Windows Server 2008: The Definitive Guide by Jonathan Hassell
Publisher: O'Reilly
Pub Date: March 15, 2008
Print ISBN-13: 978-0-59-651411-2 Pages: 492
Table of Contents | Index
Overview
This practical guide has exactly what you need to work with Windows Server 2008. Inside, you'll find step-by-step
procedures for using all of the major components, along with discussions on complex concepts such as Active Directory replication, DFS namespaces and replication, network access protection, the Server Core edition, Windows PowerShell, server clustering, and more. All of this with a more compact
presentation and a tighter focus on tasks than you'll find in bulkier references. Windows Server 2008: The Definitive Guide takes a refreshing approach. You won't find the history of
Windows NT, or discussions on the way things used to work. Instead, you get only the information you need to use this server. If you're a beginning or intermediate system
administrator, you learn how the system works, and how to administer machines running it. The expert administrators among you discover new concepts and components outside of your realm of expertise. Simply put, this is the most thorough reference available for Windows Server 2008, with complete guides to:
Installing the server in a variety of different environments File services and the Windows permission structure
Active Directory, including its logical and physical structure, hierarchical components, scalability, and replication
Group Policy's structure and operation
Managing security policy with predefined templates and customized policy plans
Architectural improvements, new features, and daily administration of IIS 7
Terminal Services from both the administrator's user's point of view
Networking architecture including DNS, DHCP, VPN, RADIUS server, IAS, and IPSec
Windows clustering services --- applications, grouping machines, capacity and network planning, user account management
Windows PowerShell scripting and command-line technology
With Windows Server 2008: The Definitive Guide, you to come away with a firm understanding of what's happening under the hood, but without the sense that you're taking a graduate
Windows Server 2008: The Definitive Guide by Jonathan Hassell
Publisher: O'Reilly
Pub Date: March 15, 2008
Print ISBN-13: 978-0-59-651411-2 Pages: 492
Table of Contents | Index
Preface
Chapter 1. Introducing Windows Server 2008 Section 1.1. The Biggest Changes
Section 1.2. Networking Improvements Section 1.3. Security Improvements
Section 1.4. Manageability Improvements
Section 1.5. Performance and Reliability Upgrades Section 1.6. Windows Server 2008 Editions
Section 1.7. Hardware Requirements Section 1.8. The Last Word
Chapter 2. Installation and Deployment
Section 2.1. Installing Windows Server 2008 Section 2.2. Initial Configuration Tasks
Section 2.3. Deployment Section 2.4. The Last Word Chapter 3. File Services
Section 3.1. File and Print Server Features Section 3.2. Setting Up File Sharing Services Section 3.3. NTFS File and Folder Permissions Section 3.4. The File Server Resource Manager Section 3.5. Disk-Based Quotas
Section 3.8. The Distributed File System Section 3.9. Command-Line Utilities Section 3.10. The Last Word
Chapter 4. Domain Name System Section 4.1. Nuts and Bolts
Section 4.2. Zones Versus Domains Section 4.3. Resource Records
Section 4.4. Using Primary and Secondary Nameservers Section 4.5. Building a Nameserver
Section 4.6. Subdomains and Delegation Section 4.7. Dynamic DNS
Section 4.8. Active Directory-Integrated Zones Section 4.9. Forwarding
Section 4.10. The Split DNS Architecture Section 4.11. Backup and Recovery
Section 4.12. Command-Line Utilities Section 4.13. The Last Word
Chapter 5. Active Directory
Section 5.1. Active Directory Domain Services Objects and Concepts
Section 5.2. Building an AD DS Structure
Section 5.3. Understanding Operations Master Roles Section 5.4. Understanding Directory Replication Section 5.5. Active Directory Troubleshooting and Maintenance
Section 5.6. The Last Word
Chapter 6. Group Policy and IntelliMirror
Section 6.1. An Introduction to Group Policy Section 6.2. Group Policy Implementation Section 6.3. Local Group Policy
Section 6.4. Domain Group Policy
Section 6.6. Troubleshooting Group Policy
Section 6.7. Other Group Policy Management Tools Section 6.8. Command-Line Utilities
Section 6.9. The Last Word
Chapter 7. Windows Security and Patch Management Section 7.1. Understanding Security Considerations Section 7.2. Locking Down Windows
Section 7.3. Using Auditing and the Event Log Section 7.4. The Last Word
Chapter 8. Internet Information Services 7 Section 8.1. Major Improvements
Section 8.2. The New Architecture Section 8.3. Roles
Section 8.4. Managing IIS Graphically
Section 8.5. Managing IIS from the Command Line Section 8.6. The Last Word
Chapter 9. Windows Server 2008 Server Core Section 9.1. The Lack of a Shell
Section 9.2. Realistic Deployment Scenarios Section 9.3. No Managed Code
Section 9.4. Few Third-Party Software Applications Section 9.5. Installation
Section 9.6. Initial Configuration
Section 9.7. Administering Windows Server 2008 Server Core Machines
Section 9.8. The Last Word Chapter 10. Terminal Services
Section 10.1. The Remote Desktop Protocol Section 10.2. Adding the Terminal Server Role Section 10.3. Enabling Remote Desktop
Section 10.4. On the User's Side
Section 10.6. Terminal Services RemoteApp Section 10.7. Terminal Services Web Access Section 10.8. Terminal Services Gateway Section 10.9. Command-Line Utilities Section 10.10. The Last Word
Chapter 11. DHCP and Network Access Protection Section 11.1. Dynamic Host Configuration Protocol Section 11.2. Network Access Protection
Section 11.3. The Last Word
Chapter 12. An Introduction to Clustering Technologies Section 12.1. Network Load-Balancing Clusters
Section 12.2. Server Clustering
Section 12.3. Command-Line Utilities Section 12.4. The Last Word
Chapter 13. PowerShell
Section 13.1. Why PowerShell? Section 13.2. Installing PowerShell Section 13.3. PowerShell and Security Section 13.4. Starting Up PowerShell
Section 13.5. Cmdlets: The Heart of PowerShell Section 13.6. Getting Help with PowerShell
Section 13.7. Using Data Stores and PowerShell Providers Section 13.8. The Pipeline
Section 13.9. Formatting Basics Section 13.10. Variables
Section 13.11. Writing Scripts
Section 13.12. Objects: .NET, WMI, and COM Section 13.13. Advanced PowerShell
Section 13.14. Learning More About PowerShell Section 13.15. The Last Word
Chapter 14. Hyper-V
Section 14.2. Getting Started with Hyper-V Section 14.3. Virtualization Strategy
Section 14.4. The Last Word Colophon
Windows Server 2008: The Definitive Guide by Jonathan Hassell
Copyright © 2008 Jonathan Hassell. All rights reserved. Printed in the United States of America.
Published by O'Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472.
O'Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (safari.oreilly.com). For more information, contact our corporate/institutional sales department: (800) 998-9938 or [email protected].
Editor: John Osborn
Production Editor: Rachel Monaghan
Copyeditor: Colleen Gorman
Proofreader: Rachel Monaghan
Indexer: Lucie Haskins
Cover Designer: Karen Montgomery
Interior Designer: David Futato
Illustrator: Jessamyn Read
Printing History:
March 2008: First Edition.
Nutshell Handbook, the Nutshell Handbook logo, and the
Windows Server 2008: The Definitive Guide, the image of an albatross, and related trade dress are trademarks of O'Reilly Media, Inc.
Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O'Reilly Media, Inc. was aware of a trademark claim, the designations have been printed in caps or initial caps.
While every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for
errors or omissions, or for damages resulting from the use of the information contained herein.
This book uses RepKover™, a durable and flexible lay-flat binding.
Preface
Microsoft's server-oriented Windows operating systems have grown by leaps and bounds in capabilities, complexities, and sheer number of features since the release of Windows NT Server in the early 1990s. With each release, system
administrators have found themselves grappling with new
concepts, from domains, directory services, and virtual private networks, to client quarantining, disk quota, and universal
groups. Just when you've mastered one set of changes, another comes along and suddenly you're scrambling once again to get up to speed. A vicious cycle this IT business is.
One source of help for the beleaguered administrator has
always been the technical book market and its communities of authors, publishers, and user groups. Major releases of popular operating systems have always been accompanied by the
publication of books written to support them, often encouraged by the software manufacturers. Some tout themselves as
complete guides to their software compadres, while others
approach their subject gingerly, as though their readers were of a questionable intellectual capacity. But over the years, many of these books have become as complex, and have accumulated as much detritus, as the operating systems they explain. You now see on the shelves of your friendly local bookstores 1,200-plus-page monstrosities that you might find useful, but only if you enjoy dealing with 30 pounds of paper in your lap or on your desk, and only if you find it productive to wade through references to "how things worked" four versions of Windows NT ago. After all, there's a limit to how many times you can revise something before it's best to simply start from scratch. Do you need all of that obsolete information to do your job efficiently? I'm wagering that you don't (my luck in Las Vegas
systems work in this version of Windows. I want you to come away from reading sections with a firm understanding of what's happening under the hood of the system, but without the sense that you're taking a graduate course in OS theory. Most of all, I want this book to be a practical guide that helps you get your work done—"here's how it works; here's how to do it."
The book you're either holding in your hands right now or reading online provides a more compact presentation, a lower price, and a tighter focus on tasks than other books on the market.
I hope that this work meets your expectations, and I hope you turn to it again and again when you need to understand the massive product that is Windows Server 2008.
P2.1. Audience
Beginning-to-intermediate system administrators will find this book a very helpful reference to learning how Windows Server 2008 works and the different ways to administer machines running that operating system. This book has step-by-step procedures, discussions of complex concepts such as Active Directory replication, DFS namespaces and replication, network access protection, the Server Core edition, Windows
PowerShell, and server clustering. Although I've eliminated material that isn't relevant to day-to-day administration, you will still find the chapters full of useful information.
Advanced system administrators will also find this book useful for discovering new concepts and components outside of their realm of expertise. I've found that senior system administrators often focus on one or two specific areas of a product and are less familiar with other areas of the OS. This book provides a stepping-stone for further exploration and study of secondary parts of the operating system.
cases, as opposed to) graphical ways to accomplish tasks. Command lines, in my opinion, are fabulous for quickly and efficiently getting things done, and they provide a great basis for launching into scripting repetitive tasks. Microsoft has done an excellent job of integrating command-line functions into this revision of Windows, and I've attempted to do the effort justice within the text. But none of this should make you shy away from this book if you are a GUI aficionado: you'll still find everything you're accustomed to within this volume.
P2.2. Organization and Structure
In structuring the contents of this book I have tried to make a logical progression through the product, from a high-level
overview through complete discussions and treatments of all its major components. Here's how this book is organized:
Chapter 1
Covers the product on a very general basis, from Microsoft's philosophy behind the product itself and the different
versions of the product that are available, to an overview of the features in this release that are new or otherwise
improved and a complete overview of the system design. This chapter is designed to give the administrator a
complete and systematic overview of the product.
Chapter 2
Provides a detailed guide to installing the product in a
variety of environments. I also include information on mass deployments using Windows Deployment Services, a vast improvement over previous image installation options offered in the box.
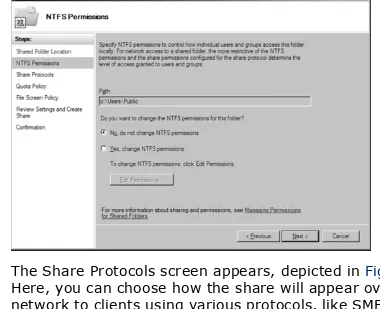
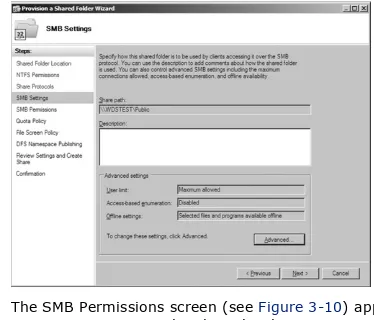
Discusses the file services built into Windows Server 2008. The chapter begins with an overview of sharing and a guide to creating shares, publishing them to Active Directory, mapping drives, using the My Network Places applet, and accessing shares from the Start Run command and from within Internet Explorer. Then I dive into a detailed
discussion of the Windows permission structure, including permission levels, "special" permissions, inheritance, and ownership. Here, you'll also find a guide to settings
permissions. Also covered in this chapter is an overview of the Distributed File System (DFS), and how to set it up and manage it.
Chapter 4
Covers the domain name system, or DNS. Because DNS is such a fundamental component of Active Directory, I
wanted to include a separate treatment of how it works, including a discussion of the different types of resource records and zone files supported, integration with Active Directory, the split DNS architecture, and backup and recovery of DNS data.
Chapter 5
Most installations of Windows Server 2008 will include installation of the Active Directory technology because so many products that require the server OS are tightly integrated with Active Directory. Chapter 5 provides a
strategies, installing Active Directory onto Windows Server, and the day-to-day administrative tools.
Chapter 6
Discusses Group Policy (GP), one of the most
underappreciated management technologies in any server product. Chapter 6 is dedicated to introducing GP and its structure and operation. I begin with a survey of GP and Active Directory interaction, objects, and inheritance. Then I provide a practical guide to implementing GP through user and computer policies and administrative templates,
installing software through GP, administration through scripting, and redirecting folders and other user interface elements. I also discuss IntelliMirror, a cool technology for application distribution (similar to ZENworks from Novell).
Chapter 7
Helps ensure that you are well versed in locking down your systems to protect both your own computers and the
Internet community as a whole. I cover security policy,
including ways to manage it using predefined templates and customized policy plans, and an overview of the Security Configuration and Analysis Tool, or SCAT. Then I provide a complete procedural guide to locking down both a Windows network server and a standard Windows client system
(despite the fact that this is a server book, administrators often are responsible for the entire network, and client and server security go hand in hand).
Chapter 8
In version 7, IIS is arguably the best web server software available. I cover the architectural improvements and new features in this release, and then move on to a practical discussion of daily IIS administration.
Chapter 9
Covers the new Server Core editions of Windows Server 2008, including deployment, activation, and using these new GUI-less versions of the operating system.
Chapter 10
Provides a guide to Terminal Services, including an overview from the server administrator's perspective and a similar overview from a typical user's point of view. Then I cover how to install both Terminal Services itself and applications such as Microsoft Office and other tools inside the Terminal Services environment. A guide to configuring Terminal
Services follows, including procedures for general
configuration, remote control options, environment settings, logons, sessions, and permission control. Concluding the chapter is a guide to daily administration using Terminal Services Manager, the Active Directory user tools, Task Manager, and command-line utilities.
Chapter 11
Covers the standard networking architecture of the
operating system, including addressing and routing issues. Then I move into a discussion of the various network
encryption, and the RADIUS server bundled with .NET
Server, the Internet Authentication Service (IAS). Finishing up the chapter, I discuss IPSec, its support from within the OS, and how to install, configure, use, and administer it. Coverage of client quarantining is also included.
Chapter 12
Covers Windows clustering services. First, a discussion of the different types of clustering services is provided, and then I cover successfully planning a basic cluster and its different elements: the applications, how to group the machines, capacity and network planning, user account management, and the possible points of failure. A
treatment of Network Load Balancing clusters follows, and I round out the chapter with a guide to creating and
managing server clusters, as well as an overview of the administrative tools bundled with the OS.
Chapter 13
Discusses Windows PowerShell, the powerful object-based scripting and command-line technology now bundled with Windows Server 2008.
Chapter 14
Covers the fundamentals of Microsoft's currently prerelease virtualization solution called Hyper-V, including its structure, operation, and setup on Windows Server 2008. We'll also look at creating virtual machines, and we'll wrap up with what to expect upon Hyper-V's official release.
The following typographical conventions are used in this book.
Plain text
Indicates menu titles, menu options, menu buttons, and keyboard accelerators (such as Alt and Ctrl).
Italic
Indicates new terms, URLs, email addresses, filenames, file extensions, pathnames, directories, and command-line utilities.
Constant width
Indicates commands, options, switches, variables,
attributes, keys, functions, types, classes, namespaces, methods, modules, properties, parameters, values, objects, events, event handlers, XML tags, HTML tags, macros, the contents of files, or the output from commands.
Constant width bold
Shows commands or other text that should be typed literally by the user.
Constant width italic
This icon signifies a tip, suggestion, or general note.
This icon indicates a warning or caution.
P2.4. Using Code Examples
This book is here to help you get your job done. In general, you can use the code in this book in your programs and
documentation. You do not need to contact O'Reilly for
permission unless you're reproducing a significant portion of the code. For example, writing a program that uses several chunks of code from this book does not require permission. Selling or distributing a CD-ROM of examples from O'Reilly books does require permission. Answering a question by citing this book and quoting example code does not require permission.
Incorporating a significant amount of example code from this book into your product's documentation does require
permission.
O'Reilly appreciates, but does not require, attribution. An attribution usually includes the title, author, publisher, and ISBN. For example: "Windows Server 2008: The Definitive Guide by Jonathan Hassell. Copyright 2008 Jonathan Hassell, 978-0-596-51411-2."
If you feel your use of code examples falls outside fair use or the permission given above, feel free to contact O'Reilly at [email protected].
P2.5. We'd Like to Hear from You
the publisher:
O'Reilly Media, Inc.
1005 Gravenstein Highway North Sebastopol, CA 95472
800-998-9938 (in the United States or Canada) 707-829-0515 (international or local)
707-829-0104 (fax)
O'Reilly has a web page for this book, where it lists errata, examples, and any additional information. You can access this page at:
http://www.oreilly.com/catalog/9780596514112
To comment or ask technical questions about this book, send email to:
For more information about our books, conferences, Resource Centers, and the O'Reilly Network, see the O'Reilly web site at:
http://www.oreilly.com
P2.6. Safari® Books Online
When you see a Safari® Books Online icon on the cover of your favorite technology book, that means the book is available
online through the O'Reilly Network Safari Bookshelf.
Safari offers a solution that's better than e-books. It's a virtual library that lets you easily search thousands of top tech books, cut and paste code samples, download chapters, and find quick answers when you need the most accurate, current information. Try it for free at http://safari.oreilly.com.
I've always liked the fact that the acknowledgments in technical books are typically in the front. That way, when you read the remainder of the book, you already know who to thank for it, unlike in a movie. So, without further ado:
John Osborn at O'Reilly was instrumental in getting this process organized and off the ground and provided very welcome
guidance and feedback during the initial stages of writing this book.
Errors and shortcomings were dutifully found by the technical review team, which consisted of IT professionals Dan Green, Eric Rezabek, and Debbie Timmons.
Special thanks to the many folks at Microsoft and Waggener-Edstrom with whom I worked during the development of the book—their assistance and timely information was quite helpful in putting together this project.
Of course, my family is also to thank: particularly my wife, Lisa, who patiently accepted the insufficient answer of "not yet"
Chapter 1. Introducing Windows Server
2008
It all started with Windows NT, Microsoft's first serious entry into the network server market. Versions 3.1 and 3.5 of
Windows NT didn't garner very much attention in a NetWare-dominated world because they were sluggish and refused to play well with others. Along came Windows NT 4.0, which used the new Windows 95 interface (revolutionary only to those who didn't recognize Apple's Macintosh OS user interface) to put a friendlier face on some simple yet fundamental architectural improvements. With version 4.0, larger organizations saw that Microsoft was serious about entering the enterprise computing market, even if the product currently being offered was still limited in scalability and availability. For one, Microsoft made concessions to NetWare users, giving them an easy way to integrate with a new NT network. The company also included a revised security feature set, including finely grained permissions and domains, which signified that Microsoft considered
enterprise computing an important part of Windows. After a record six and one-half service packs, NT 4.0 is
considered by some to be the most stable operating system ever to come out of Redmond. However, despite that, most administrators with Unix experience required an OS more
credible in an enterprise environment—one that could compare to the enormous Unix machines that penetrated that market long ago and had unquestionably occupied it ever since. It wasn't until February 2000, when Windows 2000 Server was released, that these calls were answered. Windows 2000 was a complete revision of NT 4.0 and was designed with stability and scalability as first priorities.
infamous security problems associated with the bundled
Windows 2000 web server, Internet Information Services (IIS), cast an ominous cloud over the thought that Windows could ever be a viable Internet-facing enterprise OS. Given that many saw Microsoft as "betting the company" on a web services
initiative called .NET, it was critical that Microsoft save face and do it right the next time. It wasn't too late, but customers were very concerned about the numerous security vulnerabilities and the lack of a convenient patch management system to apply corrections to those vulnerabilities. Things had to change. From stage left, enter Windows Server 2003. What
distinguished the release other than a longer name and a three-year difference in release dates? Security, primarily. Windows Server 2003 came more secure out of the box and was heavily influenced by the month-long halt of new development in March 2002, referred to by Microsoft as the beginning of the
Trustworthy Computing Initiative, wherein all developers and product managers did nothing but review existing source code for security flaws and attend training on new best practices for writing secure code. Performance was also improved in the Windows Server 2003 release, focus was put on making the operating system scalable, and in general enterprise
administration was made more efficient and easier to automate. Microsoft also updated some bundled software via the Windows Server 2003 R2 release, making it more straightforward to
manage identities over different directory services and security boundaries, distribute files and replicate directory structures among many servers, and more.
1.1. The Biggest Changes
Unlike the transition from Windows 2000 Server to Windows Server 2003, which was a fairly minor "point"-style update, Windows Server 2008 is a radical revision to the core code base that makes up the Windows Server product. Windows Server 2008 shares quite a bit of fundamental code with Windows
Vista, which was a product derived directly from the techniques of the secure development model (SDM)—sea change in
programming methodologies at Microsoft that puts secure code at the forefront of all activity. Thus, a lot of new features and enhancements you will see in the product are a result of a more secure code base and an increased focus on system integrity and reliability.
The most radical changes to Windows Server 2008 include Server Core and the new Internet Information Services 7.0.
1.1.1. Server Core
Server Core is a minimal installation option for Windows Server 2008 that contains only a subset of executable files and server roles. Management is done through the command line or
through an unattended configuration file. According to Microsoft:
Server Core is designed for use in organizations that either have many servers, some of which need only to perform dedicated tasks but with outstanding stability, or in
environments where high security requirements require a minimal attack surface on the server.
Accordingly, there are limited roles that Core servers can perform. They are:
File server, including the file replication service, the Distributed File System (DFS), Distributed File System Replication (DFSR), the network filesystem, and single instance storage (SIS)
Print services
Domain controller, including a read-only domain controller Active Directory Lightweight Directory Services (AD LDS) server
Windows Server Virtualization
IIS, although only with a portion of its normal abilities— namely only static HTML hosting, and no dynamic web application support
Windows Media Services (WMS)
Additionally, Server Core machines can participate in Microsoft clusters, use network load balancing, host Unix applications, encrypt their drives with Bitlocker, be remotely managed using Windows PowerShell on a client machine, and be monitored through Simple Network Management Protocol, or SNMP. Most administrators will find placing Server Core machines in branch offices to perform domain controller functions is an
excellent use of slightly older hardware that might otherwise be discarded. The smaller footprint of Server Core allows the OS to do more with fewer system resources, and the reduced attack surface and stability make it an excellent choice for an
appliance-like machine. Plus, with a branch office, you can combine Server Core with the ability to deploy a read-only
domain controller and encrypt everything with BitLocker, giving you a great, lightweight, and secure solution.
1.1.2. IIS Improvements
revision in Windows Server 2008. IIS 7 is, for the first time, fully extensible and fully componentized—you only install what you want, so the service is lighter, more responsive, and less vulnerable to attack. The administrative interface for IIS has also been completely redesigned. Key improvements include:
Newly rearchitected componentized structure
For the first time in IIS history, administrators exercise complete control over exactly what pieces of IIS are installed and running at any given time. You can run the exact services you require—no more, no less. This is of course more secure, not to mention easier to manage and better performing.
Flexible extensibility model
IIS 7 allows developers to access a brand-new set of APIs that can interact with the IIS core directly, making module development and customization much easier than it ever has been. Developers can even hook into the configuration, scripting, event logging, and administration areas of IIS, which opens a lot of doors for enterprising administrators and third-party software vendors to extend IIS' capabilities sooner rather than later.
Simplified configuration and application deployment
Configuration can be accomplished entirely through XML files. Central IIS configuration can be spread across multiple files, allowing many sites and applications hosted by the same server to have independent but still easily managed configurations. One of Microsoft's favorite demos of IIS 7 is setting up a web farm with identically configured machines; as new members of the farm are brought online, the
configuration files over to the new server, and in a matter of seconds, the IIS setup on the new machine is identical to that on the existing machines. This is perhaps the most meaningful, and most welcome, change in IIS 7.
Delegated management
Much like Active Directory allows administrators to assign permissions to perform certain administrative functions to other users, IIS administrators can delegate control of some functions to other people, like site owners.
Efficient administration
Chapter 1. Introducing Windows Server
2008
It all started with Windows NT, Microsoft's first serious entry into the network server market. Versions 3.1 and 3.5 of
Windows NT didn't garner very much attention in a NetWare-dominated world because they were sluggish and refused to play well with others. Along came Windows NT 4.0, which used the new Windows 95 interface (revolutionary only to those who didn't recognize Apple's Macintosh OS user interface) to put a friendlier face on some simple yet fundamental architectural improvements. With version 4.0, larger organizations saw that Microsoft was serious about entering the enterprise computing market, even if the product currently being offered was still limited in scalability and availability. For one, Microsoft made concessions to NetWare users, giving them an easy way to integrate with a new NT network. The company also included a revised security feature set, including finely grained permissions and domains, which signified that Microsoft considered
enterprise computing an important part of Windows. After a record six and one-half service packs, NT 4.0 is
considered by some to be the most stable operating system ever to come out of Redmond. However, despite that, most administrators with Unix experience required an OS more
credible in an enterprise environment—one that could compare to the enormous Unix machines that penetrated that market long ago and had unquestionably occupied it ever since. It wasn't until February 2000, when Windows 2000 Server was released, that these calls were answered. Windows 2000 was a complete revision of NT 4.0 and was designed with stability and scalability as first priorities.
infamous security problems associated with the bundled
Windows 2000 web server, Internet Information Services (IIS), cast an ominous cloud over the thought that Windows could ever be a viable Internet-facing enterprise OS. Given that many saw Microsoft as "betting the company" on a web services
initiative called .NET, it was critical that Microsoft save face and do it right the next time. It wasn't too late, but customers were very concerned about the numerous security vulnerabilities and the lack of a convenient patch management system to apply corrections to those vulnerabilities. Things had to change. From stage left, enter Windows Server 2003. What
distinguished the release other than a longer name and a three-year difference in release dates? Security, primarily. Windows Server 2003 came more secure out of the box and was heavily influenced by the month-long halt of new development in March 2002, referred to by Microsoft as the beginning of the
Trustworthy Computing Initiative, wherein all developers and product managers did nothing but review existing source code for security flaws and attend training on new best practices for writing secure code. Performance was also improved in the Windows Server 2003 release, focus was put on making the operating system scalable, and in general enterprise
administration was made more efficient and easier to automate. Microsoft also updated some bundled software via the Windows Server 2003 R2 release, making it more straightforward to
manage identities over different directory services and security boundaries, distribute files and replicate directory structures among many servers, and more.
1.1. The Biggest Changes
Unlike the transition from Windows 2000 Server to Windows Server 2003, which was a fairly minor "point"-style update, Windows Server 2008 is a radical revision to the core code base that makes up the Windows Server product. Windows Server 2008 shares quite a bit of fundamental code with Windows
Vista, which was a product derived directly from the techniques of the secure development model (SDM)—sea change in
programming methodologies at Microsoft that puts secure code at the forefront of all activity. Thus, a lot of new features and enhancements you will see in the product are a result of a more secure code base and an increased focus on system integrity and reliability.
The most radical changes to Windows Server 2008 include Server Core and the new Internet Information Services 7.0.
1.1.1. Server Core
Server Core is a minimal installation option for Windows Server 2008 that contains only a subset of executable files and server roles. Management is done through the command line or
through an unattended configuration file. According to Microsoft:
Server Core is designed for use in organizations that either have many servers, some of which need only to perform dedicated tasks but with outstanding stability, or in
environments where high security requirements require a minimal attack surface on the server.
Accordingly, there are limited roles that Core servers can perform. They are:
File server, including the file replication service, the Distributed File System (DFS), Distributed File System Replication (DFSR), the network filesystem, and single instance storage (SIS)
Print services
Domain controller, including a read-only domain controller Active Directory Lightweight Directory Services (AD LDS) server
Windows Server Virtualization
IIS, although only with a portion of its normal abilities— namely only static HTML hosting, and no dynamic web application support
Windows Media Services (WMS)
Additionally, Server Core machines can participate in Microsoft clusters, use network load balancing, host Unix applications, encrypt their drives with Bitlocker, be remotely managed using Windows PowerShell on a client machine, and be monitored through Simple Network Management Protocol, or SNMP. Most administrators will find placing Server Core machines in branch offices to perform domain controller functions is an
excellent use of slightly older hardware that might otherwise be discarded. The smaller footprint of Server Core allows the OS to do more with fewer system resources, and the reduced attack surface and stability make it an excellent choice for an
appliance-like machine. Plus, with a branch office, you can combine Server Core with the ability to deploy a read-only
domain controller and encrypt everything with BitLocker, giving you a great, lightweight, and secure solution.
1.1.2. IIS Improvements
revision in Windows Server 2008. IIS 7 is, for the first time, fully extensible and fully componentized—you only install what you want, so the service is lighter, more responsive, and less vulnerable to attack. The administrative interface for IIS has also been completely redesigned. Key improvements include:
Newly rearchitected componentized structure
For the first time in IIS history, administrators exercise complete control over exactly what pieces of IIS are installed and running at any given time. You can run the exact services you require—no more, no less. This is of course more secure, not to mention easier to manage and better performing.
Flexible extensibility model
IIS 7 allows developers to access a brand-new set of APIs that can interact with the IIS core directly, making module development and customization much easier than it ever has been. Developers can even hook into the configuration, scripting, event logging, and administration areas of IIS, which opens a lot of doors for enterprising administrators and third-party software vendors to extend IIS' capabilities sooner rather than later.
Simplified configuration and application deployment
Configuration can be accomplished entirely through XML files. Central IIS configuration can be spread across multiple files, allowing many sites and applications hosted by the same server to have independent but still easily managed configurations. One of Microsoft's favorite demos of IIS 7 is setting up a web farm with identically configured machines; as new members of the farm are brought online, the
configuration files over to the new server, and in a matter of seconds, the IIS setup on the new machine is identical to that on the existing machines. This is perhaps the most meaningful, and most welcome, change in IIS 7.
Delegated management
Much like Active Directory allows administrators to assign permissions to perform certain administrative functions to other users, IIS administrators can delegate control of some functions to other people, like site owners.
Efficient administration
1.2. Networking Improvements
The Windows Server 2008 team has made a special effort at improving network performance and efficiency. For the first time, there is a dual-IP layer architecture for native IPv4 and IPv6 support together, simultaneously. (If you've ever
configured IPv4 and IPv6 on a Windows Server 2003 machine, you'll know what a pain it is to get them to interoperate without falling all over each other.) Communications security is
enhanced through better IPsec integration throughout the various pieces of the TCP/IP stack. Hardware is used more efficiently and robustly to speed up performance of network transmissions, intelligent tuning and optimization algorithms run regularly to ensure efficient communication, and APIs to the network stack are more directly exposed, making it easier for developers to interact with the stack. Let's take a look at some of the improvements in what the team is calling Next
Generation Networking.
1.2.1. TCP/IP Stack Enhancements
As I alluded to earlier, many changes in Windows Server 2008 were made to the TCP/IP stack itself. One such improvement is the auto-tuning TCP window size: Windows Server 2008 can automatically tune the size of the receive window by each individual connection, increasing the efficiency of large data transfers between machines on the same network. Microsoft quotes the following example: " ... on a 10 Gigabit Ethernet network, packet size can be negotiated up to 6 Megabytes in size."
The dead gateway detection algorithm present in Windows
functions from the CPU itself to the processing circuitry on the network interface card, freeing up the CPU to manage other processes.
There are also improvements to network scaling. For example, in previous versions of Windows Server, one NIC was associated with one single, physical processor. However, with the right
network card, Windows Server 2008 supports scaling NICs and their associated traffic among multiple CPUs (a feature called receive-side scaling), permitting much higher amounts of traffic to be received by one NIC on a highly loaded server. This
particularly benefits multiprocessor servers, since more scale can be added simply by adding processors or NICs and not by adding entirely new servers.
1.2.2. Changes to Terminal Services
Network applications are growing in popularity with each passing week. Windows Server 2008 sees more work in the Terminal Services/Remote Desktop area than might have been expected, and some of the new capabilities are very welcome improvements. Aside from the three new features, the team worked on improving the core processes that make TS tick, including single sign-on to Terminal Services sessions, monitor spanning and high-resolution support for sessions, integration with the Windows System Resource Manager to better monitor performance and resource usage, and themes that make TS sessions seamless to the client.
There are three key new features added in the Windows Server 2008 release. The first is Terminal Services RemoteApp. Like the functionality offered by Citrix MetaFrame years ago,
application is hosted elsewhere, except for the occasional slow response because of network latency or server overload. It's also simple to enable this functionality: administrators create .RDP files, which are essentially text-based profiles of a
Terminal Services connection that the client reads and uses to configure an RDP session for that particular program. They can also create .MSI files that can populate profiles; the main
advantage here is that .MSI files are traditionally very easy to deploy via automated system management methods like
Systems Management Server, Group Policy and IntelliMirror, and so on.
Next, there's the Terminal Services Gateway. This feature allows users to access Terminal Services-hosted applications from a web portal anywhere on the Internet, secured via an encrypted HTTPS channel. The gateway can send connections through firewalls and correctly navigate NAT translation situations that stymied the use of this technology before. This saves
corporations from having to deploy VPN access to remote users for the sole purpose of accessing a Terminal Services machine; plus, since the data is sent over HTTPS, almost anyone can
access the sessions, even at locations where the RDP protocol is blocked by the firewall. Administrators can set connection
authorization policies, or CAPs, that define user groups that are permitted to access TS through the TS Gateway machine.
Finally, in conjunction with the Terminal Services RemoteApp feature, there is also in Windows Server 2008 the TS Web Access feature, which lets administrators publicly display available TS Remote Programs on a web page. Users can
browse the list for the application they want to run, click on it, and then be seamlessly embedded in the application—using all the features of TS Remote Programs—while retaining the ability to launch other programs from the same Web Access site. The service is smart enough to know that multiple programs
sites using an included web part.
1.2.3. Active Directory: Read-Only Domain
Controllers
Windows Server 2008 introduces the concept of a read-only domain controller (RODC), which is great for branch offices and other locations where the machines hosting the domain
controller role can't be physically protected in the same way as a machine in a datacenter might be. RODCs hold a read-only copy of Active Directory, which allows for the immediate
1.3. Security Improvements
Security problems have plagued Microsoft since the Windows inception, but only in the last few years, as more people have become connected, have those flaws been exploited by
malcontents. Indeed, some of the vulnerabilities in products that we see patches for on "Patch Tuesdays" are the results of poor design decisions. These types of flaws are the ones
Microsoft is hoping to stamp out in the release of Windows
Server 2008. You'll see quite a bit of change to the architecture of services in Windows Server 2008, including increasing the number of layers required to get to the kernel, segmenting
services to reduce buffer overflows, and reducing the size of the high-risk, privileged layers to make the attack surface smaller. While fundamentally changing the design of the operating system, the Windows Server 2008 team has also included several features designed to eliminate security breaches and malware infestations, as well as capabilities meant to protect corporate data from leakage and interception. Let's take a look at some of the improvements.
1.3.1. Operating System File Protection
A new feature currently known as operating system file
protection ensures the integrity of the boot process for your servers. Windows Server 2008 creates a validation key based on the kernel file in use, a specific hardware abstraction layer (HAL) for your system, and drivers that start at boot time. If, at any subsequent boot after this key is created, these files
change, the operating system will know and halt the boot process so you can repair the problem.
(processes that are often the most sensitive to elevation
attacks). These hashes are stored in a specific system catalog, or in an X.509 certificate embedded within a secure file on the drive. If any of these tests result in failure, OS file protection will halt the process to keep your machine secure. This is active protection against problematic malware.
1.3.2. BitLocker
The need for drive encryption has been a popular topic in a lot of security channels lately, and in both Windows Vista and Windows Server 2008 Microsoft has risen to the call by developing a feature called BitLocker. BitLocker is designed especially for scenarios where a thief may gain physical access to a hard drive. Without encryption, the hacker could simply boot another operating system or run a hacking tool and access files, completely bypassing the NTFS filesystem permissions. The Encrypting File System in Windows 2000 Server and
Windows Server 2003 went a step farther, actually scrambling bits on the drive, but the keys to decrypt the files weren't as protected as they should have been. With BitLocker, the keys are stored within either a Trusted Platform Module (TPM) chip on board your system, or a USB flash drive that you insert upon boot up.
BitLocker is certainly complete: when enabled, the feature encrypts the entire Windows volume including both user data and system files, the hibernation file, the page file, and
temporary files. The boot process itself is also protected by BitLocker—the feature creates a hash based on the properties of individual boot files, so if one is modified and replaced by, for example, a Trojan file, BitLocker will catch the problem and
prevent the boot. It's definitely a step up from the limitations of EFS, and a significant improvement to system security over unencrypted drives.
1.3.3. Device Installation Control
proliferation of the USB thumb drive. No matter how securely you set your permissions on your file servers, no matter how finely tuned your document destruction capabilities are, and no matter what sort of internal controls you have on "eyes-only" documentation, a user can simply pop a thumb drive into any open USB port and copy data over, completely bypassing your physical security. These drives often contain very sensitive information that ideally should never leave the corporate
campus, but they're just as often found on keychains that are lost, inside computer bags left unattended in an airport lounge, or in some equally dangerous location. The problem is
significant enough that some business have taken to disabling USB ports by pouring hot glue into the actual ports. Effective, certainly, but also messy.
In Windows Server 2008, an administrator will have the ability to block all new device installs, including USB thumb drives, external hard drives, and other new devices. You can simply deploy a machine and allow no new devices to be installed. You'll also be able to set exceptions based on device class or device ID—for example, to allow keyboards and mice to be added, but nothing else. Or, you can allow specific device IDs, in case you've approved a certain brand of product to be
installed, but no others. This is all configurable via Group Policy, and these policies are set at the computer level.
1.3.4. Windows Firewall with Advanced Security
The Windows Firewall version included with Windows Server 2003 Service Pack 1 was exactly the same as that included in Windows XP Service Pack 2. Microsoft bundled that firewall with Service Pack 1 as a stopgap measure—deploy this firewall now, Microsoft said, so you will be protected, and we will work to improve the firewall in the next version of Windows.
rearchitected to reduce coordination overhead between filtering and IPsec. More rules functionality has been enabled, and you can specify explicit security requirements such as authentication and encryption very easily. Settings can be configured on a per-AD computer or user group basis. Outbound filtering has been enabled; there was nothing but internal filtering in the previous version of Windows Firewall. And finally, profile support has
been improved as well—on a per-computer basis, there is now a profile for when a machine is connected to a domain, a profile for a private network connection, and a profile for a public
network connection, such as a wireless hotspot. Policies can be imported and exported easily, making management of multiple computers' firewall configuration consistent and simple.
1.3.5. Network Access Protection
Viruses and malware are often stopped by software defenses before they can run within a user's session, but the ultimate protection would be if they never even got access to the network. In Windows Server 2008, Microsoft has created a platform whereby computers are examined against a baseline set by the administrator, and if a machine doesn't stack up in any way against that baseline, that system can be prevented from accessing the network—quarantined, as it were, from the healthy systems until the user is able to fix his broken machine. This functionality is called Network Access Protection.
NAP can be broken down into three key components:
Health policy validation
Validation is the process wherein the machine attempting to connect to the network is examined and checked against certain health criteria that an administrator sets.
Health policy compliance
that fail the validation process can be automatically updated or fixed via Systems Management Server or some other management software, as well as by Microsoft Update or Windows Update.
Limited access
Access limiting can be the enforcement mechanism for NAP. It's possible to run NAP in monitoring-only mode—which logs the compliance and validation state of computers connecting to the network—but in active mode, computers that fail validations are put into a limited-access area of the network, which typically blocks almost all network access and restricts traffic to a set of specially hardened servers that contain the tools most commonly needed to get machines up to snuff.
Keep in mind that NAP is only a platform by which these checks can be made—pieces of the puzzle are still needed after
deploying Windows Server 2008, including system health
1.4. Manageability Improvements
Servers are only effective if the administrator configures them properly. Windows Server products have traditionally been fairly simple to operate, but in Windows Server 2008 there are many improvements to the initial setup and configuration experience. Much of these details are still being worked out, and these
elements may change as we draw nearer to the anticipated release date, but let's take a look anyway and see what Windows Server 2008 has to offer in terms of manageability enhancements.
1.4.1. Server Manager
Server Manager is a one-stop shop for viewing information on a server, looking at its stability and integrity, managing installed roles, and troubleshooting configuration issues that may arise. Server Manager replaces the Configure Your Server, Manage Your Server, and Security Configuration Wizard interfaces. It centralizes a variety of MMC 3.0 snap-ins, allowing you to see at a glance what roles and features are installed on any given
machine, and giving you an easy jumping-off point to begin management of those pieces.
1.4.2. Windows Deployment Services
Many an administrator have come to love Remote Installation Services (RIS), the add-on to Windows 2000 Server and
Windows Server 2003 that streamed an installation of client and server operating systems over the network and provided the ability to customize installations and set them off with just a few keystrokes. In Windows Server 2008, Microsoft has
radically revised RIS and renamed it Windows Deployment Services (WDS). WDS still works using pre-boot execution
1.5. Performance and Reliability
Upgrades
Among the other enhancements in Windows Server 2008, work was done to improve overall system reliability and performance. For example, to view processes in previous versions of Windows Server, you had two basic tools, both of which were virtually unchanged from release to release—the Task Manager and the Performance Monitor. In Windows Server 2008, these tools have been combined into a single interface, called the Performance Diagnostics Console (which is also integrated into the
aforementioned Server Manager), to make it easier to view
statistics and alerts about how well your machine is handling its duties.
The Resource View is a simpler, but more powerful, view of how certain processes and services, among other metrics, are using the available resources on your machine. The Reliability Monitor shows a detailed view of exactly what events are occurring on a regular or intermittent basis to degrade the stability of your server. For example, you can see problems and degradations based on software installation activity, application failures,
1.6. Windows Server 2008 Editions
As always, Microsoft has split up the various editions of Windows Server 2008 so that, in theory, each customersegment is served by the right product with the right feature set at the right price. Windows Server 2008 is available in the following editions:
Windows Web Server 2008
This version of Windows Server 2008 is optimized to host web sites using IIS and is therefore limited in its support of hardware and in its feature set. It's designed specifically as a web server, so you won't find many features enabled
other than IIS, ASP.NET, and some other web hosting-specific capabilities. Avoid this edition unless you have machines whose sole purpose is serving web and other Internet content.
Standard Edition (SE)
This is the plain-vanilla version of Windows that most
corporations likely will deploy. Included with it is support for up to two processors and 4 GB of memory. SE includes
most of the features and support of the other editions, including the .NET Framework, IIS 7, Active Directory, the distributed and encrypting filesystems, and various
management tools. You also receive Network Load
Enterprise Edition (EE)
Aimed squarely at more demanding environments, EE adds clustering support, support for eight processors, 64 GB of RAM for x86-based systems and up to 2 TB of RAM for x64 systems, the ability to hot-add memory to a running server, and unlimited network connections, among other things.
Datacenter Edition (DE)
This performance- and scalability-enhanced Windows Server 2008 edition supports from 8 to 32 processors, hot-adding of processors and their replacement, and features the same memory support of the Enterprise Edition. With the
exception of more extensive firewalling features and some increase in virtual machine licensing, DE is identical to EE.
For more information, visit the Microsoft web site at
1.7. Hardware Requirements
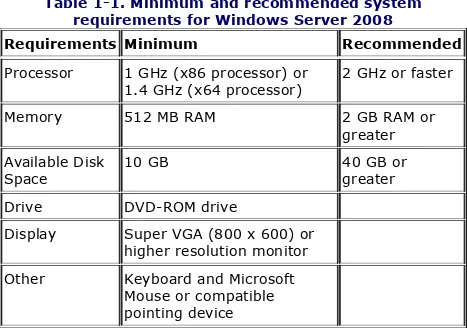
Table 1-1 lists Microsoft's minimum and recommended system requirements for running Windows Server 2008.
Table 1-1. Minimum and recommended system requirements for Windows Server 2008
Requirements Minimum Recommended
Processor 1 GHz (x86 processor) or
1.4 GHz (x64 processor) 2 GHz or faster
Memory 512 MB RAM 2 GB RAM or
greater Available Disk
Space 10 GB 40 GB orgreater
Drive DVD-ROM drive
Display Super VGA (800 x 600) or higher resolution monitor Other Keyboard and Microsoft
Mouse or compatible pointing device
However, anyone with prior experience with Windows operating systems is likely familiar with the simple fact that Microsoft's minimum system requirements (and often, the recommended requirements as well) are woefully inadequate for all but the most casual serving duties. Based on price and performance considerations as of this writing, I recommend the following specifications for any Windows Server 2008 version available through traditional channels. I'll refer to these as the "realistic minimums" from this point on in the book.
A Pentium III 1GHz processor
At least 512 MB of RAM At least 9 GB of disk space
In this day and age, PC hardware changes in value, speed, and availability on what seems like a daily basis. Unless your sole job is to continually specify the hardware platforms and
configurations on which your client and server computers will run, it only takes missing a week's worth of developments to miss out on new processor speeds, chipset replacements or introductions, and hard-drive enhancements.
1.8. The Last Word
Windows Server 2008 presents an interesting set of features that result in tangible benefits for many administrators. The Server Core version of the product is perhaps the most useful new installation option of Windows on the server in quite a while, and it's appropriate for use in many situations where rock-solid servers are required. If your server farm hosts network-intensive applications, you'll find the changes to the TCP/IP stack and other network performance improvements tantalizing, and hardware assistance now makes network scaling much more cost effective by requiring fewer physical servers than before. Security is of course of paramount
importance, and NAP alone is worth investing in Windows Server 2008. Management capabilities are improved as well. Two general camps of people and their organizations will find compelling reasons to immediately upgrade to Windows Server 2008:
Those still running a version of Windows NT or Windows 2000 Server
NT Server 4.0 reached the end of its supportable life on December 31, 2004. Windows 2000 Server's mainstream support ended June 30, 2005, and while extended support will be available until July 13, 2010, it's smart to consider a move. Windows Server 2008, a fundamentally major
release, provides a good jump up to new features, although it will likely require a hardware refresh if you are still
running Windows NT or Windows 2000 in production.
Those with current Microsoft Select, Software Assurance, or Open License agreements that allow them to upgrade to the latest release at no additional cost
upgrade, you can get the benefit of Windows Server 2008 for little overall monetary cost.
If you are not a member of either group, the value of upgrading to Windows Server 2008 is less clear, though a strong case
could be made for moving up. If you're happily chugging away with Windows Server 2003 or R2, have read this chapter and don't see any features you absolutely must have now, and don't have an update agreement with Microsoft, you might want to skip this release and wait for Windows Server 2009 (or
whatever the appropriate year might be).
For most corporations, it's a question of timing. Consider that the next radically different revision of Windows is about three years away on the desktop and four to five years away on the server. You'll have plenty of time to move to Windows Server 2008 in that window. For others, it's a question of finances: if you can't afford to upgrade to Windows Server 2008, then it's a dead end. If you are satisfied with Windows Server 2003, or the R2 edition, and have secured it properly, nothing in Windows Server 2008 is absolutely mandatory. The same goes with those running the original release of Windows Server 2003 with
Chapter 2. Installation and Deployment
Now that you've been thoroughly introduced to what's new, what's hot, and what's not in Windows Server 2008, the time has come to install the operating system on your machines. Installing Windows Server 2008 is easy: the fun comes in
configuring and customizing the operating system. I'll begin by covering the installation process. Then I devote a large part of this chapter to unattended installations, automated deployment, and batch machine imaging, because you can gain a significant time savings by letting your computer handle as many of the tedious installation tasks as possible. So, let's jump in and get started.
2.1. Installing Windows Server 2008
It's a fairly effortless procedure to install Windows Server 2008 onto new systems. Here are the steps:
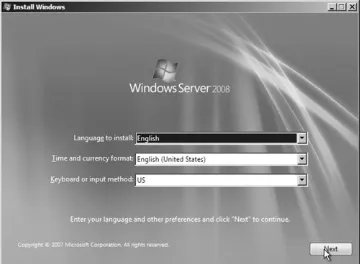
1. Turn the system power on and insert the Windows Server 2008 DVD into the drive. If you receive a prompt asking you to select from what location to boot, choose the option to boot from the CD. The system will boot and begin the initial installation procedure. Figure 2-1 shows the
beginning of this phase from the Install Windows screen. Choose the correct language, time and currency format, and keyboard input method, and then click Next.
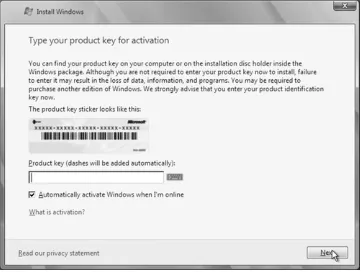
2. Click the "Install now" button in the middle of the screen. 3. When you click the next screen, shown in Figure 2-2, you
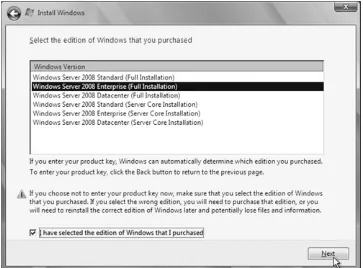
are prompted for your product key. You do not have to enter the key now, but you will be required within a certain amount of time to enter a valid key once installation is complete. Enter your key if you wish and then click Next. Note that if you don't enter a key now, make sure that when you choose an edition to install (on the next screen), you choose the edition that corresponds to the key you will enter later; otherwise, you may need to reinstall.
4. If you did not enter a key, the screen shown in Figure 2-3 will appear, asking you to select the edition of Windows that you purchased. (If you had entered a key, Windows would have automatically chosen the correct edition based on the contents of your key.) Choose which edition of the product— including the standard installation or the Server Core flavor —to install. Then, click Next.
5. Read the terms of the license agreement. If you accept (which, of course, you have to do to continue installation), check the box and click to continue.
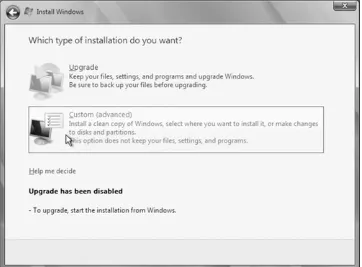
6. The "Which type of installation do you want?" screen appears, depicted in Figure 2-4. If you were running this installation from within Windows, the Upgrade selection would be enabled, allowing you to move to Windows Server 2008 with most of your programs, files, and settings intact. This is not the recommended path; here, in this example, we are completing a clean installation onto a formatted, blank disk. In this case, the only available option is Custom. Click "Custom (advanced)" to continue.
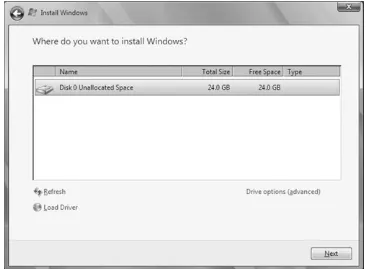
7. A screen listing your current disk partitions will appear, as shown in Figure 2-5. You can delete, create, and format partitions to your heart's content here. Once you have at least one partition with 15 GB or more of disk space on it, you can click Next. If you haven't yet formatted, Setup will handle that.
8. Finally, files are copied and settings are finalized. This process can take a little while, up to 30 minutes, so feel free to step away (Figure 2-6).
Chapter 2. Installation and Deployment
Now that you've been thoroughly introduced to what's new, what's hot, and what's not in Windows Server 2008, the time has come to install the operating system on your machines. Installing Windows Server 2008 is easy: the fun comes in
configuring and customizing the operating system. I'll begin by covering the installation process. Then I devote a large part of this chapter to unattended installations, automated deployment, and batch machine imaging, because you can gain a significant time savings by letting your computer handle as many of the tedious installation tasks as possible. So, let's jump in and get started.
2.1. Installing Windows Server 2008
It's a fairly effortless procedure to install Windows Server 2008 onto new systems. Here are the steps:
1. Turn the system power on and insert the Windows Server 2008 DVD into the drive. If you receive a prompt asking you to select from what location to boot, choose the option to boot from the CD. The system will boot and begin the initial installation procedure. Figure 2-1 shows the
beginning of this phase from the Install Windows screen. Choose the correct language, time and currency format, and keyboard input method, and then click Next.
2. Click the "Install now" button in the middle of the screen. 3. When you click the next screen, shown in Figure 2-2, you
are prompted for your product key. You do not have to enter the key now, but you will be required within a certain amount of time to enter a valid key once installation is complete. Enter your key if you wish and then click Next. Note that if you don't enter a key now, make sure that when you choose an edition to install (on the next screen), you choose the edition that corresponds to the key you will enter later; otherwise, you may need to reinstall.
4. If you did not enter a key, the screen shown in Figure 2-3 will appear, asking you to select the edition of Windows that you purchased. (If you had entered a key, Windows would have automatically chosen the correct edition based on the contents of your key.) Choose which edition of the product— including the standard installation or the Server Core flavor —to install. Then, click Next.
5. Read the terms of the license agreement. If you accept (which, of course, you have to do to continue installation), check the box and click to continue.
6. The "Which type of installation do you want?" screen appears, depicted in Figure 2-4. If you were running this installation from within Windows, the Upgrade selection would be enabled, allowing you to move to Windows Server 2008 with most of your programs, files, and settings intact. This is not the recommended path; here, in this example, we are completing a clean installation onto a formatted, blank disk. In this case, the only available option is Custom. Click "Custom (advanced)" to continue.
7. A screen listing your current disk partitions will appear, as shown in Figure 2-5. You can delete, create, and format partitions to your heart's content here. Once you have at least one partition with 15 GB or more of disk space on it, you can click Next. If you haven't yet formatted, Setup will handle that.
8. Finally, files are copied and settings are finalized. This process can take a little while, up to 30 minutes, so feel free to step away (Figure 2-6).
2.2. Initial Configuration Tasks
After your password is changed, Windows Server 2008 logs you in as an administrator, and the Initial Configuration Tasks screen appears, as shown in Figure 2-7. On this screen, you can
complete the numerous but sometimes tedious steps to
configure a newly installed machine for daily use, like setting the time zone, adding IP addresses and configuring them,
naming the computer and joining it to a workgroup or domain, updating, and so on.
Figure 2-7. The Initial Configuration Tasks screen
I strongly recommend that the first step you complete on this screen is to immediately click the "Download and install
updates" link (assuming you have an active network connection that can route to the Internet) to apply the latest security fixes and service packs before placing the machine into production.