Journal of Theoretical and Applied I nformati on Technology
© 2005 - 2014 JATIT & LLS. All rights reserved
ISSN: 1992-8645 www.jatit.org E-ISSN: 1817-3195
JOURNAL OF THEORETICAL AND APPLIED
INFORMATION TECHNOLOGY
EDITORIAL COMMITTEE
NIAZ AHMAD
(Chief Editor)
Professor, FCE, MOE, H-9 Islamabad
PAKISTAN
SHAHBAZ GHAYYUR
(Co- Chief Editor)
Assistant Professor, DCS, FBAS, International Islamic University Islamabad,
PAKISTAN
SAEED ULLAH
(Associate Editor)
Assistant Professor, DCS, Federal Urdu University of Arts, Science & Technology Islamabad,
PAKSITAN
MADIHA AZEEM
(Associate Editor)
Journal of Theoretical and Applied Information Technology, Islamabad.
PAKISTAN
SALEHA SAMAR
(Managing Editor)
Journal of Theoretical and Applied Information Technology, Islamabad.
PAKISTAN
KAREEM ULLAH
(Managing Editor)
Journal of Theoretical and Applied Information Technology, Islamabad.
PAKISTAN
SHAHZAD A. KHAN
Lecturer IMCB, FDE Islamabad, PAKISTAN
(Managing Editor/Linguists & In-charge Publishing)
Journal of Theoretical and Applied Information Technology, Islamabad.
PAKISTAN
June 2014. Vol. 64 No.1
.
i
Journal of Theoretical and Applied I nformati on Technology
© 2005 - 2014 JATIT & LLS. All rights reserved
ISSN: 1992-8645 www.jatit.org E-ISSN: 1817-3195
JOURNAL OF THEORETICAL AND APPLIED
INFORMATION TECHNOLOGY
REGIONAL ADVISORY PANEL
Dr. SIKANDAR HAYAT KHIYAL
Professor &Chairman DCS& DSE, Fatima Jinnah Women University, Rawalpindi, PAKISTAN
Dr. MUHAMMAD SHER
Professor &Chairman DCS, FBAS, International Islamic University Islamabad, PAKISTAN
Dr. ABDUL AZIZ
Professor of Computer Science, University of Central Punjab, PAKISTAN
Dr. M. UMER KHAN
Asst. Professor Department of Mechatronics, Air University Islamabad, PAKISTAN
Dr. KHALID HUSSAIN USMANI
Asst. Professor Department of Computer Science, Arid Agriculture University,
Rawalpindi, PAKISTAN
June 2014. Vol. 64 No.1
.
Journal of Theoretical and Applied I nformati on Technology
© 2005 - 2014 JATIT & LLS. All rights reserved
ISSN: 1992-8645 www.jatit.org E-ISSN: 1817-3195
JOURNAL OF THEORETICAL AND APPLIED
INFORMATION TECHNOLOGY
June 2014. Vol. 64 No.1
.
iii
Dr. CHRISTEL BAIER
Technical University Dresden, GERMANY
Dr KHAIRUDDIN BIN OMAR UniversitiKebangsaanMalysia, 43600 Bangi
Selangor Darul-Ehsan, MALYSIA
Dr. YUSUF PISAN
University of Technology, Sydney, AUSTRALIA
Dr. S. KARTHIKEYAN Department of Electronics and Computer Engineering, Caledonian College of Engineering,
OMAN (University College with Glascow University, Scotland, UK) DR. YUXIN MAO
School Of Computer & Information Engineering Zhejiang Gongshang University, CHINA
Dr. ZARINA SHUKUR
FakultiTeknologidanSainsMaklumat, University Kebangsaan MALYSIA
Dr. NOR AZAN MAT ZIN
Faculty of Information Science & Technology, National University of MALYSIA
Dr. R.PONALAGUSAMY
National Institute of Technology, Tiruchirappalli, Tamil Nadu, INDIA
Dr. MOHAMMAD TENGKU SEMBOK Universiti Kebangsaan MALYSIA
Dr. PRABHAT K. MAHANTI University of New Brunswick, Saint John, New
Brunswick, CANADA
Dr. NITIN UPADHYAY
Birla Institute of Technology and Science (BITS), Pilani-Goa Campus, INDIA
Dr. S.S.RIAZ AHAMED
Mohamed Sathak Engineering College, Kilakarai, &Sathak Institute of Technology, Ramanathapuram , Tamilnadu, INDIA
Dr. A. SERMET ANAGÜN Eskisehir Osmangazi University, Industrial Engineering Department, Bademlik Campus,
26030 Eskisehir, TURKEY.
Dr. YACINE LAFIFI
Department of Computer Science, University of Guelma, BP 401, Guelma 24000, ALGERIA.
Dr. CHRISTOS GRECOS
School Of Computing, Engineering And Physical Sciences University Of Central Lancashire.
UNITED KINGDOM
Dr. JAYANTHI RANJAN Institute of Management Technology Raj Nagar, Ghaziabad, Uttar Pradesh, INDIA
Dr. ADEL M. ALIMI
National Engineering School of Sfax (ENIS), University of SFAX, TUNISIA
Dr. RAKESH DUBE
Professor & Head, RKG Institute of Technology, Ghaziabad, UP, INDIA
Dr. ADEL MERABET Department of Electrical & Computer Engineering, Dalhousie University, Halifax,
CANADA
Dr. HEMRAJ SAINI
CE&IT Department, Higher Institute of Electronics, BaniWalid. LIBYA
Journal of Theoretical and Applied I nformati on Technology
© 2005 - 2014 JATIT & LLS. All rights reserved
ISSN: 1992-8645 www.jatit.org E-ISSN: 1817-3195
June 2014. Vol. 64 No.1
.
iv Dr. SEIFEDINE KADRY
Lebanese International University, LEBONON
Dr. AIJUAN DONG Department of Computer Science Hood College Frederick, MD 21701. USA
Dr. ZURIATI AHMAD ZUKARNAIN University Putra Malaysia,
MALAYSIA
Dr. HEMRAJ SAINI
Higher Institute of Electronic, BaniWalid LIBYA
Dr. CHELLALI BENACHAIBA University of Bechar, ALGERIA
Dr. MOHD NAZRI ISMAIL
University of Kuala Lumpur (UniKL) MALYSIA
Dr. VITUS SAI WA LAM The University of Hong Kong, CHINA
Dr. WITCHA CHIMPHLEE SuanDusitRajabhat University, Bangkok,
THAILAND
Dr. SIDDHIVINAYAK KULKARNI University of Ballarat, Ballarat,
AUSTRALIA
Dr. S. KARTHIKEYAN Caledonian College of Engineering,
OMAN
Dr. DRAGAN R. MILIVOJEVIĆ Mining and Metallurgy Institute BorZelenibulevar
35, 19210 Bor, SERBIA
Dr. E. SREENIVASA REDDY Principal - VasireddyVenkatadri Institute of
Technology, Guntur, A.P., INDIA
Dr OUSMANE THIARE Gaston Berger University, Department of Computer Science, UFR S.A.T, BP 234 Saint-
Louis SENEGAL
Dr. SANTOSH DHONDOPANT KHAMITKAR RamanandTeerthMarathwada University, Nanded.
Maharashtra 431605, INDIA
Dr. M. IQBAL SARIPAN
(MIEEE, MInstP, Member IAENG, GradBEM) Dept. of Computer and Communication Systems Engineering, Faculty of Engineering, Universiti
Putra MALAYSIA
Dr. E. SREENIVASA REDDY Principal - VasireddyVenkatadri Institute of
Technology, Guntur, A.P., INDIA
Dr. T.C.MANJUNATH, Professor & Head of the Dept., Electronicis& Communication Engg. Dept,
New Horizon College of Engg., Bangalore-560087, Karnataka, INDIA.
Dr. SIDDHIVINAYAK KULKARNI
Graduate School of Information Technology and Mathematics University of Ballart AUSTRALIA
Dr. SIKANDAR HAYAT KHIYAL Professor & Chairman DCS& DSE, Fatima
Jinnah Women University, Rawalpindi,
PAKISTAN
Dr. MUHAMMAD SHER Professor & Chairman DCS, FBAS, International Islamic University Islamabad,
PAKISTAN
Dr. ABDUL AZIZ
Professor of Computer Science, University of Central Punjab, PAKISTAN
Dr. M. UMER KHAN
Journal of Theoretical and Applied Informati on Technology
© 2005 - 2014 JATIT & LLS. All rights reserved
ISSN: 1992-8645 www.jatit.org E-ISSN: 1817-3195
Elite Panel Members Have A Decision Weight Equivalent of Two Referees (Internal OR External). The Expertise Of Editorial Board Members Are Also Called In For Settling Refereed Conflict About
June 2014. Vol. 64 No.1
Acceptance/Rejection And Their Opinion Is Considered As Final.
.
v Dr. RIKTESH SRIVASTAVA
Assistant Professor, Information Systems Skyline University College P O Box 1797, Sharjah, UAE
Dr. BONNY BANERJEE
PhD in Computer Science and Engineering, The Ohio State University, Columbus, OH, USA
Senior Scientist Audigence, FL, USA
PROFESSOR NICKOLAS S. SAPIDIS DME, University of Western Macedonia
Kozani GR-50100, GREECE.
Dr. NAZRI BIN MOHD NAWI Software Engineering Department, Faculty of
Science Computer Information Technology,
Universiti Tun Hussein Onn
MALAYSIA
Dr. JOHN BABALOLA OLADOSU Ladoke Akintola University of Technology,
Ogbomoso, NIGERIA
Dr. ABDELLAH IDRISSI
Department of Computer Science, Faculty of Science, Mohammed V University - Agdal,
Rabat, MOROCCO
Dr. AMIT CHAUDHRY University Institute of Engineering and Technology, Panjab University, Sector-25,
Chandigarh, INDIA
Dr. ASHRAF IMAM
Aligarh Muslim University, Aligarh-INDIA
Dr. MOHAMMED ALI HUSSAIN Dept. of Computer Science & Engineering, Sri Sai Madhavi Institute of Science & Technology,
Mallampudi, Rajahmundry, A.P, INDIA
Dr. KHALID HUSSAIN USMANI Asst. Professor Department of Computer Science,
Arid Agriculture University, Rawalpindi, PAKISTAN
Dr. GUFRAN AHAMD ANSARI Qassim University, College of Computer Science,
Ministry of Higher Education, Qassim University, KINGDOM OF SAUDI
ARABIA
Dr. Defa Hu
School of Information, Hunan University of Commerce
Changsha 410205, Hunan, P. R. of China
Journal of Theoretical and Applied I nformati on Technology
© 2005 - 2014 JATIT & LLS. All rights reserved
ISSN: 1992-8645 www.jatit.org E-ISSN: 1817-3195
PREFACE
Journal of Theoretical and Applied Information Technology (JATIT) published since 2005 (E-ISSN 1817- 3195 / ISSN 1992-8645) is an International refereed research publishing journal with a focused aim of promoting and publishing original high quality research dealing with theoretical and scientific aspects in all disciplines of Information Technology. JATIT is an international scientific research journal focusing on issues in information technology research. A large number of manuscript inflows, reflects its popularity and the trust of world's research community. JATIT is indexed with various organizations and is now published on monthly basis.
All technical or research papers and research results submitted to JATIT should be original in nature, never previously published in any journal or undergoing such process across the globe. All the submissions will be peer-reviewed by the panel of experts associated with JATIT. Submitted papers should meet the internationally accepted criteria and manuscripts should follow the style of the journal for the purpose of both reviewing and editing. All of its articles also appear online as per policy of JATIT
Journal of Theoretical and Applied Information Technology receives papers in continuous flow and we will consider articles from a wide range of Information Technology disciplines encompassing the most basic research to the most innovative technologies. Please submit your papers electronically to our submission system at http://jatit.org/submit_paper.php in an MSWord, Pdf or compatible format so that they may be evaluated for publication in the upcoming issue. This journal uses a blinded review process; please remember to include all your personal identifiable information in the manuscript before submitting it for review, we will edit the necessary information at our side. Submissions to JATIT should be full research / review papers (properly indicated below main title).
It is the sole responsibility of the submitting authors to make sure that the submitted manuscript is not in process of publication anywhere in any conference/journal across the globe, nor part or whole of it is copied from any source.
The review process may take anywhere from five days to two months depending on the response time to referees. Authors will be informed about the updated status via e-mail as soon as we receive the evaluation results. After submission of publication dues for accepted manuscripts a publication slot will be allocated to your manuscript for its publication in upcoming monthly issues of JATIT.
******************
June 2014. Vol. 64 No.1.
Journal of Theoretical and Applied I nformati on Technology
© 2005 - 2014 JATIT & LLS. All rights reserved
ISSN: 1992-8645 www.jatit.org E-ISSN: 1817-3195
ABSTRACTING & INDEXING
Journal of Theoretical and Applied Information Technology Islamabad Pakistan is focused, double blind peer reviewed journal that is now being published monthly and is published by Asian Research Publishing Network and is Indexed / Abstracted by the following International Agencies and institutions. JATIT has been regularly published since 2005 and now has a well reputed international standing and invites contributions from researchers, scientists, and practitioners from all over the world.
*- Ulrich's Periodicals Directory
*- DataBase systems and Logic Programming (DBLP) *- EBSCO Publishing USA
*- Directory of Open Access Journals (DOAJ) *- Google & Google Scholar Journals
*- The Index of Information Systems Journals *- Information Technology Resources Collection *- ZDNet Australia
*- NLM Catalog
*- Computing Research and Education Association of Australasia *- CiteSeer
*- Elsevier *- SCOPUS
*- Engineering Village *- TOC Premier
******************
Feel free to suggest JATIT to any Indexing & Abstracting Services which are appropriate to its scope
TM
June 2014. Vol. 64 No.1
*- Computer Science Journals
*- Computers and Applied Sciences Complete *- N|W Switzerland
*- Microsoft Academic Search *- Cabell Publishing
*-OpenJgate *- INSPEC
*- IAOR Palgrave Macmillan
.
vii
Journal of Theoretical and Applied Information Technology
10th June 2014. Vol. 64 No.1
© 2005 - 2014 JATIT & LLS. All rights reserved.
ISSN: 1992-8645 www.jatit.org E-ISSN: 1817-3195
BONE FRACTURE DETECTION USING OPENCV
1SAMUEL FEBRIANTO KURNIAWAN, 2I KETUT GEDE DARMA PUTRA
, 3 A.A KOMPIANG OKA SUDANA 1,2,3
Department of Information Technology, Udayana University, Indonesia
E-mail: [email protected]
,
2
,
3
ABSTRACT
Image processing is important in modern data storage and data transmission especially in progressive transmission of images, video coding (teleconferencing), digital libraries, image database, and remote sensing. The purpose of this project is to find out the accuration of an X-Ray Bone Fracture Detection using Canny Edge Detection Method. Fractured bone is a bone condition that suffered a breakdown of bone integrity. A disconnected connection between two cartilages also categorized as bone fracture. Normally, bones have elasticity and a great number of strength. Bone fracture only happen when the bones took a force beyond their elasticity or strength. This system is built using OpenCV library combined with Canny Edge Detection method to detect the bone fracture. Canny Edge Detection method is an optimal edge detection algorithm on determining the end of a line with changeable threshold and less error rate. The simulation results have shown how canny edge detection can help determine location of fractures in x-ray images.
Keywords: Fracture, Edge, Edge Detection, Canny, Threshold, x-ray images.
1. INTRODUCTION
Digital image processing is an expanding area with applications regarding to our daily lives, especially in progressive transmission of images, video coding (teleconferencing), digital libraries, image database, remote sensing, and other particular applied usage. Many image processing and analysis techniques have been developed to aid the interpretation of remote sensing images and to extract as much information as possible from the image. The huge collection of digital images are collected due to the improvement in the digital storage media, image capturing devices like scanners, web cameras, digital cameras and rapid development in internet. This leads to rapid and efficient retrieval of these images for visual information in different fields of life like medical, medicine, art, architecture, education, crime preventions, etc [1,2].
The medical imaging field has grown substantially in the recent year and has generated additional interest in methods and tools for management, analysis, and communication of medical image. Many diagnostic imaging modalities, such as x-ray, magnetic resonance imaging (MRI), digital radiography, and ultrasound
are currently available and are routinely used to support clinical decision making. By using medical imaging, physicians are able to glean qualitative and quantitative information about anatomy and physiology of the patients. With this advantages, medical imaging has become central to medical diagnosis. Thus, with the advances in computer processing capabilities, it has become possible to approach the problem of automating diagnosis in medical imaging. This paper will focus on canny edge detection that help radiologist in automated diagnosis image. Radiologist often experiencing difficulty on reading x-ray image. This can be caused by the lack of lighting, fractures the hardly seen by naked eyes, or noises the happened on image capturing process. By building the system, we hope the system can help people especially radiologist on detecting bones anomaly that happened on x-ray images [3].
Journal of Theoretical and Applied Information Technology
10th June 2014. Vol. 64 No.1
© 2005 - 2014 JATIT & LLS. All rights reserved.
ISSN: 1992-8645 www.jatit.org E-ISSN: 1817-3195
250
2. IMAGE PROCESSING TECHNIQUE
Image processing techniques are employed to develop this algorithm. It is discussed in detail in this section.
2.1 Canny Edge
Edges are considered to be most important image attributes that provide valuable information for human image perception. Edge detection is a very complex process affected by deterioration due to different level of noise [4]. An edge is the boundary between an object and the background. Edge detection is identifying points in a digital image at which the image brightness changes sharply or more formally has discontinuities. The purpose of detecting sharp changes in image brightness is to capture important events and changes in properties of the world [4].
Edge detection is used for identification of blurred frame broad classification among smooth and rough surface classification of cement and asphalt. The Canny edge detection is performed on the frames with the sensitive threshold values (upper threshold 10000 and lower threshold 4900) and again it is performed with the insensitive threshold values (upper threshold 50000 and lower threshold 9800) [4]. If a pixel has a gradient greater than the upper threshold, then it is an edge pixel. If a pixel has a gradient lower than the lower threshold, it is not an edge pixel. If the pixel’s gradient is between the upper and the lower thresholds, then it is considered as an edge, only if it is connected to a pixel that is above the high threshold value as given in [5,11].
Canny is one of modern edge detection method that founded by Marrdan Hildreth, who is doing research in modeling human visual perception. There are several criteria on edge detecting that can be fulfilled by Canny Edge Detection:
1. Canny has better detection (for detection criteria). Canny method capable to marks all existing edges matching with user determined parameter’s thresshold. Also giving high flexibility on determining thickness level of edge detection according to the required conditions.
2. Canny has better localizing way (localize criteria). Canny capable on producing minimum gap between detected edge and the real image edge.
3. Obvious response (response criteria). Only one response for every edge. This make less confusion on edge detection for the next image. Chosing parameters on Canny Edge Detection
will giving effect on every result and edge detection. The parameters are :
a. Gaussian Deviation Standard Value. b. Thresshold Value.
The following is the steps to do Canny Edge Detection.
1. Remove all noise on the image by implementing Gaussian Filter. The result is an image with less blur. It is intended to obtain the real edges of the image. If we did not apply the Gaussian Filter before, sometimes the noise itself will be detected as an edge.
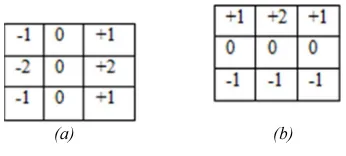
2. Detect the edge with one of these detection operators, like Roberts, Perwit, or Sobel by do horizontal searching (Gx) and vertical searching (Gy). The following is the sample of edge detection operator (Sobel operators).
(a) (b)
Figure 1 Sobel Operator (a) Gx, (b) Gy
The result from both operators combined to obtain the summary of vertical edge and horizontal edge with this formula[6]:
(3)
3. Determining direction of the edge by using the following formula:
ଶ ଶ (4)
ீ௬
ீ௫ (5)
Canny Edge Detection using two thresholds (maximum threshold and minimum threshold). If pixel gradient higher than maximum threshold, pixel will be marked as an edge. If the pixel gradient lower than minimum threshold, the pixel will be denied as background image. If the pixel gradient between maximum threshold and minimum threshold, the pixel will be accepted as an edge if it is connected with other edge pixel that higher than maximum threshold.[11]
Journal of Theoretical and Applied Information Technology
10th June 2014. Vol. 64 No.1
© 2005 - 2014 JATIT & LLS. All rights reserved.
ISSN: 1992-8645 www.jatit.org E-ISSN: 1817-3195
5. The last step is binarizing the image pixels by applying two threshold value.
2.3 System Overview
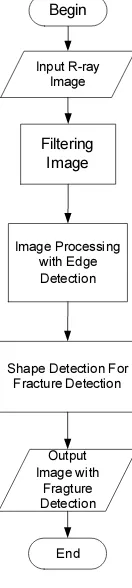
System overview of this program is discussed in detail in this section.The next figure show the system design in flowchart. This flowchart explain the process flows from detecting X-ray image until producing the bone fracture detection on the X-ray image. Input R-ray Image Filtering Image Image Processing with Edge Detection
Shape Detection For Fracture Detection Output Image with Fragture Detection Begin End
Figure 2 Flowchart System
Here is an explanation of the performance of the system:
1. First user must input an image to be processed, the image will then be carried filtering to remove noise that exist in the image.
2. The next step will performed after image filtering process, the image will be processed using Canny Edge method, it will give results more visible lines on an X-ray image.
3. The system then combines the results of early detection canny with the original image, then user can clearly see the shape of the bone and this combined images will be processed by the system.
4. To detect the location of the fracture in the image, the system use shape detection with multiple parameters. A broken bone is expressed
when the line has an end, and do not have a connection with another line. A broken bone stated, if the lines form an angle less than 145 degrees, although the line still has a connection with the other lines.
5. The parameters on system specify in determining the location of the broken bone is as follows:
a. The red color, indicating the location after the end of a line through a process canny edge detection. Where the line is only a single line and doesn’t have adjacent to any other lines.
b. The blue color indicates the location of the end of a line next to each other (this is intended to indicate the location of the line that has the possibility of having a hairline fractured bone).
c. The green color indicates the location of the end of a line in the line has a lot of ends. The amount of a tip in the first line helps the system to recognize the location of a major fracture in the picture.
This system builds from OpenCv library, CV namespace contains image processing and camera calibration methods. The computational geometry functions are also located here. CVAUX namespace is described in OpenCv's documentation as containing obsolete and experimental code. However, the simplest interfaces for face recognition are in this module. The code behind them is specialized for face recognition, and they're widely used for that purpose. ML namespace contains machine-learning interfaces. HighGUI namespace contains the basic I/O interfaces and multi-platform windowing capabilities. CVCAM namespace contains interfaces for video access through DirectX on 32-bit Windows platforms.[7,8]. In book of [13,14,15] there much information about using OpenCv for build this system. Here is an example pseudocode from OpenCv that determining the location of the broken bone.
//Setting the parameter for edge detection
Journal of Theoretical and Applied Information Technology
10th June 2014. Vol. 64 No.1
© 2005 - 2014 JATIT & LLS. All rights reserved.
ISSN: 1992-8645 www.jatit.org E-ISSN: 1817-3195
252 CV_POLY_APPROX_DP,
cvContourPerimeter(contours)*0.05, 0);
//Red Point detection indicating for edge detection
if(result->total==2 )
{
CvPoint *pt[2]; for(int i=0;i<3;i++){
pt[i] = (CvPoint*)cvGetSeqElem(result, i); }
// blue point detection, indicating for hairline fracture bone
if(result->total==3 )
{
CvPoint *pt[3]; for(int i=0;i<3;i++){
pt[i] = (CvPoint*)cvGetSeqElem(result, i); }
//Green Point detection, indicating for major fracture
else if(result->total==4 )
{
CvPoint *pt[4]; for(int i=0;i<4;i++){
pt[i] = (CvPoint*)cvGetSeqElem(result, i); }
3. RESULT
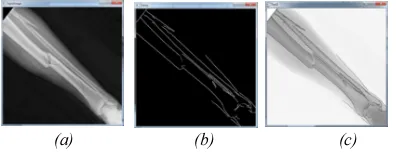
Figure 3 shows step 1 – 5 in chapter 3 to start the bone fracture detection process. The first image output has been processed through Canny Edge Detection method, and then followed by the shape detection. Shape detection used to find the end of a line. End of a line can be ascertained as the position where the fracture occured. This application can reduce the unused parameter that categorized as undamaged part (chapter 2).
There are many outputs from this proses, which are the original image to be processed, 2 images that has been processed by Canny Edge Detection method, and 2 images that shows the user the result of fracture detection. Figure 3 will show those 5 outputs.
In figure 3 the user uploads an x-ray image, figure 3(a). Then system will process that image
with Canny Edge detection, figure 3(b). In figure 3(c) system shows the output of image processing, by combining the image of canny edge detection result and inverting the original image that uploaded by the user. In figure 3(d) system will detect the location of the end of each line. In Figure 3(e) the system will then automatically detect fractured bone and its location.
(a) (b) (c)
(d) (e)
Figure 3 (a) Input Image (b) Output Image with canny Detection(c) Invert Output Image Canny Detection (d) Output image with canny Detection with edge detection in every edge (e) Output image with Fracture detection.
To clarify the performance of the system, we decided to process the other images. Here is an example of the results of the image processing:
Journal of Theoretical and Applied Information Technology
10th June 2014. Vol. 64 No.1
© 2005 - 2014 JATIT & LLS. All rights reserved.
ISSN: 1992-8645 www.jatit.org E-ISSN: 1817-3195
(d) (e)
Figure 4 (a) Input Image (b) Output Image with canny Detection(c) Invert Output Image Canny Detection (d) Output image with canny Detection with edge detection in every edge (e) Output image with Fracture detection.
(a) (b) (c)
(d) (e)
Figure 5 (a) Input Image (b) Output Image with canny Detection(c) Invert Output Image Canny Detection (d) Output image with canny Detection with edge detection in every edge (e) Output image with Fracture detection.
After a number of attempts to detect the location of the fracture, the results of the experiments are summarized in Table 1.
Table 1 Result of Fracture Detection No End Of Line
Detection (Red) Hairline Fracture Detection (Blue) Fracture Detection (Green)
1 11 Edge
Detection None Hairline Fracture Detection 6 Major Fracture Detection
2 22 Edge
Detection 1 Hairline Fracture Detection 9 Major Fracture Detection
3 15 Edge
Detection 2 Hairline Fracture Detection 3 Major Fracture Detection
Table 1 shows the number of results of the detection system bone fracture, and accuracy of system detection can be seen in Table 2.
Table 2 Accuracy of Fracture Detection No Hairline
Fracture (a) Major Detection (b) Accuracy
True False True False A b
1 - - 4 2 - 50%
2 1 - 5 4 100% 55,6%
3 1 1 2 1 50% 66,7%
4. CONCLUSION
This Paper presented the Canny Edge detection framework to assist radiologist in detecting fractured bones from x-ray images. It has been tested with real data. Simulation result shows that the system need to be improvised on it performance and reduce the response time.
According to the test result that has been done to detect the bone fracture, a conclusion can be made that the performance and accuration of the detection method affected by the quality of the image. The better the image quality, the better result system got.
For the future development, there are some things that must be noted:
a. Implement another image processing method in order to improve the accuration of image detection.
b. Adding various language will capable on supporting the integration of this application to other application or system.
c. Improvise the method performance to decrease the amount of time and decrease the percentage of error by adding several model of different neural networks trained with different architecture before initiating this system.
REFRENCES:
[1] Mubeena Pathan, K.Jusoff, M. S. Alias ”Implication Of Image Processing Algorithm In Remote Sensing and gis applications”, Journal of Theoretical and Applied Information Technology, 15th December 2011, vol 34 No 1.
Journal of Theoretical and Applied Information Technology
10th June 2014. Vol. 64 No.1
© 2005 - 2014 JATIT & LLS. All rights reserved.
ISSN: 1992-8645 www.jatit.org E-ISSN: 1817-3195
254 [3] Mostafa Syiam, “AdAgen : Adaptive Interface
Agent For X-Ray Fracture Detection”, International Journal of Computing & Information Sciences, December 2004, vol 2, no 3.
[4] Dhanabal R,” Digital Image Processing Using Sobel Edge Detection Algorithm In Fpga “, Journal of Theoretical and Applied Information Technology, 10th December 2013, Vol. 58 No.1.
[5] Rafael C. Gonzalez, Richard and E. Woods, “Digital Image Processing”, Third Edition, 2009.
[6] Batra Yudha Pratama,”Pendeteksian Tepi Pengolahan Citra Digital “, 2007, Komunitas eLearning IlmuKomputer.Com.
[7] Robin Hewitt, 2010, Available at :http://www.cognotics.com/opencv/servo_2007 _series/part_1/index.html 2010/09/02.
[8] Shervin Emami,”Facial Recognition using OpenCV”, Journal of Mobile, Embedded and Distributed Systems, vol. IV, no. 1, 2012. [9] Bin Yu and Anil K. Jain, “Lane Boundary
Detection Using A Multiresolution Hough Transform,” Dept. of Computer Science Michigan State University, East Lansing, MI 48824, IEEE Conference, October 1997, vol. 2, pp. 748-751.
[10] N. Otsu, “A threshold selection method from grey-level histograms”, IEEE Trans. Syst., Man, Cybern, Vol. SMC-8, 1978, pp. 62–66. [11] Darma Putra,“Pengolahan Citra Digital”.
Andi. Yogjakarta, Indonesia, 2010.
[12] Xuan Mo, “OpenCV Tutorial I: Image Processing”, iPal Grub Meeting , 2011. [13] David Stavens,” The OpenCV Library:
Computing Optical Flow”, Stanford Artificial Intelligence Lab, 2013.
[14] Robert Laganière,” OpenCV 2 Computer Vision Application Programming Cookbook”. Packt Publishing , 2011.
[15] Klaus D. Toennies, “Advances in Computer Vision and Pattern Recognition”. Springer-Verlag, London, 2012.
Home
Journal Rankings
Journal Search
Country Rankings
Country Search
Compare
Map Generator
Help
About Us
Display journal title
Just copy the code below and paste within your html page:
<a href="http://www.scimagojr.com/journalsearch.php?q=19700182903&tip=sid&exact=no" title="SCImago Journal & Country Rank"><img border="0" src="http://www.scimagojr.com/journal_img.php?id=19700182903&title=true" alt="SCImago Journal & Country Rank" /></a>
How to cite this website?
F o l l o w u s :
SJR is developed by:
J o u r n a l S e a r c h
in Journal Title Search
Exact phrase
J o u r n a l o f T h e o r e t i c a l a n d A p p l i e d I n f o r m a t i o n T e c h n o l o g y
Country: Pakistan
Subject Area: Computer Science | Mathematics
Subject Category: Computer Science (miscellaneous) , Theoretical Computer Science
Publisher: Asian Research Publishing Network (ARPN). Publication type: Journals. ISSN: 18173195, 19928645
Coverage: 2010-2013
H Index: 5
Charts Data
Indicators 1999 2000 2001 2002 2003 2004 2005 2006 2007 2008 2009 2010 2011 2012 SJR 0,000 0,000 0,000 0,000 0,000 0,000 0,000 0,000 0,000 0,000 0,000 0,000 0,137 0,167
Total Documents 0 0 0 0 0 0 0 0 0 0 0 222 229 622
Total Docs. (3years) 0 0 0 0 0 0 0 0 0 0 0 0 222 451
Total References 0 0 0 0 0 0 0 0 0 0 0 3.880 4.120 9.475
Total Cites (3years) 0 0 0 0 0 0 0 0 0 0 0 0 61 178
Self Cites (3years) 0 0 0 0 0 0 0 0 0 0 0 0 4 17
Citable Docs. (3years) 0 0 0 0 0 0 0 0 0 0 0 0 222 451
Cites / Doc. (4years) 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,27 0,39 Cites / Doc. (3years) 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,27 0,39 Cites / Doc. (2years) 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,27 0,39 References / Doc. 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 17,48 17,99 15,23
Cited Docs. 0 0 0 0 0 0 0 0 0 0 0 0 43 101
Uncited Docs. 0 0 0 0 0 0 0 0 0 0 0 0 179 350
% International
Collaboration 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 0,00 5,86 5,68 5,31