Information Security and
Assurance
Jatinder N.D. Gupta
The University of Alabama in Huntsville, USA
Sushil K. Sharma
Ball State University, USA
Hershey • New York
Director of Editorial Content: Kristin Klinger Managing Development Editor: Kristin M. Roth Assistant Development Editor: Deborah Yahnke Editorial Assistant: Heather A. Probst Senior Managing Editor: Jennifer Neidig Managing Editor: Jamie Snavely Assistant Managing Editor: Carole Coulson
Copy Editors: Laura Kochanowski, Jennifer Young Typesetter: Carole Coulson
Cover Design: Lisa Tosheff Printed at: Yurchak Printing Inc. Published in the United States of America by
Information Science Reference (an imprint of IGI Global) 701 E. Chocolate Avenue, Suite 200
Hershey PA 17033 Tel: 717-533-8845 Fax: 717-533-8661 E-mail: [email protected] Web site: http://www.igi-global.com and in the United Kingdom by
Information Science Reference (an imprint of IGI Global) 3 Henrietta Street
Covent Garden London WC2E 8LU Tel: 44 20 7240 0856 Fax: 44 20 7379 0609
Web site: http://www.eurospanbookstore.com
Copyright © 2009 by IGI Global. All rights reserved. No part of this publication may be reproduced, stored or distributed in any form or by any means, electronic or mechanical, including photocopying, without written permission from the publisher.
Product or company names used in this set are for identification purposes only. Inclusion of the names of the products or companies does
not indicate a claim of ownership by IGI Global of the trademark or registered trademark. Library of Congress Cataloging-in-Publication Data
Handbook of research on information security and assurance / Jatinder N.D. Gupta and Sushil K. Sharma, editors. p. cm.
Summary: "This book offers comprehensive explanations of topics in computer system security in order to combat the growing risk associated with technology"--Provided by publisher.
Includes bibliographical references and index.
ISBN 978-1-59904-855-0 (hardcover) -- ISBN 978-1-59904-856-7 (ebook)
1. Computer networks--Security measures--Handbooks, manuals, etc. 2. Electronic information resources--Access control--Handbooks, manuals, etc. 3. Computer crimes--Prevention--Handbooks, manuals, etc. I. Gupta, Jatinder N. D. II. Sharma, Sushil K.
TK5105.59.H353 2008 005.8--dc22
2008008472
British Cataloguing in Publication Data
A Cataloguing in Publication record for this book is available from the British Library.
All work contributed to this book set is original material. The views expressed in this book are those of the authors, but not necessarily of the publisher.
Elisa Bertino
Purdue University, USA
Queen Booker
Minnesota State University, Mankato, USA
Mei Cao
Arkansas State University, USA Amita Goyal Chin
Virginia Commonwealth University, USA
Gurpreet Dhillon
Virginia Commonwealth University, USA
Sanjay Goel
State University of New York at Albany, USA
Ajay K. Gupta Gsecurity, USA
Sushil Jajodia
George Mason University, USA
Stephan Jones
Ball State University,USA
Shivraj Kanungo
The George Washington University, USA
Pradeep Khosla
Carnegie Mellon University, USA
Ronlad Kovac
Ball State University, USA
Vipin Kumar
University of Minnesota, USA
Eldon Y. Li
National Chengchi University, Taiwan
Dengpan Liu
The University of Alabama in Huntsville, USA
Herbert J. Mattord, CISSP Kennesaw State University, USA
P.K. Mahanti
University of New Brunswick, Canada
Joon S. Park
Syracuse University, USA Mike Raisinghani
Texas Woman’s University, USA
M. K. Raja
The University of Texas at Arlington, USA
Rajeev Raje
Indiana University – Purdue University, Indianapolis, USA
Rathindra Sarathy
Oklahoma State University, USA
Mohini Singh
RMIT University, Australia
Jim Tiller
Managing Editor, (ISC)2 Journal, USA Vijay Varadharajan
Mark Weiser
Oklahoma State University, USA
Michael Whitman
Kennesaw State University, USA
Branden Williams
Principal Consultant, VeriSign, Global Security Consulting, USA
John Zeleznikow
List of Contributors
Aickelin, Uwe / University of Nottingham, UK ...109
Aissioui, Abdelkader / LRIA – USTHB, Algeria ...152
Ajoku, Pamela / University of Pittsburgh, USA ...18
Al-Hamdani, Wasim A. / Kentucky State University, USA ...122
An, Gaeil / Electronics and Telecommunications Research Institute, Korea ...29
Bellettini, Carlo / Università degli Studi di Milano, Italy ...139
Benhamou,Belaïd / Technopôle de Château-Gombert, France ...152
Botelho, Christopher M. / Baylor Health, USA ...423
Boughaci, Dalila / LRIA – USTHB, Algeria ...152
Burt, Carol C. / 2AB Inc., Helena, AL, USA ...254
Cazier, Joseph A. / Appalachian State University, USA ...423
Chin, Amita Goyal / Virginia Commonwealth University, USA ...292
Clark, Tom / Brocade Communications, USA ...433
Coffey, Tom / University of Limerick, Ireland ...165
Conger, Sue / University of Dallas, USA ...279
Conklin, Wm. Arthur / University of Houston,USA ...415
Crespi, Alex / Indiana University-Purdue University Indianapolis, USA ...254
D’ Arcy, John / University of Notre Dame, USA ...55
Dojen, Reiner / University of Limerick, Ireland ...165
Drias, Habiba / LRIA – USTHB, Algeria ...152
Durresi, Arjan /Indiana University-Purdue University Indianapolis, USA ...372
Ege, Raimund K. / Northern Illinois University, USA ...218
Fernández-Medina, Eduardo / Universidad de Castilla-La Mancha, Spain ...495
Friedman, William H. / University of Central Arkansas, USA ...301
Ghafoor, Arif / Purdue University, USA ...331
Ghormley, Yvette / Saint Leo University, USA ...308
Graham, Erik / General Dynamics C4 Systems, USA...393
Green, David T. / Governors State University, USA...458
Gupta, Ajay / Gsecurity, Inc., USA ...382
Gupta, Jatinder N. D. / The University of Alabama at Huntsville, USA ... Gupta, Manish / State University of New York, Buffalo, USA...266, 447 Habib, Ahsan / Siemens TTB Center, Berkeley, USA ...179
Harrison, Britta / Louisiana State University, USA ...68
Hovav, Anat / Korea University, Korea ...55
Johnson, Kapp L. / California Lutheran University, USA ...347
Khazanchi, Deepak / University of Nebraska at Omaha, USA ...230
Lando, Jillian K. / Syracuse University, USA ...7
Landry, Bret J. L. / University of Dallas, USA ...279
Lee, JinKyu /Oklahoma State University, USA ...266
Luse, Andy / Iowa State University, USA ...98
Manulis, Mark / Horst-Görtz Institute for IT Security, Germany ...202
Martin, Andrew P. / University of Nebraska at Omaha, USA ...230
Masood, Ammar / Purdue University, USA ...331
Mathur, Aditya / Purdue University, USA ...331
Mishra, Sushma / Virginia Commonwealth University, USA ...292
Ng, Roy / Ryerson University, Canada...42
Olson, Andrew M. / Indiana University-Purdue University Indianapolis, USA ...254, 360 Oubeka, Brahim / LRIA – USTHB, Algeria ...152
Park, Joon S. / Syracuse University, USA ...7, 29 Piattini, Mario / Universidad de Castilla-La Mancha, Spain ...495
Ponnam, Aditya / Louisiana State University, USA ...68
Pradhan, M. / Indiana University-Purdue University Indianapolis, USA ...529
Proctor, Robert W. / Purdue University, USA ...402
Raje, Rajeev R. / Indiana University-Purdue University Indianapolis, USA ...254
Rao, H.R. / State Univerity of New York, Buffalo, USA ...266
Rea, Alan / Western Michigan University, USA ...193
Rrushi, Julian L. / Università degli Studi di Milano, Italy ...139
Rutherfoord, Rebecca H. / Southern Polytechnic State University, USA...483
Samuel, Arjmand / Purdue University, USA ...331
Santos, Javier / TECNUN University of Navarra, Spain ...467
Sarriegi, Jose M. / TECNUN University of Navarra, Spain ...467
Scheibe, Kevin / Iowa State University, USA ...98
Schultz, E. Eugene / High Tower Technologies, USA ...402
Schwenk, Jörg / Horst-Görtz Institute for IT Security, Germany ...202
Shaikh, Siraj Ahmed / United Nations University (UNU), Macau, SAR China ...240
Sharma, Sushil K. / Ball State University, USA ...341
Sharman, Raj / State University of New York, Buffalo, USA ...447
Steinbart, Paul John / Arizona State University, USA ...339
Stevens, Dwayne / Community Trust Bank, USA ...458
Taylor, Art / Rider University, USA ...518
Tilak, Omkar J./ Indiana University-Purdue University Indianapolis, USA ...254
Torres, Jose M. / TECNUN University of Navarra, Spain ...467
Townsend, Anthony / Iowa State University, USA ...98
Trujillo, Juan/ Universidad de Alicante, Spain ...495
Tupakula, Udaya Kiran / Macquarie University, Australia ...85
Twycross, Jamie / University of Nottingham, UK ...109
Varadharajan, Vijay / Macquarie University, Australia ...85
Villarroel, Rodolfo / Universidad Católica del Maule, Chile ...495
Vu, Kim-Phuong L. / California State University, USA ...402
Wang, Hai / The Pennsylvania State University, USA ...504
Watson, Ed / Louisiana State University, USA ...68
Weippl, Edgar / Vienna University of Technology and Science, Austria & Secure Business, Austria ...441
White, Doug / Roger Williams University, USA ...193
Witman, Paul D. / California Lutheran University, USA ...347
Xia, Y. / Indiana University-Purdue University Indianapolis, USA ...529
Table of Contents
Preface ... xxiv
Acknowledgment ...xxviii
Section I Enterprise Security Chapter I
Ransomware: A New Cyber Hijacking Threat to Enterprise ... 1
Xin Luo, The University of New Mexico, USA
Qinyu Liao, The University of Texas at Brownsville, USA
Chapter II
E-Commerce: The Benefits Security Risks, and Countermeasures ... 7
Joon S. Park, Syracuse University, USA Jillian K. Lando, Syracuse University, USA
Chapter III
Information Warfare: Survival of the Fittest ... 18
Pamela Ajoku, University of Pittsburgh, USA
Chapter IV
Evolution of Enterprise Security Federation ... 29
Gaeil An, Electronics and Telecommunications Research Institute, Korea Joon S. Park, Syracuse University, USA
Chapter V
A Holistic Approach to Information Security Assurance and Risk Management in an
Enterprise ... 42
Roy Ng, Ryerson University, Canada
Chapter VI
An Integrative Framework for the Study of Information Security Management Research ... 55
Ed Watson, Louisiana State University, USA
Section II
Security Approaches, Frameworks, Tools, and Technologies Chapter VIII
Distributed Denial of Service Attacks in Networks ... 85
Udaya Kiran Tupakula, Macquarie University, Australia Vijay Varadharajan, Macquarie University, Australia
Chapter IX
Firewalls as Continuing Solutions for Network Security ... 98
Andy Luse, Iowa State University, USA Anthony Townsend, Iowa State University, USA Kevin Scheibe, Iowa State University, USA
Chapter X
An Immune-Inspired Approach to Anomaly Detection ... 109
Jamie Twycross, University of Nottingham, UK Uwe Aickelin, University of Nottingham, UK
Chapter XI
Cryptography for Information Security ... 122
Wasim A. Al-Hamdani, Kentucky State University, USA
Chapter XII
Memory Corruption Attacks, Defenses, and Evasions ... 139
Carlo Bellettini, Università degli Studi di Milano, Italy Julian L. Rrushi, Università degli Studi di Milano, Italy
Chapter XIII
Design and Implementation of a Distributed Firewall ... 152
Dalila Boughaci, LRIA – USTHB, Algeria Brahim Oubeka, LRIA – USTHB, Algeria Abdelkader Aissioui, LRIA – USTHB, Algeria Habiba Drias, LRIA – USTHB, Algeria
Belaïd Benhamou, Technopôle de Château-Gombert, France
Chapter XIV
A Formal Verification Centred Development Process for Security Protocols ... 165
Tom Coffey, University of Limerick, Ireland Reiner Dojen, University of Limerick, Ireland
Chapter XV
Edge-to-Edge Network Monitoring to Detect Service Violations and DoS Attacks ... 179
Chapter XVI
A “One-Pass” Methodology for Sensitive Data Disk Wipes ... 193
Doug White, Roger Williams University, USA Alan Rea, Western Michigan University, USA
Chapter XVII
Securing E-Mail Communication with XML Technology ... 202
Lijun Liao, Horst-Görtz Institute for IT Security, Germany Mark Manulis, Horst-Görtz Institute for IT Security, Germany Jörg Schwenk, Horst-Görtz Institute for IT Security, Germany
Chapter XVIII
Aspect-Oriented Analysis of Security in Distributed Virtual Environment ... 218
Li Yang, University of Tennessee at Chattanooga, USA Raimund K. Ege, Northern Illinois University, USA Lin Luo, Florida International University, USA
Chapter XIX
Information Availability ... 230
Deepak Khazanchi, University of Nebraska at Omaha, USA Andrew P. Martin, University of Nebraska at Omaha, USA
Chapter XX
Formal Analysis and Design of Authentication Protocols ... 240
Siraj Ahmed Shaikh, United Nations University (UNU), Macau, SAR China
Chapter XXI
Access Control Frameworks for a Distributed System ... 254
Rajeev R. Raje, Indiana University-Purdue University Indianapolis, USA Alex Crespi, Indiana University-Purdue University Indianapolis, USA Omkar J. Tilak, Indiana University-Purdue University Indianapolis, USA Andrew M. Olson, Indiana University-Purdue University Indianapolis, USA Carol C. Burt, 2AB Inc., Helena, AL, USA
Chapter XXII
Implications of FFIEC Guidance on Authentication in Electronic Banking ... 266
Manish Gupta, State Univerity of New York, Buffalo, USA JinKyu Lee, Oklahoma State University, USA
H.R. Rao, State Univerity of New York, Buffalo, USA
Chapter XXIII
Disruptive Technology Impacts on Security ... 279
Internal Auditing for Information Assurance ... 292
Sushma Mishra, Virginia Commonwealth University, USA Amita Goyal Chin, Virginia Commonwealth University, USA
Chapter XXV
IT Continuity in the Face of Mishaps ... 301
William H. Friedman, University of Central Arkansas, USA
Chapter XXVI
Business Continuity and Disaster Recovery Plans ... 308
Yvette Ghormley, Saint Leo University, USA
Chapter XXVII
Security Policies and Procedures ... 320
Yvette Ghormley, Saint Leo University, USA
Chapter XXVIII
Enterprise Access Control Policy Engineering Framework ... 331
Arjmand Samuel, Purdue University, USA Ammar Masood, Purdue University, USA Arif Ghafoor, Purdue University, USA Aditya Mathur, Purdue University, USA
Chapter XXIX
Information Security Policies: Precepts and Practices ... 341
Sushil K. Sharma, Ball State University, USA
Jatinder N.D. Gupta, The University of Alabama at Huntsville, USA
Chapter XXX
A Guide to Non-Disclosure Agreements for Researchers ... 347
Paul D. Witman, California Lutheran University, USA Kapp L. Johnson, California Lutheran University, USA
Chapter XXXI
Assurance for Temporal Compatibility Using Contracts ... 360
Omkar J. Tilak, Indiana University-Purdue University Indianapolis, USA Rajeev R. Raje, Indiana University-Purdue University Indianapolis, USA Andrew M. Olson, Indiana University-Purdue University Indianapolis, USA
Chapter XXXII
Spatial Authentication Using Cell Phones ... 372
Section IV Mitigating Security Risks Chapter XXXIII
Plugging Security Holes in Online Environment ... 382
Sushil K. Sharma, Ball State University, USA
Jatinder N.D. Gupta,The University of Alabama in Huntsville, USA Ajay K. Gupta, Gsecurity, Inc., USA
Chapter XXXIV
Six Keys to Improving Wireless Security ... 393
Erik Graham, General Dynamics C4 Systems, USA Paul John Steinbart, Arizona State University, USA
Chapter XXXV
Human Factors in Information Security and Privacy ... 402
Robert W. Proctor, Purdue University, USA E. Eugene Schultz, High Tower Technologies, USA Kim-Phuong L. Vu, California State University, USA
Chapter XXXVI
Threat Modeling and Secure Software Engineering Process ... 415 Wm. Arthur Conklin, University of Houston,USA
Chapter XXXVII
Guarding Corporate Data from Social Emgineering Attacks ... 423
Christopher M. Botelho, Baylor Health, USA Joseph A. Cazier, Appalachian State University, USA
Chapter XXXVIII
Data Security for Storage Area Networks ... 433
Tom Clark, Brocade Communications, USA
Chapter XXXIX
Security Awareness: Virtual Environments and E-Learning ... 441
Edgar Weippl, Vienna University of Technology and Science, Austria & Secure Business, Austria
Chapter XL
Security-Efficient Identity Management Using Service Provisioning (Markup Language) ... 447
Manish Gupta, State University of New York, Buffalo, USA Raj Sharman, State University of New York, Buffalo, USA
Chapter XLI
A Strategy for Enterprise VoIP Security ... 458
Jose M. Sarriegi, TECNUN University of Navarra, Spain Javier Santos, TECNUN University of Navarra, Spain
Chapter XLIII
Privacy, Societal, and Ethical Concerns in Security ... 483
Rebecca H. Rutherfoord, Southern Polytechnic State University, USA
Chapter XLIV
An MDA Compliant Approach for Designing Secure Data Warehouses ... 495
Rodolfo Villarroel, Universidad Católica del Maule, Chile
Eduardo Fernández-Medina, Universidad de Castilla-La Mancha, Spain Mario Piattini, Universidad de Castilla-La Mancha, Spain
Juan Trujillo, Universidad de Alicante, Spain
Chapter XLV
Survivability Evaluation Modeling Techniques and Measures ... 504
Hai Wang, The Pennsylvania State University, USA Peng Liu, The Pennsylvania State University, USA
Chapter XLVI
The Last Line of Defense: A Comparison of Windows and Linux Authentication and
Authorization Features ... 518
Art Taylor, Rider University, USA
Chapter XLVII
Bioterrorism and Biosecurity ... 529
M. Pradhan, Indiana University-Purdue University Indianapolis, USA Y. Xia, Indiana University-Purdue University Indianapolis, USA
About the Contributors ... 537
Detailed Table of Contents
Preface ... xxiv
Acknowledgment ...xxviii
Section I Enterprise Security
As new technologies emerge, organizations recognize the need for enterprise security solutions. Enterprise security is important to almost all organizations. Seven chapters in Section I discuss various kinds of security threats that enterprises face today. This section also dwelves upon the risk management, audit and control approaches that could be used for security assurances in a variety of business environemnt, including e-commerce. The synopsis of each chapter is outlined below:
Chapter I
Ransomware: A New Cyber Hijacking Threat to Enterprise ... 1
Xin Luo, The University of New Mexico, USA
Qinyu Liao, The University of Texas at Brownsville, USA
The first chapter, titled “Ransomware: A New Cyber Hijacking Threat to Enterprise” by Xin Luo and Qinyu Liao, attempts to discover the surreptitious features of ransomware in information systems security research. This chapter proposes a ransomware extortion scheme, compares ransomware with other malware, and discusses future trends and research directions.
Chapter II
E-Commerce: The Benefits Security Risks, and Countermeasures ... 7
Joon S. Park, Syracuse University, USA Jillian K. Lando, Syracuse University, USA
Pamela Ajoku, in her chapter, “Information Warfare: Survival of the Fittest”,presents a basic understanding of the concept of Information Warfare (IW) and the need for relevant strategies to aid its successful implementation. Based on the adaptive nature of IW, she discusses a Survival of the Fittest IW (SFIW) conceptual framework and uses a case study is for its validation.
Chapter IV
Evolution of Enterprise Security Federation ... 29
Gaeil An, Electronics and Telecommunications Research Institute, Korea Joon S. Park, Syracuse University, USA
In their chapter on “Evolution of Enterprise Security Federation”, Gaeil An and Joon S. Park discuss the evolution of enterprise security federation, including why the framework should be evolved and how it has been developed and applied to real systems. They analyze the vulnerabilities and weaknesses in current security approaches. This leads them to propose the Policy-based Security Management (PSM) architecture for an integrated security framework and the Packet-Marking (PM) architecture for a cooperative security framework. The simulation result shows that the PSM architecture can automatically detect and respond against network attacks and the PM architecture can
effectively handle suspicious traffic such as DDoS traffics.
Chapter V
A Holistic Approach to Information Security Assurance and Risk Management in an
Enterprise ... 42
Roy Ng, Ryerson University, Canada
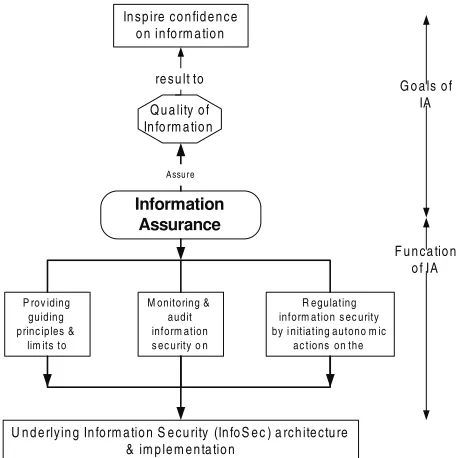
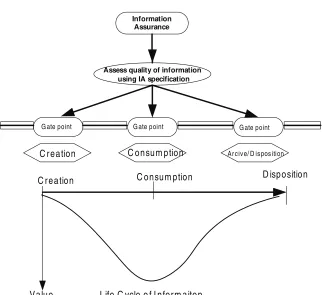
The chapter, “A Holistic Approach to Information Security Assurance and Risk Management in an Enterprise”, by Roy Ng discusses a holistic approach to information security assurance and risk management in an enterprise. The “information life cycle” with its stage value and the underlying security operatives (gate-points) is designed to protect the information. The “information assurance” framework and its functions are designed to audit the information security implemented in an enterprise. The author suggests that an organization must assess the value and the business impact of the information so that optimal and effective security and assurance systems can be designed.
Chapter VI
An Integrative Framework for the Study of Information Security Management Research ... 55
John D’ Arcy, University of Notre Dame, USA Anat Hovav, Korea University, Korea
The chapter, “An Integrative Framework for the Study of Information Security Management Research”,by John D’ Arcy, and Anat Hovav review the current state of information security management (ISM) research and propose an integrative framework for future studies. Using the proposed framework as a guide, they identify areas of depth within current ISM literature and areas where research is underdeveloped. Finally, they call for a more comprehen-sive approach to ISM research that considers multiple dimensions of our framework and their interrelationships.
Chapter VII
Information Systems Risk Management: An Audit and Control Approach ... 68
Aditya Ponnam, Britta Harrison, and Ed Watson, in their chapter on “Information Systems Risk Management: An Audit and Control Control Approach”,review the most common risks and threat agents for a typical organization’s information technology infrastructure. They discuss the manner in which systematic risk management procedures and controls can manage and minimize these risks
Section II
Security Approaches, Frameworks, Tools, and Technologies
As attacks on computer systems are becoming much more sophisticated—and potentially devastating—than they ever were in the past, new and effective tools and technologies are needed to prevent, detect, and correct the security breeches in organizations. Sixteen chapters in Section II of this handbook describe the development, implementation, and application of various approaches, tools, technologies, and frameworks for effective information assurance and security protection in various types of enterprises.The synopsis of each chapter is outlined below:
Chapter VIII
Distributed Denial of Service Attacks in Networks ... 85
Udaya Kiran Tupakula, Macquarie University, Australia Vijay Varadharajan, Macquarie University, Australia
Udaya Kiran Tupakula and Vijay Varadharajanin their chapter “Distributed Denial of Service Attacks in Networks” explain how DDoS attacks are performed and what best could be done for defending against the DDoS attacks in the Internet. They thoroughly analyse some of the important techniques that have been recently proposed. They also outline some best practices that the users are urged to follow to minimize the DoS attacks in the Internet.
Chapter IX
Firewalls as Continuing Solutions for Network Security ... 98
Andy Luse, Iowa State University, USA Anthony Townsend, Iowa State University, USA Kevin Scheibe, Iowa State University, USA
This chapter is designed as an introductory tutorial to the underlying concepts of firewall technologies. In this chapter, Andy Luse, Anthony Townsend, and Kevin Scheibe describe various firewall conventions and how these
technologies operate when deployed on a corporate network. Highly neglected internal security mechanisms
uti-lizing firewall technologies are presented including host-based firewalls and the more novel distributed firewall
implementations.
Chapter X
An Immune-Inspired Approach to Anomaly Detection ... 109
Jamie Twycross, University of Nottingham, UK Uwe Aickelin, University of Nottingham, UK
The chapter on“An Immune-Inspired Approach to Anomaly Detection”, byJamie Twycross and Uwe Aickelin
show that, through realistic testing and validation, second generation artificial immune systems are capable of
anomaly detection beyond generic system policies. The chapter also outlines the next steps in this exciting area of computer security.
Chapter XI
Cryptography for Information Security ... 122
application in protocols, communications, and e-mails.
Chapter XII
Memory Corruption Attacks, Defenses, and Evasions ... 139
Carlo Bellettini, Università degli Studi di Milano, Italy Julian L. Rrushi, Università degli Studi di Milano, Italy
Carlo Bellettini and Julian L. Rrushi, in their chapter “Memory Corruption Attacks, Defenses, and Evasions”, describe representative defense mechanisms to protect from both basic and advanced exploitation of low-level coding vulnerabilities. These authors argue that most of the defensive techniques protect only from a limited set of attack techniques, thus a defense employment requires multiple complementary mitigation techniques. In response to these limitations, these authors propose better defensive mechanisms such as pointer taintedness detection and attack data burning capable of countering any kind of control-data or pure-data attack.
Chapter XIII
Design and Implementation of a Distributed Firewall ... 152
Dalila Boughaci, LRIA – USTHB, Algeria Brahim Oubeka, LRIA – USTHB, Algeria Abdelkader Aissioui, LRIA – USTHB, Algeria Habiba Drias, LRIA – USTHB, Algeria
Belaïd Benhamou, Technopôle de Château-Gombert, France
Dalila Boughaci, Brahim Oubeka, Abdelkader Aissioui, and Habiba Drias, in their chapter “Design and Implemen-tation of a Distributed Firewall”, discuss the design and implementation of a decentralized firewall. The proposed
framework includes a set of controllers’ agents that ensure the packets filtering services, a proxy agent that plays a role of a proxy server, and an identifier agent which is responsible for user authentication.
Chapter XIV
A Formal Verification Centred Development Process for Security Protocols ... 165
Tom Coffey, University of Limerick, Ireland Reiner Dojen, University of Limerick, Ireland
This chapter on “A Formal Verification Centered Development Process for Security Protocols”, byTom Coffey and
Reiner Dojen discusses the importance of formal verification of security protocols prior to their release. A discus
-sion on logic-based verification of security protocols and its automation provides the reader with an overview of the current state-of-the-art of formal verification of security protocols. The authors propose a formal verification centered development process for security protocols. This process provides strong confidence in the correctness
and reliability of the designed protocols.
Chapter XV
Edge-to-Edge Network Monitoring to Detect Service Violations and DoS Attacks ... 179
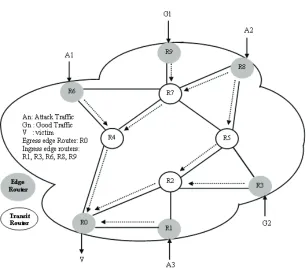
Ahsan Habib, Siemens TTB Center, Berkeley, USA
This chapter, “Edge-to-Edge Network Monitoring to Detect Service Violations and DoS Attacks”, byAhsan Habib, proposes a distributed monitoring scheme that uses edge-to-edge measurements to identify congested links. The
proposed scheme captures the misbehaving flows that violate service-level-agreements and inject excessive traf
and computation overhead among monitoring schemes. Results in this chapter show that, compared to edge-to-edge network monitoring scheme, core-assisted network monitoring has higher communication and computation overhead.
Chapter XVI
A “One-Pass” Methodology for Sensitive Data Disk Wipes ... 193
Doug White, Roger Williams University, USA Alan Rea, Western Michigan University, USA
Doug White and Alan Rea, in their chapter “A ‘One-Pass’ Methodology for Sensitive Data Disk Wipes,” argue that hard disk wipes are a crucial component of computing security. These authors argue that when an organization does not follow a standard disk wipe procedure, the opportunity to expose sensitive data occurs. The chapter proposes
the one-pass methodology, verified with a zero checksum, which is more than adequate for organizations wishing
to protect against the loss of sensitive hard drive data.
Chapter XVII
Securing E-Mail Communication with XML Technology ... 202
Lijun Liao, Horst-Görtz Institute for IT Security, Germany Mark Manulis, Horst-Görtz Institute for IT Security, Germany Jörg Schwenk, Horst-Görtz Institute for IT Security, Germany
This chapter, “Securing E-mail Communication with XML Technology”, byLijun Liao, Mark Manulis, and Jörg Schwenk, discusses the most popular security mechanisms and standards related to the e-mail communication and identify potential threats and vulnerabilities. Authors suggest a new approach, called XMaiL, which can be con-sidered as an advanced e-mail security mechanism based on the popular XML technologies. The proposed XMaiL
supersedes all currently available e-mail security standards in the sense of the higher flexibility and security.
Chapter XVIII
Aspect-Oriented Analysis of Security in Distributed Virtual Environment ... 218
Li Yang, University of Tennessee at Chattanooga, USA Raimund K. Ege, Northern Illinois University, USA
Lin Luo, Florida International University, USA
The chapter by Li Yang, Raimund K. Ege, and Lin Luo, “Aspect-Oriented Analysis of Security in Object-Oriented Distributed Virtual Environments”,describes an approach to handle security in a complex Distributed Virtual En-vironment (DVE). This chapter illustrates an aspect-oriented approach to the impact analysis of security concerns upon the functionalities of DVEs. A design-level security model for DVEs is provided to show how to weave security concerns into the models of DVE designs seamlessly.
Chapter XIX
Information Availability ... 230
Deepak Khazanchi, University of Nebraska at Omaha, USA Andrew P. Martin, University of Nebraska at Omaha, USA
Deepak Khazanchi and Andrew P. Martin in their chapter, “Information Availability”, discuss the notion of
infor-mation availability as it relates to inforinfor-mation security and identify key first and second order factors that impact
The next chapter, “Formal Analysis and Design of Authentication Protocols”, bySiraj Ahmed Shaikh, discusses
the concept of formal analysis of authentication protocols. It briefly introduces the basic notions of cryptography
and its use in authentication protocols. The chapter looks at the Needham-Schroeder (1978) protocol as an example of an authentication protocol and examine the history of the protocol as a stimulus to the formal analysis of such protocols.
Chapter XXI
Access Control Frameworks for a Distributed System ... 254
Rajeev R. Raje, Indiana University-Purdue University Indianapolis, USA Alex Crespi, Indiana University-Purdue University Indianapolis, USA Omkar J. Tilak, Indiana University-Purdue University Indianapolis, USA Andrew M. Olson, Indiana University-Purdue University Indianapolis, USA Carol C. Burt, 2AB Inc., Helena, AL, USA
This chapter, “Access Control Framework for Distributed System”,by Rajeev R. Raje, Alex Crespi, Omkar J. Tilak, Andrew M. Olson, and Carol C. Burt, focuses on access control properties of a distributed system. It provides a framework that addresses the issues such as specifying access control properties for individual components, iden-tifying components with required access control properties, and formulating compositional models for predicting the access control properties of a composed system from those of its individual components.
Chapter XXII
Implications of FFIEC Guidance on Authentication in Electronic Banking ... 266
Manish Gupta, State Univerity of New York, Buffalo, USA JinKyu Lee, Oklahoma State University, USA
H.R. Rao, State Univerity of New York, Buffalo, USA
This chapter, “An Implications of FFIEC Guidance on Authentication in Electronic Banking”,byManish Gupta, JinKyu Lee, and H.R. Rao, discusses the Federal Financial Institutions Examination Council (FFIEC)
recom-mendations for reliably authentication methods for financial institutions to deploy security measures. The chapter
will allow Information Technology managers to understand information assurance issues in e-banking in a holistic manner and will help them make recommendations and actions to ensure security of e-banking components.
Chapter XXIII
Disruptive Technology Impacts on Security ... 279
Sue Conger, University of Dallas, USA Bret J. L. Landry, University of Dallas, USA
Section III
Security Policies and Procedures
Security Policy is a foundational element in any Security Program. The purpose of a general security policy is to outline the legal, privacy, and security-related responsibilities that members of the institution have. Because probing a network for vulnerabilities can disrupt systems and expose private data, organizations need a policy in place to address Acceptable Use Policies. There is also a need for policies and ethical guidelines for making employees understand the appropriate action when illegal materials are found on their systems during a vulnerability scan. Eight chapters in this Section III discuss all those security policy related concerns and issues. The synopsis of each chapter is outlined below.
Chapter XXIV
Internal Auditing for Information Assurance ... 292
Sushma Mishra, Virginia Commonwealth University, USA Amita Goyal Chin, Virginia Commonwealth University, USA
This chapter, “Internal Auditing for Information Assurance”, by Sushma Mishra and Amita Goyal Chin, discusses how auditing helps organizations in internal control assessment, change management, and better governance pre-paredness, thus enhancing information assurance. Various facets of internal auditing are discussed in this chapter and the role of internal auditing in information assurance is analyzed.
Chapter XXV
IT Continuity in the Face of Mishaps ... 301
William H. Friedman, University of Central Arkansas, USA
William Friedman in his chapter “IT Continuity in the Face of Mishaps”, proposes a general theoretical context for IT disasters within the wider class of all types of disasters to which a business is subject—whether caused by natural or human action. He suggests numerous practical and proactive prevention methods that can be applied both before and after an IT disaster.
Chapter XXVI
Business Continuity and Disaster Recovery Plans ... 308
Yvette Ghormley, Saint Leo University, USA
This chapter, “Business Continuity and Disaster Recovery Plans”, by Yvette Ghormley, describes the tools that businesses can use to create a business continuity and disaster recovery plan. Author argues that business continuity and disaster recovery plan are much more likely to survive than businesses that do not have such a plan.
Chapter XXVII
Security Policies and Procedures ... 320
Yvette Ghormley, Saint Leo University, USA
Arif Ghafoor, Purdue University, USA Aditya Mathur, Purdue University, USA
This chapter, “Enterprise Access Control Policy Engineering Framework”, by Arjmand Samuel, Ammar Masood, Arif Ghafoor, and Aditya Mathur, outlines the overall access control policy engineering framework in general and discusses the subject of validation of access control mechanisms in particular. Requirements of an access control policy language are introduced and their underlying organizational philosophy is discussed.
Chapter XXIX
Information Security Policies: Precepts and Practices ... 341
Sushil K. Sharma, Ball State University, USA
Jatinder N.D. Gupta, The University of Alabama at Huntsville, USA
Sushil Sharma and Jatinder Gupta, in their chapter “ExaminingIS Security Policies for Organizations: Precepts and Practices”, review the IS security framework and examine few security policies of few organizations.
Chapter XXX
A Guide to Non-Disclosure Agreements for Researchers ... 347
Paul D. Witman, California Lutheran University, USA Kapp L. Johnson, California Lutheran University, USA
Paul Witman and Kapp Johnson, in their chapter “Guide to Non-Disclosure Agreements for Researchers”, describe a set of guidelines to assist information assurance and security researchers in creating, negotiating, and reviewing non-disclosure agreements, in consultation with appropriate legal counsel. It also reviews the use of non-disclosure agreements in academic research environments from multiple points of view.
Chapter XXXI
Assurance for Temporal Compatibility Using Contracts ... 360
Omkar J. Tilak, Indiana University-Purdue University Indianapolis, USA Rajeev R. Raje, Indiana University-Purdue University Indianapolis, USA Andrew M. Olson , Indiana University-Purdue University Indianapolis, USA
This chapter, “Assurance for Temporal Compatibility Using Contracts”, by Omkar Tilak, Rajeev Raje, and Andrew Olson, depicts a formal method to specify component interactions involving temporal constraints. Using the
com-ponent interactions, various types of temporal interaction compatibility classes are defined. A simple case study is presented that indicates the benefits of the component interaction specifications are discussed.
Chapter XXXII
Spatial Authentication Using Cell Phones ... 372
Arjan Durresi,Indiana University-Purdue University Indianapolis, USA
Section IV Mitigating Security Risks
While the new regulations and statutes are sure to get some attention, the pressure to mitigate data security risks certainly increases. It is becoming increasingly obvious then that inadequate data policies and data security measures can have very costly consequences. Organizations for mitigating security risks invest substantial resources developing complicated solutions that are critical to daily operations and long term success. Therefore, the 15 chapters in this section discuss ways and means to mitigate the security risks. The synopsis of each chapter is outlined below:
Chapter XXXIII
Plugging Security Holes in Online Environment ... 382
Sushil K. Sharma, Ball State University, USA
Jatinder N.D. Gupta, The University of Alabama in Huntsville, USA Ajay K. Gupta, Gsecurity, Inc., USA
This chapter, “Plugging Security Holes in Online Environment”, by Sushil Sharma, Jatinder Gupta, and Ajay Gupta, points out the various security holes in online environments and suggests a comprehensive framework to defend against these security holes.
Chapter XXXIV
Six Keys to Improving Wireless Security ... 393
Erik Graham, General Dynamics C4 Systems, USA Paul John Steinbart, Arizona State University, USA
Erik Graham and Paul John Steinbart in their chapter ”Six Keys to Improving Wireless Security”, discuss a step-by-step approach to improve the security of wireless networks. It describes the basic threats to achieving the security
objectives of confidentiality, integrity, and availability when using wireless networking. It also explains various
countermeasures that can be used to reduce the risks associated with wireless networks.
Chapter XXXV
Human Factors in Information Security and Privacy ... 402
Robert W. Proctor, Purdue University, USA E. Eugene Schultz, High Tower Technologies, USA Kim-Phuong L. Vu, California State University, USA
This chapter, “Human Factors in Information Security and Privacy”, by Robert Proctor, Eugene Schultz, and Kim-Phuong Vu, reviews basic components of information security and privacy with an emphasis on human factors issues. The authors conclude by discussing how human factors analyses can lead to the design of usable systems for information security and privacy assurance.
Chapter XXXVI
Threat Modeling and Secure Software Engineering Process ... 415 Wm. Arthur Conklin, University of Houston,USA
Christopher Botelho and Joseph Cazier, in their chapter “Guarding Corporate Data from Social Engineering Attacks”,discuss the results of a social engineering attack based on a survey conducted in the downtown area of
a large financial center in the United States. The authors suggest that corporate policies should include ways to
protect their employees and systems from intrusions based on social engineering attacks.
Chapter XXXVIII
Data Security for Storage Area Networks ... 433
Tom Clark, Brocade Communications, USA
This chapter, “Data Security for Storage Area Networks”, by Tom Clark, provides an overview of storage networking technology and the security mechanisms that have been developed to provide data integrity for data center storage infrastructures. The authors argue that data storage is playing an increasingly visible role in securing application data in the data center. He suggests that the established and emerging Fibre Channel and IP standards are required to secure the storage infrastructure and protect data assets from corruption or misappropriation.
Chapter XXXIX
Security Awareness: Virtual Environments and E-Learning ... 441
Edgar Weippl, Vienna University of Technology and Science, Austria & Secure Business, Austria
This chapter, “Security Awareness: Virtual Environments and E-Learning”, by Edgar Weippi, outlines advanced options for security training. The author lists various examples that characterize successful programs. The author cooperated with ENISA (http://www.enisa.eu.int/) to create a new multi-language awareness training program that uses virtual environments to allow users to train on real systems without any danger.
Chapter XL
Security-Efficient Identity Management Using Service Provisioning (Markup Language) ... 447
Manish Gupta, State University of New York, Buffalo, USA Raj Sharman, State University of New York, Buffalo, USA
This chapter, titled “Security-Efficient Identity Management Using Service Provisioning (Markup Language)”, by Manish Gupta and Raj Sharman, outlines how imminent technologies such as Provisioning and Identity Man-agement, leverage information security and productivity in an organization. This chapter also discusses SPML
architecture and benefits of using SPML in detail.
Chapter XLI
A Strategy for Enterprise VoIP Security ... 458
Dwayne Stevens, Community Trust Bank, USA David T. Green, Governors State University, USA
Dwayne Stevens and David Green, in their chapter “A Strategy for Enterprise VoIP Security”, describe how Voice over Internet Protocol (VoIP) networks can be protected against various kinds of attacks such as: DOS attacks, crash
Chapter XLII
Critical Success Factors and Indicators to Improve Information Systems Security Management
Actions ... 467
Jose M. Torres, TECNUN University of Navarra, Spain Jose M. Sarriegi, TECNUN University of Navarra, Spain Javier Santos, TECNUN University of Navarra, Spain
This chapter, “Critical Success Factors and Indicators to Improve Information Systems Security Management Actions”, by Jose Torres, Jose Sarriegi, and Javier Santos, presents an Information Systems Security Management Framework (ISSMF) which encapsulates 11 Critical Success Factors (CSFs) along with a set of 62 indicators to
properly manage and track the evolution of security management models. These CSFs have been identified as the
most cited key factors published in the current information security literature.
Chapter XLIII
Privacy, Societal, and Ethical Concerns in Security ... 483
Rebecca H. Rutherfoord, Southern Polytechnic State University, USA
Rebecca Rutherfoord, in her chapter “Privacy, Societal, and Ethical Concerns in Security”, discusses issues of privacy, societal, and ethical concerns in enterprise security. She argues that privacy of individual’s data must be considered both internally and externally and laws protecting corporations and individuals need to be understood to keep a company from being liable for infringements of unprotected data.
Chapter XLIV
An MDA Compliant Approach for Designing Secure Data Warehouses ... 495
Rodolfo Villarroel, Universidad Católica del Maule, Chile
Eduardo Fernández-Medina, Universidad de Castilla-La Mancha, Spain Mario Piattini, Universidad de Castilla-La Mancha, Spain
Juan Trujillo Universidad de Alicante, Spain
This chapter, “An MDA Compliant Approach for Designing Secure Data Warehouse”, by Rodolfo Villarroel, Eduardo Fernández-Medina, Mario Piattini, and Juan Trujillo, presents an approach for designing secure data warehouses (DWs) that accomplish the conceptual modeling of secure DWs independently from the target platform where the DW has to be implemented. Authors claim that their complete approach follows the model driven architecture (MDA) and the model driven security (MDS).
Chapter XLV
Survivability Evaluation Modeling Techniques and Measures ... 504
Hai Wang, The Pennsylvania State University, USA Peng Liu, The Pennsylvania State University, USA
In his chapter “The Last Line of Defense: A Comparison of Windows and Linux Authentication and Authorization Features”, Art Taylor states that, although much attention has been focused on the role of the network in security attacks, evidence suggests that the computer server and its operating system deserve closer examination since it is ultimately the operating system and its core defense mechanisms of authentication and authorization which are compromised in an attack. This chapter provides an exploratory and evaluative discussion of the authentication and authorization features of two widely used server operating systems: Windows and Linux.
Chapter XLVII
Bioterrorism and Biosecurity ... 529
M. Pradhan, Indiana University-Purdue University Indianapolis, USA Y. Xia, Indiana University-Purdue University Indianapolis, USA
This chapter, “Bioterrorism and Biosecurity”, by M. Pradhan and Y. Xia, gives a picture how information technol-ogy can be used to combat bio-terrorism. Also, this chapter gives an understanding of different Bioinformatics techniques and tools that are widely used for biosecurity measures.
About the Contributors ... 537
xxiv
Preface
Information Systems and Technology have evolved to a level that its use is becoming a common occurrence. While the academic profession is still debating the utility or value of Information Systems and Technology, its use in organizations all over the globe is rising at an increasing rate. However, this widespread use of information systems and technology is not without its associated problems. While several emerging information and internet ubiquitous technologies provide tremendous positive opportunities, there are still a number of vulnerabilities and risks
associ-ated with technology systems. Organizations invest heavily in the latest firewalls, intrusion detection systems and
other advanced security technologies, yet losses from security incidents continue to grow each year. According to the Computer Emergency Response Team at Carnegie Mellon University, during 2003 and 2004, approximately 42,000 cyber incidents were reported. As technologies advance, hackers also advance their tools, techniques, and methods to break-ins. Up until a few years ago, phishing attacks (phony e-mails designed to entice users to give up personal information) were unheard of. Now they are relatively common and pharming (creating phony Web sites designed to extract personal information) has become one of the latest strategies employed by identity thieves. Security experts noted that the legions of infected computers are adding to the number of bot networks controlled by hackers. Symantec observed an average of 10,352 active bot network computers per day, an increase of more than 140 percent from the previous reporting period’s 4,348 bot computers. According to Symantec, denial-of-service attacks grew from an average of 119 per day to 927 per day since January 2005, a 680 percent increase over the previous six months.
As a result of the above risks associated with the deployment of Information Systems and Technology, infor-mation assurance and security has become an important research issue in networked and distributed inforinfor-mation sharing environments. Finding effective ways to protect information systems, networks, and sensitive data within the critical information infrastructure is challenging even with the most advanced technology and trained profes-sionals. Information assurance and security has become an important research issue in networked and distributed information sharing environments. In today’s companies, information systems not only support business functions but are also an integral part of business operations. For example, ERP systems (Enterprise Resource Planning) are now essential for organizations and their supply chains. Incorrect information in ERP systems can have seri-ous consequences for the inter-networked companies. Information securitymeans protecting information from malicious threats and damage due to external or internal sources. Assurance in computer security is a measure of
confidence that the security features and architecture of an automated information system accurately mediate and
enforce the security policy.
Information assurance combines the requirements of information security, integrity, and significance. Assuring
information means having a safe information system, which guarantees that information is secure and at the same
time keeps its integrity and its significance during its lifetime. The goal of information assurance is to provide trustworthy and significant information to users in operational, service systems that rely on the information for the fulfillment of their objectives. However, despite an organization’s best efforts at protection, there have been and
will continue to be breaches, even as IT security improves. The difference now is that companies are required to
report on more of their financial information than ever before. Sarbanes Oxley, Gramm-Leach-Bliley, PCI stan -dards, and HIPAA regulations, each in different ways, mandate that companies and executives be accountable for the integrity of their customers’ data as well as the company’s bottom line.
processes, techniques, and tools that are required to protect data and systems. An enterprise security handbook that includes methodologies, techniques, and methods to protect data and systems would be a great contribution to practitioners as well as academicians.
To create such a handbook of research on information assurance and security, we decided to launch this hand-book project where researchers from all over the world were invited to contribute. The primary objective of this project was to assemble as much research coverage as possible related to the information security and assurance. As you would agree that information security and assurance subject is not only challenging but also continuously changing. The idea behind this project was to gather latest information from researchers worldwide on information security and assurance. Therefore, in order to provide the best balanced coverage of concepts and issues related to the selected topics of this handbook, researchers from around the world were asked to submit proposals describ-ing their proposed coverage and the contribution of such coverage to the handbook. All proposals were carefully reviewed by the editors in light of their suitability as well as the researchers’ record of similar work in the area of the proposed topics.
The goal was to assemble the best minds in the information security and assurance field from all over the world
to contribute to the handbook. Upon the receipt of full chapter submissions, each submission was forwarded to expert external reviewers on a double-blind, peer review basis. Only submissions with strong and favorable re-views were chosen as chapters for this handbook. In many cases, submissions were sent back for several revisions
prior to final acceptance. As a result, this handbook includes 47 chapters highlighting current concepts, issues, and
emerging technologies. All entries are written by knowledgeable, distinguished scholars from many prominent research institutions around the world. The authors who have contributed to this book are well known security experts who have been doing research on various aspects of information assurance and security for several years
and have tried to present their technical work in most lucid and simple words. It is hoped that readers will find it
easy to understand and implement some of suggested approached to protect their organizations from various kind of security attacks and breaches.
This handbook or organized into four broad sections to cover a variety of topics related to the identification, specification, correction, and mitigation of the security threats in varying conditions. In each case, the role of information assurance and security are clearly identified. Brief description of each section and the coverage of
various chapters in each section is provided below.
Section I, titled Enterprise Security, starts the discussion of informaion assurance and security issues. As en-terprises are becoming increasingly dependent on their information systems, Information assurance and security has become an important aspect for safety of their data, information, and systems. Finding effective ways to protect information systems, networks, and sensitive data within the critical information infrastructure is challenging even with the most advanced technology and trained professionals. Information systems security and assurance is a complicated subject, and historically only tackled by well-trained and experienced experts. However, as more and more companies are networked and have started using pervasive computing technologies, an increasing number of people need to understand the basics of security in a networked world. Enterprise security is important to almost all organizations. As new technologies emerge, organizations must recognize the need for enterprise security solu-tions. The seven chapters in Section 1 discuss various kinds of security threats that enterprises face today. Various chapters in this section also dwelves upon the risk management, audit, and control approaches that could be used for security assurances in a variety of business environment, including e-commerce.
xxvi
Section III, titled Security Policies and Procedures, is devoted to the important topic of Information security polices and procedures. Security Policy is a foundational element in any Security Program. The purpose of a general security policy is to outline the legal, privacy, and security-related responsibilities that members of the institution have. Because probing a network for vulnerabilities can disrupt systems and expose private data, organizations need a policy in place to address Acceptable Use Policies. There is also a need for policies and ethical guidelines for making employees understand the appropriate action when illegal materials are found on their systems during a vulnerability scan. Eight chapters in Section 3 discuss those various security policy related concerns and issues and offer suggestions for the information assurance and security researchers and practitioners. The discussion in these chapters also discusses the need for effective business continuity and disaster recovery plans and the means to develop, implement, and use these plans to minimize the disruptions in business continuity.
Section IV of this handbook deals with is the topicof Mitigating Security Risks. While the new regulations and statutes are sure to get some attention, the pressure to mitigate data security risks certainly increases. It is becoming increasingly obvious then that inadequate data policies and data security measures can have very costly consequences. Regardless of the solutions employed to reduce the risk of data security breaches, a balance of prevention strategies and mitigation efforts is likely the best possible protection. In fact, given how dependent modern business is on electronic data transmissions, it may no longer be an option to develop a data protection strategy. In order to mitigate security risks, organizations invest substantial resources in developing complicated
solutions that are critical to daily operations and long term success. Fifteen chapters in this final section of the
handbook describe various developments in identifying and mitigating information assurance and security risks in various types of organizations. The authors of these various chapters also suggest some guidelines to effectively implement risk mitigating solutions including the use of biosecurity measures to understand and mitigate the bioterrorism threats.
This handbook is written with the basic computer user and information systems manager in mind, explaining the concepts needed to read through the hype in the marketplace and understand risks and how to deal with them. Companies need not only to invest in more sophisticated security tools and technologies but also to educate their employees about security and assurances. The market is challenged with an increased need for security and as-surance to present security in terms the audience can understand and hopefully this book will do an excellent job of meeting that challenge. Therefore, this handbook is also written for the academic and professional researcher interested in developing appropriate and state-of-the-art tools, techniques, and approaches to deals with various issues arising in information assurance and security.
It is hoped that the diverse and comprehensive coverage of information security and assurance in this authoritative
handbook will contribute to a better understanding all topics, research, and discoveries in this evolving, significant field of study. Furthermore, we hope that the contributions included in this handbook will be instrumental in the expansion of the body of knowledge in this vast field. The coverage of this handbook of research on information
assurance and security provides a reference resource for both information science and technology researchers and also decision makers in obtaining a greater understanding of the concepts, issues, problems, trends, challenges,
and opportunities related to this field of study. It is our sincere hope that this publication and its great amount of
information and research will assist our research colleagues, faculty members, students, and organizational deci-sion makers in enhancing their understanding of the current and emerging issues in information assurance and security. Perhaps this publication will even inspire its readers to contribute to the current and future discoveries
in this immense field, tapping possibilities to assist humankind in making the world a better place to live for all
its inhabitants.
Jatinder N. D. Gupta
The University of Alabama in Huntsville
Sushil K. Sharma
Acknowledgment
This book would not have been possible without the cooperation and assistance of many people: the authors, reviewers, our colleagues, and the staff at IGI Global. The editors would like to thank Mehdi Khosrow-Pour for inviting us to produce this book, Jan Travers for managing this project, and Jessica Thompson and Heather Probst as assistant managing development editors for answering our questions and keeping us on schedule. Many of the authors of chapters in this book also served as reviewers of other chapters, and so we are doubly appreciative of their contributions. We also acknowledge our respective universities for supporting us for this project. Finally, the editors wish to acknowledge their families for their support throughout the project.
Section I
Chapter I
Ransomware:
A New Cyber Hijacking Threat to
Enterprises
Xin Luo
The Univeristy of New Mexico, USA
Qinyu Liao
The University of Texas at Brownsville, USA
ABSTRACT
In computer virology, advanced encryption algorithms, on the bright side, can be utilized to effectively protect valuable information assets of enterprises. Yet, on the dark side, they can also be of use for malicious attackers to conduct pernicious activities. This article attempts to discover the surreptitious features of ransomware and to address it in information systems security research. It intends to elicit attention from enterprises with regard to ransomware—a newly emerged cyber hackjacing threat using such encryption technology as RSA—and to help both academic researchers and IT practitioners understand the technological characteristics of ransomware, along with its severity analysis. As ransomware infections continue to rise, and attacks employing refined algorithm become increasingly sophisticated, data protection faces serious challenges. This chapter draws a ransomware extortion scheme, compares ransomware with other malware, and discusses future trends and research directions in an effort to cater to both practitioners and researchers.
INTRODUCTION
Today’s enterprises confront not only keen peer com-petitions in business society, but also increasingly sophisticated information security threats in cyber-world, as online presence and business transaction
are considered as a possible profit-driven avenue and
a necessary means for global competence. In computer virology, as technologies continue to evolve, advanced encryption algorithms, on the bright side, can be utilized to effectively protect valuable information assets of enterprises. On the dark side, however, they can also be employed by malicious attackers to conduct pernicious
activities in search of profits or benefits. Past informa
-tion systems security research has investigated such malware programs as Trojan horse, worms, and spyware
from a plethora of scientific perspectives (Warkentin,
Luo, & Templeton, 2005), and relevant strategies and tactics have been proposed to alleviate and eradicate the cyber threats (Luo, 2006).
victim-2
Ransomware
izes Internet users by hijacking user files, encrypting
them, and then demanding payment in exchange for the decryption key. Seeking system vulnerabilities, ransomware invariably tries to seize control over the
victim’s files or computer until the victim agrees to the
attacker’s demands, usually by transferring funds to the designated online currency accounts such as eGold or Webmoney or by purchasing a certain amount of pharmaceutical drugs from the attacker’s designated online pharmacy stores.
This chapter attempts to discover the surreptitious features of ransomware, and to address it in information systems security research. In an effort to cater to both security practitioners and researchers, the rest of this chapter is organized in four parts. Part 1 will address ransomware’s underpinning structures (recent statistics and attack methodologies of ransomware infection are also offered); Part 2will compare the technological dif-ferences between ransomware and Trojan horse, worm, and spyware (a sample attack scheme will be listed to address the attacking process); Part 3 will discuss the future trend of ransomware in terms of technological sophistication level; and Part 4 will propose the recom-mendations for antiransomware.
IN-DEPTH ANALYSIS: HOW
RANSOMWARE WORKS
In the cyber world, computer users have faced certain types of threat such as worms, spyware, phishing, viruses, and other malware. Ransomware is an extor-tion scheme whereby attackers hijack and encrypt the
victim’s computer files, and then demand a ransom from the victim for these files in original condition. Kasper -sky, one of the global leading antivirus companies, warned that ransomware is a serious threat, because there is no way to recover the effected data.
We thereby define ransomware as a piece of
pernicious software that exploits a user’s computer vulnerabilities to sneak into the victim’s computer and
encrypt all his/her files; then the attacker keeps the files locked unless the victim agrees to pay a ransom.
In a typical ransomware attack, the attacker reaches into a compromised computer by seeking the exposed system vulnerabilities. If this system was victimized earlier by a worm or Trojan, the attacker can easily
enter the weakly configured system. He then searches for various types of important files with such extension
names as .txt, .doc, .rft, .ppt, .chm, .cpp, .asm, .db, .db1, .dbx, .cgi, .dsw, .gzip, .zip, .jpg, .key, .mdb, .pgp .pdf.
Knowing these files are of possible crucial importance to the victims, he then encrypts these files, making them
impossible for the victim or owner to access. Later, the attacker sends the victim an e-mail ransom or pop-up window demanding for the encryption key that unlocks
the frozen files.
Once the attacker locates these files, there are several
processing strategies that he might implement. First, he
can compress all the located files into a password-pro -tected zip package, then he removes the entire original
files; second, he can individually encrypt each located file, and then remove the original files. For example, if the original file is “DissertationFinalVersion.doc,”
ransomware will create a file such as “ Encrypted_Dis-sertationFinalVersion.doc” in order to label the original
file; third, the attacker might create a hidden folder and move all the located files to this folder, produc -ing a pseudophase to deceive the victim. The third strategy, of course, carries the slightest damage, and is comparatively feasible for the victim to retrieve all
the “lost” files.
Furthermore, when ransomware attacks success-fully take control of an enterprise’s data, the attacker encrypts the data using a sophisticated algorithm. The password to the encryption is only released if ransom is paid to the attackers carrying out the attack. The
at-tacker usually notifies the victim by means of a striking message, which carries specific instructions as to how the victim reacts to retrieve the lost files. A text file or
a pop-up window message is generally created in the
same folder where files are encrypted. The text file or
message box clearly indicates that all the important
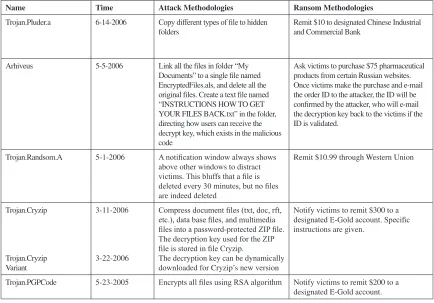
files are already encrypted and informs the victim of specific money remittance methods. Table 1 lists all
the methodologies used by recent ransomware attacks and ransom methodologies as to what the attacker demands for.
MALWARE COMPARISONS
Despite the fact that the infection record is still com-paratively limited, ransomware has become a serious security concern for both businesses and individual computer users. It’s a new form of Internet crime that
extorts computer files. Ransomwares are induced