A Software Defined Sketch System for Traffic Monitoring
Theophilus Wellem
†,‡, Yu-Kuen Lai, Wen-Yaw Chung
†Dept. of Electronic Engineering†, Dept. of Electrical Engineering
Chung Yuan Christian University, Chung-Li 32023, Taiwan
{g10202604, ylai, eldanny}@cycu.edu.tw
Dept. of Informatics‡
Satya Wacana Christian University, Salatiga 50711, Indonesia
[email protected]
ABSTRACT
Sketch-based data streaming algorithms are used in many network monitoring applications. The sketch data struc-ture is capable of summarizing high-speed network traffic in real-time and producing accurate estimation result of a specific traffic measurement task. However, due to the fixed hardware implementation of the sketch counter array, the flexibility of adopting the same data structure for various traffic measurement applications is limited. In this work, we propose a scheme for the sketch-based monitoring appli-cations to define the flow keys for updating the sketch data structure in more general settings. The system prototype is implemented on the NetFPGA-10G platform.
Categories and Subject Descriptors
C.2.3 [Network operation]: Network monitoring
General Terms
Algorithms, Design, Performance
Keywords
Entropy estimation; Bloom filter; Sketch; NetFPGA;
1.
INTRODUCTION
Sketch-based data streaming algorithms are used in high-speed network monitoring applications (e.g., change detec-tion [1], superspreader detecdetec-tion [2], entropy estimadetec-tion [3]). The sketch data structure is used in network traffic monitor-ing for summarizmonitor-ing packets into a compact representation. It has small memory footprint and guaranteed accuracy on its estimation result. In addition, the sketch data structure is updated for each incoming packet without packet sam-pling.
As studied in [4], the sketch-based data streaming algo-rithms for traffic monitoring are efficient. However, they are too application-specific and lack of generality to be imple-mented as primitive operations on network devices. Sketch-based methods are also not flexible because each flow key requires separate instance of sketch data structure. Fur-thermore, because sketch data structure does not maintain any flow keys, a complex reversible sketch method is often employed by monitoring application to obtain the original flow key. This adds more complexity to the implementation on network devices.
NetFPGA-10G Network
Traffic
Hash Function
Flow statistics table (counters ) SRAM and Flow key table in DRAM
Header Parser
Other supporting
modules Read the table and counters
from NetFPGA via PCIe interface
Settings from host software/Commands Sketches Sketches Sketches
CPU + GPU (Heterogeneous System
Architecture , HSA)
Monitoring Applications (Flow monitoring and statistics functions)
FPGA Hardware
Figure 1: System architecture
OpenSketch [4] is designed to make sketch-based measure-ments on network devices more general and flexible by using a customized data plane and control plane. The OpenSketch data plane relies on hashing and wildcard rules (classification using TCAM) to choose specific flow to collect and measure. Its control plane consists of measurement library (Count-Min sketch, reversible sketch, etc.) and applications.
Different from OpenSketch, we propose a data plane that employs two tables for flow-level data collection (flow key, byte/packet count). By using these tables, the sketch-based monitoring applications can have the flexibility of selecting flow key, without using a classification scheme using TCAM.
2.
DESIGN AND ARCHITECTURE
The overall system architecture is shown in Figure 1. The data plane prototype is implemented on the NetFPGA-10G platform. For each packet, the 5-tuple flow key is extracted from the packet by the header parser module. The hash function module then computes a hash value from the flow key as an address and store the flow key in the SRAM ta-ble. The hash function module is implemented based on 5-universal hash function and linear probing [5] to handle the hash collisions with constant number of probes per lookup. There are two tables in the system. The table in QDRII SRAM is used to store the flow counts. The table of 5-tuple
flow information is kept in the RLDRAM queue.
During an observation interval, when a flow entry is cre-ated, its 32-bit flow ID and counters are stored in the ta-ble in SRAM. The flow is also checked for its existence in DRAM by using a Bloom filter. If the flow does not ex-ist, its 5-tuple information is added to the flow key table in RLDRAM FIFO. After the observation interval, both of the flow counter and flow key tables are sent to the host via the PCIe interface. Therefore, the tables (5-tuple key and counter) are only kept in the SRAM and DRAM dur-ing the observation interval. The CPU then processes the flow data and updates the sketch data structures based on the application settings (e.g., which flow key is used to up-date the sketch). The CPU also performs the queries over the sketch data structures of previous observation intervals with the current flow keys to identify the anomalies in the traffic, without the complex reversible sketch method.
The time needed for application runs on the host CPU to read data from SRAM and DRAM via the PCIe interface is important for proper operation of the system. For the table size and number of flows processed in our system, it took less than 5 ms for the application to read the data from SRAM and DRAM. Furthermore, the processing time on CPU side (for sketch updates and queries) is shorter than the observation interval.
This scheme provides a software-defined flexibility for net-work monitoring applications using various sketch-based data streaming algorithms.
3.
EVALUATION
In current prototype implementation, the flow counter ta-ble has 512k entries. Each entry contains the 32-bit flow ID, 32-bit packet counter and 64-bit byte counter (16 bytes per entry), with total size of 8 MB. The flow key table en-try contains the 104-bit 5-tuple (13 bytes per enen-try). For 512k flow entries, the total DRAM space needed is 6.5 MB. Therefore, the memory space requirements for these tables can be accommodated in the SRAM and DRAM available on board. Four Bloom filters size, with three hash functions (k= 3) used in the evaluation.
We evaluated our system with trace-driven tests using trace available from CAIDA [6]. The trace, with duration of 56 seconds, consists of 28.7 million packets and 1.4 million distinct 5-tuple flows. The observation interval used in the experiments is 15 seconds. In this interval, the number of distinct 5-tuple flows is ranging from 385k to 500k.
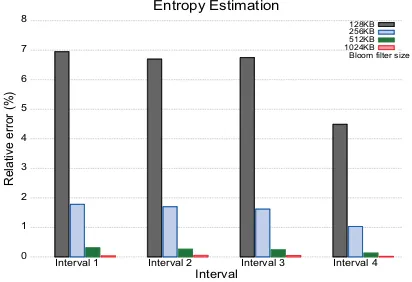
Entropy estimation application from [7] is run on CPU to estimate the flow 5-tuple entropy norm. The accuracy met-ric used for entropy estimation is relative error. As shown in Figure 2, the estimation accuracy increases with the in-creases of Bloom filter size due to reduced false positive rate of the Bloom filter. Using the information from the tables in SRAM and DRAM, the monitoring application can easily select different flow keys (source IP, destination IP, or their combinations) and compute the entropy norm.
4.
CONCLUSION AND FUTURE WORK
The proposed scheme provides the software-defined flexi-bility for sketch-based monitoring applications to choose flow keys to process. Using entropy estimation as the measure-ment task, the accuracy of measuremeasure-ments is shown for ano-maly detection. Other applications, such as superspreader
0 1 2 3 4 5 6 7 8
Interval 1 Interval 2 Interval 3 Interval 4
Relative error (%)
Interval Entropy Estimation
Bloom filter size 128KB 256KB 512KB 1024KB
Figure 2: Experiment results
detection from our previous work in [8] and change detec-tion are under development based on the proposed scheme. Currently, the memory requirements for the tables are quite large if we want to increase the observation time interval. More works, such as compressing the flow entries and coun-ters need to be done in order to improve the system perfor-mance with smaller memory requirements.
Acknowledgments
This research was funded in part by the National Science Council, Taiwan, under contract number NSC 102-2221-E-033-031, MOST 103-2221-E-033-030, and MOST 103-2632-E-033-001.
5.
REFERENCES
[1] B. Krishnamurthy, S. Sen, Y. Zhang, and Y. Chen. Sketch-based change detection: Methods, evaluation, and applications. InProceedings of the 3rd ACM SIGCOMM Conference on Internet Measurement, IMC ’03, p. 234–247, 2003. ACM
[2] Q. Zhao, A. Kumar, and J. Xu. Joint data streaming and sampling techniques for detection of super sources and destinations. InProceedings of the 5th ACM
SIGCOMM Conference on Internet Measurement, IMC
’05, p. 77–90, 2005. USENIX Association.
[3] A. Lall, V. Sekar, M. Ogihara, J. Xu, and H. Zhang. Data streaming algorithms for estimating entropy of network traffic.SIGMETRICS Perform. Eval. Rev., 34(1):145–156, 2006.
[4] M. Yu, L. Jose, and R. Miao. Software defined traffic measurement with OpenSketch. InProceedings of the 10th USENIX Conference on Networked Systems
Design and Implementation, NSDI’13, p. 29–42, 2013.
USENIX Association.
[5] M. Thorup and Y. Zhang. Tabulation based 5-universal hashing and linear probing. 2009.
[6] The CAIDA UCSD Anonymized Internet Traces equinixsanjose.dira.20120119-125903.utc.anon.pcap.gz, 2012
[7] Y.-K. Lai, T. Wellem, and H.-P. You. Hardware-assisted estimation of entropy norm for high-speed network traffic.Electronics Letters, 50(24):1845–1847, 2014. [8] T. Wellem, G.-W. Li, and Y.-K. Lai. Superspreader
Detection System on NetFPGA Platform. In Proceedings of the Tenth ACM/IEEE Symposium on Architectures for Networking and Communications
Systems, ANCS ’14, p. 247–248, 2014. ACM.