I. The Origins of Blockchain
This chapter explores the historical context and evolution of blockchain technology, examining its development from traditional ledger systems to its current decentralized form. The authors trace the progression of record-keeping methods, highlighting the limitations of centralized systems and the need for a more secure, transparent, and efficient alternative. The chapter emphasizes the shift from centralized trust models to decentralized consensus mechanisms, illustrating the pivotal role of technological innovation in achieving this transition. The narrative uses visual aids such as figures illustrating the evolution of bookkeeping from Paleolithic methods to modern computerized accounting, effectively showcasing the historical progression and the challenges addressed by blockchain.
1.1 The Evolution of the Ledger: The Rise and Fall of the Account Book
This subsection details the evolution of bookkeeping from its rudimentary forms in Paleolithic times, through various stages involving pictorial representations, knotted cords, and finally, the double-entry bookkeeping system. The authors use numerous illustrations (Figs. 1-1 to 1-8) to visually represent these historical stages, emphasizing the inherent limitations of centralized systems and the challenges of ensuring accuracy and trust. The section culminates in the introduction of blockchain as a distributed ledger technology, contrasting its decentralized nature with the vulnerabilities of prior systems. This section provides a valuable historical context for understanding the innovative aspects of blockchain.
1.2 Value Transfer: What to Expect After the Internet
This section contrasts the limitations of the internet in handling value transfer with the capabilities of blockchain. The authors explain how the internet excels at information dissemination but lacks a secure mechanism for verifiable value transfer, highlighting the reliance on centralized third-party intermediaries and the inherent risks involved. The introduction of blockchain as a peer-to-peer value transfer network is presented, emphasizing its role in establishing trust and reducing the need for intermediaries. Figures (Figs 1-9 to 1-13) illustrate the contrast between centralized and decentralized systems and the advantages of blockchain’s transparency and security in handling value transfer. This section demonstrates the unique application of blockchain beyond simple data storage.
1.3 Credit Cost: How Many Faces Can You Remember?
This section discusses the concept of trust and its limitations in traditional systems. The authors draw parallels between the limited capacity for trust in small tribal societies and the challenges posed by information asymmetry in modern financial transactions. The discussion focuses on the cost of maintaining trust, using the Ezubao scandal as a case study to illustrate the failures of centralized systems. The introduction of blockchain as a mechanism for establishing 'intelligent trust' is presented, with examples of its application in resolving issues of property rights and financial integrity (Figs 1-14 to 1-20). The pedagogical value lies in highlighting the limitations of traditional trust mechanisms and the potential of blockchain to resolve them.
1.4 Technical Innovation: From Bitcoin to Blockchain
This subsection focuses on the technical origins of blockchain within the context of Bitcoin's development. The authors describe Satoshi Nakamoto's seminal work and the fundamental principles behind Bitcoin's design, emphasizing its solution to the double-spending problem. They explain how blockchain emerged as the underlying technology supporting Bitcoin, detailing its core functionalities and its broader applications beyond cryptocurrency. Figures (Figs. 1-21 and 1-22) visualize the emergence of Bitcoin and its ongoing smooth operation, establishing the technological foundation of blockchain and its historical context. This section provides a solid technical introduction to the workings of blockchain.
II. The Theory: Consensus Creates Coded Trust
This chapter delves into the theoretical underpinnings of blockchain technology, explaining its core concepts in an accessible manner. The authors employ analogies and storytelling techniques to illustrate the complexities of distributed ledgers and consensus mechanisms. The chapter emphasizes the importance of understanding decentralization, the role of consensus in maintaining data integrity, and the mechanisms that prevent tampering or manipulation. The use of relatable examples and visual aids makes complex concepts easily digestible for a broad audience. The chapter also addresses potential challenges and limitations within the blockchain ecosystem, fostering a critical understanding of its strengths and weaknesses.
2.1 What is Blockchain?
This section provides a simplified definition of blockchain, using the analogy of a distributed ledger to explain its core functionality. The authors compare and contrast centralized and decentralized systems, illustrating the vulnerabilities of centralized structures and the resilience of decentralized approaches. The discussion of ‘consensus’ mechanisms and the role of multiple nodes in maintaining data integrity is crucial. The concept is further clarified with the use of examples such as a virtual city with five residents, demonstrating how consensus is reached and maintained without a central authority (Figs 2-1 to 2-9). This makes abstract concepts more tangible and easily understandable.
2.2 Centralization and Decentralization
This subsection contrasts centralized and decentralized systems using real-world examples like online book purchases. The reliance on third-party intermediaries in centralized systems, like Alipay, is highlighted, demonstrating their potential points of failure. The section uses visuals (Figs 2-5 and 2-6) to illustrate how the failure of a central node can disrupt the entire transaction process. This provides a contrast with the resilience of decentralized blockchain systems, which distribute trust and responsibility across multiple nodes, enhancing security and reliability. This section is crucial for understanding the fundamental difference between traditional and blockchain-based systems.
2.3 A Virtual City Running as Blockchain
This subsection utilizes a hypothetical scenario of a small city using a blockchain-like system for transactions. It explains how individuals record transactions on their own ledgers, creating a distributed record that is resistant to tampering. The authors introduce the concept of a reward mechanism (akin to Bitcoin mining) that incentivizes participation in record-keeping. This example illustrates the principles of decentralization and consensus in a simple and effective way, making complex blockchain operations more approachable (Figs. 2-7 to 2-9). This section leverages a compelling narrative to make the technical aspects more accessible.
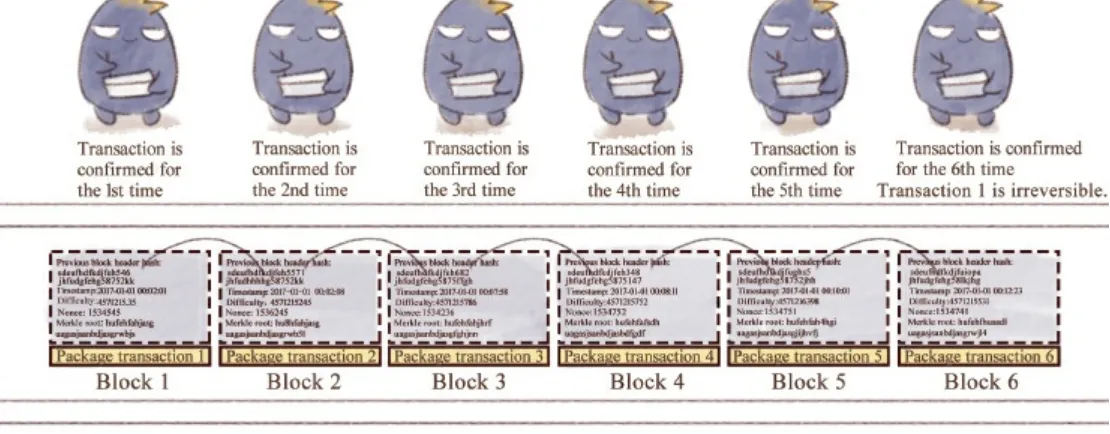
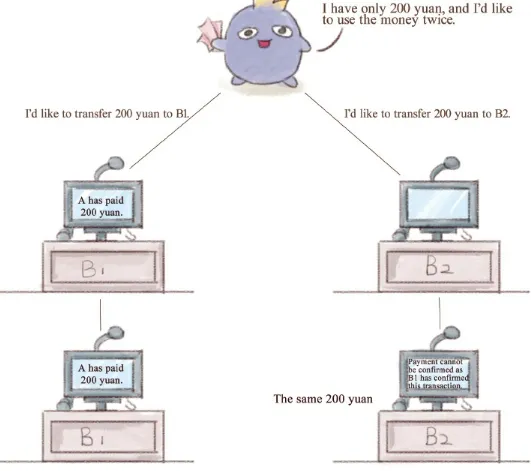
2.4 A Few Problems in Small Cities
This section addresses potential challenges and limitations of blockchain systems using the virtual city analogy. It discusses issues such as forking (multiple competing versions of the ledger) and double spending. The discussion of solutions to these problems, such as prioritizing longer chains and implementing sophisticated cryptographic mechanisms, offers a realistic perspective on the complexities of blockchain technology. Figs 2-10 to 2-14 illustrate the complexities involved in maintaining consistency and security in a decentralized system, which are essential for learners to grasp the challenges inherent in this technology.