Informasi Dokumen
- Penulis:
- Farid Akbar Siregar
- Sekolah: Universitas Sumatera Utara
- Mata Pelajaran: Ilmu Komputer
- Topik: Implementasi Kombinasi Algoritma Vigenere dan Algoritma Data Encryption Standard (DES) pada Aplikasi Short Message Service (SMS) Berbasis Windows Phone
- Tipe: graduation project
- Tahun: 2016
- Kota: Medan
Ringkasan Dokumen
I. Implementation of Vigenere and DES Algorithms in SMS Application
This section discusses the implementation of the Vigenere and Data Encryption Standard (DES) algorithms within a Windows Phone-based SMS application. The integration of these algorithms aims to enhance the security of SMS messages by encrypting the plaintext into ciphertext, ensuring confidentiality during transmission. The document outlines the technical specifications, including the programming language used (C#) and the .NET framework for the graphical user interface (GUI). This implementation serves as a practical solution for secure communication, addressing the vulnerabilities of message interception by unauthorized parties.
3.1 System Analysis
System analysis is crucial for breaking down the overall system into smaller subsystems, identifying the relationships between components to achieve security objectives. The analysis identifies key problems, such as the risk of unauthorized access to confidential messages and the inadequacy of single-key encryption methods. By employing the Vigenere algorithm for message encryption and DES for key encryption, the system aims to mitigate these risks and enhance overall message security.
3.2 System Requirements Analysis
The requirements analysis includes both functional and non-functional aspects. Functional requirements detail the necessary operations, such as the ability to encrypt plaintext into ciphertext and decrypt ciphertext back into plaintext using the same key. Non-functional requirements emphasize performance, user-friendliness, documentation, error control, and cost-effectiveness, ensuring that the application is efficient and accessible to users.
3.3 System Modeling
System modeling visually represents the software's requirements through various diagrams, including flowcharts and use case diagrams. Flowcharts illustrate the encryption and decryption processes, showing how plaintext is transformed into ciphertext and vice versa. Use case diagrams identify user interactions with the system, emphasizing roles such as the message sender and receiver, which are critical for understanding system functionality.
3.4 System Design
The system design phase specifies the detailed architecture of the software, focusing on the implementation of the Vigenere and DES algorithms. The application is designed with a user-friendly interface that includes sections for message creation, encryption, and decryption. Prototypes are provided to demonstrate the layout and functionality of the application, ensuring that users can easily navigate through the encryption and decryption processes.
II. System Implementation
This section outlines the practical implementation of the system, developed using C# and the .NET framework for the GUI. The application comprises multiple screens for different functionalities, including the main screen, message creation, decryption, help, and about sections. Each screen is designed to facilitate user interactions, ensuring a seamless experience when sending and receiving encrypted messages.
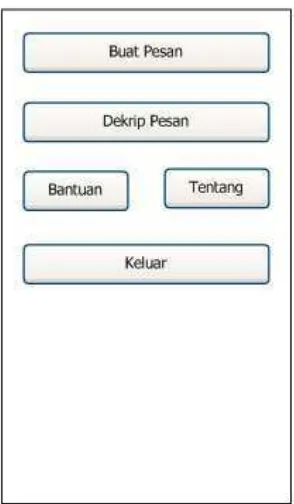
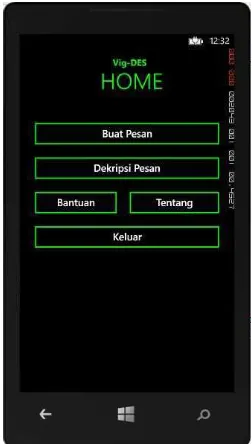
4.1 Main Screen
The main screen serves as the initial interface of the application, featuring buttons that allow users to navigate to different functionalities. This screen is crucial as it sets the stage for user engagement with the encryption and decryption processes.
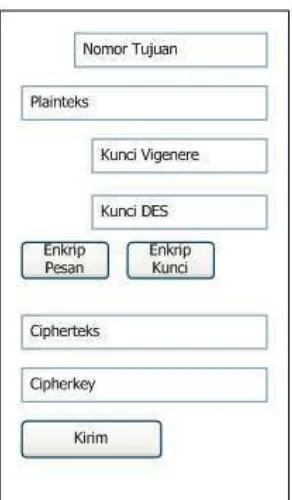
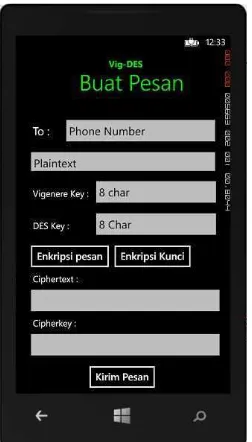
4.2 Message Creation Screen
In the message creation screen, users can input the recipient's phone number along with the plaintext message and keys for both the Vigenere and DES algorithms. The application then facilitates the encryption process, converting plaintext into ciphertext for secure transmission.
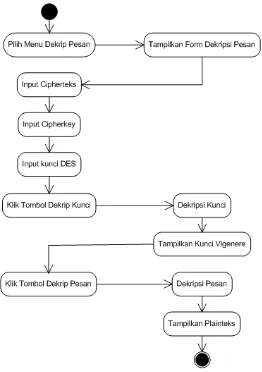
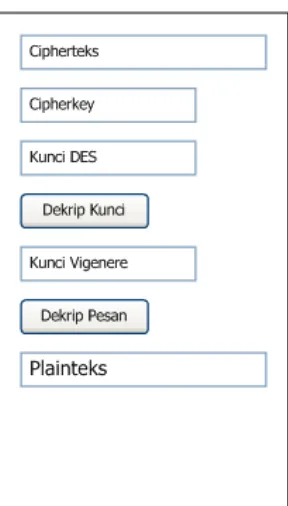
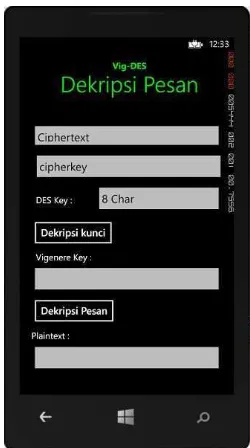
4.3 Decryption Screen
The decryption screen allows users to decrypt received ciphertext back into plaintext. Users must enter the correct keys to retrieve the original message, ensuring that only authorized individuals can access the content.
4.4 Testing the System
System testing is conducted to evaluate the effectiveness of the encryption and decryption processes. Various scenarios are tested to measure the time taken for encryption and decryption, ensuring that the application performs efficiently under different conditions.