1
THESIS REPORT
WEB SECURITY SERVICE APPLICATION BY USING WEB SERVICE AND RON SHAMIR ADLEMAN DIGITAL SIGNATURE WITH MESSAGE DIGEST 5 ALGORITHM (CASE STUDY: FINANCE INFORMATION SYSTEM RANCANGAN KERJA DAN ANGGARAN –
SATUAN KERJA PERANGKAT DAERAH KOTA MALANG)
By: Galih Nabihi 107091102733
INFORMATICS ENGINEERING STUDY PROGRAM FACULTY OF SCIENCE AND TECHNOLOGY
4
STATEMENT
I HEREBY DECLARE THAT THIS THESIS IS REALLY WORKS OF MINE THAT HAVENOT YET MADE AS THESIS SCIENTIFIC WORKS IN ANY UNIVERSITY OR INSTITUTION.
Jakarta, November 17, 2011
5 PREFACE
Alhamdulillah, all of praise and grateful given to Allah SWT who poured mercy, guidance, and helpful till arranging the Thesis Report with the title “Web Security Service Application by Using Web Service and Ron Shamir Adleman Digital Signature with Message Digest 5 Algorithm (Case Study: Finance Information System Rancangan Kerja dan Anggaran – Satuan Kerja Perangkat Daerah Kota Malang)” can be finished without any obstacle.
This thesis almost talk about Web Service and digital signature to avoid your data from being sabotage, this main purpose for this project is to develop the information system of RKA-SKPD Kota Malang in security side.
After one month of developing a service with digital signature using PHP and mysql, the researcher filling the increase of his knowledge, learning a lot of PHP coding strategy and techniques make me enjoy the software engineering field and for better future we need better basic knowledge.
In this moment, the writer would to thanks to all of structural person that covering this program
1. Mr. Dr. Syopiansyah Jaya Putra, M.Sis, Dean of Science Technology Faculty. 2. Mr. Yusuf Durrachman, M.Sc, MIT, The Head of Informatics Engineering 3. Mrs. Ria Hari Gusmita, M.Kom, Technical Coordinator of International Class
and My Supervisor help me a lot for the thesis.
6 I would like to say special thanks for:
1. Ayu Kharisma Maharani she give me motivation help me where I got problems.
2. My parent, my brothers, my sisters who always give support and never let me down.
3. Mrs. Mamita D who always help me in administration problem.
Jakarta, November 2011
7
LIST OF CONTENT
TITLE PAGE ………... i
EXAM VALIDATION ………..……… .... ii
PAGE VALIDATION ……… ... iii
STATEMENT... iv
ABSTRACT... v
PREFACE... ... vi - vii LIST OF CONTENT... viii - x LIST OF PICTURE... xi - xii LIST OF TABLE... xiii
GLOSARRY... xiv
CHAPTER I INTRODUCTION 1.1 Background……….………... 1
1.2 Problems Identification... 4
1.3 Problem Limitation... 4
1.4 Purpose of Research... 5
1.5 Benefit of Research... 5
1.5.1 Academic Parts... 5
8
1.5.3 Writer... 5
1.6 Research Methodology... 6
1.6.1 The Method of Collection Data... 6
1.6.2 Method of Development System... 6
1.7 Structure of Report... 7
CHAPTER II LITERATURE REVIEW 2.1 Basic Concept of System...……. 9
2.2 System Characteristic... 9 2.3 Web Service………... 10
2.4 Authentication…... 17
2.5 Cryptography ... 18
2.6 Encryption... 19
2.7 Element of Encryption………... 20
2.8 Digital Signature………... 21
2.9 RSA Algorithm………. 24
2.10 Research Methodology……… 25
2.10.1 Collection the Data... 25
2.10.2 Object Oriented Analysis And Design... 27
2.10.3 Basic principles of Object Oriented... 27
9
2.10.6 Development Cycle with OOAD... 30
2.10.7 Main Activity of OOAD... 30
2.11 Unified Modeling Language (UML)... 40
2.12 PHP………... 47
2.13 MYSQL... 48
2.14 XAMPP………... 48
2.15 Related Works………... 49
CHAPTER III RESEARCH METHOD 3.1.1. Collection data... 52
3.1.2. System Development Methodology... 53
CHAPTER IV ANALYSIS AND DESIGN SYSTEM 4.1 Problem Domain Analysis………... 56
4.1.1 Profile RKA-SKPD Kota Malang... 56
4.1.1.1 A Glance with Information System RKA-SKPD Kota Malang. 56 4.1.1.2 Scope Work RKA-SKPD Kota Malang……..……. 56
4.1.2 Analysis of the existing system (RKA-SKPD Kota Malang)...59
4.1.3 Analysis the proposed system (RKA-SKPD Kota Malang).... 60
4.2 Application Domain Analysis... 92
4.4 Architectural Design... 110
4.5. Component Design... 113
4.6. Programming... 133
10 CHAPTER V CONCLUSION
11
LIST OF PICTURE
Figure 2.3.1 Example of WSDL... 12
Figure 2.3.2 Example of xml... 14
Figure 2.7.1: Grouping of encryption along with examples... 20
Figure 2.8.1 Two Bob's Lock On... 21
Figure 2.8.2 Public Key Bob ... 21
Figure 2.8.3 Encrypt and Decrypt Message... 22
Figure 2.8.4 Encrypt digital signature in document... 22
Figure 2.8.5 example digital signature in document... 23
Figure 2.8.6 Digital Signature in document………... 23
Figure 2.8.7 Digital Signature cerficate in document……... 24
Figure 2.10.3.1 Example of Understanding Inheritance Kitchen Equipment and Furniture is inherited from House wares ……….……….. 28
Figure 2.10.6.1 Development Cycle OOA&D…………... 30
Figure 2.11.5.1 Example of rich picture………..……… 32
Figure 2.10.7.1 Activities in Problem Domain Analysis... 33
Figure 2.10.2 UML clasification diagram ... 42
Figure 3.1 frames of mind... 51
Figure 4.1.2.1 Rich Picture Existing system... 59
Figure 4.1.3.1 Rich Picture Proposed System... 60
Figure 4.1.3.2.1 XML Request Login Format………. 63
Figure 4.1.3.2.2 XML Response Login Format………. 64
12
Figure 4.1.3.2.4 XML Response input Format……… 69
Figure 4.1.3.2.5 XML Request view Format……..………... 72
Figure 4.1.3.2.6 XML Response view Format………..……. 73
Figure 4.1.3.2.7 XML Request Delete Format…….………..………. 74
Figure 4.1.3.2.8 XML Response Delete Format..……….…... 75
Figure 4.1.3.2.9 XML Request Edit Format……… 77
Figure 4.1.3.2.10 XML Request Edit Format………... 80
Figure 4.1.3.1 Class Diagram……….. 86
Figure 4.1.3.6.1 Statechart Diagram of Login Page………. 87
Figure 4.1.3.6.4 Statechart Diagram Management Xml……. ... 88
Figure 4.1.3.6.6 Statechart Diagram View RKA SKPD... ... 89
Figure 4.1.3.6.7 Statechart Diagram Input RKA SKPD... 90
Figure 4.1.3.6.8 Statechart Diagram Edit RKA SKPD... 91
Figure 4.1Use Case Model Diagram………..... 93
Figure 4.2.2.1 Sequence Diagram Use Case Login... 101
Figure 4.2.2.2 Sequence Diagram Use Case Management XML... 102
Figure 4.2.2.3 Sequence Diagram Use Case view RKA... 102
Figure 4.2.2.4 Sequence Diagram Use Case input RKA……….. 103
Figure 4.2.2.5 Sequence Diagram Use Case edit RKA ……….. 104
Figure 4.2.2.6 Sequence Diagram Use Case Logout………. 104
Figure 4.3.2.1 Window Diagram Login Form……….………. 106
Figure 4.3.2.2 Window Diagram Home Form……… 107
13
Figure 4.3.2.4 Window Diagram management RKA……….. 108
Figure 4.3.2.5 Window Diagram input management RKA………...…. 109
Figure 4.3.2.6Window Diagram management edit RKA………. 110
Figure 4.32 Deployment Diagram web secure system………... 113
Figure4.33 Component Diagram web secure system………. 114
Figure 4.4.1.1 Home Page……….……….. 115
Figure 4.4.1.2 Management XML Page………. 116
Figure 4.4.1.3 Management RKA View Page………... 116
Figure 4.4.1.3 Management RKA Input Page………... 117
Figure 4.4.2.1 Simulation Input Page……… 117
Figure 4.4.3.1 Generate Key Pair……….. 121
Figure 4.4.3.2 Generate Key Pair Password……….. 122
Figure 4.4.3.3 Generate Key Pair File……… 122
Figure 4.4.3.4 Entering Data for Key Pair………. 122
Figure 4.4.3.5 Entering Valid Day Key Pair………. 122
Figure 4.4.3.5 Entering Valid Day Key Pair………. 123
Figure 4.4.3.6 Creating Cer File……… 123
14
LIST OF TABLE
Table 2.15 Summary of Related Work Chart……….……….... 51
Table 2.11.1 UML Diagram type……….. 41
Table 4.1.3.2.1 Login request data description table…………... 64
Table 4.1.3.2.2 Login response data description table... 66
Table 4.1.3.2.3 input request data description table……... 70
Table 4.1.3.2.4 input response data description table………... 73
Table 4.1.3.2.5 view request data description table …... 75
Table 4.1.3.2.6 view response data description table……... 76
Table 4.1.3.2.7 delete request data description table ……... 78
Table 4.1.3.2.8 delete response data description table……... 79
Table 4.1.3.2.9 edit request data description table ……... 83
Table Table 4.1.3.2.10 edit response data description table……... 86
Table 4.1.3.2.1 Entity Class Candidates on the Web Secure system... 88
Table 4.2.1.1 Actor Identification………... 95
Table 4.2.1.2 Use Case identification…………... 95
Table 4.2.1.3 Narratives Use Case Login…………... 97
Table 4.2.1.4 Narratives Use Case Management RKA………... 97
Table 4.2.1.5 Narratives Use Case Management XML... 98
Table 4.2.1.6 Narratives Use Case Logout……... 100
Table 4.2.3 Function List in web secure system... 105
Table 4.2.1 Criteria proposed system…………... 111
15 Define of General Term
OOAD : Object Oriented Analysis and Design
UML : Unified Modeling Language
User : End Users / User Management
Black box : A new type of software testing based on the inputs, outputs user.
SQL : Database for storing data
HTML : HyperText Markup Language
RKA – SKPD : Rencana Kerja Dan Anggaran – Satuan Kerja Perangkat Daerah
SYMBOL DEFINITION
: Terminator
: Process
: Action / include
16 CHAPTER I INTRODUCTION
1.1.Background
Information technology developed very fast, now it gives a lot of advantages for the efficiency and affectivity for the user. The Development information system itself developed with their support technology.
For example in the system of weather forecast application, there are a lot of application that will take the data and use from main server, those application could have many different flat form, the different could be in the language , operating system and devices. This condition of course give problem to doing synchronize data in every system.
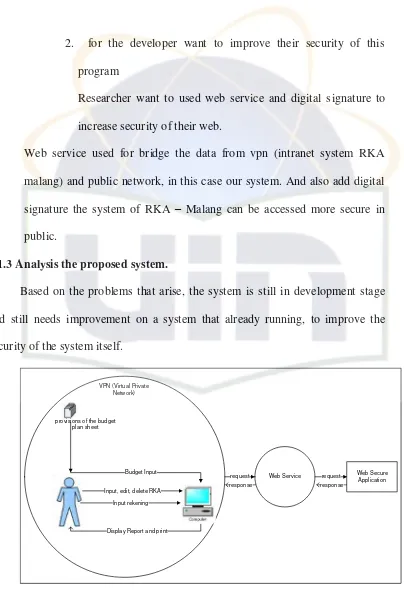
To solve that problem, so that web service was used. Web service allow the different devices, operating system and different application to exchange data and information with else (Lucky, 2008)
Another problem is when someone needs to increase protection for their data from someone who want to stole or crash their data, they need to think some method to improve defense of their web.
17
Second DES (Data Encryption Standard) is algorithm that used block of key pair with a block size of 64-bit and 56-bit key size. Previously, there is some research done with DES which is used in archives system in hospital, this algorithm is quite fast to process but this algorithm has been determined no longer safe in recent years. The main cause of the problem is the key size is very short (56-bit), and if it is compare with technology in this era it has possibility to break it.
Third is AES (Advanced Encryption Standard) this algorithm is, AES that related with key size become block size of 128 bits and a key size of 128, 192, or 256 bits. Literally this algorithm already fixed the weakness of DES which related with key size that has only 56 bits max. This algorithm used in research to become algorithm that used in digital signature to verify card of identity republic of Indonesia. But AES is the one group of symmetric algorithm which is only has one key of encryption that means if it still compare with RSA which have two key encryption AES have higher possibility than RSA to be cracked. So that way in this research writer used RSA AND MD5 algorithm to be implemented in system.
RSA was found by Ron (R)ivert, (S)hamir and Leonard (A)dleman so this algorithm called RSA. The security of RSA algorithm exist in the difficulty of factoring all of big numbers become prime factor, as long the factor of prime number still not found for factorized, the security of RSA algorithm will secure. Bank is one company that used this method and also the consultant company
18
the researcher decided to used RSA and MD5 to become digital signature algorithm in this research because RSA is the better algorithm instead of the other algorithm that researcher already explained before and MD5 to improve the security of the RSA algorithm.
As we know internet become the biggest place to do criminal. In this era, it is possible that someone suddenly access to the system and crash everything. The same condition with the finance information system of RKA – SKPD Kota Malang, there a lot of people who interact or used the system. So they need a new system that can authenticate the originality of the data especially finance data in finance division.
19 1.2 PROBLEM IDENTIFICATION
In this research the problem identification are:
1. How to create a service (in this case web service) to interface (see, edit and verify) the data in private network ( in this case skpd – malang information system ) which used intranet for their security so that only people that involved in their institution can access the databases. 2. How to implemented digital signature inside the web service instead
to verify the data from manipulation data.
3. How to Create and use two key pair to lock and open the encryption, private (to lock the data put in server side) and public key (to decrypt the data put in client) and also the opposite. This key pair used to take data from intranet of SKPD malang.
1.3 PROBLEM LIMITATION
In this research Problem limitations are:
1. Digital signature only focus on MD5 and RSA algorithm to encrypt and produce hashing code in system
2. RSA algorithm used certified as public key (.cer) in this case used certified X509 and PKCS12 to produce public key.
20 1.4 PURPOSE OF RESEARCH
The purpose of this project is to create the web security service by using web service and RSA digital signature with MD5 algorithm.
1.5 BENEFIT OF RESEARCH 1. ACCADEMIC PARTS
- To help another researcher as reference to implement and to do the same research with another method in security to protect data.
2. Finance archives information system RKA-SKPD (Rencana Kerja Dan Anggaran - Satuan Kerja Perangkat Daerah) malang city
- For the object itself will help to minimize the risk of system hacked.
- Establish cooperation between the Agencies and work education for writer, so that could be used as reference to prepare workforce of more advanced and competitive.
3. THE WRITER
- For writer will help to give knowledge in digital signature, web service and cryptography.
- To meet one of the requirements of graduation degree (S1), Informatics Engineering, Faculty of Science and Technology State Islamic University Syarif Hidayatullah Jakarta.
21 1.6 RESEARCH METODOLOGY
Writer research methodology is divided into two steps, first gathering the data and develops system.
1.6.1 Gathering the data
For gathering the data the writer use 3 methods as listed below: 1. Observation
Observation (observe) is a technique or approach to obtain primary data by observing directly the object data In this Observation one researcher directly involved with object of research (finance archives information system skpd malang).
1. Interview
Interview is two way communications to get data from respondents. Do some interview with stakeholder that involved in system which can give the needed data.
3. Study Literature
In this method, the authors collected data and information by searching and reading reference books and internet sites that can be used as a reference the discussion in this issue (Gulo, 2002).
1.6.2 Method of Development System
22
UseCase Diagram, Rich Diagram, Class Diagram, Sequence Diagram and
Window Diagram. OOAD consists of several main stages, there are: 1. Problem Domain Analysis.
2. Application Domain Analysis. 3. Architecture Design.
4. Component Design. 5. Programming. 6. Quality Assurance.
1.7 STRUCTURE OF REPORT
Systematic of writing is structured on 5 (five) chapters, organized as follows: CHAPTER I: INTRODUCTION
This chapter contains background, problem identification, problem limitation, advantages of research, research methodology and systematic of research.
CHAPTER II: LITERATURE REVIEW
This chapter contains a whole theory and concept of this research such as web service, digital signature, cryptography and so on.
CHAPTER III: RESEARCH METOHOLOGY
This chapter contains data for analysis and steps to create the application. CHAPTER IV: RESULT AND EXPLANATION
23
CHAPTER II
LITERATURE REVIEW 2.1 Definition System
The system is an interconnected group of components and works together to achieve a common goal by accepting inputs and producing outputs in an orderly process of transformation (O'Brien, 2005).
2.2 System Characteristics
A good system has the following characteristics (Mcleod and Schell, 2001): 1. Flexible
Although an effective system is a system that structured and well organized, but should be flexible enough to be more easily adapted to the circumstances that change frequently.
2. Easily Adapted
A good system should also be quickly and easily adapted to new conditions without changing the old system and interfere with its primary function.
3. Systematic
In order to function effectively, the existing system should be logical and systematic, that is, the system created will not complicate the work activities that already exist.
4. Functional
24
A system should be simpler so it is more easily understood and implemented.
6. Optimal resource utilization
Well-designed system will make use of the resources of the organization can be optimized utilization.
2.3 Web Service
Web service is a method of communication between two electronic devices over a network.
The W3C defines a "Web service" as "a software system designed to support interoperable machine-to-machine interaction over a network. It has an interface described in a machine – process able format (specifically Web Services Description Language WSDL). Other systems interact with the Web service in a manner prescribed by its description using SOAP messages, typically conveyed using HTTP with an XML serialization in conjunction with other Web-related standards[6].
The Web Services Description Language (WSDL, pronounced 'wiz-del') is an XML-based language that provides a model for describing Web services. The WSDL defines services as collections of network endpoints, or ports. The WSDL specification provides an XML format for documents for this purpose. The abstract definitions of ports and messages are separated from their concrete use or instance, allowing the reuse of these definitions [6].
25
the data being exchanged, and port types are abstract collections of supported operations. The concrete protocol and data format specifications for a particular port type constitutes a reusable binding, where the operations and messages are then bound to a concrete network protocol and message format. In this way, WSDL describes the public interface to the Web service.
Figure 2.3.1 Example of WSDL
Service/Service: The service can be thought of as a container for a set of system functions that have been exposed to the Web-based protocols.
26
Binding/Binding: The binding specifies the interface as well as defining the SOAP binding style (RPC/Document) and transport (SOAP Protocol). The binding section also defines the operations.
PortType/Interface: The <portType> element, renamed to <interface> in WSDL 2.0, defines a Web service, the operations that can be performed, and the messages that are used to perform the operation.
Operation/Operation: Each operation can be compared to a method or function call in a traditional programming language. Here the SOAP actions are defined and the way the message is encoded, for example, "literal."
Message/N.A.: Typically, a message corresponds to an operation. The message contains the information needed to perform the operation. Each message consists of one or more logical parts. Each part is associated with a message-typing attribute. The message name attribute provides a unique name among all messages. The part name attribute provides a unique name among all the parts of the enclosing message. Parts are a description of the logical content of a message. In RPC binding, a binding may reference the name of a part in order to specify binding-specific information about the part. A part may represent a parameter in the message; the bindings define the actual meaning of the part. Messages were removed in WSDL 2.0, in which XML schema types for defining bodies of inputs, outputs and faults are referred to simply and directly.
27
XML's design goals emphasize simplicity, generality, and usability over the Internet. It is a textual data format with strong support via Unicode for the languages of the world. Although the design of XML focuses on documents, it is widely used for the representation of arbitrary data structures, for example in web services.
Figure 2.3.2 Example of xml
The material in this section is based on the XML Specification. This is not an exhaustive list of all the constructs which appear in XML; it provides an introduction to the key constructs most often encountered in day-to-day use.
(Unicode) Character
By definition, an XML document is a string of characters. Almost every legal Unicode character may appear in an XML document.
Processor and Application
28
must do and not do, but the application is outside its scope. The processor (as the specification calls it) is often referred to colloquially as an XML parser [6].
Markup and Content
The characters which make up an XML document are divided into markup and content. Markup and content may be distinguished by the application of simple syntactic rules. All strings which constitute markup either begin with the character "<" and end with a ">", or begin with the character "&" and end with a ";". Strings of characters which are not markup are content.
Tag
A markup construct that begins with "<" and ends with ">. Tags come in three flavors: start-tags, for example <section>, end-tags, for example </section>, and empty-element tags, for example <line-break />.
Element
Element is a logical component of a document which either begins with a start-tag and ends with a matching end-tag, or consists only of an empty-element tag. The characters between the start- and end-tags, if any, are the element's content, and may contain markup, including other elements, which are called child elements. An example of an element is <Greeting>Hello, world.</Greeting> (see hello world). Another is <line-break />.
Attribute
29
example would be <step number="3">Connect A to B.</step> where the name of the attribute is "number" and the value is "3".
SOAP, originally defined as Simple Object Access Protocol, is a protocol specification for exchanging structured information in the implementation of Web Services in computer networks. It relies on Extensible Markup Language (XML) for its message format, and usually relies on other Application Layer protocols, most notably Remote Procedure Call (RPC) and Hypertext Transfer Protocol (HTTP), for message negotiation and transmission. SOAP can form the foundation layer of a web services protocol stack, providing a basic messaging framework upon which web services can be built. This XML based protocol consists of three parts: an envelope, which defines what is in the message and how to process it, a set of encoding rules for expressing instances of application-defined data types, and a convention for representing procedure calls and responses [6].
2.4 Authentication
Authentication derived from the Greek, authentes = author, namely an action to set something or someone is genuine. Proving originality an object is to establish the place of origin, while to prove the authenticity of a person is with their identity [4].
Authentication in humans depends on several factors: A. Something the user is
30 B. Something the user has
An example is the ID card, security token, software token and cell phone.
C. Something the user know
Examples include passwords, PINs etc.
The first problem, prove the authenticity of documents, can be done with watermarking and digital signature technology. Watermarking can also be used to protect intellectual property, namely by marking the documents or the work of the maker's signature.
The second problem is access control. A computer system is expected to can be used only by that given the right, so that the computer system should be able to detect and reject a user who does not have rights.
Sample access control which Authentication include : ² Using the internet banking system
² controlling the remote computer with internet 2.5 Cryptography
31
related with aspects of information security such as data confidentiality, validity of data, integrity bag data, and authentication data. [4]
There are four fundamental goals of science cryptography which is the security aspect:
A. Confidentiality
It is a service used to keep the contents of the information from anyone except the one with the authority or the secret key to unlock or peel the information that has been encoded.
B. Data Integrity
Associated with the maintenance of the data changes illegally, for maintaining data integrity, the system must have the ability to detect manipulation of data by parties who are not eligible, including insertion,
removal, and other data into the data. [4] C. Authentication
Associated with the recognition, either in whole system as well as the information itself, the two parties must communicate with each other introduced themselves. Information sent through the canal should authenticated authenticity, data content, delivery time, and others.
D. Non- Repudiation
32
The process of randomization or the process being undertaken to secure a message (called plaintext) into a hidden message (called a cipher text) is encrypted (encryption). According to ISO 7498-2, terminology opposite process, to convert ciphertext into plaintext, called de descriptions (decryption). According to ISO 7498-2, more precise terminology for this process is to decipher.
2.6 Encryption
Encryption used to compare the data or information so they cannot read by people
who don’t have permission. With data encryption your data will be encrypted with
a key. For opened the chipper text (decrypt) used another key. The key can be the same like key that used for encryption or different. [4]
Mathematically, the process for encryption (E) can be written as: E (M) = C
Where M is the plaintext (message) and C is the ciphertext (Encrypted message). The process of decryption (D) can be written as:
D(C) = M 2.7 Elements of Encryption
33
Figure 2.7.1: Grouping of encryption along with examples 2.8 Digital Signature
What is digital signature?
Here is an overview of the digital signature. Bob has been given 2 keys, one called the public key and one called the private key (David Youd, 1996).
34
Figure 2.8.2 Public Key Bob
[image:34.595.114.522.79.567.2]Bob's public key available to everyone who needs it the private key saved for himself, where that key used for lock of the data. Susan can encrypt a message using the public key of Bob and Bob use, his private key to decrypt the message (Figure 2.2). Anyone from bob co-worker may have access to the massage that susan encrypt before, but without bob public key the data is not valuable(David Youd, 1996).
Figure 2.8.3 Encrypt and decrypt message
35
To sign a document, Bob's software will crunch down the data into just a few lines by a process called "hashing". These few lines are called a message digest. (It is not possible to change a message digest back into the original data from which it was created.) (David Youd , 1996).
Figure 2.8.4 Encrypt digital signature in document
So Bob's software then encrypts the message digest with his private key. The result is the digital signature.
Figure 2.8.5 example digital signature in document
36
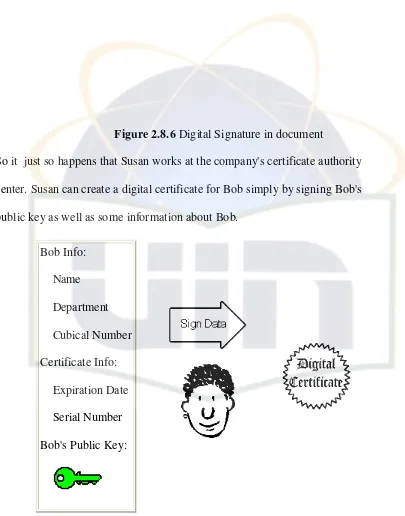
Figure 2.8.6 Digital Signature in document
So it just so happens that Susan works at the company's certificate authority center. Susan can create a digital certificate for Bob simply by signing Bob's public key as well as some information about Bob.
Bob Info: Name Department Cubical Number Certificate Info: Expiration Date Serial Number Bob's Public Key:
Figure 2.8.7 Digital Signature cerficate in document
2.9 Ron Shamir Adleman (RSA) Algorithms
[image:36.595.118.523.69.585.2]37
Rivest, Adi Shamir and Leonard Adleman, who first publicly described it in 1978(Menezes, 1998).
Key Generation
Finding the large primes p and q is usually done by testing random numbers of the right size with probabilistic primality tests which quickly eliminate virtually all non-primes.
Numbers p and q should not be 'too close', lest the Fermat factorization for n be successful, if p − q, for instance is less than 2n1/4 (which for even small 1024-bit values of n is 3×1077) solving for p and q is trivial. Furthermore, if either p − 1 or q − 1 has only small prime factors, n can be factored quickly by Pollard's p − 1 algorithm, and these values of p or q should therefore be discarded as well.
It is important that the private key d be large enough. Michael J. Wiener showed that if p is between q and 2q (which is quite typical) andd < n1/4/3, then d can be computed efficiently from n and e(Menezes, 1998).
Adaptive chosen ciphertext attacks
38
as Optimal Asymmetric Encryption Padding, and RSA Laboratories has released new versions of PKCS #1 that are not vulnerable to these attacks(Menezes, 1998). Magnitude scale used in the RSA algorithm:
1. p dan q Prime Number (Secret) 2. r = p * q (public)
3. m = (p – 1)(q – 1) (Secret) 4. PK (encryption key) (public) 5. SK (descryption key) (Secret) 6. X (plainteks) (Secret)
7. Y (cipherteks) (public) Example:
p = 3 looking for e
dan q = 11 (both prime). gcd(e, 20)=1
n= p ⋅ q = 33 e= 3
m = (p – 1)(q – 1) = 20
count d public key : e, n privte key : d, n
e*d = 1 mod (m) Private key : (7, 33 )
3 * d = 1 mod 20 Public key : (3, 33 )
3 * d mod 20 = 1 = 7
X (text) = 2
39 2.10 Message Digest 5 (MD5)
The MD5 Message-Digest Algorithm is a widely used cryptographic hash function that produces a 128-bit (16-byte) hash value. MD5 was designed by Ron Rivest in 1991 to replace an earlier hash function, MD4. In 1996, a flaw was found with the design of MD5. While it was not a clearly fatal weakness, cryptographers began recommending the use of other algorithms, such as SHA-1 (which has since been found also to be vulnerable). In 2004, more serious flaws were discovered, making further use of the algorithm for security purposes questionable; specifically, a group of researchers described how to create a pair of files that share the same MD5 checksum. Further advances were made in breaking MD5 in 2005, 2006, and 2007. In an attack on MD5 published in December 2008, a group of researchers used this technique to fake SSL certificate validity (Thomas A, 1992).
ALGORITHM
40
filled up with a 64-bit little endian integer representing the length of the original message, in bits.
The main MD5 algorithm operates on a 128-bit state, divided into four 32-bit words, denoted A, B, C and D. These are initialized to certain fixed constants. The main algorithm then operates on each 512-bit message block in turn, each block modifying the state. The processing of a message block consists of four similar stages, termed rounds; each round is composed of 16 similar operations based on a non-linear function F, modular addition, and left rotation. Figure 1 illustrates one operation within a round(Thomas A, 1992).
MD5 HASHES
The 128-bit (16-byte) MD5 hashes (also termed message digests) are typically represented as a sequence of 32 hexadecimal digits. The following demonstrates a 43-byte ASCII input and the corresponding MD5 hash:
Example:
MD5 ("The quick brown fox jumps over the lazy dog.") = e4d909c290d0fb1ca068ffaddf22cbd0
MD5 ("")
= d41d8cd98f00b204e9800998ecf8427e
41 2.11.1 Gathering The data
1. Observation
Observations are the fact-gathering technique in which systems analysts participating or watching someone who is doing an activity to learn the system. Observation is one of many effective data collection techniques for studying a system (Whitten et al, 2004).
bservation has its advantages and disadvantages, the following advantages and disadvantages of observation according to (Whitten et al, 2004):
1. Advantages of observation:
- Data are collected based on observations can be very reliable. Sometimes observation done by verified validity of the data which can directly see individually.
- Analysis can see what actually happened. The Complex tasks sometimes difficult to explain with words. Through the observation, system analyst can identify tasks that are missing or not described accurately by the other fact-finding techniques. Analysts can also find data describing the physical environment of a task.
- Observations are relatively inexpensive compared to other fact-finding techniques. Another fact-fact-finding technique usually requires a special time of labor and a lot of money.
42
- People usually feel uncomfortable when being watched (observed) they may apply differently when observed.
2. Interview
Is a two-way communication to get data from respondents (Jogiyanto, 2008). 1. Advantages of interview (Jogiyanto, 2008):
- Good corporate from respondent can be happened. - Special visual aid or other assessment tool can be done. - Respondents who had no knowledge can be identified. - The interviewer can filter the respondents as required. 2. Disadvantages of interview (Jogiyanto, 2008):
- Requires trained interviewer. - Long data collection time.
- Some of respondent did not want to talk with strangers. 3. Study Literature
Is a written record of events or occasions in the past and journals in a particular scientific field; including important documents is a reference for researchers in understanding the object of his research. Even the literature, relevant literature is also included in documents that support the research. All documents relating to the research in question should be noted as a source of information (Gulo, 2002).
2.11.2 Object Oriented Concept
43
conditions stated in the attribute, while the behavior of an object defines how an object to act and react. Behavior of an object expressed in the operation.
2.11.3 Basic principles of Object Oriented
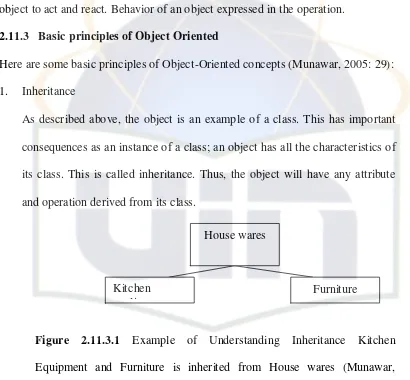
Here are some basic principles of Object-Oriented concepts (Munawar, 2005: 29): 1. Inheritance
As described above, the object is an example of a class. This has important consequences as an instance of a class; an object has all the characteristics of its class. This is called inheritance. Thus, the object will have any attribute and operation derived from its class.
Figure 2.11.3.1 Example of Understanding Inheritance Kitchen Equipment and Furniture is inherited from House wares (Munawar, 2005:29).
2. Encapsulation
The term encapsulation is often used interchangeably with information hiding. Not all agree on the distinctions between the two though; one may think of information hiding as being the principle and encapsulation being the technique. A software module
House wares
Furniture Kitchen
[image:43.595.114.524.139.519.2]44
hides information by encapsulating the information into a module or other construct which presents an interface.
3. Message Sending
In object oriented systems, objects are mutually communicated each other by sending messages. An object sends a message to another object to perform an operation and the object that receive will give the response to run the operation.
4. Association
Association is the relationship between objects that need each other. This relationship can be one-way or multiple ways.
5. Aggregation
Aggregation is a special form of association that describes all parts of an object is part of another object.
2.10.4 The Concept of Object Oriented Analysis and Design (OOAD)
Object Oriented Analysis and Design or OOA&D is a collection of general guidelines for carrying out analysis and design. It must therefore be tailored to your organization and project. To make our method more usable, we designed it so that adaptations, improvements, and part substitutions would be easy to implement.
OOA&D reflects four central perspectives on a system and its context: the
system’s information contents, how the system will be used, the system as a
45
main activities: problem-domain analysis, application-domain analysis, architectural design, and component design, respectively. Each activity leads to specific results, which are subsequently included in the analysis and design documentation (Mathiassen, et.al. 2000:12).
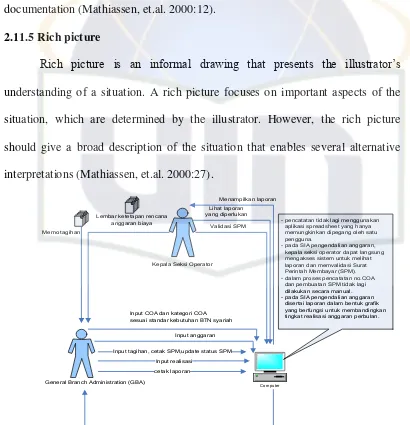
2.11.5 Rich picture
Rich picture is an informal drawing that presents the illustrator’s
understanding of a situation. A rich picture focuses on important aspects of the situation, which are determined by the illustrator. However, the rich picture should give a broad description of the situation that enables several alternative interpretations (Mathiassen, et.al. 2000:27).
Kepala Seksi Operator
General Branch Administration (GBA) Lembar ketetapan rencana
anggaran biaya Memo tagihan
Computer
Input anggaran
Input tagihan, cetak SPM,update status SPM
Menampilkan SPM dan laporan siap dicetak Lihat laporan yang diperlukan
Input realisasi Input COA dan kategori COA sesuai standar kebutuhan BTN syariah
Menampilkan laporan
- pencatatan tidak lagi menggunakan aplikasi spreadsheet yang hanya memungkinkan dipegang oleh satu pengguna.
- pada SIA pengendalian anggaran, kepala seksi operator dapat langsung mengakses sistem untuk melihat laporan dan memvalidasi Surat Perintah Membayar (SPM). - dalam proses pencatatan no.COA dan pembuatan SPM tidak lagi dilakukan secara manual. - pada SIA pengendalian anggaran disertai laporan dalam bentuk grafik yang berfungsi untuk membandingkan tingkat realisasi anggaran perbulan.
cetak laporan
Validasi SPM
Figure 2.11.5.1 Example of rich picture 2.11.6 Development Cycle with OOAD
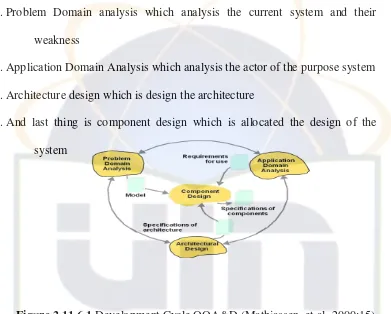
[image:45.595.109.519.194.619.2]46
1. Problem Domain analysis which analysis the current system and their weakness
2. Application Domain Analysis which analysis the actor of the purpose system 3. Architecture design which is design the architecture
4. And last thing is component design which is allocated the design of the system
[image:46.595.133.524.108.422.2]
Figure 2.11.6.1 Development Cycle OOA&D (Mathiassen, et.al, 2000:15) 2.11.7 Main Activity of OOAD
There are four main activities that are used in Unified Software Deployment methods for OOAD (Object Oriented Analysis and Design) and 2 activity Mathiassen implementation based on the usual approach is also called A Traditional Top-Down Approach Based on OOAD namely (Mathiassen, 2000): 1. Problem Domain Analysis
2. Application Domain Analysis 3. Architecture Design
47 2. Quality Assurance
2.10.7.1 Problem Domain Analysis
Problem domain analysis is part of a context in which administered, monitored or controlled by a system. In this stage system is designed according to the information needs from users, this step determines the overall outcome of the analysis and design activities.
The problem domain consists of: 1. Classes
Class is a description of a collection of objects that have a behavior pattern and structure of the same attributes. Abstraction, classification, and selection is a major task in classroom activities. Class is the main objective in defining and limiting the problem domain. Class consists of class names, attributes and operations. The name of the class is defines the class itself.
2. Structure
Structure activity focused on the relationship between classless and objects.
3. Events
Event is an instantaneous event that involves one or more objects. Event table make easier to analyze the system so that no event is overlooked in creating a class diagram.
48
Behavior pattern is a description of the event trace is possible for all objects in the class. Event trace is a sequence of events of a particular object.
State diagrams describe the general behavior of all objects of a certain class, which consists of the parts and the transitions among them and may also explain the usecase. Statechart diagrams describe the transition and changes the state of an object on the system as a result of stimulation received. Notation on the behavioral pattern consists of three kinds, namely, sequence selection and iteration. Sequence is the events that occurred only once. Selection is something that comes out of events occurring. Iteration is the events that occur zero or more.
Figure 2.11.7.1 Problem Domain Analysis (Mathiassen, 2000) 2.11.7.2 Application Domain Analysis
This stage focuses on how the system will be used by the user. This stage and earlier stage can be started in turn, depends on the condition of the user. Application Domain is the organization that manages, monitor or control the problem domain. Application Domain consists of:
49 a. Usecase
Usage describes how the system interacts with people and systems in context. Usage consists of sequence diagrams and use case diagrams. Use case diagram is a diagram illustrating the interaction between system and actors within the application domain. Actor is an abstraction of the user or other systems that interact with the target system. Actor is abstraction of people and other systems that are active on the system function. A use case is abstraction of interaction with the target system. Use cases can be activated by the actor or the target system. Complete use case that determines all uses of the target system in the application domain.
b. Sequence
50
the operation carried out is referred to as activation. Activation period in the period, including some period of time during the operation waiting for a response from the other operations that are requested will begin immediately.
2. Function
Function is a facility to create a useful model for the actor. Function consists of complete function list. There are several types of functions include:
1. Update Function is activated by an event from the problem domain and the result is a change in the model state.
2. Signal Function is activated by a change in the model state and the result of a reaction on the context. This reaction may be a display of the actor in the model domain.
3. Read Function is activated by a need for information on a work assignment at the actors and the result display system associated with the model.
4. Compute function is activated by a need for information on a work assignment on the actor and consists of a calculation involving information provided by the actor or model. The result is a display of calculation results.
3. Interface
51
elements of a complete user interface, windows are selected diagrams and diagram navigation. System interface is a class diagram for the external devices and protocols for interaction with other systems. Navigation charts are all the windows of the user interface and dynamic relationship.
2.11.7.3 Architectural Design
In this step architectural relationship between the client and server are sufficient for the system to run correctly. The design of this stage determines how the structure of the physical system will be created and how the distribution of the information system on the physical design. The resulting report is a Deployment Diagram.
According to (Mathiassen, 2000), Activities in architectural design consist of: a. Criteria
Criterion Measure of
Usable
Secure
Efficient Correct Reliable
The system’s adaptability to the
organizational, work-relative, and technical contexts.
The precautions against unauthorized access to data and facilities.
The economical exploitation of the
technical platform’s facilities.
The fulfillment of requirements.
52 Maintainable
Testable
Flexible
Comprehensible
Reusable
Portable
Interoperable
The cost of locating and fixing system defects.
The cost of locating and fixing system defects.
The cost of modifying the deployed system.
The effort needed to obtain a coherent understanding of the system.
The potential for using system parts in other related systems.
The cost of moving the system to another technical platform.
The cost of coupling the system to other systems.
b. Components
Good component architecture makes a system easier to understand, organizing the design work and reflecting the stability of the system’s
53
UML’s diagram contains packages denoting components, and
dependencies between packages denoting component connection. c. Process
The process architecture brings us closer to the system’s physical level.
We focus on distribution and execution, and work with processes and objects as opposed to components and classes. We also deal with the physical devices that the system will be executed on and consider whether we need to coordinate shared resources.
2.11.7.4 Component Design
The starting point for component design is the architectural specification and the system requirements. The result of this activity is specification of the connected components. The component design builds on two general principles. The first is respect the component architecture; the second is adapting component designs to the technical possibilities.
2.11.7.5 Programming
At this stage the activities undertaken already entered the stage of the design program to design a system that has been in its design.
2.11.7.6 Quality Assurance
At this stage there are two activities involved (Mathiassen, 2000): 1. System testing
54
not only to obtain the correct program, but also ensure that the program is free of errors for all conditions.
2. Software release
At this stage of its activities is to apply the system to the end user. 2.11 Unified Modeling Language (UML)
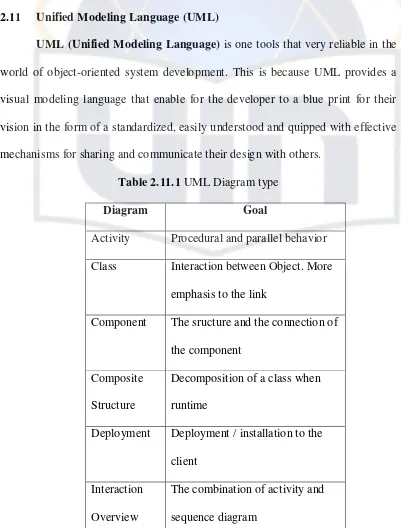
[image:54.595.113.514.214.742.2]UML (Unified Modeling Language) is one tools that very reliable in the world of object-oriented system development. This is because UML provides a visual modeling language that enable for the developer to a blue print for their vision in the form of a standardized, easily understood and quipped with effective mechanisms for sharing and communicate their design with others.
Table 2.11.1 UML Diagram type
Diagram Goal
Activity Procedural and parallel behavior Class Interaction between Object. More
emphasis to the link
Component The sructure and the connection of the component
Composite Structure
Decomposition of a class when runtime
Deployment Deployment / installation to the client
Interaction Overview
55
Object Example of instance configuration Package Hierarchical structure when
compiling
Sequence Interaction between Object. More emphasis on the order
State Machine
How does event change an object
Timing Intercation between object. More emphasis on time
Use case How user interact with the system
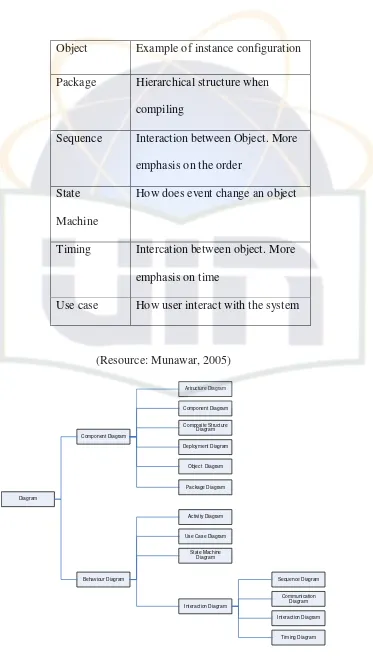
(Resource: Munawar, 2005)
Component Diagram Artructure Diagram Component Diagram Composite Structure Diagram Deployment Diagram
Object Diagram
Package Diagram
Diagram
Behaviour Diagram
Activity Diagram
Use Case Diagram
[image:55.595.148.521.73.734.2]State Machine Diagram Interaction Diagram Sequence Diagram Communication Diagram Interaction Diagram Timing Diagram
56
(Resource: Munawar, 2005) 2.11.1 Use Case Diagram
Usecase diagram is a description of a system from a user perspective. Use cases work by describing a typical interactionbetween the user of a system with its own system through a story of how a system is used. Sequence of steps that describe theuser with a system called a scenario. Each scenario describes the sequence of events. Each sequence is initialized by the people, the other system, hardware or time sequence. Three components in theuse case diagram are actors, associations and use-case line.
57
Stereotype is a special model is limited to certain conditions. To realize the stereotypes used the symbol "<<" diawalnya and closed under the symbol ">>" an end. <<extend>> Used to show that one use case is a functional addition of another use case if certain conditions or requirements are met. While <<include>> used to describe the use case that was entirely the functionality of another use case. Usually <<include>> is used to prevent copying of a use case because it is often used.
Each use case should be described in a document called the document flow of event. This document defines what should be done by the system when the actors to enable the use case. The structure of the document use case can very, but generally this description should at least contain ( Munawar , 2005);
- Brief Description - Actor who involved
- Precondition the importance thing for the use case to start - Detail description of the flow event that include:
o Main flow of the event specified can be divided into:
- Sub Flow
o Alternative Flow
- Post condition which describes the state of the system after the use case ends. 2.11.2 Class Diagram
58
the class is a description of the structure of an object with properties, behavior and the same relation. Besides class diagrams can provided a global view of a system. This is reflected in the classes that have relationship with one another.
2.11.3 Activity Diagram
Activity diagrams model the workflow a business process and sequence of activities in a process. This diagram is very similar to the flow chart because we can model the logic procedures, business processes and workflow. The main deference is the flow chart created to describe the workflow of the system, while the activity diagram is made to describe the activity of the actor. As already discussed in the first part of this case study, by modeling the activity diagram in advance would be very helpful in understanding the overall business process. Activity diagram are also very useful in describing the behavior of parallel or explain how the behavior of the various use cases interact.
2.11.4 Sequence Diagram
Sequence diagrams are used to describe the behavior in a scenario. This diagram shows a number of object instances and message (the message) that is placed between these objects in a use case. The main component sequence diagrams consist of objects specified with rectangular boxes called. Message is represented by lines with arrows and the time indicated by vertical progress. 2.11 .5 Collaboration Diagram
59
emphasize the sequence of the event. In the collaboration diagram there are several object links and message. Collaboration diagrams are used as a tool to describe interaction that reveals the decision regarding the behavior of the system 2.11.6 Statechart Diagram
Statechart diagrams show the possible state-state of an object, an event that can detect and respond to these events. In general, the detection of an event can cause an object moves from one state to another state. This is called a transition.
2.11.7 Component Diagram
Component diagrams illustrate the allocation of all classes and object into components in the physical design of the system software. This diagram shows the arrangement and dependencies between software and components, such as source, code, binary code, and executable components. We can create one or more component diagrams to describe or explain the component and the package contents of the package component.
2.11.8 Deployment Diagram
60
manifestation of the software, usually files. These files are usually executable (such as EXE file , binner , JAR , assembly or script), or data files, configuration files , HTML document and others.
2.12 PHP
PHP stands for Hypertext Preprocessor is server side scripting programming language, programming language used by the web server to generate HTML documents on-the-fly. PHP is an interpreter that can be executed as a program Common Gateway Interface (CGI) for web server or used as a module of the web server. PHP is a widely-used general-purpose scripting language that is especially suited for Web development and can be embedded into HTML.
61
This is because of convenience portability PHP on all platforms (Sidik, 2005:323-325).
PHP is a server-side scripting language that allows your Web site to be truly dynamic (Elizabeth, et.al, 2005).
There are four kinds of couples PHP tags that can be used to mark blocks of PHP scripts, namely (Peranginangin, 2006):
1. <?php…?>
2. <script language = “PHP”>…</script> 3. <?...?>
4. <%...%> 2.13 MYSQL
MySQL is a database management system that is open source. MySQL is a couple of PHP. MySQL created and developed by MySQL AB in Sweden. MySQL can be used to create and manage a database and its contents. MySQL can be used to add, modify, and delete data that resides in the database. MySQL is a database management system that is relational. This means that data is managed in the database will be placed on separate tables so that some data manipulation will be faster. MySQL can be used to manage databases ranging from small to large. MySQL can also run commands Structured Query Language (SQL) to manage relational databases in it (Ramadan, 2006).
2.14 XAMPP
62
on the computer. XAMPP can also be called a virtual server Control Panel which helps us to do a preview so that it can modify the web site without having to online accessible to the internet (Wicaksono, 2008).
2.15 Related Works
There are many studies has been done in related to this topics in adition to support this research there are:
Rahmawati(2007), title of her research Aplikasi Digital Signature Sebagai Autentikasi Pada Kartu Tanda Penduduk , finding the system that will autenticate the identity card for manipulated, used java and used SDLC strutured, recommendation try to used web based system that will improved the performance the system.
Other researher is Adharawati (2010), titled Penerapan web service sebagai alat pengendalian biaya, finding manipulating budget trough different platform as web based system, used qualitative approaches method, recommendation can have function for upload the phical file.
Other researcher is Ramadan (2009), titled Aplikasi digital signature sebagai sistem pengarsipan rumah sakit, finding autentication system to hospital file that will keep the data in original version, recommendation used web base to support system better.
63
Other researcher is Rianto (2007), Implementasi Web Service Untuk Menambah dan Mengurangi Service Pada Web Service Lain, finding intergrated with multi platform data system can give effect to anther syetm via web service, recommendation used simple algorithm to encrypt data that send via xml.
Other researcher is Pratama (2008), Implementasi Digital Signature Pada Sistem Keamanan Mobile Banking, finding intergrated with multi platform data in moble divice, recommendation used simple algorithm to encrypt data that send via xml.
Table 2.15 Summary of Related Work Chart
No Literatur Metode Tools Weakness System offered
1 Aplikasi Digital Signature Sebagai Autentikasi Pada Katu Tanda Penduduk (Desi Ramayanti, 2007)
Terstruktur/ Waterfall
Java Use AES Algorithm
because in this eras technology develop very well we actually we can use better algorithm to protect it
in terms of features, the proposed
system provides a report in the form of graphs that can show the
event rate difference in the number of variance or a larger budget than the budgeted cost.
2 Penerapan web service sebagai Alat
Research usin g qualitative a
PHP,MYSQ L
Results of the study is
Was applied by
64 Pengendalian Biaya
(Athena Adharawati, 2010)
pproaches only a theory
of how the
F maliputi budget b ut not
yet implemented by utilizing informatio n technology
nology by using the tools ofxampp, Dreamwe aver
8, Star UML and Ms.Visi o. With the PHP
programming language.
3 Aplikasi Digital signature sebagai autentikasi system pengarsipan rumah sakit ( Ramadan , 2009 )
SDLC PHP
MYSQL
Still used old algorithm DES that can be creaked now
System that will intergrated even they have different platform.
4. Penerapan teknologi web services pada prototype layanan informasi lowongan pekerjaan
secara online(HARTO NO,2009)
SDLC C#, SQL
SERVER
System tranfer data via xml and it is not encrypted
System that will intergrated even they have different platform.
5. Implementasi Web Service Untuk
Prototyping VB Data that transfer via xml not
65
Based on all related work above researcher want to make a system that integrated between web service and digital signature, so beside the system can integrated with multi platform application they can also can authenticated data that need to be checked in this case RKA – SKPD Kota Malang.
Menambah dan Mengurangi Service Pada Web Service Lain(Andi
Rianto,2007)
encrypted different system
6. Implementasi Digital Signature Pada Sistem Keamanan Mobile Banking (Ramadani Pratama ,2008)
Prototyping JAVA Still used AES algorithm
66 CHAPTER III RESEARCH METHOD
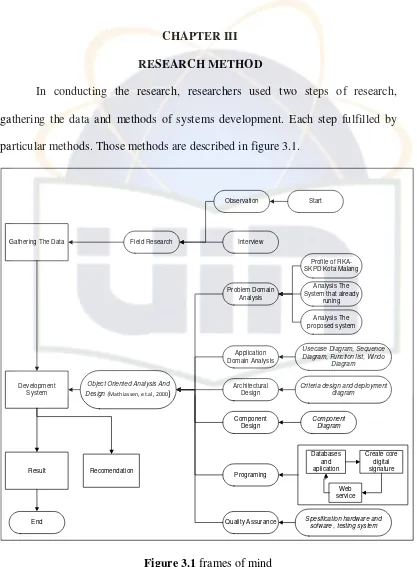
In conducting the research, researchers used two steps of research, gathering the data and methods of systems development. Each step fulfilled by particular methods. Those methods are described in figure 3.1.
Gathering The Data
Development System Result Field Research Observation Interview
Object Oriented Analysis And Design (Mathiassen, et.al, 2000)
Problem Domain Analysis
Profile of RKA-SKPD Kota Malang
Analysis The System that already
runing
Analysis The proposed system
Application Domain Analysis
Usecase Diagram, Sequence Diagram, Function list, Windo
Diagram
Architectural Design
Criteria design and deployment diagram Component Design Programing Quality Assurance Component Diagram
Spesification hardware and sofware , testing system
[image:66.595.113.530.84.651.2]Recomendation End Start Create core digital signature Databases and aplication Web service
Figure 3.1 frames of mind 3.1 Gathering the data
67
investigators get answers from the formulation of a problem that has been determined.
For gathering the data researcher used tree methods observation, literature study and interview.
3.1.1 Literature Study
Working on literature review and study by reading books as listed bellow:
1. Systems Analysis and Design (Mathiassen, et.al., 2000) and (wiritern, baley 2009) and writer get an overview about OOAD (object oriented analysis and design).
2. Human Resources Development book for suitable interface for customer. 3. Programming books about php and mysql integration
4. Software Engineering books and books that support the discussed topics in the preparation of this research.
5. Websites rosihanari related to php programming and mysql integration with web service.
6. http://library.nu there a lot of e-book that related to RSA algorithm and cryptography
3.1.1 Observation Method
68
was done by 1 mei – 30 mei 2011. The researcher observed the system of RKA-SKPD Kota Malang and sees the function one by one.
3.1.2 Interview
This method of collecting data involves presentation or oral-verbal stimuli and reply in terms of oral-verbal responses. The purpose of this interview is to know more detail about current system. There are two interviews in general as follows:
1) Personal Interviews with the developer of this project related to finance archives system RKA-SKPD Kota Malang in this case Mr syafedi syafei.
2) Writeable document from the system that includes more technically aspects from finance archives system RKA-SKPD Kota Malang. 3.2 System Development Methodology
There are four main OOAD activities that are using in this research 1. Problem Domain Analysis
At this stage, writer gives explanation about previous system that already running, the system is archives system RKA-SKPD Kota Malang, analysis behavior and characteristic of the system that already running in a
rich picture, also described is a system proposed in the form of rich picture, class diagrams, database structure, CRUD matrix and State chart diagrams.
2. Application Domain Analysis
69
usage. And also determine how the system interacts with people (actors) and other systems in the function. And explain how the designs of the system can verify the data from network.
Stages of the Application Domain Analysis are described in the form of use case diagrams, sequence diagrams, function list and diagram window.
3. Architectural Design
[image:69.595.113.522.107.608.2]At this stage will be explained the. Architecture Design In the design criteria contained in the web secure system (proposed system) in table of criteria and will be described web secure system in the layout of a physical system, exposing parts of the software that runs on parts of the hardware components of what is required in the that data will be show in
deployment diagrams. 4. Component Design
Purpose of this phase is to determine an implementation of requirements within an architectureal framework of web secure that offered. Build a model compnenet and function component from existing class diagram. 5. Programming
70 6. Quality Assurance
At this stage it is described on the specifications of the hardware and software needed. In Addition, system testing also done with black-box testing method, where the authors perform data input the system and sees its output as expected. The black-box testing focusing on user oriented
71 CHAPTER IV
ANALYSIS AND DESIGN SYSTEM
4.1 Problem Domain Analysis
4.1.1 Profile RKA-SKPD Kota Malang
4.1.1.1 A Glance with Information System RKA-SKPD Kota Malang
Local government finance system is part of the public sector’s financial
system, which records and report all financial transaction relating to area. Called regional financial is all the rights and obligations in the area of local government framework that can be valued in money, including all forms of property-related right and obligations of the ar