learning redefined
LESSON 1: ADVANCED ICT CONCEPTS AND PC OPERATIONSWe are living in the "digital decade," according to Microsoft Chairman Bill Gates.
Today, computer advances influence all individuals, families, organizations, and schools (Figure 1). As discussed on your CIT manual, computers are an essential part of people's daily lives; they quickly have become a mainstay, much as the automobile, television, and telephone have.
In the future, computers will take on many new roles and become an even more pervasive and critical part of homes, schools, and businesses. This special feature looks at several computer technology trends that will influence the direction of the computer field and then looks at the impact those
technologies will have on information technology in business.
In the future, computers will have an even more important role in all aspects of your life by providing vast information resources, fast communications, and powerful support for activities in homes, schools, and businesses.
1.1 TRENDS IN COMPUTER TECHNOLOGY
During the next several years, the greatest advances in computer technology will occur in areas such as:
• hardware
• software
• communications and networks,
• mobile and wireless connectivity • robotics
1.1.1. HARDWARE
Manufacturers intensely are developing and producing new devices, including tablet PCs, microdisplays, and headsets, that will pervade all aspects of people's lives, especially learning and playing.
This hardware will contain faster and smaller chips, which could be implanted in your body.
• Atomic Quantum computers and optical computers could process data at record-breaking speeds.
• Fluorescent multiplayer discs and digital books will revolutionize the ways information is stored and accessed.
1. UBIQUITOUS COMPUTING
Computers are not yet everywhere especially those who are in remote areas, but as they get smaller, faster, and less expensive, they are being utilized in everything from
toothbrushes and curling irons to cars and spaceships.
Ralph Merkle, a research scientist at Xerox's Palo Alto Research Center, envisions a "not-so-distant future, maybe by 2020, definitely by 2050, [in which] we will have devices with the computational power of . . . roughly a billion Pentium computers." Every device known to man, including the human body, will use some type of computer.
According to Doug McGowan, President, Suitelinq, Inc.:
learning redefined
These issues are serious enough, in his view, that the PC will have to undergo significant changes in order to make computing truly pervasive and easily useful to everyone:
1. Windows interface. Although much improved over earlier versions, it is still complicated and hard to learn. Many people have difficulty using their computer, either at home or at work.
2. Security. PC’s today have still have major security issues once they are installed on a network.
3. Data accessibility. If you put all of your significant work and personal data on a single PC, then you have to be at that PC to access any of the data. Once you’re more than 6 feet from the PC, it becomes totally useless to you.
4. Upgradability. Every 3 years or so, most users find they need to replace their PC. This is a major hassle. Although it is easy enough to buy and install the PC (ignoring monetary issues.), it is another thing to get this new PC to be ‘yours.
5. Usability. As mentioned above, today’s PC is much easier to use than older ones. Microsoft, and all application developers, have made major strides in computer usability. However, there is much more to do. These devices are still too intimidating to many people, especially older people.
2. NEXT GENERATION CHIP
New production techniques will use nanotechnology, which is the science of building molecular devices one atom at a time. The precise positioning of these atoms increases computing power, which enhances the intelligence needed to solve some of the most complex problems worldwide.
Engineers are using extreme ultraviolet lithography (UVL) to turn their circuit designs into silicon chips. This technology uses ultrasmooth mirrors, rather than optical projection, to draw circuits that are 100 times more powerful than today's chips.
IBM Corp. is introducing its next generation of microprocessor chips and systems that use them, hoping to extend the computer giant's recent lead in the market for midrange servers.
The computer maker says its Power7 chip, is four times faster than its predecessor.
IBM is also announcing new servers for chores like:
• Processing cancer-research data, • Managing electrical grids
• Analytics for financial institutions
The IBM announcement comes amid a flurry of activity in chips aimed at servers. Intel Corp. is expected to introduce a long-delayed version of its high-end Itanium product family, a separate product family from the x86 chips used in most personal computers and lower-priced servers.
Intel's latest Itanium—a massive chip with two billion transistors that is code-named
Tukwila—is expected to be used by customers that include Hewlett-Packard Co., the Palo Alto, Calif., company that helped develop the original Itanium design in the 1990s.
learning redefined
Figure 2: Video and television images will appear right before your eyes with new visual appliances.Figure 3: Microdisplays give you the visual equivalent of a 19-inch monitor and allow you to view Web pages, e-mail, maps, and calendars.
Figure 4: Doctors hope to use a microsubmarine to detect and repair defects in the human body. This device measures four millimeters in length and 0.65 millimeter in diameter.
In the announcement it was mentioned that:
"As the beginning of a new era" in information technology that delivers integrated solutions to customers rather than "a bag of parts."
Other moves are coming from the company in 2010 that will further change the economics of the IT infrastructure for businesses.
3. MICRODISPLAYS AND HEADSETS
You will be seeing technology in a whole new way with the advent of visual devices that resemble glasses and sunglasses (Figure 2).
One model replicates a 52-inch television screen
or Sony PlayStation 2 on an LCD screen.
IBM has developed glasses that translate Japanese signs to English.
Headsets plug into computers, digital cameras, and DVD players and allow a display measuring one-tenth of an inch to look like a full-sized theater screen. Microdisplays the size of postage stamps fill your field of vision and appear as large as a regular monitor when magnified (Figure 3).
4. HUMAN COMPUTER INTEGRATION
Some researchers believe the processor eventually will become an integral part of the most complex device known - the human body.
Physical therapists, athletic trainers, and footware designers
will use the data collected by sensors integrated into smart sneakers.
Computers already are used inside the human body. Cochlear implants, for example, help some deaf people hear by stimulating the ear and the nerves that send information to the brain. The next step in human computer integration will involve implanting chips in
the body to help it perform basic functions (Figure 4).
5. ATOMIC QUANTUM COMPUTERS
By the middle of this century, the computer on your desk could very well be filled with liquid instead of transistors and chips. It probably will be called a QC for Quantum computer, rather than a personal computer.
Quantum computers use quantum mechanics, rather than digital technology. In a Quantum computer, bits are replaced by atoms.
Quantum computing represents a new paradigm in information processing that may complement classical computers.
learning redefined
Figure 5Figure 6
"At some point in time you get to the limit where a single transistor that makes up an
electronic circuit is one atom, and then you can no longer predict how the transistor will work with classical methods," by UW-Madison physics professor Mark Saffman.
6. OPTICAL COMPUTERS
An optical computer (also called a photonic computer) is a device that uses the photons of visible light or infrared (IR) beams, rather than electric current, to perform digital computations.
It transmitting data using optical technology has become commonplace in:
• CD-ROM drives
• laser printers • photocopiers
• scanners
• fiber-optic digital communications
Some engineers believe this technology will extend to computers using visible light or infrared beams to perform digital
computations, increasing the speed of operations tenfold. Likewise, it should decrease the optical computers' physical size
because the light beams can pass through each other without interacting.
7. FLOURESCENT MULTIPLAYER DISC
The next step in storage capacity is the Fluorescent Multilayer Disc (FMD). The first generation of this five-inch clear optical medium can hold 140 GB of data - almost 30 times more than a DVD-ROM disc can store.
Data is recorded on fluorescent materials, which reflect light, on the disc's multiple layers. These discs could have as many as 100 layers of data, which will increase their storage capacity to one terabyte (one trillion bytes).
Uses include high-definition television, digital cinema, and mobile applications such as digital cameras. FMD-ROM drives currently are read-only, but engineers are perfecting recordable FMD technology.
Fluorescent Multilayer Disc (FMD) was an optical disc format developed by Constellation 3D that uses fluorescent, rather than
reflective materials to store data.
Reflective disc formats (such as CD and DVD) have a practical limitation of about two layers, primarily due to interference, scatter, and inter-layer cross talk.
However, the use of fluorescence allowed FMDs to operate according to the principles of 3D optical data storage and have up to 100 data layers.
learning redefined
8. DIGITAL BOOKSThe Internet clearly will have a major impact on libraries. During this decade, many libraries will convert hard copy documents into digital form. Eventually, this could develop into online universal libraries to which all schools have access.
Initial consumer reluctance for the electronic book, or e-book, is expected to subside more in the next few years. Several companies have introduced these small book-sized computers (Figure 6) that can hold up to 56,000 pages, or about 150 books' worth of text. By pressing a button, you can move forward or backward through the text. You also can download Web pages and add notes or highlight text using a small pen input device.
Figure 7: Demand is expected to increase for electronic books (e-books). Some of these devices can hold up to 56,000 pages, or the equivalent of 150 books' worth of text.
An e-book (short for electronic book,or EBook), also known as a digital book, is "an electronic version of a printed book which can be read on a personal computer or hand-held device designed specifically for this purpose".
9. TABLET PC
These devices, about the size of a legal pad of paper, can be used with a mouse and a keyboard. You also can enter text and numbers using a pen-like tool.
In general terms, tablet PC refers to a slate- or tablet- shaped mobile computer device, equipped with a touchscreen or stylus.
Figure 8: HP Compaq tablet PC with rotating/removable keyboard
10. VIRTUAL KEYBOARDS
Typing a document or entering numbers in a
worksheet may become easier by not using an actual keyboard. New wireless products (Figure 9) allow users to strap sensors on their fingers or hands and then make hand motions to type or control their computers.
Figure 9: Enter data and control your computer using a wireless virtual keyboard.
11. EDUCATION
The use of personal computers in educational settings is another rapidly growing area. The Internet and the World Wide Web are affecting education, as distance education allows students to take classes or Webinars - online seminars - whenever they have time from home or workplace computers. Such courses are ideal for workers seekingadvanced training but lacking the time to pursue on-campus studies or for undergraduates living far from campus.
learning redefined
If you wanted to learn Dutch, you could purchase a chip from a local retail store, just as you purchase a CD. Once you upload the chip to your brain through an implanted port,
immediately you will know Dutch - without ever taking a class.
Distance education, or distance learning, is a field of education that focuses on the pedagogy, technology, and instructional system designs that aim to deliver education to students who are not physically "on site".
Technologies used in delivery
The types of available technologies used in distance education are divided into two groups:
1. Synchronous technology: Is a mode of online delivery where all participants are "present" at the same time requiring a timetable to be organized.
Web Conferencing is an example of synchronous technology.
2. Asynchronoustechnology: Is a mode of online delivery where participants access course materials on their own schedule. Students are not required to be together at the same time.
Message board forums, e-mail and recorded video are examples of asynchronous technology.
12. ENTERTAINMENT
For the younger members of the family, playing games using entertainment software always has had a large appeal.
Many adults, however, find that entertainment software also provides them with hours of enjoyment. Popular types of entertainment software include arcade games, board games, and simulations.
Entertainment software also consists of a variety of interactive adventure games, which range from rescuing a princess from a castle's dungeon to solving a murder mystery. You can play many of these games in groups using a network or on the World Wide Web, or you can play simply with the computer as your opponent.
1.1.2. SOFTWARE
Several trends are emerging within the area of software development. A second major area of technology innovation involves the instructions that tell computers what tasks to perform.
Software trends include:
• improved user interfaces
• enhanced Internet content
• digital music
• MP4 video compression
• intelligent agents
• speech recognition
• remote control of home appliances
1. USER INTERFACE
Most computers use a graphical user interface (GUI), which developers have dubbed the WIMP (windows, icons, menus, and pointer) interface.
To use the WIMP interface, you must learn a new mode of communications that includes pointing, clicking, dragging, and so on.
Next-generation operating systems will be more natural and human-centric, meaning they will allow you to interface with a computer using many of the methods you now use to
communicate with humans. Such methods will include natural language, hand gestures,
learning redefined
2. THE INTERNET AND THE WEBIn this decade, the Internet and the Web promise many exciting developments. The Internet is the fastest growing segment of the computer industry and is a major reason why
consumers are buying personal computers and handheld devices at a record pace.
At present, individuals primarily use the Internet to access information and communicate using e-mail. In the future, individuals increasingly will rely on two other Internet-based communication applications - telephony and videoconferencing.
Other developments will be Web tablets (Figure 10), which feature full-color touch screens allowing users easy access to the Internet, and the continued integration of television, networks, and computers.
Figure 10: Web tablets offer consumers easy access to browsers and Web sites.
The Web as a Platform
The browser provides a rich runtime environment and friction-free access to applications.
Developers are increasingly choosing the web as their platform of choice for software and software development.
Increasingly, developers and designers are using tools that offer a rich development, debugging, and profiling experience designed for the web. JavaScript libraries allow web developers to get more done with JavaScript than ever before while reaching a wide audience, and immersive internet applications, such as those written for Silverlight, allow developers to break free of the limitations of HTML and take advantage of a range of resources and features while guaranteeing compatibility across platforms.
3. MUSIC AND THE INTERNET
As more digital music becomes available for download from the Internet, market analysts predict fewer consumers will buy CDs and instead will turn to MP3 and other digital audio players.
MP3 technology compresses audio files, so music can be downloaded from Web pages and transmitted in e-mail messages much faster than with uncompressed files. Sales of players using this technology have soared, in part to Shawn Fanning and his Napster software and company, which were created as a means of allowing music lovers to swap songs.
Legal proceedings for copyright infringement against Napster and its progeny helped spur consumer awareness that high-quality music is available on the Internet, and many musicians have released songs solely on the Web. Sony and many other entertainment companies are pursuing selling music via Internet-based pay-per-listen systems. Some analysts predict one-third of all consumers will have virtual music collections.
4. MP4 VIDEO COMPRESSION
Video files can be compressed to 10 percent of their original size with MP4 technology, which filters out images the eye cannot perceive.
Using today's standards, a full-length compressed video would take two hours to download, but as broadband Internet access and data transfer rates increase, the download time should become more manageable.
learning redefined
5. INTELLIGENT AGENTSFor more than 40 years, artificial intelligence (AI) experts promoted the advantages of smart software - that is, software with built-in intelligence.
In recent years, as this concept has become reality, the term, intelligent agent, has evolved to describe any software program that independently asks questions, pays attention to work patterns, and carries out tasks on behalf of a user (Figure 11).
Figure 11: Intelligent agents are programs with built-in intelligence that monitor a user's work patterns and carry out tasks independently.
Some intelligent agents are embedded and work within a single program. Other intelligent agents, sometimes called network agents, perform tasks on multiple remote computers with different platforms before bringing the results back to the user.
Intelligent agents already are a part of several productivity software packages. Some e-mail software, for example, includes intelligent agents that allow individuals and businesses to filter incoming messages and request immediate notification of messages about specific subjects or from specific individuals. The Intellisense™ technology built into Microsoft Office XP also is based on an intelligent agent.
6. SPEECH RECOGNITION
The ability to understand a natural language means that a computer will be capable of translating your spoken statements into computer instructions and responding in an appropriate fashion. Microsoft Office XP includes speech recognition software, which allows you to speak the names of menu commands, toolbar buttons, dialog box controls, text, and numbers.
In the near future, computers will support continuous-speech voice recognition and use artificial intelligence to determine the meaning of your spoken
words.
In an even more advanced use of speech recognition, computers will recognize your voice commands and respond in a computer-generated voice through an on-screen presence that resembles a person, animal, or other object.
IBM and Apple, for example, have developed prototype interfaces that resemble the human head (Figure 12). When using this interface, you turn off the computer by telling the character to go to sleep. The character closes its eyes and droops its head as the computer begins to shut down.
Figure 12: Companies have prototype interfaces that resemble the human head to make voice recognition more realistic.
7. CONTROL OF HOME SYSTEMS
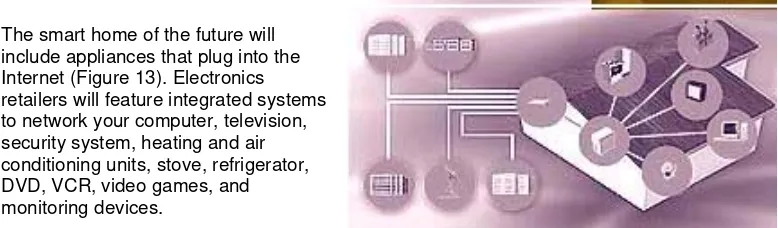
The smart home of the future will include appliances that plug into the Internet (Figure 13). Electronics retailers will feature integrated systems to network your computer, television, security system, heating and air conditioning units, stove, refrigerator, DVD, VCR, video games, and monitoring devices.
learning redefined
You then will be able to use a telephone or computer to change the operation of one of the control systems, such as turning lights on or off or viewing the contents of your storeroom by using a Web cam.
Smart appliances using the Sun Microsystems Java and Jini technologies can perform time-consuming chores.
1.1.3. COMMUNICATIONS AND NETWORKS
The methods of transmitting and sharing data are changing dramatically. Updates include Microsoft's .NET strategy, personal area networks, home wireless networks, wired broadband, wireless communications, the Bluetooth™ standard, mobile Internet access, global positioning systems, electronic paper and ink, and multiple-function telephones.
1. .NET AND SOFTWARE SUBSCRIPTIONS
Microsoft's .NET strategy is a new environment for developing and running software applications.
.NET will provide instant access to data and services in the context of your current task. Microsoft plans to shift the focus of software from the desktop to Web-based services and to extend Windows XP elements to the Internet.
2. PERSONAL AREA NETWORKS
A handshake may mean more than a goodwill gesture. Two people wearing small
transmitters and receivers could communicate by exchanging digital data using the electrical conductivity of their bodies. Their handshake will complete the electric circuit needed to transfer this data.
3. HOME WIRELESS NETWORKS
Most technology companies are taking sides and backing one of two competing wireless standards for the home, but others are backing both.
Apple Computer, Dell Computer, Sony, 3Com, and 70 other companies are supporting the Wi-Fi (wireless fidelity), or 802.11B, standard, while Intel, Motorola, Hewlett-Packard, and 80 other corporations are backing the alternate HomeRF standard. IBM and other companies are backing both, reluctant to be caught with obsolete equipment.
The battle for dominance likely is to continue as new Net appliances and wireless devices emerge, data transfer rates increase, and prices drop.
4. WIRED BROADBAND
During the next few years, home and business users can expect much faster access to the Internet as cable and telephone companies provide broader bandwidth.
As discussed in previous manual (CIT), bandwidth is a measure of the amount of data a communications channel can transmit over a given period.
The key to speeding up Internet access is to increase the bandwidth of the communications channel between the user and the access provider.
For most users, this part of the communications channel, which is called the last mile, often involves using a modem to dial up and connect to a server over slow analog telephone lines.
learning redefined
1.1.4. MOBILE WIRELESS CONNECTIVITYAs the personal-computing market matures, consumers are looking for new ways to access the Internet and to communicate.
Cordless products are in high demand, and these devices with Bluetooth™ technology were flood more in the market. Third-generation communications service will increase Internet services.
Other advances will be made in global positioning systems, electronic paper and ink, and multiple-function telephones.
1. WIRELESS DEVICES
Recent advances in digital wireless technology have focused on using mobile telephones and handheld computers and devices. During the next few years, as these wireless forms of communication become the norm, attention will turn toward developing cordless computers (Figure 14) and other household appliances.
Figure 14: Wireless desktop connections will continue in popularity.
Wrist-top computers will allow you to make a telephone call and check your e-mail, pager messages, and appointments.
Palmtops are expected to be the top-selling wireless devices (Figure 15) with an average annual growth of 28 percent from 2004. Palm, Inc., continues to dominate the wireless market, but products from
Handspring and from companies using the Pocket PC 2002 operating system will continue to erode Palm's market share.
Figure 15: Wireless Internet connections will boost sales of handheld computers, particularly with expansion port add-ons such as keyboards, GPS modules, and bar code scanners.
2. BLUETOOTHTM
Bluetooth™ technology allows cellular telephones, pagers, handheld computers and devices, and other wireless products to detect one another and communicate across short distances, usually a maximum of 30 feet.
The Bluetooth Special Interest Group (SIG) developers from the computing, networking, and telecommunications fields jointly planned a wide range of applications, such as those that allow travelers to receive flight information automatically at airports or to be directed to the nearest coffee shop as they walk down a street.
Shoppers with Bluetooth-enabled cellular telephones could receive coupons as they walk past displays.
Figure 16: Samsung Bluetooth
learning redefined
3. MOBILE INTERNET ACCESSJapan's pioneer mobile-Internet company, NTT DoCoMo, Inc., plans to lead the world's new phase of broadband services, Wideband Code Division Multiple Access (W-CDMA).
This third-generation (3G) mobile communications service has the data-transmission capacity to download songs and short video clips.
Each day, more than 50,000 new Japanese consumers subscribe to DoCoMo's mobile Internet service, i-mode (Figure 17), which provides access to thousands of official i-mode and independent news services, information, and entertainment, as well as such specialized services as airline reservations, online shopping and banking, and the ability to exchange digital images.
Figure 17: NTT DoCoMo's i-mode mobile Internet service is immensely popular among Japanese consumers.
In contrast, American consumers have been reluctant to subscribe to mobile services that offer shopping, weather updates, and e-mail. DoCoMo has invested $9.8 billion in AT&T's wireless unit, representing a venture to close the gap between wireless technologies in the two countries.
Wireless Internet access makes mobile email access and Web searching possible from phones and roaming mobile computers.
Wi-Fi, which stands for wireless fidelity, is a wireless networking technology used across the globe.
Wi-Fi (pronounced /’waifai’/) is a trademark of the Wi-Fi Alliance that may be used with certified products that belong to a class of wireless local area network (WLAN) devices based on the IEEE 802.11 standards. Because of the close relationship with its underlying standard, the term Wi-Fi is often used as a synonym for IEEE 802.11 technology.
Figure 18: WIFI
4. GLOBAL POSITIONING SYSTEMS
learning redefined
Cellular telephone companies will be able to locate the position of their callers to within 100 meters and when localized wireless advertising is available.
Cellular telephones may contain GPS technology that can be used on a pay-per-use basis.
Designed to be implanted in the human body, the Digital Angel™, wearable patch (Figure 19) will send and receive GPS information along with medical diagnostic data.
In another use, a wind-up generator may provide the power for recreational GPS users who travel without power, such as hikers, bikers, and kayakers.
Figure 19: The Digital Angel™ provides location
and monitoring information. Its microchip includes biosensors that measure body parameters and an antenna that communicates with GPS satellites.
The Global Positioning System (GPS) is a satellite-based navigation system made up of a network of 24 satellites placed into orbit by the U.S. Department of Defense.
5. ELECTRONIC PAPER/ELECTRONIC INK
Engineers are developing electronic paper and ink products (Figure 20) that combine the strengths of digital technology with the qualities of paper, including its light weight and high contrast.
Several companies are developing this rewriteable medium. Some use microscopic liquid particles or beads that are white on one side and black or red on the other and are suspended in a transparent plastic cavity. This display screen currently is as thick as a mouse pad, but eventually it will become as thin as four sheets of paper. The particles or beads respond to electronic impulses and move depending on the images requested.
The next generation of e-paper will add organic light-emitting diodes (OLEDs) to the plastic sheets to display full color and full-motion video.
Figure 20: Electronic paper and ink products can be used for commercial displays. The
messages can be changed by remote control.
6. MULTIPLE-FUNCTION TELEPHONES
Cellular telephones will be packed with new features. Some will be popular among young users - those between the ages of 10 and 24 - who are the target group for the newest products (Figure 21).
The fastest growing cellular telephone application is e-mail messaging. Nearly every digital wireless telephone sold will feature this two-way text messaging, which allows users to type short messages into their telephones and then transmit the words to other wireless telephones.
Figure 21: Cellular telephone manufacturers and carriers are aiming to lure young users to their products. (Source: Cahners In-Stat Group)
This service is very popular in Asia and Europe, especially in countries that do not have reliable or easily accessible wired telephone service.
learning redefined
More people worldwide will be accessing the Internet via cellular telephones rather than by personal computers. Fourth generation (4G) wireless standards are in place now in 2010, and they will offer even more faster mobile Internet access.
1.1.5. ROBOTICS
Computers capable of performing human tasks will be seen everywhere from hospitals to your home. Medical breakthroughs achieved in hospitals include brain pacemaker implants and distance surgery. Homes are becoming lively and clean with the advent of robots for entertainment and vacuuming.
1. BRAIN PACEMAKER
Scientists working with monkeys and studying how brain cells interact are perfecting a type of pacemaker to implant in the brain and send brain waves directly to a robot or device (Figure 22).
Figure 22: Research involving monkeys is helping researchers’ record brain cell activity. When the monkeys perform a learned task, their neurons generate brain waves that are transmitted to computers via wires implanted in the monkeys' brains. The computer decodes and sends the data to a robot that replicates the monkey's movements.
One practical use is for reading the brain waves of people with seizure disorders, anticipating a seizure, and delivering drugs or electrical impulses that can stop or prevent a seizure.
2. DISTANCE SURGERY
The next generation of health care will promote the use of robots to perform surgeries (Figure 23).
The robots' precise skills and small sizes - less than one-fifth the size of traditional instruments - make surgeries less invasive and recovery times less prolonged. Surgeons view three-dimensional images of internal organs on large monitors and can control the robots' actions through voice commands.
Operating rooms will undergo another dramatic change when surgeons practice telemedicine. Through the use of
videoconferencing and satellites, doctors can perform surgery when they are in locations other than the operating room.
Figure 23: Robot-aided surgeries help surgeons remove brain tumors. Information regarding the precise location of the tumor displays on the monitor and is fed into the robot's computer. Robotic surgeries result in minimal damage to the surrounding brain tissue.
3. AIBO
Now you can have mankind's best friend without the mess and expensive veterinarian bills.
Sony Corporation's AIBO (Artificial Intelligence Robot), which coincidentally is the Japanese word for companion, is a breed of entertainment robot with voice recognition technology,
emotions, instincts, the ability to learn 50 verbal commands, and senses for touch, hearing, sight, and balance (Figure 24).
Figure 24: Each AIBO develops an individual personality based on its interaction with its environment.
learning redefined
1.2 THE FUTURE OF INFORMATIONS SYSTEMS IN BUSINESSAlthough millions of homes now include one or more computers, businesses by far are the largest users of computers.
Around the world, organizations install and use millions of computers of all types - mainframes, personal computers, and more - for applications such as inventory control, billing, and accounting. These computers often are part of a large information system that includes data, people, procedures, hardware, and software.
Existing business information systems will undergo profound changes as a result of the computer trends just described.
As computers become increasingly ubiquitous and technologies converge, businesses will rely on computers for communications - and users at all levels will need to be computer literate. These new technologies will enhance security measures, provide computers for all employees, improve
communications and health care in hospitals, and shape t-commerce (embedded television advertising) and e-business.
1.2.1 AUTHENTICATION/SECURITY
Public surveillance by businesses, government, and institutions is a growing industry, spurred by smaller and less expensive technology.
According to the Security Industry Association, nearly $2 billion has been spent on computer controlled closed-circuit television networks such as those being
used in more than 60 U.S. cities to curb vandalism, prevent crime, and record incidents.
Surveillance is being taken to a higher level with software that converts images of faces to a series of 14 reference points, such as the eyebrows' bone structure and the distance between the eyes. This data is stored in databases and compared at rates of 45 million records per minute with people who pass by security cameras at countries' border crossings and who apply for new driver's licenses.
Upcoming software can be trained to recognize threatening behavior, such as when someone points a gun, and then alert the police.
Applications also could help maintain security at automatic teller machines, where cardholders' facial images could be stored in a database and compared with a person using the machine (Figure 25).
Figure 25: Instead of entering a PIN, automatic teller machine users can access their accounts securely using face recognition to verify their identities.
Computers also will use video cameras to record and identify individuals through facial expressions and fingerprint recognition (Figure 26).
Industry experts’ project that surveillance cameras could become so prevalent that everyone could watch everyone at anytime.
learning redefined
1.2.2 WIRING THE ENTIRE WORKFORCEFor many years, computer use centered around white-collar professionals sitting at desks using wired computers.
Indeed, of all employees, nearly 70 percent use some type of computer during the workday. With the influx of wireless products, manufacturers are striving to wire the other 30 percent of workers holding mobile positions, such as mechanics, inspectors, messengers, and warehouse workers, so they can send and retrieve detailed information while keeping their hands free for other tasks.
The Palm OS® and Pocket PC 2002 platforms are opening opportunities for the blue-collar world, as are hardware and software advances in speech recognition, wireless headsets, and wearable computers equipped with processing power equal to that of desktop computers.
1.2.3 HEALTH-CARE INDUSTRY
The medical industry has been recognized, in general, as being one of the last fields to integrate the Internet and high-tech solutions.
Recent cuts in insurance reimbursements and federal Medicare spending have decreased revenues, resulting in budget-cutting measures.
Many health-care facilities, however, are integrating online medical-records systems, electronic medical charts, and medical literature searches. Wireless products will help improve patient care and communications; for example, some emergency room personnel use Palm handheld computers to access patients' medical records.
1.2.4 T-COMMERCE
Television advertising is taking a new turn with the advent of t-commerce. Instead of buying commercial time, advertisers embed their ads in actual television programs (Figure 27).
Viewers use their remote controls to interact with the television programs and advertisements by replying to free offers, buying items, receiving sports scores, and participating in games. The Wink service is featured on CNN, The Weather Channel, ESPN, and "The Tonight Show with Jay Leno." This form of advertisement can be termed merchantainment - a combination of
merchandising and entertainment.
Figure 27: Wink Communications uses t-commerce in a variety of television programs.
1.2.5 E-BUSINESS
The volatile e-commerce marketplace has produced some winners and many losers. Companies with greater successes were those with both Internet and physical presences, known as clicks-and-mortar businesses.
Each year, individual and business consumers purchase more goods and services online; approximately 50 percent of Web users shop online, and the same percent of investors trade securities online.
During the next few years, more e-commerce applications - and the technologies used to support them - will be developed.
learning redefined
1.3 SYSTEM MAINTENANCE AND TROUBLESHOOTINGMaintenance is not the same thing as repair. Proper maintenance can prevent the need for repairs when performed in a timely fashion. At the same time, performing needed maintenance can sometimes do more harm than good. The old adage "If it isn't broke, don't fix it" applies just as much to computers as it does to a tractor. This lesson covers the basics of developing plans and procedures for
performing routine maintenance.
1.3.1 DEVELOP A SET OF MAINTENANCE PLANS AND PROCEDURES
Computers are devices built on the very concept of logic. A logical approach will go a long way toward keeping them running properly.
Having a well-organized, predefined set of plans and procedures covering the different aspects of computer care for every class of computer and operating system you deal with is required to make sure that you offer the same level of appropriate care to all of your clients.
Let's define the terms plan and procedure:
A plan is the broader scope of care, and it can contain several procedures. For example, a periodic maintenance plan can detail the activities and tasks that should take place at regular intervals (daily, monthly, annually, and so on), or relative to some specific activity, like a system upgrade.
A procedure is a detailed list of steps that should be performed, often in the form a checklist. This list can also include the necessary tools, parts, and remarks about important issues regarding the procedure.
One way to organize plans and procedures is to have a maintenance policy manual. These policies can be ordered by time since the last regular maintenance, and there should be an appropriate plan for each interval.
The monthly plan might include:
• Regular disk defragmentation,
• A performance inspection,
• A short conversation with a user to ascertain if the system is performing as well as expected, and
• An update of the master recovery disks.
Some of these same procedures might also show up on the semiannual and annual plans. The plan references the procedures, which are kept in a separate part of the folder or another folder altogether.
If a change in policy or a change in the operating environment requires changes to a given procedure (perhaps due to new software), then simply updating a machine with the procedure will automatically bring all the periodic plans into compliance.
One of the keys to success is:
• To develop a maintenance program that takes into account the types of computers you will be working on,
• The needs of the end user, and
• The best practices recommendations provided by the manufacturers of the hardware and the software vendors.
Another critical element of success is putting the plans and procedures into writing and keeping good records of the tasks performed, as well as the computers on which they were performed.
1. Automated Tasks
learning redefined
2. Keeping Proper RecordsWhen working with computers, it is as important to work smart as it is to work hard. Being organized and keeping good records is the key to becoming efficient, effective, and successful.
A simple set of records with essential information and a work history for each computer you work on can make identifying tasks, settings, and potential problems much easier.
Excel or Access can be used to make virtual quick references. Keeping it on a laptop makes it both easy to maintain and easy to access when out on a call. Be sure to back up the data and keep a hard copy on file for quick reference.
The following table provides some suggestions about the information you might want to keep.
Suggestion Usage
Name each computer.
The actual name you choose does not matter, but make it unique and descriptive.
9 One idea is to use the same name that Windows uses to identify the computer on a network.
9 You may have to add some notes about who the related client is or the location.
9 Establish naming conventions to make remembering them easier. 9 Use names in addition to serial numbers.
Document all technical information.
Include the:
9 operating system name and version,
9 startup and configuration files, 9 hardware IRQs (interrupt
requests),
9 I/O (input/output) base address,
9 direct memory access (DMA) channels,
9 device driver names, 9 processor type and speed, 9 size of cache,
9 RAM (random access memory),
9 BIOS (basic input/output system),
9 monitor, video card, modems, and sound cards.
Save startup data to floppy disks (unique data).
Include the startup disk (based on the current version of the operating system), device driver disks, and recovery disks—as required by an antivirus program or system.
Keep an incident log.
In your log of events for each computer, include such things as the user, application installations (date and version), upgrades (hardware), and problems (cause of failure and actions taken for resolution). Set up a local and
specific
maintenance task schedule.
Include in the front part of the log a list of the tasks that are to be performed and how often. Note the dates when they have been performed and by whom.
1.3.2 BASIC HARDWARE MAINTENANCE
Cleaning
For the most part, computer equipment is very reliable and lasts a long time. However, dirt and other airborne contaminants will greatly accelerate the deterioration of computer equipment. Therefore, part of a good preventive maintenance regimen is keeping the equipment clean.
The first step is to be sure that the computer is installed in a computer-friendly environment. This means that it should be in a dust-free (relatively speaking), smoke-free, and humidity-controlled (within a range of 50–70 percent relative humidity) location.
learning redefined
In the event that the location of a computer is not as desirable as it should be, the frequency of preventive maintenance (cleaning) should be accelerated. In these instances, consideration should be given to establishing a computer-friendly zone around the computer, for instance, installing it into a cabinet and providing a source of clean fresh air.
The table below describes what a computer technician should include in a basic cleaning kit.
Item Usage
Lint-free chamois cloth or old t-shirt
A cloth is useful for cleaning the outside surfaces.
Cleaning solution
Standard household cleaning solutions (not extra-strength) can be used in moderation. The solution should be applied to a lint-free cloth and then applied to the computer surface. Do not use aerosol sprays. These generally use solvents as a propellant, which can damage the plastic as well as the electrical components of a computer.
Foam swabs
Use these with cleaning solutions to clean small parts such as the wheels inside a mouse. (Cotton swabs are not recommended, because the cotton fibers can come off and be a contaminant themselves.)
Antistatic spray
An antistatic spray or solution should follow any cleaning in envi- ronments with a risk of ESD. A solution composed of 10 parts water to 1 part common household fabric softener will do.
Small paintbrush or small hand-held vacuum cleaner
Use to remove dust from around the computer and inside its cabinet. The vacuum can be used to remove dust from the keyboard and other input devices.
Canned air
Use to remove dust from the power supply fan or from inside a computer. These cans can be purchased from any computer supplier; they are made especially for removing dust from electronic equipment.
CAUTION: Never use liquids to clean inside a computer. Never apply liquids directly to the surface of a computer. Never use solvent-based cleanser or aerosols.
The proper placement or location of a computer relative to its environment is important for ease of maintenance and long life.
In summary, a computer should be:
• Located in a dust-free and smoke-free environment
• Subjected to controlled humidity (50–70 percent relative humidity)
• Subjected to controlled temperature (do not place too close to a heater or in direct sunlight— avoid temperature extremes)
• Have good ventilation (make sure fan and ventilation vents aren't blocked)
1.3.3 GENERALPREVENTIVE MAINTENANCE
For the most part, the MTBF (mean time between failures) of a computer and its peripheral devices is quite long. By following the general cleaning and safety measures just described, you can extend this time.
This lesson describes several components and their special maintenance requirements.
1. Monitors
learning redefined
• Keep it clean—use periodic cleaning, dusting, and good common sense with a monitor.• Use simple cleaning solutions, not aerosol sprays, solvents, or commercial cleansers. Don't use window-cleaning sprays on a monitor screen.
• Do not leave unattended monitors on for extended periods of time. Use a screen saver or the computer's power-conservation features to reduce power consumption and (on older models) to prevent burn-in of the monitor screen.
• Don't ever attempt to work inside the cabinet unless you are properly trained to do so.
• Don't tamper with the monitor. Monitors emit x-ray radiation. Changing the settings or operating the monitor with the cover removed can disable the manufacturer's safety devices, thus increasing the hazard.
2. Hard Disk Drives
Hard disk drives are another type of device that requires very little intervention to keep running. Mechanical failure of hard drives is rare, and, when it does occur, the solution is generally replacement.
Here are a few suggestions for preventing mechanical problems with hard drives:
• Avoid rough handling.
• Never move a hard disk when it is still spinning.
• Never expose the internal housing to open air.
• Perform regular data backups and disk maintenance tasks.
3. Floppy Disk Drives
Floppy disk drives are highly susceptible to failure. This is due mostly to the fact that they are exposed to the environment (through the disk slot) and to mechanical damage from insertion and removal of disks. When they fail, the best solution is usually to replace them because they are inexpensive and simple to install.
Here are a few tips to increase the life of floppy drives and disks:
• Do not expose the disks to magnets.
• Never touch the exposed surface of a floppy disk.
• Do not allow smoking near a computer.
• Clean the read/write heads. Special head-cleaning diskettes and solutions such as
isopropyl alcohol and methanol that do not leave a residue when they dry are available. Cotton swabs are not recommended because of the fibers they shed. Use cellular foam swabs or a lint-free cloth.
4. Keyboards and Pointing Devices
Keeping a keyboard and mouse clean is the key to prolonging their lives. Never place drinks (coffee, soda, tea, and so on) around a keyboard; spilling liquids is a common cause of keyboard failures.
Here are a few tips to increase the life of a keyboard, mouse, or other pointing device:
• Use a handheld vacuum cleaner to remove dust from the small crevices.
• Never use spray cleaners.
• Clean a mouse or trackball by removing the ball and cleaning the rollers (if it has a ball inside).
learning redefined
5. PrintersPrinters are more mechanical than other peripherals and therefore require more attention. Because they use paper, ink, or carbon, printers generate pollutants that can build up and cause problems. Always check the manufacturer's recommendations for cleaning.
Following are a few steps for cleaning the most popular types of printers.
a. Dot-Matrix Printers
• Adjust the print-head spacing.
• Check the tension on the print-head positioning belt. Use a nonfibrous swab dipped in alcohol to clean the print head.
• Clean the printer's roller surfaces.
• Clean the surface of the platen.
• Clean the gear train of the paper-handling motor.
• Apply light oil to the gears using a foam swab.
• Turn the platen to distribute the oil.
• Apply a light coating of oil to the rails.
• Move the carriage assembly to distribute the oil.
b. Ink-Jet Printers
• Adjust the print-head spacing.
• Check the tension on the print-head positioning belt.
• Clean the printer and its
mechanism.
• Clean the printer's roller surfaces.
• Clean the surface of the platen.
• Clean the surface of the ink-jet print head.
• Clean the gear train of the paper-handling motor.
• Apply light oil to the gears using a foam swab.
• Turn the platen to distribute the oil.
• Apply a light coating of oil to the rails.
• Move the carriage assembly to distribute the oil.
c. Laser Printers
• Vacuum to remove dust buildup and excess toner from the interior. Remove the toner cartridge before vacuuming.
• Clean the laser printer's rollers using a damp cloth or denatured alcohol.
• Clean the gear train of the paper-handling motor using a foam swab.
• Apply light oil to the gears using a foam swab.
• Distribute the oil throughout the gear train.
• Clean the writing mechanism thoroughly using compressed air. If possible, wipe the laser lens with lint-free wipes to remove fingerprints and stains.
• Clean the corona wires using a foam swab dipped in alcohol. Be careful not to break any of the strands because, if you do, your printer will be rendered useless until they are repaired.
1.3.4 PREVENTIVE MAINTENANCE SCHEDULE
There are no universal preventive maintenance schedules that work on every computer. Each schedule must be individualized to meet the needs of the work environment.
Use the following suggestions as maintenance guidelines for developing your own polices and procedures.
1. Do This Daily • Back up data.
learning redefined
2. Do This Weekly• Clean the outside of the case.
• Clean the screen.
• Run the appropriate disk inspection program for the operating system in use on all hard disks. Windows comes with scheduling programs to help you accomplish this on a regular basis.
• Run a current antivirus program and check all drives. These programs also come with scheduling features to help you accomplish this on a regular basis. They also remind you when to update the virus list (usually done through the manufacturer's Web site).
• Inspect all peripheral devices.
3. Do This Every Time a New Device or Software Application Is Added to the System • Back up all critical data and system files.
• Update the ERD, Rescue disk, or other core files to a floppy in case of system failure or corruption.
• Store the user license, configuration data, any special settings, and technical support access information in the permanent record file kept for this computer.
• Complete and submit the warranty registration card for this product.
4. Do This Monthly
• Clean the inside of the system.
• Clean the inside of any printers.
• Vacuum the keyboard.
• Clean the mouse ball and tracking wheels.
• Defragment all hard disk drives.
• Delete any unnecessary temporary files.
5. DoThisEvery Six Months
• Perform an extensive preventive maintenance check.
• Apply an antistatic solution to the entire computer.
• Check and reseat all cables.
• Run the printer's self-test programs.
6. Do ThisAnnually
• Reformat the hard disk drive and reinstall all software. Don't forget to back up data first.
• Check all floppy disk drives.
• Consider an upgrade to your computer. Check to see that your components can handle
your workload.
1.3.5 MAINTAINING WINDOWS SYSTEMS ENVIRONMENT
This topic describes the basic steps required to provide proper periodic maintenance to the operating system and data files contained on a Windows-based computer.
Perform the following:
• Provide an appropriate level of virus protection.
• Remove old and unused files on a regular basis and keep adequate open space on disks used for virtual memory.
• Scan the media for errors and fix any problems.
• Defragment the drives.
• Back up files and keep updated recovery disks.
learning redefined
1. VIRUS PROTECTIONViruses are nasty little programs that can wreak havoc on a computer and its data. The sole purpose of a virus is to replicate itself and make life miserable for computer users.
Many viruses are simple annoyances, but some of them can cause irreparable harm to files. Viruses can be caught from various sources including shareware, files downloaded from the Internet, software from unknown origins, and bulletin boards.
There are several different types of viruses:
• File infectors attach themselves to executable files and spread to other files when the program is run.
• Boot sector viruses replace or hide inside the master boot record (or boot sector on a floppy disk). They write themselves into memory any time the computer is booted.
• Trojan horses are disguised as legitimate programs, but, when loaded, they begin to harm the system.
• Macro viruses attach themselves as executable code inside a document (such as a
Microsoft Word document) and run when the document is opened. (They can also attach themselves to certain kinds of e-mail.) It used to be true that you couldn't get a virus from opening a document; running a program was required. Unfortunately, this has changed thanks to the widespread use of macros by computer users. Although macros are very valuable, they mean that when you open a document you are running a program.
• Polymorphic viruses are an especially unsettling class of invader. They're designed to modify themselves over time and replicate new forms. This makes them both unpredictable and harder to detect.
The following are some general guidelines for virus programs:
• Make sure your choice is compatible with the specific version of Windows on the system, including any upgrades. The wrong antivirus program might do more damage than good.
• If the computer has a BIOS setting that allows you to disable boot-sector writes (prevent applications from writing to the boot sector of the hard disk), consider enabling it. This setting must be disabled before installing Windows updates and some other programs as well. Keep in mind these BIOS-level virus checkers are very limited in ability and should not be relied on for total protection.
• Viruses are often transmitted by floppy disks. Be careful when reading a floppy disk of unknown origin or using your disk on an unfamiliar machine.
• Currently, many viruses and macro viruses are transmitted over the Internet. Use extreme caution when you download files, especially if they come from sources other than a manufacturer's Web site. The most secure protection against Internet-distributed viruses is to have an antivirus program running at all times (or at least when you're downloading and first running new files).
• Trust no one when it comes to loading programs on your machine. Be aware that any
program you load on your computer could contain a virus.
• Be sure to keep your antivirus program updated. Hundreds of new viruses are written and transmitted each month.
When designing an antivirus program, you need to take into consideration the needs of the user and the level of risk. A computer that does not have a connection to the Internet or a LAN (local area network) and rarely receives files from outside sources is at little risk.
learning redefined
2. DISK CLEANUPCleaning up old files not only saves on media and reduces copy time during backups; it also frees up disk space and improves file system performance.
Latest Windows offer Disk Cleanup wizards available on the System Tools menu that make cleaning up old files on a disk easy.
Simply invoke the routine and direct it to the desired drive. Wait for the utility to prepare a list of various temporary files, unnecessary program files, files that have been moved to the Recycle Bin, and Internet files that are cached locally on the disk.
You can then determine which of these files you wish to delete. Simply click OK and the files are removed. Figure on the right shows the wizard ready to delete the files.
3. CHECKING DRIVE INTEGRITY WITH SCANDISK
ScanDisk is an incredibly useful program, and, in the early days of MS-DOS, many people bought utilities like this to keep their system running properly. It inspects the file system and fixes problems and can do so when the system is in use.
ScanDisk is built into all the currently shipping versions of Windows. You should be very careful to make sure that any version of ScanDisk you use is actually the one that is compatible with the version of Windows and the file for the PC to be checked and corrected.
On most systems, ScanDisk is available in both a command-line version and one that operates within the Windows graphical user interface (GUI).
The ScanDisk utility can both detect and fix problems on local hard disks, floppy drives, RAM drives, and some memory cards. It works with compressed drives set up using DoubleSpace and DriveSpace, but offers only limited support for third-party compression software.
Among the operations you can perform on a ScanDisk are: • Inspecting the physical surface of the drive for bad sectors
• Inspecting the file structure, compression structure, and volume signatures of any compressed drives
• Locating and repairing crossed-linked files and lost clusters
• Verifying the integrity of both FAT16 and FAT32 file systems
• Verifying and repairing problems with the directory tree structure of a drive
ScanDisk operates in two modes:
1. Standard performs a check of both files and folders;
2. Thorough mode adds an inspection of integrity of the drive's physical surface.
You can set ScanDisk to run automatically and fix errors or to prompt you before making any corrections (see figure on the right).
4. KEEPING FILES ORDERLY WITH DISK DEFRAGMENTER
Disk Defragmenter is a utility you access by clicking Start\Programs\Accessories\ System Tools\, and it is found in all current versions of Microsoft Windows.
learning redefined
The newest versions of Disk Defragmenter have logic that makes them aware of the way the operating system reads executable and dynamic-link library (DLL) files, so they can place clusters in the order they are read.
Both of these operations can significantly improve system performance. This utility should be run at least monthly, and more often on busy systems.
Any time a computer user complains of a slowdown over regular system performance, fragmentation analysis should be performed. Figure on the right shows the Windows program in operation, “Disk defragmentation in process”.
As you can see, it works with both NTFS (Windows NT file system) and file allocation table (FAT)-based file systems.
You can schedule the defragmentation to take place when the computer is not being used, so the speed of its operation is generally not a concern.
Some screen savers or other programs that involve disk activity can slow down the operation of the defragmenter, so for best performance they should be disabled during its operation. Windows offers a Maintenance Wizard to automate this and other common disk care tasks.
1.3.6 SOFTWARE BACKUP AND RESTORE
To prevent against data loss caused by a system failure, computer users should back up files regularly.
A backup is a duplicate of a file, program, or disk that can be used if the original is lost, damaged, or destroyed.
In the case of a system failure or the discovery of corrupted files, you restore the files by copying the backed up files to their original location on the computer.
1. FILE BACKUPS • Hard drives fail.
• Critical files become corrupted.
• Data loss is not a matter of it, but when.
As a computer technician, one of the most valuable services you can perform is ensuring that your client's critical data is secure.
The best way to do that is by developing a good backup plan and making it as automatic as possible.
2. DEVELOPING A BACKUP PLAN
There are five different common types of backups based on frequency and which files are added to the archive. With some versions of software, you must select the files manually, whereas in others a wizard or a predefined file list determines what data is moved to the archive.
The backup types are:
learning redefined
2. Straight copy backup. Similar to normal backup, copies all selected files, whether they'vebeen backed up recently or not. The difference is that it does not mark the file as having been backed up. This is useful if you are making a separate backup copy of a set of files, because it will not exclude them from the next regular backup.
3. Daily backup. Copies all the preselected files modified on the date the backup was performed. The files are not marked as being copied to the archive.
4. Incremental backup. Copies just the files that have been created or modified since the last regular backup. This process changes the archives setting on the file when it is copied.
Incremental backup is used in combination with normal backup. If it is necessary to restore a drive, the last normal backup is placed back on the volume, followed by the contents of the most recent differential backup.
5. Differential backup. Archives only those files that do not show that they have been backed up since the last normal or incremental backup.
A backup plan incorporates these different backup methods into a series of regular copies of data that produces an archive refreshed frequently enough to meet the user's needs.
In some cases, backups must be very frequent and complete because core data is constantly changing. In other cases, most of the files hardly change at all, so infrequent differential copies may work.
1.3.7 BASIC HARDWARE MAINTENANCE
Most PC owners today think their computers are disposable. When it breaks down, most people end up replacing it for a newer (more expensive) model.
By understanding what makes computers break down, you can add years to the life of your system.
1. HOW TO MAINTAIN YOUR COMPUTER
Even with the most sophisticated hardware and software, you will need to do some type of maintenance to keep everything working properly. You can simplify and minimize the maintenance by following the steps listed below.
1. Start a notebook that includes information about your computer.
Keep a notebook that provides a single source of information about your entire computer, both hardware and software.
2. Before you work inside your computer, turn off the power and disconnect the equipment from the power source.
3. The greatest enemy of computer is heat. It causes the internal components and chips to wear out. Heat also lowers the performance of your system.
9 The first thing to check is the ventilation around your system.
9 Make sure the top and rear of your monitor are also kept clean and clear of debris.
4. Keep the areas surrounding your computer dirt and dust free. 5. Back up important files and data.
6. Protect your computer from viruses. 7. Keep your computer tuned.
8. Learn to use diagnostic tools.
learning redefined
2. VISUAL DISPLAY UNIT (VDU) MAINTENANCEThe visual display unit (VDU), or more popularly known as the monitor, is the primary output device of the computer system.
In order to keep the VDU operational for long periods of time and to extend its mean time between failures, it is necessary to maintain the VDU. Several guidelines can be taken in the case of VDU maintenance, such as:
1. Store the VDU in an appropriate place, eg.
•
Keep the VDU properly ventilated.•
Keep the VDU away from water and moisture.•
Keep the VDU in a cool environment – away from direct sunlight.•
Keep the VDU in a stable place. Ensure it doesn’t just fall off the table.•
Ventilation is important. Remove dust covers when the monitor is operational and ensure the ventilation holes are not blocked.•
Position the VDU away from high magnetic sources as it may affective the VDU’s performance.2. The VDU’s power source should be constant and stable. The power cord should also be plugged in properly onto the monitor.
3. Cover the monitor with a dust cover when not in use. It is always advisable to cover the monitor a few minutes after the monitor is turned off to allow the monitor to cool down.
4. Last, if you have a vent designed for a case fan, by all means get one!
5. Allow your computer room to breathe, and keep it clean inside, and it will be around for many years to come.
3. COMPUTER SHOULD BE SHUT OFF FOR PHYSICAL MAINTENANCE
• External
9 Monitor, CPU and keyboard.
Use either cleaning wipes or glass cleaner and a soft cloth. Do not spray glass cleaner directly on the exterior parts; instead dampen the cloth with glass cleaner first and gently rub to clean the components.
9 Mouse
If you begin to experience difficulty in controlling your screen cursor, your mouse probably needs cleaning.
To clean a mouse:
•
Turn mouse over.•
Twist bezel in direction of arrow.•
Remove bezel and mouse ball.•
Look for three wheels (in most cases) inside the mouse. Using a Q-tip or pencil eraser, carefully remove dirt on the wheels, examining each entire wheel.•
Clean mouse ball with Windex.•
Reassemble mouse.learning redefined
• Internal9 Every few weeks, make it a point to remove unnecessary files from your hard drive:
Go to:
Temp files [My Computer/C:/Windows/Temp]. Remove all files with .tmp extension. Internet temp files [My Computer/Windows/Temporary Internet Files]. Highlight the
file(s). Delete key. Recycle Bin [Desktop].
Right click, Empty Recycle Bin.
9 Once a month, make it a point to defragment your computer. Go to:
My Computer/C:/Windows/Defrag.
Select the drive that you want to defragment. Confirms drive and percentage of Drefragmenting.
4. PRINTER MAINTENANCE
In order to maintain a printer in proper working condition, there are several guidelines that need to be followed, such as:
1.
Use the right type of paper for the right type of printer.2.
Clean the printer regularly.3.
Lubricate the printer should any printing jam occur.4.
Store the printer in:• A cool place away from direct sunlight.
• Avoid water and moisture.
• On a sturdy table that will not topple over when exposed to the printing vibration.
• On high ground if continuous form is to be used.
• Properly ventilated.
• The printer cable should not be stretched too long.
5.
Avoid moving the paper feed knob when the printer is on or tugging the paper when printing. Never obstruct the print head’s path.1.3.8 BASIC HARDWARE TROUBLESHOOTING TOOLS
There are available several pieces of hardware that can be very helpful in troubleshooting some specific hardware problems.
1. DIAGNOSTIC HARDWARE
If you are a serious home builder or troubleshooter, you may want to consider one or more of the following:
• Loop-Back Plugs: These are small plugs that go onto the serial and parallel ports on your computer and connect the receive to transmit lines to simulate a connection (they connect the port to itself). Using these with a program like Norton Diagnostics allows for full testing of the operation of these ports, whereas without them only the internal portions of the port can be tested.