Shutting down unused servers and switches can reduce overall infrastructure energy. There is also latency due to the virtualization technique used, which depends on server load and other configurations (eg CPU cache misses).
4 Integrating SDN into the Optimal Deployment of DSP Applications
- The SIDF Architecture
- DSP Deployment Problem
- Illustrative Example
- Related Work on Big Data and SDN
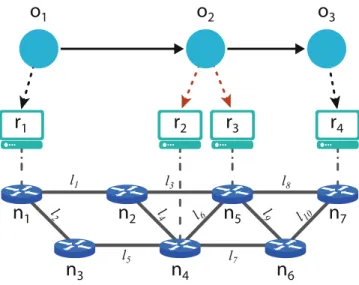
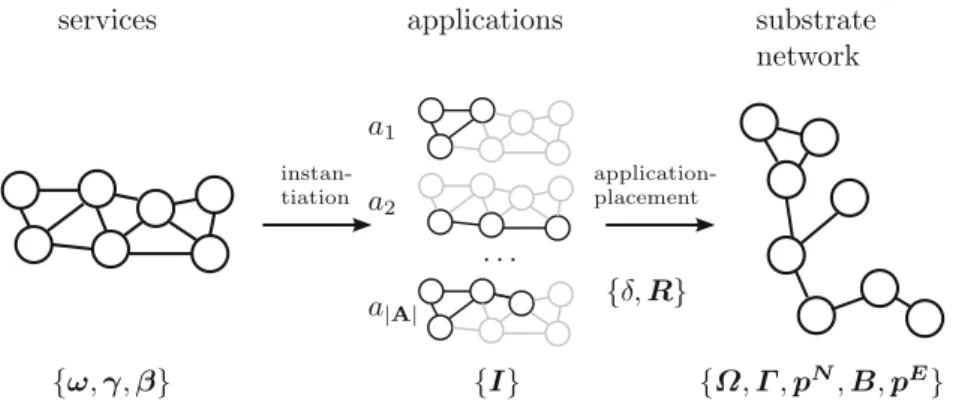
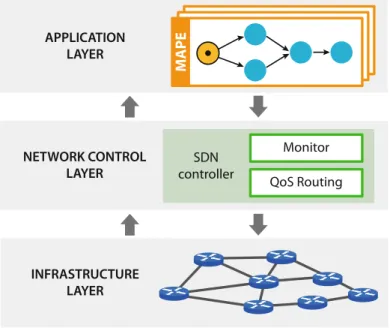
In this setting, an optimal deployment algorithm determines not only the application components' placement on the underlying infrastructure, but also the network paths between them. The network control layer manages the heterogeneity of network devices and controls their working conditions.
5 Context-Aware Composition of Big Services
- Software-Defined Service Composition (SDSC)
- Componentizing Data-Centric Big Services on the Internet Workflows of mission-critical applications consist of redundancy in links and
- Illustrative Example
- eScience Workflows as Service Compositions
- Inter-domain SDN Deployments
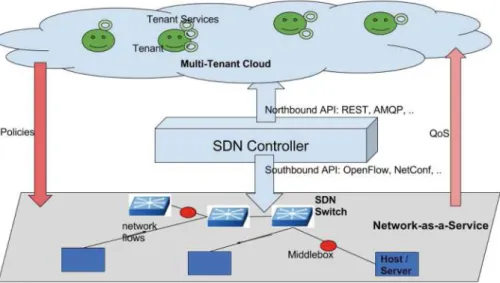
Many aspects, such as the location of the operating cloud data center and policies, need to be considered for the efficient execution of the service workflow. The workflow represents multiple possible execution paths when the service composition is decomposed or composed into services (Services 1, 2, ., n).
6 Benefits and Open Issues
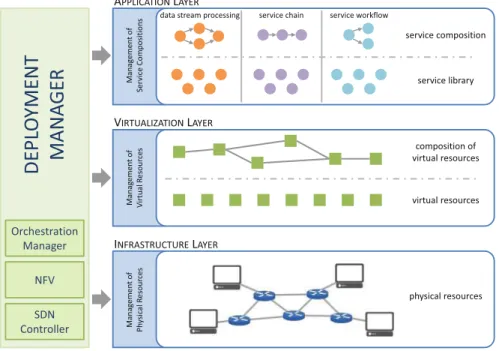
New service development formalisms may be required to standardize processes at the network management level. So, a significant increase in network usage is expected with a number of new and innovative services.
7 Conclusions
Në: Proceedings of 10th International ACM Conference on Distributed and Event-Based Systems, DEBS 2016, pp. In: Proceedings of 3rd IEEE Workshop on Hot Topics in Web Systems and Technologies, HotWeb 2015, pp.
Services Management
1 Introduction
Under these circumstances, it is necessary to find a compromise solution that optimizes the antagonistic criteria in the most efficient way. Therefore, the resource allocation problem becomes a multi-criteria optimization problem, and the importance of each criterion becomes extremely important.
2 Dealing with Multi-criteria Optimization: Frameworks and Optimization Tools
- Generic Definition of the Problem
- Incorporating Multiple Criteria in General Optimization Methods
- Complexity of Defining Multi-criteria Utility Functions to be Incorporated in Network/Management Mechanisms
- Multi-criteria Problems Solving Mechanisms
- Fairness Consideration
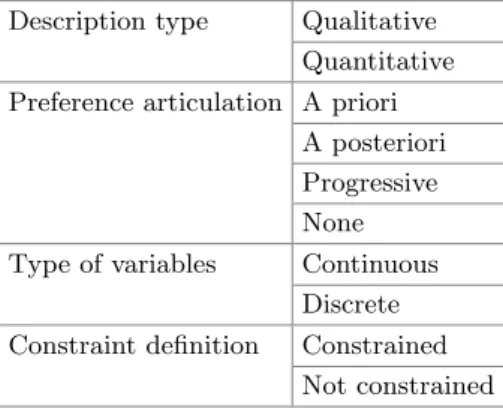
In this section, we present a comprehensive taxonomy of the optimization problem synthesized from the works. This means that the optimality of the resource allocation is measured for a static combination of flows.
3 Cost/Energy/*-Aware Network and Cloud Services Management Scenarios
- Modeling and Analysis of Performance-Energy Trade-Off in Data Centers
- Characterization and Energy-Efficiency of Applications in Cloud Computing
- Energy-Aware Load Balancing in 5G HetNets
- Incorporating Energy and Cost to Opportunistic QoE-Aware Scheduling
However, depending on the level of congestion at the small cell, it may be better from a system point of view to use the resources of the macro cell instead. They also typically operate on a different frequency than the macro cell and thus do not interfere with the macro cell's transmissions.
4 Current Technologies and Solutions
Industry Efforts for Integrating Energy Consumption in Network Controlling Mechanisms
Given the significance of work and pay in Whittle-related models, such an extension might require the modification of the structure of the problem itself (i.e. alternative MDP) or only consider different criteria in the work/pay assignments. However, there is a potential for significant reductions in energy consumption because the networks are sized above current demand and even when there is little traffic on the network, the power used is very important and most of it is wasted [34].
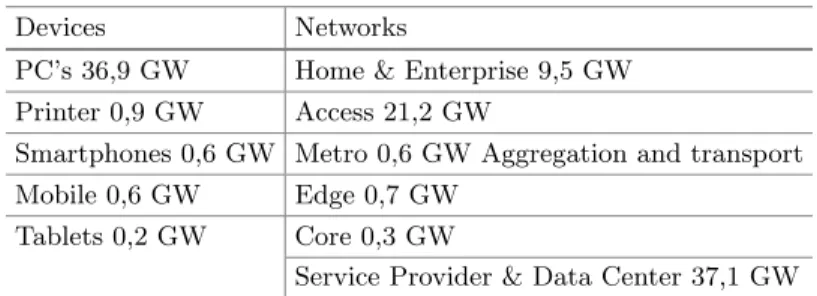
C-RAN: Access Network Architecture of Future 5G Networks Cloud computing represents a paradigm shift in the evolution of ICT and has
GeSI facilitates real world solutions to real world issues within the ICT industry and the wider sustainability community. Several projects based on the C-RAN architecture have been initiated in the Next Generation Mobile Networks (NGMN) consortium and EU FP7 [10], and the C-RAN architecture will most likely also be considered in the standardization by 3GPP.
A Framework for Energy-Aware Network Management Systems Considering the problem modeling and the existing optimization frameworks
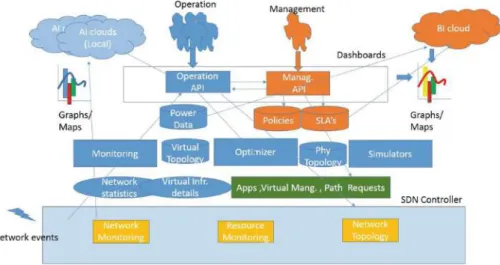
At the top are the two agents responsible for network management: On the one hand, those responsible for negotiating SLAs with customers and setting operating policies. The Intelligent Business Cloud helps the Management API generate dashboards for optimizing the results of business operations, issuing recommendations to managers or autonomously implementing decisions.
5 Conclusions and Foreseen Future Research Lines
Conclusions
The next step is to model and analyze the problem of incorporating the performance/energy trade offer in different scenarios in the scope of the ACROSS project. The growing complexity of cloud service management and orchestration requires advanced network control methods and algorithms.
Future Work
Hyytia, E., Righter, R., Aalto, S.: Energy conscious task allocation in server farms with setup delays under LCFS and PS. Taboada, I., Aalto, S., Lassila, P., Liberal, F.: Delay and power-aware load balancing in ultra-dense heterogeneous 5G networks.
2 Cloud Federation Architectures
Cloud Architectural Views
Public Clouds offer their services to users outside the company and may use cloud functionality from other providers. They only offer interoperability solutions for the low-level functionality of the clouds, which are not focused on the latest user requirements, but on solutions for IaaS system operators.
Standardization for Cloud Federation
In 2014, the ITU released standard documents on the vocabulary, a reference architecture, and a framework for intercloud computing. For each service, the intercloud federation can act as an intercloud intermediary with a primary CSP responsible for the service.
3 Multi-level Model for Traffic Management in Cloud Federation
Level 5: Strategy for Cloud Resource Distribution in Federation .1 Motivation and State of the Art
- Proposed Model
- Exemplary Results
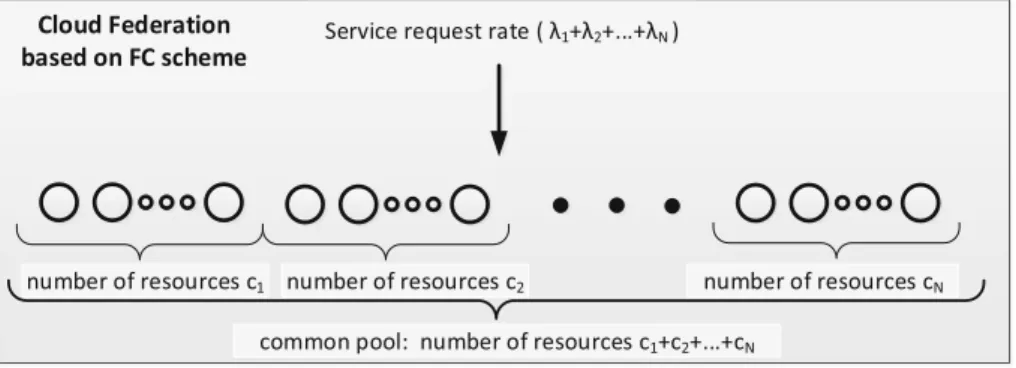
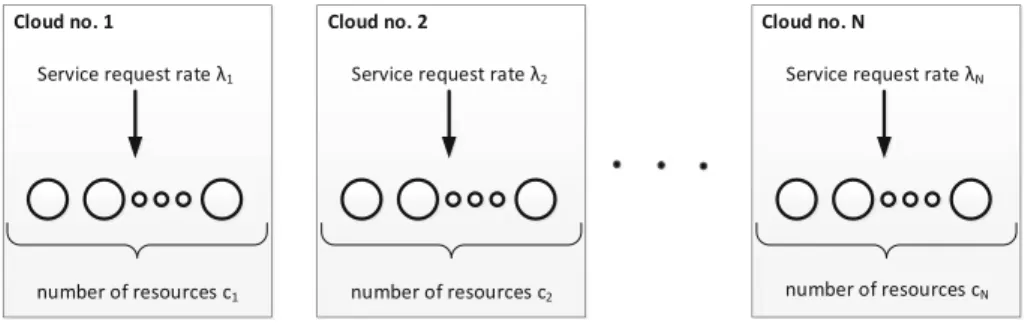
In the proposed approach, we assume that the capacity of each cloud is characterized in terms of the number of resources and service request rate. 3 (see Fig.5): for this scheme, we assume that each cloud can only delegate part of its resources to CF as well as part of service requests coming from its clients.
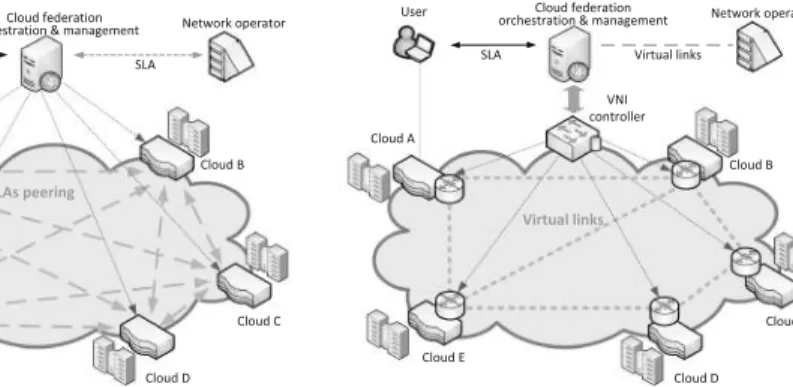
Level 4: Network for Cloud Federation .1 Motivation and State of the Art
- Proposed Solution
- Performance Evaluation
The VNI control algorithm is invoked when a flow request comes from the CF orchestration process. Assign flow in VNI. In this step, the algorithm allocates flows in previously selected subset of feasible paths.
Level 3: Service Provision
The total availability is then the probability that at least one of the VMs is available. In the next section, we present an integer linear programming (ILP) formulation of the problem.
Level 2: Service Composition and Orchestration
- Background and Motivation
- Literature and Related Work
- Composition and Orchestration Model
- Real Time QoS Control
The response time of each concrete service provider CS(i,j) is represented by the random variable D(i,j). For each used concrete service, the response time distribution is updated with the new realization.

Level 1: Resource Management in Virtualized Infrastructure Level 1 deals with the dependencies of different physical resources, such as Cen-
- Methodology
- Results
- New Findings
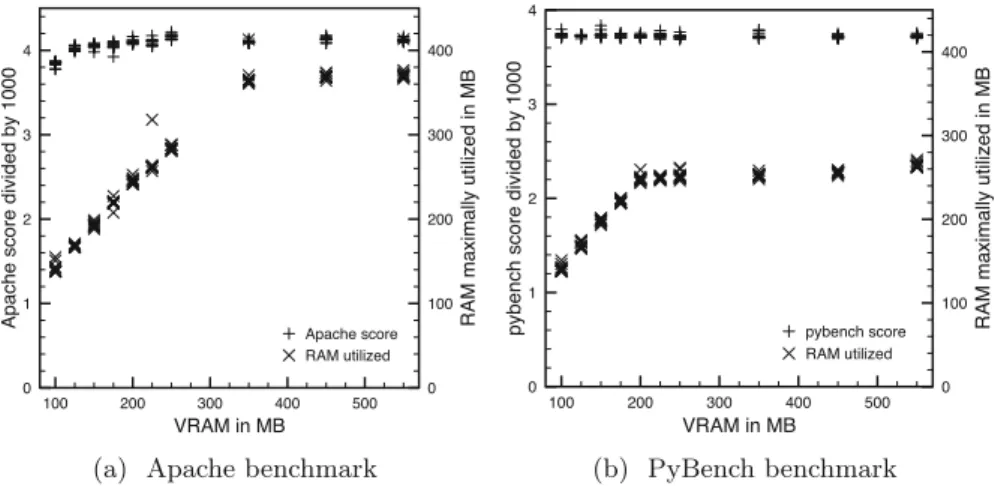
Figure 12a shows that when the VM runs Apache, it never uses more than 390 MB of RAM. Figure 12b shows that when the VM runs PyBench, the VM process uses up to 270 MB of RAM.
4 Cloud Federation for IoT
State-of-the-Art in IoT Cloud Research
Since these devices can discover each other over local wireless connections, they can be combined to provide higher-level capabilities. Finally, resource conservation scenarios, where great improvements can be made in the monitoring and optimization of resources such as electricity and water.
MobIoTSim for Simulating IoT Devices
The default Bluemix IoT service type can be used if the user has a registered account for the Bluemix platform and has already created an IoT service. These devices can be started and stopped by the user at will, both together or separately for the selected.
5 Summary
In: Proceedings of the 3rd International Conference on Cloud Computing (CLOUD 2010), Miami, Florida, VS, pp. Proceedings of the Fourth International Conference on Internet and Web Applications and Services, pp.
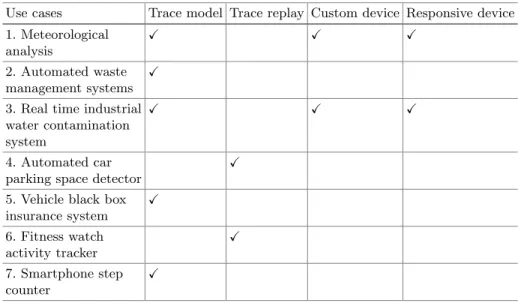
Cloud Use Cases
This requires a lot of specialized code (such as sensor behavior and network infrastructure) to be implemented on top of the chosen simulator, which can be time consuming and may need to be changed frequently as situations change. This limits the application of simulators as it requires programming skills, a lot of time and a strong understanding of the API.
2 Related Work
They argue that system designers and operations managers face numerous challenges to realize IoT cloud systems in practice, due to the complexity and diversity of their requirements in terms of IoT resource consumption, customization, and time governance. of operation. We generally share these views in this work and build on these results specifying our contribution to the field of IoT cloud simulations.
3 General IoT Extension for Cloud Simulators
This mechanism introduces an important behavioral model through which the sensors produce data that can trigger events that indirectly change the behavior of the sensors via a feedback loop. Due to the above reasons, it would be required that a wide range of traces be collected to obtain a large enough sample size of different behavioral models to perform an accurate simulation of the system (which can be scaled up/down as required) .
4 Implementing the Extension for a Meteorological Application
Implementation with the Generic IoT Oriented Extensions The weather station’s caching behaviour is a prime example for the need of respon-
Since the sensors produce data independently of each other, and they can have varying frequencies and data sizes, the station must cache all produced data before sending it to the cloud for processing. At each check call, our custom device determines whether or not there is a need to send its buffered content to the cloud.

Evaluation with Alternative Application Level Scenarios
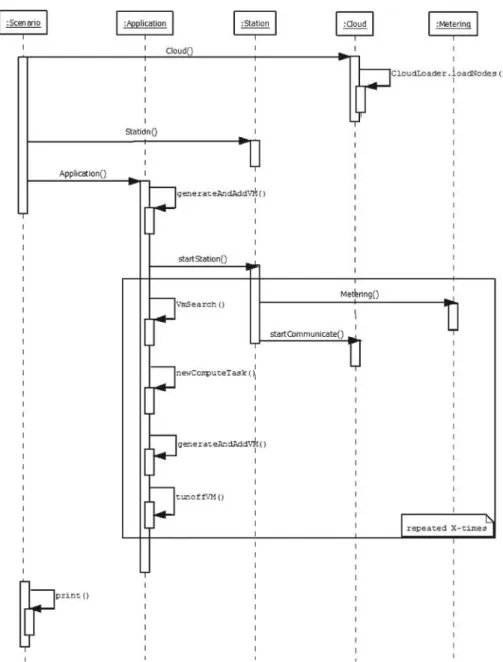
If at the end of the task allocation phase there are still VMs available, they are all decommissioned (byturnoffVM()) except the last one (which allows the next rounds to start with an already available VM). 7. Sequence diagram of the weather station modeling use case and its relationships to our DISSECT-CF extensions.
Evaluation
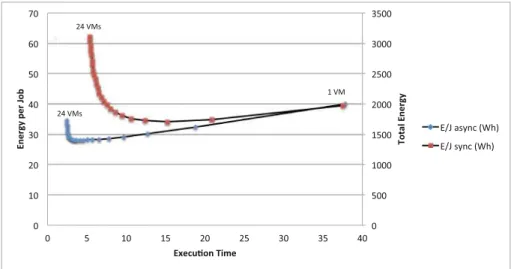
In Fig.11b we can read the number of VMs required for processing the tasks in the real case. We can see that without shutting down the unused VMs from 18:00, we kept more than 20 VMs alive (resulting in more overprovisioning), while in the other case the number of running VMs dynamically changed to the one that required by the number of tasks to be processed.
5 Implementing the Extension for a Fitness Application
Trace Collection
Initially, we aimed to collect all the network traffic between the three devices using a packet analysis software (such as Wireshark) on a laptop that acted as a wireless hotspot for the smartphone. Additionally, we would have lost the ability to track the Bluetooth traffic between the watch and the smartphone.
Implementation and IoT Extensions to DISSECT-CF
In the second XML, device models can be associated with each of the previously loaded machines. Finally, the extension provides alternative packet routing models as well in the form of several implementations for the connection event interface.

Evaluation
6 Conclusion
In: 2013 IEEE 9th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), p. Images or other third-party material in this chapter are covered by the chapter's Creative Commons license unless otherwise noted in the credit line for the material.
Reliable Internet of Services
Although all the scenarios are related to the security of IoT, the last two scenarios have direct connections. Section 6 consists of studies that analyze the effects of D/DoS attacks for IoT networks.
2 Related Works
Their work considered the limitations of IoT environments that affect security and privacy. In this study, we aimed to provide a comprehensive view on IoT security for reliable IoS.
3 Internet of Things
Internet of Things Architecture
5] proposed a literature review on the security of IoT where history of IoT security, taxonomy of security challenges and requirements, cryptography-based defense mechanisms and IDSs were evaluated. Although there are some topics of interest and viewpoints in common with the previous reviews, our work tries to portray a more complete picture of security of IoT.
Application Layer
Processing Layer
IoT – Internet Connection Layer
IoT Access Network Layer
Perception Layer
Business Layer
Standardized Protocol Stack for Low Power and Lossy Networks
37] proposed a protocol stack for low-power and low-loss IoT networks that uses protocols/standards proposed by IEEE and IETF. This standard promises energy-efficient PHY and MAC operations for low-power and low-loss networks, and is also used by Thread and ZigBee technologies.
CoAP UDP
Therefore, it may not be a good candidate for IoT applications based on low-power and low-loss networks, where most devices will be battery-powered devices with small form factors and reasonable costs. However, when IPv6 was proposed, low power and lossy networks were not considered, leading to an incompatible packet size problem.
6LoWPAN IEEE 802.15.4
RPL [56] was proposed by the IETF as IPv6 routing protocol for low-power and lossless networks. The standardized protocol stack for low-power and lossless networks uses the Constrained Application Protocol (CoAP) [50] for the application layer.
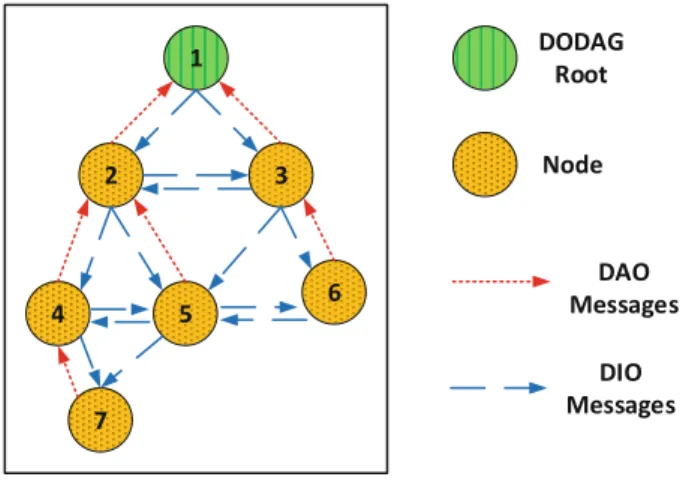
4 Internet of Things Security
Cryptography-Based Security Solutions for Low Power and Lossy Networks
Nodes are expected to follow the rules of the RPL specification to create loop-free and efficient RPL DODAGs. To optimize the data carried by CoAP messages, the IETF proposed another standard for the binary representation of the structured data called Concise Binary Object Representation (CBOR) [12] on top of CoAP.
Which Security Solution to Use?
If the routing path has a malicious node, then the security of messages routed through this path cannot be guaranteed. So, routing security becomes vulnerable to attacks such as DoS and DDoS attacks.
We Have Cryptography-Based Solutions, Are We All Set?
Designers don't have to worry about the reliability of other nodes, devices or networks along the way. We know that most people are not aware of security and that the usability of security mechanisms has problems [47].
5 Denial of Service Attacks Targeting Internet of Things Networks
- D/DoS Attacks to the Physical Layer
- D/DoS Attacks to the MAC Layer
- D/DoS Attacks to the 6LoWPAN Layer
- D/DoS Attacks to the Network Layer
- D/DoS Attacks to the Transport and Application Layer
D/DoS attacks that can target RPL networks exploit vulnerabilities in the design of the RPL protocol. If an attacker uses a high-power radio, he can affect a large part of the network in this way.
6 Studies that Analyze D/DoS Attacks for Internet of Things
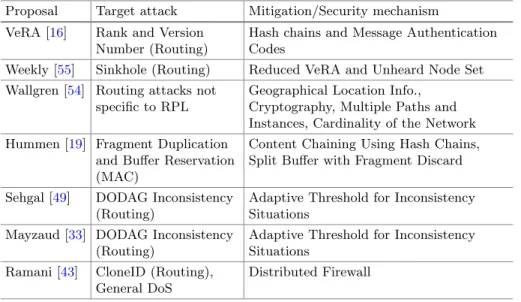
In addition, three of the studies found correlations with attack success and attack settings. In Table 1, we had provided a categorization of the D/DoS attacks for IoT and it is clear that many attacks have not been implemented and analyzed in a similar way.
7 Mitigation Systems and Protocol Security Solutions for Internet of Things
This proposal changes the fixed RPL threshold to a flexible threshold to better mitigate the effects of the attack. Geographic location information, cryptography, multiple paths and instances, network cardinality Hummen [19] Fragment duplication.
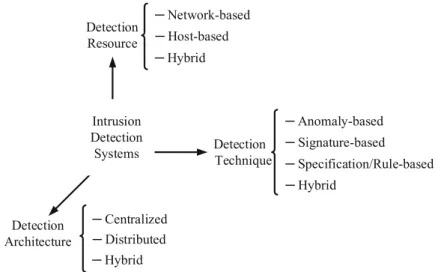
8 Intrusion Detection Systems for Internet of Things
Intrusion Detection Systems
Intrusion Detection Systems can be divided into three categories in terms of the resources they use for detection. One of the main reasons for choosing a central intrusion detection point can be the resources available.
Intrusion Detection Systems Proposed for Internet of Things Cho et al. [15] proposed a botnet detection mechanism for 6LoWPAN-based
Regarding the detection sources used, we can classify SVELTE into network-based IDSs. Regarding the detection source, we can consider this study as a network-based IDS.

9 Discussion and Open Issues
Most studies only focus on a small number of attacks, as reported in another study [60]. Another problem with IoT security research is related to the reproducibility and comparability of the studies.
10 Conclusion
Evans, D.: Internet stvari, kako naslednja evolucija interneta spreminja vse (2011). V: Proceedings of the 2011 International Conference on Internet of Things and 4th International Conference on Cyber, Physical and Social Computing, ITHINGSCPSCOM 2011, pp.
Access: A Comprehensive Analysis
None of these live measurements took into account the effect of speed in the execution of TCP or the behavior of different types of CCAs. There are only a few works that have considered the impact of different speeds on the performance of TCP over LTE networks.
3 Research Environment
TCP Variants
Hybrid Slow-Start focuses on finding the right starting point for standard Slow-Start to avoid massive packet losses. TCP Westwood+ was selected in this study for its hybrid behavior utilizing loss-based mechanisms in combination with delay awareness. v) TCP Illinois [21] controls the AIMD mechanism by estimated queue delay and buffer size.
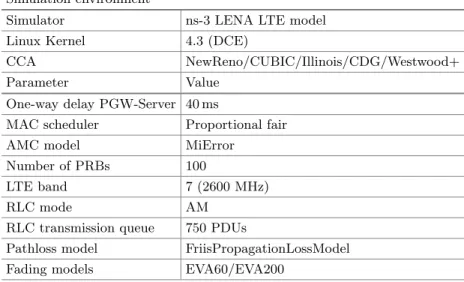
LTE Setup
With timeouts, thesthresh is calculated according to ratings, and thecwnd is set to 1 segment. To simulate the distance to the server, the propagation delay between the fixed remote host and the packet data gateway (PGW) was set to 40 ms.
4 Methodology Description
On the other hand, the increasing movement of the quality represents the behavior of TCP to continuously improve the quality of the channel (point IV in Figure 1). To better understand the evolution of various performance-related parameters, cwnd, RTT, outstanding data and goodput were collected in the server.
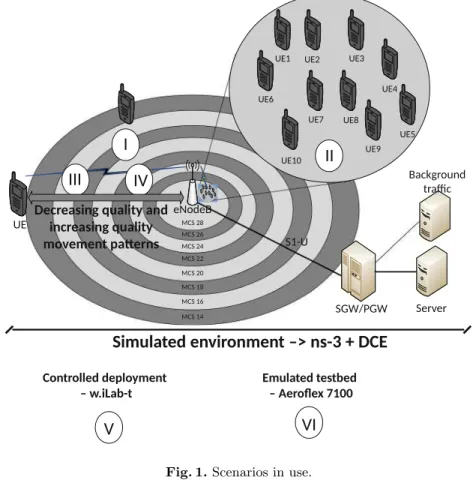
5 Analysis of the Interactions Observed in Different Scenarios
Cross-Traffic Impact and Responsiveness of TCP
In fig. 4, the size of the flows and the number of induced droplets are correlated. Good performance without the influence of Hybrid Slow-Start due to the low available capacity at the start of the transmission.

Start-Up Performance
6.Hybrid Slow-Start Impact in Mobile Networks: Packets injected during a standard Slow-Start period. So under certain conditions of delay variability, Hybrid Slow-Start delays TCP startup.
Mobility Performance
Figure 8 shows the difference in behavior between CUBIC with Hybrid Slow-Start and NewReno with Standard Slow-Start. Slow-Start are completely different, leading to better utilization of network resources in the case of Standard Slow-Start.

Correlation of TCP Behavior over w-iLab.t LTE Testbed
The performance difference with Standard Slow-Start (present in NewReno and Illinois) can be attenuated if the transmission is long enough (the average value of CUBIC is close to NewReno or Illinois in 20 s transmission). Therefore, to better understand the performance yield of CUBIC, NewReno and Illinois in the congestion avoidance phase under mobility conditions, a further analysis was required.
Performance Tradeoff of Selected TCP Variants Under Mobility in Emulated Testbed
However, it has shown good lag control, keeping it close to baseline lag. However, the protocol's delay limits can be very well adapted to the limitations of mobile networks.