What is more important, however, is that stating that library assets need better protection is not the same as calling librarians criminals. Extortion and robbery are examples of the first possibility, whereas fraud falls under the latter category.
WHAT KIND OF PEOPLE COMMIT FRAUDS?
Once the act has been committed, the perpetrator must hide it – for example, by falsifying the accounts to hide the theft of petty cash. This helps them to commit the crime by understanding the weaknesses of the system and it helps to hide it.
WHY DO EMPLOYEES COMMIT FRAUD?
THE FRAUD TRIANGLE AND LIBRARIES
As we discussed earlier, a basic element of fraud is the concealment of the crime. Another important aspect of opportunity, at least from a managerial perspective, is that it is the easiest element of the fraud triangle to manage.
HOW ARE LIBRARIES UNIQUELY AT RISK FOR FRAUD?
A common theme among board members in all types of nonprofit fraud is, "We didn't realize we had to provide oversight." While this may be an attempt by some board members to shirk responsibility, it is usually the case that they receive little or no direction in their duties. This increases the likelihood that board members will not be aware of the need for independent financial control or, if they are aware, will not be able to provide it.
WHY SHOULD LIBRARIES RECOGNIZE THE RISK?
I'm sure it's no news to anyone reading this book that working in the library profession is not the path to personal wealth. Instead, in the following chapters, I hope we can work on two parallel sets of solutions: the technical aspects of detecting and preventing fraud in libraries and the change management needed to convince library directors and boards to embrace better fraud prevention.
WHAT IS INTERNAL CONTROL?
IC is probably the cheapest and most effective means of combating fraud and is often the most overlooked. The problem is that while early detection or prevention or both are usually the best way to deal with any problem, we tend to ignore them as solutions because we don't feel any urgency for future problems.
WHAT ARE THE ELEMENTS OF INTERNAL CONTROL?
Bond premiums behave much like other insurance policies - most of the cost is for the initial policy. Independent checking should be done regularly throughout the year and it is the duty of library management and staff to ensure that this happens.
WHAT ARE SOME COMMON AREAS OF WEAKNESS?
In other words, they do not cheat the firm because it is in their interest to keep it successful. Whatever the reason, it is not in the best interest of good internal control to allow a director to have too many related duties.
WHAT ELSE CAN WE DO TO CORRECT WEAKNESSES IN INTERNAL CONTROL?
Committee members must have the courage to insist on proper documentation, but they must also be willing to do the extra work to review what they have requested. Conversely, library staff members must insist that committee members take the extra time to review the checks they sign and be willing to do the extra work necessary to properly document expenses.
HOW GOOD LIBRARIES CAN GO BAD
Unfortunately, the same oversight of the director no longer applied, and the accountant was able to take advantage of this weakness to rob the library's treasury. Indeed, MPL already had many of them, but was unable to take advantage of them because it did not follow its own procedures.
MORE THAN INTERNAL CONTROLS
As a result, small libraries can become too unwieldy to manage and often fail just at the point where they seem ready to start. Many libraries fail simply because the director fails to give employees enough authority to run the organization.
GETTING DIRECTORS TO CHANGE
A good approach in many cases is to discuss the director's time as a commodity that brings benefits to the library. One way to deal with this is to place internal controls in the context of an investment in the library.
EPILOGUE: MPL SURVIVES AND BECOMES EVEN MORE SUCCESSFUL
Employee input not only gives management better information about internal control, it also helps to approve any changes by including employees in the process. In each of the following sections, we look at examples of specific types of fraud, examine how they happen, and discuss strategies for detecting and deterring them. However, unless otherwise noted in the preview, case names and details have been changed to protect the privacy of the source.
STEALING CASH
Although the outright theft of cash is a major component of cash embezzlement, it is not the only type or even the most harmful. In this case, cash theft is defined as the theft of cash after it has been entered into the library's financial records. This system is not the only way to separate cash handling, but it is not a bad way either.
Branch Library
In any case, a copy of the summary sheet is sent to the central library and kept there until the bank sends a copy. The first is that the person doing the reconciliation is not the same as the one who prepared the cash count or deposit statement. Most of us have eaten in restaurants or shopped in stores with a "your meal/purchase is free/discounted if you don't receive a receipt" policy. The purpose of such a policy is not to distribute free food or merchandise, but to ensure that the sale is registered.
STEALING MONEY THROUGH BILLINGS
Anyone wanting to do business under an assumed name simply registers the company as John Smith "Doing Business As" the XYZ Company. The possessive apostrophe in "The Red River Valleys source for office hardware" and the period after the W in L.D. This isn't as positive a sign as some of the others on the list, but it's a good secondary check if there are other symptoms.
STEALING MONEY FROM PAYROLL
We sure could use the help." The manager left with a promise to look into the matter. Similarly, the checks may be issued by the employee's immediate supervisor, in which case the supervisor who created the ghost employee or who worked with the payroll department simply removes the check .This is not the only technique for dealing with payroll fraud, but it is central to most of the methods we will discuss here.
STEALING MONEY
Managers should periodically review a sample of payroll transactions against timesheets to ensure that each timesheet is both approved and written for the approved number of hours.
THROUGH EXPENSE REIMBURSEMENT
- Improper Classification of Expenses
- Fabricated Expenses
- Overstated Expenses
- Duplicate Expenses
Expense reimbursement fraud differs from other types of fraud only in that the employee makes personal expenses on behalf of the library rather than the library making the expenses directly. It's no doubt the images of all the raucous ALA conventions they've heard about.). The real difficulty is that employees start looking for ways to "game" the system in order to recoup what they see (in many cases correctly) as legitimate expenses.
STEALING MONEY WITH CHECKS
To be fair, libraries are no more to blame for this than any other organization; the nature of check stock makes it easy to forget.). Once the fraudster has obtained a supply of checks, the next step is to create a check that looks legitimate. It is all too easy to create the wrong entry in the control registry or simply not make any entry at all.
STEALING INVENTORY
The most common method for staff to obtain inventory is to pick it up—that is, pick it up and check it out of the library. In some cases, the fraudster may simply "borrow" the assets and use them for some non-work-related purpose. If this is the case, the next best solution is to rotate the inventory control work among staff.
STEALING THROUGH ABUSES OF POSITION
More specifically, an illegal gratuity is defined as. the giving or receiving of 2. Unlike bribery, an illegal gratuity does not require criminal intent. If the library is not subject to a statute defining the limits of an illegal gratuity, it would do well to adopt its own standards. That's fascinating,” I can hear you say, “but remind me again why I need to know this?” The moral of this particular anecdote is that there is still nothing that offers better protection against trespass than the observation of an alert and interested person.
INVESTIGATING FRAUD—A RISK ANALYSIS MODEL
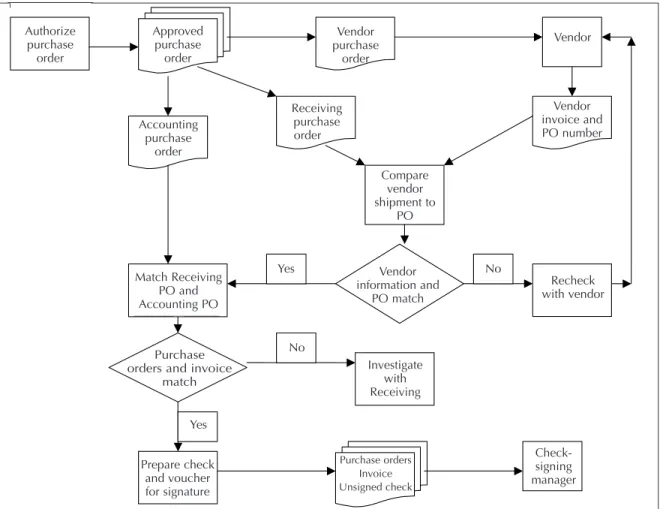
If the shipment is correct, the invoice and receipt copy of the PO are sent to the accounting office. The person who fills in the PO is not the same person who authorizes it. As with horizontal and vertical analyses, gaps only tell us that something is out of the ordinary, not the cause.
KNOW YOUR LIMITS AS A FRAUD EXAMINER
In this case, the checks are pre-numbered and we compare our records with the bank's. If you find something out of the ordinary and it's anything but the most basic fraud, I strongly advise you to get a professional to investigate. Some frauds are easy to spot because no one in the library was paying attention.
RED FLAGS—WHAT ARE COMMON WARNING SIGNS OF FRAUD?
What is less understandable (or at least less forgivable) is that the individual receiving the complaint never follows up with both the creditor and library staff to see how it is resolved. The tacit assumptions underlying this red flag are that the library has a budget, that someone reviews it on a regular basis to compare actual spending with projected spending, and that the individual conducting the review is not fraudulent. Changes in programs or cost increases beyond the library's control (eg, for fuel or insurance) may cause legitimate discrepancies.
RESPONSE — WHAT STEPS SHOULD YOU TAKE IF YOU SUSPECT A CRIME HAS BEEN COMMITTED?
This includes not only the employee's personal computer, but also any shared drives on the library's network. Let's assume you've done all the work and have solid evidence that a library employee committed fraud. As a result, the library will probably be required to carry out a significant amount of the research work itself.
DAMAGE CONTROL — HOW DO YOU TELL THE PUBLIC?
Legal action is messy and uncertain and is bound to bring fraud to public attention. The point here is that you can't keep a lid on bad information; the only real question is whether you will retain any control of the situation. For more information, go to the website of the American Library Association, which has an excellent discussion of the topic (ALA 2005).
THE LAZARUS LIBRARY — A CASE STUDY OF RETURNING FROM THE DEAD
Remember that when dealing with fraud and communicating with the public, the longer you wait, the more difficult the problem becomes. Have a single individual or select group speak for the library and refer all questions to them. This is an opportunity to demonstrate not only your understanding of the situation, but also your ability to deal with it decisively.
IF THE WORST HAPPENS
The embezzlement was subsequently discovered, not by the library, but by a state payroll clerk. Conversely, it is often inconvenient for library staff to have financial documents assessed by board members. Third, the library embarked on an aggressive training program for both staff and board members.
UNDERSTANDING THE COST OF PROTECTION
UNDERSTANDING RISK IN THE NONPROFIT WORLD
RISK MANAGEMENT
This becomes particularly important if the library is considering covering its fraud damage through insurance. This can be done by investing in preventive measures, by paying insurance premiums or by tacitly agreeing to go bankrupt if the losses are too great. It is important that the library knows how it intends to deal with a loss, even if no anti-fraud measures are taken.
THE GOOD NEWS — BASIC FRAUD PREVENTION IS CHEAP