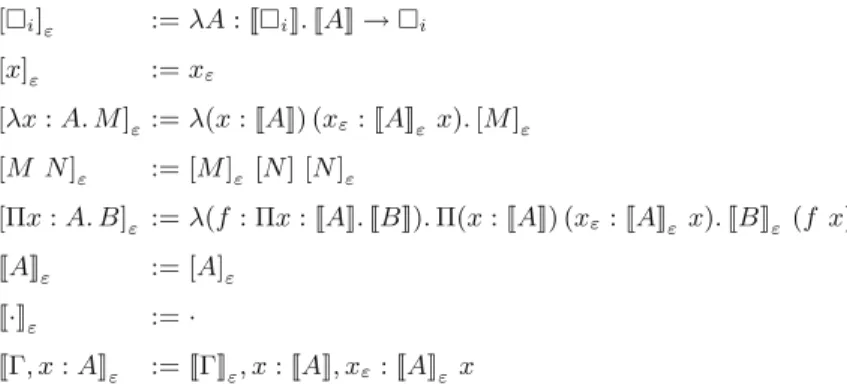For simplicity, we axiomatize it instead of requiring inductive types in the translation target. We now turn to the translation of the elimination of inductive expressions, that is, to pattern matching.

1 Introduction
This paper presents a variant of two-way type checking where the type information flows from arguments to functions. A variant of two-way type checking where the diversion mode is combined with a new, so-called application mode.
2 Overview
- Background: Bi-directional Type Checking
- Bi-directional Type Checking with the Application Mode We propose a variant of bi-directional type checking with a new application mode
- Benefits of Information Flowing from Arguments to Functions Local Constraint Solver for Function Variables. Many type systems, including
- Application 1: Type Inference of Higher-Ranked Types
- Application 2: More Expressive Type Applications
However, this is not true because the application mode is not conservative over traditional two-way type checking. In our system, the expression above is not typeable, due to the information flow in the application mode.
3 A Polymorphic Language with Higher-Ranked Types
- Syntax
- Type System
- Subtyping
- Translation to System F, Coherence and Type-Safety
- Algorithmic System
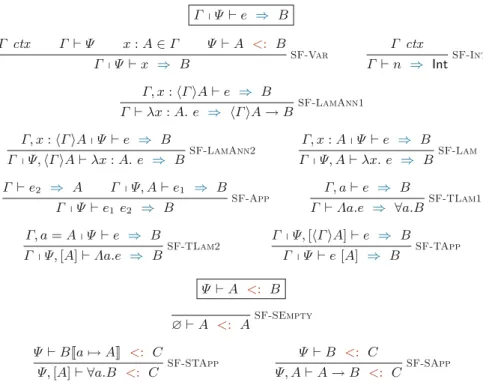
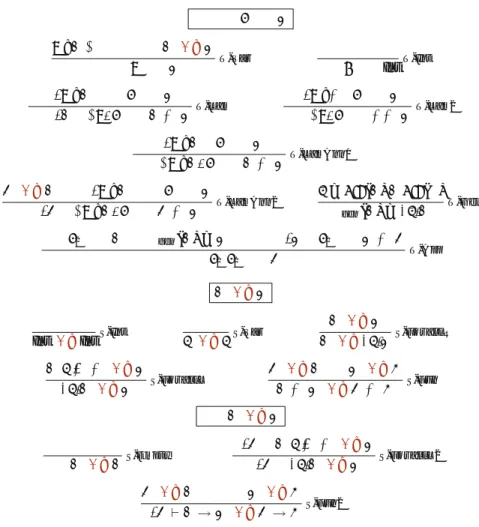
The standard way of reasoning Γ e ⇒ B can be considered as a special case when the application context is empty. One special feature is that the context of the application determines the format of the typing result.
4 More Expressive Type Applications
Syntax
The type well-formedness under type contexts is given in Fig.3, which is quite simple. The well-formedness of type contexts Γ ctx, and the well-formedness of application contexts Γ Ψ can be naturally defined based on the well-formedness of types.
Type System
RuleSF-Lampops type A from the application context, puts x:A in the typing context, and returns only the return type B. A variable of type a is pushed to the typing context, and the returned type is a polymorphic type.
Meta Theory
RuleSF-LamAnn2 has a non-empty application context, so it requests that the type at the top of the application context is equal to ΓA. We interpret the rule form Ψ A <: B if, under the application context Ψ, A is a subtype of the type whose type arguments are Ψ and whose return type is B.
5 Discussion
Combining Application and Checked Modes
Detailed definitions of semantics and operational values can be found in the supplementary materials. Note that adding expression annotations can bring convenience to programmers, as annotations can be placed more freely in a program.
Additional Constructs
An extended version of the calculation presented in Section 3, which includes rules for pairs (T-Pair, S-Pair, T-Fst2andT-Snd2), is formally studied.
Dependent Type Systems
6 Related Work
Bi-directional Type Checking
The three-way type checking system [15] is based on two-way type checking and has an extensive set of property types, including intersections, connections, and quantified dependent types, but without parametric polymorphism. Greedy bidirectional polymorphism [13] adopts a greedy idea from Cardelli [4] about bidirectional type checking with higher ranked types, where the type variables in instantiations are determined by the first constraint.
Type Inference for Higher-Ranked Types
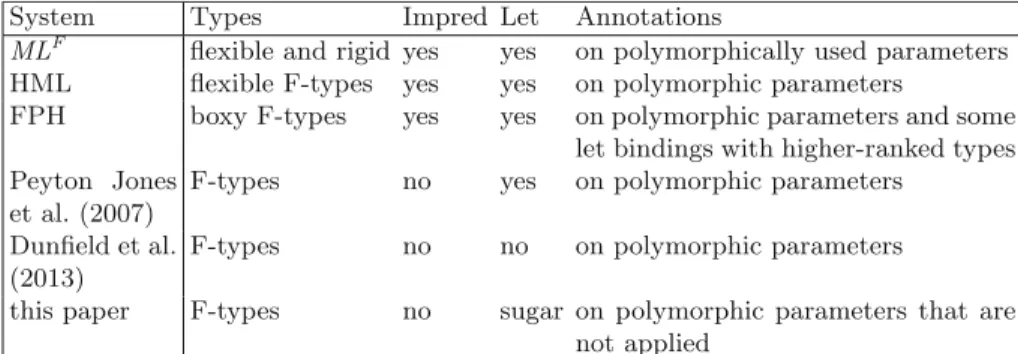
MLF flexible and rigid yes yes on polymorphic parameters used HML flexible F-types yes yes on polymorphic parameters. FPH boxy F-types yes yes on polymorphic parameters and some show bonds with higher ranked Peyton Jones types.
Tracking Type Equalities
2007) F-type does not give regarding polymorphic parameters Dunfield et al. 2013) F-types no no no regarding polymorphic parameters.
7 Conclusion
Compared to traditional two-way type checking, application mode opens up a new way to design inference/type checking. An obvious possible future work is to investigate more systems where the mode of application brings benefits.
Specifically, we consider a call-by-value functional programming language with algebraic effects in the sense of Plotkin and Power [21]. To focus on the main contributions of the paper (behavioral logic and its induced behavioral equivalent), we instantiated a "call-by-value functional language with algebraic effects" using a very simple language.
2 A Simple Programming Language
Example 0 (Pure Functional Calculus). This is the trivial case (from the point of view of the effect) in which the signature of the effect operations is empty. Otherwise, the evaluation process can only end in a configuration of the form (S, σ(. .)) for some operations with effect σ∈ Σ.
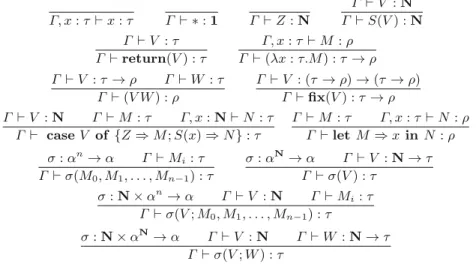
3 Behavioural Logic and Modalities
Note that in the case of pure functional computation, all trees are leaves: either value leaves V or non-termination leaves⊥. The semantics of the termination modality↓ is defined as above. Intuitively, exec(t, s) defines the result of "executing" the command tree in the effect tree starting in states s whenever this execution ends.

4 Behavioural Equivalence
The one of the latter states that is finite and all leaves are finite trees that have only ∗leaves. If this sum is greater than a rationalq, some finite approximation of the sum must already be over q.
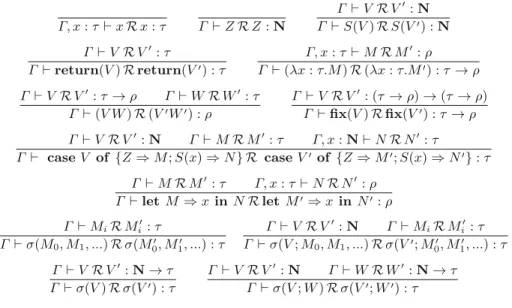
5 Applicative O -(bi)similarity
For any family of upward closed modalitiesO, we have that the logical equivalence ≡V is identical to O-bisequality. Using these special formulasχV, the rest of the proof is very similar to the proof in Theorem2(a).
6 Howe’s Method
7 Pure Behavioural Logic
We know of no proof of the compatibility of the ≡F and F+ relations that do not pass through the logicV. In particular, the compatibility property of the fix operator seems to be difficult to establish directly for≡F andF+.
8 Discussion and Related Work
- Algebraic Effect Handlers
- Elaborating Subtyping
- Polymorphic Subtyping for Types and Effects
- Guaranteed Erasure with Skeletons
First, in Sect.3 we present ImpEff, a polymorphic implicitly typed calculus for algebraic effects and handlers with a subtyping-based type-and-effect system. ImpEffis essentially a (desugared) source language as it appears in the compiler frontend of a language like Eff. But by dropping the effect variables and subtyping constraints of the type f, we get ∀α, α.(Unit → α) →α instead of the expected type∀α.(Unit→α)→α.
3 The ImpEff Language
Typing
Note that we use ρ instead of π, which allows us to define subtypes between two value types, calculation types or dirts, within the same relationship. Rules VCoTrans, CCoTrans, and DCoTrans express the transitivity of subtyping for value types, computation types, and dirts, respectively.

4 The ExEff Language
Typing
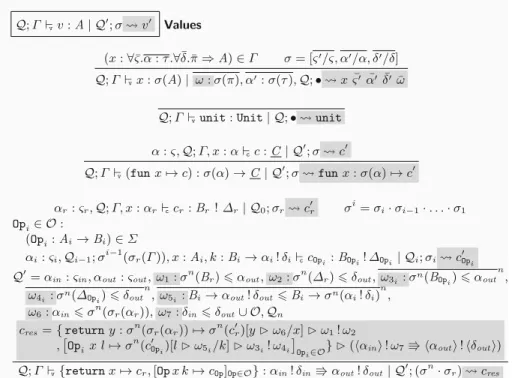
Aside from the typing rules for skeleton, type, impurity, and constraint abstraction (and, subsequently, skeleton, type, impurity, and constraint application), the main difference between typing for ImpEff and ExEff lies in the explicit casting shapes, (vγ) and (cγ). Good formation of types, constraints, impurities and skeletons. The definitions of judgments controlling the well-formedness of ExEffvalue types (Γ T T : τ), calculation types (Γ C C : τ), impurities (Γ Δ Δ), and skeletons (Γ τ τ) are as straightforward as those.
Operational Semantics
Since we know that the computation bound to x calls no operations, we (a) safely "drop" the impure part of γ and (b) substitutexwithvT, cast with the pure part of γ (thus preserving the types). If an operation is called in a sequencing calculation, the evaluation is suspended and the rest of the calculation is caught in the continuation.
Type Safety)
The first of the two catches cases where the called operation is handled by the handler, in which case the respective clause of the handler is called. The last line catches cases where the operation is not covered by the handler and therefore remains untreated.
5 Type Inference and Elaboration
Type Preservation)
- Constraint Generation and Elaboration
- Constraint Solving
- Discussion
In turn, we require that (a) the type of the return clause be a subtype of αout!δout (given by the combination of ω1 and ω2), (b) the type on the right side of each operation clause is a subtype of the general result type: σn(BOpi!ΔOpi) αout!δout (attested to ω3i!ω4i), (c) the actual types of the continuations Bi → αout!δout in the operation, clauses must be subtypes of their assumed types Bi →σn(αi!δi) (witness ω5i). d) the general argument type αin is a subtype of the assumed type of x:σn(σr(αr)) (witnessed by ω6), and (e) the input dirt set δin is a subtype of the resulting dirt set δout, extended by the handled operations O(witnessed by ω7). In the following four cases, a skeleton annotation α : τ is considered at the beginning of the queue and the skeleton concrete is passed to the type variable.
6 Erasure of Effect Information from ExEff
The SkelEff Language
At first glance, the constraint generation algorithm of Section 5.2 seems unnecessarily complicated, due to its eager solving of let generalization constraints. In turn, since skeletal constraints are generated when solving subtyping constraints (Section 5.3), all skeletal annotations should be available during constraint resolution.
Erasure
By dropping binders, values can be turned into calculations that trigger their side effects immediately, rather than at the later time when the original binder was eliminated. However, there is no call for this careful approach in our setting, since our grammatical division of terms into values (without side effects) and computations (with side effects) guarantees that this problem cannot arise when we delete values into values and computations into computations.

7 Related Work and Conclusion
Në: Proceedings of the 11th ACM SIGACT-SIGPLAN Symposium on Principles of Programming Languages, POPL 1984, pp. In: Proceedings of the 2007 ACM SIGPLAN Workshop on Types in Languages Design and Implementation, TLDI 20.
Semantics
As such, it provides more evidence for the claim that the promising semantics satisfactorily solves the out-of-air problem. The second major contribution is the proof of SLR's solidity against the promising semantics [13]2.
2 Our Logic
- The Assertions of the Logic
- The Rules of the Logic for Relaxed Accesses
- Reasoning About Coherence
- Handling Release and Acquire Accesses
- Plain Accesses
Note that we cannot determine what values the read reads until the end of the litmus test. Again, we can obtain O(x, v0x,0), where v0x is the initial value of x, from the initial write permission forx, and distribute it to all the threads that will read from x, expressing the fact that the initial value is available to all threads, and use it as the required O(x, , t) in the prerequisite of the read rule.
3 The Promising Semantics
- Storage Subsystem
- Thread Subsystem
- Interaction Between a Thread and the Storage Subsystem The interaction between a thread and the storage subsystem is given in
- Constraining Promises
- Full Machine
A thread state is a pair of TS = σ, V, where σ is the internal state of the thread and V is a representation. Finally, the full machine transitions simply lift the wire configuration =⇒ transitions to the machine level.
4 Semantics and Soundness
- The Intuition
- A Closer Look at the Resources and the Assertion Semantics We now take a closer look at the structure of resources and the semantics of
- Relating Concrete State and Resources
- Soundness
- Non-promising safety implies safety)
This is the main lemma in the sound proof of the (r-rlx*) and (r-acq*) rules. The delete used in non-promise security does not limit the current thread's promises.
5 Related Work
A number of other logics - GPS [26], iGPS [12], OGRA [16], iCAP-TSO [24], the reliance-guarantee proof system for TSO by Ridge [23] and the program logic for TSO by Wehrman and Berdine [28] - have been developed for even stronger memory models (release/acquire or TSO), and also rely quite heavily on the stronger consistency guarantees offered by those models and attempt to expose them. to lay. 3], such models cannot be used to define a language-level model that allows for the weak behavior of LB+data+fakedep and similar litmus tests while prohibiting fanciful behavior.
6 Conclusion
Kaiser, JO, Dang, HH, Dreyer, D., Lahav, O., Vafeiadis, V.: Strong logic for weak memory: reasoning about release-acquire consistency in Iris. The third-party images or other materials in this chapter are included in the Creative Commons license of the chapter, unless otherwise noted in a line of credit accompanying the materials.
Permissions
Since fractions are simpler and more uniform than protocol-based logics, they are amenable to automation [26,33]. There has been considerable work in recent years on tool support for protocol-based approaches, but they require significant user input and provide essentially no conclusions.
2 Technical Preliminaries
To prevent deformation of recursive structures shown in Fig. In Sect.3 we will see how disjointness enables the distribution of predicate multiplication over, and in Sect.4 we will see how disjointness enables antiframe inference under biabduction.
3 Predicate Multiplication
Proof Rules for Predicate Multiplication
Complicating the picture a bit, predicate multiplication pushes into implication⇒but does not pull out of it. The predicate dtree(x) is even weirder and owns different amounts of different branches of the tree, essentially depending.
Verification of processTree using predicate multiplication We now explain how the proof of processTree is carried out in Fig. 4 using
The base basex=nullis handled in lines 4–5 by applying the DotPure rule, i.e., x=null π· x=nulland thenDotPos,π· x=null π·tree(x). Note that we need DotDotrule to "collapse" the two uses of predicate multiplication into one so that we can implement the recursive specification (with newπ in the recursive precondition equal toL ⊗π).
4 Bi-abductive Inference with Fractional Permissions
Fractional Residue Computation
Eventually, the remaining unmatched fragments of the predecessor are returned to build the completion framework. Following the spirit of Calcagnoet al.[10], the steps in both subroutines involve applying folding and unfolding rules to the predicate tree and then matching the corresponding pair of fragments from the predecessor and successor.
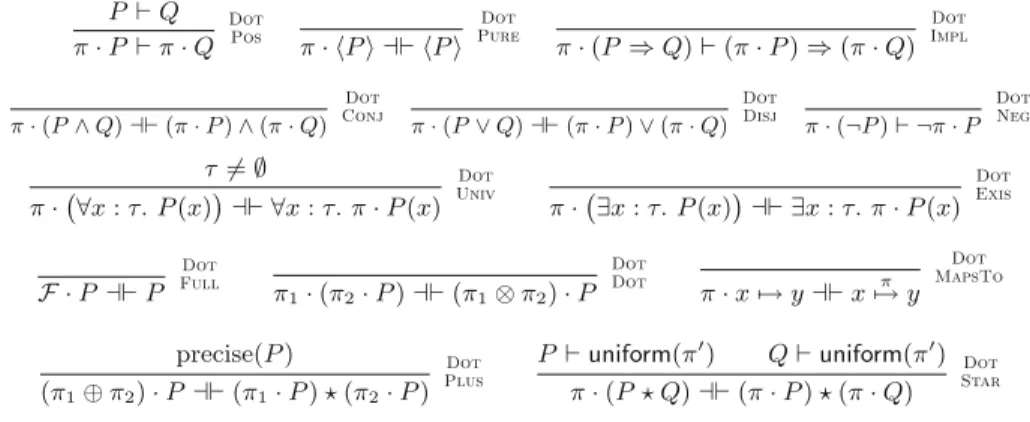
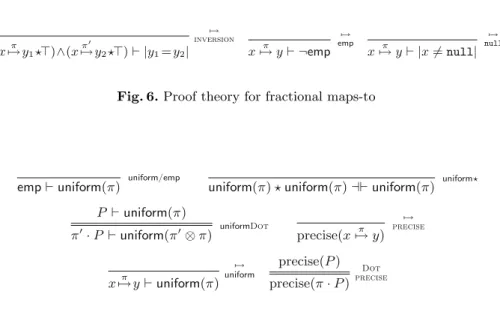
5 A Proof Theory for Fractional Permissions
- Proof Theory for Predicate Multiplication and Fractional Maps-To
- Proof Theory for Proving that Predicates Are Precise
- Proof Theory for Induction over the Finiteness of the Heap Recursive predicates such as list(x) and tree(x) are common in SL. However,
- Using Our Proof Theory
To use predicate multiplication, we will need to prove two kinds of side conditions: uniform/emp tells us that empisπ-uniform for allπ; conclusion (all defined heap locations are kept by share) is absolutely true. The uniformDot rule tells us that if P is π-uniform, then after multiplying P by the fraction π, the result is (π⊗π)-uniform.
6 The ShareInfer fractional biabduction engine
To check the precision, the tool maneuvers over the proof rules in fig. 6 and 8 to achieve the desired goal. In both cases, recursive predicates are handled with the rules in Fig.
7 Building a Model for Our Logic
- Cancellative Separation Algebras
- Fractional Share Algebras
- Scaling Separation Algebra
- Compositionality of Scaling Separation Algebras
- Model for Inductive Logic
12. 14 additional axioms for scaling division algebras beyond those inherited from canceling division algebras. Example 1 (Shares). The action modelS,⊕is an SSA, and the positive (non-E)actionsS+,⊕is a WSSA, with strengthS(π, π)def= πandmulS(π, π)def= π⊗π.
8 Lower Bounds on Predicate Multiplication
Predicate Multiplication’s Axioms Force Share Model Properties
Disjointness in a Multiplicative Setting
9 Related Work
Bornate et al.[4] introduced integer counting permissions Z,+,0 to reason about semaphores and combined rationals and integers in a hybrid permission model. On the other hand, HIP/SLEEK [31] uses rationales to model "thread as resource" so that the ownership of a thread and its resources can be transferred.
10 Conclusion
One potential problem with these programs is that the waiting thread can be suspended forever, resulting in a deadlock, a condition in which every thread of the program is waiting for a condition variable or lock. However, one potential problem with these synchronizers is deadlock, where all threads of the program are waiting for a state variable or lock.
2 Background Information on the Underlying Approaches
Verifying Absence of Data Races
In this paper, we present a modular approach to verify deadlock freedom of programs in the presence of state variables. Section 3 introduces a preliminary approach to verify deadlock freedom for some common applications of state variables.
Verifying Absence of Deadlock
To satisfy the first rule, where the pending object is a lock, as shown in the example on the left side of Figure 3, after the lock is acquired, that lock is loaded into the bag1 (multiset) of the thread's commitment, denoted by obs(O). Before the receiver thread forks, a credit and a liability for the channel are created in the main thread.
Proof Rules
It therefore does not make sense to fulfill an obligation for a state variable every time it is declared. A wait command is usually executed in a loop that checks the wait state of the related state variable.
3 Deadlock-Free Monitors
- High-Level Idea
- Tracking Numbers of Waiting Threads and Obligations
- Resource Transfer on Notification
- Proof Rules
- Verifying Channels
- Other Examples
In addition, notify(v) consumes moving resources, denoted by M(v), that appear in the postcondition of the notified thread. In the barrier program shown in Figure 8, barrierb consists of an integer variable indicating the number of remainders.
4 Relaxing the Precedence Relation
A Relaxed Precedence Relation
If is a slot or a channel, where P(om) =false, then at least one thread has an obligation to and waits for an object whose wait level is lower than the wait level of om, which contradicts the minimal wait level of om. Consequently, this thread must wait for an object whose wait level is lower than the wait level of om, which contradicts the minimality of the wait level of om.
A Further Relaxation
A Valid Graph Is Not Deadlocked)
One application of the new definition is the bounded-channel program shown in Figure 13, where the sending thread waits for the receiving thread if the channel is full, synchronized with vf, and the receiving thread waits for the sending thread if the channel is empty, synchronized with ve. Specifically, a sending thread with a forve commitment could execute a wait(vf, l) command, and a receiving thread with a vf commitment could execute a wait(ve, l) command.
5 Soundness Proof
- Correctness of Commands)
- Rule Consequence)
- Rule Frame)
- Rule Sequential Composition)
- The Initial Configuration is Valid)
Several approaches to verify termination [1,21], total correctness [3], and lock-freeness [2] of concurrent programs have been proposed. Consequently, they cannot be used to verify deadlock-freeness of programs using state variables, where suspending a notification thread can cause a waiting thread to be blocked indefinitely.
Shape Analysis
However, in many concurrent data structure implementations, the heap represents more sophisticated structures, such as skip lists and arrays of singly linked lists [12]. Our framework is the first to automatically verify concurrent data structure implementations that use singly linked lists, skip lists as well as arrays of singly linked lists [12], at the same time as handling an unlimited number of concurrent threads, an unbounded domain of data values (including timestamps), and a heap shared.