, the researchers have analyzed diverse logs in order to identify the attack pattern from attacker and victim perspective in nine different attack scenario: scenario A to scenario I. The output of the analysis are the proposed general malware attacker attack pattern, general malware victim attack pattern and general malware multi-step attack pattern. This general malware attack pattern is then extended to be further used in designing malware attack model. The finding is essential for further research in alert correlation and computer forensic investigation.
ACKNOWLEDGEMENT
We thank to Universiti Teknikal Malaysia Melaka for the Short Grant funding (PJP/2009/FTMK (8D)S557) for this research project.
REFERENCES
[1] Mihai Christodorescu , Somesh Jha , Sanjit A. Seshia , Dawn Song , Randal E. Bryant, “Semantics-Aware Malware Detection”, Proceedings of the 2005 IEEE Symposium on Security and Privacy, p.32-46, May 08-11, 2005
[2] Vasudevan, A., & Yerraballi, R., “SPiKE: Engineering Malware Analysis Tools using Unobtrusive Binary-Instrumentation”. Australasian Computer Science Conference (ACSC 2006),2006 [3] Karresand, M., “A proposed taxonomy of software weapons” (No.
FOI-R-0840-SE): FOI-Swedish Defence Research Agency, 2003. [4] IBM. (2011). IBM X-Force® 2010-Trend and Risk Report. Technical
Report for IBM.
[5] Bailey, M., Cooke, E., Jahanian, F., Watson, D., & Nazario, J. (2005). The Blaster Worm: Then and Now. IEEE Computer Society. [6] Lazarevic, A., Kumar, V. & Srivastava, J. (2005). Managing Cyber
Threats. On Massive Computing: Springer US. pp. 19-78.
[7] McAfee. (2003). Virus Profile: W32/Lovsan.worm.a [Electronic Version]. Retrieved 23 July 2009 from
http://home.mcafee.com/VirusInfo/VirusProfile.aspx?key=100547.
[8] Barnum, S., & Sethi, A. (2006). Introduction to Attack Patterns. [Electronic Version]. Retrieved 18 April 2010.
[9] Hoglund, G., & McGraw, G. (2004). Exploiting Software: How to Break Code. Boston, Massachussetts: Addison-Wesley/Pearson. [10] P. Moore, A., J. Ellison, R., & C. Linger, R. (2001). Attack Modeling
for Information Security and Survivability. (No. CMU/SEI-2001-TN-001.): Pittsburgh, Pennsylvania: Software Engineering Institute, Carnegie Mellon University.
[11] Fernandez, E., Pelaez, J., & Larrondo-Petrie, M. (2007). Attack Patterns: A New Forensic and Design Tool. Paper presented at the IFIP International Federation for Information Processing.
[12] Kent, K., Chevalier, S., Grance, T., & Dang., H. (2006). Guide to Integrating Forensic Techniques into Incident Response: NIST Special Publication 800-86.
[13] Robiah, Y., Siti Rahayu, S., Shahrin, S., Mohd Faizal, A., Mohd Zaki, M., & Marliza, R. (2010). New Multi-step Worm Attack Model.
Journal of Computing, 2(1), 1-7.
[14] Robiah, Y., Siti Rahayu, S., Shahrin, S., Mohd Faizal, A., Mohd Zaki, M., & Marliza, R. (2010). An Improved Traditional Worm Attack Pattern. Proceedings of the 4th International Symposium on
Information Technology 2010 (ITSIM 2010).
[15] Siti Rahayu Selamat, Robiah Yusof, Shahrin Sahib, Mohd Zaki Masud, Mohd Faizal Abdollah, Zaheera Zainal Abidin. 2010. Advanced Trace Pattern for Computer Intrusion Discovery. Journal of Computing. Vol. 2 No. 6, June 2010.
[16] Barse, E. L. & Jonsson, E. (2004). Extracting Attack Manifestations to Determine Log Data Requirements for Intrusion Detection.
Proceedings of the IEEE 20th Annual Computer Security Applications