I understand that I may apply to the University to maintain the right to withhold or restrict access to my thesis for a period normally not exceeding four calendar years from the congregation in which the degree is awarded, the length of the period to be specified in the application, in total with the exact reasons for making this application. The author, whose copyright is indicated on the title page of the work, has granted the British University in Dubai the right to lend his research work to users of its library and to make partial or single copies for educational and research use. The author has also granted permission to the University to retain or make a digital copy for similar use and for the purposes of digital preservation of the work.
Any use of this work, in whole or in part, respects the author's moral rights to recognition and reflection in good faith and without prejudice to the meaning of the content and original authorship. This article uses a qualitative approach to provide a case study analysis of the growing use of technology by insurgents. Through a review of the literature and a comparative analysis of the trends of recent years, the researcher came to the conclusion of the growing need for
Introduction
2 Finally, the paper concludes with an overview of what is currently being done to combat cyberterrorism and makes recommendations for what else could be done in the coming years. In realism, states are regarded as the main actors in international relations (Goldstein and Pevehouse 2012) and the need for a heavily fortified state through heavy spending on the military is seen as paramount. They see states as inherently cooperative and believe in the importance of international organizations in global governance.
Constructivism believes in the flexibility of the international system and the subsequent changing national interests of countries. After careful investigation and extensive digital national security research, I can confirm that the confidentiality of such classified documents is of utmost importance to protect and reduce vulnerability. However, as previously mentioned, there was a relatively large lack of research into cyberattacks carried out by insurgents.
Disruption of traditional methods of security
A second major force that disrupted traditional methods of war and security was the information technology revolution (Goldstein and Pevehouse 2012). This revolution has impacted both state and non-state actors in fundamental ways and has forever changed the perception of security. The first is the growing emergence of non-state actors in international politics and the second is the increasing use of information technology by both state and non-state actors to increase their resources.
Global telecommunications are profoundly changing the way information and culture work in international relations” (Goldstein and Pevehouse 2012). Information technology in international relations is a double-edged sword; it not only enables countries to more effectively manage their populations, but also provides non-state actors with powerful tools to direct opposition movements (Goldstein and Pevehouse 2012). Non-state actors such as radical movements are finding it easier than ever to operate because of information technology.
A relatively new term in the terminology of international relations, the definition of cyber terrorism and the legal eventualities it entails is not universally accepted. Second, proficiency in information technology and especially cybercrime enables radical organizations to acquire large amounts of capital through hacking, thus giving them the ability to finance themselves (Veerasamy and Grobler 2011). The condensation of time and space due to the information technology revolution has proved to be the greatest catalyst for the spread of radical activities.
As we can see, the realist ideology is no longer effective in combating the unique security challenges of the 21st century. First, realism states that the major security dilemmas of the international system have to do with states alone. As we have seen, non-state actors such as radical groups challenge current security frameworks to refute this claim.
Second, the traditional focus of realists on large investments in military fortification is also undermined by the pervasive nature of information technology and the security challenges it presents.
Case Study Analysis: Insurgents
Thus, the world was caught off guard by the rebels' ruthless and subsequently effective use of information technology and the media. This document served as a handbook for rebel recruits and its subtitle was "You Are Also a Mujahid". The insurgents' use of social media networks and this operator, who apparently gave a sense of ownership to new recruits, aided in this ability to attract people from far and wide.
All those who participate in the production and distribution of propaganda should be considered one of the insurgents of the 'media mujahideen'. As mentioned in the previous subsection, the insurgent's successful manipulation of social media networks led to its ability to recruit members from around the world and spread its propaganda. Just looking at this process of digital recruitment of insurgent members and/or sympathizers shows how important information technology plays in today's global security crises.
So far, in this case study of insurgents, we have examined the use of information technology by insurgents, studied how they manipulate social networks, and how they recruit members. He aimed to spread propaganda that would ensnare potential members and was responsible for content to keep the community of insurgent supporters around the world still interested. The International Center for the Study of Radicalization (ICSR) has written a detailed study of the differences in the messages of the insurgents in both its physical territories and in the digital realm.
For example, Twitter initially did not respond to insurgents' heavy use of its social network (Berger 2015; Winter 2015). This shows insurgents' ability to have a consistent online presence and is also indicative of the nature of social networks that allow users to create and delete accounts. Admittedly, these were rarer than insurgents' heavy use of social media, but counterterrorism experts must devote resources to studying and understanding the nature of these few cyberattacks in order to be better prepared.
In this hacking incident, the photos and addresses of 70 drone pilots were released "in exoneration of other members of the insurgency killed in the drone strikes." This seems like an odd target, however, upon further examination, experts discovered that the insurgents' hacking division was arbitrarily targeting official websites that were on. However, as the strength and power of the insurgents had largely waned by this point, this was merely an insurgent support group and not the main center of insurgent operations itself.
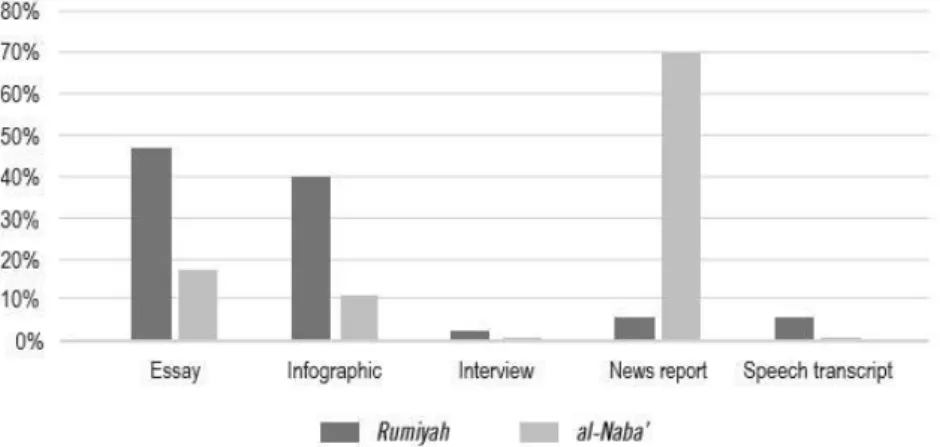
Recommendations
The first is to combat the radicals' use of social media to recruit members and spread propaganda. The first method is a touchy subject as these social networks were created to feed a desire for freedom of expression and privacy and the ability to trigger social change. Having governments work heavily with these social networks to control radicals' use of these networks is highly controversial.
The controversy is not only in the violation of the privacy of the users of these social networks, but also in crossing the line of government interference in a somewhat capitalistic 'private' enterprise. The world of social networks is in its infancy and teething problems are bound to happen as governments and the management of these social networks learn how to work with each other. The dichotomy here is that the counterterrorism experts are concerned with 'open source intelligence on insurgents', compared to the social networks whose priorities (mainly driven by financial goals) are to protect the data of its users (Berger 2015).
Some kind of algorithm can be used to notify the management of these social networks if there are any. Milton (2016) further confirms this point by pointing out that 'the need for both resources and flexibility suggests the importance of a public-private partnership in attacking the insurgents' propaganda activities'. However, given the nature of the internet, “the use of repressive measures, such as criminalization of online activity, is not necessarily the most appropriate solution…because it is ineffective, as other methods will soon replace [the] blocked options ( Van Ginkel). Give an example of a hack in Bangladesh).
As can be seen, there are several important measures that counterterrorism experts can take to not only defend against cyber-radicals, but also carry out attacks themselves and limit the capabilities of these cyber-radicals. It requires governments to not only join forces with social media networks, but also to develop sophisticated digital strategies to thwart and attack cyber-radicals. Social media networks have indirectly disrupted counter-terrorism efforts, as radical groups such as insurgents have used these very networks to increase their reach.
It is a gray and controversial area, but governments need to work with the management of social media to prevent and limit the ability of radicals to use these channels for propaganda and recruitment. Tailored Online Interventions: The Islamic State's Recruitment Strategy," CTC Sentinel, Vol. https://www.ctc.usma.edu/posts/tailored-onlineinterventions-the-islamic-states- recruitment-strategy. Available from: https://icsr .info a-tale-of- two-caliphates-comparing-the-islamic-states-internal-and-external-messaging- priorities/.Tweeting of Jihad: Social Media Networks of Western Foreign Fighters in Syria and Iraq'.