CISSP for Dummies, 2nd Edition
byLawrence MillerandPeter Gregory
John Wiley & Sons
2007 (434 pages)ISBN:9780470124260
Including quick assessments at the beginning of each chapter, a prep test at the end of each chapter, and a full-length practice exam, this guide offers proven test-taking tips and will get you up to speed on the latest changes to the exam.
Table of Contents
CISSP for Dummies, 2nd Edition
Cheat Sheet
- CISSP For Dummies, 2nd Edition
Introduction
Part I - Certification Basics
Chapter 1
- (ISC)
2and the CISSP Certification
Chapter 2
- The Common Body of Knowledge
(CBK)
Chapter 3
- Putting Your Certification to Good
Use
Part II - Domains
Chapter 4
- Access Control
Chapter 5
- Telecommunications and Network
Security
Chapter 6
- Information Security and Risk
Management
Chapter 7
- Application Security
Chapter 8
- Cryptography
Chapter 10
- Operations Security
Chapter 11
- Business Continuity and Disaster
Recovery Planning
Chapter 12
- Legal, Regulations, Compliance, and
Investigations
Chapter 13
- Physical (Environmental) Security
Part III - The Part of Tens
Chapter 14
- Ten Test Preparation Tips
Chapter 15
- Ten Test Day Tips
Chapter 16
- Ten More Sources for Security
Certifications
Part IV - Bonus Chapters
Bonus Chapter 1
- Glossary
Bonus Chapter 2
- Ten Security Web Sites
Bonus Chapter 3
- Ten Essential Reference Books
Index
List of Figures
List of Tables
List of Labs
Back Cover
Cramming for the CISSP exam? This friendly test-prep
guide makes studying a snap! Prepared by two
CISSP-certified experts, it gets you up to speed on the latest
changes to the exam and gives you proven test-taking
tips. You’ll find complete coverage of all ten domains of
the (ISC)2 Common Body of Knowledge to help you
pass with flying colors.
Discover how to:
Register for the exam
Develop a study plan
Document your security work experience
Break down exam questions
Prepare for the bid day
Put your certification to good use
About the Authors
Lawrence Miller, CISSP has worked in systems
engineer and a security consultant for service
providers and clients in the retail, financial, and
manufacturing sectors and served over 13 years in the
U.S. Navy as a Chief Petty Officer in various roles
including information systems security and “weather
guesser.”
Peter H. Gregory, CISA, CISSP, is the author of twelve
books on security and technology including
Solaris
Security, Computer Viruses For Dummies,
and
Blocking
Spam and Spyware For Dummies.
Peter is a security strategist at a publicly-traded
financial management software company located in
Redmond, Washington. Prior to this, he held tactical
and strategic security positions in large wireless
telecommunications organizations. He has also held
development and operations positions in casino
CISSP for Dummies, 2nd Edition
by Lawrence Miller and Peter GregoryCISSP For Dummies ® , 2nd Edition Published by
Wiley Publishing, Inc. 111 River Street
Hoboken, NJ 07030-5774 www.wiley.com
Copyright © 2007 by Wiley Publishing, Inc., Indianapolis, Indiana Published by Wiley Publishing, Inc., Indianapolis, Indiana
Published simultaneously in Canada
No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic,
mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or
authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for
permission should be addressed to the Legal Department, Wiley
Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, or online at
http://www.wiley.com/go/permissions.
Trademarks: Wiley, the Wiley Publishing logo, For Dummies, the
associated with any product or vendor mentioned in this book.
LIMIT OF LIABILITY/DISCLAIMER OF WARRANTY: THE PUBLISHER AND THE AUTHOR MAKE NO REPRESENTATIONS OR WARRANTIES WITH RESPECT TO THE ACCURACY OR COMPLETENESS OF THE CONTENTS OF THIS WORK AND SPECIFICALLY DISCLAIM ALL WARRANTIES, INCLUDING WITHOUT LIMITATION WARRANTIES OF FITNESS FOR A PARTICULAR PURPOSE. NO WARRANTY MAY BE CREATED OR EXTENDED BY SALES OR PROMOTIONAL
MATERIALS. THE ADVICE AND STRATEGIES CONTAINED HEREIN MAY NOT BE SUITABLE FOR EVERY SITUATION. THIS WORK IS SOLD WITH THE UNDERSTANDING THAT THE PUBLISHER IS NOT ENGAGED IN RENDERING LEGAL, ACCOUNTING, OR OTHER PROFESSIONAL SERVICES. IF PROFESSIONAL ASSISTANCE IS REQUIRED, THE SERVICES OF A COMPETENT PROFESSIONAL PERSON SHOULD BE SOUGHT. NEITHER THE PUBLISHER NOR THE AUTHOR SHALL BE LIABLE FOR DAMAGES ARISING
HEREFROM. THE FACT THAT AN ORGANIZATION OR WEBSITE IS REFERRED TO IN THIS WORK AS A CITATION AND/OR A POTENTIAL SOURCE OF FURTHER INFORMATION DOES NOT MEAN THAT THE AUTHOR OR THE PUBLISHER ENDORSES THE INFORMATION THE ORGANIZATION OR WEBSITE MAY PROVIDE OR
RECOMMENDATIONS IT MAY MAKE. FURTHER, READERS SHOULD BE AWARE THAT INTERNET WEBSITES LISTED IN THIS WORK MAY HAVE CHANGED OR DISAPPEARED BETWEEN WHEN THIS WORK WAS WRITTEN AND WHEN IT IS READ.
For general information on our other products and services, please
contact our Customer Care Department within the U.S. at 800-762-2974, outside the U.S. at 317-572-3993, or fax 317-572-4002.
For technical support, please visit www.wiley.com/techsupport.
ISBN: 978-0-470-12426-0
Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1
About the Authors
Lawrence Miller, CISSP has worked in systems administration and information security for more than a decade and has earned numerous other certifications throughout that time including MCSE+I, CCNP, SCSA, CNA, A+, Network+, Security+, and i-Net+. He has also received NSA IAM certification training. He is currently working as the Information Technology Operations Manager for a top 100 U.S. law firm. He has previously worked as an internetworking security engineer and a security consultant for service providers and clients in the retail, financial, and manufacturing sectors and served over 13 years in the U.S. Navy as a Chief Petty Officer in various roles including information systems security and “weather guesser.”
Peter H. Gregory, CISA, CISSP, is the author of twelve books on
security and technology including Solaris Security, Computer Viruses For Dummies, and Blocking Spam and Spyware For Dummies.
Peter is a security strategist at a publicly-traded financial management software company located in Redmond, Washington. Prior to this, he held tactical and strategic security positions in large wireless
telecommunications organizations. He has also held development and operations positions in casino management systems, banking,
government, non-profit organizations, and academia since the late 1970s.
Peter’s Web sites can be found at www.isecbooks.com and www.peter hgregory.com. He can be reached at
Dedication
To those in all our lives that make it exciting, interesting, and fun, and are there for us when it isn’t.
From Peter H. Gregory:
To security professionals everywhere who are trying to do the right thing to protect their organizations’ assets.
Authors’ Acknowledgments
Peter H. Gregory would like to thank Katie Feltman, Senior Acquisitions Editor at Wiley, for her perseverance and patience. Thank you to Mark Enochs, Senior Project Editor at Wiley, for your help, and to Nicole Haims for your thoughtful editing. Thank you, Larry, for agreeing once again to coauthor this book. It’s great as always to work with you on security books.
And finally, heartfelt thanks go to Liz Suto, wherever you are, for getting me into this business over ten years ago when you asked me to do a tech review on your book Informix Online Performance Tuning.
Lawrence Miller would like to thank the folks at Wiley for all of your great work on this project, particularly Katie Feltman, Mark Enochs, and Nicole Haims. Your wonderful efforts helped ensure this 2nd Edition wasn’t just a Brady Bunch Reunion or CHIPS 2000, but rather a thorough and
complete update of the 1st Edition that our readers will certainly
appreciate. Peter, thank you again for working with me on yet another project and ensuring the same. And again, congratulations are in order for your recent successes, both personal and professional. I look forward to the opportunity to work together again.
Publisher’s Acknowledgments
Acquisitions, Editorial, and Media Development
Sr. Project Editor Mark Enochs
(Previous Edition: Pat O’Brien) Sr. Acquisitions Editor
Katie Feltman Copy Editors Nicole Haims Virginia Sanders Technical Editors Lawrence Miller Peter Gregory Editorial Manager Leah Cameron
Media Development Specialists Angela Denny
Kate Jenkins Steven Kudirka Kit Malone
Media Project Supervisor Laura Moss-Hollister
Editorial Assistant Amanda Foxworth Sr. Editorial Assistant Cherie Case
Cartoons Rich Tennant
( www.the5thwave.com)
Project Coordinator Heather Kolter
Layout and Graphics Claudia Bell
Carl Byers Proofreaders Aptara
David Faust Indexer Aptara
Anniversary Logo Design Richard Pacifico
Publishing and Editorial for Technology Dummies
Richard Swadley, Vice President and Executive Group Publisher Andy Cummings, Vice President and Publisher
Mary Bednarek, Executive Acquisitions Director Mary C. Corder, Editorial Director
Publishing for Consumer Dummies
Diane Graves Steele, Vice President and Publisher Joyce Pepple, Acquisitions Director
Composition Services
Months before the test
1. Develop your preparation strategy. Get started by getting all your study aids lined up. CISSP For Dummies belongs on top of the pile.
2. Budget your preparation time. The breadth of the CISSP exam requires that you make time to review every aspect of the exam domains. Chances are you don’t apply every aspect of the CISSP arsenal every day at work, so you can’t count on it being fresh in your mind without reviewing every domain
completely from the ground up. You’ll be unpleasantly surprised by what you’ve forgotten if you don’t plan to review.
3. Schedule your exam time and make travel arrangements. The CISSP exam is scheduled frequently at many locations around the world. If necessary, you need to make travel arrangements, hotel arrangements, arrange child care, and actually find an available seat in a scheduled exam. It’s no more expensive to schedule the exam in advance and then
Weeks before the test
1. Schedule your preparation time. There’s enough to review that you have to be completely honest with yourself about your progress. A last-moment cram will be a disaster. Book blocks of time in your schedule for review, and be honest about sticking to your schedule.
2. Study CISSP For Dummies. This book reviews all aspects of the CISSP exam, as well as being packed with test preparation tips.
3. Take practice tests and answer practice questions. Practice questions confront you with gaps in your preparation and get you used to the brain sweat that the CISSP exam demands. 4. Check other resources. If there are any aspects of the CISSP
exam domains that you haven’t experienced up close and personal, now is the time to get that exposure.
Night before the test
1. Have a nutritious dinner. Avoid spicy and rich foods. Think marathon runnerfor the day ahead.
2. Double-check your admission and travel plans. Make sure that you know exactly where you need to be, what you need for admission, when you need to be there, and how early you need to leave to arrive with time to spare.
3. Double-check your exam supplies. The CISSP exam is longer than other standard professional exams, and the testing conditions are different. You can bring snacks, beverages, tissues, and other comfort and refreshment items. In our
opinion, a big bottle of water is tops on the list. Wear an analog watch; digital watches are forbidden in some testing areas. 4. Review CISSP For Dummies. Once more around the block
should get your head on straight. At this point, you should know the book cold.
Day of the exam
1. Dress in layers. The exam room may not be the most
comfortable temperature, and your needs may change during the very long exam. Give yourself some flexibility to warm up or cool down.
2. Review CISSP For Dummies. By now, you could write out this book from memory.
3. Head to the exam room, sit down, and listen to the
After you leave the exam room
1. Prepare for a retest. It’s just like the Space Shuttle crew taking time to carefully shut down the bird even when they’re safely on the ground. Take the time immediately to make notes about what you found most difficult about the exam. If you need to retest, those notes are your shortest, most reliable path to follow-up success.
2. Relax and wait for your results. At this point, there’s nothing left but to enjoy the quiet after the storm. So do it. Hug your family, play with your dog, and be optimistic. You’ve done
everything you needed to do, and now you can enjoy the quiet. Wiley, the Wiley Publishing logo, For Dummies, the Dummies Man logo, the For Dummies Bestselling Book Series logo and all related trade dress are trademarks or registered trademarks of John Wiley & Sons, Inc.
and/or its affiliates. All other trademarks are property of their respective owners.
Introduction
Over the past several years, security practitioners around the world have begun pursuing a now well-known and highly regarded professional credential: the Certified Information Systems Security Professional (CISSP) certification.
In turn, security-minded companies have been actively seeking individuals who have earned the coveted CISSP certification. It has surpassed the demand for many vendor-sponsored technical
About This Book
Our goals in this book are simple: to help you prepare for and pass the CISSP examination, and to guide you after you earn the certification. Although we’ve stuffed it chock-full of good information, we don’t expect that this book will be a weighty desktop reference on the shelf of every security professional - although we certainly wouldn’t object.
And this isn’t the Library of Congress. We don’t intend for this book to be an all-purpose, be-all-to-end-all, one-stop shop with all the answers to life’s great mysteries. Given the broad base of knowledge required for the CISSP certification, we strongly recommend using multiple resources to prepare for the exam. This book will provide you with a road map to the CISSP certification and sufficient information to help you pass the exam. It will not make you a security expert - or help you build pumped-up forearms!
As a security professional, you’ll find that earning the CISSP certification is only a beginning. Business and technology, with their associated risks and vulnerabilities, require each of us as security professionals to
constantly press forward, consuming vast volumes of knowledge and information in a constant tug of war against the bad guys. Thus, when preparing for your CISSP certification, you should study as much relevant information as your time and resources allow. CISSP For Dummies
How This Book Is Organized
This book is organized into four parts. We cover the (ISC) 2 Common Body of Knowledge (CBK) domains in Part II. Although this book’s chapters don’t necessarily have to be read in order, they’re organized according to the CBK domains and follow a somewhat logical
progression - as logic dictates!
Part I:
Certification Basics
In Part I, we first introduce the International Information Systems Security Certifications Consortium (ISC)2, earning the CISSP certification, and an overview of the CBK. Then we provide some helpful guidance for study. The last chapter in this part is a guide for actions and activities after you’ve earned your certification.
Part II:
Domains
Part II contains the domains of the CBK. A CISSP candidate must have some practical work experience with at least a few of the concepts and technologies that we cover in this part. Taken individually, these domains represent at least a slightly larger part of the actual CISSP exam than other domains. This is certainly true about the Telecommunications and Network Security domain and the Information Security and Risk
Management domain, which are largely introductions to basic security concepts discussed throughout the CBK.
Part III:
The Part of Tens
The much loved and revered Part of Tens contains four chapters that are more than mere lists. We include information to help you prepare for the CISSP exam and to also help you in your career as a security
professional.
Part IV:
Appendixes and Bonus Chapters
How the Chapters Are Organized
CISSP For Dummies (now in its second edition) is unique in the For Dummies series. Because the CISSP examination covers such a broad base of information, we don’t recommend skipping any of the material in this book. The information presented in some of the chapters may be familiar to you or easier to understand than others, but we still
recommend at least a quick, cursory read of those chapters. For this reason, we don’t include a quick assessment test at the beginning of each chapter as in other For Dummies certification books. Instead, we chose to pack this book with as much useful information as possible to help you succeed in your quest for the CISSP certification.
Chapter introductions
The first page of each domain chapter begins with a brief introduction to the domain covered therein. You also find a list of chapter objectives that closely correlates to the CISSP knowledge objectives for that domain.
Study subjects
In the heart of each CISSP domain chapter, we extensively cover the knowledge objectives listed in the CISSP CBK. These chapters provide the relevant information for the CISSP exam with enough detail to place the information into proper context.
Tables and illustrations
To be helpful to you in your study, we provide tables and illustrations of important information or concepts whenever we can. However, because CISSP is a vendor-neutral certification, don’t expect to find screen
captures or simulation-type graphics. More room for good, old-fashioned information!
Prep Tests
Icons Used in This Book
Throughout this book, you note little icons in the left margin that act as road signs to help you quickly pull out the stuff that’s most important to you. Here’s what they look like and what they represent.
Instant Answer Instant Answer icons highlight important information to help you answer questions on the actual exam. To succeed on the CISSP exam look for these icons to highlight critical points.
Remember Information tagged with a Remember icon identifies general information and core concepts that you may already know but should certainly understand and review before the CISSP exam.
Tip Tip icons include short suggestions and tidbits of useful information. Warning Look for Warning icons to identify potential pitfalls, including easily confused or difficult-to-understand terms and concepts.
Cross-Reference These icons point you toward other places in the book for more information on a particular subject.
Let’s Get Started!
Part Overview
Chapter 1: (ISC) 2 and the CISSP Certification
Chapter 2: The Common Body of Knowledge (CBK)
In this part . . .
(ISC)2? CBK? CISSP? No, they’re not droids in a new Star Wars movie. The chapters in this part describe the “who, what, when, where, how, and why” of the CISSP certification, as well as the “now what?” and the
Chapter 1: (ISC)2 and the CISSP Certification
In This ChapterFinding out about (ISC) 2 and the CISSP certification Understanding CISSP certification minimum requirements Registering for the exam
Developing a study plan
Overview
Some say that the Certified Information Systems Security Professional (CISSP) candidate requires a breadth of knowledge 50 miles across and 2 inches deep. To embellish on this statement, we believe that the CISSP candidate is more like the Great Wall of China, with a knowledge base extending over 3,500 miles, with a few holes here and there, stronger in some areas than others, but nonetheless one of the Seven Wonders of the Modern World.
The problem with many currently available CISSP preparation materials is in defining how high the Great Wall actually is: Some material
About (ISC)
2
and the CISSP Certification
The International Information Systems Security CertificationsConsortium, or (ISC)2, established the Certified Information Systems Security
Professional (CISSP) certification program in 1989. The (ISC) 2 is a nonprofit, tax-exempt corporation chartered for the explicit purpose of developing and administering the certification and education programs associated with the CISSP (as well as several CISSP concentrations, and the Systems Security Certified Practitioner, or SSCP, and the Certification and Accreditation Professional, (or CAP) certification. The CISSP certification is based on a Common Body of Knowledge (CBK) identified by the (ISC) 2 and defined through ten distinct domains:
Access Control
Telecommunications and Network Security Information Security and Risk Management Application Security
Cryptography
Security Architecture and Design Operations Security
You Must Be This Tall to Ride (And Other
Minimum Requirements)
The CISSP candidate must have a minimum of four years of professional work experience in one or more of the domains listed in the preceding section. After being notified of a passing score on the CISSP
examination, the candidate must submit a qualified third-party
endorsement (from another CISSP; the candidate’s employer; or any licensed, certified, or commissioned professional, such as a banker, attorney, or certified public accountant) to validate the candidate’s work experience. This endorsement must be submitted within 90 days of the date of the exam results notification letter or the application and exam results are voided. A percentage of submitted applications will be
randomly audited, requiring additional documentation (normally a resume and confirmation from employers of work history) and review by (ISC)2. Final notification of certification upon receipt of the endorsement letter will normally be sent by (ISC) 2 via e-mail within one business day (seven business days if audited).
The candidate must also subscribe to the (ISC) 2 Code of Ethics and renew certification every three years. The CISSP certification can be renewed by accumulating 120 Continuing Professional Education (CPE) credits or by retaking the CISSP examination. You earn CPE credits for various activities, including taking educational courses or attending
seminars and security conferences, membership in association chapters and meeting attendance, vendor presentations, university or college course completion, providing security training, publishing security articles or books, serving on industry boards, self-study, and volunteer work. You must submit evidence of any such activities to (ISC) 2 for determining and documenting CPE credits. In most cases, this can be done online in the secure area of the (ISC) 2 Web
Tip The minimum requirement for CISSP certification is four years of professional work experience in one or more of the ten domains of the CISSP CBK. However, you can be credited for one year of experience if you have either a four-year college degree or a master’s degree in
Information Security from a National Center of Excellence (but you
cannot combine both the four-year degree and the master’s degree to get two years of credit).
Registering for the Exam
You can register for the CISSP exam online, via mail, or via fax. First, you need to find a suitable exam date and location. It’s given
throughout the year at various locations (typically at colleges, community centers, or convention centers) worldwide. You can find exam schedules on the (ISC) 2 Web site at www.isc2.org.
Remember Unlike many other certification exams, the CISSP examination isn’t conveniently available at Thomson Prometric or Pearson VUE testing centers.
Some travel may be necessary, which requires planning in advance for travel arrangements . . . possibly including airline, rental car, and hotel reservations. If you’re traveling to another country for your CISSP examination, visa requirements may apply.
After you find a suitable exam date and location on the (ISC) 2 Web site, complete the online registration form or download a copy of the form so that you can mail or fax it back to (ISC)2. If you’re registering online or via fax, you need to use a MasterCard or Visa for payment. If registering by mail, you can pay for the exam via MasterCard, Visa, personal check, or money order. The current fee to take the test is $499 if you register more than 16 days in advance. The mailing address for registrations is:
(ISC) 2 Services
2494 Bayshore Boulevard, Suite 201, Dunedin, FL 34698 U.S.A.
The number for fax registration is 727-738-8522.
When you register, you’ll be required to quantify your work experience in information security. You’re not required to have experience in all the ten domains, but the cumulative total of your work experience must be at least four years.
The total charge of $499 for early registration and the $100 rescheduling fee is exactly the same as the fee for normal registration: $599.
By committing to a specific testing date, you’re more likely to stay focused and avoid procrastination.
Registering early allows you to better plan your travel arrangements and possibly save some money by booking reservations well in advance.
Space is limited at all test centers. Reservations are accepted on a first-come, first-served basis; in the case of registrations by mail, the date of the postmark is used. If the test date fills up before you register (and this is a hot certification), you may be hard-pressed to find another test date and location that suits you this year.
Developing a Study Plan
Many resources are available to help the CISSP candidate prepare for the exam. Self-study is a major part of any study plan. Work experience is also critical to success and can be incorporated into your study plan. For those who learn best in a classroom or training environment, (ISC) 2 offers CISSP review seminars.
We recommend that you commit to an intense 60-day study plan leading up to the CISSP exam. How intense? That depends on your own
personal experience and learning ability, but plan on a minimum of 2 hours a day for 60 days. If you’re a slow learner or reader, or perhaps find yourself weak in many areas, plan on 4–6 hours a day and more on the weekends. But stick to the 60-day plan. If you feel you need 360 hours of study, you may be tempted to spread this out over a 6-month period for 2 hours a day. Consider, however, that committing to 6 months of intense study is much harder (on you, as well as your family and
friends) than 2 months. In the end, you will find yourself studying only as much as you would have in a 60-day period.
Self-study
Self-study can include books and study references, a study group, and practice exams.
Begin by requesting an official CISSP Candidate Information Bulletin (CIB) from the (ISC) 2 Web site ( www.isc2.org). It’s free and will be e-mailed to you as a password-protected Adobe Acrobat PDF document. This booklet provides a good outline of the subjects on which you’ll be tested.
Next, read this book, take the practice exam and review the materials on the accompanying CD-ROM. CISSP For Dummies is written to provide the CISSP candidate an excellent overview of all the broad topics covered on the CISSP exam.
references; we list several great ones on the CD-ROM. As a minimum, we highly recommend The CISSP Prep Guide: Gold Edition by Ronald L. Krutz and Russell Dean Vines (John Wiley & Sons, Inc.).
You can also find several study guides at www.cissps.com, www.cccure.org, and www.cramsession.com.
Joining or creating your own study group will help you stay focused and also provide a wealth of information from the broad perspectives and experiences of other security professionals.
Remember No practice exams exactly duplicate the CISSP exam (and forget about brain dumps). However, many resources are available for practice questions. You’ll find that some practice questions are too hard, others are too easy, and some are just plain irrelevant. Don’t despair! The repetition of practice questions will help reinforce important information that you need to know in order to successfully answer questions on the CISSP exam. For this reason, we recommend taking as many practice exams as possible. Use the Practice Exam and/or the Flash Cards on the CD-ROM and try the practice questions on the CISSP Open Study Guide (OSG) Web site ( www.cccure.org).
Getting hands-on experience
Getting hands-on experience may be easier said than done, but keep your eyes and ears open for learning opportunities during your course of study for the CISSP exam.
For example, if you’re weak in networking or applications development, talk to the networking group or programmers in your company. They may be able to show you a few things that will help make sense of the
volumes of information that you’re trying to digest.
Tip Your company should have a security policy that’s freely available to its employees, particularly if you have a security function in the
time for you to educate management about issues of due care, due diligence, and other concepts from the Legal, Regulations, Compliance, and Investigations security domain.
Review your company’s Business Continuity and Disaster Recovery plans. They don’t exist? Perhaps this is an initiative that you can lead to help both you and your company.
Attending an (ISC)
2CISSP review seminar
The (ISC) 2 also administers a five-day CISSP CBK Review Seminar to help the CISSP candidate prepare. Schedules and registration forms for the CBK Review Seminar are available on the (ISC) 2 Web site at
www.isc2.org.
The early rate for the CISSP CBK Review seminar is $2,495 if you register 16 days or more in advance (the standard rate is $2,695). Members of ISSA, IIA, or ISACA also get a $250 discount. (All dollar amounts listed here are U.S. currency, and are subject to change.) If you generally learn better in a classroom environment or find that you only have knowledge or actual experience in one or two of the domains, you might seriously consider attending a review seminar.
Attending other training courses or study groups
Other reputable organizations such as SANS ( www.sans.org) offer high-quality training in classroom and self-study formats. Before signing up and spending your money, we suggest that you talk to someone who has completed the course and can tell you about its quality. Usually, the quality of a classroom course depends upon the instructor; for this
reason, we think it’s valuable to find out from others whether the proposed instructor is as helpful as he or she is reported to be.
group where you live; or, if you know some CISSPs in your area, you might ask them to help to organize a self-study group (and tell him or her you will help!).
Tip Always confirm the quality of a study course or training seminar before committing your money and time.
See Chapter 3 for more information on starting a CISSP study group.
Are you ready for the exam?
Are you ready for the big day? This is a difficult question for us to answer. You must decide, based on your individual learning factors, study habits, and professional experience when you’re ready for the exam. We don’t know of any magic formula for determining your chances of success or failure on the CISSP examination. (If you find one, please write to us so that we can include it in the next edition of this book.)
In general, we recommend a minimum of two months of focused study. Read this book and continue taking the practice exam in this book and on the accompanying CD until you can consistently score 80 percent or better in all areas. CISSP For Dummies covers all the information that you will need to pass the CISSP examination. Read this book (and
reread it) until you’re comfortable with the information presented and can successfully recall and apply it in each of the ten domains.
Continue by reviewing other materials (particularly in your weak areas) and actively participating in an online or local study group. Take as many practice exams from as many different sources as possible. There are no brain dumps for the CISSP examination, and no practice test will exactly duplicate the actual exam (some are too easy, and others are too
About the CISSP Examination
The CISSP examination itself is a grueling 6-hour 250-question
marathon. To put that into perspective, in 6 hours you could walk about 25 miles, watch a Kevin Costner movie 11/2 times, or sing “My Way” 540 times on a karaoke machine. Each of these feats respectively closely approximates the physical, mental (not intellectual), and emotional toll of the CISSP examination.
As described by the (ISC)2, a minimum score of “70 percent” is required to pass the examination. Not all the questions are weighted equally, so it’s not possible to absolutely state the number of correct questions required for a passing score.
The examination isn’t computer based. It is administered the
old-fashioned way: exam booklet, answer sheet, and lots of pencils. You may write in the exam booklet, but only answers recorded on the answer
sheet are scored.
You won’t find any multiple-answer, fill-in-the-blank scenario or simulation questions on the CISSP exam. However, all 250 multiple-choice
questions require you to select the best answer from 4 possible choices. This means that the correct answer isn’t always a straightforward, clear choice. In fact, you can count on many questions to initially appear as though they have more than one correct answer. (ISC) 2 goes to great pains to ensure that you really, really know the material. For instance, a sample question might resemble the following:
Which of the following is the FTP control channel? A TCP port 21
B UDP port 21 C TCP port 25 D IP port 21
but is it TCP, UDP, or IP?
Increasingly, CISSP exam questions are based more upon situations than on simple knowledge of facts. For instance, here’s a question you might get:
A system administrator has found that a former employee has successfully logged in to the system. The system administrator should:
A Shut down the system.
B Confirm the breach in the IDS logs. C Lock or remove the user account. D Contact law enforcement.
You won’t find the answer to this in a book (well, probably not). But there is still a best answer to every exam question - perhaps not an ideal
answer, but there is a best answer.
A common and effective test-taking strategy for multiple-choice questions is to carefully read each question and then eliminate any obviously wrong choices. The CISSP examination is no exception.
Warning Wrong choices aren’t so obvious on the CISSP examination. You will find a few obviously wrong choices, but they only stand out to someone who has studied thoroughly for the examination and has a good grasp of all ten of the security domains.
Only 225 questions are actually counted toward your final score. The other 25 are trial questions for future versions of the CISSP examination. However, these questions aren’t identified within the exam, so you have to answer all 250 questions as if they’re the real thing.
Language (TOEFL) exam prior to attempting the CISSP examination.
Chapter 14 covers the details of the exam environment.
Waiting for Your Results
Perhaps the most painful part of the CISSP examination is waiting for the results. You can expect to come out of the CISSP examination, at best, with no idea of whether you have passed or failed . . . or worse, with the sinking feeling that you bombed it miserably. Take heart - this is an
almost universal reaction, caused by mental fatigue, but it’s certainly not the universal result.
(ISC) 2 officially states that you can expect your exam results via first class mail within 4–6 weeks of your examination date. However, (ISC) 2 is getting more efficient and often has results out within 1–2 weeks. No results are given out via telephone. If you don’t receive your results within 6 weeks, you should contact (ISC) 2 to inquire about the status.
Your results will be simply Pass or Fail. No score is given, and your domain strengths/weaknesses aren’t identified. You just receive an official letter informing you of your results. When you pass, you receive your CISSP certification number, CISSP certificate, wallet card, lapel pin, and username/ temporary password for access to the secure (ISC) 2 Web site.
Tip While waiting for your results, assume the worst and prepare for the retest. Recall specific problem areas from the examination. Write them down and study those areas again. If you fail the examination, this effort will pay huge dividends when you try again. And if you find out that you did pass the examination, you’ll be a better CISSP!
Chapter 2: The Common Body of Knowledge
(CBK)
In This Chapter
Getting up close and personal with the CBK
Overview
The Common Body of Knowledge (CBK) defines a basic and common knowledge base for all security professionals. This is collectively referred to as the ten domains of information security. The CBK also provides minimum knowledge requirements for the Certified Information Systems Security Professional (CISSP) exam. Although these knowledge
requirements are analogous to the test objectives, they are distinctly different. For one thing, the test objectives require a candidate to perform specific tasks or demonstrate skill with a specific technology, while the CBK is relatively abstract, and changes little over time.
The CBK is periodically updated by the CBK Committee, which is
appointed by the International Information Systems Security Certifications Consortium (ISC) 2 Board of Directors.
Access Control
The Access Control domain encompasses the set of mechanisms employed to restrict or direct the behavior, use, and content of an
information system. It defines a user’s rights on a system, including what a user can do and what resources are available to a user.
This domain is covered in Chapter 4. Major topics include Accountability
Access control techniques Access control administration Access control models
Identification and authentication techniques
Access control methodologies and implementation File and data ownership
Methods of attack Monitoring
Telecommunications and Network Security
The Telecommunications and Network Security domain encompasses the structures, transmission methods, transport formats, and security
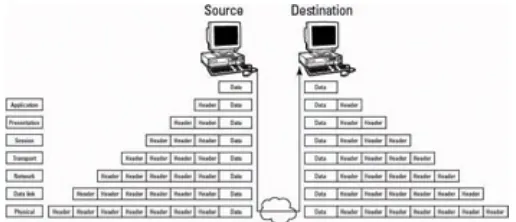
measures used to provide confidentiality, integrity, availability, and authentication for transmissions over private and public networks. This domain is covered in Chapter 5. Major topics include
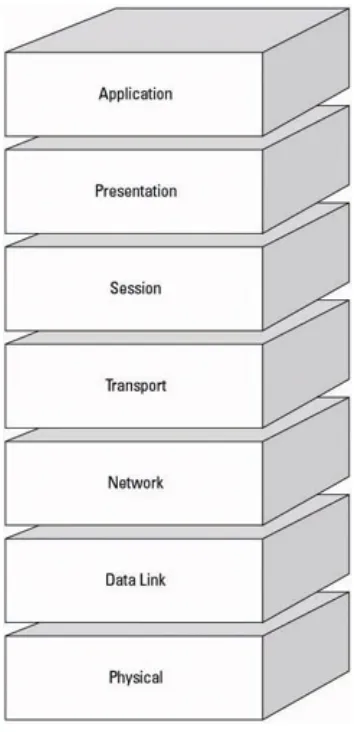
The Open Systems Interconnection (OSI) Model Communications and network security
Internet/intranet/extranet E-mail and facsimile security Secure voice communications
Information Security and Risk Management
The Information Security and Risk Management domain encompasses the following topics:
Security management: The identification of an organization’s information assets and the development, documentation, and implementation of policies, standards, procedures, and guidelines that ensure confidentiality, integrity, and availability.
Risk management: The identification, measurement, control, and minimization of loss associated with uncertain events or
risks, including overall security review, risk analysis, selection and evaluation of safeguards, cost-benefit analysis, management decision, safeguard implementation, and effectiveness review. This domain is covered in Chapter 6. Major topics include
Security management concepts and principles Change control and change management Information and data classification
Employment policies and practices
Policies, standards, guidelines, and procedures Individual roles and responsibilities
Application Security
The Application Security domain encompasses the controls included within systems and application software, as well as the steps used in their development.
This domain is covered in Chapter 7. Major topics include Application issues
Databases and data warehousing Data and information storage Knowledge-based systems Systems development controls Malicious code
Cryptography
The Cryptography domain encompasses the principles, means, and methods of disguising information to ensure its integrity, confidentiality, and authenticity.
This domain is covered in Chapter 8. Major topics include Use of cryptography to achieve security goals
Cryptographic concepts, methodologies, and practices Private and public key algorithms
Public Key Infrastructure (PKI)
Security Architecture and Design
The Security Architecture and Design domain encompasses the concepts, principles, structures, and standards used to design,
implement, monitor, and secure operating systems, equipment, networks, and applications.
This domain is covered in Chapter 9. Major topics include
Common computer and network organizations, architectures, and designs
Operations Security
The Operations Security domain encompasses the controls over hardware, media, and operators with access privileges to resources, including monitoring and auditing.
This domain is covered in Chapter 10. Major topics include Administrative management
Security concepts Control types
Operations controls Resource protection Auditing and audit trails
Monitoring tools and techniques Intrusion detection
Penetration testing Inappropriate activities
Business Continuity and Disaster Recovery
Planning
The Business Continuity and Disaster Recovery Planning domain
encompasses the preparation, testing, and updating of specific actions to protect critical business processes from the effect of major system and network failures.
This domain is covered in Chapter 11. Major topics include Business continuity planning
Disaster recovery planning
Legal, Regulations, Compliance, and
Investigations
The Legal, Regulations, Compliance, and Investigations domain
encompasses computer crime laws and regulations, compliance issues, incident handling, investigative measures and techniques, evidence
gathering, ethical issues, and codes of conduct for security professionals. This domain is covered in Chapter 12. Major topics include
Major categories and types of laws Regulatory compliance
Investigations and evidence
Major categories of computer crime Incident handling
Physical (Environmental) Security
The Physical (Environmental) Security domain encompasses the threats and countermeasures related to the physical protection of people,
facilities, data, equipment, support systems, media, and supplies. This domain is covered in Chapter 13. Major topics include
Facility requirements Technical controls
Chapter 3: Putting Your Certification to Good
Use
In This Chapter
Living the (ISC) 2 code of ethics Maintaining your certification
Being an active (ISC) 2 member
Volunteering for (ISC) 2
Getting active in local security chapters Starting or aiding a study group
Promoting the CISSP certification Being an agent of change
Overview
For many of you, life will be divided into two halves: life before you
earned your CISSP certification, and life afterwards. Much of this book is devoted to helping you get from the “before” half to the “after” half. This chapter is entirely devoted to “after.”
So, what do you do after earning your CISSP? Plenty of things. Some activities are mandatory, like living the code of ethics (provided that you want to keep your hard-won certification - we presume that you do), getting security training, and paying your annual maintenance fee. Other activities, like earning more certifications, are optional but highly
recommended (we think obtaining additional certifications is a very good idea to enrich your professional lives and that of others). Table 3-1 lists required and optional post-CISSP activities.
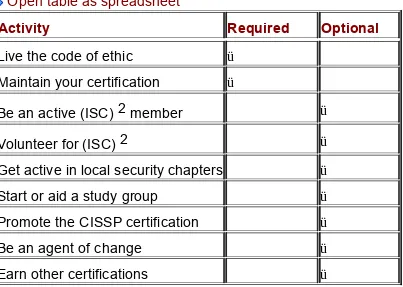
Table 3-1: Post-CISSP Activities
Open table as spreadsheet
Activity Required Optional
Live the code of ethic ü
Maintain your certification ü
Be an active (ISC) 2 member ü
Volunteer for (ISC) 2 ü
Get active in local security chapters ü
Start or aid a study group ü
Promote the CISSP certification ü
Be an agent of change ü
Following the (ISC)
2
Code of Ethics
The short version of the (ISC) 2 code of ethics contains four canons: Protect society, the commonwealth, and the infrastructure. Act honorably, honestly, justly, responsibly, and legally. Provide diligent and competent service to principals. Advance and protect the profession.
When you earn the CISSP certification, you are obligated to do these things. In fact, you are required to take on a new responsibility as a protector of the organizations that you are directly or indirectly involved with.
Keeping Your Certification Current
They say if you don’t use it, you lose it. So it goes with your CISSP certification, anyway. After you earn your CISSP certification, you must do a few things in order to maintain your hard-won CISSP certification:
Keep your contact information current: As soon as you receive your certification, register on the (ISC) 2 Web site immediately, and provide your contact information. (ISC) 2 will inform you about your annual maintenance fee, board of director elections, annual meeting, and events, but only if you maintain your contact info.
Pay your annual maintenance fee (AMF): You are required to pay the annual maintenance fee (AMF) each year in order to continue to hold your CISSP certification. You can easily pay the AMF online at the (ISC) 2 Web site ( www.isc2.org).
Attending training and conferences to earn CPEs: CPEs are Continuing Professional Education credits. You’re required to continue to earn CPEs through security-and professional-related education opportunities in order to maintain your CISSP
certification. During each three-year certification cycle, you have to earn a minimum of 120 CPEs.
Tip To submit your CPEs, log in to the ISC Web site and register your training and other qualified events, one at a time. Conferences and training courses are great ways to earn lots of CPEs, but there are many more ways, too, such as by providing training, attending chapter meetings, or publishing articles or books.
Warning You must keep your CPE documentation with you. (ISC) 2 randomly audits its members to verify that they have
Remaining an Active (ISC)
2
Member
Besides volunteering (see “Considering (ISC) 2 Volunteer Opportunities,” later in this chapter), you can participate in several other activities,
including voting in annual elections and attending the annual meeting and other events:
Vote in (ISC) 2 elections: Every year, the election for the (ISC) 2 Board of Directors takes place. Board members serve three-year terms, and every year one-third of the members are reelected. In any democracy, it is important to participate in the election
process; this concept is just as true for the (ISC) 2 board. If you maintain your contact information with (ISC)2, you’ll receive notifications of upcoming elections.
Attend the (ISC) 2 annual meeting: Each year, the (ISC) 2
annual meeting takes place. In the annual meeting, Board of Directors election results are announced, along with any voted changes in bylaws, a reading of the treasurer’s report, and other items of business. Awards and honors are bestowed upon worthy recipients.
Considering (ISC)
2
Volunteer Opportunities
Volunteers perform much of the work done by the (ISC)2. When you take your CISSP certification exam, most or all the officials in the room are volunteers. Volunteers write the questions in the CISSP exam itself. Most or all the speakers at (ISC) 2 events are volunteers.
(ISC) 2 is much more than a certification or an organization: it is a cause. It is the raison d’être, the reason we exist - professionally, anyway. As such, we should consider throwing our weight into the cause.
Volunteers made (ISC) 2 what it is today, and contributed toward your certification. You can’t stand on the sidelines and watch others do the work. Use your talents to help those who will come after you. There are many ways that you can help. Information on how to volunteer can be found on the (ISC) 2 Web site ( www.isc2.org).
Tip Most sanctioned (ISC) 2 volunteer activities earn CPE credits. Check with (ISC) 2 for details.
Writing certification exam questions
The state of technology, laws, and practices within the (ISC) 2 Common Body of Knowledge (CBK) is continually advancing. In order to be
effective, CISSP exams need to have exam questions that reflect how security is done today.
That means that people working in the industry - like you - need to write the questions. If you’re interested in being a question writer, visit the (ISC) 2 Web site.
Speaking at events
speakers are local volunteers, experts in their professions who want to share what they know and have learned with others. If you have an area of expertise or a unique perspective on CISSP-related issues, consider educating others with a speaking engagement. For more information, visit the (ISC) 2 Web site.
Supervising examinations
Volunteers who have already earned their CISSP certifications supervise local certification exams. Exam volunteers check in candidates, proctor exams, and observe test-takers to ensure that no one cheats on the certification exam.
Remember If you proctor CISSP examinations, you are ineligible for many other activities - in particular, performing any instructional activities such as teaching a CISSP class or study group. If you are interested in proctoring CISSP exams (a noble activity, in our opinion), make sure that your other activities aren’t in conflict with (ISC)2’s terms and conditions for proctoring. Don’t hesitate to contact (ISC) 2 if you’re not sure which other outside teaching activities you may participate in if you’re
considering being a proctor.
Writing articles for the (ISC)
2Journal or (ISC)
2Newsletter
The (ISC) 2 Journal and the (ISC) 2 Newsletter benefit from articles submitted by (ISC) 2 members. The entire security community benefits by sharing what others have learned.
The (ISC) 2 Newsletter is a free monthly publication for all (ISC) 2 members. Find the newsletter, as well as information about writing articles, at www.isc2.org/newsletter/.
Why volunteer?
Volunteerism of any kind is about giving back to a larger community (in this case, the community that helped you to earn your CISSP
certification).
Volunteering looks good on your resume. Personally, we consider this a byproduct of volunteering, and not the primary reason for doing it.
Volunteering for (ISC) 2 or any other cause should be a reflection of your character, and not simply an activity to embellish your resume.
The (ISC) 2 Journal is a fee-based publication that is published
bimonthly. Find information about subscribing and writing articles on the journal’s home page ( www.isc2.org/journal/).
Participating in (ISC)
2focus groups
(ISC) 2 has developed focus groups and QA (quality assurance) testing opportunities. (ISC) 2 is developing new services and needs to receive early feedback during the requirements and design phases of its projects. This is a great opportunity to influence future (ISC) 2 services that will aid future certification holders and us.
Getting involved with a study group
Many communities have a CISSP study group that consists of volunteer mentors and instructors who will help those who want to earn the
certification.
Becoming an Active Member of Your Local
Security Chapter
There are many security organizations around the world that have local chapters, perhaps in or near your community. Here is a short list of some organizations that you may be interested in:
International Systems Security Association (ISSA): www.issa.org
Information Systems Audit and Control Association (ISACA): www.isaca.org
Society for Information Management (SIM): www.simnet.org
InfraGard: www.infragard.net
Open Web Application Security Project (OWASP): www.owasp.org
ASIS International: www.asisonline.org
High Technology Crime Investigation Association (HTCIA): www.htcia.org
Risk and Insurance Management Society (RIMS): www.rims.org
Institute of Internal Auditors (IIA): www.theiia.org Disaster Recovery Institute International (DRII): www.drii.org
Computer Technology Investigators Network (CTIN): www.ctin.org
find the network especially valuable when they’re looking for new career opportunities.
Tip (ISC) 2 doesn’t “do” local chapters today, but who knows - someday they might. Stay informed, or speak up on your own!
Spreading the Good Word about CISSP
Certification
As popular as the CISSP certification is, many people still don’t know about it. And many who may have heard of it don’t understand what it’s all about. Tell people about your CISSP certification, and explain the certification process to your peers. And here are some facts you can share with anyone and everyone you meet:
CISSP is the top-tier information security professional certification.
Over 42,000 security professionals around the world are CISSP certified.
The CISSP certification started in 1989.
The organization that manages the CISSP certification has other certifications for professionals who specialize in various fields of information security. The organization also promotes information security awareness through education programs and events. Promote the fact that you are certified - or are trying to be. How can you promote it? You can simply put the letters CISSP after your name on your business cards, stationery, e-mail signature, resume, blog, and Web site. While you’re at it, put the CISSP or (ISC) 2 logo on there, too.
Technical Stuff If you hold the CISSP certification, you are ISO/IEC 17024:2003 compliant. Find out more by going through press releases from 2005 on the (ISC) 2 Web site.
Promoting other certifications
Associate of (ISC)2: If you can pass the CISSP or SSCP certification exams but do not yet possess the required
professional experience, you can become an Associate of (ISC)2. Read about this on the ISC Web site.
SSCP (Systems Security Certified Practitioner): This midlevel certification is for hands-on security techs and analysts.
These two certs may be steppingstones for your colleagues, and eventually they may be ready for the big one.
Wearing the colors proudly
There’s a lot of neat stuff at the (ISC) 2 online store, from jackets to shirts to mugs to caps. There is something for everybody there. The
organization introduces new items now and again, and runs closeout specials on the stuff no one wanted in the first place.
Using Your CISSP Certification to Be an Agent of
Change
We are agents of change in our respective organizations: The state of threats and regulations is ever changing, and we must respond by ensuring that our employers’ environments and policies continue to defend our employers against harm. Here are some of the important principles regarding successful agents of change:
Identify and promote only essential changes
Promote only those changes that have a chance to succeed Anticipate sources of resistance
Distinguish resistance from well-founded criticism Involve all affected parties the right way
Do not promise what you cannot deliver
Use sponsors, partners, and collaborators as co-change agents Change metrics and rewards to support the changed world Provide training
Celebrate All Successes
Remember You’re not here to preach, but to recognize opportunities for improvement and lower risks to the business. Work within your
Earning Other Certifications
In business and technology, no one’s career stays in one place. We are continuously growing and changing, and ever-changing technology also influences organizations and our roles within them.
You shouldn’t consider your quest for certifications finished when you have earned your CISSP - even if it is the highest-level information security certification out there! Security is a journey, and your CISSP certification is not the end goal, but a milestone along the way.
Other (ISC)
2certifications
(ISC) 2 has several other certifications, including some that you may aspire to earn after receiving your CISSP. (ISC) 2 calls these
concentrations, because they represent the four areas you may choose to specialize in:
ISSAP (Information Systems Security Architecture
Professional): This concentration is suited for technical systems security architects.
ISSEP (Information Systems Security Engineering
Professional): This concentration demonstrates competence for security engineers.
ISSMP (Information Systems Security Management
Professional): Yes, of course this is about security management. CAP (Certification and Accreditation Professional): Jointly developed by the U.S. Department of State’s Office of Information Assurance and (ISC)2, the CAP credential reflects the skills
required to assess risk and establish security requirements for complex systems and environments.
Non-(ISC)
2certifications
Other organizations have security-related certifications, one or more of which may be right for you. None of these directly compete with CISSP, but some of them do overlap with CISSP somewhat.
Non-technical/non-vendor certifications
CISA (Certified Information Systems Auditor): This may be good if you are in internal audit or if your organization is subject to one or more security regulations such as Sarbanes-Oxley, HIPAA, GLBA, PCI, and so on.The Information Systems Audit and Control Association and Foundation (ISACA), at
www.isaca.org, manages this certification.
CISM (Certified Information Security Manager): Similar to (ISC)2’s ISSMP, this certification is suited for you if you are in security management. Like CISA, this certification is managed by ISACA.
CPP (Certified Protection Professional): Primarily a security management certification, CPP is managed by ASIS
International, at www.asisonline.org/certification. PSP (Physical Security Professional): ASIS International also offers this certification.
CBCP (Certified Business Continuity Planner): This is a business continuity planning certification offered by the Disaster Recovery Institute. You can find out more at www.drii.org.
PMP (Project Management Professional): A good project manager is a wonderful thing, especially on larger projects. The Project Management Institute, at www.pmi.org, offers this certification.
Operations, and Security Administration. Our favorite GIAC non-vendor-specific certifications that complement CISSP are the GIAC Certified Forensics Analyst (GCFA) and GIAC Certified Incident Handler (CGIH). Find more information at
www.giac.org/certifications.
Technical/vendor certifications
We won’t even pretend to list all the technical and vendor certifications here. These are some of the well-known vendor-related security
certifications.
CCSP (Cisco Certified Security Professional) and CCIE (Cisco Certified InternetworkingExpert) Security: Cisco also offers several product-related certifications for products including PIX firewalls and intrusion prevention systems. Find out more at www.cisco.com/certifications.
Check Point Security Administration certifications: You can earn certifications related to Checkpoint’s firewall and other security products. Visit
www.checkpoint.com/certification.
MCSA:Security and MCSE:Security: These are two
specializations for the Microsoft Certified Systems Administrator and Microsoft Certified Systems Engineer certifications from Microsoft. Read more at
www.microsoft.com/certification.
CEH (Certified Ethical Hacker): We know, we know. A
contradiction in terms to some, real business value for others. Read carefully before signing. Offered by the International
Council of E-Commerce Consultants (EC-Council). You can find out more at www.eccouncil.org.
Certified UNIX Security Administrator (GCUX), and GIAC Securing Oracle Certification (GSOC). Read more at www.giac.org/certifications.
Security+: This is a security competency certification for PC techs and the like. We consider this an entry-level certification that may not be for you, but you may well advise your aspiring colleagues who want to get into information security that this is a good place to start. You can find out more at
www.comptia.org.
Security5: Like Security+, this is an entry-level security competency certification for anyone interested in learning computer networking and security basics. Find out more at www.eccouncil.org.
There are many other security certifications out there. Use your favorite search engine and search on phrases such as security certification to find information.
Choosing the right certifications
Regularly, we are asked which certifications a person should earn next. Our answer is always the same: Your decision depends upon where you want your career to go. There is no “right” certification for everyone - it is a very individual thing.
When considering other certifications, ask yourself the following questions:
Where am I in my career right now? Are you more focused on technology, policy, operations, or development?
Where do I want my career to go in the future? If you’re stuck in operations but you want to be focusing on policy, let that goal be your guide.
possess.
What do I need to do in my career to earn more
qualifications? You need to consider not only what certifications you may be qualified to earn right now, but also what experience you must develop in order to earn future certifications.
Remember Most nontechnical certifications require you to prove that you already possess the required job experience in order to earn them. A common mistake that people make is this: They want to earn a
Part Overview
Chapter 4: Access Control
Chapter 5: Telecommunications and Network Security
Chapter 6: Information Security and Risk Management
Chapter 7: Application Security
Chapter 8: Cryptography
Chapter 9: Security Architecture and Design
Chapter 10: Operations Security
Chapter 11: Business Continuity and Disaster Recovery Planning
Chapter 12: Legal, Regulations, Compliance, and Investigations
In this part . . .
Chapter 4: Access Control
In This ChapterUnderstanding access control concepts
Discovering identification and authentication techniques
Following methodologies and implementation in centralized and decentralized environments
Knowing methods of attack
Understanding discretionary and mandatory access control Getting to know access control models
Overview
Access control is at the heart of information security. For that matter, access control is at the heart of all security. During medieval times,
castles were built to provide safety and security. The castle was normally built in a strategic location with towering walls surrounded by a moat. Battlements were positioned along the top of the wall with bastions at the corners. A heavily fortified and guarded entrance was secured by a
drawbridge to control entry to (and departure from) the castle. These measures created a security perimeter, preventing hostile forces from freely roaming through the castle grounds and attacking its inhabitants. Breaching the perimeter and gaining entry to the castle was the key to victory for an attacking force. After getting inside, the castle defenses were relatively simple, and the attackers were free to burn and pillage. Hard and crunchy on the outside, chewy in the middle.
Similarly, computer security requires a strong perimeter and elaborate defenses. Unfortunately, a drawbridge doesn’t suffice for access control in computer security. Threats to computer security are much more
sophisticated and prevalent than marauding bandits and the occasional fire-breathing dragon. Access control is still critical to securing a
perimeter, but it’s not limited to a single point of entry. Instead, security professionals must protect their systems from a plethora of threats, including Internet-based attacks, viruses and Trojan horses, insider attacks, covert channels, software bugs, and honest mistakes.
Additionally, you must ensure that the drawbridge operator (the firewall administrator) is properly trained on how and when to raise or lower the drawbridge (following policies and procedures), and you must be sure that he’s not sleeping on the job (that is, monitoring your logs). The End! The Certified Information Systems Security Professional (CISSP)
Uncovering Concepts of Access Control
Access control, in the context of information security, is the ability to permit or deny the use of an object (a passive entity such as a system or file) by a subject (an active entity such as an individual or process). Such use is normally defined through a set of rules or permissions: read, write, execute, list, change, and delete.
Control types
Access control is achieved through an entire set of controls that, identified by purpose, include preventive (which reduce risk) and
detective (which identify violations and incidents) controls. Other types of controls include corrective (which remedy violations and incidents and improve existing preventive and detective controls), deterrent (which discourage violations), recovery (which restore system