• Table of Content s • I ndex
MP LS and V PN Ar chi te ctur e s, V olum e I I
By Jim Guichard, I van Pepelnjak, Jeff Apcar
Pub lish er: Cisco Press Pub Dat e: Ju ne 06, 2 00 3
I SBN: 1- 58 705 -1 12 -5 Pages: 50 4
With MPLS and VPN Ar chit ect u res, Volum e I I, you'll lear n :
How to integr ate v ar iou s r em ote access techn ologies in to th e back bone p r ovidin g VPN ser vice to m any d iffer ent typ es of cu stom er s
The n ew PE- CE r out in g op tions as w ell as ot her adv anced feat ur es, includ ing per- VPN Netw ork Ad dr ess Tr an slation ( PE- NAT)
How VRFs can be ex tended into a custom er site to pr ov ide sep ar ation inside t he custom er netw ork
The latest MPLS VPN secur ity featu res an d d esign s aim ed at pr otecting th e MPLS VPN backbone
How to carr y custom er m ulticast tr affic insid e a VPN
The latest in ter - car rier enh ancem ents t o allow for easier and m or e scalable d ep loym ent of inter - car r ier MPLS VPN services
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
• Table of Content s • I ndex
MP LS and V PN Ar chi te ctur e s, V olum e I I
By Jim Guichard, I van Pepelnjak, Jeff Apcar
Pub lish er: Cisco Press Pub Dat e: Ju ne 06, 2 00 3
I SBN: 1- 58 705 -1 12 -5 Pages: 50 4
With MPLS and VPN Ar chit ect u res, Volum e I I, you'll lear n :
How to integr ate v ar iou s r em ote access techn ologies in to th e back bone p r ovidin g VPN ser vice to m any d iffer ent typ es of cu stom er s
The n ew PE- CE r out in g op tions as w ell as ot her adv anced feat ur es, includ ing per- VPN Netw ork Ad dr ess Tr an slation ( PE- NAT)
How VRFs can be ex tended into a custom er site to pr ov ide sep ar ation inside t he custom er netw ork
The latest MPLS VPN secur ity featu res an d d esign s aim ed at pr otecting th e MPLS VPN backbone
How to carr y custom er m ulticast tr affic insid e a VPN
The latest in ter - car rier enh ancem ents t o allow for easier and m or e scalable d ep loym ent of inter - car r ier MPLS VPN services
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced ser vices b ased on MPLS VPN tech nology in a secur e and scalab le w ay.
• Table of Content s
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced
• Table of Content s
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced
Cha pter 4. Vir tu al Rou t er Con nect ivit y
Hierarchical VPNs: Carrier's Carr ier MPLS VPNs VPN Conn ect ivit y Bet ween Different Service Providers
• Table of Content s • I ndex
MP LS and V PN Ar chi te ctur e s, V olum e I I
By Jim Guichard, I van Pepelnjak, Jeff Apcar
Pub lish er: Cisco Press Pub Dat e: Ju ne 06, 2 00 3
I SBN: 1- 58 705 -1 12 -5 Pages: 50 4
With MPLS and VPN Ar chit ect u res, Volum e I I, you'll lear n :
How to integr ate v ar iou s r em ote access techn ologies in to th e back bone p r ovidin g VPN ser vice to m any d iffer ent typ es of cu stom er s
The n ew PE- CE r out in g op tions as w ell as ot her adv anced feat ur es, includ ing per- VPN Netw ork Ad dr ess Tr an slation ( PE- NAT)
How VRFs can be ex tended into a custom er site to pr ov ide sep ar ation inside t he custom er netw ork
The latest MPLS VPN secur ity featu res an d d esign s aim ed at pr otecting th e MPLS VPN backbone
How to carr y custom er m ulticast tr affic insid e a VPN
The latest in ter - car rier enh ancem ents t o allow for easier and m or e scalable d ep loym ent of inter - car r ier MPLS VPN services
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced
Copyright
Cop yr igh t© 2 003 Cisco Sy st em s, I nc.
Cisco Pr ess log o is a trad em ar k of Cisco Sy stem s, I nc.
Pub lished by: Cisco Pr ess
20 1 W est 103 rd Str eet I ndian apolis, IN 462 90 USA
All r ights reserved. No par t of th is book m ay b e repr od uced or tr ansm itted in an y for m or b y any m eans, electr onic or mechan ical, includ in g photocopying, r ecor ding, or by an y
inform ation stor age and r etrieval system , w ithout w r itten p er m ission fr om th e pu blish er , except for t he inclusion of b rief qu otations in a r eview .
Pr inted in th e Un ited States of Am erica 1 2 3 4 5 6 7 8 9 0
Lib rar y of Con gr ess Cataloging- in - Publication Num ber: 61 947 205 1122
Warning and Disclaimer
This b ook is desig ned to pr ovide infor mat ion ab out MPLS an d VPN ar ch itectu res. Every effor t has been m ade to m ake this book as com p lete an d as accur ate as possib le, b ut no w ar r anty or fitness is im p lied.
The in for m ation is p r ovided on an " as is" basis. The au thor s, Cisco Pr ess, and Cisco Syst em s, I nc. shall h ave n eith er liab ility n or r espon sib ility t o any person or entity w ith r espect t o any loss or dam ages ar isin g fr om th e infor m ation con tained in th is book or fr om the u se of the discs or pr ogr am s th at m ay accomp any it.
The op inions expr essed in this b ook belong to the aut hor s and ar e not necessarily th ose of Cisco Sy st em s, I nc.
Trademark Acknowledgments
All ter ms ment ion ed in this b ook that ar e kn ow n t o be trad em ar k s or serv ice mar ks have been ap pr opr iately cap it alized. Cisco Press or Cisco Sy stem s, I nc. cann ot att est to th e accu r acy of th is infor m ation. Use of a ter m in this b ook should not be r egar ded as affectin g the validity of an y tr adem ark or ser v ice m ar k.
Feedback Information
At Cisco Press, our g oal is to cr eate in- d ep th techn ical books of the h ig hest qu alit y and valu e. Each book is cr afted w ith car e an d p recision , und er g oin g r igor ous developm ent that in volves the uniqu e exp er tise of m em ber s from the pr ofessional technical com m unity .
Reader s' feed back is a n atur al continu ation of this pr ocess. I f you h ave any com ments r eg ar ding how w e cou ld im pr ov e the q uality of this b ook, or other w ise alter it to b ett er su it your n eeds, you can contact us th rou gh e- mail at feedback@ciscopr ess.com. Please make sur e to in clu de th e book title an d I SBN in your m essag e.
• Table of Content s
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced We g reatly app r eciate your assistan ce.
Pub lisher John Wait
Ed it or- I n - Chief John Kane
Cisco Repr esent ative Anth ony Wolfen den
Cisco Pr ess Pr ogr am Manager Sonia Torr es Ch avez
Man ager, Mar keting Com m unications, Cisco Systems Scott Miller
Cisco Mar ketin g Pr og ram Manager Ed ie Quir oz
Tech nical Ed it ors Matt Birkner , Dan Tap pan
• Table of Content s
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced 17 0 W est Tasm an Dr ive Cisco, the Cisco Cer tified I nter netw ork Expert logo, Cisco I OS, the Cisco I OS logo, Cisco Pr ess, Cisco Sy stem s, Cisco System s Capital, the Cisco System s logo, Emp ow er ing the I nter net Gener ation, Enter pr ise/ Solv er , EtherChann el, Ether Sw it ch , Fast Step, Gig aStack , I nter net Qu otien t, I OS, I P/ TV, iQ Exper tise, t he iQ log o, Lig htStr eam, MGX, MI CA, the Netw ork ers logo, Netw ork Regist rar , Packet , PI X, Post- Routing , Pr e- Routing , RateMUX,
Registr ar, Slid eCast , SMARTn et, Strat aView Plu s, Strat m, SwitchPr ob e, TeleRouter ,
• Table of Content s • I ndex
MP LS and V PN Ar chi te ctur e s, V olum e I I
By Jim Guichard, I van Pepelnjak, Jeff Apcar
Pub lish er: Cisco Press Pub Dat e: Ju ne 06, 2 00 3
I SBN: 1- 58 705 -1 12 -5 Pages: 50 4
With MPLS and VPN Ar chit ect u res, Volum e I I, you'll lear n :
How to integr ate v ar iou s r em ote access techn ologies in to th e back bone p r ovidin g VPN ser vice to m any d iffer ent typ es of cu stom er s
The n ew PE- CE r out in g op tions as w ell as ot her adv anced feat ur es, includ ing per- VPN Netw ork Ad dr ess Tr an slation ( PE- NAT)
How VRFs can be ex tended into a custom er site to pr ov ide sep ar ation inside t he custom er netw ork
The latest MPLS VPN secur ity featu res an d d esign s aim ed at pr otecting th e MPLS VPN backbone
How to carr y custom er m ulticast tr affic insid e a VPN
The latest in ter - car rier enh ancem ents t o allow for easier and m or e scalable d ep loym ent of inter - car r ier MPLS VPN services
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced occasions.—I van
• Table of Content s • I ndex
MP LS and V PN Ar chi te ctur e s, V olum e I I
By Jim Guichard, I van Pepelnjak, Jeff Apcar
Pub lish er: Cisco Press Pub Dat e: Ju ne 06, 2 00 3
I SBN: 1- 58 705 -1 12 -5 Pages: 50 4
With MPLS and VPN Ar chit ect u res, Volum e I I, you'll lear n :
How to integr ate v ar iou s r em ote access techn ologies in to th e back bone p r ovidin g VPN ser vice to m any d iffer ent typ es of cu stom er s
The n ew PE- CE r out in g op tions as w ell as ot her adv anced feat ur es, includ ing per- VPN Netw ork Ad dr ess Tr an slation ( PE- NAT)
How VRFs can be ex tended into a custom er site to pr ov ide sep ar ation inside t he custom er netw ork
The latest MPLS VPN secur ity featu res an d d esign s aim ed at pr otecting th e MPLS VPN backbone
How to carr y custom er m ulticast tr affic insid e a VPN
The latest in ter - car rier enh ancem ents t o allow for easier and m or e scalable d ep loym ent of inter - car r ier MPLS VPN services
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced
About the Authors
Ji m Guicha rd , CCI E N o. 2 0 6 9, is a Tech nical Leader I I w ithin the I nt er net Techn ologies
Division ( I TD) at Cisco System s. Du r in g t he past six year s at Cisco an d pr ev iously at I BM, Jim has been inv olved in t he design, im p lem entation, and plannin g of m any lar g e- scale WAN an d LAN netw ork s. His br eadth of ind ustry kn ow ledg e, hand s- on ex perience, and un derstan ding of comp lex in ter n etw or kin g architectur es hav e enabled him to pr ovid e valu ed assistan ce t o m any of Cisco's lar ger ser vice pr ovider cu stomer s. His pr evious pub lications in clu de MPLS and VPN Ar chit ect u res, b y Cisco Pr ess.
I v an P ep el nj a k , CCI E N o. 1 3 5 4, is th e Ch ief Tech nology Ad visor and m em ber of the b oard with NIL Dat a Com m un ications (w w w .NI L.si) , a high - tech data comm u nicat ion s comp any that focu ses on pr oviding high - valu e ser v ices in new - wor ld ser vice p r ovider technolog ies.
I van h as m ore t han 10 y ear s of exp er ience in design ing, in st alling , tr oub leshooting , and oper ating larg e corp orat e and ser v ice p r ovider WAN and LAN netw ork s, sever al of them alr ead y deploy in g MPLS- based vir tual pr ivate netw orks ( VPNs) . He is t he auth or or lead develop er of a nu mb er of highly successfu l adv anced IP cour ses cover ing MPLS/ VPN, BGP, OSPF, and I P QoS, and he is the ar chitect of NI L's rem ote lab solu tion. I v an' s pr evious pu blication s include MPLS and VPN Ar chit ect u res an d EI GRP Net w or k Design Solu t ion s, b y
Cisco Pr ess.
Je ff A pcar is a Senior Design Consulting Engineer in the Asia Pacific Ad van ced Ser v ices gr oup at Cisco System s. He is one of th e Cisco lead consultan ts on MPLS in t he r eg ion an d has design ed MPLS n etw or k s for man y ser vice p rovider s in AsiaPac u sin g p acket- based an d cell- based MPLS. Jeff has also d esigned and m aintained larg e I P r outer n etw or ks ( 50 0+ nod es) and has a br oad and deep r ang e of skills cover ing man y facets of netw or kin g com mu nication s.
• Table of Content s • I ndex
MP LS and V PN Ar chi te ctur e s, V olum e I I
By Jim Guichard, I van Pepelnjak, Jeff Apcar
Pub lish er: Cisco Press Pub Dat e: Ju ne 06, 2 00 3
I SBN: 1- 58 705 -1 12 -5 Pages: 50 4
With MPLS and VPN Ar chit ect u res, Volum e I I, you'll lear n :
How to integr ate v ar iou s r em ote access techn ologies in to th e back bone p r ovidin g VPN ser vice to m any d iffer ent typ es of cu stom er s
The n ew PE- CE r out in g op tions as w ell as ot her adv anced feat ur es, includ ing per- VPN Netw ork Ad dr ess Tr an slation ( PE- NAT)
How VRFs can be ex tended into a custom er site to pr ov ide sep ar ation inside t he custom er netw ork
The latest MPLS VPN secur ity featu res an d d esign s aim ed at pr otecting th e MPLS VPN backbone
How to carr y custom er m ulticast tr affic insid e a VPN
The latest in ter - car rier enh ancem ents t o allow for easier and m or e scalable d ep loym ent of inter - car r ier MPLS VPN services
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced
About the Technical Reviewers
Ma t t h ew H . Birk n er, CCI E No. 371 9, is a Techn ical Leader at Cisco Sy stems, sp ecializin g in
I P an d MPLS n etw or k d esign. He has in fluenced m ultip le lar g e car r ier and en terp rise designs w or ld w ide. Matt has spoken at Cisco Netw ork er s on MPLS VPN tech nologies in both the U.S. and EMEA over the past few year s. A "d ouble CCI E", h e has p ublished the Cisco Pr ess book, Cisco I nter netw ork Design . Matt holds a BSEE from Tuft s Un iver sity, w her e he maj or ed in electr ical en gineering .
• Table of Content s • I ndex
MP LS and V PN Ar chi te ctur e s, V olum e I I
By Jim Guichard, I van Pepelnjak, Jeff Apcar
Pub lish er: Cisco Press Pub Dat e: Ju ne 06, 2 00 3
I SBN: 1- 58 705 -1 12 -5 Pages: 50 4
With MPLS and VPN Ar chit ect u res, Volum e I I, you'll lear n :
How to integr ate v ar iou s r em ote access techn ologies in to th e back bone p r ovidin g VPN ser vice to m any d iffer ent typ es of cu stom er s
The n ew PE- CE r out in g op tions as w ell as ot her adv anced feat ur es, includ ing per- VPN Netw ork Ad dr ess Tr an slation ( PE- NAT)
How VRFs can be ex tended into a custom er site to pr ov ide sep ar ation inside t he custom er netw ork
The latest MPLS VPN secur ity featu res an d d esign s aim ed at pr otecting th e MPLS VPN backbone
How to carr y custom er m ulticast tr affic insid e a VPN
The latest in ter - car rier enh ancem ents t o allow for easier and m or e scalable d ep loym ent of inter - car r ier MPLS VPN services
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced
About the Content Reviewer
Mon iqu e Mor row is cu rr ently CTO Con sulting Eng ineer at Cisco Syst em s, I nc. She has 20
• Table of Content s • I ndex
MP LS and V PN Ar chi te ctur e s, V olum e I I
By Jim Guichard, I van Pepelnjak, Jeff Apcar
Pub lish er: Cisco Press Pub Dat e: Ju ne 06, 2 00 3
I SBN: 1- 58 705 -1 12 -5 Pages: 50 4
With MPLS and VPN Ar chit ect u res, Volum e I I, you'll lear n :
How to integr ate v ar iou s r em ote access techn ologies in to th e back bone p r ovidin g VPN ser vice to m any d iffer ent typ es of cu stom er s
The n ew PE- CE r out in g op tions as w ell as ot her adv anced feat ur es, includ ing per- VPN Netw ork Ad dr ess Tr an slation ( PE- NAT)
How VRFs can be ex tended into a custom er site to pr ov ide sep ar ation inside t he custom er netw ork
The latest MPLS VPN secur ity featu res an d d esign s aim ed at pr otecting th e MPLS VPN backbone
How to carr y custom er m ulticast tr affic insid e a VPN
The latest in ter - car rier enh ancem ents t o allow for easier and m or e scalable d ep loym ent of inter - car r ier MPLS VPN services
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced
Acknowledgments
Ev ery maj or pr oj ect is a r esu lt of team w ork, an d t his book is n o exception . We'd like t o th ank ever yon e w ho help ed u s in t he long w r it in g pr ocess: our developm ent ed itor , Gr ant Munr oe, w ho helped u s w ith t he intr icacies of w r iting a book; the r est of the ed it orial t eam fr om Cisco Pr ess; an d especially ou r r eviewer s, Dan Tapp an, Matt Bir kn er , an d Monique Mor row . They not only cor rected ou r err or s an d om ission s, but they also included several useful su ggestions to im p rove th e quality of th is pub lication.
Jeff w ould like to th ank his m an agement team Tony Sim onsen, Mich ael Lim , and Steve Sm ith , for pr ovid in g the tim e and encour agem ent t o do the b ook. Also sp ecial th ank s to the gu ys in the AsiaPac Lab Grou p, Nick Stath akis, Ron Masson, an d Geor g e Leran tges, w ho let him hog lots of gear . Last, Jeff w ould lik e to than k Jim and I van for inviting him to collab orate with them .
• Table of Content s • I ndex
MP LS and V PN Ar chi te ctur e s, V olum e I I
By Jim Guichard, I van Pepelnjak, Jeff Apcar
Pub lish er: Cisco Press Pub Dat e: Ju ne 06, 2 00 3
I SBN: 1- 58 705 -1 12 -5 Pages: 50 4
With MPLS and VPN Ar chit ect u res, Volum e I I, you'll lear n :
How to integr ate v ar iou s r em ote access techn ologies in to th e back bone p r ovidin g VPN ser vice to m any d iffer ent typ es of cu stom er s
The n ew PE- CE r out in g op tions as w ell as ot her adv anced feat ur es, includ ing per- VPN Netw ork Ad dr ess Tr an slation ( PE- NAT)
How VRFs can be ex tended into a custom er site to pr ov ide sep ar ation inside t he custom er netw ork
The latest MPLS VPN secur ity featu res an d d esign s aim ed at pr otecting th e MPLS VPN backbone
How to carr y custom er m ulticast tr affic insid e a VPN
The latest in ter - car rier enh ancem ents t o allow for easier and m or e scalable d ep loym ent of inter - car r ier MPLS VPN services
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced
Introduction
Since our fir st MPLS book (MPLS and VPN Ar chit ect u res) was pub lished by Cisco Pr ess a few
• Table of Content s • I ndex
MP LS and V PN Ar chi te ctur e s, V olum e I I
By Jim Guichard, I van Pepelnjak, Jeff Apcar
Pub lish er: Cisco Press Pub Dat e: Ju ne 06, 2 00 3
I SBN: 1- 58 705 -1 12 -5 Pages: 50 4
With MPLS and VPN Ar chit ect u res, Volum e I I, you'll lear n :
How to integr ate v ar iou s r em ote access techn ologies in to th e back bone p r ovidin g VPN ser vice to m any d iffer ent typ es of cu stom er s
The n ew PE- CE r out in g op tions as w ell as ot her adv anced feat ur es, includ ing per- VPN Netw ork Ad dr ess Tr an slation ( PE- NAT)
How VRFs can be ex tended into a custom er site to pr ov ide sep ar ation inside t he custom er netw ork
The latest MPLS VPN secur ity featu res an d d esign s aim ed at pr otecting th e MPLS VPN backbone
How to carr y custom er m ulticast tr affic insid e a VPN
The latest in ter - car rier enh ancem ents t o allow for easier and m or e scalable d ep loym ent of inter - car r ier MPLS VPN services
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced
Who Should Read This Book?
This b ook is not desig ned t o be an in trod uction to Mu lt ip r otocol Label Sw itching ( MPLS) or virtu al pr ivate netw or ks ( VPNs) ; Volum e I (MPLS and VPN Ar chit ect u res) pr ovides you w ith that know led ge. This b ook is intend ed to trem endou sly incr ease you r kn ow ledg e of adv anced MPLS VPN d ep loym ent scenar ios and enable y ou to d ep loy MPLS and MPLS VPN solutions in a variety of com plex desig ns. Anyone w h o is involved in design , deploym en t, or
• Table of Content s • I ndex
MP LS and V PN Ar chi te ctur e s, V olum e I I
By Jim Guichard, I van Pepelnjak, Jeff Apcar
Pub lish er: Cisco Press Pub Dat e: Ju ne 06, 2 00 3
I SBN: 1- 58 705 -1 12 -5 Pages: 50 4
With MPLS and VPN Ar chit ect u res, Volum e I I, you'll lear n :
How to integr ate v ar iou s r em ote access techn ologies in to th e back bone p r ovidin g VPN ser vice to m any d iffer ent typ es of cu stom er s
The n ew PE- CE r out in g op tions as w ell as ot her adv anced feat ur es, includ ing per- VPN Netw ork Ad dr ess Tr an slation ( PE- NAT)
How VRFs can be ex tended into a custom er site to pr ov ide sep ar ation inside t he custom er netw ork
The latest MPLS VPN secur ity featu res an d d esign s aim ed at pr otecting th e MPLS VPN backbone
How to carr y custom er m ulticast tr affic insid e a VPN
The latest in ter - car rier enh ancem ents t o allow for easier and m or e scalable d ep loym ent of inter - car r ier MPLS VPN services
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced
How This Book Is Organized
Althou gh this book cou ld b e r ead cover - to- cover , it is desig ned t o be flexible an d allow you to easily m ove betw een chapt er s and sect ion s of chapter s to cov er ju st the mat er ial th at you need m or e infor mat ion on. I f you do intend to r ead them all, the ord er in th e book is an excellent seq uence to use.
P ar t I: I nt r oduct ion
Ch apter 1, "MPLS VPN Architectur e Ov er view ," ser ves as a r efr esh er to th e inform ation contained w ithin MPLS and VPN Ar chitectu res. I t d oes not descr ibe th e MPLS or MPLS VPN technology in detail; if y ou need b aseline MPLS or MPLS VPN kn ow ledg e, read MPLS and VPN Ar ch it ect ur es: Volu me I fir st.
P ar t I I: Adv a ncedP E- CEConne ct iv it y
Ch apter 2, "Rem ote Access t o an MPLS VPN," discusses int eg ration of access technologies such as dial, DSL, and cable into an MPLS VPN backbone. Th is ch apter show s how y ou can integr ate var ious access technologies into the backb one, ther eb y pr ov iding VPN service to m any ty pes of custom ers.
Ch apter 3, "PE- CE Rout in g Protocol Enhan cem ents an d Ad van ced Featu res," bu ild s on Volum e 1 of the MPLS and VPN Ar chit ect u res b ook and intr odu ces m or e adv anced options/ featu res for
OSPF conn ectiv ity as w ell as supp ort for I S- IS and EI GRP r outing pr otocols.
Ch apter 4, "Vir tual Router Connectivity ," d iscusses the use of th e VRF constr ucts to bu ild virtu al r outer type conn ectivity, extend in g the VRF con cept to t he CE r outer . This chap ter also discusses n ew VRF- related featur es, in clu ding VRF- lite and PE- b ased netw or k addr ess
tr anslation ( PE- NAT) .
P ar t I I I: Adv a nced D e ploy m en t Sce na ri os
Ch apter 5, "Pr otecting the MPLS- VPN Back bone," looks at var ious secur it y issues w ithin the backbone and descr ibes the n ecessar y steps th at a ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites.
Ch apter 6, "Larg e- Scale Routing and Mu lt ip le Ser vice Pr ovider Con nectiv ity," descr ibes th e advanced featur es, design s, and topologies th at w er e m ade possible w ith the enhan cem ents to Cisco IOS since the fir st MPLS and VPN Ar chitect ur es book w as w r itten .
Ch apter 7, "Multicast VPN," discusses th e deployment of I P m ulticast b etw een VPN client sites.
Ch apter 8, "I P Ver sion 6 Acr oss an MPLS Backbone," d iscusses a m odel ( 6 PE) t hat gives th e ser vice pr ovider s an option to pr ovid e IPv6 connectivity acr oss an MPLS- enab led I Pv4 backbone.
P ar t I V: Trou ble shoot in g
• Table of Content s • I ndex
MP LS and V PN Ar chi te ctur e s, V olum e I I
By Jim Guichard, I van Pepelnjak, Jeff Apcar
Pub lish er: Cisco Press Pub Dat e: Ju ne 06, 2 00 3
I SBN: 1- 58 705 -1 12 -5 Pages: 50 4
With MPLS and VPN Ar chit ect u res, Volum e I I, you'll lear n :
How to integr ate v ar iou s r em ote access techn ologies in to th e back bone p r ovidin g VPN ser vice to m any d iffer ent typ es of cu stom er s
The n ew PE- CE r out in g op tions as w ell as ot her adv anced feat ur es, includ ing per- VPN Netw ork Ad dr ess Tr an slation ( PE- NAT)
How VRFs can be ex tended into a custom er site to pr ov ide sep ar ation inside t he custom er netw ork
The latest MPLS VPN secur ity featu res an d d esign s aim ed at pr otecting th e MPLS VPN backbone
How to carr y custom er m ulticast tr affic insid e a VPN
The latest in ter - car rier enh ancem ents t o allow for easier and m or e scalable d ep loym ent of inter - car r ier MPLS VPN services
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced
Icons Used in This Book
Thr oug hout this b ook, you w ill see the follow ing icons u sed for netw orking devices:
The follow in g icons are u sed for perip herals an d other devices:
• Table of Content s • I ndex
MP LS and V PN Ar chi te ctur e s, V olum e I I
By Jim Guichard, I van Pepelnjak, Jeff Apcar
Pub lish er: Cisco Press Pub Dat e: Ju ne 06, 2 00 3
I SBN: 1- 58 705 -1 12 -5 Pages: 50 4
With MPLS and VPN Ar chit ect u res, Volum e I I, you'll lear n :
How to integr ate v ar iou s r em ote access techn ologies in to th e back bone p r ovidin g VPN ser vice to m any d iffer ent typ es of cu stom er s
The n ew PE- CE r out in g op tions as w ell as ot her adv anced feat ur es, includ ing per- VPN Netw ork Ad dr ess Tr an slation ( PE- NAT)
How VRFs can be ex tended into a custom er site to pr ov ide sep ar ation inside t he custom er netw ork
The latest MPLS VPN secur ity featu res an d d esign s aim ed at pr otecting th e MPLS VPN backbone
How to carr y custom er m ulticast tr affic insid e a VPN
The latest in ter - car rier enh ancem ents t o allow for easier and m or e scalable d ep loym ent of inter - car r ier MPLS VPN services
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
• Table of Content s • I ndex
MP LS and V PN Ar chi te ctur e s, V olum e I I
By Jim Guichard, I van Pepelnjak, Jeff Apcar
Pub lish er: Cisco Press Pub Dat e: Ju ne 06, 2 00 3
I SBN: 1- 58 705 -1 12 -5 Pages: 50 4
With MPLS and VPN Ar chit ect u res, Volum e I I, you'll lear n :
How to integr ate v ar iou s r em ote access techn ologies in to th e back bone p r ovidin g VPN ser vice to m any d iffer ent typ es of cu stom er s
The n ew PE- CE r out in g op tions as w ell as ot her adv anced feat ur es, includ ing per- VPN Netw ork Ad dr ess Tr an slation ( PE- NAT)
How VRFs can be ex tended into a custom er site to pr ov ide sep ar ation inside t he custom er netw ork
The latest MPLS VPN secur ity featu res an d d esign s aim ed at pr otecting th e MPLS VPN backbone
How to carr y custom er m ulticast tr affic insid e a VPN
The latest in ter - car rier enh ancem ents t o allow for easier and m or e scalable d ep loym ent of inter - car r ier MPLS VPN services
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced
Command Syntax Conventions
The con ventions used to pr esent comm an d sy ntax in this b ook ar e the sam e conventions u sed in the I OS Com m and Refer en ce. Th e Com m and Refer en ce d escr ibes these con vent ion s as follow s:
Vert ical b ars ( | ) separ ate alter native, m u tually exclusive elem en ts.
Squ are br ackets [ ] ind icate op tional elements.
Br aces { } indicate a requ ired choice.
Br aces w ithin br ack ets [ { } ] in dicat e a r equir ed choice w ithin an optional elem en t.
Boldface in dicates com m ands and keyw ord s that ar e enter ed liter ally as show n . I n actual con figur ation exam ples an d ou tput ( not gener al com man d syntax) , b oldface indicates com man ds th at ar e m anu ally in put by th e user ( such as a show com m and ) .
• Table of Content s • I ndex
MP LS and V PN Ar chi te ctur e s, V olum e I I
By Jim Guichard, I van Pepelnjak, Jeff Apcar
Pub lish er: Cisco Press Pub Dat e: Ju ne 06, 2 00 3
I SBN: 1- 58 705 -1 12 -5 Pages: 50 4
With MPLS and VPN Ar chit ect u res, Volum e I I, you'll lear n :
How to integr ate v ar iou s r em ote access techn ologies in to th e back bone p r ovidin g VPN ser vice to m any d iffer ent typ es of cu stom er s
The n ew PE- CE r out in g op tions as w ell as ot her adv anced feat ur es, includ ing per- VPN Netw ork Ad dr ess Tr an slation ( PE- NAT)
How VRFs can be ex tended into a custom er site to pr ov ide sep ar ation inside t he custom er netw ork
The latest MPLS VPN secur ity featu res an d d esign s aim ed at pr otecting th e MPLS VPN backbone
How to carr y custom er m ulticast tr affic insid e a VPN
The latest in ter - car rier enh ancem ents t o allow for easier and m or e scalable d ep loym ent of inter - car r ier MPLS VPN services
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced
Part I: Introduction
• Table of Content s • I ndex
MP LS and V PN Ar chi te ctur e s, V olum e I I
By Jim Guichard, I van Pepelnjak, Jeff Apcar
Pub lish er: Cisco Press Pub Dat e: Ju ne 06, 2 00 3
I SBN: 1- 58 705 -1 12 -5 Pages: 50 4
With MPLS and VPN Ar chit ect u res, Volum e I I, you'll lear n :
How to integr ate v ar iou s r em ote access techn ologies in to th e back bone p r ovidin g VPN ser vice to m any d iffer ent typ es of cu stom er s
The n ew PE- CE r out in g op tions as w ell as ot her adv anced feat ur es, includ ing per- VPN Netw ork Ad dr ess Tr an slation ( PE- NAT)
How VRFs can be ex tended into a custom er site to pr ov ide sep ar ation inside t he custom er netw ork
The latest MPLS VPN secur ity featu res an d d esign s aim ed at pr otecting th e MPLS VPN backbone
How to carr y custom er m ulticast tr affic insid e a VPN
The latest in ter - car rier enh ancem ents t o allow for easier and m or e scalable d ep loym ent of inter - car r ier MPLS VPN services
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced
Chapter 1. MPLS VPN Architecture
Overview
Vir tual p rivate n etw or ks ( VPNs) hav e r ecent ly received a lot of attent ion from eq uipm ent m anufactur ers, consultan ts, netw or k desig ners, service pr ov id er s, lar ge enter pr ises, an d end users due t o th eir cost ad van tages over trad itional enter pr ise netw orks. As w ith m ost
technologies, the foun dation for tod ay' s VPN netw orks an d u nder lying technolog ies w as created m ore t han 20 year s ago. Dur ing its d evelop m en t, end user s d iscover ed that it m ade fin ancial sen se t o r ep lace lin ks b et ween sites in their ow n pr ivate netw ork w ith v irtu al connections acr oss a shar ed in fr astru ct ur e. The assum ption for d oing this w as th at a shar ed environ ment ( or VPN) is eq uivalent in term s of secu rity and pr ivacy to the n etw or k ( links) it w as r eplacin g.
This chap ter r eview s t he basic Mu ltip r otocol Label Sw itching ( MPLS) an d MPLS- based VPN concep ts and ter m in ologies to ensur e an un derstan ding of the ter m s used in th is book . I t also cover s the lat est developm ents in the MPLS VPN ar en a and h ow they enable t he ser v ice pr ovider to offer n ew MPLS- b ased ser v ices, such as rem ote access into an MPLS- b ased VPN or I nter net Pr otocol ( I P) m ulticast w it hin a VPN. Th ese develop ment s are also descr ibed in depth in later ch apter s.
NO TE
• Table of Content s • I ndex
MP LS and V PN Ar chi te ctur e s, V olum e I I
By Jim Guichard, I van Pepelnjak, Jeff Apcar
Pub lish er: Cisco Press Pub Dat e: Ju ne 06, 2 00 3
I SBN: 1- 58 705 -1 12 -5 Pages: 50 4
With MPLS and VPN Ar chit ect u res, Volum e I I, you'll lear n :
How to integr ate v ar iou s r em ote access techn ologies in to th e back bone p r ovidin g VPN ser vice to m any d iffer ent typ es of cu stom er s
The n ew PE- CE r out in g op tions as w ell as ot her adv anced feat ur es, includ ing per- VPN Netw ork Ad dr ess Tr an slation ( PE- NAT)
How VRFs can be ex tended into a custom er site to pr ov ide sep ar ation inside t he custom er netw ork
The latest MPLS VPN secur ity featu res an d d esign s aim ed at pr otecting th e MPLS VPN backbone
How to carr y custom er m ulticast tr affic insid e a VPN
The latest in ter - car rier enh ancem ents t o allow for easier and m or e scalable d ep loym ent of inter - car r ier MPLS VPN services
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced
MPLS VPN Terminology
Since the ear ly day s of X.25 and Fr ame Relay ( the tw o tech nologies initially used to deploy VPN ser vices) , man y different tech nologies have been pr oposed as t he basis to en able a VPN infrastr uctur e. Th ese r anged fr om Layer 2 technolog ies ( X.25 , Fram e Relay, an d
Asyn ch ron ous Tr ansfer Mode [ ATM] ) to Layer 3 t echn olog ies ( pr im ar ily I P) or even Layer 7 technologies. I BM on ce h ad a pr odu ct th at tr anspor ted IP datag ram s over Sy st em s Netw or k Ar ch itectu re ( SNA) app lication session s, and TGV ( a com pany later acqu ired by Cisco System s) h ad im plem en ted I P t ran sp ort over DECnet sessions. Not su rp r ising ly , w ith such a variety of im plement ation p rop osals, th e over all ter m in ology in the field has chan ged dr am atically. Th is book uses the ter m inology in trod uced w ith the MPLS- based VPN.
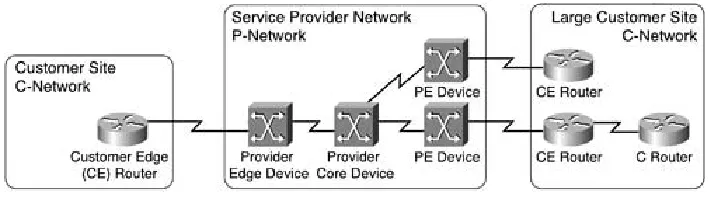
MPLS VPN- based t er m inology is b ased on a clear distin ction b etw een t he ser vice pr ovid er netw or k ( P- netw or k ) and th e customer n et wor k ( C- netw or k) , as sh ow n in Figur e 1- 1.
Figu r e 1 - 1 . M PLS VPN- Ba se d Te r m in ology
The P- netw ork is alw ays top olog ically contigu ous, w her eas the C- netw ork is usually clear ly delineated int o a num ber of sit es ( con tiguou s par ts of th e cu st omer n etw or k th at ar e
connected in som e w ay other th an th r ough the VPN ser vice) . Note that a site does not need to be geogr aph ically contain ed ; if the cu stom er is using a VPN ser vice for its in ter nat ion al connectivity only, a site could sp an a w hole coun try.
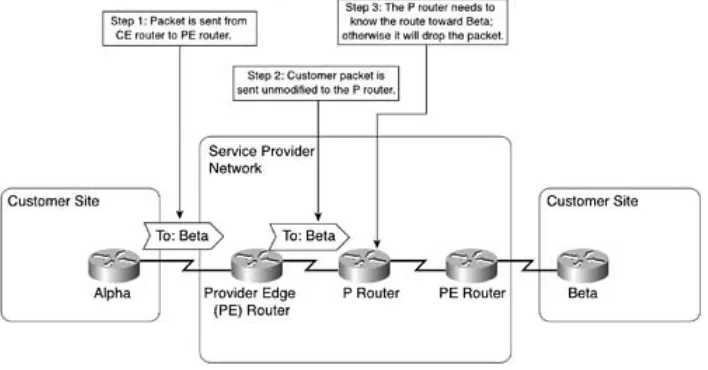
The d evices that lin k the custom er sites to th e P- netw or k ar e called cust om er ed ge ( CE) dev ices, w her eas the ser vice pr ovider devices to wh ich th e CE r outers con nect ar e called pr ov id er ed ge ( PE) dev ices. I n m ost cases, th e P- netw or k is m ade up of m or e than j ust th e PE r outer s. These other dev ices ar e called P d evices ( or , if th e P- netw or k is im plem ented w ith Layer 3 tech nology , P rou ter s) . Sim ilarly, th e additional Layer 3 devices in th e custom er sites that hav e n o dir ect connectivity t o the P- netw ork are called C r outer s.
VPN techn olog ies h ave ev olved into tw o m ajor appr oaches tow ar d im p lem enting VPN ser vices:
Conne ct ion- orie nt e d V PN— The PE dev ices pr ovide virtu al leased lines betw een the
CE dev ices. These vir tu al leased lin es are called v ir t ual circuit s ( VCs) . The VCs can b e
per m anent, established ou t- of- b and by th e ser vice p r ovider n etw or k m anag em ent team ( called per m anent v irt ual cir cuit s, or PVCs) . Th ey can also be tem por ar y, estab lish ed on dem and by t he CE devices th rou gh a sign alin g p rot ocol that the PE devices un der stan d. ( These VCs ar e called sw it ched vir t ual cir cuit s, or SVCs) .
• Table of Content s • I ndex
MP LS and V PN Ar chi te ctur e s, V olum e I I
By Jim Guichard, I van Pepelnjak, Jeff Apcar
Pub lish er: Cisco Press Pub Dat e: Ju ne 06, 2 00 3
I SBN: 1- 58 705 -1 12 -5 Pages: 50 4
With MPLS and VPN Ar chit ect u res, Volum e I I, you'll lear n :
How to integr ate v ar iou s r em ote access techn ologies in to th e back bone p r ovidin g VPN ser vice to m any d iffer ent typ es of cu stom er s
The n ew PE- CE r out in g op tions as w ell as ot her adv anced feat ur es, includ ing per- VPN Netw ork Ad dr ess Tr an slation ( PE- NAT)
How VRFs can be ex tended into a custom er site to pr ov ide sep ar ation inside t he custom er netw ork
The latest MPLS VPN secur ity featu res an d d esign s aim ed at pr otecting th e MPLS VPN backbone
How to carr y custom er m ulticast tr affic insid e a VPN
The latest in ter - car rier enh ancem ents t o allow for easier and m or e scalable d ep loym ent of inter - car r ier MPLS VPN services
Advanced t rou blesh ooting techn iques includ in g r ou ter outpu ts to en su re high availab ility
MPLS and VPN Ar chit ect u res, Volum e I I, b uilds on the best- sellin g MPLS an d VPN
Ar ch itectu res, Volum e I ( 1 - 587 05- 0 02- 1) , from Cisco Pr ess. Extendin g int o m or e advanced topics an d d ep loym ent architectur es, Volu m e II pr ovid es r eader s w ith the necessar y tools they n eed to d ep loy and m ain tain a secur e, hig hly av ailab le VPN.
MPLS and VPN Ar chit ect u res, Volum e I I, b eg in s w ith a br ief refresher of the MPLS VPN Ar ch itectu re. Par t II descr ibes adv anced MPLS VPN con nectivity includ in g the integr ation of ser vice pr ovider access t echn olog ies ( dial, DSL, cab le, Ether net) an d a variety of r outin g pr otocols ( I S- I S, EI GRP, and OSPF) , ar m in g the r eader w ith the know ledge of h ow to integr ate th ese feat ur es in to th e VPN b ackbon e. Part I II details adv anced d ep loy m ent issues includin g secu r ity, ou tlining the n ecessar y steps th e ser vice p rovider m ust take to p rotect t he backbone and any attached VPN sites, and also detailin g the latest secu rity featur es to allow m or e advanced top ologies and filterin g. This par t also cover s m ulti- car r ier MPLS VPN
deploym en ts. Fin ally, Par t IV pr ovid es a m ethodology for ad van ced MPLS VPN tr oub leshooting .
MPLS and VPN Ar chit ect u res, Volum e I I, also int rod uces the latest advances in cu st omer integr ation, secur ity, and tr oubleshooting featu res essential to p roviding th e advanced