Wiley Publishing, Inc.
CISSP
®
Certified Information Systems
Security Professional
Study Guide
Fourth Edition
James Michael Stewart
Ed Tittel
CISSP
®
Certified Information Systems
Security Professional
Wiley Publishing, Inc.
CISSP
®
Certified Information Systems
Security Professional
Study Guide
Fourth Edition
James Michael Stewart
Ed Tittel
Acquisitions Editor: Jeff Kellum
Vice President and Executive Group Publisher: Richard Swadley Vice President and Executive Publisher: Joseph B. Wikert Vice President and Publisher: Neil Edde
Media Associate Project Manager: Laura Moss-Hollister Media Assistant Producer: Kit Malone
Media Quality Assurance: Josh Frank Book Designers: Judy Fung and Bill Gibson
Compositor: Craig J. Woods, Happenstance Type-O-Rama Proofreaders: Sondra Schneider and Nancy Bell
Indexer: Jack Lewis Cover Designer: Ryan Sneed
Copyright © 2008 by Wiley Publishing, Inc., Indianapolis, Indiana
Published simultaneously in Canada
ISBN: 978-0-470-27688-4
No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, or online at http://www.wiley.com/go/permissions.
Limit of Liability/Disclaimer of Warranty: The publisher and the author make no representations or warranties with respect to the accuracy or completeness of the contents of this work and specifically disclaim all warranties, including without limitation warranties of fitness for a particular purpose. No warranty may be created or extended by sales or promotional materials. The advice and strategies contained herein may not be suitable for every situation. This work is sold with the understanding that the publisher is not engaged in rendering legal, accounting, or other pro-fessional services. If propro-fessional assistance is required, the services of a competent propro-fessional person should be sought. Neither the publisher nor the author shall be liable for damages arising herefrom. The fact that an organi-zation or Website is referred to in this work as a citation and/or a potential source of further information does not mean that the author or the publisher endorses the information the organization or Website may provide or recom-mendations it may make. Further, readers should be aware that Internet Websites listed in this work may have changed or disappeared between when this work was written and when it is read.
For general information on our other products and services or to obtain technical support, please contact our Customer Care Department within the U.S. at (800) 762-2974, outside the U.S. at (317) 572-3993 or fax (317) 572-4002.
Wiley also publishes its books in a variety of electronic formats. Some content that appears in print may not be avail-able in electronic books.
Library of Congress Cataloging-in-Publication Data is available from the publisher.
TRADEMARKS: Wiley, the Wiley logo, and the Sybex logo are trademarks or registered trademarks of John Wiley & Sons, Inc. and/or its affiliates, in the United States and other countries, and may not be used without written per-mission. CISSP is a registered trademark of International Information Systems Security Certification Consortium, Inc. All other trademarks are the property of their respective owners. Wiley Publishing, Inc., is not associated with any product or vendor mentioned in this book.
Dear Reader,
Thank you for choosing CISSP: Certified Information Systems Security Professional Study Guide. This book is part of a family of premium quality Sybex books, all written by out-standing authors who combine practical experience with a gift for teaching.
Sybex was founded in 1976. More than thirty years later, we’re still committed to producing consistently exceptional books. With each of our titles we’re working hard to set a new standard for the industry. From the paper we print on, to the authors we work with, our goal is to bring you the best books available.
I hope you see all that reflected in these pages. I’d be very interested to hear your comments and get your feedback on how we’re doing. Feel free to let me know what you think about this or any other Sybex book by sending me an email at [email protected], or if you think you’ve found a technical error in this book, please visit http://sybex.custhelp.com. Customer feedback is critical to our efforts at Sybex.
Best regards,
Neil Edde
To Cathy, whenever there is trouble, just remember “Some beach, somewhere….”
—James Michael Stewart
To my family: Renee, Richard, Matthew, and Christopher, who lovingly put up with me during the hours I spent buried in my laptop writing this book.
Acknowledgments
I hope our efforts to improve this study guide will lend themselves handily to your understand-ing and comprehension of the wide berth of CISSP concepts. I’d like to express my thanks to Sybex for continuing to support this project. Thanks to Ed Tittel and Mike Chapple for con-tinuing to contribute to this project. Also thanks to all my CISSP course students who have provided their insight and input to improve my training courseware and ultimately this tome.
To my wonderful wife, Cathy, our life together is just getting started. To my son, Xzavier Slayde, may you grow to be more than we could imagine. To my parents, Dave and Sue, thanks for your love and consistent support. To Mark, as best friends go, it could’ve been worse. And finally, as always, to Elvis—all hail the King!
—James Michael Stewart
Thanks to both Michael Stewart and Mike Chapple for keeping me involved in this inter-esting project. I’m glad Michael has had the opportunity to keep teaching CISSP courses and provide us all with a lifeline to the hard-working professionals in the trenches for whom this credential can mean so much. Congrats also to Michael on the latest addition to his family; my son, Gregory, just turned four and it seems like only last month we brought him home from the hospital. May the months and years slip by as pleasantly and painlessly for you as they have for us. Next, thanks to the folks at Sybex, especially Jeff Kellum for rounding us all up and keeping us headed in the same direction and for his excellent view of where we need to take this book. Finally, I’d like to thank my loving and lovely wife, Dina, for putting up with me and for making our lives together both comfortable and interesting.
—Ed Tittel
Special thanks go to the information security team at the University of Notre Dame. Gary Dobbins, Bob Winding, David Seidl, and Robert Riley provided hours of interesting conversation and debate on security issues that inspired and informed much of the mate-rial in this book.
I would like to thank Jeff Kellum, our editor at Wiley, and the people at Allegro Editorial Services, who provided invaluable assistance throughout the book development process. I also owe a debt of gratitude to my literary agent, Carole Jelen of Waterside Productions. My coauthors, Ed Tittel and James Michael Stewart, have worked with me ever since we pub-lished the first edition of this book together five years ago. I’d also like to thank the many people who participated in the production of this book but whom I never had the chance to meet: the graphics team, the production staff, and all of those involved in bringing this book to press.
About the Authors
James Michael Stewart, CISSP, has been writing and training for more than 14 years, with a current focus on security. He has taught dozens of CISSP training courses, not to mention numerous sessions on Windows security and the Certified Ethical Hacker certification. He is the author of several books and courseware sets on security certification, Microsoft topics, and network administration. More information about Michael can be found at his website: www.impactonline.com.
Ed Tittel is a full-time freelance writer, trainer, and consultant specializing in matters related to information security, markup languages, and networking technologies. He is a regular contributor to numerous TechTarget websites; teaches online security and technology courses for companies including HP, Sony, and Motorola; and writes regularly for Tom’s Hardware. Ed’s professional bio and other information are available at www.edtittel.com.
Contents at a Glance
Introduction xxvii
Assessment Test xxxv
Chapter 1 Accountability and Access Control 1
Chapter 2 Attacks and Monitoring 45
Chapter 3 ISO Model, Protocols, Network Security,
and Network Infrastructure 77
Chapter 4 Communications Security and Countermeasures 139
Chapter 5 Security Management Concepts and Principles 179
Chapter 6 Asset Value, Policies, and Roles 205
Chapter 7 Data and Application Security Issues 243
Chapter 8 Malicious Code and Application Attacks 293
Chapter 9 Cryptography and Private Key Algorithms 333
Chapter 10 PKI and Cryptographic Applications 375
Chapter 11 Principles of Computer Design 411
Chapter 12 Principles of Security Models 451
Chapter 13 Administrative Management 495
Chapter 14 Auditing and Monitoring 527
Chapter 15 Business Continuity Planning 563
Chapter 16 Disaster Recovery Planning 591
Chapter 17 Law and Investigations 629
Chapter 18 Incidents and Ethics 665
Chapter 19 Physical Security Requirements 691
Appendix About the Companion CD 725
Glossary 729
Contents
Introduction xxvii
Assessment Test xxxv
Chapter 1 Accountability and Access Control 1
Access Control Overview 2
Types of Access Control 2
Access Control in a Layered Environment 4 The Process of Accountability 5 Identification and Authentication Techniques 9 Passwords 10 Biometrics 13 Tokens 18 Tickets 20
Single Sign-On 20
Access Control Techniques 23
Discretionary Access Controls 23 Nondiscretionary Access Controls 23
Mandatory Access Controls 24
Role-Based Access Control 25
Lattice-Based Access Controls 26 Access Control Methodologies and Implementation 27 Centralized and Decentralized Access Control 27
RADIUS and TACACS 28
Access Control Administration 29
Account Administration 29
Account, Log, and Journal Monitoring 30 Access Rights and Permissions 30 Summary 34
Exam Essentials 35
Written Lab 37
Answers to Written Lab 38
Review Questions 39
Answers to Review Questions 43
Chapter 2 Attacks and Monitoring 45
Monitoring 46
Intrusion Detection 47
xii Contents
IDS-Related Tools 52
Understanding Honey Pots 52
Understanding Padded Cells 53
Understanding Vulnerability Scanners 53
Penetration Testing 54
Methods of Attack 55
Brute-Force and Dictionary Attacks 56
Denial-of-Service Attacks 58
Spoofing Attacks 62
Man-in-the-Middle Attacks 63
Sniffer Attacks 64
Spamming Attacks 64
Crackers, Hackers, and Attackers 64
Access Control Compensations 65
Summary 65
Exam Essentials 66
Written Lab 68
Answers to Written Lab 69
Review Questions 70
Answers to Review Questions 74
Chapter 3 ISO Model, Protocols, Network Security,
and Network Infrastructure 77
OSI Model 78
History of the OSI Model 78
OSI Functionality 79
Encapsulation/Deencapsulation 80
OSI Layers 81
TCP/IP Model 87
Communications and Network Security 88
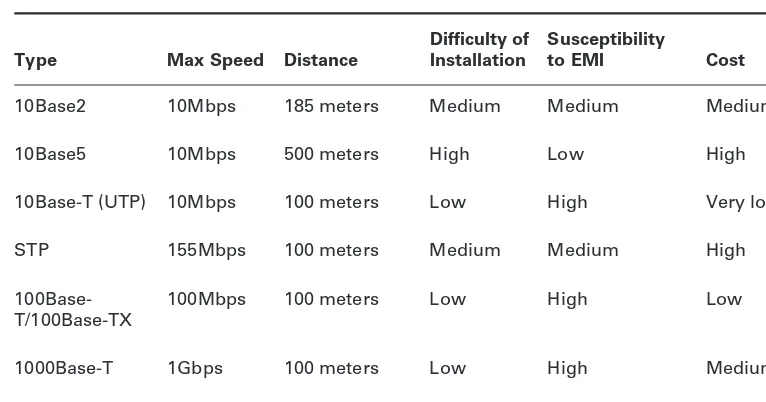
Network Cabling 88
LAN Technologies 99
Network Topologies 103
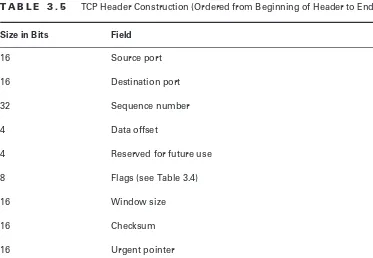
TCP/IP Overview 105
Internet/Intranet/Extranet Components 116 Firewalls 116
Other Network Devices 119
Remote Access Security Management 123 Network and Protocol
Security Mechanisms 124
Secure Communications Protocols 124
Dial-Up Protocols 125
Authentication Protocols 126
Contents xiii
Avoiding Single Points of Failure 127
Redundant Servers 127
Failover Solutions 127
RAID 128 Summary 129
Exam Essentials 130
Written Lab 131
Answers to Written Lab 132
Review Questions 133
Answers to Review Questions 137
Chapter 4 Communications Security and Countermeasures 139
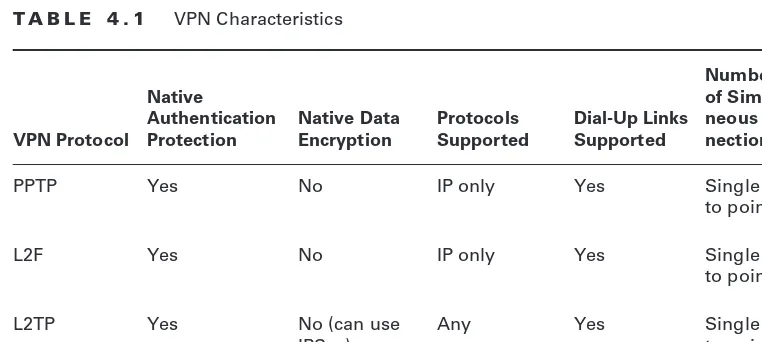
Virtual Private Network (VPN) 140 Tunneling 141
How VPNs Work 142
Implementing VPNs 142
Network Address Translation 144
Private IP Addresses 145
Stateful NAT 146
Static and Dynamic NAT 146
Automatic Private IP Addressing (APIPA) 147
Switching Technologies 147
Circuit Switching 148
Packet Switching 148
Virtual Circuits 149
WAN Technologies 149
WAN Connection Technologies 151 Dial-Up Encapsulation Protocols 154 Miscellaneous Security Control Characteristics 154 Transparency 154
Verifying Integrity 154
Transmission Mechanisms 155
Managing Email Security 156
Email Security Goals 156
Understanding Email Security Issues 157
Email Security Solutions 158
Securing Voice Communications 160
Social Engineering 160
Fraud and Abuse 161
Phreaking 162
Security Boundaries 163
Network Attacks and Countermeasures 164 Eavesdropping 164
xiv Contents
Summary 168
Exam Essentials 169
Written Lab 171
Answers to Written Lab 172
Review Questions 173
Answers to Review Questions 177
Chapter 5 Security Management Concepts and Principles 179
Security Management Concepts and Principles 180 Confidentiality 180 Integrity 181 Availability 183
Other Security Concepts 183
Protection Mechanisms 187
Layering 187 Abstraction 188
Data Hiding 188
Encryption 188
Change Control/Management 189
Data Classification 190
Planning to Plan 193
Summary 193
Exam Essentials 195
Written Lab 196
Answers to Written Lab 197
Review Questions 198
Answers to Review Questions 202
Chapter 6 Asset Value, Policies, and Roles 205
Employment Policies and Practices 206 Security Management for Employees 206
Security Roles 211
Security Management Planning 212
Policies, Standards, Baselines, Guidelines, and Procedures 214
Security Policies 214
Security Standards, Baselines, and Guidelines 215
Security Procedures 216
Risk Management 217
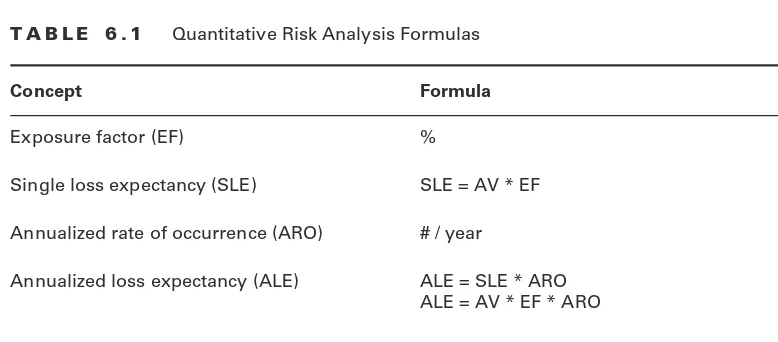
Risk Terminology 218
Risk Assessment Methodologies 220
Quantitative Risk Analysis 223
Qualitative Risk Analysis 227
Contents xv
Security Awareness Training 230
Summary 231
Exam Essentials 233
Written Lab 235
Answers to Written Lab 236
Review Questions 237
Answers to Review Questions 241
Chapter 7 Data and Application Security Issues 243
Application Issues 244
Local/Nondistributed Environment 244
Distributed Environment 246
Databases and Data Warehousing 250 Database Management System (DBMS) Architecture 250
Database Transactions 254
Security for Multilevel Databases 255 ODBC 257 Aggregation 257
Data Mining 259
Data/Information Storage 260
Types of Storage 260
Storage Threats 261
Knowledge-Based Systems 261
Expert Systems 262
Neural Networks 263
Decision Support Systems 263
Security Applications 264
Systems Development Controls 264
Software Development 264
Systems Development Life Cycle 269
Life Cycle Models 272
Gantt Charts and PERT 277
Change Control and Configuration Management 278
Software Testing 279
Security Control Architecture 280
Service-Level Agreements 283
Summary 283
Exam Essentials 284
Written Lab 285
Answers to Written Lab 286
Review Questions 287
xvi Contents
Chapter 8 Malicious Code and Application Attacks 293
Malicious Code 294
Sources 294 Viruses 295
Logic Bombs 300
Trojan Horses 300
Worms 301
Spyware and Adware 303
Active Content 303
Countermeasures 304
Password Attacks 305
Password Guessing 305
Dictionary Attacks 306
Social Engineering 307
Countermeasures 307
Denial-of-Service Attacks 308
SYN Flood 308
Distributed DoS Toolkits 309
Smurf 309
DNS Amplification Attacks 311
Teardrop 311 Land 313
DNS Poisoning 313
Ping of Death 314
Application Attacks 314
Buffer Overflows 314
Time-of-Check-to-Time-of-Use 315
Trap Doors 315
Rootkits 315
Web Application Security 316
Cross-Site Scripting (XSS) 316
SQL Injection 317
Reconnaissance Attacks 319
IP Probes 319
Port Scans 320
Vulnerability Scans 320
Dumpster Diving 320
Masquerading Attacks 321
IP Spoofing 321
Session Hijacking 321
Decoy Techniques 322
Honey Pots 322
Contents xvii
Summary 323
Exam Essentials 323
Written Lab 324
Answers to Written Lab 325
Review Questions 326
Answers to Review Questions 330
Chapter 9 Cryptography and Private Key Algorithms 333
Historical Milestones in Cryptography 334
Caesar Cipher 334
American Civil War 335
Ultra vs. Enigma 335
Cryptographic Basics 336
Goals of Cryptography 336
Cryptography Concepts 337
Cryptographic Mathematics 339
Ciphers 345
Modern Cryptography 351
Cryptographic Keys 351
Symmetric Key Algorithms 352
Asymmetric Key Algorithms 353
Hashing Algorithms 356
Symmetric Cryptography 357
Data Encryption Standard 357
Triple DES 359
International Data Encryption Algorithm 360 Blowfish 360 Skipjack 361 Advanced Encryption Standard 361
Key Distribution 363
Key Escrow 364
Summary 365
Exam Essentials 365
Written Lab 367
Answers to Written Lab 368
Review Questions 369
Answers to Review Questions 373
Chapter 10 PKI and Cryptographic Applications 375
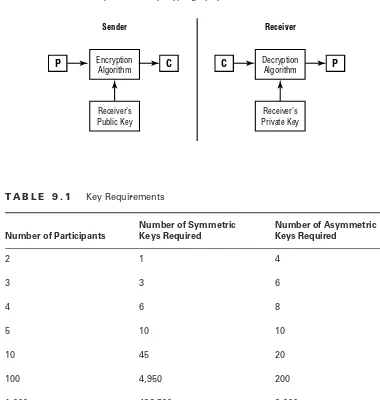
Asymmetric Cryptography 376
Public and Private Keys 377
RSA 377
El Gamal 379
xviii Contents
Hash Functions 380
SHA 381 MD2 382 MD4 382 MD5 383
Digital Signatures 384
HMAC 385
Digital Signature Standard 385
Public Key Infrastructure 386
Certificates 386
Certificate Authorities 387
Certificate Generation and Destruction 388
Key Management 390
Applied Cryptography 390
Electronic Mail 391
Web 393 E-commerce 394 Networking 395
Cryptographic Attacks 399
Summary 400
Exam Essentials 401
Written Labs 402
Answers to Written Labs 403
Review Questions 404
Answers to Review Questions 408
Chapter 11 Principles of Computer Design 411
Computer Architecture 413
Hardware 413
Input/Output Structures 432
Firmware 434 Security Protection Mechanisms 434
Technical Mechanisms 435
Security Policy and Computer Architecture 437
Policy Mechanisms 438
Distributed Architecture 439
Summary 441
Exam Essentials 441
Written Lab 443
Answers to Written Lab 444
Review Questions 445
Contents xix
Chapter 12 Principles of Security Models 451
Security Models 453
Trusted Computing Base (TCB) 454
State Machine Model 455
Information Flow Model 455
Noninterference Model 456
Take-Grant Model 456
Access Control Matrix 457
Bell-LaPadula Model 458
Biba Model 460
Clark-Wilson Model 461
Brewer and Nash Model (aka Chinese Wall) 462
Objects and Subjects 462
Closed and Open Systems 463
Techniques for Ensuring Confidentiality,
Integrity, and Availability 463 Controls 464
Trust and Assurance 465
Understanding System Security Evaluation 466
Rainbow Series 466
ITSEC Classes and Required Assurance and Functionality 471
Common Criteria 472
Certification and Accreditation 475 Common Flaws and Security Issues 478
Covert Channels 478
Attacks Based on Design or Coding Flaws and
Security Issues 479
Programming 482 Timing, State Changes, and Communication Disconnects 482
Electromagnetic Radiation 483
Summary 483
Exam Essentials 484
Written Lab 486
Answers to Written Lab 487
Review Questions 488
Answers to Review Questions 492
Chapter 13 Administrative Management 495
Operations Security Concepts 496
Antivirus Management 496
Operational Assurance and Life Cycle Assurance 498
Backup Maintenance 499
xx Contents
Need to Know and the Principle of Least Privilege 500 Privileged Operations Functions 501
Trusted Recovery 502
Configuration and Change Management Control 503 Standards of Due Care and Due Diligence 504
Privacy and Protection 505
Legal Requirements 505
Illegal Activities 505
Record Retention 505
Sensitive Information and Media 506
Security Control Types 509
Operations Controls 510
Personnel Controls 513
Summary 514
Exam Essentials 516
Written Lab 518
Answers to Written Lab 519
Review Questions 520
Answers to Review Questions 524
Chapter 14 Auditing and Monitoring 527
Auditing 528
Auditing Basics 528
Audit Trails 530
Reporting Concepts 532
Sampling 532
Record Retention 533
External Auditors 534
Monitoring 535 Monitoring Tools and Techniques 535 Penetration-Testing Techniques 537 Planning Penetration Testing 538
Penetration Testing Teams 539
Ethical Hacking 540
War Dialing 540
Sniffing and Eavesdropping 541
Radiation Monitoring 542
Dumpster Diving 542
Social Engineering 543
Problem Management 544
Inappropriate Activities 544
Indistinct Threats and Countermeasures 545
Errors and Omissions 545
Contents xxi
Collusion 546 Sabotage 547 Loss of Physical and Infrastructure Support 547
Malicious Attackers 548
Espionage 548
Malicious Code 549
Traffic and Trend Analysis 550
Initial Program Load Vulnerabilities 550 Summary 551
Exam Essentials 552
Written Lab 555
Answers to Written Lab 556
Review Questions 557
Answers to Review Questions 561
Chapter 15 Business Continuity Planning 563
Business Continuity Planning 564
Project Scope and Planning 565
Business Organization Analysis 566
BCP Team Selection 566
Resource Requirements 567
Legal and Regulatory Requirements 569
Business Impact Assessment 570
Identify Priorities 571
Risk Identification 572
Likelihood Assessment 572
Impact Assessment 573
Resource Prioritization 575
Continuity Planning 575
Strategy Development 576
Provisions and Processes 576
Plan Approval 578
Plan Implementation 578
Training and Education 578
BCP Documentation 579
Continuity Planning Goals 579
Statement of Importance 579
Statement of Priorities 579
Statement of Organizational Responsibility 580 Statement of Urgency and Timing 580
Risk Assessment 580
Risk Acceptance/Mitigation 580
Vital Records Program 581
xxii Contents
Maintenance 581 Testing 581 Summary 582
Exam Essentials 582
Written Lab 583
Answers to Written Lab 584
Review Questions 585
Answers to Review Questions 589
Chapter 16 Disaster Recovery Planning 591
The Nature of Disaster 592
Natural Disasters 593
Man-Made Disasters 597
Recovery Strategy 602
Business Unit Priorities 602
Crisis Management 602
Emergency Communications 603
Work Group Recovery 603
Alternate Processing Sites 604
Mutual Assistance Agreements 607
Database Recovery 608
Recovery Plan Development 610
Emergency Response 610
Personnel Notification 611
Backups and Off-Site Storage 612 Software Escrow Arrangements 615
External Communications 616
Utilities 616
Logistics and Supplies 616
Recovery vs. Restoration 616
Training and Documentation 617
Testing and Maintenance 618
Checklist Test 618
Structured Walk-Through 619
Simulation Test 619
Parallel Test 619
Full-Interruption Test 619
Maintenance 619 Summary 620
Exam Essentials 621
Written Lab 621
Answers to Written Lab 622
Review Questions 623
Contents xxiii
Chapter 17 Law and Investigations 629
Categories of Laws 630
Criminal Law 630
Civil Law 632
Administrative Law 632
Laws 633
Computer Crime 633
Intellectual Property 637
Licensing 642 Import/Export 643 Privacy 644 Investigations 649 Evidence 649
Investigation Process 652
Summary 654
Exam Essentials 654
Written Lab 656
Answers to Written Lab 657
Review Questions 658
Answers to Review Questions 662
Chapter 18 Incidents and Ethics 665
Major Categories of Computer Crime 666 Military and Intelligence Attacks 667
Business Attacks 667
Financial Attacks 668
Terrorist Attacks 668
Grudge Attacks 669
Thrill Attacks 670
Evidence 670
Incident Handling 671
Common Types of Incidents 672
Response Teams 673
Incident Response Process 675
Interviewing Individuals 678
Incident Data Integrity and Retention 678
Reporting Incidents 678
Ethics 680
(ISC)2 Code of Ethics 680
Ethics and the Internet 681
Summary 682
Exam Essentials 683
xxiv Contents
Answers to Written Lab 685
Review Questions 686
Answers to Review Questions 689
Chapter 19 Physical Security Requirements 691
Facility Requirements 692
Secure Facility Plan 693
Physical Security Controls 693
Site Selection 694
Visibility 695 Accessibility 695
Natural Disasters 695
Facility Design 695
Work Areas 696
Server Rooms 696
Visitors 696 Forms of Physical Access Controls 698 Fences, Gates, Turnstiles, and Mantraps 698 Lighting 698
Security Guards and Dogs 699
Keys and Combination Locks 700
Badges 701
Motion Detectors 702
Intrusion Alarms 702
Secondary Verification Mechanisms 702
Technical Controls 703
Smart Cards 704
Proximity Readers 704
Access Abuses 705
Intrusion Detection Systems 705
Emanation Security 706
Environment and Life Safety 707
Personnel Safety 707
Power and Electricity 708
Noise 709 Temperature, Humidity, and Static 709 Water 710 Fire Detection and Suppression 710
Equipment Failure 715
Summary 715
Exam Essentials 716
Written Lab 718
Answers to Written Lab 719
Review Questions 720
Contents xxv
Appendix About the Companion CD 725
What You’ll Find on the CD 726
Sybex Test Engine 726
PDF of the Book 726
Adobe Reader 726
Electronic Flashcards 727
System Requirements 727
Using the CD 727
Troubleshooting 727
Customer Care 728
Glossary 729
Introduction
The CISSP: Certified Information Systems Security Professional Study Guide, 4th Edition, offers you a solid foundation for the Certified Information Systems Security Professional (CISSP) exam. By purchasing this book, you’ve shown a willingness to learn and a desire to develop the skills you need to achieve this certification. This introduction provides you with a basic overview of this book and the CISSP exam.
This book is designed for readers and students who want to study for the CISSP certification exam. If your goal is to become a certified security professional, then the CISSP certification and this study guide are for you. The purpose of this book is to adequately prepare you to take the CISSP exam.
Before you dive into this book, you need to have accomplished a few tasks on your own. You need to have a general understanding of IT and of security. You should have the necessary five years of experience (or four years if you have a college degree) in one of the 10 domains covered by the CISSP exam. If you are qualified to take the CISSP exam according to (ISC)2, then you are sufficiently prepared to use this book to study for the CISSP exam. For more information on (ISC)2, see the next section.
(ISC)
2The CISSP exam is governed by the International Information Systems Security Certification Consortium (ISC)2 organization. (ISC)2 is a global not-for-profit organization. It has four primary mission goals:
Maintain the Common Body of Knowledge (CBK) for the field of information systems security.
Provide certification for information systems security professionals and practitioners. Conduct certification training and administer the certification exams.
Oversee the ongoing accreditation of qualified certification candidates through continued education.
The (ISC)2 is operated by a board of directors elected from the ranks of its certified practitioners. You can obtain more information about (ISC)2 from its website at www.isc2.org.
CISSP and SSCP
xxviii Introduction
The CISSP certification covers material from the 10 CBK domains:
Access Control
Telecommunications and Network Security Information Security and Risk Management Application Security
Cryptography
Security Architecture and Design Operations Security
Business Continuity and Disaster Recovery Planning Legal, Regulations, Compliance, and Investigations Physical (Environmental) Security
The SSCP certification covers material from seven CBK domains:
Access Controls Administration Audit and Monitoring Cryptography
Data Communications Malicious Code/Malware Risk, Response, and Recovery
The content for the CISSP and SSCP domains overlap significantly, but the focus is different for each set of domains. The CISSP focuses on theory and design, whereas the SSCP focuses more on implementation and best practices. This book focuses only on the domains for the CISSP exam.
Prequalifications
(ISC)2 has defined several qualification requirements you must meet to become a CISSP. First, you must be a practicing security professional with at least five years’ experience or with four years’ experience and a recent IT or IS degree. Professional experience is defined as security work performed for salary or commission within one or more of the 10 CBK domains.
Second, you must agree to adhere to a formal code of ethics. The CISSP Code of Ethics is a set of guidelines the (ISC)2 wants all CISSP candidates to follow to maintain professionalism in the field of information systems security. You can find it in the Information section on the (ISC)2 website at www.isc2.org.
Introduction xxix
To sign up for the CISSP exam, visit the (ISC)2 website, and follow the instructions listed there for registering to take the CISSP exam (the link reads “Register Now for CISSP Certification Exams”). You’ll provide your contact information, payment details, and security-related pro-fessional experience. You’ll also select one of the available time and location settings for the exam. Once (ISC)2 approves your application to take the exam, you’ll receive a confirmation email with all the details you’ll need to find the testing center and take the exam.
Overview of the CISSP Exam
The CISSP exam consists of 250 questions, and you have 6 hours to complete it. The exam is still administered using a paper booklet and answer sheet. This means you’ll be using a pencil to fill in answer bubbles.
The CISSP exam focuses on security from a 30,000-foot view; it deals more with theory and concept than implementation and procedure. It is very broad but not very deep. To success-fully complete this exam, you’ll need to be familiar with every domain in the CBK but not nec-essarily be a master of each domain.
You’ll need to register for the exam through the (ISC)2 website at www.isc2.org. (ISC)2 administers the exam itself. In most cases, the exams are held in large conference rooms at hotels. Existing CISSP holders are recruited to serve as proctors or administrators for these exams. Be sure to arrive at the testing center around 8 a.m., and keep in mind that absolutely no one will be admitted into the exam after 8:30 a.m. Once all test takers are signed in and seated, the exam proctors will pass out the testing materials and read a few pages of instructions. This may take 30 minutes or more. Once that process is finished, the 6 hour window for taking the test will begin.
CISSP Exam Question Types
Every question on the CISSP exam is a four-option, multiple-choice question with a single correct answer. Some are straightforward, such as asking you to select a definition. Some are a bit more involved, such as asking you to select the appropriate concept or best practice. And some questions present you with a scenario or situation and ask you to select the best response. Here’s an example:
1. What is the most important goal and top priority of a security solution?
A. Preventing disclosure
B. Maintaining integrity
C. Maintaining human safety
D. Sustaining availability
xxx Introduction
By the way, the correct answer for this question is C. Protecting human safety is always your first priority.
Advice on Taking the Exam
The CISSP exam consists of two key elements. First, you need to know the material from the 10 CBK domains. Second, you must have good test-taking skills. With 6 hours to complete a 250-question exam, you have just less than 90 seconds for each question. Thus, it is important to work quickly, without rushing but also without wasting time.
One key factor to remember is that guessing is better than not answering a question. If you don’t answer a question, you will not get any credit. But if you guess, you have at least a 25 percent chance of improving your score. Wrong answers are not counted against you. So, near the end of the sixth hour, be sure an answer is selected for every line on the answer sheet. You can write on the test booklet, but nothing written on it will count for or against your score. Use the booklet to make notes and keep track of your progress. We recommend circling each answer you select before you mark it on your answer sheet.
To maximize your test-taking activities, here are some general guidelines:
Answer easy questions first.
Skip harder questions, and return to them later. Consider creating a column on the front cover of your testing booklet to keep track of skipped questions.
Eliminate wrong answers before selecting the correct one. Watch for double negatives.
Be sure you understand what the question is asking.
Manage your time. You should try to complete about 50 questions per hour. This will leave you with about an hour to focus on skipped questions and double-check your work.
Be very careful to mark your answers on the correct question number on the answer sheet. The most common cause of failure is making a transference mistake from the test booklet to the answer sheet.
Be sure to bring food and drink to the test site. You will not be allowed to leave to obtain sustenance. Your food and drink will be stored against one wall of the testing room. You can eat and drink at any time, but only against that wall. Be sure to bring any medications or other essential items, but leave all things electronic at home or in your car. Wear a watch, but make sure it is not a programmable one. Bring pencils, manual sharpener, and an eraser.
Introduction xxxi
Study and Exam Preparation Tips
We recommend planning for a month or so of nightly intensive study for the CISSP exam. Here are some suggestions to maximize your learning time; you can modify them as necessary based on your own learning habits:
Take one or two evenings to read each chapter in this book and work through its review material.
Take all the practice exams provided in the book and on the CD. Complete the written labs from each chapter, and use its self-assessment questions to help guide you to top-ics where more study or time spent working through key concepts and strategies might be beneficial.
Review the (ISC)2’s study guide from www.isc2.org.
Use the flashcards found on the CD to reinforce your understanding of concepts.
We recommend spending about half of your study time reading and reviewing concepts and the other half taking practice exams. Students have reported that the more time they spent taking practice exams, the better they retained test topics.
You might also consider visiting resources such as www.cccure.org,
www.cissp.com, and other CISSP-focused websites.
Completing the Certification Process
Once you have been informed that you successfully passed the CISSP certification, there is one final step before you are actually awarded the CISSP certification. That final step is known as endorsement. Basically, this involves getting someone familiar with your work history to sign and submit an endorsement form on your behalf. The endorsement form is sent to you as an attachment to the email notifying you of your achievement in passing the exam. Simply send the form to a CISSP in good standing along with your résumé. The endorser must review your résumé, ensure that you have sufficient experience in the 10 CISSP domains, and then submit the signed form to (ISC)2 via fax or post mail. You must have submitted the endorsement files to (ISC)2 within 90 days after receiving the confirmation of passing email. Once (ISC)2 receives your endorsement form, the certification process will be completed and you will be sent a welcome packet via post mail.
xxxii Introduction
Post-CISSP Concentrations
(ISC)2 has added three concentrations to its certification lineup. These concentrations are offered only to CISSP certificate holders. The (ISC)2 has taken the concepts introduced on the CISSP exam and focused on specific areas, namely, architecture, management, and engineering. These three concentrations are as follows:
Information Systems Security Architecture Professional (ISSAP): Aimed at those who specialize in information security architecture. Key domains covered here include access control systems and methodology; cryptography; physical security integration; requirements analysis and security standards, guidelines, and criteria; technology-related aspects of business continuity planning and disaster recovery planning; and telecommunications and network security. This is a credential for those who design security systems or infrastructure or for those who audit and analyze such structures.
Information Systems Security Management Professional (ISSMP): Aimed at those who focus on management of information security policies, practices, principles, and procedures. Key domains covered here include enterprise security management practices; enterprise-wide sys-tem development security; law, investigations, forensics, and ethics; oversight for operations security compliance; and understanding business continuity planning, disaster recovery plan-ning, and continuity of operations planning. This is a credential for those professionals who are responsible for security infrastructures, particularly where mandated compliance comes into the picture.
Information Systems Security Engineering Professional (ISSEP): Aimed at those who focus on the design and engineering of secure hardware and software information systems, compo-nents, or applications. Key domains covered include certification and accreditation, systems security engineering, technical management, and U.S. government information assurance rules and regulations. Most ISSEPs work for the U.S. government or for a government con-tractor that manages government security clearances.
For more details about these concentration exams and certifications, please see the (ISC)2 website at www.isc2.org.
Notes on This Book’s Organization
This book is designed to cover each of the 10 CISSP Common Body of Knowledge domains in sufficient depth to provide you with a clear understanding of the material. The main body of this book comprises 19 chapters. The first nine domains are each covered by two chapters, and the final domain (Physical Security) is covered in Chapter 19. The domain/chapter break-down is as follows:
Chapters 1 and 2 Access Control
Chapters 3 and 4 Telecommunications and Network Security Chapters 5 and 6 Information Security and Risk Management Chapters 7 and 8 Application Security
Chapters 9 and 10 Cryptography
Introduction xxxiii
Chapters 13 and 14 Operations Security
Chapters 15 and 16 Business Continuity and Disaster Recovery Planning Chapters 17 and 18 Legal, Regulations, Compliance, and Investigation Chapter 19 Physical (Environmental) Security
Each chapter includes elements to help you focus your studies and test your knowledge, detailed in the following sections.
The Elements of This Study Guide
You’ll see many recurring elements as you read through this study guide. Here’s a description of some of those elements:
Key Terms and Glossary In every chapter, we’ve identified key terms, which are important for you to know. You’ll also find these key terms and their definitions in the glossary.
Summaries The summary is a brief review of the chapter to sum up what was covered. Exam Essentials The Exam Essentials highlight topics that could appear on one or both of the exams in some form. While we obviously do not know exactly what will be included in a particular exam, this section reinforces significant concepts that are key to understanding the body of knowledge area and the test specs for the CISSP exam.
Chapter Review Questions Each chapter includes practice questions that have been designed to measure your knowledge of key ideas that were discussed in the chapter. After you finish each chapter, answer the questions; if some of your answers are incorrect, it’s an indication that you need to spend some more time studying that topic. The answers to the practice questions can be found at the end of the chapter.
Written Labs Each chapter includes written labs that synthesize various concepts and topics that appear in the chapter. These raise questions that are designed to help you put together various pieces you’ve encountered individually in the chapter and assemble them to propose or describe potential security strategies or solutions.
Real World Scenarios As you work through each chapter, you’ll find at least two descriptions of typical and plausible workplace situations where an understanding of the security strategies and approaches relevant to the chapter content could play a role in fixing problems or in fending off potential difficulties. This gives readers a chance to see how specific security policies, guide-lines, or practices should or may be applied to the workplace.
What’s on the CD?
We worked really hard to provide some essential tools to help you with your certification process. All of the following gear should be loaded on your workstation when studying for the test.
The Sybex Test Preparation Software
xxxiv Introduction
test yourself by chapter, take the practice exams, or take a randomly generated exam com-prising all the questions.
Electronic Flashcards for PCs and Palm Devices
Sybex’s electronic flashcards include hundreds of questions designed to challenge you further for the CISSP exam. Between the review questions, practice exams, and flashcards, you’ll have more than enough practice for the exam!
CISSP Study Guide
in PDF
Sybex offers the CISSP Study Guide in PDF format on the CD so you can read the book on your PC or laptop. So if you travel and don’t want to carry a book, or if you just like to read from the computer screen, Adobe Acrobat is also included on the CD.
Bonus Exams
Sybex includes bonus exams on the CD, each comprised of questions meant to survey your understanding of key elements in the CISSP CBK.
How to Use This Book and CD
This book has a number of features designed to guide your study efforts for the CISSP certi-fication exam. It assists you by listing the CISSP body of knowledge at the beginning of each chapter and by ensuring that each topic is fully discussed within the chapter. The practice questions at the end of each chapter and the practice exams on the CD are designed to test your retention of the material you’ve read to make you are aware of areas in which you should spend additional study time. Here are some suggestions for using this book and CD:
Take the assessment test before you start reading the material. This will give you an idea of the areas in which you need to spend additional study time, as well as those areas in which you may just need a brief refresher.
Answer the review questions after you’ve read each chapter; if you answer any incorrectly, go back to the chapter and review the topic, or utilize one of the additional resources if you need more information.
Download the flashcards to your handheld device, and review them when you have a few minutes during the day.
Take every opportunity to test yourself. In addition to the assessment test and review questions, there are bonus exams on the CD. Take these exams without referring to the chapters and see how well you’ve done—go back and review any topics you’ve missed until you fully understand and can apply the concepts.
Assessment Test
1. Which of the following type of access control seeks to discover evidence of unwanted, unauthorized, or illicit behavior or activity?
A. Preventive
B. Deterrent C. Detective
D. Corrective
2. Can you define and detail the aspects of password selection that distinguish good password choices from ultimately poor password choices?
A. Difficult to guess or unpredictable B. Meet minimum length requirements
C. Meet specific complexity requirements
D. All of the above
3. Which of the following is most likely to detect DoS attacks?
A. Host-based IDS
B. Network-based IDS C. Vulnerability scanner
D. Penetration testing
4. Which of the following is considered a denial-of-service attack?
A. Pretending to be a technical manager over the phone and asking a receptionist to change their password
B. While surfing the Web, sending to a web server a malformed URL that causes the system to use 100 percent of the CPU to process an endless loop
C. Intercepting network traffic by copying the packets as they pass through a specific subnet D. Sending message packets to a recipient who did not request them simply to be annoying
5. At which layer of the OSI model does a router operate?
A. Network layer
B. Layer 1
C. Transport layer
D. Layer 5
6. Which type of firewall automatically adjusts its filtering rules based on the content of the traffic of existing sessions?
A. Static packet filtering
B. Application-level gateway
xxxvi Assessment Test
7. A VPN can be established over which of the following?
A. Wireless LAN connection
B. Remote access dial-up connection C. WAN link
D. All of the above
8. Email is the most common delivery vehicle for which of the following?
A. Viruses
B. Worms
C. Malicious code D. All of the above
9. The CIA Triad is comprised of what elements?
A. Contiguousness, interoperable, arranged
B. Authentication, authorization, accountability
C. Capable, available, integral
D. Availability, confidentiality, integrity
10. Which of the following is not a required component in the support of accountability?
A. Auditing B. Privacy
C. Authentication
D. Authorization
11. Which of the following is not a defense against collusion?
A. Separation of duties
B. Restricted job responsibilities C. Group user accounts
D. Job rotation
12. A data custodian is responsible for securing resources after ________ has assigned the resource a security label.
A. senior management B. data owner
C. auditor
Assessment Test xxxvii
13. In what phase of the Capability Maturity Model for Software (SW-CMM) are quantitative measures utilized to gain a detailed understanding of the software development process? A. Repeatable
B. Defined
C. Managed
D. Optimizing
14. Which one of the following is a layer of the ring protection scheme that is not normally imple-mented in practice?
A. Layer 0
B. Layer 1
C. Layer 3 D. Layer 4
15. What is the last phase of the TCP/IP three-way handshake sequence?
A. SYN packet
B. ACK packet
C. NAK packet
D. SYN/ACK packet
16. Which one of the following vulnerabilities would best be countered by adequate parameter checking?
A. Time-of-check-to-time-of-use
B. Buffer overflow
C. SYN flood
D. Distributed denial of service
17. What is the value of the logical operation shown here?
X: 0 1 1 0 1 0 Y: 0 0 1 1 0 1 X ⊕ Y: ?
A. 0 1 1 1 1 1 B. 0 1 1 0 1 0
C. 0 0 1 0 0 0
xxxviii Assessment Test
18. In what type of cipher are the letters of the plain-text message rearranged to form the cipher text?
A. Substitution cipher
B. Block cipher
C. Transposition cipher
D. One-time pad
19. What is the length of a message digest produced by the MD5 algorithm?
A. 64 bits B. 128 bits
C. 256 bits
D. 384 bits
20. If Renee receives a digitally signed message from Mike, what key does she use to verify that the message truly came from Mike?
A. Renee’s public key
B. Renee’s private key
C. Mike’s public key
D. Mike’s private key
21. Which of the following statements is true?
A. The less complex a system, the more vulnerabilities it has. B. The more complex a system, the less assurance it provides.
C. The less complex a system, the less trust it provides.
D. The more complex a system, the less attack surface it generates.
22. Ring 0, from the design architecture security mechanism known as protection rings, can also be referred to as all but which of the following:
A. privileged mode
B. supervisory mode
C. system mode
D. user mode
23. Which of the following is not a composition theory related to security models?
A. Cascading B. Feedback
C. Iterative
Assessment Test xxxix
24. Which level of Trusted Computer System Security Criteria (TCSEC) required that the evaluated system have mandatory access controls?
A. C2
B. B1
C. D
D. C1
25. Audit trails, logs, CCTV, intrusion detection systems, antivirus software, penetration testing, password crackers, performance monitoring, and cyclic redundancy checks (CRCs) are examples of what?
A. Directive controls B. Preventive controls
C. Detective controls
D. Corrective controls
26. System architecture, system integrity, covert channel analysis, trusted facility management and trusted recovery are elements of what security criteria?
A. Quality assurance
B. Operational assurance
C. Life cycle assurance
D. Quantity assurance
27. Which of the following is a procedure designed to test and perhaps bypass a system’s security controls?
A. Logging usage data
B. War dialing
C. Penetration testing
D. Deploying secured desktop workstations
28. Auditing is a required factor to sustain and enforce what?
A. Accountability
B. Confidentiality
C. Accessibility
D. Redundancy
29. What is the formula used to compute the ALE?
A. ALE = AV * EF B. ALE = ARO * EF
C. ALE = AV * ARO
xl Assessment Test
30. What is the first step of the business impact assessment process?
A. Identification of priorities
B. Likelihood assessment C. Risk identification
D. Resource prioritization
31. Which of the following represent natural events that can pose a threat or risk to an organization?
A. Earthquake
B. Flood
C. Tornado D. All of the above
32. What kind of recovery facility enables an organization to resume operations as quickly as possible, if not immediately upon failure of the primary facility?
A. Hot site
B. Warm site C. Cold site
D. All of the above
33. What law allows ISPs to voluntarily provide government investigators with a large range of user information without a warrant?
A. Electronic Communications Privacy Act B. Gramm-Leach-Bliley Act
C. USA PATRIOT Act
D. Privacy Act of 1974
34. In the United States, how are the administrative determinations of federal agencies promulgated?
A. Code of Federal Regulations
B. United States Code C. Supreme Court decisions
D. Administrative declarations
35. Why are military and intelligence attacks among the most serious computer crimes?
A. The use of information obtained can have far-reaching detrimental strategic effect on national interests in an enemy’s hands.
B. Military information is stored on secure machines, so a successful attack can be embarrassing.
C. The long-term political use of classified information can impact a country’s leadership. D. The military and intelligence agencies have ensured that the laws protecting their
Assessment Test xli
36. What type of detected incident allows the most time for an investigation?
A. Compromise
B. Denial of service C. Malicious code
D. Scanning
37. If you want to restrict access to one direction within a facility, which would you choose?
A. Gate
B. Turnstile
C. Fence D. Mantrap
38. What is the point of a secondary verification system?
A. To verify the identity of a user
B. To verify the activities of a user
C. To verify the completeness of a system
xlii Answers to Assessment Test
Answers to Assessment Test
1. C. Detective access controls are used to discover (and document) unwanted or unautho-rized activity. For more information, please see Chapter 1.
2. D. Strong password choices are difficult to guess, unpredictable, and of specified minimum lengths to ensure that password entries cannot be computationally determined. They may be randomly generated and utilize all the alphabetic, numeric, and punctuation characters; they should never be written down or shared; they should not be stored in publicly accessible or generally readable locations; and they shouldn’t be transmitted in the clear. For more infor-mation, please see Chapter 1.
3. B. Network-based IDSs are usually able to detect the initiation of an attack or the ongoing attempts to perpetrate an attack (including DoS). They are, however, unable to provide informa-tion about whether an attack was successful or which specific systems, user accounts, files, or appli-cations were affected. Host-based IDSs have some difficulty with detecting and tracking down DoS attacks. Vulnerability scanners don’t detect DoS attacks; they test for possible vulnerabilities. Penetration testing may cause a DoS or test for DoS vulnerabilities, but it is not a detection tool. For more information, please see Chapter 2.
4. B. Not all instances of DoS are the result of a malicious attack. Errors in coding OSs, services, and applications have resulted in DoS conditions. Some examples of this include a process failing to release control of the CPU or a service consuming system resources out of proportion to the service requests it is handling. Social engineering and sniffing are typically not considered DoS attacks. For more information, please see Chapter 2.
5. A. Network hardware devices, including routers, function at layer 3, the Network layer. For more information, please see Chapter 3.
6. D. Dynamic packet-filtering firewalls enable the real-time modification of the filtering rules based on traffic content. For more information, please see Chapter 3.
7. D. A VPN link can be established over any other network communication connection. This could be a typical LAN cable connection, a wireless LAN connection, a remote access dial-up connection, a WAN link, or even an Internet connection used by a client for access to the office LAN. For more information, please see Chapter 4.
8. D. Email is the most common delivery mechanism for viruses, worms, Trojan horses, docu-ments with destructive macros, and other malicious code. For more information, please see Chapter 4.
9. D. The components of the CIA Triad are confidentiality, availability, and integrity. For more information, please see Chapter 5.
10. B. Privacy is not necessary to provide accountability. For more information, please see Chapter 5.
Answers to Assessment Test xliii
12. B. The data owner must first assign a security label to a resource before the data custodian can secure the resource appropriately. For more information, please see Chapter 6.
13. C. The Managed phase of the SW-CMM involves the use of quantitative development metrics. The Software Engineering Institute (SEI) defines the key process areas for this level as Quantitative Pro-cess Management and Software Quality Management. For more information, please see Chapter 7.
14. B. Layers 1 and 2 contain device drivers but are not normally implemented in practice. Layer 0 always contains the security kernel. Layer 3 contains user applications. Layer 4 does not exist. For more information, please see Chapter 7.
15. B. The SYN packet is first sent from the initiating host to the destination host. The destination host then responds with a SYN/ACK packet. The initiating host sends an ACK packet, and the connection is then established. For more information, please see Chapter 8.
16. B. Parameter checking is used to prevent the possibility of buffer-overflow attacks. For more information, please see Chapter 8.
17. A. The ⊕ symbol represents the OR function, which is true when one or both of the input bits
are true. For more information, please see Chapter 9.
18. C. Transposition ciphers use an encryption algorithm to rearrange the letters of the plain-text message to form a cipher-text message. For more information, please see Chapter 9.
19. B. The MD5 algorithm produces a 128-bit message digest for any input. For more informa-tion, please see Chapter 10.
20. C. Any recipient can use Mike’s public key to verify the authenticity of the digital signature. For more information, please see Chapter 10.
21. B. The more complex a system, the less assurance it provides. More complexity means more areas for vulnerabilities exist and more areas must be secured against threats. More vulnera-bilities and more threats mean that the subsequent security provided by the system is less trust-worthy. For more information, please see Chapter 11.
22. D. Ring 0 has direct access to the most resources, thus user mode is not an appropriate label as user mode requires restrictions to limit access to resources. For more information, please see Chapter 11.
23. C. Iterative is not one of the composition theories related to security models. Cascading, feedback, and hookup are the three composition theories. For more information, please see Chapter 12.
24. B. The B1 level is the level that requires mandatory access controls. Other levels that require this are B2, B3, and A1. D, C1, and C2 do not require MAC. For more information, please see Chapter 12.
25. C. Examples of detective controls are audit trails, logs, CCTV, intrusion detection systems, antivirus software, penetration testing, password crackers, performance monitoring, and CRCs. For more information, please see Chapter 13.
xliv Answers to Assessment Test
27. C. Penetration testing is the attempt to bypass security controls to test overall system security. For more information, please see Chapter 14.
28. A. Auditing is a required factor to sustain and enforce accountability. For more information, please see Chapter 14.
29. C. The annualized loss expectancy (ALE) is computed as the product of the asset value (AV) times the annualized rate of occurrence (ARO). The other formulas displayed here do not accu-rately reflect this calculation. For more information, please see Chapter 15.
30. A. Identification of priorities is the first step of the business impact assessment process. For more information, please see Chapter 15.
31. D. Natural events that can threaten organizations include earthquakes, floods, hurricanes, tornados, wildfires, and other acts of nature as well. Thus A, B, and C are correct because they are natural and not man-made. For more information, please see Chapter 16.
32. A. A is correct, because hot sites provide backup facilities maintained in constant working order and fully capable of taking over business operations. Neither warm sites nor cold sites are cor-rect. Warm sites consist of preconfigured hardware and software to run the business, which pos-sess none of the vital business information. Cold sites are simply facilities designed with power and environmental support systems, but no configured hardware, software, or services. Disaster recovery services can facilitate and implement any of these sites on behalf of a company. For more information, please see Chapter 16.
33. C. The USA PATRIOT Act granted broad new powers to law enforcement, including the solicitation of voluntary ISP cooperation. For more information, please see Chapter 17.
34. A. Administrative determinations of federal agencies are published as the Code of Federal Regulations. For more information, please see Chapter 17.
35. A. The purpose of a military and intelligence attack is to acquire classified information. The detrimental effect of using such information could be nearly unlimited in the hands of an enemy. Attacks of this type are launched by very sophisticated attackers. It is often very diffi-cult to ascertain what documents were successfully obtained. So when a breach of this type occurs, you sometimes cannot know the full extent of the damage. For more information, please see Chapter 18.
36. D. Scanning incidents are generally reconnaissance attacks. The real damage to a system comes in the subsequent attacks, so you may have some time to react if you detect the scanning attack early. For more information, please see Chapter 18.
37. B. A turnstile is a form of gate that prevents more than one person from gaining entry at a time and often restricts movement in one direction. It is used to gain entry but not exit, or vice versa. For more information, please see Chapter 19.
Chapter
1
Accountability and
Access Control
THE CISSP EXAM TOPICS COVERED IN THIS
CHAPTER INCLUDE:
Access Control Overview
Accountability Overview
Access Control Techniques
Access Control Models
Access Control Administration
Identification and Authentication Techniques
The Access Control Systems and Methodology domain of the Common Body of Knowledge (CBK) for the CISSP certification exam deals with topics and issues related to monitoring, identi-fying, and authorizing or restricting user access to resources. Generally, an access control is any hardware, software, or organizational administrative policy or procedure that grants or restricts access, monitors and records attempts to access, identifies users attempting to access, and determines whether access is authorized.
In this chapter and in Chapter 2, “Attacks and Monitoring,” we discuss the Access Control Systems and Methodology domain. Be sure to read and study the materials from both chapters to ensure complete coverage of the essential material for this domain of the CISSP certification exam. We’ve called this chapter “Accountability and Access Control” because accountability and access control are interrelated concepts and share overlapping principles even though newer CISSP course materials reference only access control.
Access Control Overview
Controlling access to resources is one of the central themes of security. Access control addresses more than just controlling which users can access which files or services. Access control is about the relationships between subjects and objects. The transfer of information from an object to a sub-ject is called access. However, access is not just a logical or technical concept; don’t forget about the physical realm where access can involve disclosure, use, or proximity. A foundational principle of access control is to deny access by default if access to a subject is not granted explicitly.
Subjects are active entities that, through the exercise of access, seek information about or data from passive entities, or objects. A subject can be a user, program, process, file, computer, database, and so on. An object can be a file, database, computer, program, process, file, printer, storage media, and so on. The subject is always the entity that receives information about or data from the object. The subject is also the entity that alters information about or data stored within the object. The object is always the entity that provides or hosts the information or data. The roles of subject and object can switch back and forth while two entities, such as a program and a data-base interacting with a process and a file, communicate to accomplish a task.