Inquiries about the use of the book should be directed to INTECHOPEN LIMITED rights and permissions department ([email protected]). Dolores Kuzelj, the Writer Services Manager, who provided constant support throughout the editing process of the book.
121 Design Principles of 5G NR RoF-Based Fiber-Wireless Access Network
Introduction
There had been several works related to different types of coding in communication research. In the field of communication, the advent of multimedia had led to video on demand.
Conclusion
In the field of computer science, with the advent of the Internet, the topic of computer communication gained great importance. Anti-counterfeiting is one of the most challenging problems in digital cinema rights management.
Digital cinema
This creates two issues that must be considered when designing watermarking schemes for digital cinema. Solving this problem requires digital cinema watermarking schemes to be able to calculate distance and angle.
Digital watermarking
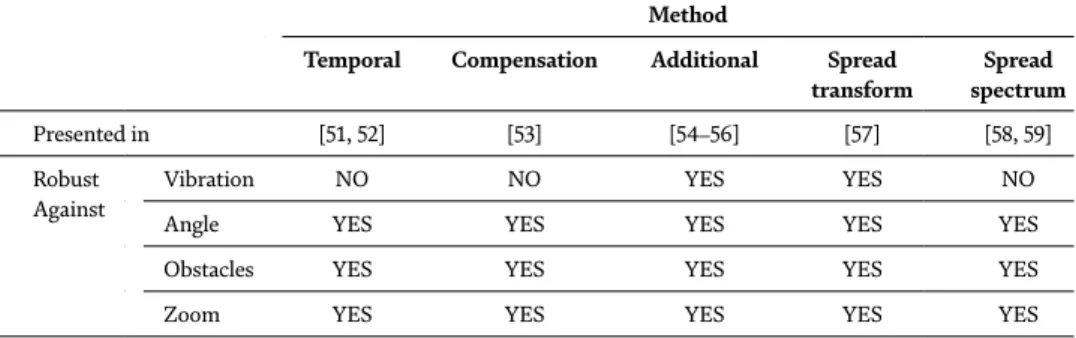
An Investigation of Piracy Protection Techniques in Digital Cinema Watermark Schemes DOI: http://dx.doi.org/10.5772/intechopen.92412. The first digital cinema system specification was published in 2005 by a consortium of six major studios.
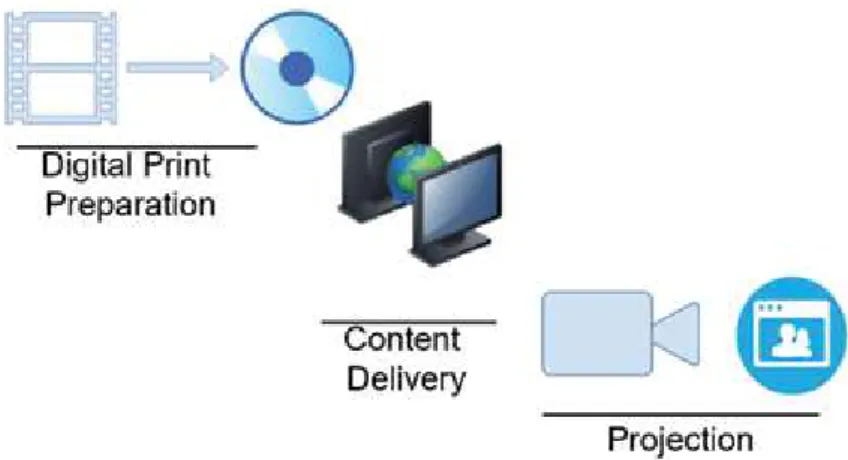
Survey on watermarking in digital cinema
- Identifying the theatre
- Locating the camcorder
Most of the methods presented in the literature avoid the audio watermark due to its complexity. In the method proposed in [50], the audio is placed on the video instead of the soundtrack.
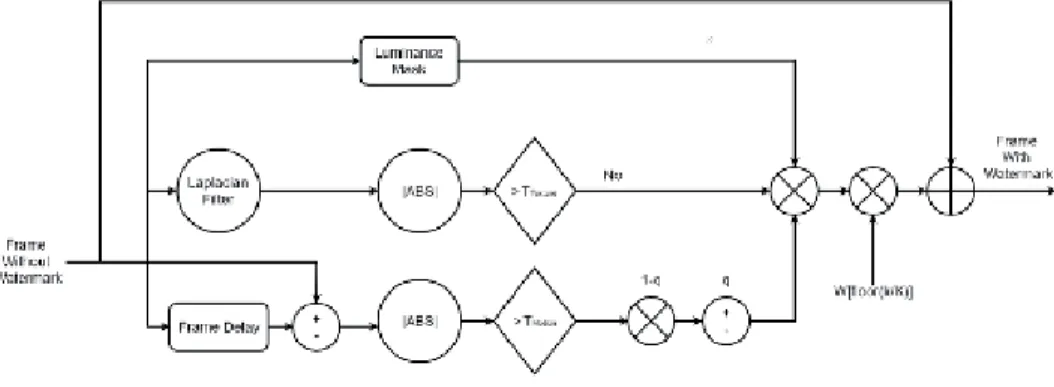
Conclusion
- Confidentiality
- Integrity
Codes, errors and erasures
- Linear block codes
- Erasures
- Separation of errors from erasures
Low-density parity-check codes (LDPC codes) are now used in many recent high-speed communication standards, such as Digital video broadcasting-S2 (DVB-S2), WiMAX, 10GBase-T Ethernet [9]. The decoder can calculate a parity check matrix for the punctured code upon receipt of the code word.
How to build an l-separating matrix
- Set separation Let H ¼ � h i , j �
- Separating matrix
- A more efficient separating matrix
If H is a parity check matrix that separates l codes of C, we can construct a parity check matrix based on H for any code punched up to a fixed number of l symbols. H can distinguish deletions from errors because H has enough parity check equations that do not check any deleted symbols and are sufficient to characterize the punched code.
Covering design
- Approach 1
- Approach 2
Thus, any subgroup of size t formed using these elements u�1 can be formed from any other subgroup in the column; (b) any subset of size t containing . It is easy to see that any subgroup of size 4 can be formed from the subgroups in Figure 9.
Conclusions
Another no less dangerous source of electromagnetic emission, formidable from the point of view of the possibility of conducting electromagnetic "clock", are computer laser printers [15, 16]. Such emissions are called "sensitive" or "valuable" or "compromising" emanations from the point of view of electromagnetic protection of processed information.
TEMPEST fonts 1 Introduction
- Symmetrical safe font
- Asymmetrical safe font
- Simply safe font
At the same time, the correct proportions of the width of the lines and the clearance of each character of the font are preserved. At the same time, the correct proportions of the width of the lines and the clearance of each character of the font are preserved.
Sensitive emissions and possibilities of reconstruction of primary information
- Introduction
- VGA standard
- DVI standard
Adequate tests were conducted to demonstrate the effectiveness of tempest fonts in protecting information from the intrusion process of electromagnetic radiation. The video signal of the VGA standard has a characteristic structure that allows distinguishing unique signatures that enable its identification, both in the time and frequency domains.
Conclusions
The mobile device used the location information consisting of Cell Identifier, Location Area Code (LAC), Mobile Network Code (MNC) and Mobile Country Code (MCC). The contributions of this chapter can be summarized as follows: we use location information for a mobile device that is always available in the cellular network.
Structural GSM/UMTS architecture
The location information collected while the mobile device is roaming between base stations connects them and the location information allows us to track the mobile device to see the historical location; the application can be used anywhere in the world covered by the GSM mobile network/. UMTS vs. location information with location APIs to provide mobile device location.
GSM/UMTS-based localization
Cell ID (ID) in combination with the MCC, the LAC and the MNC is the unique identifier of the BTS. The cell ID of the BTS has the association with certain mobile station (MS), which is known by the mobile device and can be used to evaluate the position of the mobile device [8].
Android platform
Web service
Tracking system
In this section, we propose a tracking system algorithm to develop models of the relationship between the mobile application and the server location. Note IMEI, SSN and current date and time can be retrieved from the mobile device.
Results
When a mobile phone connected to the Internet can retrieve location information from the mobile device's SQLite database, the location information is transferred to the remote server during synchronization between SQLite and MySQL. The data (latitude and longitude) is then transferred to the mobile device in the form of the JSON format and Google Maps is used which will plot the locations.
Conclusion
The application showed a low-cost tracking system using GSM/UMTS network, which is suitable for working all over the world with the combination of the Android mobile phone and web services. We demonstrated tracking using low cost hardware with open source projects and showed mapping techniques with cell tower databases to take advantage of tracking a mobile device.
Introduction to cognitive radio
In advanced wireless communication systems, an intelligence of cognitive radio helps to become aware of the environment and internal state and can adjust itself for better performance. Software-defined radio (SDR) and artificial intelligence (AI) technology enable the field of cognitive radio.
Benefits of cognitive radio
The baseband section of a communication system can be implemented by software, which is a unique platform provided by cognitive radio. Signal transmission and reception between cognitive radio mainly depends on channel and power, and they will change dynamically to improve spectrum efficiency and This process is defined as dynamic spectrum management.
Software defined radio (SDR)
- SDR overview
- Functions of SDR transmitter and receiver
- Architecture of SDR
- Introduction to complex signals
- GNU radio
The hardware aspects of a platform consist of radio frequency (RF) elements, some baseband signal processing, and communication links to the software-based signal processing element—perhaps a DSP, FPGA, or a general-purpose processor ( GPP) (Figure 3). As the quadrature signal is added, when I and φ vary identically, the amplitude of the sum changes (Figure 8).
Signal processing blocks in GNU radio
- Analog modulation techniques .1 Amplitude modulation (AM)
- Digital modulation techniques .1 ASK modulation
All the following blocks in the flowchart can wait for the production sample rate. Figure 27 and 28 shows the GRC flow chart of the transmitter which is described as follows.
Background and introduction
In bit duration detection, the bit stream is self-clocking and the timing differential varies with respect to the exact timing of the bits in TRL. In bit duration detection, the binary bit stream is self-clocking and the timing differential varies with respect to the exact timing of the bits in TRL.
Related works
- Performance modeling of PLL using random walk theory
- Cramér–Rao bound (CRB)
- Square-TRL using digital RWF
- Advanced TRL using RWF
Application of the Random Walk Model for Timing Recovery in Modern Mobile SATCOM Systems DOI: http://dx.doi.org/10.5772/intechopen.90606. This independent homogeneous finite aperiodic Markov chain is shown in Figure 3. The above Markov chain is referred to as a "random walk" with the transition probabilities q and p defined in Eq. 1) and (2), respectively, and in terms of signal and noise parameters as shown in Eq.
Mathematical modeling of timing jitter using random walk process The Wiener process was introduced as a mathematical model of Brownian
- Mathematical modeling of random time walk
- Cramér–Rao bound (CRB) for timing jitter
In Figure 9, the steady state CRB and the performance of the trained PLL are plotted for the following system parameters: σTε¼0:5%, block length N = 500, and the PLL performance is averaged over 1000 trials [8]. As seen in the figure, the performance of the PLL is a strong function of the gain parameter α, and thus it must be optimized for each SNR.
Timing recovery using RWF
- RWF concept for timing recovery
- Software implementation of RWF TRL
- Performance of RWF TRL
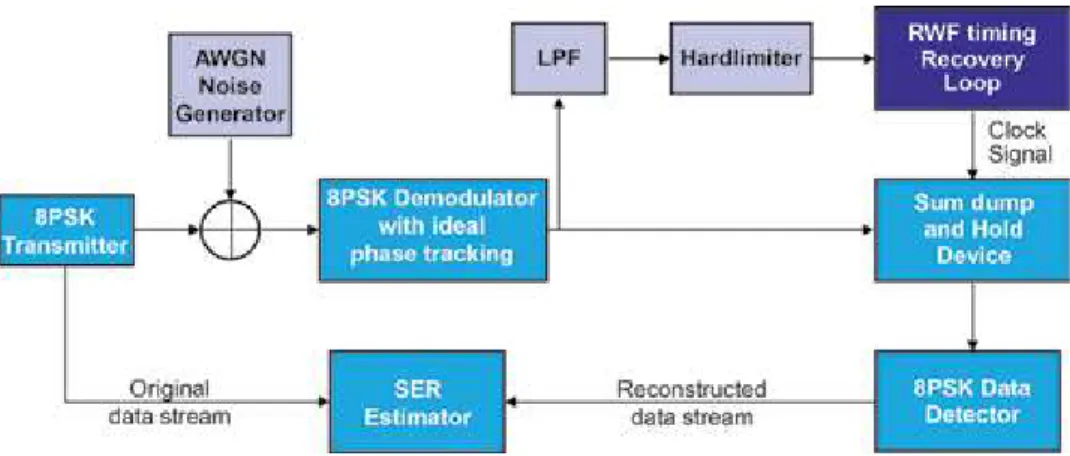
Converts the input baseband digital signal waveform to data transition pulses delayed by half the search window size, W. The Signal Processing Work (SPW) implementation of the proposed RWF TRL for 8-PSK modem is described in Figure 13.
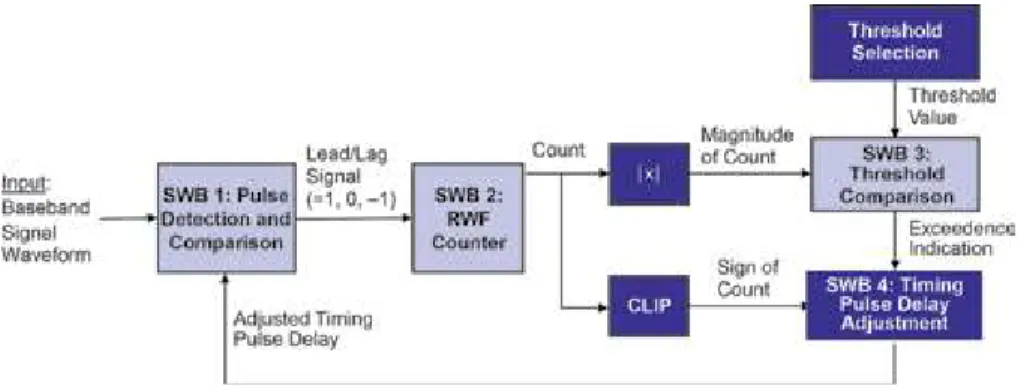
Discussion and conclusion
Elaborating on the direction, in this chapter we review the worldwide progress of RoF-architected 5G NR access networks and highlight our recent simulation results on photonic millimeter-based FiWi interface design and optimization. Elaborating on the direction, in this chapter we review the worldwide progress of RoF architecture 5G NR access networks and highlight our recent simulation results on photonics-based FiWi interface design and optimization.
The distinctive features of access networks for 5G NR mobile communication systems
- Small cell scenario
- Radio-over-fiber concept
- Example of a 5G NR network using small cell scenario and RoF concept Let us illustrate small cell scenario using an example of building a backhaul
- Microwave-photonic-based approach .1 The area of microwave photonics
One of the most important examples of the introduction of radically new approaches is the upcoming 5G NR mobile network. Comparison of key parameters achieved in 4G LTE mobile networks with similar parameters to be achieved in 5G NR networks.
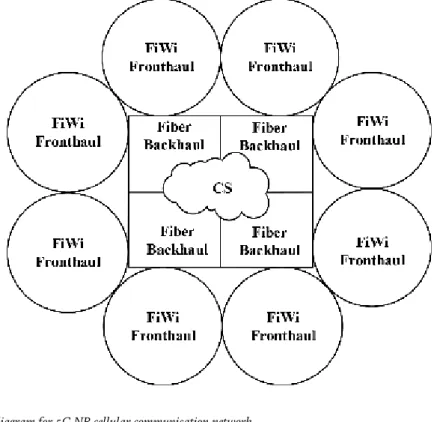
Design principles of fiber-wireless fronthaul network
- Design of optical distribution network
- Proposed models and setups for simulation experiments .1 Direct intensity modulation
- Simulation results
- Design of fiber-to-MMW-band wireless interface
- Studying an optimal signal transmitting RoF-based fiber-to-MMW-band wireless interface
The simulation results for the fiber-wireless front-haul link of the 5G NR system under study are summarized in Table 6. The result, which is a dependence of EVM versus fiber length, is shown in Figure 21.
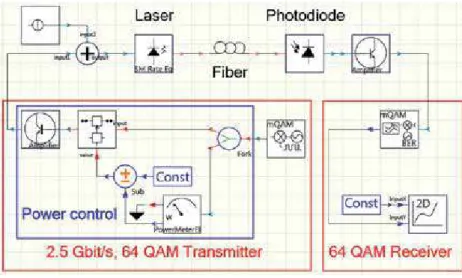
Conclusion
Proceedings of the Seventh International Conference on Advances in Computing, Communication and Information Technology—CCIT; 27–28 October 2018. Proceedings of the Eighth International Conference on Advances in Computing, Communication and Information Technology—CCIT, 23–24 April 2019, Birmingham, UK.
Implementation and methods
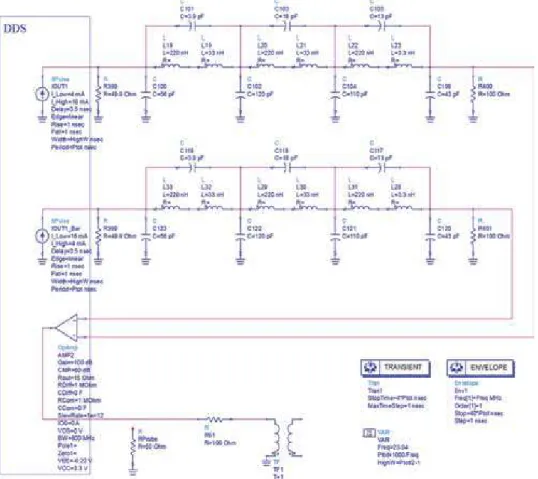
- Prototyping with Altera FPGA and MATLAB Simulink
- Reconstruction filter design and simulation
- Using AD9852A complete DDS as clock source
- Characterization and qualification test profile
Once the minimum order is defined, the design of the passive LPF can be done as shown in Figure 4. The output strength of the current DACs can be controlled by the design through an external resistor.
Result and analysis
- Software simulation
- Hardware implementation
- Comparative result analysis
The reason for this loss may be the bandwidth of the comparator itself. The on-chip activities of any modern IC are always disabled by the appearance of power supply noise (PSN) in the chip's power line.
State of art for the on-chip power supply noise problem
It should be noted that the critical path delay of the logic circuits inside the IC chip is inversely proportional to the supply voltage flow rate [3]. This current pumping occurs through the PDN inside the chip and causes a voltage drop in the circuit's electrical lines due to the presence of inductive, capacitive and resistive elements in the IC chip's power distribution network.
Discussion on the power delivery network for the chip
In ad-hoc style, the local circuit blocks are connected to the I/O pads (at the outer boundaries) using custom power/ground lines, as shown in Figure 4(a). This makes the power level insensitive to the current preconditions of the various circuit blocks.
Methodologies to suppress on-chip power supply noise
- Circuital approaches
- Non-circuital approaches
So, in recent days, the lattice-like structure of PDN design is pursued for all types of on-chip architectures. So, in most ideal cases, it is observed that the actual on-chip transient times are around 10%.
Challenges faced in suppressing on-chip power supply noise
The impact of PSN over on-chip circuits is suppressed by using different reduction and isolation techniques. In the earlier sections, there were discussions about problems claimed by PSN for the proper functioning of on-chip circuits within the modern ICs.
Probable solution to reduce the on-chip power supply noise
In fact, the reactance of these on-chip decaps is so high during low-frequency operation of the chip that as soon as the supply voltage fluctuates, it adversely affects the operation of the chip. The frequency scale directly affects the switching activity of the circuit nodes on the chip.
Conclusion
- Classification of video streaming
In the case of the circuit approach, it has been pointed out that by manipulating the on-chip clock activity, the most important factors of PSN (i.e. i(t) and di/dt) can be controlled. Some of the platforms that provide multimedia content over the Internet are YouTube [1], Net TV [2], and IPTV [3], etc.