Tevfik Bultan University of California, Santa Barbara, USA Pavol Cerny Vienna University of Technology, Austria. Krishna S India Institute of Technology, Bombay, India Sriram Sankaranarayanan University of Colorado in Boulder, USA Natarajan Shankar SRI International, USA
Model Checking
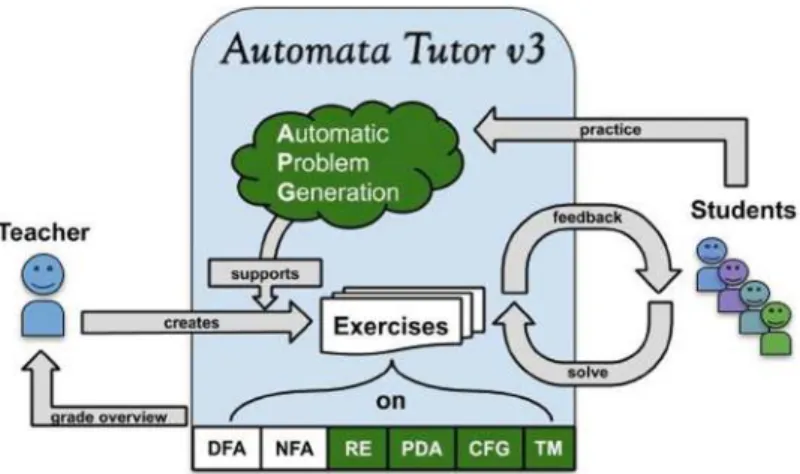
In this paper, we present the third version of Automata Tutor, a tool to assist teachers and students in large courses on automata and formal languages. The second version of Automata Tutor supported automatic grading and feedback for final automata constructions and has already been used by thousands of users in dozens of countries.
1 Introduction
This article describes the new components introduced by Automata Tutor v3 and how this new version is an improvement over the previous one. Auser study conducted on a class of 950 students to assess the effectiveness and usability of Automata Tutor v3.
2 Automata Tutor in a Nutshell
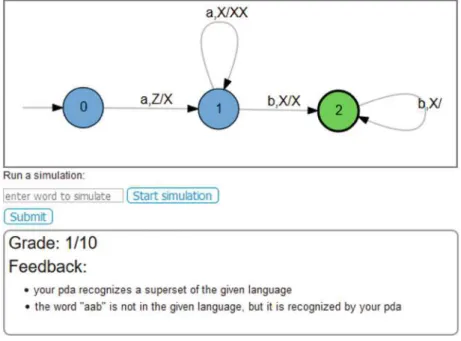
In our survey, students report that they learned quickly, felt confident and enjoyed using Automata Tutor v3, and found it easy to use. As shown in a large user study conducted on the first version of Automata Tutor [6], this rapid feedback cycle is encouraging for students and leads to students spontaneously investigating more practice problems and engaging with the course material.
3 Design
University and Course Management
Students cannot see problems immediately, but only after teachers have decided to pose them. When using their university's login service, tutors receive a certified user-to-student map and enable tutors to use Automata Tutor v3 for grading homework or exams.
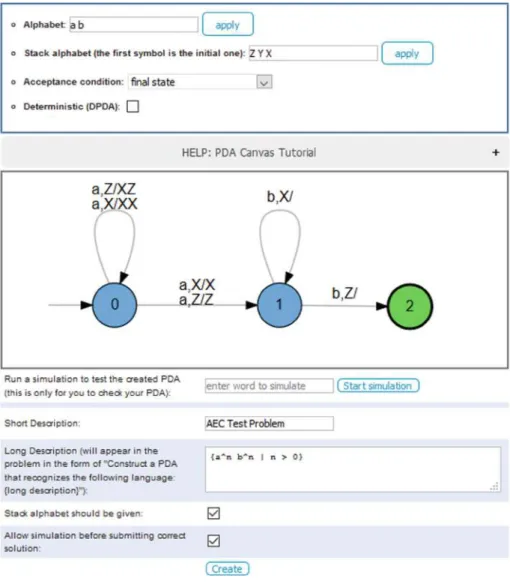
New Problem Types
This involves setting the maximum number of points, the number of attempts allowed and the start and end date. You can either register via e-mail or, if the university supports it, log in with an external login service such as LDAP or Oauth.
Automatic Problem Generation
4 Implementation and Scalability
This local rollout served as an important testing ground before the tool's large-scale public rollout online. Due to its modular structure, the tool is easily upgradeable with multiple front and rear parts along with the load distributor.
5 Evaluation and User Study
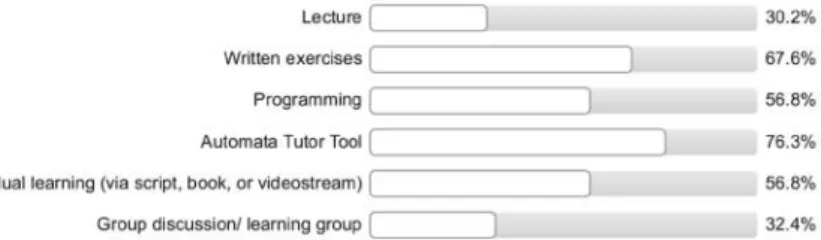
I prefer using AT over pen and paper exercises (12.9% disagree, but median and mean are 4). 5. A question from a survey we conducted to evaluate Automata Tutor, showing that this tool is preferred by most students.
6 Conclusion
The images or other third-party materials in this chapter are included in the chapter's Creative Commons license, unless otherwise indicated in a credit line for the material. If material is not included in the chapter's Creative Commons license and your intended use is not permitted by statutory regulations or exceeds the permitted use, you will need to obtain permission directly from the copyright holder.
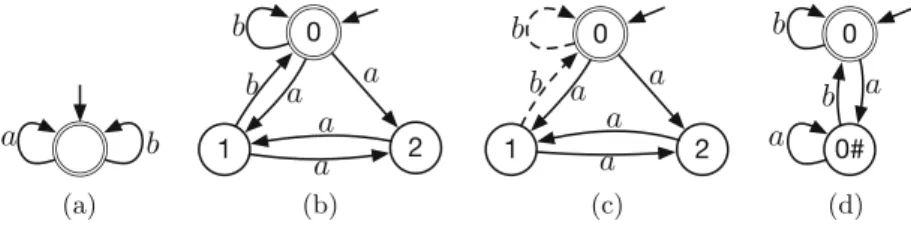
Generalized B¨ uchi Automata via Improved Semi-determinization
Since 2015, Many new results have Been Published: Several Direct Translations of LTL to Semi-Deterministic Automata Automata Specialized Comstructions for Semi-Deterministic Automata [4.6], Algorithms for Quantitative MODPATACATA Inistic Automata to Deterministic Parity Automata [10], and Reinforcement Learning of Control Policy Using Semi-Deterministic Automata [21]. As a result, it could translate TBAs into smaller semi-deterministic automata than (to our knowledge) the only other tool for semi-determination of automata called nba2ldba [26].
2 Improvements in Semi-determinization
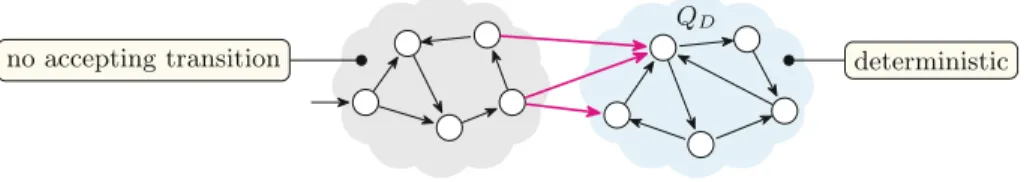
Intuitively, a TGBAA with a set of states Q and a single set of accepting transitions F can be transformed into a semi-deterministic TBA B as follows. Note that Seminator 1.1 can produce a semi-deterministic TGBA with multiple acceptance sets only if it is given a semi-deterministic TGBA as input.
3 Implementation and Usage
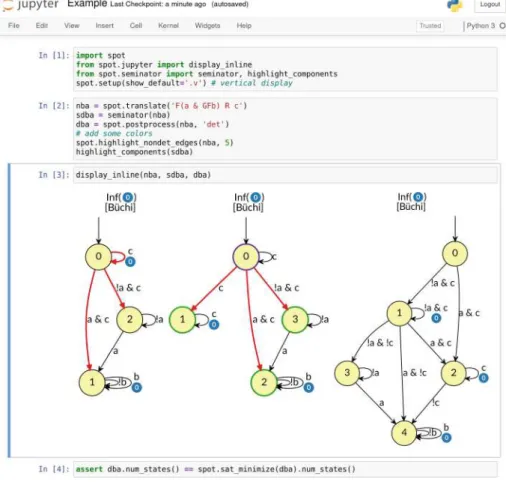
The target for a cut transition leading from q is constructed in the same way as the successor to the hypothetical state ({q},∅,0) of the deterministic part. Additional Jupyter notebooks distributed with the tool document the effect of the various optimization options.1.

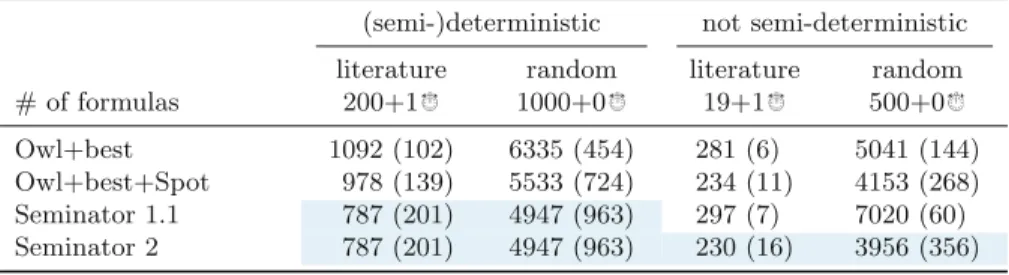
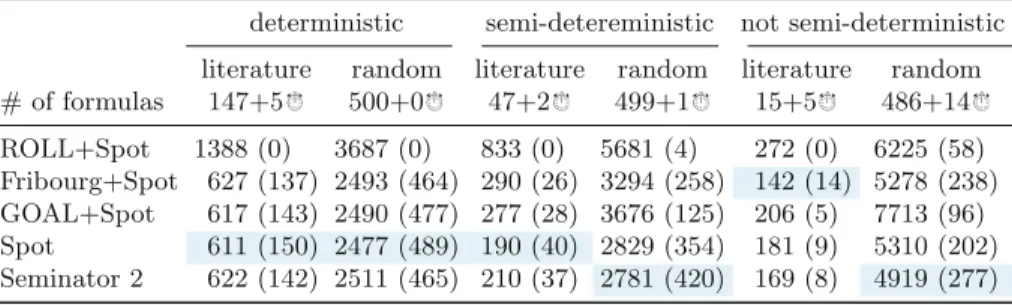
4 Experimental Evaluation
Semi-determinization
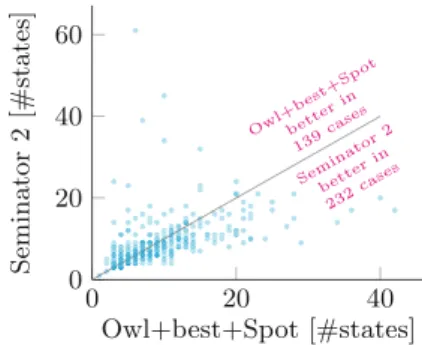
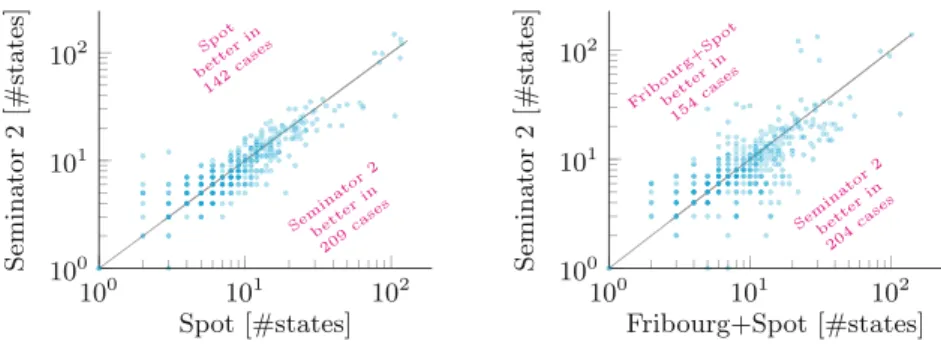
In the (semi-)deterministic category, the automaton produced by byltl2tgba and passed to both versions of Seminator is already semi-deterministic. Figure 4 shows the distribution of differences between the semi-deterministic slots produced by Owl+best+Spot and Seminator 2 for the non-semi-deterministic random set.
Complementation
6. Running times of complementation tools on the 83 hard cases of the non-semi-deterministic random benchmark. Finally, Fig.6 compares the running times of these tools over the 83 hard cases of non-semi-deterministic random benchmark (a case is hard if at least one tool did not complete in 10 s).
5 Conclusion
Esparza, J., Kˇret´ınsk´y, J., Sickert, S.: One theorem to rule them all: a unified translation of LTL inω-automata. Oura, R., Sakakibara, A., Ushio, T.: Rule policy reinforcement learning for linear temporal logic specifications using limit deterministic B¨uchi automata.
Autonomous Aircraft
Related Work
Stream-based monitoring approaches focus on an expressive specification language while dealing with non-binary data. The Copilot framework [19] contains a declarative data stream language from which constant-space and constant-time C monitors are generated; these warranties allow for use on the embedded device.
2 Setup
- Mission
- Non-Intrusive Instrumentation
- StreamLAB
- FPGA as Monitoring Platform
- RTLola Specifications
- VHDL Synthesis
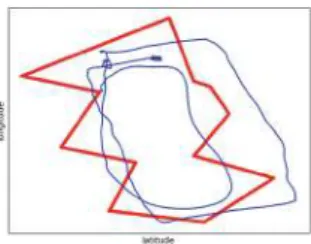
Note 1Hz.3 Current height δheight calculates the difference between the average and current height. It features validation of GPS readings as well as cross-validation of the GPS module against the Inertial Measurement Unit (IMU).
3 Results
Note that the geo-fence specification checks for 12 intersections in parallel, one for each face of the fence (see Fig.2). When monitoring the geo-fence of the reconnaissance mission in Fig.2, all twelve face transitions were successfully detected.
4 Conclusion
In addition, when replaying the sensor data from the enclosed backyard experiment from Sect.2.1, the erratic GPS sensor data results in 113 violations with respect to the GPS module on its own. Other checks, for example detecting a degradation of the GPS module based on its output frequency, were not violated in any flight and were therefore not reported.
Realizing ω -regular Hyperproperties
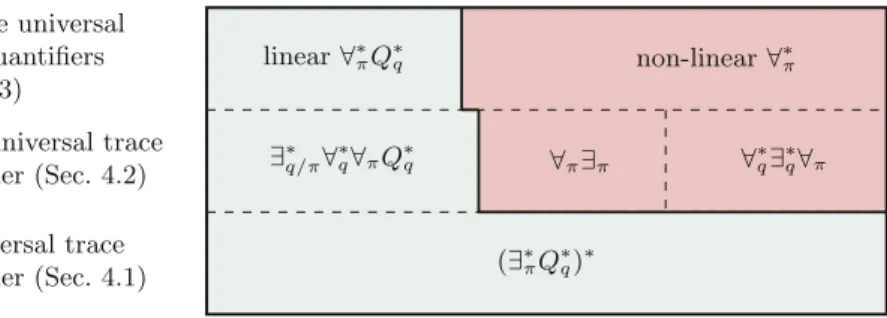
We find that propositional quantification, unlike the satisfiability problem, has an impact on the realizability problem: it becomes undecidable when a propositional∀∃ quantifier alternation is combined with a single universal trace quantifier. We find that an important factor for the decidability of the realizability problem is the number of universal traces that occur in a formula.
2 Preliminaries
For more than one universal track quantifier, we show that determinability can be guaranteed for a fragment, which we call the linear∀∗πQ∗q fragment. We also show that all the above fragments are dense, i.e. the realizability of all other formulas is generally indeterminable.
3 ω -Regular Hyperproperties
The Expressiveness of HyperQPTL
A system satisfies a Prompt-LTL formula ϕ if there is a boundary such that all traces of the system satisfy the formula where each p in ϕ is replaced by ≤k, i.e. the system must fulfill all prompt events within ink steps. For example, ϕ= pψ holds in a system if there is a bound k such that all traces of the system at all times satisfy ψ within ink steps.
4 HyperQPTL Realizability
No Universal Trace Quantifier
Therefore, if the witness sequences for the quantified propositions can be chosen correctly, any strategy realizes ϕQPTL. The second conjunct is satisfied, since two arbitrary tracks πi, πj of a strategy tree are satisfied by construction (Iπi =Iπj)R(Oπi=Oπj).
Single Universal Trace Quantifier
We denote byϕ[J →a π] the formula, where each propositional quantifier∃qj(respectively∀qj) withj∈Jer replaced by the corresponding trace quantifier∃πj (respectively or∀πj); and each qj inψ is replaced by aπj. Together with qi and pi for input i, they simulate a universal and an existentially quantified trace from the model.
Multiple Universal Trace Quantifiers
Our goal was to find the largest possible fragments where the realizability problem with HyperQPTL can still be decided. The three fragments for which we could prove decidability all map to the logical QPTL for which the realizability problem is known to be non-elementary (already its satisfiability problem is non-elementary [30]).
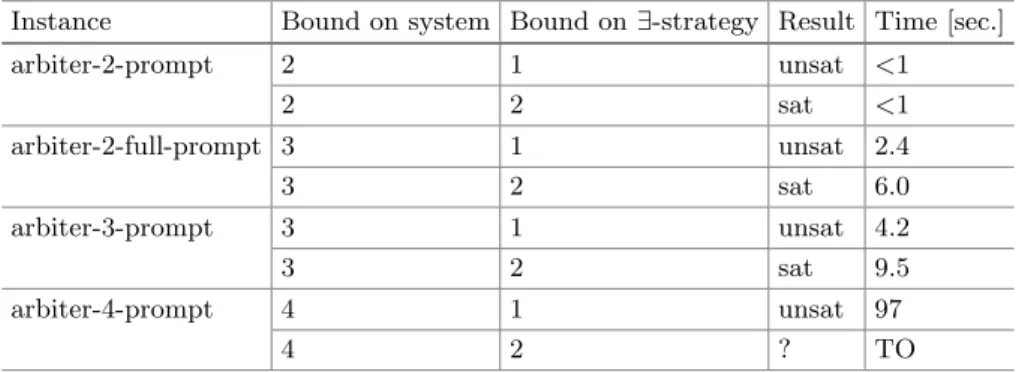
5 Experiments
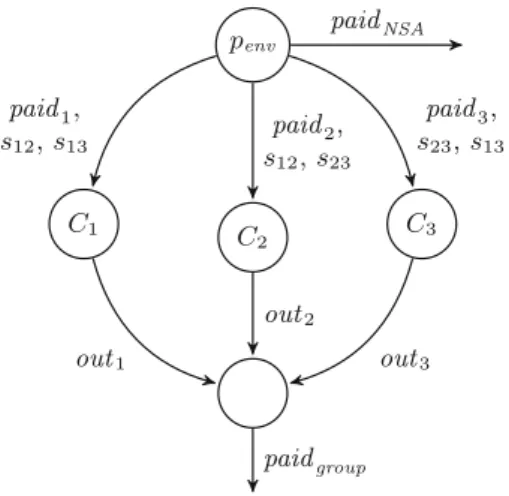
We present the tool AdamMC as the first model checker for Petri nets with throughput against Flow-LTL. The tool reduces the model checking problem for secure Petri nets with throughput against Flow-LTL to the model checking problem for secure Petri nets against LTL.
2 Petri Nets with Transits and Flow-LTL
As a final step, AdamMC reduces the model control problem of safe Petri nets against LTL to a circuit model control problem. In Section 4, we algorithmically encode simultaneous updates of software-defined networks in Petri nets with transits.
3 Application Areas
2.Overview of AdamMC's workflow: The scope of the tool is given by three different input domains: software-defined network/Flow-LTL (Input I), Petri-net with transits/Flow-LTL (Input II) and Petrinet/LTL (Input III). State-of-the-art tools like LoLA [32] and ITS-Tools [29] are limited to interleaving maximal runs and places like atomic propositions.
4 Verifying Updates of Software Defined Networks
Network Topology, Configurations, and Updates
In addition, Adam provides a concurrent view of executions and can control maximum-concurrent executions which require each subprocess of the system to progress maximally rather than just the entire system. For Petri net model control (Input III), we allow Petri nets in APT and PNML format as input and provide a parser for LTL formulas.
3.Summary of this approach follows: Each firing of a transition of the original grid is divided into starting a transition in the subgrid for the execution formula and then firing a transition in each subgrid following a flow formula. We use until operators in the constructed LTL formula to skip only the steps that do not involve the assumed chain tracing in the flow formula.
Assumptions and Requirements
The order of the switch updates is defined by the nesting of sequential and parallel updates. The update is realized by a specific token that moves through unique places of the form, uf, ss, sf, ps, pf for start and end of each switch updateu∈SwU, each sequential updates∈SeU, and each parallel updatep∈PaU.
5 Algorithms and Optimizations
However, several options to reduce the number of gates of the generated circuit worsened the performance of some benchmark families and improved the performance of others. An overview of the optional optimization parameters is available in the AdamMC documentation [12].
6 Evaluation
We found that versions of the sequential and parallel approach with blocking arcs for tracking flow chains are generally faster than the versions without. The number of TOs (out of 230 tested parts of the formula) experiences an increase with operators to in the sequential approach, but only needs disjunction in the parallel approach.
7 Related Work
The model checking subroutine of the synthesizer assumes that each packet sees at most one updated switch. There are a significant number of model checking tools (eg for Petri nets and an annual model checking competition [20]). AdamMC is limited to secure Petri nets, while other tools can handle tied and colored Petri nets.
8 Conclusion
Finkbeiner, B., Gieseking, M., Hecking-Harbusch, J., Olderog, E.: A model of checking data flows in concurrent network updates (full version). Finkbeiner, B., Gieseking, M., Hecking-Harbusch, J., Olderog, E.: AdamMC - A model checker for Petri nets with transits against Flow-LTL.
Automata, and Reduction
Linear Temporal Logic
The main difference between state-based formalism and action-based formalism is that in state-based formalism, any number of atomic propositions can hold at any step. The following fact about the state-based semantics can be proved by induction on the formula structure:.
B¨ uchi Automata
In this case, the conversion to B involves creating one transition for each a∈A for which φ holds when true is assigned to one and false is assigned to all other actions. Note that in the special case where the two automata have the same alphabet (Σ1 =Σ2), each action synchronizes, and the parallel composition is the usual "synchronous product." In this case, L(B1B2) =L(B1)∩ L(B2).
Labeled Transition Systems
In practice, tools that convert LTL formulas into BAs produce an automaton in which an edge is labeled by a propositional formula φoverαf. Such an edge represents a series of transitions, one for each P ⊆ A for which φ holds for the value that assigns true to each element of P and false to each element of A\P.
3 Interruptible Properties
- Definition and Examples
- Decidability of Interruptibility of LTL Formulas
- Generation of Interruptible LTL Formulas
- Decidability of Interruptibility of B¨ uchi Automata
An accepting path for ζ cannot pass through a sharp state or DIV, because only invisible transitions end in those states. An accepting path for ζ in ˆB consists of a prefix ˆθ of visible transitions followed by an infinite accepting pathξ of invisible transitions.
4 On-the-Fly Partial Order Reduction
General Theory and Soundness Theorem
Then for allj ≥i a the first action is θj and a is not in the extensive set last(ηj). Hence there is a cycle in R for which a is always enabled, but never in the extensive array, which contradicts C3.
Ample Sets for a Parallel Composition of LTSs
For C3 we actually have the stronger condition that in any cycle in the reduced space, at least one state is fully activated. The outer search stores j in the state, and the inner search uses j to reconstruct the SCCC0 and the spacious setE.
5 Related Work
Much of the earlier work on POR for LTSs deals with the "offline" case, that is, the construction of a subspace of M that preserves certain classes of properties. In contrast, Theorem 3 deals with an on-the-fly algorithm, i.e. the construction of a subspace of MB.
6 Experimental Results and Conclusions
The results show that all formulas from 2016 and 2019 are interruptible, which is in line with the expectations of the RERS organizers. An examination of Spin's output in verbose mode reveals that the problem is as described in Sect.5: the full set of enabled transitions is explored at each transition due to the update of the shared variable.
On the other hand, looking at the global proof (that is, the set of lemmas discovered to disprove a restricted counterexample), it is almost obvious that (a−c)≤(b−d) is an interesting generalization to prove. Furthermore, we propose an efficient example rule for the theory of Linear Integer Arithmetic.

2 Background
However, to simplify the presentation, we only describe the algorithm for the special case of the security problem. We emphasize that Spaceer, as well as the development of this paper, applies to the more general setting of CHCs (both linear and non-linear).
3 Global Guidance of Local Proofs
Without a global view of the overall evidence, it is difficult to determine when the algorithm generalizes too much. Of course, it is only assumed if it is not already blocked and does not contain any known available modes.
4 Global Guidance for Linear Integer Arithmetic
- Linear Integer Arithmetic: Background
- Lemma Selection
- Subsume Rule for LIA
- Concretize Rule for LIA
- Conjecture Rule for LIA
- Putting It All Together
The other columns (coordinates) can be expressed by linear combinations of the linearly independent ones. Note that the latter is amay pob, in the sense that some of the states it represents may not result in a security breach.
5 Evaluation
We compare to Spacer because it dominated the competition by solving 85% of the benchmarks in CHC-COMP 2019 (20% more than the number two) and 60% of the benchmarks in CHC-COMP 2018 (10% more than the number two). For the comparison with LinearArbitrary, we used both the CHC-COMP benchmarks and the benchmarks from the artifact evaluation of [28].
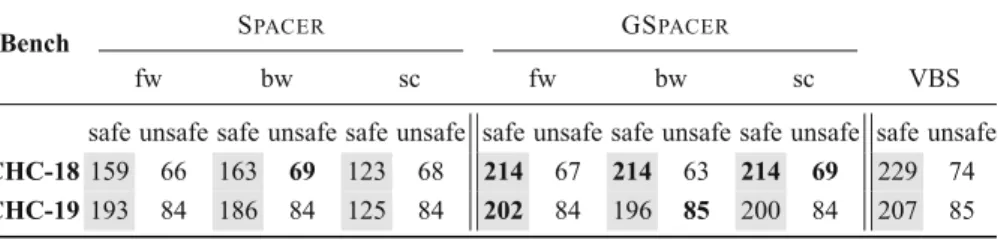
6 Related Work
This comparison shows that incorporating local reasoning with global guidance not only mitigates its shortcomings but also outperforms global data-driven reasoning. Compared to IMC, the propagation phase and inductive generalization of IC3 [7] can be seen as providing global guidance using lemmas found in other parts of the search space.
7 Conclusion and Future Work
A Subsum-like rule is suggested in [26] for bit-vector theory and in [4] for LRA, but in both cases without global guidance. Most importantly, the global instruction decouples Spacer's dependence on the interpolation strategy and performs almost equally well across the three interpolation schemes we consider.
Software-Defined Networks
Another key limitation is the fact that they cannot think of a controller program that is itself responsible for changes in the network configuration. Formal verification methods that incorporate controller code into the network model can solve this important problem.
2 Software-Defined Network Model
- Formal Model Definition
- SDN Model Components
- Guarded Transitions
- Specification Language
Initially, the switch flow tables are empty, so p is copied to the controller's request queue (transition nomatch); note that p remains in the switch's packet queue in the black due to p0.8qab withdrawal. The controller's packet handler is then called (ctrl transition) and, as a result, (1) p is copied to the black key forwarding queue, (2) rule r1 is copied to the black key control queue, and (3) r2 rule is copied to the white key control queue.
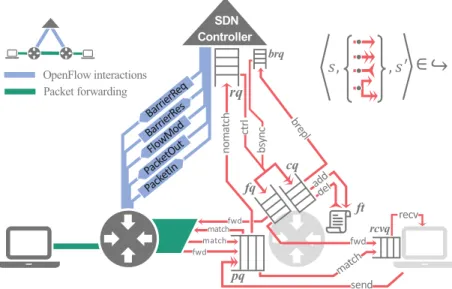
3 Model Checking
- Contextual Partial-Order Reduction
- State Representation
- Performance Comparison
- Model Expressivity
A value of 1 in thefq section indicates that one copy of the packet is queued for forwarding by the corresponding switch. A value of 1 in the rq section indicates that a copy of the packet sent by the corresponding switch (when the anomatch transition is triggered) is stored in the controller's request queue.
Software Verification
Finding loop invariants is arguably the most important part of proofreading in program verification. We perform two case studies that demonstrate the flexibility of Code2Inv on different classes of loop invariants.
3 Framework
Alternatively, the neural networks can be initialized with pre-trained weights, which can increase overall performance. The neural context is initialized for concatenating embeddings of the given verification instance (line 13), and then maintained by αctx (line 17) which at each step incorporates the neural state of the partially generated candidate invariant (line 16), where the neural state is encoded by inv.
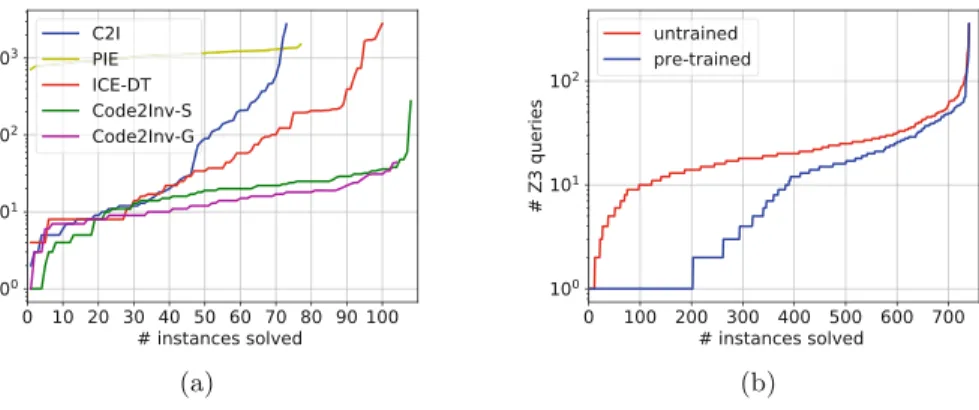
4 Evaluation
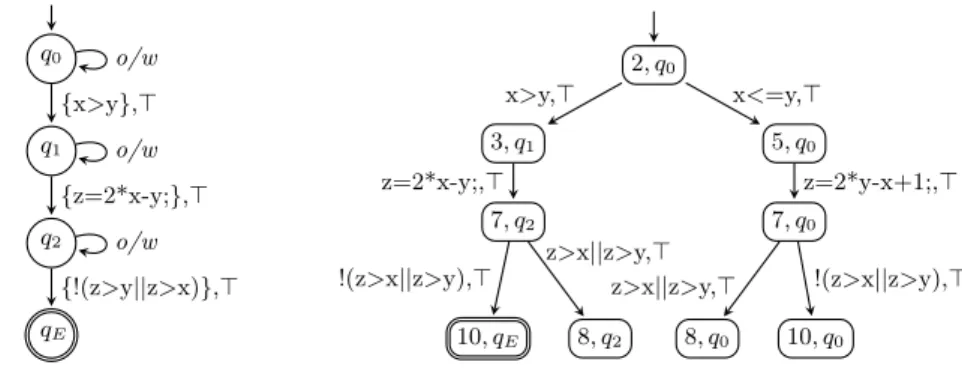
We compare Code2Inv with our previous specialized prototype and three other state-of-the-art verification tools: C2I [29], LoopInvGen [26], and ICE-DT [10]. In the corresponding CFA in Figure 3, this is represented by the reachability of the location labeled 10.
3 Approach
- From Witnesses to Programs
- Programs from Violation Witnesses
- Programs from Correctness Witnesses
- Experimental Setup
- Results
The results of the validation phase in SV-COMP 2020 [5] are summarized in Table 1 (for witnesses of violations) and Table 2 (for witnesses of correctness). Reductant-based conditional model checking. The concept of generating programs from an ARG has also been used to successfully construct conditional verifiers [14].
2 Support for Pointers
The basis of SPARK's ownership policy is the relocation semantics of assignments. The proprietary system ensures that the designated data is not re-accessible through the job source.
3 Recursive Data Structures
In fact, any effects that could occur because variables share a substructure cannot be observed because of the ownership rules. Y:= Y. Next; -- Ownership of the first cell in Y is lost for good end loop; -- Ownership of X cannot be restored.
4 Borrowing Ownership
While in the scope of the borrower, these indirect modifications can be ignored from the analysis, since the ownership policy makes it impossible to observe them. To be able to reconstruct the borrowed object from the value of the borrower, we need to trace the relationship between them.
5 Describing the Borrow Relation