This study sought to see the policy relevance of cybersecurity strategies in the United States. Where the United States has been very intense over the last 10 years is creating a cyber security strategy.
Background of Study
Cyberspace has become a way to achieve a particular interest, also known as cyberpower.4 Connectivity has significantly improved the way people travel, communicate and do business.5 Convenience is just a click away. Connectivity moves the nation forward. 6 The United States is committed to an open, secure, interoperable, and reliable Internet that enables prosperity, public safety, and the free flow of commerce and ideas. 7 These characteristics of the Internet reflect the core American values of freedom of expression and privacy, creativity, opportunities and innovation.
Problem Identification
It is crucial that the cyber attacks known to date against the United States do not represent "high class" threats that the United States could carry out. Russia has used cyber-enabled information operations to influence the population of the United States and challenge democratic processes.
Statement of Problem
22 Other actors, such as North Korea and Iran, have also used malicious cyber activities to harm US citizens and threaten US interests. The United States' growing reliance on the cyberspace realm for nearly every essential civilian and military function makes this an urgent and unacceptable risk to the nation.
Research Objectives
Significance of Study
Literature Review
- Time Span
- Scope
- Study Limitation
United States Cybersecurity Strategy, Policy, and Organization: Weakly Positioned to Cope with a Post-9/11 Security Environment?. Focusing on how the United States faces the challenges of cyberattacks from other countries under the United States Department of Defense (DoD) and military agencies.
Theoretical Framewok
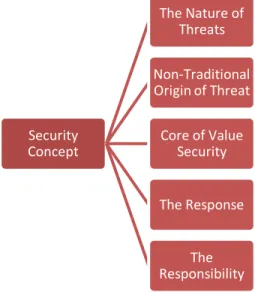
- Concept of Security Strategy
- Policy Planning Process
- Securitization Theory
- Neorealism
This research will focus on the strategy of the US government and military to face incoming threats from another states or even a terrorist attack through cyberspace and the implementation of the US cyber security strategy. Steven Spiegel and Winarno said that the expansion of the definition of national security is the result of increasing threats: nuclear, economic, social and cultural. Moreover, there is increasing recognition that analytical approaches are situational and require an understanding of the context within which the analysis is conducted.
42 Waltz, Kenneth N., Origins of War in Neorealist Theory, Journal of Interdisciplinary History, Vol. 35 to face internal and external problems.43 Also, all states are functionally similar, and thus, all states seek the same goal, namely, to maximize their security. However, STUXNET serves as a powerful example of the potential benefits of international cooperation in cyber security.
Research Methodology & Thesis Structure
Thesis Structure
The second chapter of this thesis will describe an explanation from a literature book about cyber security as a national security interest for the US national security. This chapter will further describe about the cyber space, criminal activities and cyber warfare in the cyber space, cyber security challenges the United States, including the threat models as the basic knowledge for a decision-making (US government) to consider a threat for implementation and an improvement of a US cybersecurity. It will also describe a brief history of US efforts to implement an Obama-era cybersecurity policy.
In this chapter also describe more about US Cyber Security strategies, developments and preparations in deterring Cyber Warfare. This chapter will wrap up all US cybersecurity in improving national security through US cybersecurity strategy and policy.
- Understanding Cyber Space
- Internet
- Web Surface and Deep Web
- Cyber Warfare
- Cyber Security Challenges
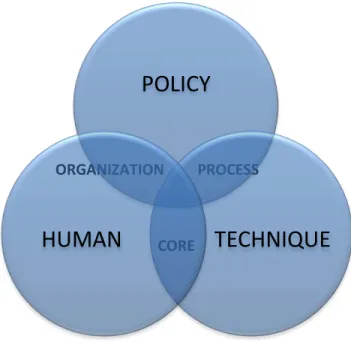
- Policy
- The Process
- Technique
- Skill
- Humans
- Organizations
- The Core of all challenges
- Understanding Cyber Threats through Threat Models
The United States (US) government has shown its seriousness in building its information security system. This is of course closely related to the US government's enormous reliance on information system security networks. 41 The United States has enough reasons to set cyber security as one of the country's top security priorities.
This may be one of the reasons for "hidden" sites on the deep web, because they are not for general use. The open, transnational, and decentralized nature of the Internet, which DoD and the country seek to protect, creates significant vulnerabilities.
The Nature of Global Cyber Security Competition
The leading role of national governments in the field of cyber security is largely reflected in the government's role in the formulation of national policy. Government cybersecurity policymaking provides a shared understanding and vision of the problem at the highest level, enabling coordinated national action to realize national cybersecurity goals. Developing a national cyber security strategy is an essential first step in addressing cyber security challenges.
Defines objectives related to cyber security (e.g. containment of cyber attacks, detection and prosecution of cyber crime, protection of data resources, etc.); It identifies measures to be taken to achieve these goals (e.g. establishment of incident response centers, adoption of cyber security standards, strengthening consumer awareness, etc.); and.
The Significant of Cyber Security Strategy
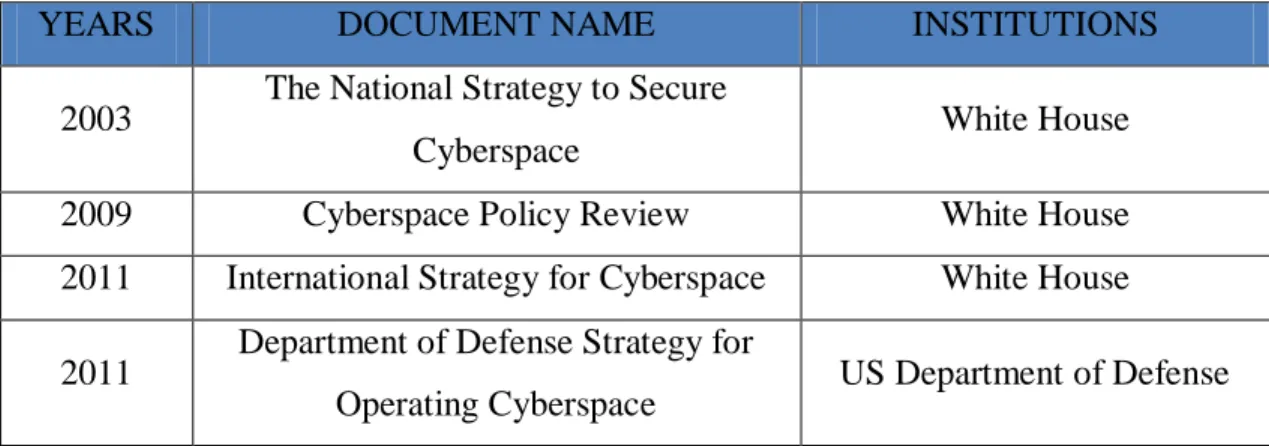
- Cyberspace Policy Review
- International Strategy for Cyberspace
- Presidential Proclamation - National Cybersecurity Awareness Month, 2014
The United States truly understands that the world still does not have a clear order regarding cyberspace. This strategy is also a guide for the United States in dealing with all the challenges of information technology security in cyberspace. 67 Department of Defense (DoD) Cyber Strategy" to answer which regions and how the US defense agency must succeed in the goals and priorities set out in the international strategy for cyberspace 2011.
Strategy Initiative 2: Develop a new defense operating system to protect US Department of Defense systems and networks. To support the cybersecurity mission, the US Department of Defense (DoD) conducts various activities outside the cyber world to develop cyber collective.
United States Executive Orders Agenda
- Executive Order 13587 - Structural Reforms to Improve the Security of
- Executive Order 13636 - Improving Critical Infrastructure Cyber Security
After issuing executive orders on structural reforms to improve network security and share responsibility for securing confidential information, President Obama described the cyber threat as one of the greatest threats to national security.96 US It is a must for Americans to keep the security and resilience of the country's vital infrastructure and cyber environment efficient, innovative and support the economy, along with promoting security, business confidence, privacy and civil liberties. This goal can be achieved by working with other countries, business owners and infrastructure managers to support cybersecurity and implement risk-based standards.
Share information about cyber security with the country cooperation, between institutions or with the private sector. The cyber security framework consists of a set of industry standards, methodologies, procedures and approaches to deal with the risk of cyber attacks.
The United States Cyber Security Strategy Implementation
With the mastery and use of good information and communication technology and supported by its cyber security strategy, the United States has succeeded in securing digital data and its vital infrastructure against the threat of cyber warfare. The United States' cybersecurity strategy requires cooperation between institutions or agencies, both government and private domestic or international cooperation. In implementing this cyber security strategy, each agency/agency has its respective roles and functions in the face of cyber warfare threats.
Thus, the success of the United States in securing digital data and its essential infrastructure rests on the performance of these agencies. In fact, the operations of the United States' intelligence agencies are a threat to other countries.
The Structure of Role Model Cyber Security Agencies in the United States
- Department of Defense as the Strategic Level Agency
- US Strategic Command (USSTRATCOM) as an Operational Level Agency
The quality of the attacks on Estonia and Iran is the same as those carried out in the US; in fact, the amount is not as high as an attack aimed at a superpower. Building strong relationships with the United States' alliance and international partners to strengthen shared cybersecurity;. The policies adopted at this strategic level are policies that are always being revised or updated in light of the evolving cyberwarfare threats the United States will face.
Second, prepare to be focused on conducting full military operations on the cyber spectrum to enable action across all Internet domains and ensure that the United States and its allies are free from cyberattacks and to prevent cyberattacks from enemies of the United States / allies counter . The NSA is tasked with collecting and analyzing communications from other countries and protecting information from the United States.100 The NSA coordinates, directs and conducts very special activities aimed at gathering intelligence from foreign countries, mainly using of cryptanalysis.
Cyber Security and United States-China Relations
The underlying concern is driven by the fact that the malicious side of cyberspace has grown hand-in-hand with the growing scale and use of the benevolent side. But perhaps even more important than the growing numbers behind the malicious use of the internet is the evolution of one's cyber threat landscape. 82 Internet by terrorist groups to cause physical harm (for example, by disrupting the operation of an air traffic control network) to the actual use of the Internet by terrorist groups to recruit members and share information about tactics and operational planning.108.
Hughes and Gudrun Wacker, China and the Internet: Politics of the Digital Leap Forward (London: Routledge. One of the key issues was that online Holocaust denial is a crime in many European states, but not in the US.
Cyber Security and United States-Russia Relations
In fact, Russia's 2000 "Doctrine of Information Security in the Russian Federation" does not even include the word Internet. In a 2008 document, "Information Society in Russian Federation Development Strategy", Russian government officials stated that they want to make Russia one of the top 20 information societies in the world by 2015. 119 The Foreign Policy Concept of the Russian Federation, approved by the President of the Russian Federation Vladimir Putin, 12 February 2013.
The interest of the United States in cyberspace is one of the reasons why Russian interests in this area are closely intertwined with bilateral Russian-American interests. According to Russian officials, the United States has long been conducting military R&D programs in cyberspace that are of serious concern to other international actors, including Russia.120 Since the early twenty-first century, Russia has repeatedly attempted to trigger a resolution in the UN