Michal Wozniak Wroclaw University of Technology, Poland Mohsen Sharifi Iran University of Science and Technology, Iran Murugan D. Mokhov Concordia University, Canada SunYoung Han Konkuk University, South Korea Susana Sargento University of Aveiro, Portugal Salah S .
Organized By
Suresh Sankaranarayanan Unibersidad ti Laud nga Indies, Jamaica Michael Peterson Unibersidad ti Hawaii idiay Hilo, E.U.A. Brajesh Kumar Kaushik Yan Luo Unibersidad ti Massachusetts Lowell, E.U.A. Yao-Nan Lien Nailian nga Unibersidad ti Chengchi, Taiwan Rituparna Chaki Unibersidad ti Teknolohia ti Laud a Bengal, India Somitra Sanadhya IIT - Delhi, India, ti India.
Distributed and Parallel Systems and Algorithms
DSP/Image Processing/Pattern Recognition/
Multimedia
Software Engineering
Database and Data Mining
Keyframe Detection Based Semantic Event Detection and Classification Using Heirarchical Approach for Cricket Sports Video.
Soft Computing (AI, Neural Networks, Fuzzy Systems, etc.)
Networks and Communications
Network and Communications Security
Sur Samarendra Nath, Bhaskar Debasish, and Bera Soumyasree A Lightweight Protocol for Data Integrity and Authentication in.
Wireless and Mobile Networks
Implementation of invisible digital watermarking by embedding data in computationally compressed form in image using variable length. Arun Srinivas Parthibarajan, and Vigneswaran Narayanamurthy An Intelligent Network for Offline Signature Verification Using Chain.
Security and Information Assurance
Ad Hoc and Ubiquitous Computing
Wireless Ad Hoc Networks and Sensor Networks
Improved Ant Colony Optimization Technique for Mobile Adhoc Networks
1 Introduction
In this work, we present an improved optimization technique for mobile adhoc networks using the ACO concept. Simulation results are presented in Section 5, and Section 6 provides conclusions and directions for future work.
2 Related Work
In early applications, ACO was used for routing in telecommunication networks, and a successful algorithm in this domain is Ant Net [11].
3 Applying ACO on MANETs
- FORWARDING
- BACKTRACKING 1. At destination node
- PACKET FORWARDING
- ROUTE MAINTENANCE
Each node in the network has a routing table whose size is the degree of the node multiplied by the number of nodes in the network. The pheromone value is updated in the node's routing table according to the quality of this route.
4 The Model Formulation
Transition Probability
The transition probability [ ] mainly helps to find the location of a new pixel in the movement of ants and is defined as .
Directional Probability
Pheromone Update
5 Simulation Framework and Results
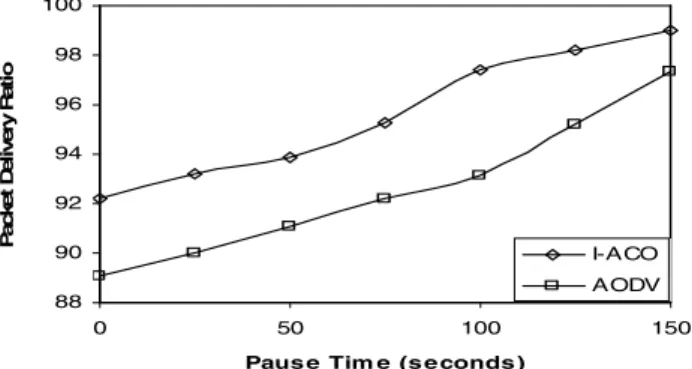
Average End to End Delay
But for all speed values, the average end-to-end delay for I-ACO is much less compared to AODV. It can be seen in Figure 5 that as the transmission range of the nodes increases, the value of the average end-to-end delay decreases for both schemes.
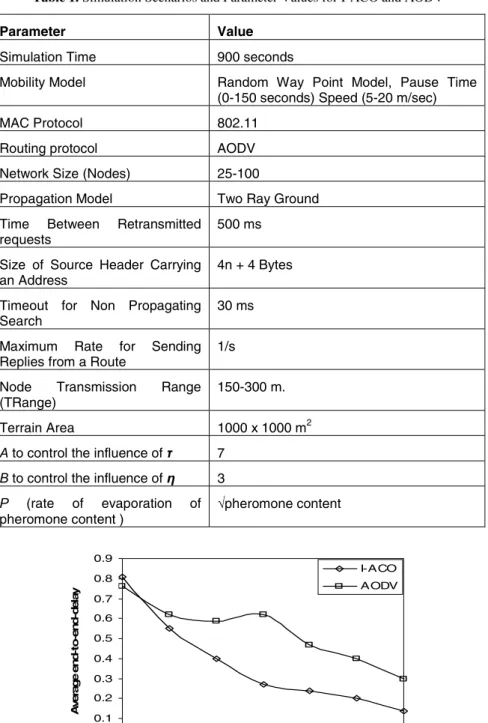
Packet Delivery Ratio
It can be seen from Figure 9 that increasing the transmission range of the nodes increases the value of the packet delivery ratio for both schemes. But again I-ACO is a better option in terms of the number of successful packets for different values of the nodes' transmission range from 150 meters to 300 meters.
6 Conclusion and Future Work
At a very high transmission range of 300 meters, I-ACO can successfully deliver more than 98% of packets, while AODV can deliver about 96%. The analysis of the scheme is still in progress to verify the value of the control overhead incurred for different network scenarios, and I-ACO also needs a better approach for network energy management.
I: Proceedings of the International Conference on Advanced Computing and Communication Technologies for High Performance Applications (2008).
A Performance Comparison Study of Two Position-Based Routing Protocols and Their Improved Versions
Typically, the source includes information about the intended location of the destination in each data packet. The source node includes the recently acquired coordinates of the destination location in the header of the data packets.
2 Review of Position-Based Routing Protocols
The location of the forwarding node in which greedy forwarding failed (and perimeter forwarding started to be used) is recorded in the data packet. According to DNP, before forwarding a data packet based on the location information of the destination in the packet header, each node searches its neighbor list for the destination node.
3 Simulation Environment and Performance Results
Control Message Overhead
We measure the total check message count as the number of destination location update query messages received by nodes in the network. Note that we measure the total control message count as the number of control messages received by nodes in the network, rather than the number of control messages transmitted.
Hop Count per Path
The main reason for this increase in the hop count for GRPP is that while forwarding a data packet to the destination, the forwarding node selects the next hop node as the neighbor node that exists (i.e. currently exists and is predicted to exist for the next three seconds) closer to the straight line joining the forwarding node's location and the location of the final packet destination, as specified in the data packet header. The hop count would have been minimized if the forwarding node chose the next hop node as the neighbor node closer to the destination (similar to the GPSR approach).
End-to-End Delay per Data Packet
The packet delivery ratio of GRPP, GPSR_AGF and GRPP_AGF is the largest in most simulation conditions. Note that the packet delivery rates for GPSR and GRPP decrease as the value of MaxTupdate increases.
4 Conclusions and Future Work
This is attributed to the lack of accurate destination location information as the time period between two consecutive destination location update searches increases. GRPP and its improved versions deliver a relatively higher packet delivery ratio compared to GPSR and its improved versions.
Privacy Preserving Naïve Bayes Classification Using Trusted Third Party Computation over Distributed
Progressive Databases
Privacy Preserving Naïve Bayes Classification Using Trusted Third-Party Computing 25 dataset consists of the union of these datasets. One of the methods in a distributed computing environment, which uses the secure sum multiparty calculation technique for privacy protection, is Naive Bayes classification [1].
3 Progressive Naïve Bayes Classification Using Trusted Third Party Computation over Distributed Databases
Horizontal Partition
Assuming that the total number of cases is public, the required probability can be calculated by dividing the corresponding global sums, leaving the local number of cases undisclosed. Since tcurrent exceeds the POI, we also need to remove cases that are no longer in the required period of interest.

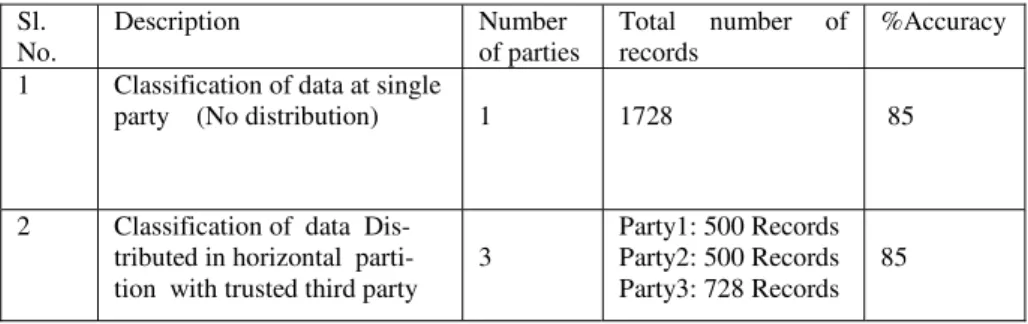
4 Results
The trusted third party is aware of the distribution of different parties with all attributes and class values.
5 Conclusion
Cluster Based Mobility Considered Routing Protocol for Mobile Ad Hoc Network
So, reasonable, cluster head election is important for the performance of the mobile ad hoc network. In section 2, a comparative study of some of the existing routing topologies was performed.
2 Related Works
The two-step Cluster Head Selection routing protocol [6] is used to solve the LEACH cluster head count variability problem [13]. A cluster head with heavy relay traffic has fewer cluster members, so the load on the cluster heads will be balanced.
3 Proposed New Routing Protocol
A routing protocol for a mobile ad hoc network based on cluster-based mobility 37 timeout value for location information, ie. when the limit set for location information is exceeded, the resource resorts to a recovery process. In Mobile Ad hoc Network Routing Protocol [2], we can calculate the movement of mobile nodes with respect to time using beacon messages.
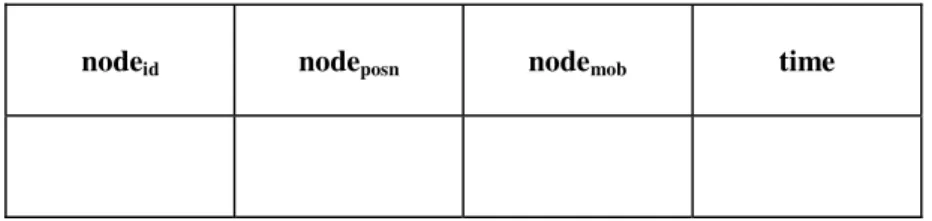
4 Performance Analysis
3, there is a comparison between number of nodes and hop count for finding route from source to destination. Here we also observed that as the number of nodes increases, the hop count initially also increases.
5 Conclusions
From the above two figures, we observed that our new proposed and implemented CBMCRP routing algorithm performs better and also its time complexity is less than another routing protocol called AMOBIROUTE [1]. In: Proceedings of the Fourth Annual ACM/IEEE International Conference on Mobile Computing and Networking (Mobicom 1998), Dallas, TX, p.
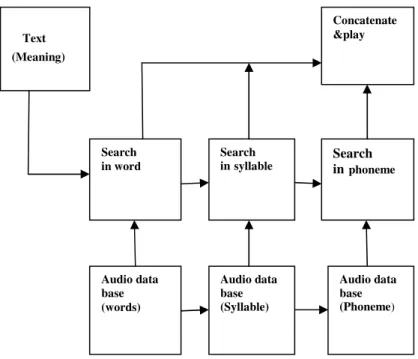
Speech Transaction for Blinds Using Speech-Text-Speech Conversions
2 Problem Statement
3 Architecture of Speech Recognition Method
4 Unit Selection Synthesis
6 Steps for Dictionary System
In example 2.a, the database is connected and the word will be checked against the words in the database and the corresponding meaning defined there will be identified. 4.
7 Conclusion
25] Segi, H., Takagi, T., Ito, T.: A concatenative speech synthesis method using variable-length context-dependent phoneme sequences as search units. 26] Lewis, E., Tatham, M.: Combining words and syllables in text-to-speech synthesis [27] Gros, J.Z., Žganec, M.: An efficient unit selection method for combining text-to-speech.
Floating-Point Adder in Techology Driven High-Level Synthesis
1 Introduction
High-Level Synthesis
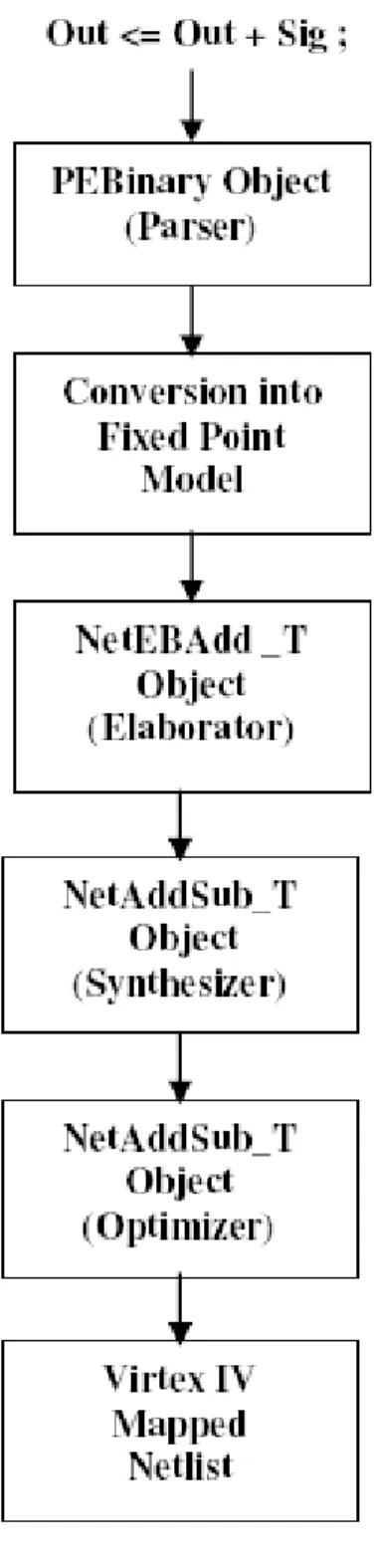
The parser converts the HDL input syntax into an annotated parse tree, which is then constructed into an intermediate representation.
Target Technology
2 Related Work
This compiler converts the floating-point algorithms into the corresponding fixed-point algorithms, synthesizes and generates optimized technology-specific netlist for a fixed-point processor.
3 Technology Driven HLS
Right Inference in Parsing
TSIR
4 Floating-Point Algorithms in THLS
5 Floating-Point Adder in THLS
Floating-Point Adder
Conversion of floating-point model to fixed-point model is performed by a set of Verilog files in the above adder. It takes two single precision floating point numbers and divides two numbers: the large mantissa with a 1 in the MSB (Most Significant Bit) and the minor mantissa.
Compiler Transformations
6 Implementation Framework
Its devices are manufactured on a state-of-the-art 90nm copper process using 300mm (12-inch) wafer technology. There are up to 40 speeds in the Virtex-IV Configurable Logic Block (CLB) compared to previous generation devices [11].
7 Results
Silicon Usage
Advanced Silicon Modular Block's innovative column architecture is unique in the programmable logic industry.
Power Consumption
THLS compiler has 26% reduction in silicon consumption compared to the conversion (fixed-point) and compiler methodology (ISE).
8 Conclusion
Tripp, J.L., Peterson, K.D., Ahrens, C., Poznanovic, J.D., Gokhale, M.B.: TRIDENT: 'n FPGA-samestellerraamwerk vir drywende puntalgoritmes. In: International Conference on Advanced Computing and Communication - ADCOM 2007, IEEE, Indian Institute of Technology Guwahati, Indië (Desember 2007).
Differential Artificial Bee Colony for Dynamic Environment
This paper proposes a new strategy based on differential update and the external result, and is therefore called Differential Artificial Bee Colony (DABC). Again, an external archive is maintained to maintain the number of good solutions produced, and the members of the archive are randomly selected for differential updates.
2 Artificial Bee Colony (ABC) Algorithm
Differential Artificial Bee Colony for Dynamic Environment 61 consists of the employed bees and the second half includes the onlookers. The dance of the employed bees decides where the onlooker bees go to forage.
3 Differential Artificial Bee Colony (DABC)
Differential Update Strategy with Elite Bee
The bees search for the food sources to maximize the objective function F(θ), θ∈R(for maximization problem). Theθi is the position of the ideal food source and F(θi) the fitness of the nectar quantity located at θi.
Preserving Good Solutions: The Archive
According to the differential updating strategy, the weighted difference between the bee and its neighbor is added under the guidance of the elite bee as shown in Fig.
Differential Update Strategy with Exemplars of Archive
4 Simulation
Parameter Settings and PC Configuration
Algorithms
Benchmark Functions
The functions are shifted by adding the random bias to the original value−→x to obtain the new shifted variable−→y =−→x−O. The random bias is generated in the search range for each direction (trace) and the algorithms are allowed to search that run as follows.
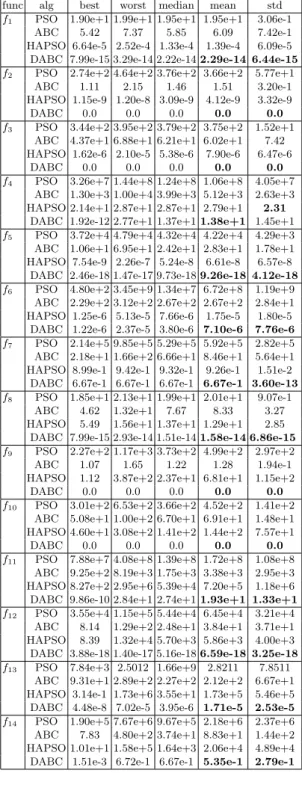
5 Results
Mean Results
Robustness
Differential artificial bee colony for dynamic environment 65 Table 2. Optimum values achieved with functions of dimension=10. Differential artificial bee colony for dynamic environment 67 Table 4. Optimum values achieved with functions of dimension=50.
Mean Result Comparison with Other State-of-the-Art
A value of 0.0 for the standard deviation indicates a very stable nature of the algorithm, any other value indicates the deviation. Table 4, which records the results of 50D problems, shows the stable nature of DABC for all problems except problems f4, f6.
6 Conclusion
Alok, S.: An artificial bee colony algorithm for the minimum leaf span tree problem. Karaboga, D., Basturk, B.: A powerful and efficient algorithm for numerical function optimization: artificial bee colony (abc) algorithm.
FAM2BP: Transformation Framework of UML Behavioral Elements into BPMN Design Element
2 Review of Related Work
3 Scope of Work
FAM2BP: UML Behavioral Element Transformation Framework 71 framework based on the relational model to address this need. Finally, an algorithm is presented to automatically transform UML elements into BPMN elements.
4 FAM2BP: Proposed Transformation Model
Formalized Analysis Model
The Relational Model
A use case activity whose node is marked as "end" will be assigned as the end event of the BPMN node. A use case activity whose node is labeled "action / decision" will be assigned as an intermediate BPMN node event.
Algorithm for Automated Transformation
- Algorithm NodeGeneration to Generate BPMN Node
- Algorithm FlowGeneration to Generate the Flow between bpmn Nodes We use an array representation FAM_flow to represent the flow between different
The following query is the realization of Rule 1 in Section 4.3. It generates the start of the #BPMN node. The following query is the realization of Rule 2 in Section 4.3. It generates the End of the # BPMN node.
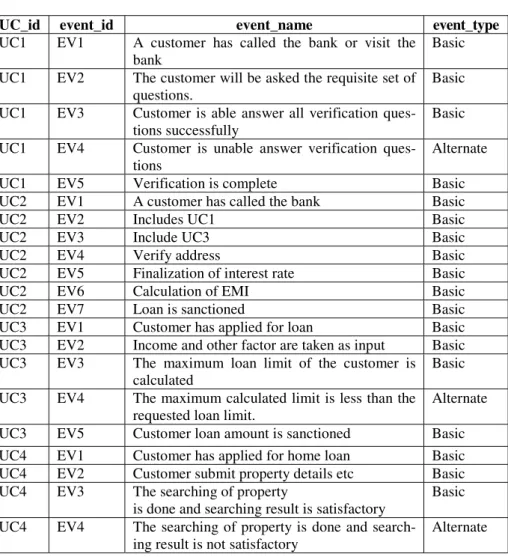
5 Case Study
UC3 EV2 Income and other factor are taken as inputs. UC3 EV5 customer alternative loan amount is sanctioned. The UC4 EV1 base customer has applied for a home loan. UC4 EV2 core client submits property details etc.
6 Conclusion
Proceedings of the International Conference on Software Engineering Research and Practice, Las Vegas, Nevada, USA, June. In: Proceedings of the International Conference on Software Engineering and Practice (SERP 2004), Las Vegas, Nevada, USA, June.
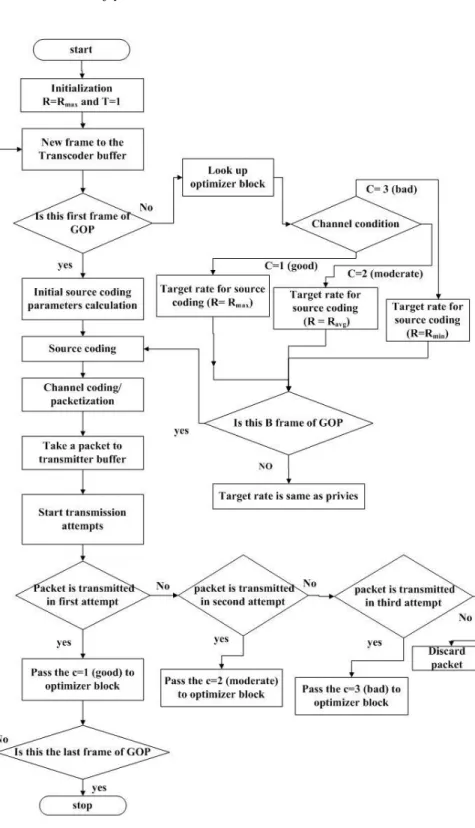
A Cross-Layer Framework for Adaptive Video Streaming over IEEE 802.11 Wireless Networks
In this work, we use the layered architecture together with cross-layer information exchange to increase the video quality of the end user. Based on application requirements, various solutions to vary the video rate are proposed in the literature.
2 The Proposed Cross Layer Framework
Optimizer Block
When the input counter value is one, it means that there is no delay in the network, thus indicating that the channel condition is good. When the input counter value is three or four, it indicates that the channel condition is bad.
Output
When the channel condition is moderate, transcoder target bitrate will be the same as it is, to take full advantage of the channel. Optimizer block estimates the channel state based on the number of transmission attempts for a packet.
3 Simulation Setup
Results
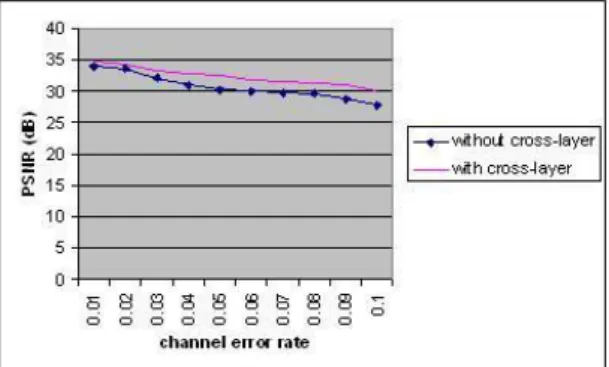
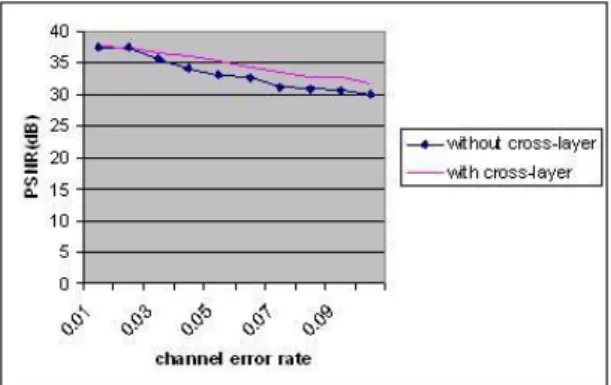
Fig.7(b') and Fig.7(b”) are screenshots of three test videos when they are reconstructed on a decoder with a channel error rate of 3 percent and in the absence of the proposed framework. When the proposed cross-layer framework was applied to video streaming, the results are shown in Figures 7(c), Figures 7(c’) and Figures 7(c”).
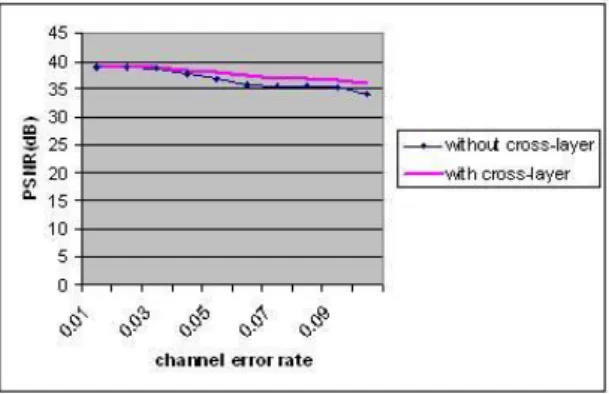
4 Conclusion and Future Work
FIFO optimization for network-based chip* power trade-off. The trade-off between power and performance is performed by varying the FIFO depth and position of the MoT-based network.
2 Methodology for Performance Evaluation and Cost Metrics
Performance Metrics
There is also some overhead in the source and destination that contributes to the total delay. Let P be the total number of packets that reach their destination IPs, the average total delay, Lavg, is then calculated as:.
Cost Metrics
The power consumption of the middle wire is derived for all 64 possible transitions in all three wires. The width and spacing between the connecting wires is taken from the interconnect dimension as shown in Fig.
3 Experimental Results and Analysis
Accepted Traffic vs. Offered Load
The overall average latency of any network depends on both the load served and the locality factor. 4 shows the overall average delay profile for the MoT varying the load offered and the locality factor.
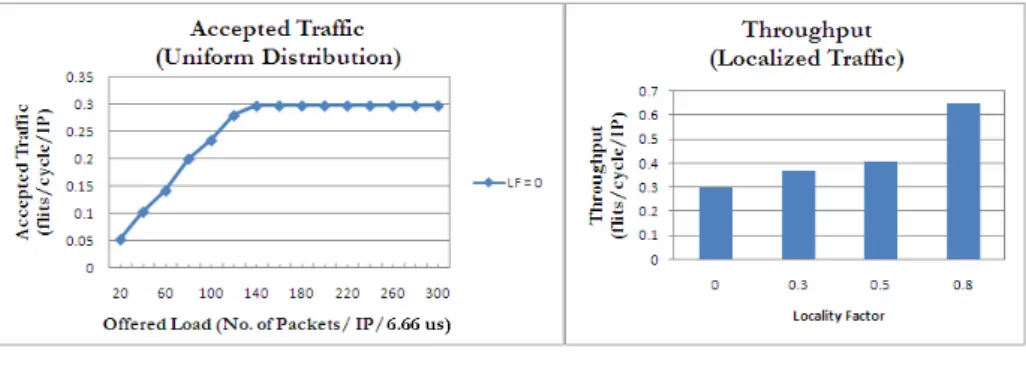
Energy Consumption at Different Locality Factors
This is due to the fact that at lower traffic, the contention in the network is less, but it will increase as the load increases, which in turn increases the delay. It has been observed that the traffic localization has a significant impact on the MT topology as the delay decreases with the increase of the locality factor.
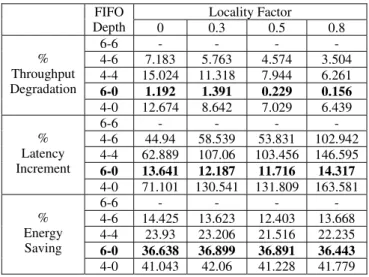
4 FIFO Optimization for Energy and Performance Trade-off
Jeang, Y.L., Huang, W.H., Fang, W.F.: A Binary Tree Architecture for Application Specific Network on Chip (ASNOC) Design. Kundu, S., Chattopadhyay, S.: Network-on-Chip Architecture Design Based on Mesh-of-Tree Deterministic Routing Topology.
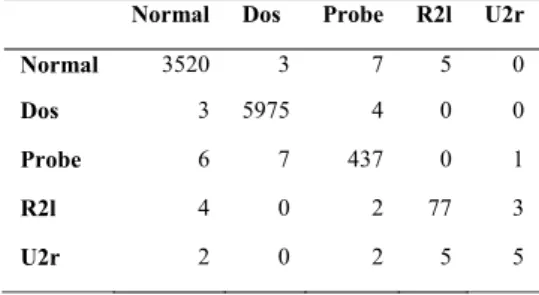
Outliers Detection as Network Intrusion Detection System Using Multi Layered Framework
If the IDS generates too many false positives, we will lose confidence in the IDS's ability to protect the network. In this case, there is an attack on the network and the IDS does not raise an alarm, even though it is designed to detect such an attack.
2 Dataset Description
3 Proposed Framework
For each selected feature calculate the z-score and set a threshold value to separate the objects into normal and outliers. Here we do this for each attribute
Outlier Detection as a Network Intrusion Detection System 103 We take majority vote to decide whether the object is outlier or normal. For a record or object that has four results showing it is an outlier and three results showing it is a normal object, it is considered an outlier or intruder because the majority votes.
Use the Bayesian network classifier to classify outliers into different classes
- Sampling
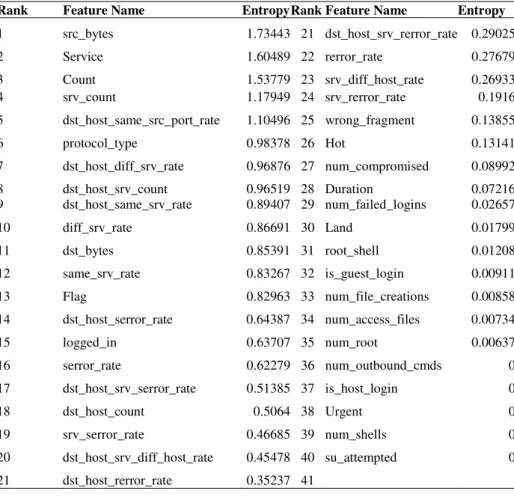
- Features Selection Using Entropy
For example, there are seven attributes and calculated z-scores and set the threshold values. In the z-score method, we first calculate the mean and standard deviation values for each attribute, Ai.
A zscore v
- Bayesian Network Classifier
- Learning Bayesian Networks
These networks [12] are directed acyclic graphs that allow efficient and effective representation of the joint probability distribution over a set of random variables. A Bayesian network [13] is an annotated directed acyclic graph that encodes a joint probability distribution over a set of random variables U.
K-Nearest Neighbor (k-NN) Method
Xdist
4 Experimental Results
TPR TP
Stolfo, S.J., Fan, W., Lee, W., Prodromidis, A., Chan, P.K.: Cost-based modeling for fraud and intrusion detection: Results from the jam project. In: Proceedings of the 3rd International Workshop on Distributed Statistical Computing (DSC 2003), Vienna, Austria, March.
A New Routing Protocol for Mobile Ad Hoc Networks
- Proactive MANET Protocol (PMP)
- Reactive MANET Protocol (RMP)
- Hybrid Routing Protocol
- Geographic Routing Protocol
- Gossip Routing Protocol
7], propose a gossip-based approach where each node forwards a message with a certain probability to reduce the cost of routing protocols. With a smaller number of executions, the maximum number of nodes gets the message, which depends on the gossip probability and network topology.
3 Gossip Routing in Adhoc Networks
Yuval Shavitt and Amir Shay [5] introduce the Gossip Network model where travelers can obtain information about the state of dynamic networks by gossiping with peer travelers using ad-hoc communication. The protocol cost is insignificant since the frequency of the communication is low compared to classical message delays.
Sleep Scheduling Mechanisms
A node (which wants to communicate) maintains a control variable called C that represents the active number of neighbors. Thus, new protocol sensibly consumes power based on local error conditions, maximizing the lifetime of the network and reducing the cost of the power consumed per successfully delivered data.
5 Simulation Results
- Simulation Model and Parameters
- Performance Metrics
- Results
- Based on number of neighbor nodes
- Based on Probability Value
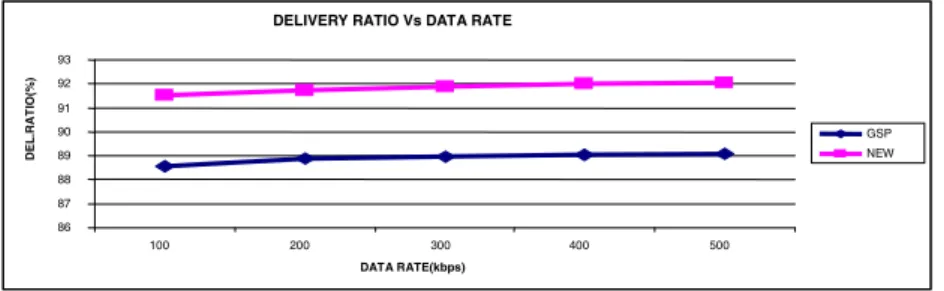
From the figure, the number of packet dropped is less in new protocol compared to existing protocol. A new routing protocol for mobile ad hoc networks 121 Figure gives the throughput of both the protocols when the number of Probability values is increased.
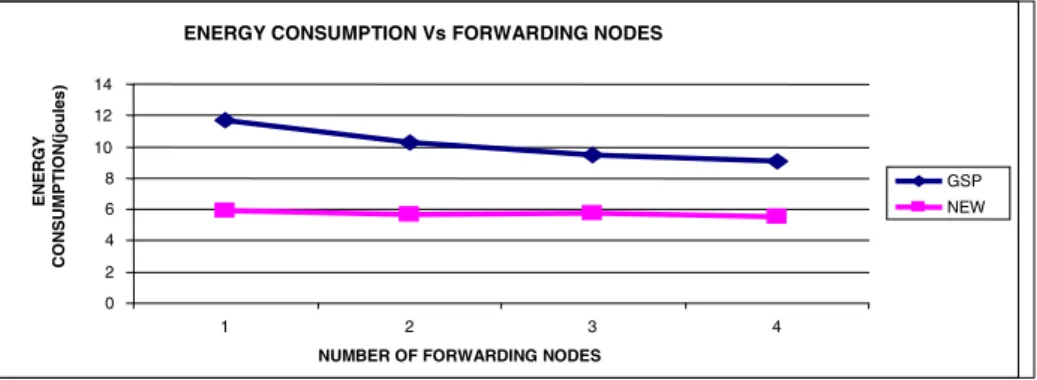
6 Based on Rate
A New Routing Protocol for Mobile Ad Hoc Networks 123 The figure shows the energy consumption results for different varying data rates. Hou, X., Tipper, D.: Gossip-based sleep protocol (GSP) for energy-efficient routing in wireless ad hoc networks.
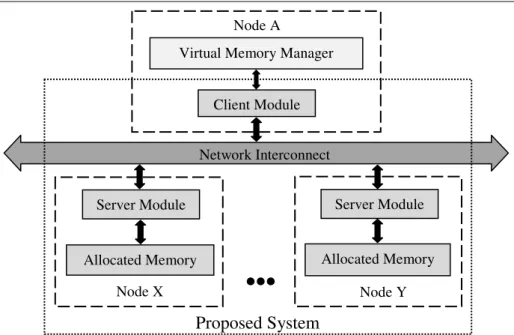
Remote-Memory Based Network Swap for Performance Improvement
The concept of using external memory started for workstation networking where high-bandwidth, low-latency networks became affordable. They further discussed their user-level implementation, which required modifying the memory allocator code to allocate memory remotely.
3 System Design
- Design Issues
- Client Module
- Server Module
- Communication Protocol
Therefore, the size of the device can only be a multiple of the size of the Swap Block. Swap Block Map maps the swap block number to the logical starting address of the Swap Block.
4 Experimentation and Results
Experimental Setup
Read: This control command is sent by the client to the server to send n bytes of data from a specified swap block, starting at a given offset. Write: This control command is sent by the client to the server to receive n bytes of data in the specified swap block, starting at the specified offset.
Job Description and Performance Results
5 Conclusions and Future Work
Acknowledgements
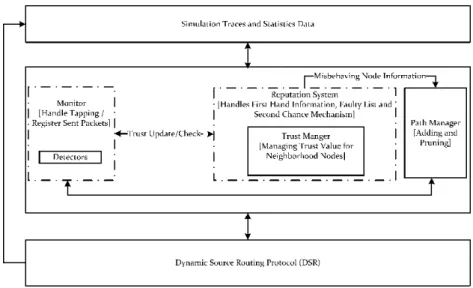
Arpaci, R.H., Dusseau, A.C., Vahdat, A.M., Liu, L.T., Anderson, T.E., Patterson, D.A.: The interaction of parallel and sequential workloads on a network of workstations. Cooperation alarm in a reputation system 143. a) Entity Mobility Scenario (b) Group Mobility Scenario Fig. a) Entity Mobility Scenario (b) Group Mobility Scenario Fig. confidence intervals on the graphs. The packet delivery fraction of CARS was increased by 24–51% and 11–27% compared to the DL scenario, 21–26% and 11–19% compared to the WP scheme under the entity and group mobility scenario, respectively, as shown in a,b of Fig.
Secure Service Discovery Protocols for Ad Hoc Networks
The paper is organized as follows: Section 2 lists the main service discovery protocols proposed so far in the literature. We will see that neither adapts well to ad-hoc networks. In ad-hoc networks, it is very important to minimize the total number of transmissions to reduce battery consumption.
3 SPDP: Secure Pervasive Discovery Protocol
Algorithm Description
- SPDP User Agent
- SPSP Service Agent
The SPDP has two mandatory messages: SPDP Service Request, which is used to send service announcements and SPDP Service Reply, which is used to answer an SPDP Service Request, which announces available services. It should process SPDP service request messages and generate the corresponding SPDP service response, if necessary.
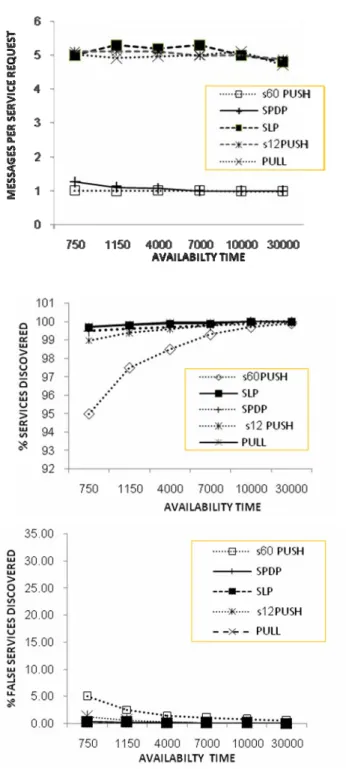
4 Evaluating the SPDP Protocol
10] Koodli, R., Perkins, C.E.: Service discovery in ondemand ad hoc networks (draft-koodli- manetservicediscovery- 00.txt), Internet-draft (work in progress) (October 2002). 31] Campo, C., Munõz, M., Perea, J.C., Mariń, A., García-Rubio, C.: GSDL and PDP: a new service discovery middleware to support spontaneous interactions in pervasive systems.
Certificate Path Verification in Peer-to-Peer Public Key Infrastructures by Constructing DFS Spanning Tree
PKI Components
A user does not issue a certificate, instead they rely on other PKI components to obtain certificates. Even for user certificate verification, it must depend on other PKI components.
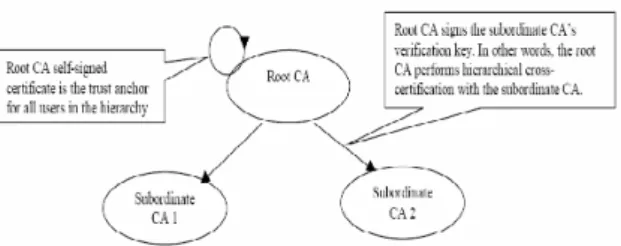
PKI Models
This model is used to reduce the number of cross-certification paths in the mesh model. The first is the hierarchical cross-certificate [5] which runs parallel to the paths of the subordinate hierarchies, but extends upward towards the root CAs.
Cross Certification
The difference between the hierarchical cross-certification and the peer-to-peer cross-certification is the location of the user's trust anchors relative to the user. All certificate validation for clients within an autonomous CA starts with the local CA's self-signed certificate.
3 Path Verification in Mesh PKI
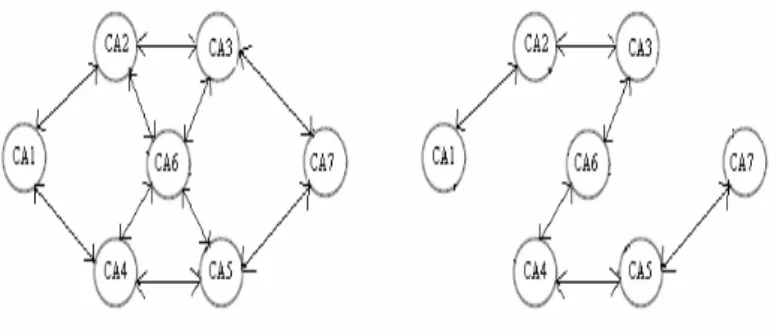
In the peer-to-peer model, path discovery is difficult because the trust relationship is bidirectional, where as in hierarchical it is unidirectional. 4 Proposed method to convert Peer-to-Peer PKI to DFS Spanning Tree to simplify certificate path validation.
4 Proposed Method of Converting Peer-to-Peer PKI to DFS Spanning Tree to Simplify Certificate Path Validation
In mesh or Peer-to-Peer PKI, certificate path verification is a complex task as multiple paths exist between CAs. In this paper, we proposed an efficient method to convert a mesh of Peer-to-Peer PKI to its equivalent DFS spanning tree to simplify the certificate path construction.
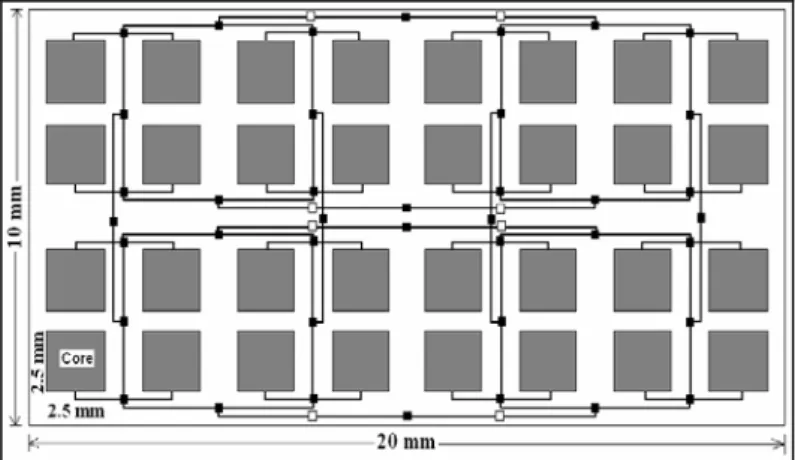
A Novel Deadlock-Free Shortest-Path Dimension Order Routing Algorithm for Mesh-of-Tree
A New Deadlock-Free Shortest-Path Dimension Order Routing Algorithm 169 (row) and then along the y dimension (column). The algorithm ensures a simple addressing scheme, simpler routing algorithm and reduced area overhead compared to [2, 3, 4].
2 Related Works and Our Contributions
3 Addressing Scheme
4 Routing Algorithm
Otherwise, if ROW CHECK is true, the packet is in the row it belongs to. If the value does not match the router's group ID, the packet is forwarded to the UP LINK.
5 Guaranteed Shortest Path