File Data Security With Applications Using Ridhcrypt
Abstract—Along with the times, increasing human needs Including the need for information. That way the data files generated by the computer user more days to make a new problem on the computer, one of which is a security problem file readable by others. Therefore, shipping and storage of data via electronic media requires a process that is able to ensure the security and integrity of the data. Cryptography is the science that studies how a message or document we are safe and can not be read by unauthorized parties. To ensure the security and integrity of the data, we need a process of encoding. This data security must be a hardship for others to read easily the stolen data. The process of securing the information to make such information can not be read without the aid of special knowledge is called encryption. But in the process of changing the messages in a language code back into the original message is called decryption. With this background, the necessary application data file protection using cryptographic methods in according with the purpose of computer users today. On securing the data file contained a variety of cryptographic methods and algorithms, one of which is the Rijndael algorithm. Cryptographic algorithm called Rijndael which became known Advanced Encryption Standard (AES) came out as winners of replacement DES cryptographic algorithm held by NIST.
Keywords— AES; Encryption; Decryption; Cryptography;
Data Security Introduction;
I. INTRODUCTION
The number of data files generated by the computer user more days to make a new problem on the computer, one of which is a security problem file readable by others. At the
company level, the file as an asset that is very important and should not be read or copied easily to another company, especially a rival company. Likewise at home users who increasingly require protection against security file stored user especially when the user is using the internet who are particularly vulnerable to theft and file readable by others. It required a security technology file. The security file must be a hard for others to read easily the stolen files. Cryptography is the science that studies how a message or document we are safe and cannot be read by unauthorized parties. During its development, cryptography is also used to identify the sender of the message with a digital signature and authenticity of the message with a digital fingerprint (fingerprint).
1. Problem Identification and Formulation
• With increasing user and the user's computer, the more files are generated and the more important files that need to be kept confidential.
• The number of cases of burglary and theft of files into a file that the computer user's personal assets, and companies.
2. Formulation of the problem
The formulation of the problem in writing this paper is how to preserve the confidentiality of the contents of the files that can not be read by people who do not have permission to utilize cryptographic techniques.
3. Research Objectives
Based on the problems which have been defined above, the purpose is as follows:
2015 International Conference on Automation, Cognitive Science, Optics, Micro Electro-Mechanical System, and Information Technology (ICACOMIT), Bandung, Indonesia, October 29–30, 2015
• To avoid piracy files to secure data by using the algorithm Rijndael
• Makes it easy for users to secure data files.
II. METHODOLOGY RESEARCH
This study so as not to deviate from what has been formulated, it takes some limitations problem. As for the limitations in this study the problem, namely:
A. Rijndael algorithm implemented for cryptographic data files.
B. Rijndael algorithm implemented at the time of encryption and decryption in the input files.
C. Securing the data file is divided into 3 parts: Only File Assets.
D. Input the form File Assets, the resulting output will be stored in encrypted form in a file extension given in the form of aset.
E. Input the form of Just File, the resulting output will be stored in encrypted form in a file extension given in the form of cryptography.
F. Input the form File Demo, the resulting output will be stored in encrypted form in a file extension given in the form of demo.
G. Specially to File Demo, the process of designing, manufacturing and discussion of a special reader File Demo (player) is not included but only described some parts of the course. Because the player is just an additional tool to support third reading of the demo
I. Author only and focuses on cryptographic algorithm Rijndael and discuss and compare with other cryptographic methods.
III. THEORY RESEARCH
Tools application software is a program written and translated by linguage software to complete a particular application. According to the Dictionary of Indonesian Dictionary "The application is the application of a system designed to process data using rule or provision particular programming language". Application is a computer program made to do and execute specific tasks of the user. Applications or instruction series of activities to be executed by the computer.
A.Definition of Cryptography
Cryptography is the science that studies mathematical techniques related to aspects such as the validity of information security, data integrity, and authentication of data (Wahana Computer, 2010)[1]. Cryptography uses a variety of techniques in an effort to secure the data. Data transmission and storage of data via electronic media requires a process that can guarantee the security and integrity of the data transmitted. Such data should remain confidential during shipping and must remain intact upon receipt at the destination (Sianturi, 2013)[2].
B. Algorithm Rijndael
According to Moh. Sjukani (2009: 1)[3] algorithm is a train of thought in completing a job, as outlined in the written form that is understandable to others. Cryptographic algorithm named Rijndael, designed by Vincent Rijmen and John Daemen Belgian came out as winners of replacement DES cryptographic algorithm held by NIST (National Institutes of Standards and Technology) belonging to the US government on 26 November 2001. Rijndael algorithm is then known as Advanced Encryption Standard (AES). After experiencing some of the standardization process by NIST, later adopted as a standard Rijndael cryptographic algorithm officially on May 22, 2002.
C. Rijndael Block Chiper
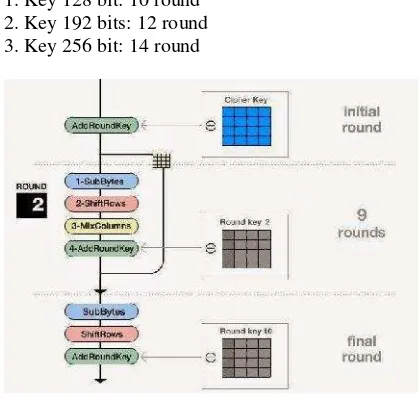
AES has a fixed block size of 128 bits long and long key size of 128, 192, or 256 bits. Based on a fixed block size, AES block work on measuring 4 x 4 matrix in which each cell matrix consisting of 1 byte (8 bits) (Dony Arius2008)[4]. Round key is derived from the cipher key through the key schedule, consisting of key expansion and selection round keys.
The number of round Rijndael cipher used is a function of the size of the key as follows:
1. Key 128 bit: 10 round 2. Key 192 bits: 12 round 3. Key 256 bit: 14 round
Source : Enrique Zabala, AES Rijndael Encryption Cipher Overview, 2012[4]
D. Encryption
Encryption is the process of converting an original message (plaintext) into a message in code (ciphertext). C = E (M)
Description:
C = ciphertext (plaintext encrypted AES) E = Encryption with Key Private M = The original message (plaintext)
In general the Rijndael encryption algorithm as follows: AddRoundKey:
•
Perform XOR between the initial state (plaintext) with the cipher key. This phase is also called the initial round.• Round: Round as Nr - 1 times. Process performed in each round are:
SubBytes: byte substitution using a substitution table (S-box).
• ShiftRows: Shifting lines are wrapping state array. MixColumns: scrambles the data in each column array state.
• AddRoundKey: Perform XOR between the state now with round key.
• Final round: The process for the last round: a) SubBytes
b) ShiftRows c)AddRoundKey
Description of the encryption process is as follows: Add Round Key Add Round Key is basically a combination of the existing text cipher with the cipher key by XOR relationship. The chart can be seen in Fig 2.
Fig. 2.Diagram AES key Round
(Source: Enrique Zabala, AES Rijndael Cipher Encryption Overview, 2012)[4]
On the picture on the left is the cipher text and the right is the key round her. XOR performed per column is the column-1 XOR cipher text in the column-1 round key and so on.
• Sub Bytes
Sub Bytes is the principle of swapping the contents of the matrix or existing table with a matrix or another table called the Rijndael S-box.
• Shift Rows
Shift Rows process () This is a very simple process. At ShiftRows to shift wrapping in the last three rows of the array state. The amount of the shift depends line value (r). Row r = 1 is shifted as far as 1 byte, row r = 2 is shifted 2 bytes, and the line r = 3 is shifted as far as 3 bytes. Row r = 0 is not shifted. Example: Slide rows 0 of 0 bytes: 0 bytes Because it does not do shift and state-was still the same.
4. Mix Columns
Transformation using MixColumns () is the third in one round AES encryption. Here, the columns in the array of state will be required as a polynomial which is in GF (28) and multiplied by the modulo x4 + 1, with a particular polynomial
• Decryption
Decryption is the process of changing the messages in a code language into the original message back.
M = D (C)
Description:
M = The original message after decryption D = Prose decrypted using the private key C = Ciphertext (encrypted plaintext Results)
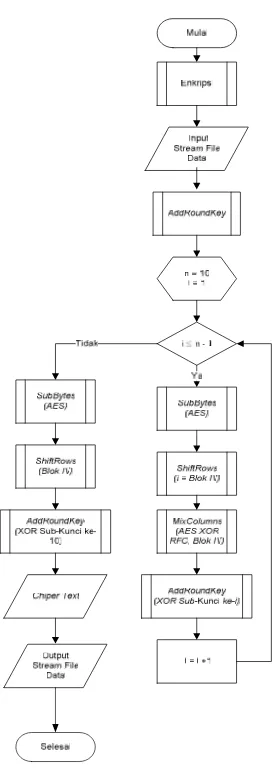
Fig 3. Process Flow Diagram Decryption (Source: Erdi Susanto, Basic Concepts Symmetric and
Cipher transformation can be reversed and implemented in the opposite direction to produce the inverse cipher. Transformation used in the inverse cipher are InvShiftRows (), InvSubBytes (), Inv Mix Clolumns (), and Add Round Key ().
• Rfc 2898 Derive Bytes
Rfc2898DeriveBytes is a class or method with a process that involves taking a key (password), mixer (salt), the number of iterations, and then generates the key depth through calls to GetBytes method. Rfc2898DeriveBytes includes a method for creating a key and initialization vector (Block IV) of passwords and mixers (salt / S-Box / ASCII).
III. ANALYSIS, DESIGN AND RESULT
• User Analysis
Securing data files on Application RidhCrypt divided into three user model. Useful to limit the space for the use of the application as limiting the right of access to the system.
• File Security Analysis Data
Securing data files on RidhCrypt application is divided into three models, namely security File security assets, securing Only File & Security File Demo
• Data File Security Algorithm
Securing data files on RidhCrypt application is using the Rijndael algorithm. Chosen the use of algorithm Rijndael because the author has conducted a series of simple experiments (implementation tool the testing has been included as a module on securing only the file on the application RidhCrypt) for data files and generated cryptographic process both in terms of current when exposed to the files small or large size and without any problems reading either when performing encryption, as well as description back. Other than that can perform encryption algorithm Rijndael with a variety of 128bit AES keys up to 256 bits
Fig 4. Illustration of Cryptography on File Data Using AES Rijndael algorithm[9]
• Flow chart
Fig 5. Flowchart Process Rijndael encryption algorithm AES-128 (10 rounds).
• User Interface Design
A communication mechanism between the user (user) with the system. The user interface (User Interface) can provide information to the user (user) to help direct the flow of the search problem to find a solution.
Fig 6. Design Interface.
Fig 7.Implementation Designing User Interfaces For Admin
•
Testing System
Testing system aims to test specific functions of the software designed. The testing is very important to do so researchers can determine whether the software is made already meet the criteria in accordance with the purpose. Result Comparison Test System
The advantages of using the application with the implementation of Rijndael: To avoid piracy files to secure data by using the algorithm Rijndael Makes it easy for users to secure data files. Can do security files according to intended use. The advantage of using the Rijndael cryptographic data files: It does not take a long time during the encryption and decryption process as a whole.
IV. CONCLUSIONS AND SUGGESTION
Based on the analysis of the system and the overall system testing has been done in the previous chapter, there are several things that can be used as a conclusion to this study include:
• Rijndael algorithm can solve the problems of security in data files.
• Confidentiality files encrypted by Rijndael algorithm is already better by using 128 Bit Block IV with integrated key AES 128 Bit, 192 Bit and 256 Bit.
• Applications built capable of performing the encryption process image data files, documents, music or sounds, movies, and archive files.
• The process of securing data files that were presented this application is divided into 3 methods namely: security asset files, only files and file security demo.
• This application makes users less often because it is only enough to enter keywords in the beginning of any program settings. So that users will become more practical in securing the data file.
• As for suggestions in future research in this application is the security of data files have potential to be developed in order to add a variety of functions, among others for sending files directly to email or some other destination with just one click so that files that have been secured could be distributed to the various techniques and variations without worries The file is read hijacked or unauthorized party to read. It is necessary to research and advanced creative ideas in the future.
REFERENCE
[1] Wahana Komputer 2010, The Best Encryption Tools, Penerbit PT. Elex Media Komputindo 2010
[2] Fricles Ariwisanto Sianturi, 2013, Perancangan Aplikasi Pengamanan Data Dengan Kriptografi
Advanced Encryption Standard (AES),Pelita
Informatika Budi Darma, Volume : IV, Nomor: 1 [3] Moh.Sjukani, 2009, Algoritma (Algoritma dan
Struktur Data 1) dengan C, C++ dan Java, Penerbit Mitra Wacana Media 2009
[4] http://www.erdisusanto.com/2012/10/konsep-dasar-kriptografi-simetris-dan.html
[5] Dony Arius, 2008, Introduction to Cryptography, Publisher Andi, 2008
[6] Jogiyanto, 2005, Analysis and Design of Information Systems, publisher Andi, Yogyakarta
[7] Moh.Sjukani, 2009, Algoritma (Algoritma dan Struktur Data 1) dengan C, C++ dan Java, Penerbit Mitra Wacana Media 2009
[8] Fricles Ariwisanto Sianturi, 2013, Perancangan Aplikasi Pengamanan Data Dengan Kriptografi
Advanced Encryption Standard (AES),Pelita
Informatika Budi Darma, Volume : IV, Nomor: 1 [9] http://banyan.cm.nctu.edu.tw/
computernetwork2/AES_Rijndael(12).ppt
![Fig 3. Process Flow Diagram Decryption(Source: Erdi Susanto, Basic Concepts Symmetric andAsymmetric Cryptography, 2012)[4]](https://thumb-ap.123doks.com/thumbv2/123dok/263104.505925/3.595.321.521.403.666/process-diagram-decryption-susanto-concepts-symmetric-andasymmetric-cryptography.webp)
![Fig 4. Illustration of Cryptography on File Data UsingAES Rijndael algorithm[9]](https://thumb-ap.123doks.com/thumbv2/123dok/263104.505925/4.595.330.551.51.213/fig-illustration-cryptography-file-data-usingaes-rijndael-algorithm.webp)