IJHIT
International Journal of Hybrid Information Technology
Vol. 7, No. 6, November 2014
S
CIENCE &
E
NGINEERING
R
ESEARCH
International Journal of Hybrid Information Technology
November 2014 Printed
November 2014 Published
Publisher:
SERSC
Publishing office: Science and Engineering Research Support soCiety
20 Virginia Court, Sandy Bay, Tasmania, Australia
E-mail : sersc@sersc.org; ijhit@sersc.org
Tel: +61-3-9016-9027
Printing office:
Hanall Co. Ltd.
i
Editor-in-Chief of the IJHIT Journal
Ha Jin Hwang,
Kazakhstan Institute of Management, Economics and Strategic Research (KIMEP), Kazakhstan
Byeong-ho Kang,
University of Tasmania, Australia
General Information of IJHIT Bibliographic Information
ISSN: 1738-9968
Publisher: SERSC
Science & Engineering Research Support soCiety
Contact Information
Science & Engineering Research Support soCiety
Head Office: 20 Virginia Court, Sandy Bay, Tasmania, Australia
Phone no.: +61-3-9016-9027
Email: ijhit@sersc.org
Journal Topics
The goal of IJHIT is to bring together the researchers from academia and industry as well as practitioners to share ideas, problems and solutions relating to the multifaceted aspects of Information Technology.
The topics covered by IJHIT include the following:
Basic Topics:
Bioinformatics and Computational Biology
Communications and Networking
ii
E-Science and Web Intelligence
Grid and Distributed Computing
Hardware and Software Co-Design
Health and Medical Informatics
Hierarchical and Adaptive Learning Systems
Human-Computer Interaction and Multimedia
Image and Signal Processing
Industrial and Environmental Engineering
Intelligent Robotics and Autonomous Agents
KDD and Data Warehousing
Multi-Scale Modeling and Simulation
Security and Safety Systems
Smart Card and Chip Technologies
Soft Computing and Rough Sets
Ubiquitous Computing and Embedded Systems
Advisory/Editorial Board
Andrew Kusiak, The University of Iowa, USA
Bogdan Gabrys, University of Bournemouth, UK
C.H. Lee, University of Maryland, USA
Chung-huang Yang, National Kaohsiung Normal University, Taiwan
D. Jude Hemanth, Karunya University, India
Debnath Bhattacharyya, Heritage Inst. of Technology, India
Dongyu Liu, Cavium Networks, USA
iii Frank Klawonn, Fachhochschule Braunschweig, Germany
Gustavo Olague, CICESE Research Center, USA
Hassan Diab, American University of Beirut, Lebanon
Heping Wang, Lemko Inc, USA
Hideyuki Sawada, Kagawa University, Japan
Jianbing Li, University of Northern British Columbia, Canada
Kamaljit I. Lakhtaria, Atmiya Institute of Technology & Science, India
Kousalya G, Lealta Media, India
Lech Polkowski, PJIIT, Poland
Maricel Balitanas, University of San Agustin, Philippines
Qiang Zhang, Dalian University, China
Pawan Jindal, Jaypee University of Engineering and Technology, India
R.Amutha, SSN College of Engineering, India
Rainer Unland, University of Duisburg-Essen, German
Randy S. Tolentino, Hannam University, Korea
Rosslin John Robles, University of San Agustin, Philippines
S. A. Channiwala, V. Regional College of Engg. and Tech., India
T.Venkat Narayana Rao, Hyderabad Institute of Technology and Management, India
Umberto Straccia, ISTI-CNR, Italy
Witold Pedrycz, University of Alberta, Canada
Wojciech Ziarko, University of Regina, Canada
Xue-wen Chen, The University of Kansas, USA
Ying Xie, kennesaw State University, USA
iv
IJHIT is indexed by:
EBSCO
ProQuest
ULRICH
DOAJ
OpenJ-Gate
Cabell
EI Compendex
Editorial Secretary
v
Foreword and Editorial
International Journal of Hybrid Information Technology
We are very happy to publish this issue of an International Journal of Hybrid Information Technology by Science and Engineering Research Support soCiety.
This issue contains 39 articles. Achieving such a high quality of papers would have been impossible without the huge work that was undertaken by the Editorial Board members and External Reviewers. We take this opportunity to thank them for their great support and cooperation.
The paper “Classified Comparison of Operational Efficiency to Internet Company in China Based on DEA Model” concentrates on the study of efficiency in internet enterprise in China. In order to evaluate the operational efficiency of the Internet Company in China, this paper constructed the index system of the efficiency evaluation at first. Then it appraises the overall efficiency and variation tendency about Internet Company of China Based on DEA method from cross section data and temporal patterns. At the same time this paper classifies the Internet Company into three types: E-commerce, Information supplier, and Communication- Equipment supplier and make a comparative analysis to the performance and changing trend of different types.
The paper author of paper “The Study of GPS Vision Navigation System of Multi-stage Real-time Matching Algorithm” introduces a matching constraint and layer-by-layer search structure which is suitable for GPS vision navigation system, and puts forward a feature aided multi-stage matching algorithm. The algorithm firstly makes the match of the more obvious characteristics points, then the matched points information are used to determine the subsequent points general disparity range through the geometric constraints, thus improving the matching speed and accuracy. Using different types of outdoor natural topographic map matching experiments were conducted.
Paper “A Low Power Low Noise Chopper-Stabilized Tow-stage Operational Amplifier for Portable Bio-potential Acquisition Systems Using 90 nm Technology” presents a high performance chopper-Stabilized Two-stage operational amplifier for biomedical applications. This Two-stage is designed for low noise, low power, high PSRR and high CMRR. The Miller compensation technique (Cc) is used with a nulling active resistance (Rz) implemented using Transmission gate (TG) transistors for stable operation in feedback mode. Chopper stabilization technique has been widely used in amplifiers for flicker (1/f) noise and offsets reduction purposes using the principles of modulation and demodulation. Thus, the functionality and performance of modulation and demodulation circuits determines the realization and attainment of chopper stabilization. The operational amplifier was manufactured in a SPECTRE using GPDK 90nm CMOS technology with threshold voltages of a 0.17 V and - 0.14 V achieve a low power 2.6uW, at 10Hz high CMRR up to 130dB and PSRR up to 70dB at 1V power supply.
vi
session based methods and click-through based methods. Adjacency based query suggestion, co-occurrence based query suggestion, query-flow graph based query suggestion, clustering based query suggestion, and bipartite graph based query suggestion are presented respectively in detail.
In the Paper “Various Roadside Populations Effects on Data Throughput over Cooperative Vehicular Ad hoc Networks” the author considers the roadside populations as to supply
vehicles’ requirements based on both a proposed algorithm and simulation results. Moreover, it studies the roadside self-participation to enhance the transfer rates and achieve fair resource distribution among the requested vehicles based on coalition formation.
Paper “LogCEP - Complex Event Processing based on Pushdown Automaton” proposed a new CEP system LogCEP using pushdown automaton to support efficient processing of conjunction and negation. First, the semantic and query language specification of LogCEP system are presented. Then, an automaton named LogPDA is proposed for query processing in LogCEP system. LogPDA construction method describes how to convert a query to LogPDA automation. The LogPDA execution approach describes how to detect the specified pattern using LogPDA. Meanwhile, most of previous NFA-based optimizations can be employed to improve the evaluation efficiency.
In the paper “A New Efficient Meta-Heuristic Optimization Algorithm Inspired by Wild Dog Packs”, a new, efficient meta-heuristic optimization algorithm inspired by wild dog packs is proposed. The main idea involves using three self-competitive parameters that are similar to the smell strength. The parameters are used to control the movement of the alpha dogs and, consequently, the movement of the whole pack. The rest of the pack is used to explore the neighboring area of the alpha dog, while the hoo procedure is used to escape from the local optima. The suggested method is applied to several unimodal and multimodal benchmark problems and is compared to five modern meta-heuristic algorithms.
In the paper “Design and Implementation of Self-validating Pneumatic Actuator Hardware System Based on DSP and MCU” A dual processor system is implemented using C8051F060 and TMS320F28335 to acquire the signals and complete fault detection, diagnosis and self-validating parameters calculating. C8051F060 is used to data acquisition and preprocessing of the actuator inner signals, and communicate with Host PC.TMS320F28335 is used to run the self-validation algorithm and fault diagnosis algorithm and transfer the self-validation outputs to C8051F060.
The authors of paper “Influencing Factors of Information Channels Adoption of Forest Farmers on Grain for Green Program in Western China”, aims to find out the main factors that influencing the adoption of these information channels of forest farmers in Western China. Rough set theory is used to solve the problem of main factors reduction.
vii power of one day is 3 ampere hours in the front station and 30 ampere hours in the middle station if the 12 voltage battery is used.
The paper “The Study of China Vehicle Internet-Consumer Satisfaction Based on Bayesian Network” analyzes the theories about customer satisfaction model both in China and abroad. All of them are expected difference theory as the core, evaluating the benefit of consumer satisfaction by perception the difference of perceived benefits and loss. On this basis, by the internet-questionnaire survey, the China internet-automobile customer satisfaction evaluation system of the bayesian model is established. From this, it can be obtained the main factors of the customer satisfaction and their influence degree.
In the paper “Research on Technological Innovation Talents of the Six Provinces of Mid-China based on BP Artificial Neural Networks of the Golden Section Theory”, BP neural network is used to evaluate based on the construction of evaluation index system of the
technological innovation talents’ competitiveness. It determine the actual situation of the
evaluation system according to the input layer, hidden layer and output layer of the model as well as the number of neurons in each layer. The number of neurons in the input layer is the number of indices of technological innovation talents evaluation. The output layer represents the comprehensive ability level and has only one neuron. However, it is difficult to figure out the number of hidden layers of BP neural networks. It uses the golden section method to accurately select their layers. This can effectively avoid the problem of excessive training error due to the random selection of hidden layer. Then it illustrates the accuracy and usefulness of this algorithm with the case of the technological innovation talents of the six central provinces. Tests show that the comprehensive ability of technological innovation talents of Hubei is the most powerful in the six central provinces and is followed by Anhui. The remaining four provinces have similar levels. The actual development of technological innovation talents agree well with the experimental results.
Paper “Information System of Yadnya Ceremony on Android-Based” design and make a model of the system that presented the Yadnya ceremony through Android-based information systems. The system will provide information related to activities such as execution time of
Yadnya ceremony, implementation procedures, pemuput, place of ceremony, video, and
images of the ceremony. Users will obtain data or information by accessing the application from the server system.
viii
Paper “Tuning New Fuzzy Control for Nonlinear Second Order System” used Cognitive method to create portfilo of movement robot manipulator. Gradient descent (GD) fuzzy
controller was used and robot’s postures and trajectory were expected in
MATLAB/SIMULINK environment. Fuzzy logic controller (FLC) is an influential nonlinear controller to certain and uncertain systems which it is based on artificial intelligent and computes the required torques using the nonlinear feedback control law. Practically a large amount of systems have uncertainties accordingly this method has a challenge. Linear proportional-integral-derivative (PID) controller is a significant combination nonlinear stable-robust controller under condition of partly uncertain dynamic parameters of system. This technique is used to control of highly nonlinear systems especially in nonlinear time varient nonlinear dynamic system. To compensate for the dependence on model-free parameters, PID methodology is used. The nonlinear model dynamic formulation problem in uncertain system can be solved by using PID theorem. Proportional-Derivative-Integral (PID) theory is used to estimate the system dynamic.
Paper “Research on Group Emotional Intelligence Effects on Group Decision-making under Emergency” proposes the concept model of group emotional intelligence, adopts 2x2 factorial design, carries on survival experiment including 52 groups, and analyzes the influence of the group emotional intelligence on intra-group conflict, conflict management, performance, satisfaction and cohesion. Utilizes the statistical software SPSS19.0 for data analysis, and draws reliable conclusions. The conclusions offer references for enhancing emotional management capacity and problem-solving abilities of decision-making groups in emergencies environment. After various types of emergencies, victims and rescuers will have negative psychological and mental reactions, such as stress response, psychological disorder. In this case, making the right group decision is the most important issue.
In the paper “A New Symbolic Method for Discernibility Matrix in Rough Set”, a novel method for discernibility matrix using Zero-Suppressed BDDs (ZBDD) and Ordered binary decision diagrams (OBDD) is proposed, experiment is carried to compare the storage space of discernibility matrix with that of ZBDD and OBDD, results show that the new method has better storage performance and improve the attribute reduction for those information systems with more objects and features.
In the paper “Novel Adaptive Fuzzy Inference Controller for Highly Nonlinear System” intelligent control of robot arm using Proportional-Integral-Derivative (PID) Adaptive Fuzzy Gain scheduling (PID-AFGS) is design for two degrees of robot arm. Robot manipulators are multi inputs-multi outputs, nonlinear and time variant system, therefore control of this system is the main challenge in robotic science. Control robot arm according to linear methodology are often having lots of problems because robotic systems are always highly nonlinear. Design accurate controller for robot manipulator is difficult because some dynamic parameters such as compliance and friction are not well understood and some robot parameters such as inertia are difficult to measure accurately and caused to variation in dynamic response. Fuzzy logic controllers have been applied in many applications. One of the important methods to solve above challenge is design adaptive controller based on fuzzy logic.
ix 0.5 nm, 0.6 nm, 0.8 nm, 1.2 nm, and 1.4 nm) have been established and simulated using the Forcite program package of Materials Studio software. The calculated results show that the interface bond energy is 38~150 Kcal/mol, which indicate the Van der Waals force exist between the nanoparticle and polyimide matrix. The interface bond energy of the smaller nanoparticle is greater than the lager nanaparticle due to the size effect. The introduction of the smaller nanoparticle could generate the stronger intermolecular bonding interaction between the nanoparticle and polyimide matrix.
The paper “Bayesian Analysis of Power Function Distribution Using Different Loss Functions” obtains Bayesian estimators of the shape parameter of Power function distribution. For the Posterior distribution of this parameter, it consider Exponential Prior, Pareto Prior, Chi-Square Prior, Quasi Prior and Extension of Jeffrey`s Prior. The three loss functions taken up are Squared Error Loss Function (SELF), Quadratic Loss Function (QLF) and Precautionary Loss Function (PLF). The performance of an estimator is assessed on the basis of its relative Posterior risk. Monte Carlo Simulations are used to compare the performance of the estimators. It is discovered that the PLF produces the least Posterior risk when Exponential and Pareto Priors are used. SELF is the best when Chi-Square, Quasi and Extension of Jeffrey`s Priors are used.
In the paper “Robust Stabilization of a Class of Uncertain Fractional-order Chaotic Systems via a Novel Sliding Mode Control Scheme”, proposes a novel sliding mode control (SMC) scheme to stabilize a class of fractional-order chaotic systems. Through constructing two sliding mode variables, the control problem of n-dimensional system can be transformed to the equivalent stabilizing problem of a reduced-order system. Subsequently, on the basis of second-order sliding mode (SOSM) technique, a robust control law is designed, which strongly attenuates the chattering phenomenon inherent in traditional sliding mode controller, and guarantees the existence of sliding motion in a finite time. The stability of two sliding mode variables to the origin is proved by conventional and fractional Lyapunov theories, respectively. Finally, two numerical examples are provided to illustrate the effectiveness of the proposed approach.
In the paper “The Study of Product Availability in a Dual-channel Distribution Supply Chain with (Q, R) Policy of Retailer”, authors focus on the supply chain model with a single product in electronic and retail channel, only a supplier and a retailer in system, customers have alternatives to choose the channel that is better suited to their needs, some of them may alternatively switch to the other channel when a stock-out occurs in their preferred channel. Supplier and retailer implement one-for-one and (Q, R) ordering policies respectively to replenish their inventories. They set up the profit model of supply chain by Markov process, and study the product availability of supply chain. The result shows that the stock-out based substitution rate may increase or decrease the efficiency of decentralized supply chain; the centralized supply chain can adjust the based-stock levels timely to different stock-out based substitution rate and benefit from it, the supplier and retailer in a decentralized supply chain
are more inattentive to customers’ stock-out based substitution rate, and prone to lose their benefits.
x
The paper “Design and Implementation of a Time-frequency Analysis System for Non-stationary Vibration Signals Using Mixed Programming” uses the EMD-WVD combined method as an example to present the programming thoughts and processes. The effectiveness of the system is validated using a simulation signal and an experimental signal. The system can be executed separated from MATLAB environment. At present, in the feature extraction of non-stationary vibration signals, many time-frequency analytic methods have emerged to meet the further need of non-stationary signal analysis such as Wavelet Transform (WT), Short Time Fourier Transform (STFT), Wigner-Ville Distribution (WVD), Empirical Mode Decomposition(EMD), Ensemble Empirical Mode Decomposition(EEMD) and so on. However, these time-frequency analysis methods can only be carried out on Matlab platform and the processes are of low efficiency, bringing a lot of inconvenience in signal analysis because they can not run on Windows system independently.
The paper about “Some Comparative Studies for Cursive Handwritten Tifinagh Characters Recognition Systems”, present two comparative studies; the first one is between two methods of features extraction which are the mathematical morphology, the zoning and the hybridization of these two methods. The second comparative study is between both supervised methods used in learning-classification which are the Multi-Layer Perceptron (MLP) and the Support Vector Machines (SVM) applied to cursive handwritten Tifinagh characters recognition.
In the paper “Study on Loading Capacity of Miniature Boats Fabricated from Hydrophobic Plant Leaves”, authors established mathematical model of loading capacity, comparing the measured values and measured values of loading capacity, the error ratio of loading capacity is about 4.0-6.1%. The loading capacity is made up of buoyancy and surface tension, percentage of buoyancy and surface tension in the loading capacity is affected by the contact angle and geometry size of miniature boats.
Paper about “Estimation of Backward Perturbation Bounds for Linear Least Squares Problem”, present a simple estimation to this bound which can be easily computed especially for large problems. Numerical results demonstrate the validity of the estimation. Waldén, Karlson, and Sun found an elegant explicit expression of backward error for the linear least squares problem. However, it is difficult to compute this quantity as it involves the minimal singular value of certain matrix.
Authors of paper “Design of Digital FIR Filter Based on MCMAT for 12 bit ALU using DADDA & WALLACE Tree Multiplier”, presents in the proposed method the effectiveness in different parameters are achieved with low cost, high speed and effective results are done by faithfully rounded truncated multipliers with operations of carry save adder. Direct form of FIR filter utilizes based on MCMAT for multiplication and accumulation operations; it will reduce the area by decreasing the number of different components like structural adders and registers. By using MCMAT operation in the digital FIR filters, optimal results can be obtained in terms of power and area specifications. The proposed 12 bit Arithmetic and Logic Unit is designed along with MCMAT based digital FIR filter for reducing area and increasing speed in real time applications.
xi and curve fitting technologies were applied in the FBG wavelength demodulation system based on tunable F-P filter. These methods could realize the accurate peak-location of output signals of the photo detector. According to the characteristics of noise, the FIR low-pass filter was designed to filter the obtained light power signals so as to provide the input signals with high SNR for the peak-detection algorithms. By analyzing and comparing several typical peak-searching algorithms, the algorithm of Gauss formula nonlinear curve fitting (L-M) was chosen to fit the digitized light power signals. The experimental results show that L-M fitting algorithm reduces the mean square error by 7.5% compared with the Gauss fitting algorithm. For the Gauss signal in the wavelength demodulation system designed in the paper, the L-M algorithm has lower mean square error than other peak-searching algorithms. This algorithm is suitable for FBG wavelength demodulation system based on tunable F-P filter. It can efficiently raise the accuracy of wavelength demodulation system.
In the paper “Enhanced Hybrid Cat Swarm Optimization Based on Fitness Approximation Method for Efficient Motion Estimation”, a new algorithm based on Hybrid Cat Swarm Optimization (HCSO) is proposed to reduce the number of search locations in the BM process. In proposed algorithm, the computation of search locations is drastically reduced by adopting a fitness calculation strategy which indicates when it is feasible to calculate or only estimate new search locations.
Paper “Research on Inventory Sharing and Pricing Strategy of Multi-channel Retailer with Channel Preference in Internet Environment” study the inventory strategy and the pricing strategy of the products in the dual channel considering the online channel preference. And then it proposes a shared inventory and a dynamical pricing strategy. In addition, it study the influence of the related parameters on the profit of the retailers. At last, the numerical analysis shows that the shared inventory and the dynamical pricing strategy can bring more profits for the retailers.
The paper about “Investigations on Modeling and Simulation of Printed Folded Dipole Antenna” modeled and simulate asymmetric microstrip folded dipole antenna on substrate materials and study the antenna performances. The conventional wire dipole antenna configurations are converted into corresponding microstrip version. The complementary nature of parallel coplanar strip line and waveguide models have been used to model the dipole antenna. The transmission line parameters namely, even-odd mode effective dielectric constant and characteristic impedance have been analyzed. It study the effect of dielectric material on radiation characteristics of the printed folded dipole antenna, such as effective dielectric constant, characteristics impedance, input impedance and bandwidth. The antenna shows bandwidth improvement below 3 GHz frequency with asymmetric form of strip folded dipole.
xii
The paper “An Approach to Verify, Identify and Prioritize IDS Alerts” present the approach to verify, identify and prioritize alerts based on post processing of alerts. Central to the approach is the computation of new alert metrics in order to further describe and understand interestingness of alerts. It synergized Alert Verification and Alert Prioritization techniques to build an effective alert management technique. The approach gives superior results when compared to other alert management techniques.
In the paper “A Event Weight Based Trust Search Algorithm with Subjective Logic”, , a new trust search algorithm was proposed. The influence of event weight to node’s recommended qualifications was fully considered in the new algorithm by the improvement of subjective logic theory, the path dependence and trust-circle caused by the overlapping of friends-circle were solved effectively by the strategies of dual-threshold screening and set added.
Paper “Fatigue Life Validation and Analysis of Connecting Rod”, deals with multi cylinder diesel engine connecting rod for experimental fatigue testing and soft validation of its design. The connecting rod in four stroke reciprocating diesel engine is subjected to variable loading when Engine is in operating condition. The design of connecting rod is critical for the engine Performance, fatigue life, linear vibration & durability of engine. The fatigue failure is occurred due to alternating compressive & tensile stresses during its two revolutions. The fuel combustion inside cylinder generates a huge compressive force at power stroke. The 3D model is prepared and CAE analysis is done to predict the maximum Stresses and check whether it is safe for fatigue failure. The modification in design is done to make it safe for fatigue life.
Paper “The Research of Software Reuse Technology Based on Component” proposes a model of library management information system. Firstly this paper introduces the research background and research status. The second part is the design of reuse system based on the component. The third part is the component-based information management system used for the library management system. The last part is the conclusion. With the expansion of the computer application, the complexity of software and the program code increase rapidly. The increasing requirement of software brings the grown of the size about software. In order to solve these problems, the idea of software reuse emerges. In these years, the software reuse technology develops rapidly. Nowadays, software reuse technology which is based on component is regarded as the most successful implement technology in the software reuse field and the available solution to solve the Software Crisis. In this paper, it researches the software architecture based on component.
In the paper “Exact Solution of Klein Gordon Equation via Homotopy Perturbation Sumudu Transform Method” applies the proposed method (NHPSTM) which is the combination of new homotopy perturbation methodand Sumudu transform to solve analytical linear and nonlinear Klein-Gordon equations. The proposed method finds the solution without any discretization or restrictive assumptions and avoids the round-off errors. The fact that the
proposed technique solves nonlinear problems without using Adomian’s polynomials can be
considered as a clear advantage of this new method over the decomposition method. Obtained results reveal that the proposed method is very efficient, simple and can be applied to other nonlinear problems arising in mathematical physics and engineering.
xiii order to balance filtering accuracy and time cost. For the lack of measurement information of the PF, it combines square root cubature Kalman filter (SRCKF) with strong tracking filter (STF), and proposes an improved square root cubature Kalman filter (ISRCKF). The ISRCPF adopting the ISRCKF to develop the proposal distribution and incorporates the latest measurement into updating phase is proposed by introducing the ISRCKF into the particle filter framework.
November 2014
Ha Jin Hwang, Kazakhstan Institute of Management, Economics and Strategic Research (KIMEP), Kazakhstan
Byeong-ho Kang, University of Tasmania, Australia
Editors of the November Issue on
xiii
Table of Contents
Classified Comparison of Operational Efficiency to Internet Company in
China Based on DEA Model 1
Liu Jiana and Li Wei
The Study of GPS Vision Navigation System of Multi-stage Real-time
Matching Algorithm 15
Bo-ping Zhang
A Low Power Low Noise Chopper-Stabilized Tow-stage Operational Amplifier for Portable Bio-potential Acquisition Systems Using 90 nm
Technology 25
Fateh Moulahcene, Nour-Eddine Bouguechal and Youcef Belhadji
A Survey on Query Suggestion 43
Lingling Meng
Various Roadside Populations Effects on Data Throughput over
Cooperative Vehicular Ad hoc Networks 57
Esraa Eldesouky, Ahmed Ali, Li Renfa and Wang Dong
LogCEP - Complex Event Processing based on Pushdown Automaton 71
Jian Cao, Xing Wei, Yaqi Liu, Dianhui Mao and Qiang Cai
A New Efficient Meta-Heuristic Optimization Algorithm Inspired by Wild
Dog Packs 83
xiv
Design and Implementation of Self-validating Pneumatic Actuator Hardware System Based on DSP and MCU 101
Zhigang Feng and Meng Qiu
Influencing Factors of Information Channels Adoption of Forest Farmers on Grain for Green Program in Western China 115
Ma Ning and Yu Jinyu
A Real-Time Vibration Frequency Measurement System of Bridge Pier 123
Yao-Ming Hong, Jian-Rong Zeng, Yao-Chiang Kan, and Hsueh-Chun Lin
The Study of China Vehicle Internet-Consumer Satisfaction Based on
Bayesian Network 133
Ma QiHua, Zhang ChunYan and Zhang RuoPing
Research on Technological Innovation Talents of the Six Provinces of Mid-China based on BP Artificial Neural Networks of the Golden Section Theory 143
Huaping Zhang
Information System of Yadnya Ceremony on Android-Based 155
Oka Sudana, A.A.K a. Sukarsa, I Made b and Wahyu Saputra, I Made
Discriminant Locality Preserving Projections Based on Neighborhood
Maximum Margin 165
Kezheng Lin, Youhu Rong, Di Wu, Liangwei Zhuang and Peng Li
Tuning New Fuzzy Control for Nonlinear Second Order System 175
xv
Research on Group Emotional Intelligence Effects on Group
Decision-making under Emergency 189
Yingxin Chen
A New Symbolic Method for Discernibility Matrix in Rough Set 199
Qianjin Wei and Tianlong Gu
Novel Adaptive Fuzzy Inference Controller for Highly Nonlinear System
211
Atefeh Chahkoutahi, Mohammad Hossein Rahimi, Sirous Ashja, Mohammad Gholami and Mohammad Reza Moradipour
Effect of Nanoparticle Size on the Interface Bond Energy in
KTa0.5Nb0.5O3 / Polyimide Composites 223
Chuntian Chen, Juan Wang, Wenlong Yang, Xiaokang Li and Jingyun Zhang
Bayesian Analysis of Power Function Distribution Using Different Loss
Functions 229
Azam Zaka and Ahmad Saeed Akhter
Robust Stabilization of a Class of Uncertain Fractional-order Chaotic Systems via a Novel Sliding Mode Control Scheme 245
Xiaomin Tian, Shumin Fei and Lin Chai
The Study of Product Availability in a Dual-channel Distribution Supply Chain with (Q, R) Policy of Retailer 259
Fan He-hua and Zhou Yong-wei
Study of One Kind of Extended Proportional Guidance Law 271
xvi
Design and Implementation of a Time-frequency Analysis System for Non-stationary Vibration Signals Using Mixed Programming 283
Miaozhong Sun, Shihai Cui and Yuanli Xu
Some Comparative Studies for Cursive Handwritten Tifinagh Characters
Recognition Systems 295
B. El Kesab, C. Daoui, B. Bouikhalene and R. Salouan
Study on Loading Capacity of Miniature Boats Fabricated from Hydrophobic
Plant Leaves 307
Wang Qingcheng Yang Xiaodong and Yang Zhuojuan
Estimation of Backward Perturbation Bounds for Linear Least Squares
Problem 315
Xinxiu Li
Design of Digital FIR Filter Based on MCMAT for 12 bit ALU using DADDA &
WALLACE Tree Multiplier 325
Jami Venkata Suman, D. G. Jignash and B. I. Neelgar
Research on Peak-detection Algorithm for High-precision Demodulation
System of Fiber Bragg Grating 337
Peng Wang, Xu Han, Simin Guan1, Hong Zhao and Minglei Shao
Enhanced Hybrid Cat Swarm Optimization Based on Fitness Approximation
Method for Efficient Motion Estimation 345
xvii
Research on Inventory Sharing and Pricing Strategy of Multi-channel Retailer with Channel Preference in Internet Environment 365
Hanzong Li
Investigations on Modeling and Simulation of Printed Folded Dipole
Antenna 375
Prabir Banerjee and Tulshi Bezboruah
Research of Evaluation Mechanism of Petrochemical Informatization
Projects Based on AHPP 389
Feng’an Wen
An Approach to Verify, Identify and Prioritize IDS Alerts 395
Tu Hoang Nguyen, JiaWei Luo and Humphrey Waita Njogu
A Event Weight Based Trust Search Algorithm with Subjective Logic 411
Junfeng tian and Peipei Zhang
Fatigue Life Validation and Analysis of Connecting Rod 423
Anand. D. Dantale and Ashok. J. Keche
The Research of Software Reuse Technology Based on Component 433
Zhai Jinbiao
Exact Solution of Klein Gordon Equation via Homotopy Perturbation
Sumudu Transform Method 445
xviii
An Improved Square Root Cubature Particle Filter for Navigation 453
ISSN: 1738-9968 IJHIT Copyright ⓒ 2014 SERSC
Information System of Yadnya Ceremony on Android-Based
Oka Sudana, A.A.K
1, Sukarsa, I Made
2and Wahyu Saputra, I Made
31,2,3
Department of Information Technology, Udayana University, Bali, 80119
agungokas@hotmail.com, e_arsa@yahoo.com,
madewahyusaputra@yahoo.com
Abstract
Implementation of very large religious ceremonies in Bali demanded Hindus to be able to understand things related to Yadnya ceremony. One of the reasons why people are reluctant to participate in the Yadnya ceremony is because they does not know how to execute the ceremony. A way that can be taken is to design and make a model of the system that presented the Yadnya ceremony through Android-based information systems. The system will provide information related to activities such as execution time of Yadnya ceremony, implementation procedures, pemuput, place of ceremony, video, and images of the ceremony. Users will obtain data or information by accessing the application from the server system.
Keywords: Android, Information System, Tree Diagram, Yadnya Ceremony
1. Introduction
Bali Cultural Tourism is one of Bali's most interesting for tourists. Yadnya ceremony in Bali is one part of the Balinese culture that must be preserved. Yadnya ceremony in Bali covering various aspects that support the implementation of the rituals for the Hindu community in Bali. Yadnya ceremony and ulam Bebantenan is one of the medium to implement a core part of Hindu ritual [1].
Implementation of Yadnya ceremony is a spiritual guidance to appreciate the source of happiness of life from God, man and nature and its contents [2]. The existence of Yadnya
ceremony is important to be maintained, one way to maintain Yadnya ceremony is by introducing it to the younger generation. The introduction can be done with a practical and efficient manner utilizing the technological advances which is developed at this time.
The most popular and growing technology recently is mobile device, or better known as smartphones. This technology is very popular because of its presence which has a variety of interesting features in it. These features include multimedia, games, until the Internet network. The Internet network feature is the most popular one in community because of the ability that Internet can provide and the ease to obtain information.
The existence of technology then will be combined with Balinese culture which is associated with the Yadnya ceremony, will give a good lesson for the Hindus in Bali. Efforts to do here is to design an application that can provide relevant information about
Yadnya ceremony activities. The basic concept of the application is an information system
of Yadnya ceremony based on Android in order to make interested to public to use it,
other than that the Android-based applications are very well known by the public at large.
Yadnya ceremony application is an information system that provides information about
the Yadnya ceremony. The purpose of the system designed is to make people easily obtain
information about the Yadnya ceremony.
2. Research Methods
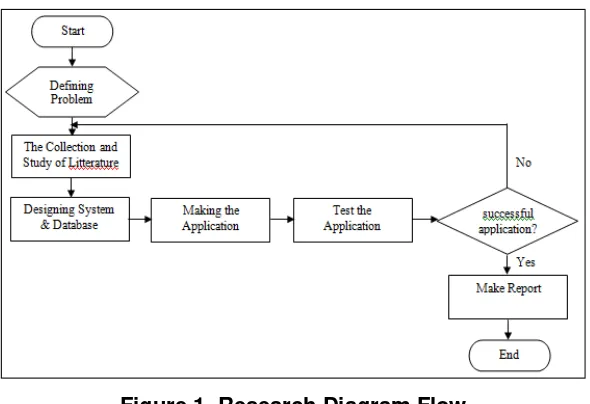
156 Copyright ⓒ 2014 SERSC application in order to make sure the application will be done according to schedule. Some of the grooves are made to work on the application of information system is illustrated in Figure 1 in the following flow chart.
Figure 1. Research Diagram Flow
Figure 1 illustrates the flow of research that consists of several stages, include:
a. Defining the problem, is the initial step before the study were defining the issues raised in the study.
b. The collection and study of literature, collection of data and literature related to the manufacture of Application Systems.
c. Designing systems and databases, applications include systems design phase, a database, as well as interface design. The design of the application must have a mature concept that will facilitate the making of the application stage.
d. Making the application, where the application developed for mobile which is based with Java as a programming language and MySQL as the database.
e. Test the application, application testing and analysis as well as documentation of the results of such testing. Errors contained in the system will then be repaired until no more errors are found.
f. Make reports, preparation of reports which includes the overall research that has been done. Reports are made to explain the process of making the application that starts from background processing application, workflow processing application, a general description of the application until the final stage of completion of the application. This report is used as written evidence of the process of the application that will be used as a literature review for the next research work.
3. Modeling System
Modeling the system was conducted to determine the relationship between ritual ceremony with the other one by using the Tree diagrams. Tree diagram is a method for modeling the system. This structure has specific characteristics and typically used to describe the hierarchy of elements relationship. [3]
Tree modeling can also provide the understanding about the system that are made so it will helps in the process of database design and application program. In general, a Yadnya
ceremony will have the following properties:
a. Yadnya group, is to determine the group of the ceremony.
b. Description, is to explanation the Yadnya ceremony.
Copyright ⓒ 2014 SERSC 157
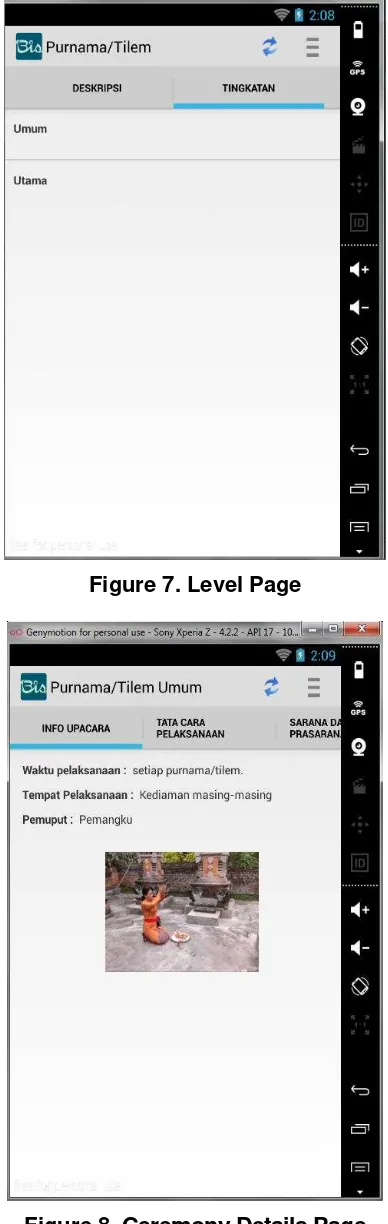
d. Levels of ceremony, which is a level of ceremony Uttama, Madya, Kanista or common level.
Tree were rooted at the level of the ceremony, which contains about Pemuput, place of
the ceremony, the implementation procedures, means of ceremony, video, and pictures of the ceremony. Pemuput, place of ceremony, the implementation procedures, means of ceremony, video and pictures are placed after the degree of the ceremony because the same ceremony might have different levels of pemuput, place of ceremony, implementation procedures, means of ceremony, video and pictures of different ceremonies, as in Figure 2.
Figure 2. General Modeling of Yadnya Ceremony
The circled property names in Figure 2 shows that the property can have more than one value. An example is the degree ceremony for the property name that can have a value of
Uttama, Madya, Kanista or Common. Examples of the application of this model can be
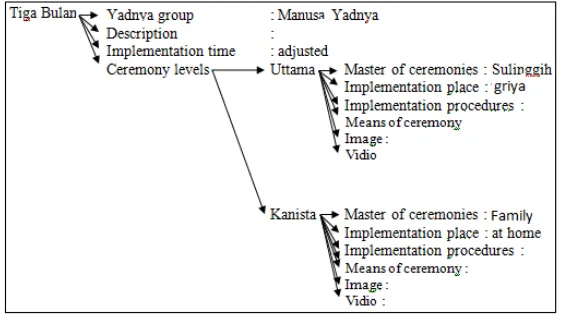
seen in Figure 3, namely modeling for TigaBulan ceremony.
Figure 3. General Modeling Tiga Bulan Ceremony
Figure 3 shows an example of modeling that name is Tiga Bulan ceremony. This ceremony has properties such as:
a. Yadnya group, which includes ManusaYadnya;
b. Description, which describes the ceremony in general; c. Execution time, which is when the baby is 105 days old; d. Levels of ceremony.
Tiga Bulan ceremony has two tiers ceremony so the tree will have two branches,
namely that leads to a level that Uttama and Kanista. Next on the level name followed by a subtree named place, pemuput, procedures, tools, videos and pictures of the ceremony.
4. Results and Discussion
158 Copyright ⓒ 2014 SERSC 4.1. General Description of the System
The system consists of two sides that can be interconnected, with the help of the web and Internet network services to manage the database on the client application. Web service is defined as an interface that describes a set of operations that can be accessed through the Internet in the form of XML messages (eXtensible Markup Language). Web services provide a standard communication between different software applications and can run as a platform and framework [4].
Application of Yadnya ceremony used as a media introduction of the types of ceremonies in Bali to the general public, especially the younger generation. In addition, this application also aims to participate in the effort to preserve the arts of Bali. This application is expected to provide information about Yadnya ceremony in Bali.
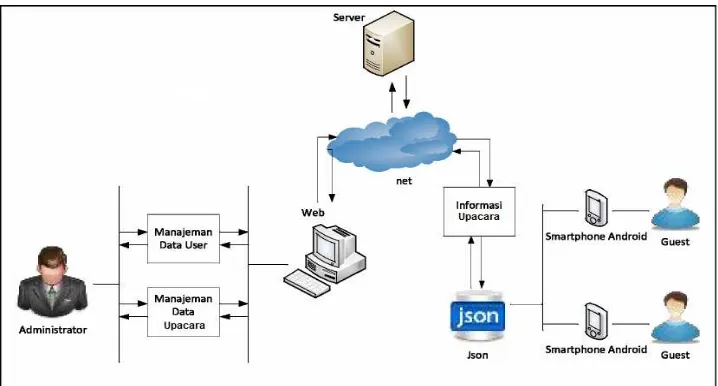
Information system of Yadnya ceremony consists of administrator and guest. Information systems administrator accessed via a web browser, while guest is accessible via Android Smartphone devices. General overview of the application of Yadnya
ceremony information system can be seen in Figure 4.
Figure 4. Overview of Yadnya Ceremony Application
Figure 3.2 above shows how the user or guest in obtaining the information. First of all, a user will make a request (request for information) via the Android Smartphone and Android Smartphone devices will then send the request to the Internet to get data from the database server. Between the application and the database server takes a PHP file with the JSON data format to accommodate the results of a database query which will then be parsed and displayed in the Android Smartphone devices.
The information displayed to user or guest is entered to the server by administrator. PHP file with the JSON format taking query results from the database server and displayed in the Android smartphone devices [5]. Administrator will input data about Yadnya ceremony through the administrator page and then the data will be uploaded to the server through the Internet.
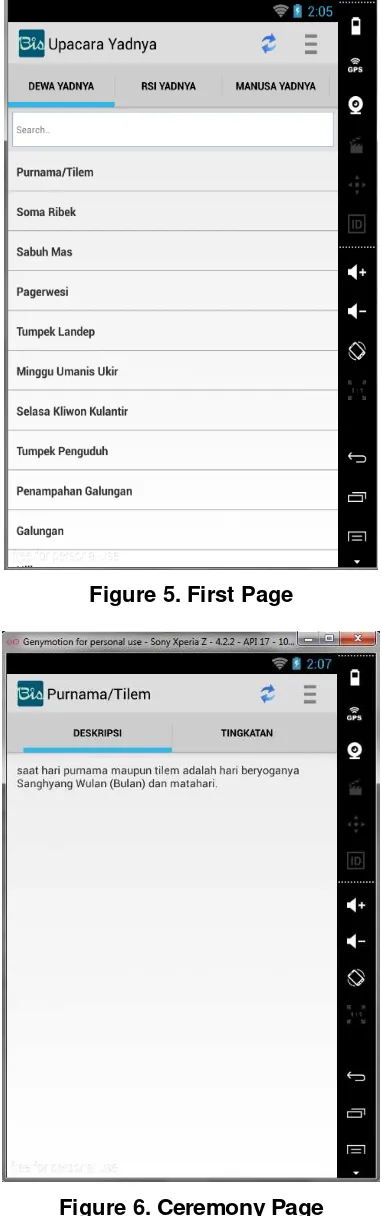
4.2. Application Display on Client Side
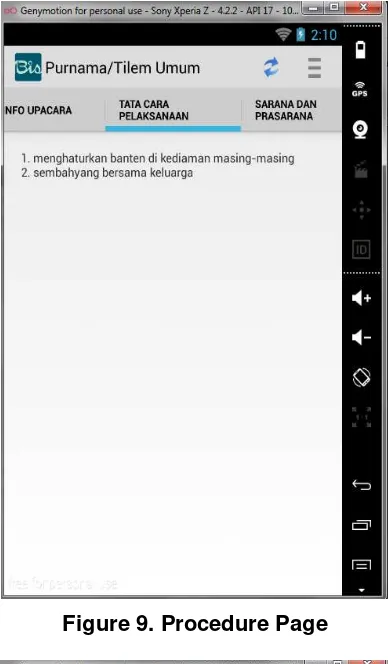
Copyright ⓒ 2014 SERSC 159
the server data will display in form of descriptions, levels, time of execution, the execution,
pemuput, procedures, facilities, and drawing ceremony.
Figure 5. First Page
160 Copyright ⓒ 2014 SERSC
Figure 7. Level Page
Copyright ⓒ 2014 SERSC 161
Figure 9. Procedure Page
162 Copyright ⓒ 2014 SERSC 4.3. Application Display on Server Side
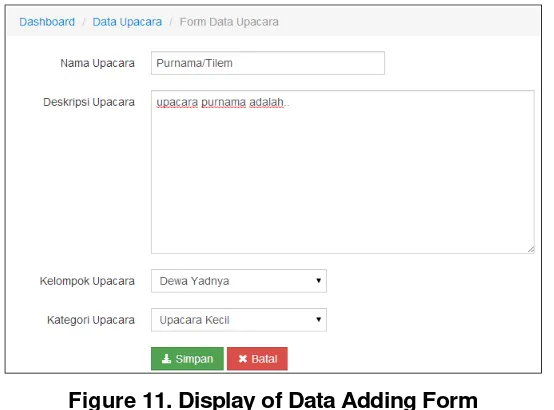
The administrator page is built in web-based applications. This application can be accessed in browser. The administrator page is to managing the database. The database system is essential to the development of the system [6]. The data entered on the page will be stored in a database administrator on the server. Through this application administrator can perform management on the database. They can then take additional data as in Figure 6.
Figure 11. Display of Data Adding Form
If the data in Figure 6 is saved, it will be displayed at a ceremony as part of the list seen in Figure 7.
Figure 12. Display of Ceremonial List
Administrator can add the data in more detail by selecting the ceremony view. Data can be added such as execution time, place, pemuput, procedures, facilities, and ceremonial images as shown in Figure 8.
Copyright ⓒ 2014 SERSC 163
5. Conclusion
The conclusion that can be drawn from the information systems of Yadnya ceremony application is as follows:
a.Yadnya ceremony can be made by a standard model that has properties that can
be used by all ceremony as group, description, time of execution, the execution, ordinances, pemuput, levels, graphics, and video of ceremony.
b.The tree diagram can be used to modeling the ceremony, because an ordinance
can have multiple sub-level with a certain degree of depth.
c.The application made with Android-based, so that users will be able to access the information from anywhere through the Internet.
d.Users with administrator authority can access the database processing so that the data contained in the database will grow and be able to help provide more information to many other user.
Acknowledgements
Thank you spoken to the whole community of the Department of Information Technology that has helped in the success of this research, and thank you also spoken to colleagues who have made significant ideas, input, and solutions in the completion of this research. All given assistance is very helpful in the success of the research of application
of Yadnya ceremony information system.
References
[1] O. Sudana, A. Agung K. Sistem Informasi Bebantenan Dalam Kaitannya dengan Upacara Yadnya. Jurnal Teknologi Elektro, ISSN: 1693-1951. Jimbaran : UNUD, 2009.
[2] Putu Darma, I Dewa. Upacara agama hindu di bali dalam perspektif pendidikan konversi tumbuhan. Jurnal Pengabdian Masyarakat, ISSN: 1412-0925. Jimbaran : UNUD, 2008.
[3] Oka Sudana, Anak Agung K. Tree Structure Implementation in Web Base E-Bebantenan. Journal of CSTID. Jimbaran : UNUD, 2009.
[4] Jogiyanto HM. Analisis dan Desain Sistem Informasi: Pendekatan Terstruktur Teori dan Praktik Aplikasi Bisnis. Yogyakarta: Andi Offset, 2005.
[5] Dunlu PENG, Lidong CAO, and Wenjie XU. “Using JSON for Data Exchanging in Web Service Applications,” Journal of Cumputational Information System 7:16. Desember 2011.
[6] Joseph M. Hellerstein, Michael Stonebraker, and James Hamilton. “Architecture of a Database System”. Foundations and Trends in Database. Vol. 1 No. 2 (2007) 141-259.
Author
Name : I Made Wahyu Saputra State: Indonesia