using Student Smart Card
(Case Study: UIN Syarif Hidayatullah Jakarta)
By:
Hossein Hosseini Farid
107091103916
INFORMATICS ENGINEERING STUDY PROGRAM
FACULTY OF SCIENCE AND TECHNOLOGY
STATE OF ISLAMIC UNIVERSITY SYARIF HIDAYATULLAH
JAKARTA
using Student Smart Card
(Case Study: UIN Syarif Hidayatullah Jakarta)
By:
Hossein Hosseini Farid 107091103916
INFORMATICS ENGINEERING STUDY PROGRAM FACULTY OF SCIENCE AND TECHNOLOGY
STATE OF ISLAMIC UNIVERSITY SYARIF HIDAYATULLAH JAKARTA
iii
Study on Developing Certificate Vending Machine by using Student Smart Card (Case Study: UIN Syarif Hidayatullah Jakarta)” can be finished without any obstacle.
This thesis almost talk about certificate vending machine and the process to print a paper without preview and taking the student data from AIS database directly, this main purpose for this project is to save the time of both students and UIN employee and encourage the students to believe on themselves and develop their own universities system by themselves.
After two month of developing a certificate vending machine application in smartcard contactless using jasper report method, the writer filling the increase of his knowledge, learning a lot of java coding strategy and techniques make me enjoy the software engineering field and for better future we need better basic knowledge.
In this moment, the writer would to thanks to all of structural person that covering this program
iv
5. Mr. Feri Fahrianto, M.Sc as a second guidance lecturer that always spare time with patience giving a guidance, a motivation, a suggestion, and a purpose to the writer in arranging the report.
6. Mrs. Finna as my partner to finish this project and developing an application in smartcard contactless using jasper report method for UIN.
7. Mr.Fauzi and Mrs. Ayu to help me where I got problems and ask helping for fix some java error.
8. The PUSOKM Team, and all of those guys that I cannot mentioned them one by one here, by the way thanks for everything.
9. My parent, my brothers, my sisters who always give support and never let me down.
10.Everyone who always help me, give me support and contribute to this research.
i UNIVERSITY OR INSTITUTION.
Jakarta, 1 June 2011
ii
Supervisor by Husni Teja Sukmana, Ph.D and Feri Fahrianto, M.Sc.
In this system students can get the UIN Surat by just clicking some buttons, Nevertheless that this data will save in database and UIN Staff will know who, when, and what kind of surat prints out. This system will help both students and UIN Staff for increasing their access to the UIN Surat. student’s time and the lack of good coordination between faculties and academic with long time of process make the students tired the reason to start study at developing certificate vending machine (CVM) was how to save the students times and make them focus on their studies, in other side helping UIN for developing new technology which for first time has been developed in Indonesian universities, in addition to that, help UIN by getting payment of each Surat that prints out.
In this research the writer has focusing about the actual and real students data by integrate the system with Academic System Information (AIS) and make the legal Surat by using barcode and Background art paper which has been explained details in chapter iv, are the important parts of the system.
Integrate netbeans with iReport and calling the data from pgadmin and save them back, having unity Surat for each student, read the data form student card (Smart Card) store the data inside chip and saving the process and more, are all activities that the writer has been done.
In this research the writer is using Extreme Programming (XP) for developing the CVM because of its fast move steps and team working which are the behavior of XP methodology.
Keywords: Developing, Integration, Certificate Vending Machine, Extreme Programming (XP), Smart Card, Barcode, Unified Modeling Language (UML), PostgresSQL, iReport, Radio Frequency Identification (RFID), Legalization. Number of Pages: 149 Pages
v
Statement... i
Abstract... ii
Preface... iii
List of Content... v
List of Picture... x
List of Table... xii
Glossary... xv
CHAPTER I INTRODUCTION 1.1 Background of the Developing System... 1
1.2Problems Identification... 3
1.3 Scope of the Developing System... 4
1.4 The Research Purpose and Advantages... 5
1.4.1 for the writer... 5
1.4.2 for the UIN JAKARTA... 7
1.5 The Research Methodology... 7
1.5.1 The Method of Gathering Data... 8
vi
2.2 Basic Concept of Information... 12
2.3 Basic Concept of Application... 15
2.4 Basic Concept of System Analysis... 16
2.5 Basic Concept of System Design... 16
2.6 Basic Concept of Information Technology... 17
2.7 Basic Concept of Software Engineering... 17
2.8 System Engineering ... …... 18
2.9 System Modeling ... …... 18
2.10 JAVA... 19
2.10.1. What is Java? ... 19
2.11 Jasper Report Concept... 20
2.12 Legalization of Paper (Secure Document) ... 22
2.13 Contactless smart card... 30
2.13.1. Benefits of Contactless Smart Cards... 30
2.14 Radio frequency identification (RFID) ... 32
2.14.1. RFID Benefit... 34
2.14.2. Common Problems with RFID... 37
2.15 About Certificate Vending Machine... 37
2.15.1. Variety Kind of Vending Machine... 39
vii
2.18 Barcode Concept... 46
2.19 PostgreSQL... 49
2.20 Unit Testing... 50
2.21 White Box……... 51
2.22 Related Works... 51
CHAPTER III RESEARCH METHOD 3.1 Research Method ... …… 54
3.1.1. Data Collection Techniques... 54
3.1.2. Requirements Gathering Techniques... 55
3.2 Systems Development Method... 56
3.2.1. Planning... 59
3.2.2. Design... 59
3.2.2.1. Applications Design... 60
3.2.2.2. Database Design... 61
3.2.2.3. Interface Design... 61
3.2.3. Coding... 61
3.2.4. Testing... 62
3.2.4.1. Unit Testing... 62
viii
4.1.1 VISION AND MISSION OF UIN... 67
4.1.2 Target Achievement PUSKOM... 67
4.1.3 Computer Science Faculty Profile... 68
4.1.3.1 International Undergraduate Program... 68
4.2 Current System Workflow... 69
4.2.1. Problem Identification... 74
4.2.2. Description of Purpose System... 75
4.2.3. Feasibility Study... 79
4.3 Requirement Gathering... 82
4.3.1 User Stories... 82
4.4 Proposed System Design... 118
4.4.1. Application Design... 119
4.4.2. Database Design... 133
4.4.3 User Interface Design... 136
4.5. Coding... 139
4.5.1. Programming Languages and Components... 139
4.5.2. Coding Implementation... 139
4.5.3. Components... 140
4.6 Testing Certificate Vending Machine... 141
ix
4.7.2. Custom Borders & Background Art... 144
CHAPTER V CONCLUSION 5.1 System Advantage... 146
5.2 Last view... 146
5.3 Suggestion... 148
5.4 Recommended... 148
xii
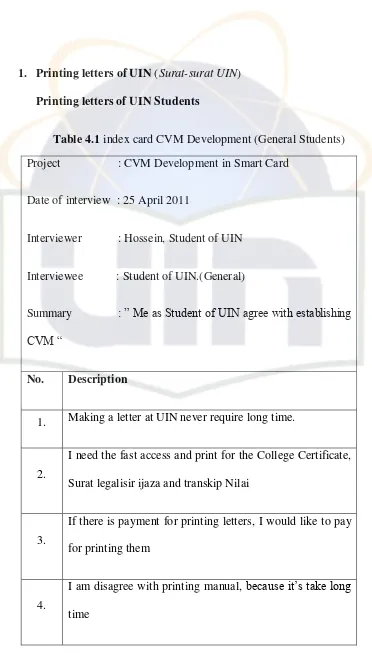
Table 4.1 index card CVM Development (General Students)... 84
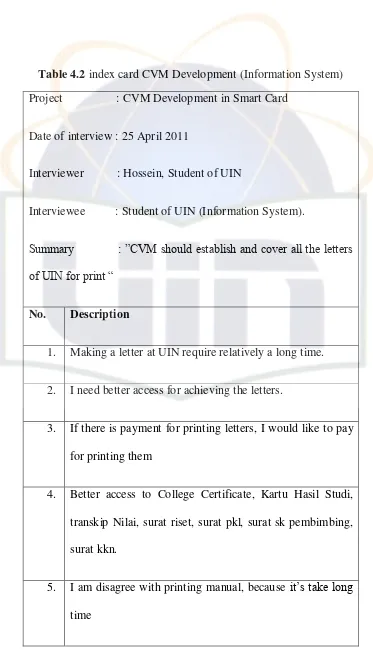
Table 4.2 index card CVM Development (Information System)... 85
Table 4.3 index card CVM Development (kesejahteraan social)... 86
Table 4.4 index card CVM Development (English Language Field)... 87
Table 4.5 index card CVM Development (Aqidah Filsafat)……... 88
Table 4.6 index card CVM Development (Aqidah Filsafat)……... 89
Table 4.7 index card CVM Development (Staff of UIN)………... 90
Table 4.8 index card CVM Development (Official staff of UIN)... 91
Table 4.9 index card CVM Development (Religious Difference)…... 92
Table 4.10 index card CVM Development (International Communication)... 93
Table 4.11 index card CVM Development (Journalistic)... 94
Table 4.12 index card CVM Development (Staff of PUSKOM.) ... 94
Table 4.13 index card CVM Development (Economy and Business)... 95
Table 4.14 index card CVM Development (Muamelat)... 96
Table 4.15 index card CVM Development (Information System)... 97
Table 4.16 index card CVM Development (Computer Science)... 97
Table 4.17 index card CVM Development (Tafsir Hadith)... 98
Table 4.18 index card CVM Development (Mazhab Fiqih Differences)... 99
Table 4.19 index card CVM Development (Dirasah Islamiah)... 100
xiii
Table 4.24 index card CVM Development (Dr. Ir. Syopiansyah Jaya Putra, M.Sis)... 105
Table 4.25 index card CVM Development (Herni Ali HT, SE, MM)... 106
Table 4.26 index card CVM Development (Mrs. Fitroh)... 107
Table 4.27 index card CVM Development (Dr. Agus Salim, M.Si)... 108
Table 4.28 index card CVM Development (Drs. Wahidin Saputra, M.Ag)... 109
Table 4.29 index card CVM Development (Mrs Mega Ratna Sari)... 110
Table 4.30 index card CVM Development (Drs. H. Mahmud Jalal, MA)... 111
Table 4.31 index card CVM Development (Mr.Guruh)... 112
Table 4.32 index card CVM Development (Prof. Dr. Ahmad Thib Raya)... 113
Table 4.33 index card CVM Development (Dr. Wahid Hasyim, M0A)... 113
Table 4.34 index card CVM Development (Prof. Dr. Abdul Shomad.)... 114
Table 4.35 index card CVM Development (Prof. Dr. Abdul Hamid, MS)... 115
Table 4.36 index card CVM Development (Drs Marzuki Mahmud MPd)... 116
Table 4.37 index card CVM Development (Mr. Joko Adianto)... 117
Table 4.38 CRC card class introduction... 119
Table 4.39 CRC card class (Students Login)... 119
Table 4.40 CRC card class bahasa (language)... 119
Table 4.41 CRC card class (Menu Selection)... 120
Table 4.42 CRC card class JumHalamanKeterangan... 120
xiv
Table 4.47 CRC card class language... 122
Table 4.48 CRC card class alumni (Menu Selection)... 122
Table 4.49 CRC card class alumni JumHalamanKeterangan (alumni)... 122
Table 4.50 CRC card class alumni JumHaltranscripts (alumni)... 123
Table 4.51 CRC card class alumni JumHalLulus (alumni)... 123
Table 4.52 requirement and use case Printing Surat... 124
Table 4.53 Use case scenario printing Surat Keterangan... 126
Table 4.54 Use case scenario printing Surat IPK and IPS... 127
Table 4.55 Use case scenario printing Transcripts... 127
Table 4.56 Use case scenario printing Surat lulus... 128
CHAPTER I
INTRODUCTION
1.1 Background of the Developing System
Developing a software engineering system nowadays is very important for companies, factories, marketing, malls and all of the shopping center and business job, you can imagine the fast of accounting, the comfortable absent for lecturers, students and employees, the easier counting for markets etc.
"To waste time is one's greatest loss."(Imam Ali as 650 M)
“Men talk of killing time, while time quietly kills them.” (~Dion Boucicault 1998)
The absence of good managements for printing College Certificate and other documentation in Islamic University of UIN JAKARTA make the writer to start to developing title, why the writer start to do this title, is for improving the ability and increasing the talent of student for using new technology and encouragement them for developing new technology for making life easier.
The main problem in manual system was Students needs to go to the academic faculty or academic center for printing the letter, Students taking a long time around one till one week for getting a letter, the lack of integration between the existing academic system, cause printing transcript value and GPA, take a long time than usual, the absence of digital signatures, cause if the Program study, faculty, or academic, are not in place then the processing of student letter will not postponed.
Smart card itself is any pocket-sized card with embedded integrated circuits that can process and store data, and communicate with a terminal via radio waves. Smart Cards are capable of not just storing data but also have processing power, in this system the writer use smart card for making the process easier and faster, storage data and process it directly is one of benefit of smart card which can done by smart card, Certificate Vending Machines (CVM) can be interpreted as a tool or machine for printing letters automatically, the students may go to the tool and by using a student card that belongs to them or their friends to print a letter that they needs Certificate Vending Machine will print letters in a real-time time, by using this tool students can save their times.
1.2 Problems Identification
According to the background in which the writer has already explained above, the areas of problem in which will explain in this thesis report are:
a. How can the writer develop a system that is easier to access by all of students, because as we know Islamic University of UIN JAKARTA is an International University which means include two languages which are Bahasa Indonesia and English.
b. Numbers of activities associated with making such as GPA letter, College certificate, transcripts value, graduation certificates, etc. c. The flow for making a letters and certificates are quite long and
consuming a lot time
d. Could delay the process of making the letters if the party concerned is not in place.
e. How to develop the title, in PUSKOM UIN JAKARTA.
f. Developing Certificate Vending Machine, using GUI, JAVA, Postgres, Smart Card Reader etc.
g. Setting the deposit for each of students thus they can print directly with the amount of deposit that they save in their ID card.
i. Adding the use of Student Identity Card (KTM) by means of integration between existing student card (smart card) With Certificate Vending Machine
j. Analysis and recommendations for printing the letters and legalized in terms of validating the authenticity (originality letter)
1.3 Scope of the Developing System
In this thesis, the writer gives the limitation in developing the system. The area includes:
1. The content of the system is the data from user (Alumni and student) at PUSKOM UIN JAKARTA in AIS database.
2. This system covers setting amount deposit which takes it from AIS database in addition to that taking the human resources from AIS database.
3. The testing process has been done by smart card reader ISO specifications 14443.
4. CVM system was limited to the design and analysis, and implementation of programs.
5. It’s specially developed for students and alumni of UIN Syarif Hidayatullah JAKARTA.
1.4 The Research Purpose and Advantages
1.4.1 for the writer
1. Learning Smart Card as a new technology. Understand the concept of Smart Card.
2. Learning about Certificate Vending Machine (CVM) as new technology and understand the way that it integrate and interact with the costumers.
3. Study about Jasper Report and its concept, beside print the report with/without the preview.
4. More understand about JAVA concept and create the system with it.
5. The writer can implement his knowledge that he got from UIN Syarif Hidayatullah JAKARTA, especially in programming language, and software engineering field. 6. Understanding about how the Extreme Programming
methodology steps and how it works and how the writer should manage the research.
7. Understanding about both netbeans and eclipse as IDE (Integrated development environment) for developing the system and their integrated with Postgres database server. 8. Understanding about CVM and how it works with using
9. Learning about object and parameter which involved in the system.
10.How to set some amount of deposit and how to save the array in txt and call it again using “buffer reader” method.
11.How to manage the barcode and give an authenticity to the official stuff of UIN.
12.Increasing knowledge and ability in PUSKOM under the teaching of smart lecturers.
13.Know how to interact with team and work together for developing a system and make it work.
14.Setting the connection of jasper report with postgres.
15.Learning the way of interacting with JFrame and calling the label method, in addition to how change the String to the Integer.
16.Using toString() method, because the parameter in class JumlahHalamanketerangan.java extends JFrame should to be string thus the writer use toString() method, that can change the object to the string.
1.4.2 for the University of UIN Syarif Hidayatullah JAKARTA
1. Making the Certificate Vending machine title in increasing the performances of the University.
2. Display the students and alumni data for easy access to CVM and printing their needs as College Certificate .
3. Allows the students and alumni to see their grades transcript and print the requires letter using their money.
4. Give a high technology to UIN, can encourage them to be better.
5. Saving the time for the both students and employee of UIN. 6. Saving the money of UIN, because this project has been done
using its own students for free as research.
1.5 The Research Methodology
The writer should collect the data for research projects. The data may be collected for either theoretical or practical research.
1.5.1 The Methodology of Gathering Data
A. Observation
The collection of data with direct observation is a way to collect data by using the eye without the help of other standard tools for this purpose. [1]
B. Interview Method
Interview is a technique of collecting data by asking a direct question by the interviewer to the respondent, and respondent's answers are noted or recorded. [1]
C. Literature Study
1.6 Structure of Report
In this theis report the writer use five chapters with some explanation in each chapter. The schemes are:
CHAPTER I INTRODUCTION
In chapter one, the writer talks about the scope of the system, what are the problems, background of developing system, identified them try to bring well sorted solution, the purpose to start developing system.
CHAPTER II LITERATURE REVIEW
In chapter two, the writer talks about definition of the systems and how to have a well known understanding about system developing method, it will help the readers for better understanding with the new words and system for software engineering. In addition the writer brings brief description about the each chapter that has been used in the title.
CHAPTER III RESEARCH METHODOLOGY
CHAPTER IV SYSTEM IMPLEMENTATION
In chapter four which is system implementation, the writer mentioned some important points, for example how the development process. The simulation of the system and Strategy of developing system also includes in this section thus the most important part of the thesis is the developing system implementation by giving all details in place.
CHAPTER V CONCLUSION
CHAPTER II
LITERATURE STUDY
2.1 Basic Concept of System
System is a collection of components that implement modeling requirements, functions, and interfaces. [2] The word sometimes describes the organization or plans itself and is similar in meaning to method.
A system is a group of interrelated components that function together to achieve a desired result. For instance, you may own a home theater system made up of a DVD player, receiver, speakers, and display monitor [3]
2.1.1 System Characteristic
A system has some characteristic and certain properties. It has components, system boundary, outside the system environment, link, input, output, processing and targets or goals. [4]
1. System Component
Systems consist of interrelated components (a relationship exists between parts and the whole).
2. System Boundary
System boundaries are artificial: systems are components of another larger system. Systems can be opened (influenced by their environment) or closed (not influenced by their environment).
3. Outside the system environment
4. System input, output, link and process
Systems must have inputs, processes, outputs, and feedback loops.
5. System’s target or goal
A system has a goals or objectives, if the system doesn't has goal, then the system will be useless. The Input to the system and the output from the system is very determined by the goal or objective. A system is said to be successful when it has achieved the goals or objectives.
2.2 Basic Concept of Information
and interpret other information. In short, you have quite an undertaking ahead of you, since there is so much information to be had. [5]
How Is Information Organized? If you consider information in the sense
hopefully as a means for teaching future people what to do and what not to do. So, when you click your mouse on a resource on the Internet and think that it is so wonderful, keep in mind that it is even more wonderful than you can imagine, but that there are also even better ways to find reliable information than just following any link that anyone happens to stick on the Internet.
Yes, you can find myriad sources of information online for free, but many of the materials that you can really count on are not freely available, so you need to rely on organization and cataloging and indexing to take advantage of those "heavy duty" sources. And you can rely on libraries to continue to provide you with materials that you may never be able to access freely on the Internet. Information and organizing information is what libraries are about.
2.3 Basic Concept of Application
Application sometimes called a program that is a series of instructions that the hardware executes one after another [6]. In information technology, an application is the use of a technology, system, or product.
programs. Applications use the services of the computer's operating system and other supporting applications.
2.4 Basic Concept of System Analysis
Analysis is the process of breaking a complex topic into smaller parts from among various alternatives to achieve a better understanding of it. In system development process, there is system analysis that provides the project team with a more thorough understanding of the problems and needs that triggered the project. The system analysis requires working with system users to clearly define business requirements and expectations for any new system that is to be purchased or developed [3]
2.5 Basic Concept of System Design
Information system design is defined as those tasks that focus on the specification of a detailed computer-based solution. It is also called physical design. Thus, whereas systems analysis emphasized the business problem, system design focuses on the technical or implementation concerns of the system.
System design is driven by the technical concerns of system designers. Hence, it address the IS building blocks from the system designer’s perspective.
2.6 Basic Concept of Information Technology
Information technology is a contemporary that describes the combination of computer technology with telecommunications technology (data, image, and voice networks) [3] Information system an arrangement of people, data, process, and information technology (IT) that interact to collect, process, store, and provide as output the information needed to support an organization.
2.7 Basic Concept of Software Engineering
Software Engineering is an approach to developing software that attempts to treat it as a formal process more like traditional engineering than the craft that many programmers believe it is. We talk of crafting an application, refining and polishing it, as if it were a wooden sculpture, not a series of logic instructions. The problem here is that you cannot engineer art. Programming falls somewhere between an art and a science [7]
2.8 System Engineering
Systems engineering is an interdisciplinary approach and means to enable the realization of successful systems. It focuses on defining customer needs and required functionality early in the development cycle, documenting requirements, and then proceeding with design synthesis and system validation while considering the complete problem.
Systems engineering integrates all the disciplines and specialty groups into a team effort forming a structured development process that proceeds from concept to production to operation. Systems engineering considers both the business and the technical needs of all customers with the goal of providing a quality product that meets the user needs, Definition Based on International Council on Systems Engineering [9].
2.9 System Modeling
2.10 JAVA
2.10.1 What Is Java?
Java is a computer programming language. It enables programmers to write computer instructions using English based commands, instead of having to write in numeric codes. It’s known as a “high-level” language because it can be read and written easily by humans. Like English, Java has a set of rules that determine how the instructions are written. These rules are known as its “syntax”. Once a program has
been written, the high-level instructions are translated into numeric codes that computers can understand and execute. In the early nineties, Java was created by a team led by James Gosling for Sun Microsystems. It was originally designed for use on digital mobile devices, such as cell phones. However, when Java 1.0 was released to the public in 1996, its main focus had shifted to use on the Internet. It provided more interactivity with users by giving developers a way to produce animated WebPages. Over the years it has evolved as a successful language for use both on and off the Internet. A decade later, it’s still an extremely popular language with over
6.5million developers worldwide.[11]
Why Choose Java?
Java was designed with a few key principles in mind:
Easy to Use: The fundamentals of Java came from a programming
too complex in its syntax, and inadequate for all of Java's requirements. Java built on, and improved the ideas of C++, to provide a programming language that was powerful and simple to use.
Reliability: Java needed to reduce the likelihood of fatal errors from
programmer mistakes. With this in mind, object-oriented programming was introduced. Once data and its manipulation were packaged together in one place, it increased Java’s robustness.
Secure: As Java was originally targeting mobile devices that would be
exchanging data over networks, it was built to include a high level of security. Java is probably the most secure programming language to date.
Platform Independent: Programs needed to work regardless of the
machine they were being executed on. Java was written to be a portable language that doesn't care about the operating system or the hardware of the computer.
2.11 Jasper Report Concept
participation, and, best of all, it's free. This article kicks off Java World's new Open Source Profile column dedicated to Java-based open source tools and components. Look for upcoming articles spotlighting the Echo Web application framework and ObJectRelationalBridge, an object/relational mapping tool. Feel free to send me your suggestions for future articles.
Jasper Reports Server is a powerful, yet flexible and lightweight reporting server. Generate, organize, secure, and deliver interactive reports and dashboards to users. Allow non-technical users to build their own reports and dashboards.
Flexible server architecture
o Semantic layer for relational and non-relational data sources - BI Editions only.
o On-premises, virtualized, or Cloud (SaaS & PaaS) deployment options.
o Open standards, web service-driven architecture simplifies application integration.
Centralized repository
o Connectivity to existing identity management systems to centralize and secure reports and analysis views.
o Report access and usage auditing for compliance.
o Granular security access down to the cell and column level. Ad hoc reports - BI Editions only
o Metadata layer masks complex data descriptions with simplified business user-friendly names.
o Web-based reports provide rich, interactive reports with drill down, filtering, animated charting, and more.
Dashboards - BI Editions only
o Web-based, drag-and-drop dashboard designer.
o Single report and dashboard-level parameters drive user interaction.
o Free-form layout designer for customized dashboard design.[12]
2.12 Legalization of Paper (Secure Document)
CVM paper products are protected by a variety of overt (obvious) and covert (unknown) security features. Depending upon the intended application, Protected Paper's layered approach to printing includes a combination of the base paper stock, custom artwork, patented Authentic Guard technologies, use of security inks, as well as a variety of finishing techniques. The writer combines these anti-copy and alter-resistant techniques to provide a product that is both effective and affordable.
Base Paper Stock
Our initial defense against counterfeiting and document alteration starts at the paper mill. Most any of our paper products are printed on a laser compatible base security paper that is UV dull, with invisible fluorescent fibers (detectable under an ultraviolet light source) and chemical sensitivity to solvents (stains or multi-language "VOID" messages appear if the document is altered). If and when required, we can also offer fully customized and Fourdrinier watermark papers.[13]
Pantograph 4000
(Original) (Attempted B&W Copy /Fax) (Attempted Color Copy / Scan)
Picture 2.1 Pantograph 4000 Legal paper
etc.) into the background of a document. Text information or other artwork is placed onto this paper. Then, when this "original" is copied of scanned, the hidden word pattern becomes visible on the duplicate. The end result a clearly distinguishable copy that cannot pass off as the original.[13]
Block out
(Original) (Attempted Color Copy / Scan)
This anti-copy technology is meant to provide protection against high-end color copiers and scanning devices. Patented Block out designs are embedded into original artwork, photographs and other important information that requires protection against unauthorized duplication. Block out technology can be placed on most any type of printable substrate, making it ideal for a multitude of applications including ID cards, product warranties, discount coupons, commercial photo proofing and ticketing..[13]
Prism
Picture 2.3 Prism Legal paper
only become visible using our Authenticator device a proprietary lens that reveals the hidden Prism messages. Customizable and low cost, AuthentiGuard's Prism technology cannot be reproduced or duplicated with even the most sophisticated digital copiers or scanners. .[13]
Custom Borders and Background Art
Picture 2.4 Custom Borders and Background Art
Heat-Sensitive Security Ink
Picture 2.5Heat-Sensitive Security Ink
Erasable Ink
Picture 2.6Erasable Ink
Coin Activated Ink
Picture 2.7Coin Activated Ink
2.13 Contactless smart card
A contactless smart card is any pocket-sized card with embedded integrated circuits that can process and store data, and communicate with a terminal via radio waves. There are two broad categories of contactless smart cards. Memory cards contain non-volatile memory storage components, and perhaps some specific security logic. Contactless smart cards do not contain an ordinary read-only RFID, but they do contain a re-writable smart card microchip that can be transcribed via radio waves. The first contactless smart card was the Octopus card introduced in Hong Kong in 1997 for the territory's mass transit system.[14]
2.13.1 Benefits of Contactless Smart Cards
Contactless smart cards can be used for identification, authentication, and data storage. Contactless smart cards provide a means of effecting business transactions in a flexible, secure, standard way with minimal human intervention.
turnstiles, and station platforms as a standalone unit. When used for security, readers are usually located to the side of an entry door. [14]
Supported Applications
o The CardMan® 5321 allows users to experience Convenience, speed, and security of contactless.
o Technology for applications including log-on to Windows®, networks, websites, or the secure Storage of user names, passwords, and personal Information.
o The use of contactless smart card.
o Technology for PC-linked applications is limited only to your
imagination.[15]
Contactless Smart Cards Supported
o The CardMan® 5321 is based on a 13.56 MHz
o Contactless smart card interface that is compliant ISO specifications 14443 A and B and 15693.
o The reader works with a variety of 13.56 MHz Contactless smart cards including, but not limited to:
2.14 Radio frequency identification (RFID)
Radio frequency identification (RFID) is a method of remotely storing and retrieving data using devices called RFID tags. An RFID tag is a small object such as an adhesive sticker, that can be attached to or incorporated into a product. RFID tags contain antennae to enable them to receive and respond to radio frequency queries from an RFID transceiver. [14]
History of RFID tags
Although some people think that the first known device may have been invented by Leon Theremin as an espionage tool for the Russian Government in 1945, the first real usage of RFID devices predates that. During World War II the United Kingdom used RFID devices to distinguish returning English airplanes from inbound German ones. RADAR was only able to signal the presence of a plane, not the kind of plane it was. [14]
The RFID System
The purpose of an RFID system is to enable data to be transmitted by a portable device, called a tag, which is read by an RFID reader and processed according to the needs of a particular application. The data transmitted by the tag may provide identification or location information, or specifics about the product tagged, such as price, color, date of purchase, etc. The use of RFID in tracking and access applications first appeared during the 1980s. RFID quickly gained attention because of its ability to track moving objects. As the technology is refined, more pervasive - and invasive - uses for RFID tags are in the works. [14]
Low -frequency RFID tags are commonly used for animal identification, beer keg tracking, and automobile key-and-lock, anti-theft systems. Pets are often embedded with small chips so that they may be returned to their owners if lost. In the United States, two RFID frequencies are used: 125kHz (the original standard) and 134.5kHz, the international standard.
High-frequency RFID tags are used in library book or bookstore tracking, pallet tracking, building access control, airline baggage tracking, and apparel item tracking. High-frequency tags are widely used in identification badges, replacing earlier magnetic stripe cards. These badges need only be held within a certain distance of the reader to authenticate the holder. [14]
2.14.1 RFID Benefit
Here is a quick checklist of several benefits that can be achieved with RFID solutions:
1. Reduce warehouse and distribution labor costs
2. Reduce point-of-sale labor costs
With RFID-enabled products, checkout can be completed with a quick scan of all items in cart helping to reduce point-of-sale labor costs. The current scan-it-yourself component of self-service checkout can be improved, helping to improve adoption, reduce self-service checkout times and reduce fraud.
3. Reduce inventory
Inventory accuracy is important to helping eliminate excess/missing inventory, losses and write downs. With RFID, inventory errors can be reduced so that the company can be assured that the inventory indicated is the actual inventory available.
4. Improve forecasting and planning
Visibility improvements throughout the supply-chain can help to improve the forecasting capabilities to help better track where inventory is and what is happening to it throughout the supply chain.
5. Reduce theft
lost. Within the retail store, RFID can and has been successfully deployed, particularly on higher margin items, to help prevent theft.
6. Reduce out-of stock conditions
When an item is out of stock the customer is often left disappointed, either avoiding the purchase altogether common in grocery stores where as much as 4% of their revenue is lost each year due to out-of-stock conditions or worse, the customer moves on to a competitor in order to source the product. Eliminating out-of-stock conditions via better RFID product tracking and inventory visibility and forecasting, such as alerting the store staff immediately when the last item leaves the shelf, can have an immediate top-line revenue impact and have residual effects by improving customer service and satisfaction.
7. Improve customer experience
2.14.2 Common Problems with RFID
Some common problems with RFID are reader collision and tag collision. Reader collision occurs when the signals from two or more readers overlap. The tag is unable to respond to simultaneous queries. Systems must be carefully set up to avoid this problem. Tag collision occurs when many tags are present in a small area; but since the read time is very fast, it is easier for vendors to develop systems that ensure that tags respond one at a time. See Problems with RFID for more details.[14]
2.15 About Certificate Vending Machine
Vending machines are coin-operated machines that can dispense snacks, drinks, sandwiches, coffee, tea and other products. Vending machines are an extremely convenient outlet for the industry known as automatic retailing. You might find vending machines in public buildings, transportation hubs and subways, at gas stations, courthouses, hospitals, and the local automotive repair shop. Any place that people gather, pass by, or must wait, is a good location for vending machines.
Though vending machines provide service to the public, not everyone is pleased in all cases with their offerings. Many school districts came under fire in the United States for providing vending machines on school grounds that offered high-sugar, low nutrient snacks and drinks. The vending machines’ contents were cited as a possible aggravating factor to potential teenage medical concerns regarding obesity and diabetes. As a result, several schools districts switched to vending machines that offered healthier alternatives.
2.15.1 Variety Kind of Vending Machine
Coin Vending Machines:
Invention of the first vending machine is credited to Hero of Alexandria circa 215BC. His vending machine accepted a coin and dispensed holy water in return.
A coffee vending machine is a coin operated, automatic dispenser of paper cups filled with one or more different types of coffees. The machines are usually quite large and rectangular in shape like most vending machines. [16]
Food Vending Machines:
Depending on where someone is placing the machine, it may be possible to sell a number of more unusual items to turn the vending machine into a destination rather than just a convenience. Vending machines are not limited to foods and beverages and can also be used to sell toys, home supplies, and other small items.
Beverage Vending Machines:
Depending on where someone is placing the machine, it may be possible to sell a number of more unusual items to turn the vending machine into a destination rather than just a convenience. Vending machines are not limited to foods and beverages and can also be used to sell toys, home supplies, and other small items.
A coffee vending machine may be placed in a row with other types of food and beverage machines. Some vending machines dispense water and soda, while others offer snacks such as potato chips and candy bars. [16]
Drinks Vending Machines:
Many school districts came under fire in the United States for providing vending machines on school grounds that offered high-sugar, low nutrient snacks and drinks. The vending machines’
contents were cited as a possible aggravating factor to potential teenage medical concerns regarding obesity and diabetes.
Coffee Vending Machines:
In 1960, a bean grinder became a part of many coffee vending machines, while 1991 saw the addition of different coffees being available by machine. These coffees include espresso, cappuccino and flavored varieties. A coffee vending machine may be placed in a row with other types of food and beverage machines.
Vending machines are coin-operated machines that can dispense snacks, drinks, sandwiches, coffee, tea and other products. Vending machines are an extremely convenient outlet for the industry known as automatic retailing. [16]
Snack Vending Machines:
No kidding, you are twice as likely to die being crushed by a falling vending machine than being eaten by a shark. The odds of being a shark snack are about 1 in 252 million, but the odds of being crushed while purchasing a frosty soda are about 1 in 112 million.
Candy Vending Machines:
Here you can find a wide variety of items for sale through vending machines, from underwear to compact discs and jewelry. Some major manufacturers of vending machines include Automatic Products, Crane National, Dixie-Narco Inc., Glasco Polyvend Lektrovend (GPL), Royal Vendors, and U Select It.
In 1888, the United States began dispensing gum and small toys in vending machines before later using them mainly for candy, potato chips, soda and coffee. [16]
Cigarette Vending Machines:
2.15.2 The Difference between Snack Machine and Automated
Vending Machine
A snack machine dispenses items like candy, gum, peanuts, cookies, sandwiches and other supplements to lunch or dinner. A vending machine will mix coffee, tea, soup, hot chocolate and other liquid supplements. Other vending machines sell cigarettes, sundry items (tissues, combs, nail clippers, etc.) and flowers. Still others will make change while the ultimate (the ATM) allows you the borrow money from your bank 24 hours per day which our certificate vending machine talk about it and it’s similar to the ATM. [16]
2.16 Digitized Signature
A digitized signature (not to be confused with a digital certificate) is an electronic signature that can be used to authenticate the identity of the sender of a message or the signer of a document, and possibly to ensure that the original content of the message or document that has been sent is unchanged. Digital signatures are easily transportable, cannot be imitated by someone else, and can be automatically time-stamped. The ability to ensure that the original signed message arrived means that the sender cannot easily repudiate it later.
2.17. Touch Screen Concept
A touch screen is a computer display screen that is also an input device. The screens are sensitive to pressure; a user interacts with the computer by touching pictures or words on the screen.
There are three types of touch screen technology:
Resistive: A resistive touch screen panel is coated with a thin metallic
electrically conductive and resistive layer that causes a change in the electrical current which is registered as a touch event and sent to the controller for processing. Resistive touch screen panels are generally more affordable but offer only 75% clarity and the layer can be damaged
by sharp objects. Resistive touch screen panels are not affected by outside elements such as dust or water.
Surface wave: Surface wave technology uses ultrasonic waves that pass
over the touch screen panel. When the panel is touched, a portion of the wave is absorbed. This change in the ultrasonic waves registers the position of the touch event and sends this information to the controller for processing. Surface wave touch screen panels are the most advanced of the three types, but they can be damaged by outside elements.[18]
Capacitive: A capacitive touch screen panel is coated with a material that
processing. Capacitive touch screen panels must be touched with a finger unlike resistive and surface wave panels that can use fingers and stylus. Capacitive touch screens are not affected by outside elements and have high clarity.
Touch screen monitors are no longer confined to bar video games as novelty items. Today, they can be found in many stores as part of cash registers, in car dashboards and on many portable computers. With the growing popularity of touch screen enabled Palm Pilots and other PDAs, many people even have one in his or her pocket at all times.
2.17.1 The touch screen benefit
2.18 Barcode Concept
What is a Barcode?
A bar code (often seen as a single word, barcode) is the small image of lines (bars) and spaces that is affixed to retail store items, identification cards, and postal mail to identify a particular product number, person, or location. The code uses a sequence of vertical bars and spaces to represent numbers and other symbols. A bar code symbol typically consists of five parts: a quiet zone, a start character, data characters (including an optional check character), a stop character, and another quiet zone.[19]
When you purchase an item from any store, you will notice a label with thin, black lines across it, along with a variation of different numbers. This label is then scanned by the cashier, and the item's description and price automatically come up. The word for this is called a barcode, and it is used to read data and information based upon the widths of those small black lines. The barcode has many uses, although most of us think of them as simply a way to price items in the grocery or department store. Barcodes are becoming more and more common in just about every facet of consumer life. For example, car rental companies now identify their rental vehicles by using a barcode. Your luggage gets assigned a barcode when you check it into the airport in order to assure more accuracy when it comes to keeping track of it. Even driver's licenses today have barcodes on them in most states. Medicine prescriptions, library books, and tracking different shipments are also other ways that a barcode can be used. [19]
their own special individuality. Barcodes are very useful for maintaining accurate information about inventory, pricing, and other important business-related data.
2.19 PostgreSQL
According to Neil Mathew and Richard Stones(2005:11), PostgreSQL
actually is a DBMS that incorporates the relational model for its databases and supports the SQL standard query language. PostgreSQL also happens to be very capable and very reliable, and it has good performance characteristics. It runs on just about any UNIX platform, including UNIX-like systems, such as FreeBSD, Linux, and Mac OS X. It can also run on Microsoft Windows NT/2000/2003 servers, or even on Windows XP for development. PostgreSQL can be compared favorably to other DBMSs. It contains just about all the features that you would find in other commercial or open-source databases, and a few extras that you might not find elsewhere.
PostgreSQL features (as listed in the PostgreSQL FAQ) include the following: • Transactions
• Subselects • Views
• Foreign key referential integrity • Sophisticated locking
• User-defined types • Inheritance
• Rules
2.20 Unit Testing
Unit testing is a software development process in which the smallest testable parts of an application, called units, are individually and independently scrutinized for proper operation. Unit testing is often automated but it can also be done manually. This testing mode is a component of Extreme Programming (XP), a pragmatic method of software development that takes a meticulous approach to building a product by means of continual testing and revision.
2.21 White Box
In software development, White-box testing (a.k.a. clear box testing, glass box testing, transparent box testing, or structural testing) is a method of testing software that tests internal structures or workings of an application, as opposed to its functionality. In white-box testing an internal perspective of the system, as well as programming skills, are required and used to design test cases
Picture 2.8White Box
2.22 Related Works
A numbers of previuos studis has been conducted on developing certificate vending machine, by using this references and related works the research will be more strong and acceptable. below the writer has mentioned them,
2.1 Related Work Table
Title Author summary Methodology
Digital
It useful for this system as long as the integration exist between systems
CHAPTER III
RESEARCH METHODOLOGY
3.1 Research Methodology
In essence, the research is a way of so many ways which is pursued to get the truth. To get the truth it is done through scientific methods. So, it’s not excessive if the method is called as strategies in scientific research [23]
3.1.1 Data Collection Techniques
Data collection techniques taken are as follows:
Good requirements start with good sources. Finding those quality sources is an important task and, fortunately, one that takes few resources. Examples of sources of requirements include: [24]
Customers Users
Administrators and maintenance staff Partners
Domain Experts Industry Analysts
3.1.2 Requirements Gathering Techniques
After you have identified these sources, there are a number of techniques that may be used to gather requirements. The following will describe the various techniques, followed by a brief discussion of when to use each technique.
To get the requirements down on paper, you can to do one or more of the following:
Conduct a brainstorming session Interview users
Send questionnaires
Work in the target environment Study analogous systems
Examine suggestions and problem reports Talk to support teams
Study improvements made by users
3.2 Systems Development Method
The first Extreme Programming project was started March 6, 1996. Extreme Programming is one of several popular Agile Processes. It has already been proven to be very successful at many companies of all different sizes and industries worldwide.
Extreme Programming is successful because it stresses customer satisfaction. Instead of delivering everything you could possibly want on some date far in the future this process delivers the software you need as you need it. Extreme Programming empowers your developers to confidently respond to changing customer requirements, even late in the life cycle.
Extreme Programming emphasizes teamwork. Managers, customers, and developers are all equal partners in a collaborative team. Extreme Programming implements a simple, yet effective environment enabling teams to become highly productive. The team self-organizes around the problem to solve it as efficiently as possible.
Extreme Programmers are able to courageously respond to changing requirements and technology.[15][16]
Picture 3.1 Steps of Extreme Programming
The most surprising aspect of Extreme Programming is its simple rules. Extreme Programming is a lot like a jig saw puzzle. There are many small pieces. Individually the pieces make no sense, but when combined together a complete picture can be seen. The rules may seem awkward and perhaps even naive at first, but are based on sound values and principles.
Our rules set expectations between team members but are not the end goal themselves. You will come to realize these rules define an environment that promotes team collaboration and empowerment that is your goal. Once achieved productive teamwork will continue even as rules are changed to fit your company's specific needs.
activities have been trimmed to reduce costs and frustration of everyone involved.[25]
The Core of Extreme Programming following twelve steps as follow: 1. Customers define application features with user stories.
2. XP teams put small code releases into production early.
3. XP teams use a common system of names and descriptions.
4. Teams emphasize simply-written, object-oriented code that
meets requirements.
5. Designers write automated unit tests upfront and run them
throughout the project.
6. XP teams frequently revise and edit the overall code design, a
process called refactoring.
7. Programmers work side by side in pairs, continually seeing and
discussing each other’s code.
8. All programmers have collective ownership of the code and the
ability to change it.
9. XP teams integrate code and release it to a repository every few
hours and in no case hold on to it longer than a day.
10. Programmers work only 40 hours per week; there’s no overtime.
11. A customer representative remains on-site throughout the
12. Programmers must follow a common coding standard so all the
code in the system looks as if it was written by a single individual.
3.2.1. Planning
This step is the stage of planning the system to be developed. At this stage the writer focus on:
a. The collection of user requests (user stories), so that the output of the system will accordance with the wishes of the users.
b. Observation of the current system at UIN Syarif Hidayatullah Jakarta.
c. Identify the problem that occurs in the current system.
d. Determining the flow work of business and applications as well as the data issues that will be supported by the system to be developed and determine the limits scope of the system. [27]
3.2.2. Design
3.2.2.1. Applications Design
To design an application, the writer uses the tool that is CRC (Class - Responsibility - Collaborator); in this section the writer defines the classes that will be used on the system. In addition, the application is also designed using the Unified Modeling Language (UML). This is done to facilitate to provide a preliminary sketch of applications, in addition to the use of UML is more suitable for use in designing an application that is object oriented. Designing applications that the writer did using UML tools include: [27]
1. Determination Actor
2. Design Use Case Diagram
3. Design Use Case Scenario
4. Design Activity Diagram
5. Design Sequence Diagram
6. Design Class Diagram
3.2.2.2. Database Design
As has been explained on the basis of the theory, the concept of Object Relational Mapping, the data used in an application will be stored into the database. Next the writer explains about the steps which will include in database design, [27]
a. Table Structure
b. Display database structure (relational database)
3.2.2.3. Interface Design
At this stage, the writer conducted the design of the user interface of this application. The design was conducted on the pages that exist in the system. [27]
3.2.3. Coding
At the coding stage, prior to developing applications based on the previous stages, unit tests for each user stories prepared. The writer conducted a deployment of applications that have been developed to target a specific server.
improve the quality of the program structure. At this stage also build program as often as possible so that errors in the program can be detected as soon as possible.[27]
3.2.4. Testing
3.2.4.1. Unit Testing
At this step writer use unit test which is individually and independently scrutinized test for Certificate Vending Machine Application, in this research the writer did the unit testing manually.
Unit testing is a software development process in which the smallest testable parts of an application, called units, are individually and independently scrutinized for proper operation. Unit testing is often automated but it can also be done manually. This testing mode is a component of Extreme Programming (XP).[28]
3.2.4.2. White Box
For this white box the writer invite two students and two
alumni as the system actors for use the system the result shown in chapter four.
outcome is, but not how the results are achieved. A white box component is a compiled program that is protected from alteration by ensuring that a programmer can only access it through an exposed interface.[28]
3.3 Research Workflow
CHAPTER IV
ANALYSIS AND DESIGN SYSTEM
4.1 UIN Profile
sympathy from the society, He also often helped people who were poor and suffering.
Syarif Hidayatullah tried not to contradict the beliefs and traditions of the local people. Rather, he showed the beauty and modesty of Islam, and also proved that Islam brings advantages and equality to all the people. In order to set a good example of tolerance and equality, he married the sister of the Mayor of the Banten regency, Princess Kaunganten (14751. a Chinese princess, Ong Tien (1481), an Arab princess, Sharifah Bagdad, and Nyi Tepasari from Majapahit.
During his lifetime he saw his son, Maulana Hasanuddin, became a religious propagator and the ruler of Banten. In 1527, with the support of Falatehan (Fatahillah). he succeeded in occupying Sunda Kelapa and expelled the Portuguese soldiers, led by Fransisco de Sa, from the island.
UIN Strategy
1. To foster the development of faculties, departments and study programs. 2. To be accredited nationally and internationally.
3. To adopt curricula based on competency and learning based on research. 4. To maximize the availability of facilities.
5. To enhance the quality of the human resources. 6. To encourage entrepreneurship.
4.1.1 VISION AND MISSION OF UIN SYARIF HIDAYATULLAH
VISION
Build self-reliance in the ICT field in order to support the vision UIN as a world class research University
MISSION
- Create a system ICT innovative and creative for supporting the UIN as word class University in 2020
- Establish a centralized data centers as a waiter in a work unit UIN - Facilitating the culture of learning and researching the new field of ICT utilization innovation.
- Utilization of internal resources in the field of ICT as part of shared knowledge and continuities of ICT in UIN
- Utilization of ICT in support of bureaucratic reform
4.1.2 Target Achievement 2010-2014 PUSKOM
• Development SIMPERTI UIN: Academic, Financial, Library, Logistics, Personnel, e-learning, websites, etc.
• Provide internet access in accordance with the needs of the stakeholders at UIN
• Establishment of Help desk 24 / 7 for the solution to the problem of ICT at UIN
• Increase ranking webometrik UIN
• Sign in the field of ICT in the award INAICA UIN and the like
4.1.3 Computer Science Faculty Profile
THE FACULTY OF SCIENCE AND TECHNOLOGY is a faculty with an Islamic orientation, with the goal of developing natural science and technology characterized by Islamic values. Graduates of this Faculty are expected to be able to combine natural science, and information technology with Islamic Science, which in turn will enable them to respond to the challenges of the twenty-first century. They will have a competitive edge in the globalization era as a result of their understanding of information technology.
Before The faculty a of since and Technology was founded since year 2000/2001 IAIN has established The Conversion Programs Study of Agribusiness, Informatics engineering In the beginning of academic year 2002/2003, the conversion programs of UIN era changed and became the faculty of Science and Technology.
4.1.3.1 International Undergraduate Program
between two universities grounds on the same vision of developing Muslim intellectual with International level competence. This program offer both single and double degrees option, where lectures are conducted in two different Universities, three years at The State Islamic University and one year at the KICT International Islamic University of Malaysia. This program conduct in English.
4.2 Current System Workflow
Next we will see how the process of the current system is, and the suggestion for the new system base on the fact documents that has been gathered by the writer from both students and employee of UIN University.
Picture 4.1 The current system for printing College Certificate.
2. The current system for printing surat Transkip Nilai
Picture 4.2 The current system for printing Transkip Nilai.
3. The current system for printing surat IPK and IPS
4.2.1 Problem Identification
Base on the flowcharts that have shown and the requirement gathering data that the writer has done, can separate the current system to twp part for identify the problems, which are
a. The long period of doing process for making each letters in UIN waste the students time and did not let them to focus on their study, the process of UIN should be easier an in time.
b. Lack of coordination between faculties and department make the process time more than usual.
c. As students answer in gathering data requirement, almost eighty percent of them have been tired for waiting the process, and asking for new technology for better and easier access.
d. Manual letters approval and giving Surat numbers disturbed the staff and employee of UIN.