A popular traditional detector is the chi-square detector, which detects on the basis of residual deviation statistics, i.e. Since the statistics of the above mentioned attacks do not change, they are not detected by the chi-square detector. Therefore, in this work, we will show why the cosine detector does not detect them and design a method to improve the detection rate of the cosine detector.
24 5.2.1 Performance of Chi-square and cosine detector without encoding and decoding 24 5.2.2 Explanation of ROC curves. This concern can be attributed to the potential of the physical cyber systems to transform the current energy industry in terms of performance and economics. The Stuxnet attacks and the US blackout have highlighted the vulnerable nature of SCADA systems (a type of CPS) which have had a huge impact on the economy. The term cyber-physical systems (CPS) refers to a new generation of systems with integrated computer and physical systems. capabilities that can communicate with people through many new modalities [2].
The paper by Miao [6] addressed the improvement of detection of Chi Square Detector using the coding techniques. In this regard, the Cosine similarity detector was proposed by [1] for the smart grid communication system and he showed the improvement in attack detection by using the cosine similarity detector over the chi-square. Since control systems will have Kalman filter in to estimate the states of the system, we use cosine similarity detector which can use predicted observations from Kalman filter and detect the attacks.
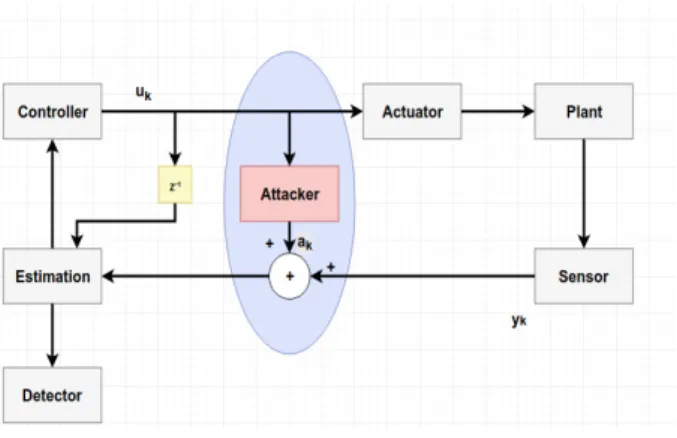
The dynamics of the plant is modeled by a linear time-invariant (LTI) system equipped with a Kalman filter and a Chi Square detector.
Kalman Filter
We have the plant equipped with Kalman filter for state estimation, Linear Quadratic Gaussian (LQG) controller for future input generation and a detector to detect attacks. We assume that the physical plant follows linear time invariant system dynamics that can be described by the following state space model.
LQG Controller
Attack Detector
False Data Injection Attacks
Contruction of Attack Vector
If v is the unstable eigenvector of A and it must be attainable condition of the equation (2.52). So we essentially find the input to the above system that the error dynamics after v i.e. unstable vector in n steps. Thus, the attack vector for the next time step is a linear combination of the attack vectors generated using equation (2.55).
To simplify the generation process, since we have generated the attack input to send the ∆ek to v in steps, we let the state of ∆ek+n at time k+nbev. So for any time greater than n the attack vector will have the form ak+n+p=−CA∆ek+n+p−1. Now if we use the above definition of attack vector for any instant greater thanks+n, we will see the design of attack vector for any instant greater thanks+ninstant.
The above was based on the assumption that ∆ek = 0 at the beginning and we moved from the starting point to v. Summarizing the construction of attack vectors, the algorithm for generating attack vectors is given by. Inputs: A,B,C,K,v-unstable eigenvector,n-order of matrixA,k-number of time steps Outputs: Attack vectorsa0, a1, a2..ak.
This way we can generate all attack vectors for an arbitrary number of time points. So here we conclude about generating the attack vectors for the false data injection attacks that can bypass the traditional chi-square detector.
Cosine Similarity Detector
False Data Injection Attacks on Actuators
No Attack Case
So thegk becomes the sum of squares of gaussian random variables, which is chi squared, so it will be lower than the threshold, so it won't cause an attack.
Attack Case
Thus, the above quantity is again Gaussian, so spurious data injection attacks are not detected by the chi square detector. Now with similar principles we will verify the performance of the cosine detector in detecting fake data injection attacks.
Cosine Similarity Detector
No Attack
Under Attack
In the previous chapter we saw that the cosine similarity detector cannot detect the injection of spurious data. Therefore, here we explore the way to improve the detection rate and formulate a simple method to increase the detection rate. From Chapter 2 we saw that the error dynamics in the case of the attack is given by. So if we make this difference in residual larger, we can detect the attack vector.
So with this method we will make the residual non-zero so that the detector detects the attack. In the previous example D=I so the residue was not detected and if D6=I we can detect the attack.
Inability of WaterMarking in case of FDI attacks
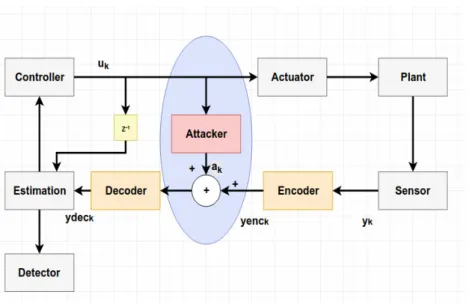
Encoding and Decoding Method
This decoded term would be used in the Kalman filter estimation so that the difference of the residual would not become zero, i.e.
Choice of Encoding and Decoder Matrix
If the rank of the matrixX is n, then A has all eigenvalues greater than 1, in which case the residue grows in the direction of all eigenvectors. From the above expression we can see that if the termλidi is maximized, the residue grows and we can detect the attacks.
Design of Decoder matrix
Herein, we will show with a numerical example in improving the performance of both the cosine and chi-square detector. A control input will be sent to the actuator to control the speed of the vehicle. Using the same principles as described in the [8] we will first generate the attack vectors and cross-check with the [8] for state deviation.
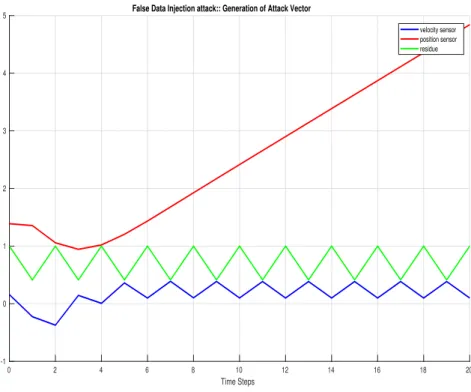
Using the algorithm explained in Chapter 2, we will generate attack vectors and the attack vectors are validated by the following result. Therefore, with the above graph we can say that the attack vector we generated increases the states of the position. Using the method explained in the previous chapter, we find that the unstable eigenvalue of matrix Ais 1 and the unstable eigenvector is [01]0.
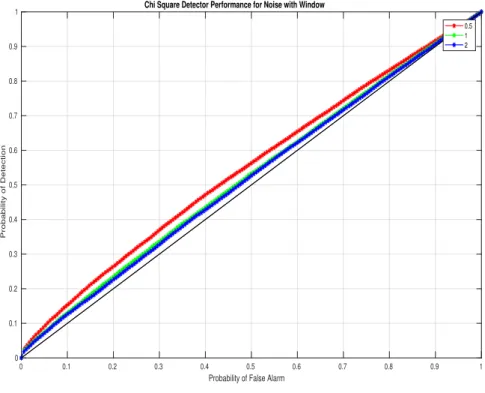
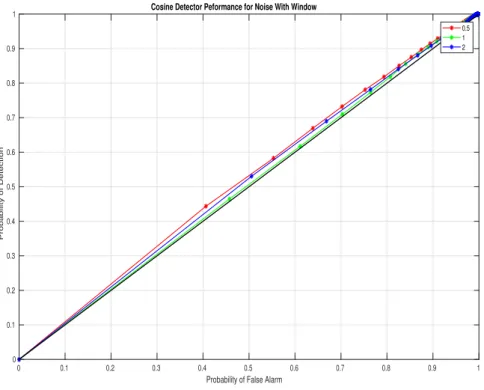
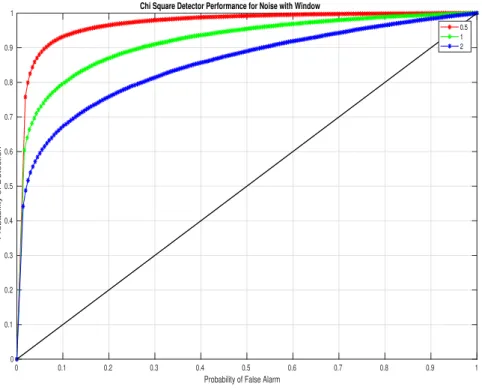
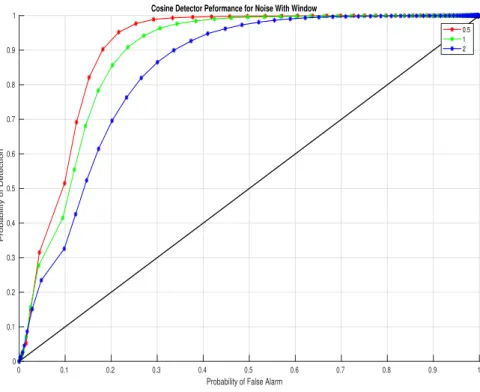
Since we have diagonal matrix, the encoder matrix M will be the inverse of the decoder matrix D obtained above. In this section, we see the simulation results of the chi-square and cosine detector without encoding and decoding. We performed the simulation on Matlab R2017b and by changing the variance of the measurement noise. In Figure 5.3, the ROC points lie on the extreme diagonal regions because the Cosine detector a.
In the case of Chi Square Detector, under attack scenario, the equations for the dynamics of the state estimation error and the residuals are given by . From Chapter 2 we have seen that under no attack the mean is zero and under attack the mean of the residual is still zero. Now coming to the Cosine similarity detector by similar analysis as in the above section, the average of the cosine similarity measure is given by .
The ROC curves shown in the previous subsection implied that the Chi-square and cosine detectors were unable to recognize the attacks due to the nature in which the fake data injection attacks are designed. Here we will show the results of both detectors in the presence of encoding and decoding. So, we have improved the performance capability of Chi square and cosine similarity detector using encoding and decoding methods.
The work presented in the previous chapters clearly explains the design of false data injection attack vectors and gives a detailed explanation of the behavior of the chi square and cosine similarity detector in the presence of attacks. We then demonstrated a simple encoding and decoding method to improve the performance of both detectors.