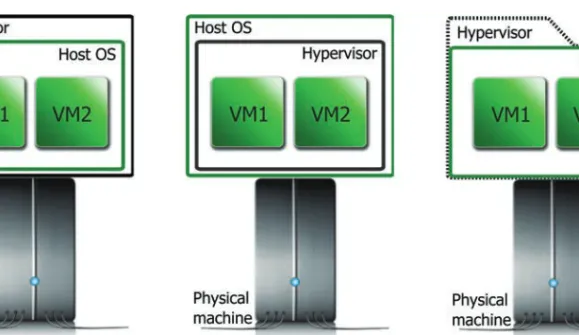
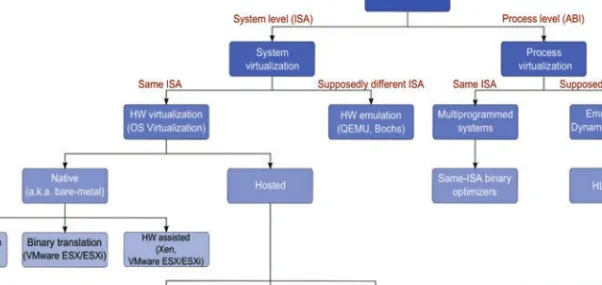
Thus, the architectural position of the hypervisor and the host operating system is swapped in the case of native and hosted virtual platforms. In the first case, the management interface is part of the host operating system, e.g. VMware ESX, KVM, Xen, Microsoft Hyper-V, hosted virtual platforms.
COMPROMISING THE GUEST
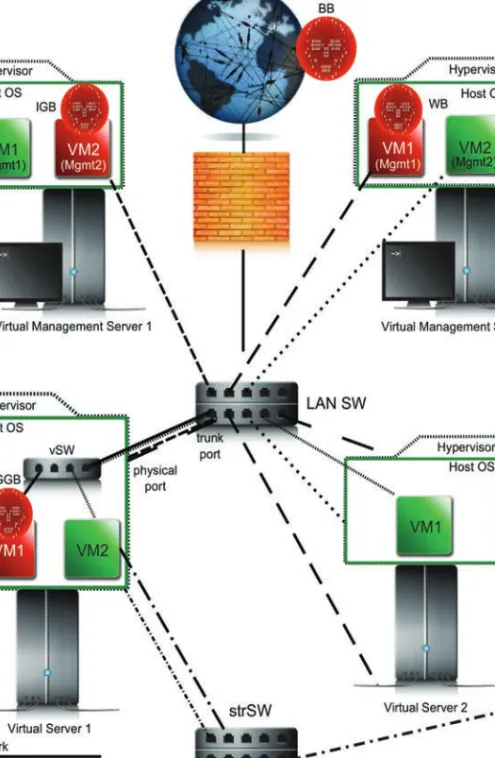
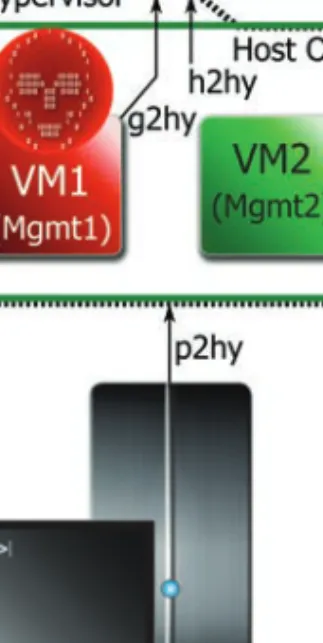
- Internet to Guest (i2g)
- Guest to Guest (g2g)
- Virtual Machine Migration Network to Guest (vmmn2g)
- Guest to Self (g2s)
- Management interface to Guest (m2g)
This may be due to an unresolved issue in the hypervisor's memory management module (MMU) that allows a malicious user to access the memory pages of other guest virtual machines. It waits until the VMM's periodic memory scan detects identical pages with other guests and merges them. The adversary issues write access to one of the pages of the allegedly running application and measures the access time.
In practice, when the processor is operating in protected mode, the two least significant bits in the code segment (CS) register represent the current privilege level (CPL). But in virtual 8086 mode, the CPL is always least privileged (3) regardless of LSB bits in the CS register. Furthermore, when a page fault (#PF) is generated, the processor pushes the actual value of the CS register and the instruction pointer onto the top of the stack, along with an error code that references the circumstances of the exception.
COMPROMISING THE HOST OS
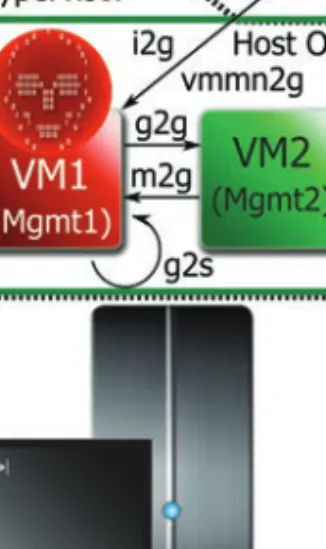
Guest to Host OS (g2h)
This way, the attacker has a communication/covert channel between the guest and host OS through which he can escape into the host OS. This definition is also important for virtualized systems, where an unprivileged attacker in the guest can gain access to sensitive information of the host OS. This poses a real security threat, allowing sensitive information to flow from the host OS to the guest OS.
In contrast, arbitrary code execution is an active and realistic threat that can greatly compromise the host operating system. Namely, it allows an attacker with unprivileged access to the guest operating system to execute arbitrary code on the host operating system by exploiting a vulnerability in the virtualized environment. Arbitrary file writing. An adversary in the guest may be able to gain write access to an arbitrary file on the host operating system.
Host OS to Self (h2s)
Arbitrary code execution. The attacks against the host operating system discussed previously were passive in the sense that the attacker could not directly manipulate the operation of the host operating system, that is, he could only freeze or make it unstable. For example, Kortchinsky [2009] investigated a vulnerability in the display function within the vmware-vmx binary, which allows its users to execute arbitrary code on the host operating system. The attack can be accomplished with minimal prerequisites (guest gray box) as the adversary only needs to instruct the VMware SVGA II driver inside the guest VM to send arbitrary code snippets to the memory (framebuffer) of the host's vmware vmx - process to copy.
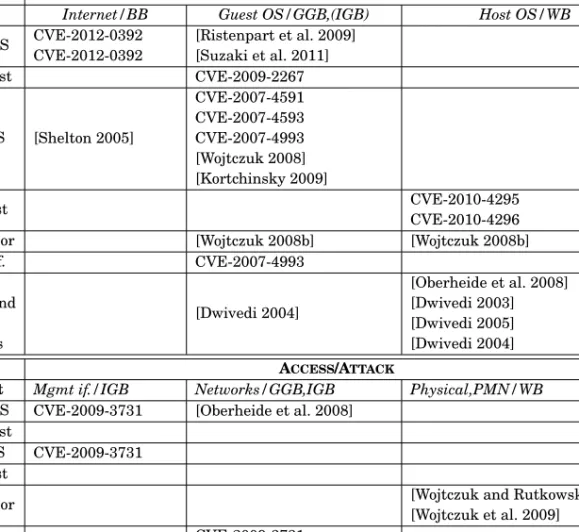
CVE-2007-1744 discloses a directory overflow vulnerability in the Shared Folder feature of VMware, where a guest user could use the I/O backdoor previously discussed in Section 6.1.2 to access an arbitrary file write to the host operating system when a directory is shared. CVE refers to this flaw in the mount processvmware stack of hosted VMware products that allows a host operating system user to gain extra privileges. In our definition, this is a certain type of white-box attack, since the adversary has restricted access to the host.
Internet to Host OS (i2h)
In this example, the access() system call is used to check the user's permission for a file opened by thefopen() system call. However, this leads to a race condition because the attacker can change the file reference returned by thefopen() function to a restricted resource, such as the /etc/shadow file, before calling thewrite_to_file() function.
COMPROMISING THE HYPERVISOR
Guest to Hypervisor (g2hy)
More precisely, access() checks the real UID and GID of the calling process instead of the effective IDs used by fopen(). An adversary can compromise the hypervisor in different ways depending on the access rights he has. The only difference between a driver domain and a traditional guest is that the former has direct access to certain physical resources, such as network cards or disk controllers.
These malicious MSIs allow the adversary to execute code in the context of the Xen hypervisor or access arbitrary physical memory locations. Note that these attacks are either limited to paravirtualized domains (eg in Xen) or processors without interrupt remapping capabilities.
Host OS to Hypervisor (h2hy)
Physical/Physical Management Interface to Hypervisor (p2hy)
COMPROMISING THE MANAGEMENT INTERFACE
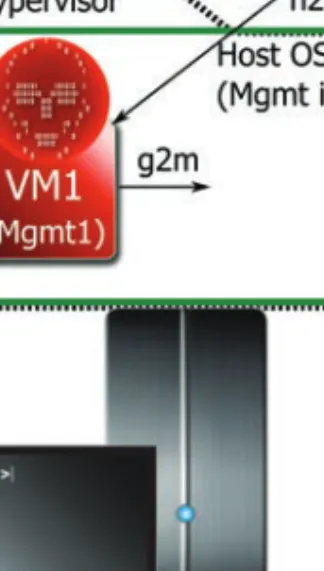
Guest to Management Interface (g2m)
Arbitrary Code Execution.CVE-2007-4993 is one example where a privileged guest user above Xen 3.0.3 can create a malicious boot configuration file (grub.conf) to execute arbitrary commands in the host operating system during system startup. By doing so, he can control other guest VMs or compromise the host operating system at will. Note that this is an indirect attack against the operating system of the administrator, so in table I the threat is also classified as a guest operating system to management interface/host operating system attack.
Information leakage. Another security issue is described in CVE where the VMware VI Client retains the server password in its process memory after connecting to the virtual center, allowing a guest user to read it. This way, a malicious user, who enters the guest through a black-box attack, can read the admin password of the legal guest user.
Network to Management Interface (n2m)
CVE-2009-3731 reports multiple cross-site scripting (XSS) vulnerabilities in various VMware products that could allow a remote attacker to inject arbitrary script or HTML code into the web interface. By doing so, the next time a system administrator opens the web interface, the embedded script is executed on his local computer, causing a system attack. He could, for example, open a root shell that could allow him to compromise other servers in the virtual architecture with administrator privileges.
COMPROMISING NETWORKS
Attack Surfaces of Physical and Virtual LANs
He could e.g. open a root shell that could allow him to compromise other servers in the virtual architecture with administrator privileges. VST) and virtual guest tagging (VGT), which defines whether VLAN tagging of packets is performed by the physical switch (EST mode), the virtual switch (VST mode), or the virtual machine (VGT mode). In the case of VGT mode, for example, VLAN tags are preserved between the virtual machine network stack and the physical switch when L2 frames are transmitted to/from virtual switches. CAM/MAC Flooding.Switches contain content-addressable memory for storing VLAN, port, and MAC address mappings in CAM tables to forward frames to appropriate egress ports.
He can use Gratuitous ARP11 or other ARP messages to poison the segment, causing the hub/switch to associate the adversary's MAC address with the IP address of another host. He can thus mediate and launch man-in-the-middle attacks between two parties by forwarding the intercepted and/or modified traffic to the original target (e.g. edge gateway). DHCP Address Range Starvation An adversary on the LAN can starve the local DHCP server of available addresses by continuously requesting new dummy leases in the DHCP range.
Compromising Networks of Virtual Systems
Also in the case of Xena, storage traffic is unencrypted and goes through the control domain (Dom0) if we use IP-based storage (NFS, iSCSI). Each node in an FC SAN has a 24-bit address managed by the fabric and a 64-bit World Wide Name (WWN)13 determined by the host bus adapter (NIC). Below we present some practical attacks on iSCSI; several examples are discussed in [Dwivedi 2005].
However, if you configure VMware to not authenticate the initiator and target, an adversary could potentially impersonate either side of the connection and perform a man-in-the-middle attack. In an iSNS man-in-the-middle attack, the adversary first identifies an iSNS server listening on port 3205. This means that the fake iSNS server captures and forwards all traffic sent to the valid iSNS server, so that the adversary has full control over the plaintext packets , which are transferred.
MISCELLANEOUS THREATS
X cannot access this folder from either Windows or *NIX, but it can check the UID and GID of Y from the *NIX console (ls -al). By doing this, CIFS permissions are undermined using NFS and access is granted to the restricted resource. As just shown, storage virtualization carries potential risks for virtual infrastructures; therefore, special attention should be paid to their proper configuration.
Best practices suggest also isolating production networks, which are usually connected to the internal network through the data management zone (DMZ). That is, DMZ servers must be secured to stop malicious users (network or local). Moreover, as DMZ services are now also preferred to be virtualized as well, more enhanced countermeasures should be applied to secure them [Cisco and VMware 2009].
COUNTERMEASURES
- Secure Programming
- Hardening the Hypervisor and VMs
- Restriction of Physical Access
- Policy and Isolation
- Separation of Roles
- Separation of VMs
- Considering the State of VMs
- Mitigating Design Discrepancies
- Securing the Network
- Adequate Logging and Monitoring
Unused physical interfaces should be disabled in order to accommodate the attack surface and limit the damage caused. Control policies for virtual environments must be implemented and maintained to provide the same level of security as physical environments. Additionally, multi-factor authentication and dual-check or split administrative passwords for different administrators should be used to reduce the risk of a malicious supervisor.
Role-based access control (RBAC) should be maintained for virtual components to avoid unwanted access to resources. For example, in case of guest-to-guest attacks (Section 5.2), virtual environments should be critically secure, especially when multi-tenancy is supported. To prevent WWN spoofing and zone hopping (section 9.2.4), port-based hard zoning should be implemented in FC SANs.
SUMMARY
Spanning Tree attacks (Section 9.1.4) can traditionally be prevented by proprietary tools (eg bpdu-guard, root-guard, from the vendor), so virtual switches must implement such methods by default. To mitigate the risk of most of the attacks targeting storage networks, system administrators must separate this traffic and apply secure channels (IPSec, SSL) to protect the data transmitted here. In Proceedings of the 12th International Conference on Architectural Support for Programming Languages and Operating Systems (ASPLOS).
DMZ Virtualization Using VMware vSphere 4 and the Cisco Nexus 1000V Virtual Switch.http://www.VMWare.com/resources/techresource/10035. Security Guidance for Full Virtualization Technologies: National Institute of Standards and Technology Recommendations.