The latest trend suggests that higher education has a higher number of reported breaches among all sectors, resulting in increased potential threats in the coming days. The latest trend suggests that higher education has a higher number of reported breaches among all sectors, resulting in increased potential threats in the coming days.
Background of the Research
It is based on the belief that the openness and accessibility of the higher education management system will not only be preserved, but also ensured. This is an attempt to evaluate an IT security management system based on unified methods of higher education information security approaches under a common topology based on hard and soft interventions.
Statement of the Problem
Unauthorized disclosure of information to individuals not authorized to view such information continues to be the leading type of information security issue facing colleges and universities. The three most common types of incidents in higher education accounted for 95% of all incidents in 2009 [4]. The case study revealed that some of the challenges facing MIT are: (a) Wireless technology (b) Vendors do not necessarily incorporate security in a useful way (c) Difficulty quantifying the value of security (d) Limited access to information encourages illegally stored data on desktops. e) Reducing response time (d) Preparing for the future [5].
Significance of the Research
Scope of the Research
Research Context
- Purpose of the Research
- Research Aim
- Research Objectives
- Research Questions
The general objective of this study is to assess the current strengths and weaknesses of the IT security management system of case institutions. How effective are MIST's strategy, policies and practices in protecting its information assets.
Delimitation of the Study
To motivate users and make them aware with an easy-to-use mobile app about secure IT behavior. How to merge the institution's cultural layout with that of its existing hard framework to satisfy security requirements with ethical issues.
Definition of the used terms
Structure of the Dissertation
This chapter is of extreme importance for the literature review to be complete and unbiased. This chapter highlighted the factors for users to use the information security facility at MIST within the boundaries of IT security strategy, policy and practice.
Theoretical Framework of References
- What is information Security?
- What for the Information Security Management System?
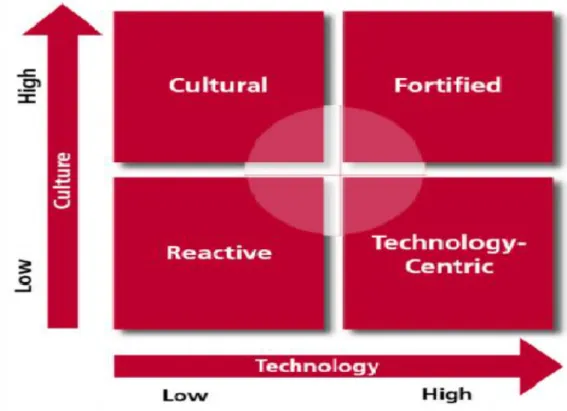
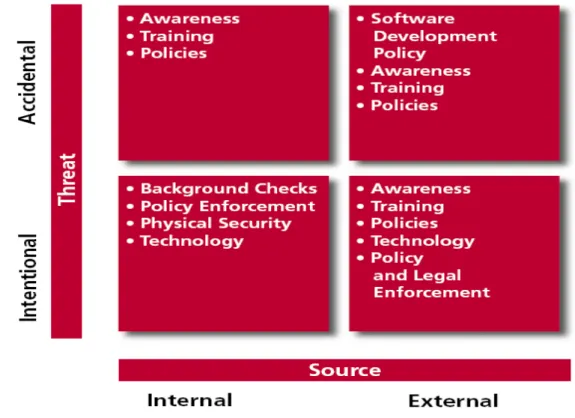
- Different Patterns of Information Security Management System
- What is Higher Education IT Security Management System?
- Current Image of the Higher Education Information Security Man-
- Development Initiatives of Higher Education Information Security
- Current Scale, Scope and Diversity of the Information Security Man-
- Recent Development of Information Security System Affecting Higher
- Major Focus of IT security Management System
- Assess the Role of Soft and Hard IT Security Interventions on Higher
- Propositional Structure of Soft and Hard IT Security Interventions
- Economic Crises Those Could Lead Higher Education Sector To-
- Impact Analysis of IT Security Management System on the Pre-
Therefore, considering the above scenario, this paper suggests an evaluation on the IT security management system of one of the reputed Institute of the country namely MIST [9]. The IT Security Management System (ISMS) is an example of the application of the conceptual model of the management system in the discipline of Information Security. Therefore, the higher education management system is simply secured in an IT Security Management System (ISMS).
The legal governance system surrounding IT security is becoming increasingly complex, presenting both challenges and opportunities.
Organizational Profile: MIST
Automated attacks replace individual hackers, becoming the most likely cause of a security breach. The changing nature of threats and the increasing sophistication required to combat them may prompt a move toward more centralized and standardized management of security at large institutions. Many institutions, especially smaller ones, may seek the help of consortia or vendors in managing the increasing burden of IT security management.
The budget allocation of MIST IT is shown approximately for the year for IT security purpose about 4,50,000 taka was spent, in addition hardware security purchases crossed about 10,00,000. MIST installed and upgraded their server equipment in the last fiscal year at an exclusive expenditure of Taka 1 crore.
Critical Assessment
To bring the resources of academia to influence both national policy and the individual responses, and thus to cope with and mitigate such riskier environments, various IT security approaches have been proposed. To solve this problem, a new security management scheme is proposed, namely Robust IT Security Balancing (RITS-B) approach, which focuses on developing such a strategic framework for security environment where facts, national and regional perspectives will be merged to lead to a proactive management and information security system without violating the freedom and openness that is at the core of academia. Since MIST is the case study, an assessment of its IT security environment provided depth to the strategy, policy and practices adopted by MIST to secure organizations' information assets.
The analyzed data helped us assess the state of the security IT environment in accordance with our proposal and present the necessary corrective measures, which were in the form of a recommendation.
Identified Knowledge Gaps
The unthinkable is now potentially a daily reality with root causes of information breaches, misuse and thus the initiation of terrorism, which has presented the world with many challenges in adapting people's personal and work lives to a changed environment. While among them the Soft IT Security (SITS) approach is highly lucrative today due to its simplicity and effectiveness in the information security sector, especially in higher education, it is unable to secure all types of educational environments using a general framework due to the fact that most of these environments are not homogeneous also due to little focus on cultures and beliefs. ISMS and RITS-B could be the rating scale that could help define, propose and measure an organizational model and ultimately an easy-to-use scheme could be developed for awareness purposes.
Analyzing the Original Research Questions and Research Objectives with
Summary
It is important for the researcher to know not only the research methods needed for the research undertaken, but also the methodology. There should be a clear understanding of how to find a solution to a physical system described by a mathematical model and how to apply a particular method as appropriate to the problem. When the research has been completed, there should be an explanation of the methodology used so that others can understand the importance of the research and how it worked. It also enables the researcher to express about each of the actions taken and the possible causes behind it, as well as the limitations of the research as well as its strengths. The information contained in this report has been collected from both primary and secondary sources.
The information has been used at the subsequent levels to find out the facts prevailing in the information security management system in the focused research area.
Research Design
Even if the method considered in two problems is the same, but the methodology may be different. To find the best result from a study, the researcher must decide the appropriateness, efficiency and accuracy ranking of a chosen research method. It provides insight into the problem or helps develop ideas or hypotheses for possible quantitative research.
It is also used to uncover trends in thoughts and opinions, and delve deeper into the problem.
Research Paradigms
This research philosophy mainly focuses on the realities and beliefs that already exist in the management system. Although there are many more modern approaches available today, forward-thinking research specialists still have confidence in them. Because these approaches are very useful for any kind of environment and have the ultimate ability to fit in any major field of technology and social sciences.
This research did not have sufficient time or budget to interview all relevant users.
Research Strategy
In this approach, researchers use small sample and evaluate it in detail [21]. 3) Realism: This research philosophy concentrates mainly on the reality and beliefs that already exist in the management system.
Population of the Study
For faculty coverage, all members including the Head of the Department of Computer Science and Engineering were interviewed. Evaluations were then obtained from selected other faculty members of other departments. A very important part of this research was the opinion of the IT people and this was emphasized with it.
All persons from different categories were faced with different sets of questionnaires with small similarities, but there were no major differences in the final findings of the research.
Sampling Strategy
Data Collection
All individuals from different categories were presented with different sets of questionnaires with some minor similarities that would not make much of a difference in the final findings of the study. Searching on different educational institutions or commercial organizations has been logistically evaluated to find out the most important study elements and variables. The main positive aspects of these data collection techniques are that it will help us obtain in-depth facts about the factors prevailing in the field of information security and how the system will react in case of a data security incident. Moreover, the critical literature review and consultation with the experts will further help us to logistically organize every aspect of the research instruments in such a way that the research factors are explicitly identified.
However, the main negative aspect of this is that it lengthens the process and if the interviewer is not expert enough to deal with this focus group and to deal with this face-to-face interview session, the exact concerns of the study will not be come out into the square.
Data Analysis
They faced a different set of questionnaires because they have to maintain a different protocol than students and IT people.
Limitation
Ethical Consideration
Linking Sampling strategy, data collection and data analysis technique with
- General
- Staffing
- Policy
- Current IT Management System
- Awareness
- Enterprise Process
- Incident Handling
- Risk Assessment
- Funding and Budget
- Outcomes
- Future Directions
For example, do they practice ISMS simply to implement IT security strategies in an organized manner. Or, IT security awareness program or risk assessment analysis is of top priority in MIST. The respondent strongly agreed that IT security is one of the top three IT issues facing MIST today.
An IT security incident can be assessed based on a particular aspect of IT security that could or has been threatened.
Quantitative Result
Existence of IT security policy
Existence of IT Security Practice
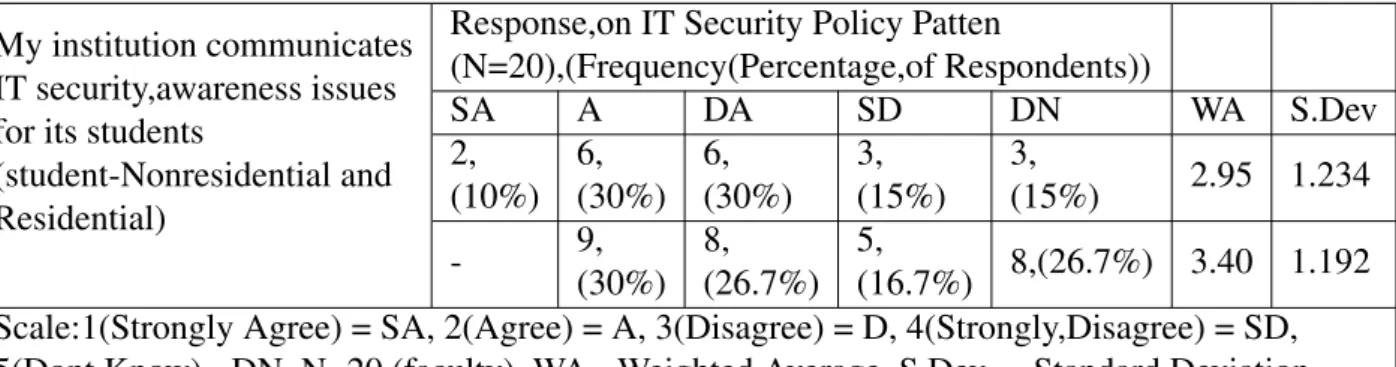
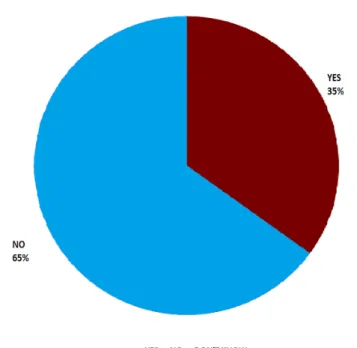
Concern of IT security Awareness Issues
The infrastructure of IT security is in full swing and will require a holistic effort in the near future. Therefore, a SWOT analysis of MIST towards the implementation of a robust IT security management framework should yield effective results. So, a study summarized with a clearer understanding of the strategy, policies and practices of MIST's IT security management system.
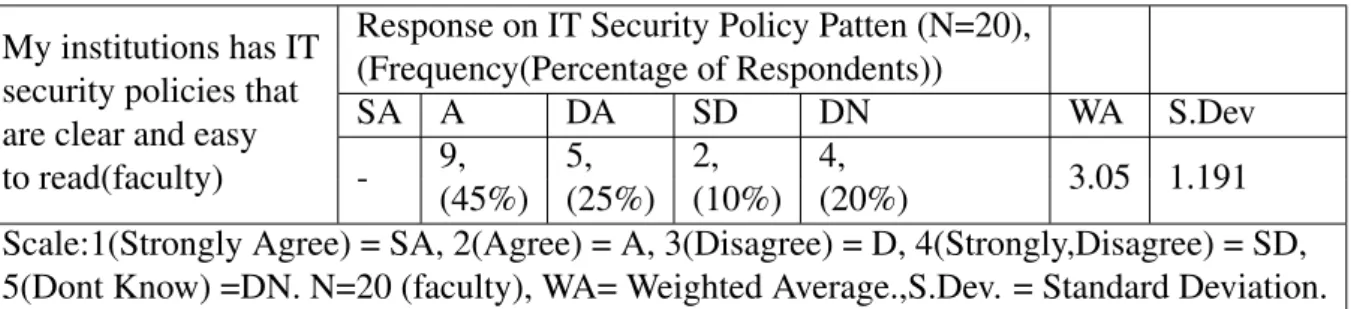
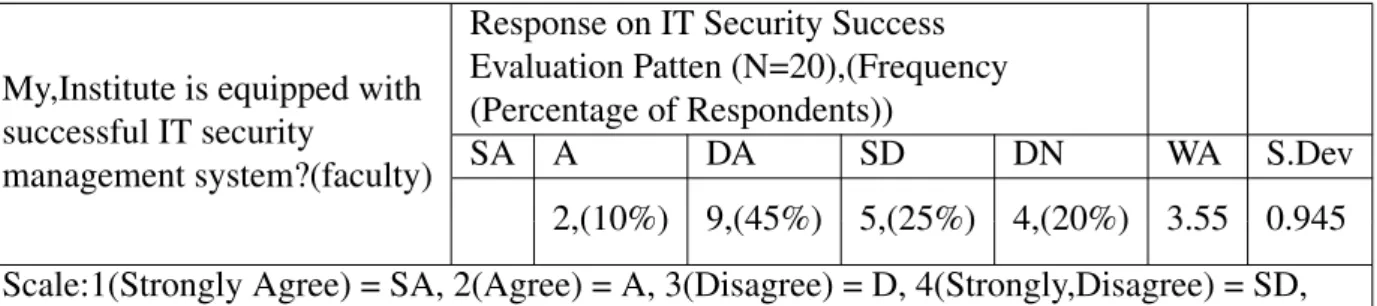
At present, MIST's authority is undertaking a number of development initiatives in the field of IT security management systems. In most cases, this study found a positive framework of strategy, policy and practice governing MIST's perceived IT security management system. My institutions have IT security policies that are clear and easy to read (faculty) see A.4.
IT Security Approach
Risk Assessment and Response
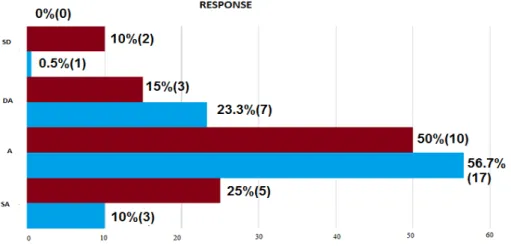
Response on Existence of IT Security Practices (N=20)
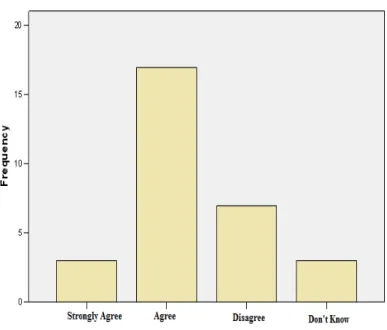
Response on IT Security as a Top Confronting Issue (N=50)
SPSS data for Figure 4.1
SPSS data for Figure 4.2
SPSS data for Table 4.2
SPSS data for Table 4.1
SPSS data for Table 4.2
SPSS data for Table 4.2
SPSS data for Table 4.3
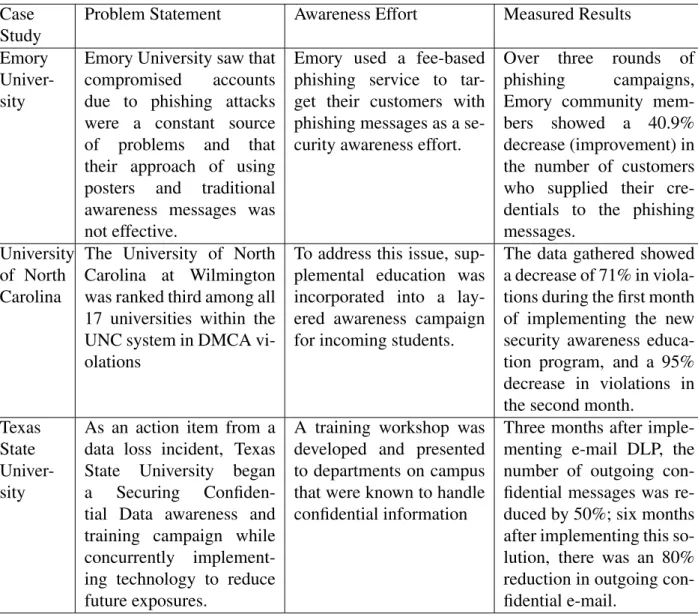
Case Study on Higher Education Security Breech
IT Security Policy Patten
IT Security Awareness Patten
IT Security success evaluation
SWOT analysis on MIST,(IT Security Management System)