Management
Management
Information Systems,
Information Systems,
10/e
10/e
Raymond McLeod and George
Raymond McLeod and George
Schell
Chapter 5
Chapter 5
Computing and
Computing and
Communications Resources
Learning Objectives
Learning Objectives
►
Know the various computer components.
Know the various computer components.
►
Know about personal computing devices.
Know about personal computing devices.
►
Understand the implications of the rapid
Understand the implications of the rapid
advances in information and communication
advances in information and communication
technologies.
technologies.
►
Be familiar with input and output resources.
Be familiar with input and output resources.
►
Recognize how different storage media differ
Recognize how different storage media differ
and the advantages of each.
Learning Objectives (Cont’d)
Learning Objectives (Cont’d)
►
Know the advantages of prewritten software.
Know the advantages of prewritten software.
►
Understand the different computer
Understand the different computer
networking strategies.
networking strategies.
►
Understand how communications over the
Understand how communications over the
public telephone system and networks differ.
public telephone system and networks differ.
►
Know about network protocols.
Know about network protocols.
►
Distinguish between intranets, extranets,
Distinguish between intranets, extranets,
and the Internet.
Hardware & Processors
Hardware & Processors
►
Mainframes
Mainframes
are large computers used
are large computers used
for centralized information systems.
for centralized information systems.
►
Microcomputers
Microcomputers
or
or
PCs
PCs
are computers
are computers
used by one person.
used by one person.
►
Processor (CPU)
Processor (CPU)
is where data
is where data
processing is performed.
processing is performed.
►
Processor speed
Processor speed
is measured by the #
is measured by the #
Processors
Processors
►
MHz
MHz
stands for
stands for
millions of cycles per
millions of cycles per
second
second
.
.
►
Word
Word
is the measure of how many bits
is the measure of how many bits
can be moved with one cycle of the
can be moved with one cycle of the
processor.
processor.
►
Word size
Word size
is how many characters, “A”,
is how many characters, “A”,
can be moved in a single cycle of the
can be moved in a single cycle of the
processor.
processor.
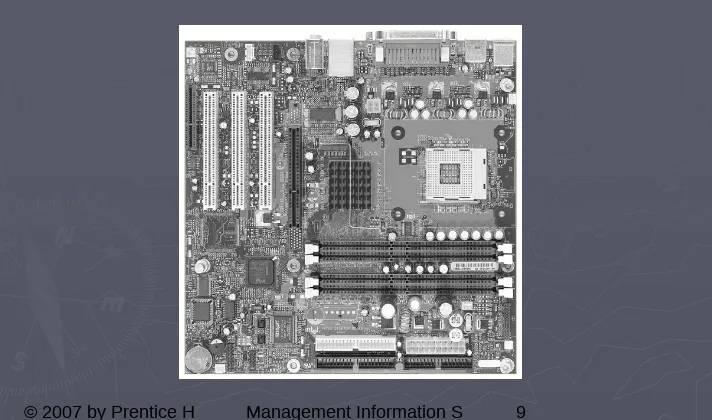
Table 5.1 Major Computer
Table 5.1 Major Computer
Components
Memory & Storage
Memory & Storage
►
Memory
Memory
(
(
primary storage or RAM
primary storage or RAM
)
)
is the storage area on the computer’s
is the storage area on the computer’s
circuit board.
circuit board.
Volatile
Volatile
Extremely fast
Extremely fast
►
Fixed storage
Fixed storage
is permanently
is permanently
installed in the computer.
installed in the computer.
►
Removable storage
Removable storage
media – tape,
media – tape,
disk, CD, DVD, USB flash drive, etc.
Input Devices
Input Devices
►
Human-captured data
Human-captured data
refers to input
refers to input
captured by a person typing on a
captured by a person typing on a
keyboard, clicking a mouse, speaking into
keyboard, clicking a mouse, speaking into
a microphone, or a similar interaction.
a microphone, or a similar interaction.
►
Machine-captured data
Machine-captured data
is data
is data
captured by an electronic or mechanical
captured by an electronic or mechanical
device.
device.
►
Point-of-sale terminals
Point-of-sale terminals
are scanners
are scanners
Output Devices
Output Devices
►
Monitor
Monitor
Screen resolution, size 17-19’’ diagonals.
Screen resolution, size 17-19’’ diagonals.
Graphic user interface (GUI).
Graphic user interface (GUI).
►
Printers
Printers
Lasers are like copier machines.
Lasers are like copier machines.
Ink-jets spray ink.
Ink-jets spray ink.
►
Multimedia is the use of more than 1
Multimedia is the use of more than 1
medium at a time.
Personal Computing Devices
Personal Computing Devices
►
Cell phones with interactive messaging
Cell phones with interactive messaging
& video
& video
►
Smart cell phones are phones that
Smart cell phones are phones that
perform tasks associated with PCs i.e.
perform tasks associated with PCs i.e.
BlackBerry 7270, Treo 650.
BlackBerry 7270, Treo 650.
►
Global Systems for Mobile
Global Systems for Mobile
Communications (GSM)
Communications (GSM)
digital
digital
cellular phone protocol.
Home Networks
Home Networks
►
Home computer networks assess the
Home computer networks assess the
Internet via
Internet via
cable modems
cable modems
or
or
DSL
DSL
modems
modems
.
.
►
Setup usually requires the modem,
Setup usually requires the modem,
network card(s), wireless router.
network card(s), wireless router.
►
Wireless security uses
Wireless security uses
Wired
Wired
equivalent privacy
equivalent privacy
(
(
WEP
WEP
) which
) which
encrypts the data transferred between
encrypts the data transferred between
the computer & wireless router.
Home Computing Security
Home Computing Security
►
Updates
Updates
for OS an application software.
for OS an application software.
For security & efficiency.
For security & efficiency.
Microsoft Update
Microsoft Update
.
.
►
Hackers
Hackers
are people who try to break
are people who try to break
into computer systems in order to
into computer systems in order to
Gather information;
Gather information;
Deny the owner access to his resources;
Deny the owner access to his resources;
Delete files;
Delete files;
Home Computing Security
Home Computing Security
(Cont’d)
(Cont’d)
►
Viruses
Viruses
are small computer programs
are small computer programs
that replicate by inserting themselves
that replicate by inserting themselves
into computer resources such as
into computer resources such as
programs or files.
programs or files.
►
Worms
Worms
are self-contained files or
are self-contained files or
programs
programs
Does not have to attach to program or file.
Does not have to attach to program or file.
Can delete, change files, send e-mails, and
Can delete, change files, send e-mails, and
Home Computing Security
Home Computing Security
(Cont’d)
(Cont’d)
►
Denial-of-service attack
Denial-of-service attack
is when the
is when the
user is denied access to the services of
user is denied access to the services of
the computer because it is overwhelmed
the computer because it is overwhelmed
with e-mail.
with e-mail.
►
Antivirus software
Antivirus software
– Norton, MacAfee,
– Norton, MacAfee,
etc. Keep virus definitions updated
etc. Keep virus definitions updated
►
Spyware
Spyware
– Microsoft Defender, Lavasoft
– Microsoft Defender, Lavasoft
Software
Software
►
System software
System software
(
(
OS
OS
) performs
) performs
certain tasks that all computers require.
certain tasks that all computers require.
Hardware interfaces, device drivers.
Hardware interfaces, device drivers.
Manage computer’s processes.
Manage computer’s processes.
OS – Windows XP, Unix, Mac OS X, Linux.
OS – Windows XP, Unix, Mac OS X, Linux.
►
Application software
Application software
processes the
processes the
user’s data.
user’s data.
►
Prewritten application software
Prewritten application software
is
is
Application Software
Application Software
►
Custom application software
Custom application software
is when
is when
programmers for the business write the
programmers for the business write the
software.
software.
►
User-written software
User-written software
in
in
End-User
End-User
Computing
Computing
is created by the user, such
is created by the user, such
as Excel Macros, Access Wizards.
as Excel Macros, Access Wizards.
►
User-friendly software
User-friendly software
is computer
is computer
Communications
Communications
►
Protocol
Protocol
is the specification for
is the specification for
formatting data to be transferred
formatting data to be transferred
between communications equipment.
between communications equipment.
►
Public connections
Public connections
Telephone modems
Telephone modems
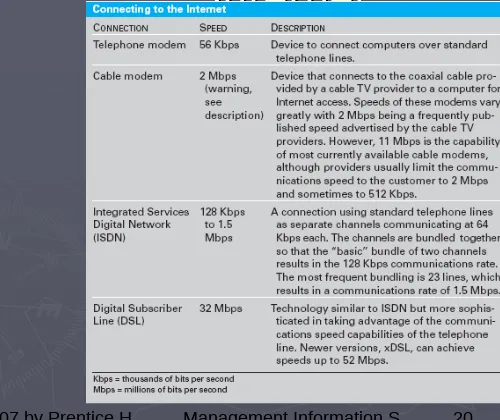
Table 5.4 Connecting to the
Table 5.4 Connecting to the
Internet
Communications (Cont’d)
Communications (Cont’d)
►
Packet
Packet
is a piece of the total data to be
is a piece of the total data to be
communicated, includes sender &
communicated, includes sender &
receiver addresses.
receiver addresses.
►
Cable modems
Cable modems
connect to the Internet
connect to the Internet
via coaxial cable.
via coaxial cable.
►
Asynchronous transfer mode (ATM)
Asynchronous transfer mode (ATM)
Private Line
Private Line
►
Circuit
Circuit
is a connection that is always
is a connection that is always
connected.
connected.
►
Private line
Private line
is a circuit that is always
is a circuit that is always
open to your communication traffic.
open to your communication traffic.
T-1
T-1
line over 1.5 Mbps;
line over 1.5 Mbps;
T-3
T-3
at 43 Mbps.
at 43 Mbps.
Multiplexed
Multiplexed
is when the line is broken
is when the line is broken
into separate lanes of communication.
Virtual Private Networks
Virtual Private Networks
►
Virtual Private Networks (VPNs)
Virtual Private Networks (VPNs)
allow
allow
you to use the security & speed of a private
you to use the security & speed of a private
line but still use the low-cost Internet.
line but still use the low-cost Internet.
►
Tunneling software
Tunneling software
establishes the set of
establishes the set of
intermediary locations of the telephone
intermediary locations of the telephone
equipment that will host a given data
equipment that will host a given data
communications transfer.
communications transfer.
►
Privacy is attained because the tunnel is not
Privacy is attained because the tunnel is not
established unless the sending & receiving
established unless the sending & receiving
computers authenticate one another.
Communications - Networks
Communications - Networks
►
Open Systems Interconnection (OSI)
Open Systems Interconnection (OSI)
standard architecture for network
standard architecture for network
connections established by the
connections established by the
ISO
ISO
.
.
►
Terminal
Terminal
is a device that has no storage or
is a device that has no storage or
processor; it allows for entering & displaying
processor; it allows for entering & displaying
data for the computer.
data for the computer.
►
Systems Network Architecture (SNA)
Systems Network Architecture (SNA)
is a
is a
protocol for large computers; it polls other
Table 5.5 OSI Reference
Table 5.5 OSI Reference
Networks (Cont’d)
Networks (Cont’d)
►
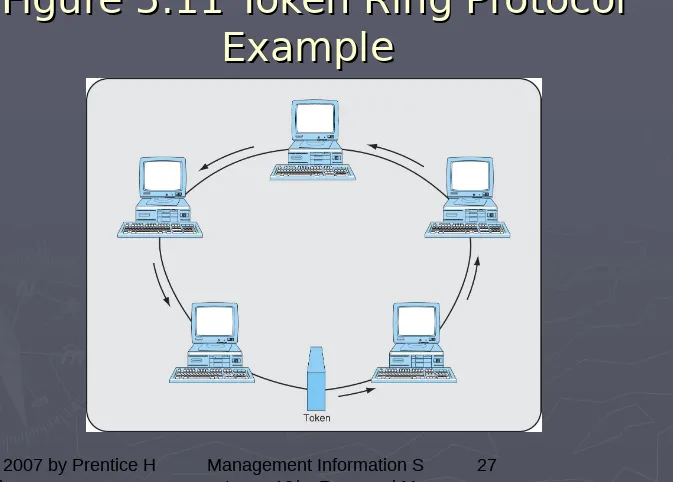
Token ring
Token ring
is a
is a
peer-to-peer
peer-to-peer
protocol
protocol
that allows each computer to
that allows each computer to
act as its own controller.
act as its own controller.
►
Ethernet
Ethernet
is an open protocol for peer-
is an open protocol for
peer-to-peer communications.
to-peer communications.
IEEE
IEEE
endorses
endorses
►
Data transmission crash
Data transmission crash
is when
is when
two peer computers try to send data
two peer computers try to send data
at the same time.
Figure 5.11 Token Ring Protocol
Figure 5.11 Token Ring Protocol
Example
Networks (Cont’d)
Networks (Cont’d)
►
Data packet
Data packet
is a piece of the total data
is a piece of the total data
to be communicated, combined with the
to be communicated, combined with the
address of the destination computer, the
address of the destination computer, the
sending computer, and other control
sending computer, and other control
information.
information.
►
Transmission Control
Transmission Control
Protocol/Internet Protocol
Protocol/Internet Protocol
(
(
TCP/IP
TCP/IP
)
)
TCP
TCP
conducts communication over the
conducts communication over the
network.
network.
Networks (Cont’d)
Networks (Cont’d)
►
IP address
IP address
is a four-part set of numbers
is a four-part set of numbers
(each from 0 to 255), separated by
(each from 0 to 255), separated by
periods.
periods.
►
Network interface card (NIC)
Network interface card (NIC)
is used
is used
to attach a device to the communications
to attach a device to the communications
medium.
medium.
►
Local Area Networks (LANs)
Local Area Networks (LANs)
is a
is a
group of computers and other devices
group of computers and other devices
Table 5.6 Communications
Table 5.6 Communications
Network Hardware
Networks (Cont’d)
Networks (Cont’d)
►
Medium used by LANs can be copper
Medium used by LANs can be copper
wire, wireless, fiber-optics, or other
wire, wireless, fiber-optics, or other
media.
media.
►
LANs join computers that are
LANs join computers that are
physically located together.
physically located together.
Same room or building.
Same room or building.
Networks (Cont’d)
Networks (Cont’d)
►
Metropolitan area network (MAN)
Metropolitan area network (MAN)
is
is
a network that has a physical distance
a network that has a physical distance
limit of roughly 30 miles.
limit of roughly 30 miles.
►
Wide are networks (WANs)
Wide are networks (WANs)
are used
are used
to connect computers and other devices
to connect computers and other devices
when the distance exceeds the
when the distance exceeds the
constraints of LANs & MANs.
constraints of LANs & MANs.
Uses common carrier, public telephone
Uses common carrier, public telephone
Internet, Intranet & Extranet
Internet, Intranet & Extranet
►
Internet
Internet
is just a collection of networks
is just a collection of networks
that can be joined together; Public.
that can be joined together; Public.
►
Intranet
Intranet
uses the same network protocols
uses the same network protocols
as the Internet but limits accessibility to
as the Internet but limits accessibility to
computer resources to a select group of
computer resources to a select group of
persons in the organization.
persons in the organization.
►
Extranet
Extranet
is when the intranet is expanded
is when the intranet is expanded
to include users beyond the firm; Trusted
to include users beyond the firm; Trusted
Convergence of Computing &
Convergence of Computing &
Communications
Communications
►
Computing devices & communications
Computing devices & communications
devices are now incorporating features
devices are now incorporating features
of the other into themselves.
of the other into themselves.
►
Voice over Internet Protocol
Voice over Internet Protocol
(
(
VoIP
VoIP
)
)
is the routing of voice communications
is the routing of voice communications
over the Internet as if they were digital
over the Internet as if they were digital
communications.
communications.
Static RAM / SRAM Dinamic RAM / DRAM
EDORAM
(Extended Data
SDRAM 168 pin
PROM
EPROM
Hard disk
Removable Storage
Removable Storage
Floppy disk
CD
Input Device
Input Device
Printer & Plotter
Printer & Plotter