A mobile ad hoc network is a collection of completely mobile nodes that can establish communication in the absence of any fixed infrastructure. In this thesis, we propose two classes of routing schemes for mobile ad hoc networks.
Introduction
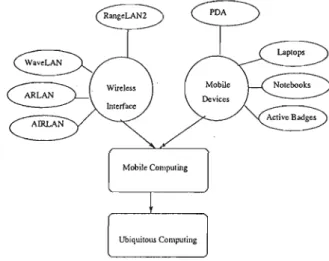
- Mobile Computing and Networking
- Mobile Ad hoc Networking and the Routing Prob- lem
- Research Overview and Contributions
- Organisation of the Thesis
One of the main challenges in mobile ad hoc networks is the routing of packets to mobile nodes. A brief discussion of recently proposed routing protocols for mobile ad hoc networks is presented here.
Mobile N etworlcs
- Mobile Computing Environment
- Infrastructure-based Mobile Networks
- Infrastructureless Mobile Networks
- Challenges and Tasks in Mobile Networks
- Mobility and the Internet
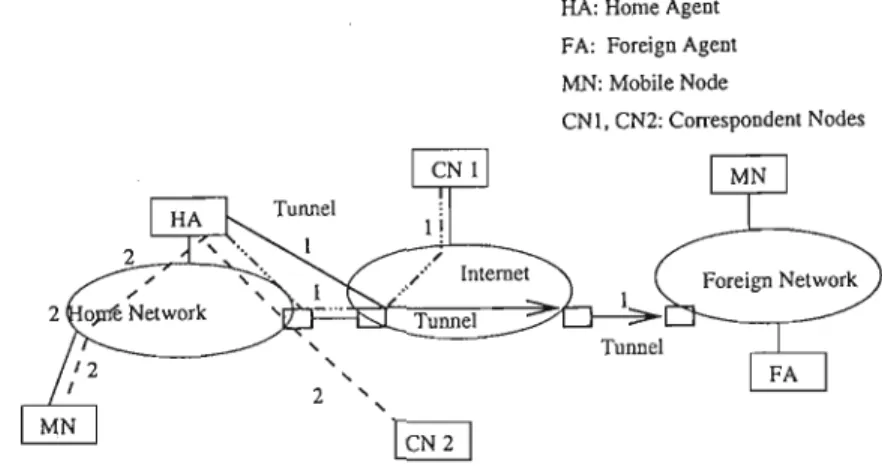
- Mobile IP
The other aspect of mobility management is routing location data to the mobile node. The home agent encapsulates the packet and sends it to the mobile node's care.
Mobile Ad hoc Networks
Description of Mobile Ad hoc Networks
The MANET working group uses the term mobile ad hoc networks and we have used this name in this thesis. The architecture of mobile ad hoc networks is a hybrid of traditional packet radio networks and cellular networks.
Applications of Mobile Ad hoc Networks
The design of unicast routing protocols is one of the main challenging topics in mobile ad hoc networks. A new media access control protocol called Dual Busy Tone Multiple Access [DBTMA] [Jin9S] has recently been proposed for mobile ad hoc networks.
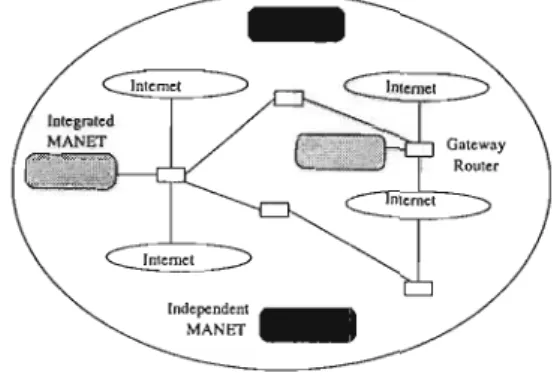
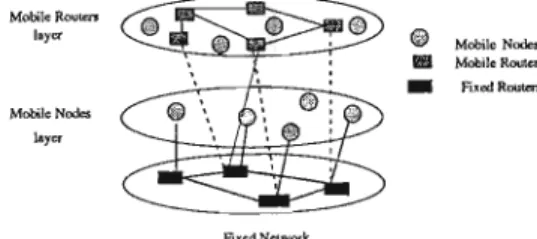
Mobile Ad hoc Networks and the Internet
Also, like ad hoc networks, the mobile router layer does not gain support from the fixed network and operates independently. In view of the future mobile Internet layer architecture, the MANET working group is developing routing standards for the mobile router layer.
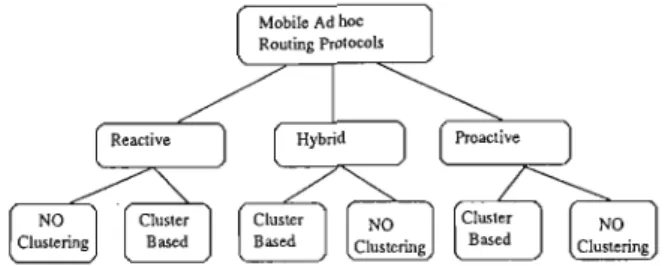
Routing Problems in Networks
Routing in 'fraditional Static Networks
In static routing protocols, communication paths are fixed regardless of network state changes. Adaptive routing protocols adapt to the dynamic nature of the network, such as changes in network topology, link quality, and traffic conditions.
Routing in Mobile Ad hoc Networks
It responds to the source with a reply packet that copies the route from the query packet. Each packet arriving at the destination will contain the association stability of the nodes along the route from the source to the destination.
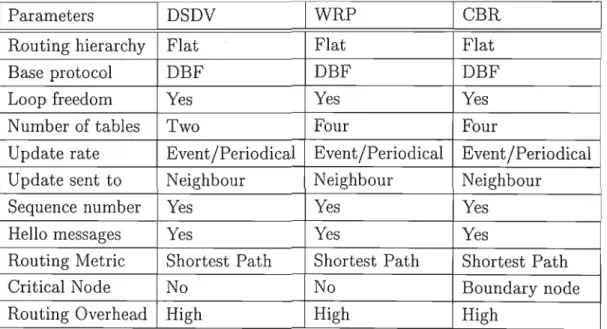
I CBRIDSDVIWRP
I DSR I ABRIAODV
Moreover, a cluster architecture with a cluster head can also help in efficient tracking of mobile nodes. By using appropriate intercluster and intracluster routing mechanisms, the clustering architecture can reduce the routing overhead in mobile ad hoc networks.
Limited Flooding for Mobile Ad hoc Networks
Flooding
Sequence numbers can be used to control flooding traffic as well as to validate updated information in existing routing protocols. Thus, sequence numbers guarantee that each packet is transmitted to its neighbors at most once by each intermediate node.
Description of Limited Flooding Protocols
For relatively highly mobile environments, the limited flooding protocol for infrequently communicating nodes is expected to provide better performance than periodic or event-driven updates of link state information in link state based protocols. Also, for link-state-based protocols, link-state packets are transmitted throughout the network through pure flooding every time the link state is updated, whereas in limited flooding, it is only transmitted along a few selected paths. Common to all the limited flooding protocols are: First, routing calculation or maintenance is not required.
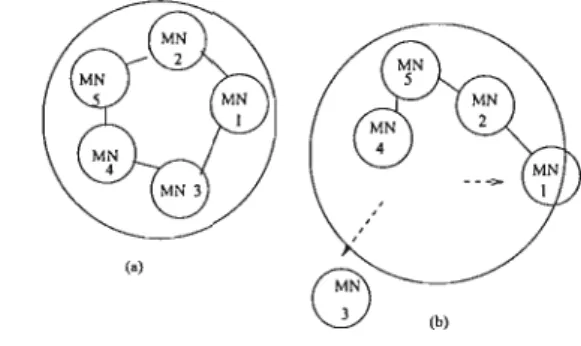
In this protocol, a proportion of outgoing links is selected at each intermediate node based on the degree of the node. So there are six variations: Randomized Limited Flooding with Randomized Paths (RLF-R), Randomized Limited Flooding with Probable Paths (RLF-L), Deterministic Limited Flooding with Randomized Paths (DLF-R), Deterministic Limited Flooding with Probable Paths (DLF -L), Priority Limited Flooding with Randomized Paths (PLF-R) and Priority Limited Flooding with Probabilistic Paths (PLF-L). Limited Flooding Protocol (LFP) is suitable for relatively highly mobile network environments with a random network characterized by relatively low communication traffic.
Related Protocols
It uses sequence numbers but does not require the use of reliable or sequential packet delivery. This protocol switches to the pure flooding algorithm when the rate of mobility is high. Since the mobility rate is not uniform across all the hosts, the protocol adapts to the situations encountered at each node.
Simulation Environment for Limited Flooding
An Overview of the Simulation Environment
The packet is stored in the buffer until the sender is ready to send or the receiver is ready to receive. There is a separate up-link and down-link channel so that a node can receive and transmit at the same time.
The Simulation Language
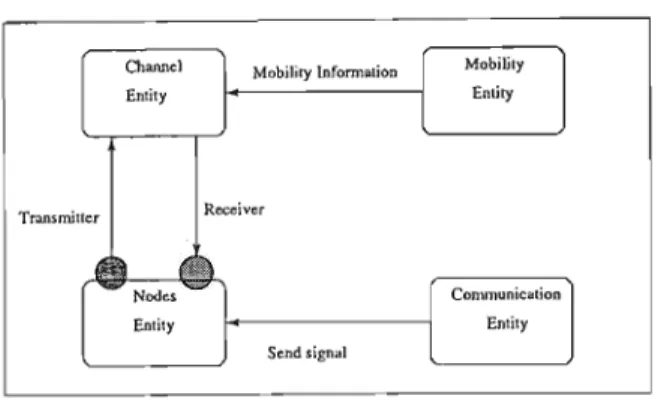
The Simulation Entities
Two nodes A and B are said to be neighbors if the Euclidean distance between them in the network is less than the transmission range. The communication unit is responsible for initiating the communication and handling the data traffic in the network. Data rates: This is assumed fixed for the simulation and the same for all nodes.
The mobile node in the ad hoc network is handled by the node entity that implements the proposed routing protocols. The sender and receiver entities are modeled in the node entity to simulate the sender and receiver sections of the node. Length of the acknowledgment packet 1101 bits Time after which acknowledgment timeouts 200 ms Time after which the next hello message is generated 180 ms Bandwidth used in the simulation 512 KB.
Discussion of the Results
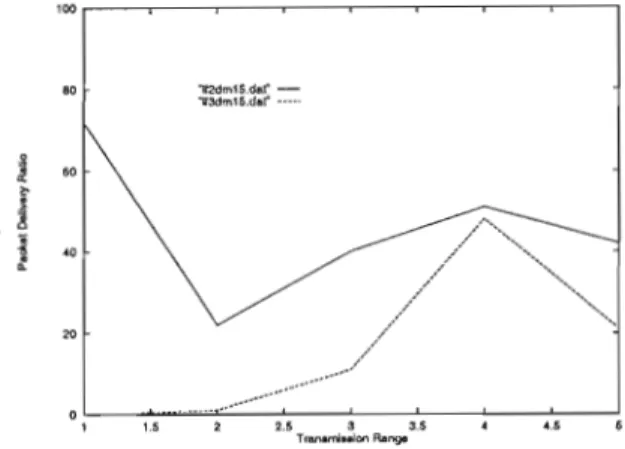
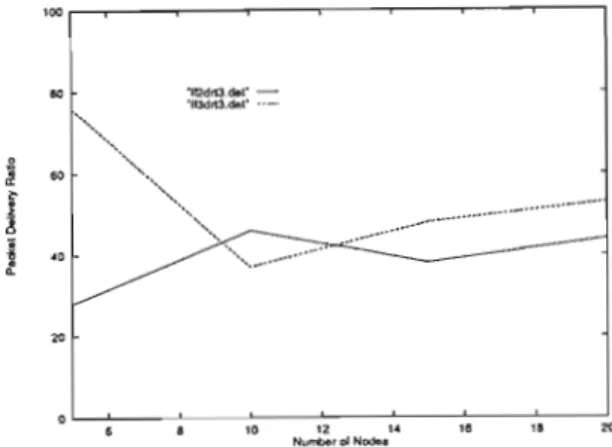
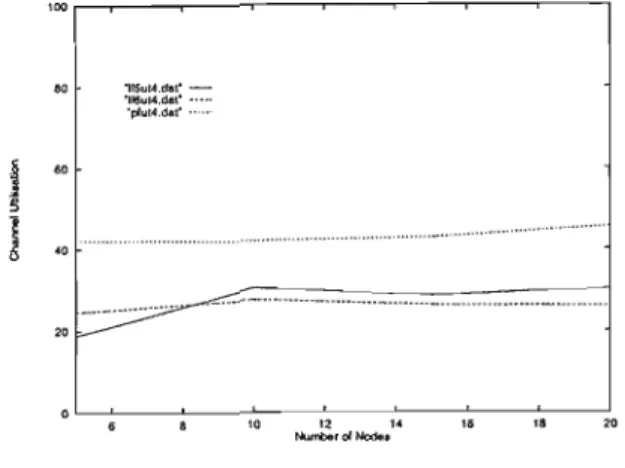
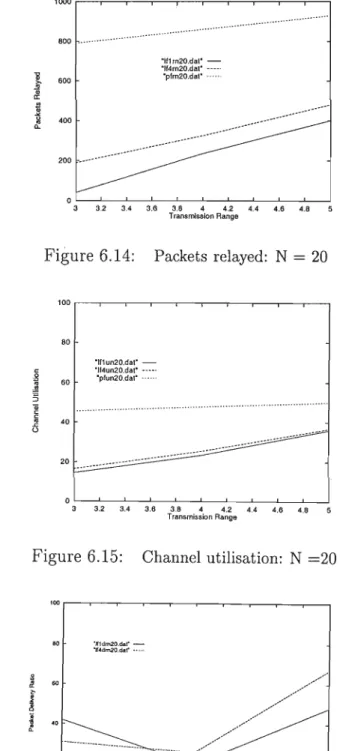
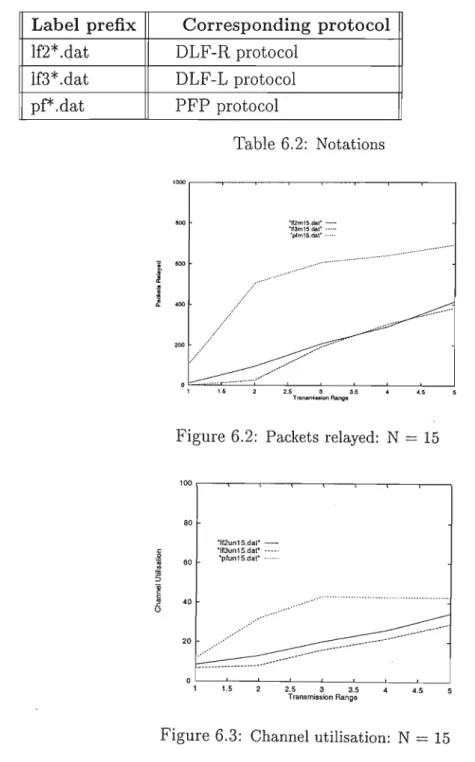
Figures 6.2-6.4 present simulation results as a function of transmission range, while Figures 6.5-6.7 present the obtained results as a function of network size. The results indicate that constrained flooding protocols reduce channel usage overhead compared to PFP. The difference between limited flooding protocols and PFP is greater with varying transmission range compared to varying number of nodes.
The packet forwarding load decreases as the network size increases for limited flooding protocols, except DLF-L, which shows a slight increase. The average number of packets passed as a function of transmission range is shown in Figure 6.29. The results as a function of transmission range, shown in Figure 6.37, indicated that packet delivery increases as transmission range increases.
Summary and Conclusions
Hybrid Cluster-based Hierarchical Routing
- Benefits of Hierarchical Clustering
- Description of a hybrid Hierarchical Cluster-based Routing (HCR)
- Definition of some terminology
- Intra-cluster Routing Mechanisms
- Inter-cluster Routing
If intra-cluster routing is based on route computation at each node, a route to the desired destination is first looked up in its routing table. The route reply packet is sent back via the clusterhead to the source node which adds the entry to its routing table. If intra-cluster routing is based on route calculation at clusterheads, a route to the desired destination is first looked up in the clusterhead's routing table.
If the destination is not found, the cluster head initiates the route discovery process by sending a broadcast message to the other cluster heads through the specified border node. When the destination is found, a route reply packet is sent back to the cluster head. If the routing is through the cluster head, then the source node always sends its packet to the cluster head.
Simulation of Clustering Algorithms
Cluster Computation
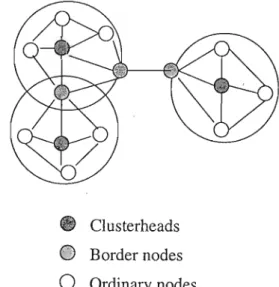
An optimal cluster architecture depends on various factors, including network topology, network traffic, routing algorithm, and geographic location of the nodes [Ame88]. Our goal is to achieve a relatively "good" cluster topology that meets some of the cluster design goals. One option for clustering is that each node is a neighbor of the cluster head and at most two hops from the other members of the cluster.
Another possibility is, for example, that each node is at most two hops from the group head and at most four hops from other members of the group. We choose a two-hop cluster architecture where there are at most two hops between common nodes in a cluster and one hop between a node and its cluster head. In the neighbor table, each entry stores the ID of the neighbor node and its role (cluster head, border node, or common node).
Proposals
A new node joins the cluster if it is within an I-hop distance of any of the existing cluster heads. Cluster failure or mobility is detected by cluster members through the exchange of neighborhood information. A node that detects the absence of the group takes responsibility as the head of the group and starts the re-election process by sending this information to its neighbors.
Then, a node that meets the election criteria becomes the master cluster and forwards the result to its neighbors. Either the information is stored in both the cluster head and the backup node or such information will be forwarded by the cluster head on demand. A cluster is split if the number of nodes in the cluster exceeds the split threshold, it is merged if the number of nodes becomes less than the merge threshold.
Simulation
It runs the algorithm only if the size of the new cluster after merging is close to the preferred cluster size and does not exceed the cluster split threshold. A stable clustering algorithm is necessary for efficient operation of this mechanism. This includes sending a signal to start or end the reception of a data packet and to start or end the data slot time for each node in the simulation. Each node moves randomly by one unit in each direction with a predetermined move probability.
A mechanism is provided to allow different types of mobility patterns and travel probabilities for the simulation. The current simulation results are based on a free-space propagation model [Rap95], where the received signal strength depends only on the distance to the transmitter.
Discussion of the Simulation Results
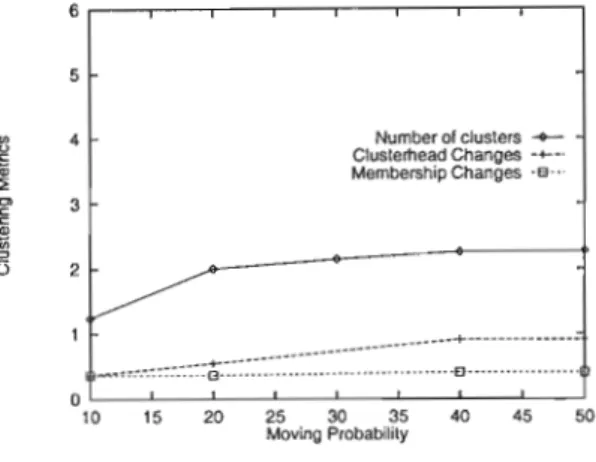
The number of clusters increases with increasing number of nodes at all levels of moving probability, but with a slight increase at P = 10% for larger network size. The largest number of clusters is obtained with a larger network size of N = 20 in the simulation. Figures 8.14 and 8.15 show that the number of clusters increases with increasing network size for all simulated moving probabilities.
The number of clusters increases with increase in network size at all moving probability levels compared. This indicates that the higher the moving probability, the larger the number of clusters will be. It can be observed that the number of clusters increases with increase in number of nodes.
Summary and Conclusions
Conclusions and Future Work
Summary and Conclusions
Three possibilities for intra-cluster routing were proposed and it was argued that on-demand routing is suitable for inter-cluster routing. The performance metrics used were average number of clusters, changes in cluster heads, and changes in cluster membership.
Future Work
Bibliography
In Proceedings of the 14th MSc/PhD Annual Conference in Computer Science, Golden Gate, South Africa, p. In Proceedings of the 5th International Conference on Communication Systems (AFRICOM 2001), Breakwater lodge, Cape Town, South Africa, May 2001 In Proceedings of the Fourth ACM/IEEE International Conference on Mobile Computing and Networking (MOBICOM'9S), Dallas, Texas, p.
In Proceedings of the Third Annual ACM/IEEE International Conference on Mobile Computing and Networking (MOBI-COM'97), Budapest, Hungary, p. '97), p. In Proceedings of the Fourth ACM/IEEE International Conference on Mobile Computing and Networking (MOBICOM'98), Dallas, Texas, p.
Limited Flooding Algorithms Source Code
Clustering Algorithms Source Code