The Application of Mixed Method in Developing a Cyber
Terrorism Framework
*
Rabiah Ahmad, Zahri Yunos
Dept of Computer System and Communication Faculty of Information and Communication Technology
Universiti Teknikal Malaysia Melaka (UTeM) Melaka, Malaysia
Email: [email protected], [email protected]
Received **** 2012
Abstract
Mixed method research has becoming an increasingly popular approach in the discipline of sociology, psychology, education, health science and social science. The purpose of this paper is to describe the application of mixed method in developing a cyber terrorism framework. This project has two primary goals: firstly is to discover the theory and then develop a conceptual framework that describes the phenomena, and secondly is to verify the conceptual framework that describes the phenomena. In order to achieve conclusive findings of the study, a mixed method research is recom-mended: qualitative data and quantitative data are collected and analyzed respectively in a separate phase. The mixed method approach improves the rigor and explanation of the research results, thus bring conclusive findings to the study outcome. By utilizing qualitative and quantitative techniques within the same study, we are able to incorporate the strength of both methodologies and fit together the insights into a workable solution.
Keywords: Mixed Method Research; Methodology; Data Analysis; Data Collection; Cyber Terrorism
1.
Introduction
Methodology can be simplified as a plan of action where the method used brings to the desired outcome. The con-text of methodology as described by Crotty [1] cited in Levy [2], defines methodology as "the strategy, plan of action, process or design lying behind choice of particu-lar methods and linking the choice and use of methods to the desired outcome". Methodology refers to the theoret-ical arguments that researchers use in order to justify their research methods and design [3].
The purpose of this paper is to describe the applica-tion of mixed method in developing a cyber terrorism framework. This project has two primary goals, firstly is to discover a theory and then develop a conceptual framework that describes the phenomena by using qua-litative method. Secondly is to verify the conceptual framework that describes the phenomena by quantitative method. By utilizing both techniques within the same study, the researcher is able to incorporate the strength of both methodologies and fit together the insights into a workable solution.
2.
Literature Review
2.1.Cyber Terrorism
In this digital age, the concept of cyber terrorism or the use of cyberspace to carry out terrorist activities has emerged. The convergence of physical terrorism and new advancement of ICT have spawned a new term called cyber terrorism [4]. It can be summarized that cyber ter-rorism is the perpetration of attack through the cyber-space and the virtual world. However, there is no un-iversally accepted definition of cyber terrorism, which seems to be a fundamental issue and challenge in coun-tering threats from cyber terrorism.
multidimen-sional structure (or components) of cyber terrorism, we can say that the concept of cyber terrorism is a contested concept whereby various parties interpret it differently.
The concept of cyber terrorism has several attributes (or components) such as motivation, impact and target [11]. Due to complexity of various interacting variables in the concept of cyber terrorism, to formulate a frame-work in describing its influential components would be beneficial. Therefore, accurate knowledge of the context of cyber terrorism enhances clarity and helps to avoid obscuring intent. Thus, there is a need for a more struc-tured approach in understanding the various components of cyber terrorism. The outcome of this study serves the basis for various strategic decisions for policy and deci-sion makers as well as useful foundation for academic research in understanding the context of cyber terrorism.
2.2.Mixed Method Research
One important way to strengthen a study design is through triangulation, or the combination of qualitative and quantitative approaches in the study of a situation or a certain phenomenon [12]. Usually, the researchers tri-angulate the two methods in order to check on the accu-racy of the data gathered by each method, to make the choices available more concrete, to amplify strengths and lessen weaknesses in a study, and to answer broader and more complete range of research problems [13].
Currall et al. [14] study the use of qualitative and quantitative methods and conclude that the mixed me-thods promoted both theory development and theory evaluation (or verification). Srnka and Koeszegi [15] conclude that qualitative studies are accepted in the so-cial sciences as exploratory or triangulation efforts that complement quantitative studies, which provide quality checks for each of these stages for result's validity and reliability. A detailed study that examine the ways in which quantitative and qualitative research were inte-grated and combined in practice was conducted by Bry-man [16]. He defines triangulation as traditional view where quantitative and qualitative researches are com-bined to triangulate findings in order to be mutually cor-roborated.
3.
Knowledge Management Architecture in
Developing Cyber Terrorism Framework
Knowledge management is a matter of managing analyti-cal process to transform data into information, and infor-mation into knowledge, and knowledge into wisdom [17]. Recent research suggests that architectural knowledge, such as design decisions, is important and should be rec-orded alongside the architecture description [18]. In this research, the conceptual framework describing cyber ter-rorism is developed by using the grounded theory me-thod. In grounded theory, the main source of data
collec-tion are interviews conducted with participants and ob-served by the researcher, whereby the researcher looks for common patterns among the sets of data [19]. Grounded theory is a rigorous process that involves generating a conceptual model (or theory) that is grounded in the data [20].
Egan [21] recommended five steps in the process of grounded theory research; initiating research, data selec-tion, initiation and ongoing data collecselec-tion, data analysis and concluding the research (Figure 1). Jones and Alony [22] suggest five steps in grounded theory approach: ac-knowledgement of researchers’ bias, data selection, data collection, data coding & analysis and compilation of results. Likewise, the grounded theory method employed by Esteves et al. [23] composed of the following phases: research design phase, data collection phase, data analysis phase and comparison phase. Overall, the steps of grounded theory approach discussed above are more or less similar with each other. For this research, we adopted Egan’s recommendation.
INITIATION OF THE RESEARCH 1
DATA SELECTION 2
DATA COLLECTION 3
DATA ANALYSIS 4
CONCLUDING THE RESEARCH 5
Figure 1: Grounded Theory Process (Adapted from Egan [21])
The first level, initiation of the research involves the selection of an area of inquiry. The research begins with an awareness of the context of the research by reviewing literatures relevant to the area of inquiry. In the second level, data selection, involves the identification of poten-tial data sources (individuals and organizations they represent) associated with the research questions. The respondents are chosen from various expert positions to reflect variety of expertise.
The third level is initiation of data collection from targeted respondents. Data collection is an ongoing process, whereby the researcher can return to the inter-viewees for clarification and elaboration besides compar-ing related documents or records with data collected dur-ing initiation of the research.
the understanding and to enable researcher to present what have been discovered. Lastly, concluding the re-search, involves documenting the grounded theory based on researcher observation of the data saturation and suffi-cient theory which has emerged from the data. Data satu-ration is the evident when data collection no longer con-tributes to elaboration of the phenomenon being investi-gated
.
4.
Conceptual Framework of this Study
Two research methods that are commonly used are qua-litative research and quantitative research. It is suggested that when the goal of a research is to develop a concep-tual model for the purpose of building theory around a particular phenomenon or process, an interpretive ap-proach utilizing a qualitative methodology may be more appropriate [2]. On the other hand, if the primary goal of a research problem is to test the validity of a model where all the variables of influence a phenomenon or process is already known, then quantitative methodology may be appropriate [2]. In summary, qualitative research ap-proaches seek to explore phenomena while quantitative research approaches seek to confirm hypothesis about phenomena.
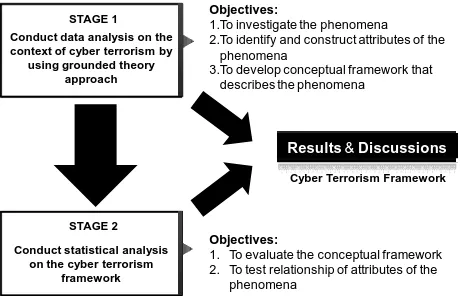
This research is about exploring the context of cyber terrorism, focusing on the attributes or components of cyber terrorism. Since this project is exploratory in na-ture, a qualitative research by using a grounded theory method is adopted for this study. The phrase grounded theory refers to theory that is developed from a corpus of data through literatures, interviews and observations [24]. In this method, the objectives are to investigate the phe-nomena under study, to identify and construct attributes of the phenomena, and to develop a conceptual frame-work that describe the phenomena.
Once the theory discovery and conceptual framework have been developed, the next stage is to test or verify the conceptual framework. The outcome can be achieved by using quantitative method to quantify them and then ap-plied statistical test to conduct the hypothesis test. In this method, the objectives are to evaluate the framework and to test the dynamic relationship of attributes (or components) of the framework.
In short, we believe that a mixed method approach is appropriate to be used in this study in order to accomplish both theory discovery and verification within a single research project. Theory discovery is achieved by using qualitative data to sharpen our theoretical ideas about the phenomena under investigation, while verification is achieved by using quantitative data to quantify them and then applied statistical test to conduct hypothesis test. The combination of qualitative and quantitative techniques within one research study able to incorporate the strength
of both methodologies. The framework of research me-thodology is described below (Figure 2).
Results & Discussions
Objectives:
1. To evaluate the conceptual framework 2. To test relationship of attributes of the
phenomena
Objectives:
1.To investigate the phenomena 2.To identify and construct attributes of the
phenomena
3.To develop conceptual framework that describes the phenomena
Cyber Terrorism Framework
Conduct statistical analysis on the cyber terrorism
framework STAGE 2 Conduct data analysis on the context of cyber terrorism by
using grounded theory approach
STAGE 1
Figure 2. The framework of research methodology
The approach discussed in this paper is well described by Srnka and Koeszegi [15] where they state that the combination of two separate studies, one collects and analyzed qualitative and quantitative data sequentially, has been acceptable to researchers in the social science. By conducting qualitative method in a preliminary stage, the objective is for the researchers to develop a concep-tual framework (or to generate hypothesis) for the quan-titative study. Thus, when qualitative data collection pre-cedes the quantitative data collection, the intent is to first explore the problem under study then follow up on this study with quantitative data that are amenable to studying a large sample so that results might be inferred to a popu-lation [25]. We believe that by merging the results pro-vides an overall picture of the research problem.
5.
Framework of Data Collection and Data
Analysis
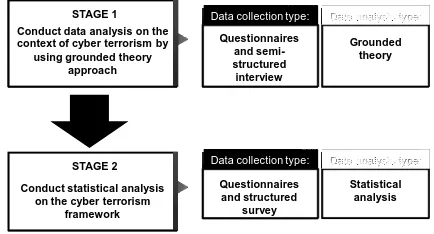
research includes a variety of methodological approaches and one example is grounded theory [27]. As have been mentioned earlier, the phrase grounded theory refers to theory that is developed from a corpus of data through literatures, interviews and observations.
Data collection type: Data analysis type:
Questionnaires Conduct data analysis on the
context of cyber terrorism by using grounded theory
approach STAGE 1
Conduct statistical analysis on the cyber terrorism
framework STAGE 2
Data collection type: Data analysis type:
Figure 3. Framework for data collection and data analysis
In the next stage, quantitative approach is applied to corroborate the researcher's initial discovery. A survey with close-ended questions format are used for data col-lection to determine the views and opinions of the popu-lation that represents various groups in the society. In this phase, the researcher's goal is to test the theory or hypothesis, which finding is generalized from a larger representative sampling. Statistical analysis is performed to test the validity of the theory or hypothesis. The nu-merical findings help to interpret the results, where clearer interpretations of the statistical results are ob-tained. Figure 3 shows the summary on how the data are collected and analyzed.
6.
Suitability of Mixed Method in this
Research
All the relevant methodological issues discussed in this paper provide justification and practical approach on how the research is conducted. The methodology ex-plained in this paper provides the researchers with the right direction and understanding in conducting the re-search by choosing the right rere-search design. Rere-search design as defined by Cooper and Schindler [27] is a plan and structure of investigation so conceived as to obtain answers to research questions. It includes an outline on what the researcher will do from initiation of the research to the final analysis of the data.
In this study, we suggest that a mixed method re-search approach is appropriate to be applied. The moti-vation factors in applying the mixed method (as opposed to a single method) are due to the following reasons. Firstly, the nature of the research is exploratory and ex-planatory in nature, and is grounded in theory. The goals
are to discover theory and to develop a conceptual framework that describes the phenomena (qualitative method); and to test or verify the conceptual framework that describes the phenomena (quantitative method). As noted by Yauch and Steudel [13], the mixed method search complements each other, which explains the re-sults of analyses. The qualitative research is interpretive, which allow for the discovery of new ideas and unanti-cipated occurrences. Qualitative research aims to achieve an in-depth understanding of a situation or a certain phenomenon [27]. Focus of the research is to explore (understand and interpret) of a situation or a certain phenomenon. On another hand, quantitative research aims to achieve precise measurement of something such as participants behavior, knowledge or opinion [27]. Fo-cus of the research is to confirm (describe and explain) hypothesis about a situation or a certain phenomenon. Therefore, by utilizing a mixed method research, we be-lieved it would bring conclusive findings on outcome of this study.
Secondly, mixed method approach helps to answer questions that cannot be answered by qualitative or quantitative approaches alone, thus, provide breadth and depth to the study [28]. Researchers who conduct mixed methods research are more likely to select methods and approaches with respect to their underlying research questions in ways that offer the best opportunity for answering important research questions [28]. In this re-search, a survey questionnaire using qualitative in-depth interviews is conducted as a way to tap into participants' perspectives and insights. During analysis, the qualitative researcher uses content analysis of written or recorded materials drawn from participants' expressions and ob-servations [27] or documents review [2]. Qualitative re-search study via questionnaires interview, and supple-ment with close-ended survey systematically provide breadth and depth to the research [12]. Quantitative research looks at the frequency [27] or any kind of re-search that produces findings arrived at by means of sta-tistical procedures [2]. Through this approach, it is be-lieved that the findings are corroborated across different approaches, thus provide greater confidence in the con-clusion.
lo-cating a true position by referring to two or more other coordinates [12]. As noted by Yauch and Steudel [13], triangulation corroborates data and obtains convergent validity. Moreover, triangulation reduces biasness be-sides be able to heighten the validity of the data collec-tion and analysis.
7.
Conclusion
The study on the context of cyber terrorism is quite com-plex as it is about threat perception which makes the concept differ from one to another. Understanding simi-larities and differences in perception of what constitutes cyber terrorism can provide insight on the concept of cyber terrorism. The outcome of this study serves the basis for various strategic decisions for policy and deci-sion makers as well as useful foundation for academic research in understanding the context of cyber terrorism. Detail focus analysis can be conducted to investigate and analyze the context of cyber terrorism.
This paper provides information on how this research is conducted. It also describes the framework of research methodology, where we have recommended that the study to be conducted by using a mixed method research: qualitative data and quantitative data are collected and analyzed respectively in a separate phase. This paper also established the conceptual framework that guides the data collection and data analysis techniques. Finally, the research methodology explained in this paper provides the researchers with the right direction by choosing the right research design. The mixed method improves the rigor and explanation of the results, thus bring conclusive findings to the research outcome. By utilizing qualitative and quantitative techniques within the same study, a mixed method research should be able to incorporate the strength of both methodologies and fit together the in-sights into a workable solution.
8.
Acknowledgements
The authors would like to thank the following individu-als who provided valuable input to this paper: Dr Sola-huddin Shamsuddin and Zaleha Abd Rahim of CyberSe-curity Malaysia. We also would like to thank the Univer-siti Teknikal Malaysia Melaka (UTeM) that provided research grant for this project.
REFERENCES
[1] M. Crotty, The Foundation of Social Research: Meaning and Perspective in the Research Process. St Leonards, NSW: Allen and Unwin, 1998.
[2] D. Levy, “Qualitative Methodology and Grounded Theory in Property Research,” Pacific Rim Property Research Journal, vol. 12, no. 4, pp. 369-388, 2006.
[3] J. M. Case and G. Light, “Emerging Methodologies in Engineering Education Research,” Journal of Engineer-ing Education, vol. 100, no. 1, pp. 186-210, 2011. [4] D. A. Simanjuntak, H. P. Ipung, and C. Lim, “Text
Clas-sification Techniques Used To Facilitate Cyber Terrorism Investigation,” in Proceeding of Second International Conference on Advances in Computing, Control, and Telecommunication Technologies (ACT 2010), Jakarta, Indonesia, 2 Dec, 2010, pp. 198-200.
[5] M. Dogrul, A. Aslan, and E. Celik, “Developing an In-ternational Cooperation on Cyber Defense and Deterrence against Cyber Terrorism,” in 2011 3rd International Conference on Cyber Conflict, Tallinn, Estonia, 7-10 June, 2011, pp. 1-15.
[6] M. Conway, “Against Cyberterrorism,” Communications of the ACM, vol. 54, no. 2, p. 26, Feb. 2011.
doi:10.1145/1897816.1897829
[7] Z. Yunos, S. H. Suid, R. Ahmad, and Z. Ismail, “Safe-guarding Malaysia’s Critical National Information Infra-structure (CNII) Against Cyber Terrorism: Towards De-velopment of a Policy Framework,” in IEEE Sixth Inter-national Conference on Information Assurance & Secu-rity, Atlanta, GA, 23-25 Aug, 2010, pp. 21-27. [8] P. A. H. Williams, “Information Warfare: Time for a
Redefinition,” in Proceedings of the 11th Australian In-formation Warfare & Security Conference, Perth West-ern, Australia, 30 Nov - 2 Dec, 2010, pp. 37-44.
[9] C. Czosseck, R. Ottis, and A. M. Taliharm, “Estonia after the 2007 Cyber Attacks: Legal, Strategic and Organisa-tional Changes in Cyber Security,” InternaOrganisa-tional Journal of Cyber Warfare and Terrorism, vol. 1, no. 1, pp. 24-34, 2011. doi:10.4018/ijcwt.2011010103
[10] J. Matusitz, “Social Network Theory: A Comparative Analysis of the Jewish Revolt in Antiquity and the Cyber Terrorism Incident over Kosovo,” Information Security Journal: A Global Perspective, vol. 20, no. 1, pp. 34-44, Feb. 2011.
[11] R. Ahmad and Z. Yunos, “A Dynamic Cyber Terrorism Framework,” International Journal of Computer Science and Information Security, vol. 10, no. 2, pp. 149-158, 2012.
[12] M. Q. Paton, Qualitative Evaluation and Research Me-thods, Second Edi. SAGE Publications, 1991.
[13] C. Yauch and H. Steudel, “Complementary Use of Qua-litative and Quantitative Cultural Assessment Methods,” Organizational Research Methods, vol. 6, no. 4, pp. 465-481, Oct. 2003.
[14] S. C. Currall, T. H. Hammer, L. S. Baggett, and G. M. Doniger, “Combining Qualitative and Quantitative Me-thodologies to Study Group Processes: An Illustrative Study of a Corporate Board of Directors,” Organizational Research Methods, vol. 2, no. 1, pp. 5-36, 1999.
[15] K. J. Srnka and S. T. Koeszegi, “From Words to Numbers: How to Transform Qualitative Data into Meaningful Quantitative Results,” SBR 59 Simply the Best Research, pp. 29-57, 2007.
[17] R. J. Chenail, “Conducting Qualitative Data Analysis : Qualitative Data Analysis as a Metaphoric Process,” The Qualitative Report, vol. 17, no. 1, pp. 248-253, 2012. [18] A. Tang, P. Avgeriou, A. Jansen, R. Capilla, and M. Ali
Babar, “A Comparative Study of Architecture Knowledge Management Tools,” Journal of Systems and Software, vol. 83, no. 3, pp. 352-370, Mar. 2010.
doi:10.1016/j.jss.2009.08.032
[19] R. Hoda, J. Noble, and S. Marshall, “Using Grounded Theory to Study the Human Aspects of Software Engi-neering,” in Proceeding HAoSE ’10 Human Aspects of Software Engineering, Nevada, USA, 17-21 Oct, 2010. [20] A. A. Singh, A. Urbano, M. Haston, and E. Mcmahan,
“School Counselors’ Strategies for Social Justice Change : A Grounded Theory of What Works in the Real World,” American School Counselor Association, vol. 13, no. 3, pp. 135-145, 2010.
[21] T. M. Egan, “Grounded Theory Research and Theory Building,” in Advances in Developing Human Resources, vol. 4, no. 3, Sage Publications, 2002, pp. 277-295. [22] M. Jones and I. Alony, “Guiding the Use of Grounded
Theory in Doctoral Studies – An Example from the Aus-tralian Film Industry,” International Journal of Doctoral Studies, vol. 6, pp. 95-114, 2011.
[23] J. Esteves, U. Politécnica, and J. Carvalho, “Use of Grounded Theory in Information Systems Area : An Ex-ploratory Analysis,” European Conference on Research Methodology for Business and Management, pp. 129-136, 2000.
[24] J. W. Creswell, Qualitative Inquiry And Research Design: Choose Among Five Traditions. London: Sage Publica-tions, 1998.
[25] J. M. Azorin and R. Cameron, “The Application of Mixed Methods in Organisational Research: A Literature Re-view,” Electronic Journal of Business Research Methods, vol. 8, no. 2, pp. 95-105, 2010.
[26] G. Walsham, “Doing Interpretive Research,” European Journal of Information Systems, no. 15, pp. 320-330, 2006.
[27] D. R. Cooper and P. S. Schindler, Business Research Method. NY: McGraw-Hill Companies, Inc, 2008. [28] R. B. Johnson and A. J. Onwuegbuzie, “Mixed Methods
Research: A Research Paradigm Whose Time Has Come,” Educational Research, vol. 33, no. 7, pp. 14-26, 2004. doi:10.3102/0013189X033007014
![Figure 1: Grounded Theory Process (Adapted from Egan [21])](https://thumb-ap.123doks.com/thumbv2/123dok/556381.65590/2.612.347.508.327.459/figure-grounded-theory-process-adapted-egan.webp)