For further information, contact the Special Sales Department, AMACOM, a division of American Management Association, 1601 Broadway, New York, NY 10019. This publication is intended to provide accurate and authoritative information relating to the subject matter covered.
Preface
Defending the brand must be a coordinated effort across departments supported by an executive-level champion who can easily recognize the overall implications. The primary goal of the early chapters of Defending the Brand is to help you familiarize yourself with the types of threats and opportunities that may exist online.
Acknowledgments
I would like to thank Patrick and Stephanie Fox, Mark Fischer, Todd Bransford, Sue Deagle, Meghan McNamara, Dipankar and Rini Sen and James Cowart for taking time out of their extremely busy schedules to conduct peer reviews. Finally, I want to acknowledge you, the reader, for your interest in learning more about the unique challenges of defending a brand in the new millennium.
Introduction
According to Microsoft's corporate lawyer, Tim Cranton, test purchases made by Microsoft show that more than 90 percent of Microsoft software sold online is counterfeit or infringes the company's intellectual property rights. The anonymity and widespread access to the Internet make online fraud a serious problem worldwide, causing both consumer and economic harm,'' said Cranton.3.
Digital Brand Abuse
The Dark Side
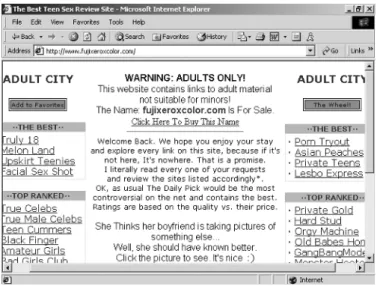
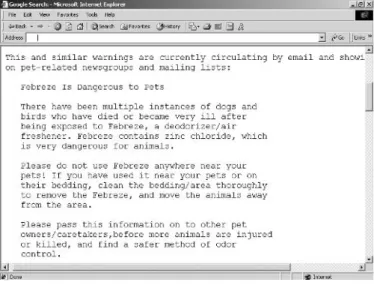
Unfortunately, Hormel's belated attempts to protect the brand from being associated with spam -- the term is used in slang -- have been futile. Since many of the company's brands are aimed at children, linking to controversial content has the highest priority.
The Opportunities and Threats of Online Commentary
Enron executives executed an elaborate scam scheme that fooled even the most sophisticated analysts,” the report said. Sometimes the comments on these sites can be vulgar, one-sided and not representative of the overall image of the brand.
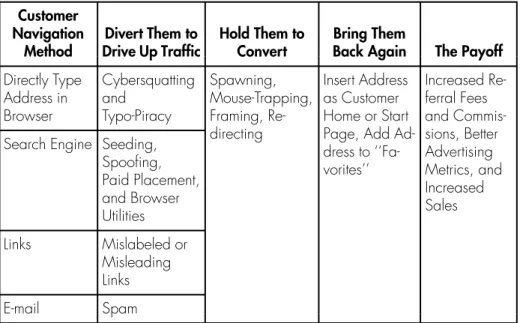
Customer Diversion
An example of hacking occurred when a porn company called ''The Net'' launched a website at www.foradodge.com, attracting significant Internet traffic from surfers whose intended destination was the strong promotion. To date, all but two of the identified sites have transferred their domain ownership to the hotel group. It's the digital equivalent of hanging popular logos and slogans outside your store to entice shoppers to come inside.
Invisible Seeding. The most common search engine optimization tactic is the hidden ''seeding'' of content to get the highest possible ranking in search engine returns. The ads are displayed to users by opening a new window at the top of the displayed page. Mousetrap is another offshoot of the online porn industry that is becoming more mainstream.
Finally, some sites try to keep shoppers on a site by "framing" the browser window while they view content from other domains (Figure 3-13). According to the complaint, in a practice called "page-scraping," the defendants made exact copies of Web pages posted by a wide range of unrelated parties, including the embedded code used by search engines to index the subject matter. of the site.
Online Partners and Distribution Issues
Managing Partner Compliance
Unfortunately, while organizations invest millions of dollars in developing and executing customer-centric strategies, few are aware of the need to manage the customer's total experience – including their interaction with online partners. While some of the breaches may seem relatively minor on the surface, they can have a significant impact - especially when aggregated across large partner networks. The convenience of online shopping is now an integral aspect of the Mary Kay brand customer experience.
In the aftermath of the terrorist attacks of September 11, 2001, a wave of fraudulent emails, online messages and websites appeared using the Red Cross brand to capitalize on the public's desire to help victims. All other merchants claiming to collect on behalf of the Red Cross did not meet official guidelines, and there is no real way to determine whether the money ultimately made its way back to the Red Cross. One of the first steps is to carefully draft and communicate partner policies and guidelines.
Well-managed affiliate networks can serve as brand ambassadors and can be an effective way to extend a brand's reach. Some dealers actually take advantage of automaker brands to drive traffic to a website and then sell advertising to competitors.
Counterfeits and Gray Markets
Compaq has also established a Gray Market Code of Conduct for all its employees and educates employees worldwide about the risks associated with gray marketing. The World Health Organization estimates that 10 percent of the world's medicines are counterfeit, which causes the pharmaceutical industry to lose tens of billions of dollars in revenue annually. 14. Government agencies and global organizations such as the International Chamber of Commerce (ICC) have recognized the extent and urgency of the dangers associated with the online distribution of counterfeit pharmaceuticals.
Depending on the nature of the product, there can be thousands of potential outlets. Given the scope and complex nature of the problem, the challenge then becomes to identify the distributors and prioritize efforts to reach them. The website is based outside the country whose customers are targeted by the website.
If companies do not take reasonable precautions against counterfeiting, they can also expose themselves to liability or even run afoul of the law. Most of the sites are operated from developing countries and the products are shipped overseas.
Defending Against Digital Piracy
Whether the site owns its own domain (as opposed to using personal pages where the main domain is part of a larger community like AOL or Yahoo!) is another indicator of the website's commercial potential. They managed to shut down more than 300 internet sites offering pirated copies of the film. Tackling digital copyright infringements, such as video piracy, varies widely depending on the scale of the problem the organization is trying to manage.
Movielink.com notes that downloads can take 40 minutes or longer, depending on the size of the movie file and the user's connection speed. Copy protection technologies and digital rights management plans are one of the approaches used by the film industry to help manage the problem of piracy. When we make a test purchase, we find that 90 percent of the products we get on the Internet are fake.''23.
Publishers who take the threat seriously monitor the issue to assess the severity of the problem. While the Internet as a distribution channel creates many opportunities and efficiencies for legitimate business, illegitimate operations also take advantage of the same capabilities of the Internet.
Trust
The Costs of Compromised Privacy and Security
Web developers take advantage of the ability to collect this information to customize and streamline the user experience. The lawsuit called the practice "a gross abuse of the trust placed in Toys 'R' Us by parents and their children" and sought damages for customers who shopped on the site. Only a very small percentage of Internet traffic involves someone's credit card information.
Part of the challenge is that e-commerce by its very nature presents a challenge for security professionals. Despite these facts, many businesses are still unaware of the risks associated with their online presence. By the same token, a breach of customer privacy can be devastating to a company's bottom line in terms of recovery and downtime costs, reduced market value and lost brand equity.
A major competitor seizes the opportunity to launch an aggressive marketing campaign to recruit these customers. Privacy and security are a high priority for shoppers and key elements of the online customer experience.
Competitive Intelligence
Using Online Competitive Intelligence to Outmaneuver Competitor Brands
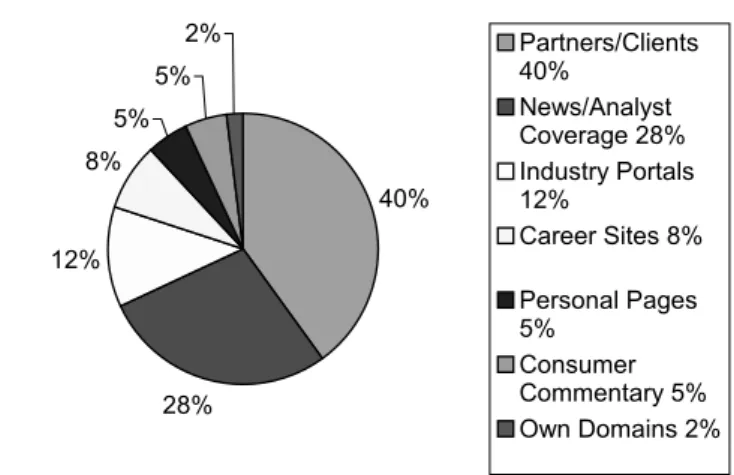
The easiest way to get a contextual sense of brand presence is to categorize events based on the nature of the site where the brand is present. Beyond relative breadth and context, the challenge of analyzing a leading brand's Internet presence can be met by focusing on the specific aspects of the presence most likely to yield competitive intelligence. AdRelevance lures customers with the promise of “discovering every detail of your competitor's advertising strategy.” The main difference between advertising and brand outreach is that, depending on the care with which your competitors' ads are placed, they can sometimes provide you with information insight into where the competition wants to be, as opposed to where they actually are.
Alexa Internet, which bills itself as "The Web Information Company," tracks the online habits of more than 10 million people worldwide as they browse the web. The first step in deciphering your competitors' strategies is to collect a dataset that will be used to generate information. Since the quality of the output will depend on the input, it is important to cast a wide net when gathering intelligence.
The value of incremental branding must be carefully weighed against the potential value of the intelligence your brand presence can give to the competition. Some of the specific mechanisms that can be used to determine a competitor's strategy include analyzing its brand reach (i.e., who views the competitor's brands online), partners, and online comments.
Taking Action
How to Use Online Monitoring to Control Your Brand and Capture
Web and FTP sites, on the other hand, have thousands of online search engines competing to help visitors find what they're looking for. Many of the same search engines offer image searches, which can be used to supplement your efforts by identifying the presence of logos. There are also metasearch engines, such as Dogpile.com, that allow you to query multiple search engines through a single portal.
Advanced search options are provided by most search engines and can be selected to exclude results with specific words such as starshiporERP (a common acronym for Enterprise Resource Planning). Popular search engines. Just as the most advanced search engines do a pretty good job of filtering out abuse, they can also help identify instances of abuse when properly prompted. Depending on your target market, it may be a good idea to include third-party search engines and engines that offer paid placement in your listings.
Domain name searches. The most abused marks appear not only in the content of the website, but sometimes in the domain name as well. There are a number of free domain name search engines online where you can enter your brand and see who is cybersquatting your brand names (see Figure.