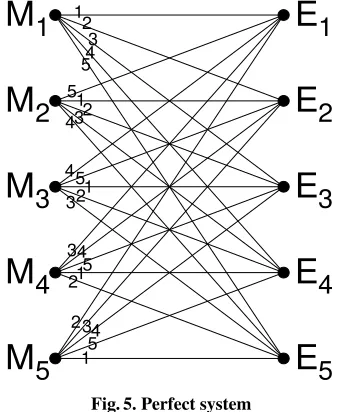
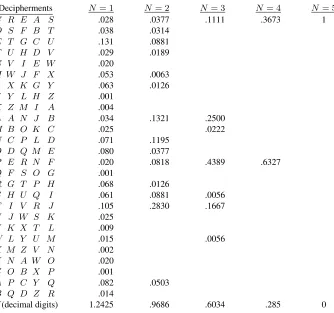
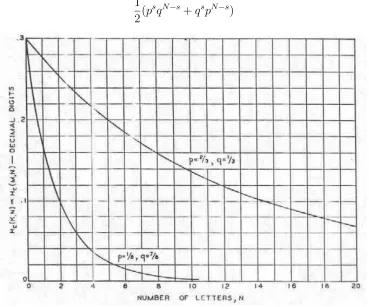
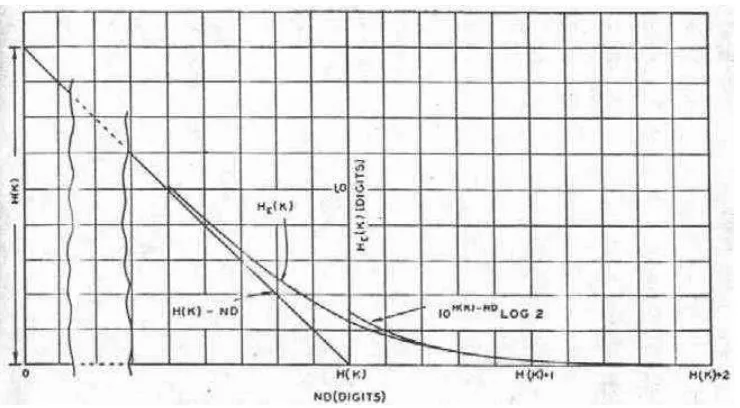
Communication Theory of Secrecy Systems
Teks penuh
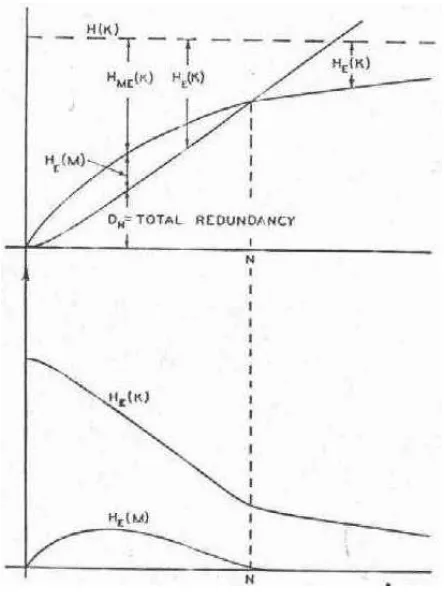
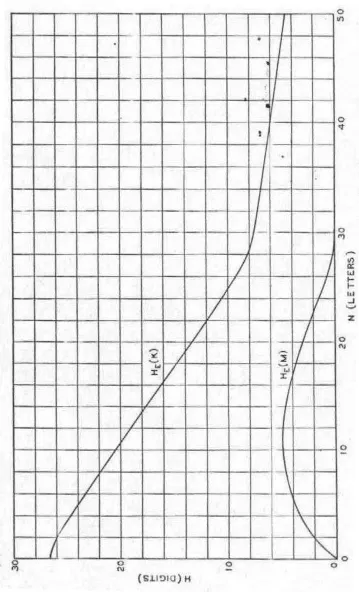
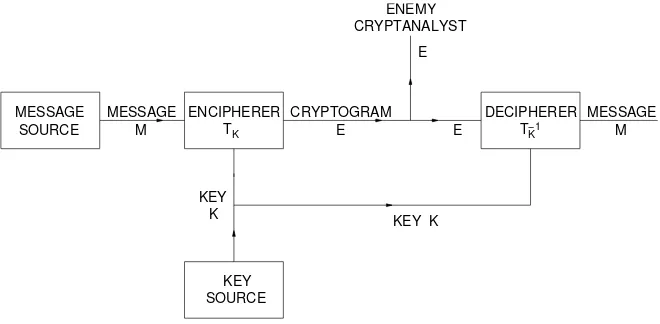
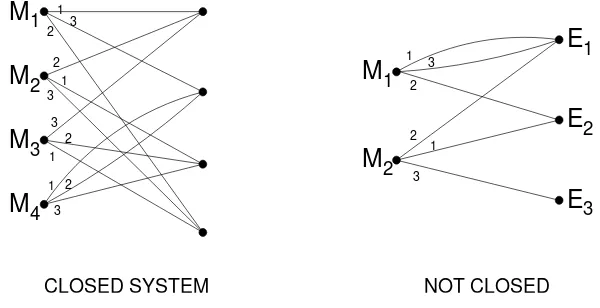
Gambar
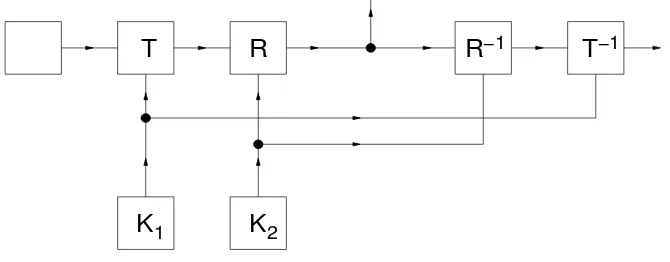
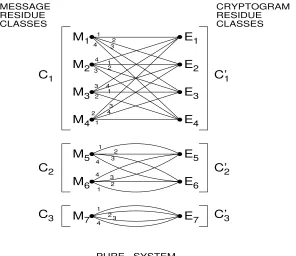
Garis besar
Dokumen terkait
Digital signature verification is the process of checking the digital sig- nature by reference to the original message and a given public key, thereby determining whether the
Figure 13.7 illustrates corresponding classes of asymmetric signature systems, contrasting public-key systems (with explicit public keys), identity-based systems (the public key is
Communication” (China Media Research, 2008) dan “An Introduction to Key Concepts of Understanding Chinese: Harmony as The Foundation of Chinese Communication” (China
4 Finding the set of all minimal keys of a relation In this section, we give the following algorithm finding all minimal keys of a given relationR.. Remember that this problem is
Part V: Oral Forms of Business Communication—With respect to oral communication, the authors provide details on efficient communication in meetings, keys to effective interpersonal
8.5.3 Separation Principle for Stoichiometric Systems Given a stable steady state of system 8.2, if the system input is written as p¼p0þ qv qp 1 Kavqv qpLas ; then the local e¤ect
As a representative ex- ample, the node coloring problem in graph theory is applicable to the channel assignment problem in cellular mobile communication systems.. The node coloring
In particular, for the fourth approximation system we discuss the well-posed initial and boundary value problem and obtain the a-priori estimate of the solution belonging to the space