Full Terms & Conditions of access and use can be found at
http://www.tandfonline.com/action/journalInformation?journalCode=vjeb20
Download by: [Universitas Maritim Raja Ali Haji] Date: 11 January 2016, At: 21:59
Journal of Education for Business
ISSN: 0883-2323 (Print) 1940-3356 (Online) Journal homepage: http://www.tandfonline.com/loi/vjeb20
Retail E-Commerce Security Status Among Fortune
500 Corporations
Jensen J. Zhao & Sherry Y. Zhao
To cite this article: Jensen J. Zhao & Sherry Y. Zhao (2012) Retail E-Commerce Security Status Among Fortune 500 Corporations, Journal of Education for Business, 87:3, 136-144, DOI: 10.1080/08832323.2011.582191
To link to this article: http://dx.doi.org/10.1080/08832323.2011.582191
Published online: 01 Feb 2012.
Submit your article to this journal
Article views: 369
ISSN: 0883-2323 print / 1940-3356 online DOI: 10.1080/08832323.2011.582191
Retail E-Commerce Security Status Among
Fortune 500
Corporations
Jensen J. Zhao
Ball State University, Muncie, Indiana, USA
Sherry Y. Zhao
Massachusetts Institute of Technology, Cambridge, Massachusetts, USA
The authors assessed theFortune 500corporations’ retail e-commerce security to identify their strengths and weaknesses for improvement. They used online content analysis, information security auditing, and network security mapping for data collection and analysis. The findings indicate that most sites posted security policies; however, only one third stated what security measures were in action. Second, all of the sites securedMy Accountlogin with secure Sockets Layer Encryption, but only 16% limited 3 attempts of login access. Third, although the sites had most of their Internet ports filtered or behind firewalls, nearly one third of the sites’ computer operating systems were detected from the few open ports.
Keywords: computer network systems, port 80/tcp, port 443/tcp, retail e-commerce, security
The U.S. Census Bureau (2009) reported that e-commerce activities in the United States were growing faster than to-tal economic activities. Over the past years, the e-commerce share was on a continuous rise in the following major eco-nomic sectors: manufacturing industries, merchant whole-salers, retailers, and service industries. In the second quarter of 2010 the U.S. e-commerce estimate increased 14% from the second quarter of 2009, while total retail sales increased 7.5% in the same period (U.S. Census Bureau, 2010).
Although e-commerce has become popular, Internet pri-vacy violations and cyber attacks to the e-commerce systems are also on the rise. Privacy violations, such as failing to protect sensitive customer and employee data, have put these individuals at high risk of being victims of personal-identity and credit-card thefts (e.g., Farrell, Sheer, & Garrison, 2009; Lordan & Crawford, 2009). Cyber attacks have impaired or even shut down the e-commerce activities completely by damages such as website defacement, denial of service, price manipulation, financial fraud, or data breach (e.g., Greene, 2008; Hovanesian, 2008; Mookhey, 2004).
Correspondence should be addressed to Jensen J. Zhao, Ball State Uni-versity, Miller College of Business, Department of Information Systems & Operations Management, 2000 W. University Avenue, Muncie, IN 47306, USA. E-mail: jzhao@bsu.edu
Several federal laws are in effect to protect information privacy and security in the United States. The U.S. Federal Trade Commission (FTC) has been educating businesses and consumers about the importance of personal information privacy and security. Under the Federal Trade Commis-sion Act (FTCA; 2006), the commisCommis-sion guards against unfair competition and deceptive practices by enforcing companies’ privacy policies about how they collect, use, and secure consumers’ personal information. The U.S. Safe Web Act (2006), which is incorporated in the FTCA, enables the commission to cooperate with foreign law enforcement authorities in dealing with international fraud-ulent spam, spyware, misleading advertising, privacy and security breaches, and other consumer protections through confidential information sharing, investigative assistance, and enhanced staff exchanges (Federal Trade Act of 2006).
Even though the laws clearly mandate the privacy pro-tection, some companies neglected the laws and failed to protect consumers’ sensitive information or hackers violated the laws and broke the companies’ cyber defense. For in-stance, the FTC charged CVS Caremark in violation of fed-eral law for failing to take appropriate security measures to protect the sensitive financial and medical information of its customers and employees. CVS Caremark agreed to settle the FTC charges and establish, implement, and maintain a comprehensive information security program for protecting
RETAIL E-COMMERCE SECURITY 137
the security, confidentiality, and integrity of the personal in-formation it collects from consumers and employees (Farrell et al., 2009).
In July 2005, TJX Corporation experienced a massive in-trusion into its computer network systems, resulting in the largest systems and data security breach in history. As a Jan-uary 2007 report ofComputer Worldrevealed, at the time TJX disclosed the scope of its security breach, more than three dozen banks in Massachusetts reported that credit cards they issued had been compromised (Vijayan, 2007). According to documents filed with the federal court in Boston, this TJX security breach affected millions of consumers’ private in-formation, including about 29 million MasterCard victims and 65 million Visa victims (Schuman, 2007).
A 2006 survey of 214 bank websites (Hovanesian, 2008) reported that 75% of the sites were vulnerable to hacking, with two big worrisome trends: a) login boxes were placed on unencrypted web (http) pages on a bank’s domain and b) the use of third-party services transferred customers to insecure outside pages.
Symantec’s Global Internet Security Threat Report (Fossi et al., 2009) revealed that 90% of all Internet security threats detected by Symantec during 2008 attempted to steal confi-dential information. Threats with a keystroke-logging capa-bility, which can be used to steal information such as online bank account credentials, made up 76% of threats to confi-dential information, up from 72% in 2007. As the reported pointed out, in 2008 the average cost per incident of a data breach in the United States was $6.7 million, which is 5%
increase from 2007.
According to a cyber security report by NetWitness (Gorman, 2010), from late 2008 to early 2010, hackers gained access to a wide array of data at 2,411 companies, from ac-cessing corporate servers that process credit-card transac-tions to servers that store large quantities of business data, such as intellectual property files, contracts, and even up-coming versions of software products. Because the Internet is now the primary conduit for hacker attacks, it appears nec-essary to assess how secure the e-commerce sites are to block cyber intrusions and attacks.
Purpose of the Study and Research Questions
The purpose of the present study was to assess the security status of the retail e-commerce sites among theFortune 500
U.S. corporations because these corporations are the lead-ers in their respective industries. In the present study we addressed four research questions:
Research Question 1:What privacy and security measures are stated in policies on Fortune 500corporations’ e-commerce sites?
Research Question 2: How do Fortune 500 corporations’ e-commerce sites protect customer and employee infor-mation?
Research Question 3:How secure are the computer network systems ofFortune 500corporations’ e-commerce sites?
Research Question 4:Are there any significant differences among industry groups of theFortune 500corporations’ e-commerce sites?
The findings of the study would benefit the participat-ing companies for the continuous improvement of their e-commerce security. In addition, the findings would enable students specialized in Internet security or e-commerce to identify opportunities for internships or jobs at theFortune 500retail e-commerce sites that need to strengthen or main-tain their Internet security.
METHOD
Three main types of security diagnoses for assessing net-work security are security audit, vulnerability assessment, and penetration test. Security audit measures an information network system’s performance against a list of criteria such as laws and regulations through analyzing the web content and performance. A vulnerability assessment seeks security weaknesses of a network system exposed to hacker threats by using the network mapping software. Penetration test is a covert operation permitted by the network owner. In the test, a security expert tries a number of attacks to ascertain whether a system could withstand the same types of attacks from a malicious hacker (Ciampa, 2009; Winkler, 2004).
To assess the security status of the Fortune 500 e-commerce sites, we delimited the research scope by using information security audit and vulnerability assessment to address the research questions. Although the information security audit collected data for web content analysis and security audit to address Research Questions 1 and 2, the vulnerability assessment used the network security mapping to answer Research Question 3.
The web content analysis is commonly used in assessing organizations’ web content, deliveries, and strategies (Boggs & Walters, 2006; Wilkinson & Cappel, 2005; Zhao & Zhao, 2004). This method was used to systematically and objec-tively identify and record the privacy and security policies available at the e-commerce sites and then to analyze what privacy and security measures were stated as in implemen-tation. Specifically, two research assistants were trained to use an instrument (see Appendix A) to collect data for the web content analysis. To assure the validity and reliability of the data, the research assistants followed the data collec-tion procedure in the following way: Each week, the two assistants were assigned same five sites. From the same sites they collected data independently, and then, they compared their collected data and reached an agreement if there was any difference between them. When the research assistants encountered any difficulty and could not come to a team solu-tion or agreement, they met with the researchers for problem
solving and assurance of data quality. The method generated the following content categories for analysis: a) existence of privacy and security policies, b) antihacking notice, c) data transmission encryption, d) intrusion detection, e) investiga-tion of improper user activities, f) login authenticainvestiga-tion, g) no-liability notice, and h) Internet traffic monitoring.
The information security audit was used to determine or-ganizations’ compliance of the legislation, such as the Pri-vacy Act (1974) and the Children’s Online PriPri-vacy Protection Act (1998), which specify how organizations must handle in-formation and protect privacy (Hurley, 2002; Winkler, 2004). To determine how securely the e-commerce sites protect per-sonal information, we audited the sites’ information security by a) checking whether the My Accountlogin pages were secured with the Secure Socket Layer (SSL) encryption for data transmission, b) testing whether the login pages set a limited number of access attempts to prevent hackers’ guess-ing of usernames and passwords, and c) searchguess-ing through the sites’ search tools and Google search to see whether any personal information would be identified (Ciampa, 2009).
The network security mapping is a method of using soft-ware tools for assessing the vulnerability of an entire com-puter network system without intrusion and identifying areas of potential security threats (Garcia, 2004; Winkler, 2004). To assess the vulnerability of the e-commerce network systems, we selected a popular, free network mapping tool,Nmap, pro-vided by the website insecure.org.Nmapis a port scanning and network mapping software. It uses raw Internet protocol packets to determine what hosts are available on the network; what ports are open, filtered, or closed; what web services (application name and version) those hosts are offering; what computer operating systems (OS) and OS versions they are running; what type of packet filters and firewalls are in use; and many other characteristics (cf. http://insecure.org/).
To ensure that it would be legal and ethical to useNmapfor port scanning, the study reviewed related literature and could not find federal or state laws that specifically address the is-sue (e.g., U.S. Department of Justice, 2003). However, in a Georgia District Court case of Moulton v. VC3 (Jamieson, 2002), the judge declared a port scan in the case legal because it did not impair the integrity nor availability of the network. The judge found that since the activity performed no damage to the target, it could not be illegal (Jamieson, 2002). The implication of this case is that a port scan is not an attack and usually causes no damage to a target network; the legality and ethics of a port scan depend on whether the intent of a port scan is to cause damage or to improve security. As the purpose of this study was to provide the e-commerce admin-istrators with the findings that they need for the continuous improvement of their e-commerce security, usingNmapfor this study was justified.
The population of this study consisted of the retail e-commerce sites of theFortune 500largest U.S. corporations. A thorough search of the Fortune 500 corporate websites (Fortune, 2009) identified 116 retail e-commerce sites. These
TABLE 1
Demographic Profile ofFortune 500Retail E-Commerce Sites (N=116)
Group Type of company business n %
1. Airlines and hospitality services 13 11
2. Apparel and shoes 17 15
3. Commercial banks 12 10
4. Computer/telecommunication/electronic tools 29 25 5. Food/beverage/drug/personal products 23 20 6. General merchandisers/specialty retailers 22 19
116 sites were all used in the study according to the sample size requirement (Cochran, 1977). Table 1 shows the demo-graphic profile of these 116 sites.
Data were collected between October 2009 and April 2010 and then coded for statistical analysis. Frequency counts, per-centage distributions, means, and standard deviations were prepared. The Pearson chi-square test was used to determine if any significant differences existed at the .01 Cronbach’s al-pha level among industry groups in order to address Research Question 4.
RESULTS
The findings of the study are reported in the following se-quence: a) privacy and security measures on e-commerce sites, b) protection of personal information, c) security status of e-commerce network systems, and d) differences among industry groups.
Privacy and Security Measures on E-Commerce Sites
Research Question 1 asked the following: What privacy and security measures are stated in policies onFortune 500 cor-porations’ e-commerce sites? As Table 2 shows, of the 116 sites, 112 (97%) provided a link to the privacy policy state-ment on their home pages, but the name of the link varied and included “Privacy Policy,” “Privacy,” “Privacy Rights,” “Privacy/Security,” “Privacy, Security & Legal,” and “Terms of Use & Privacy.” The privacy policies commonly stated that the e-commerce sites are committed or dedicated to protect-ing the privacy and personal data it receives from customers in compliance with all relevant data protection and privacy laws. Most privacy policies consisted of the following sec-tions: a) what personal information does the site collect, b) how does the site use the collected information, c) how does the site protect users’ and children’s privacy, d) how can users access their own information, and e) what about links to other websites.
A total of 102 sites (88%) also presented a link to the se-curity policy on their homepages or embedded it within the privacy policy. The security policies usually indicated that
RETAIL E-COMMERCE SECURITY 139
TABLE 2
Fortune 500Privacy & Security Policy Status on their E-Commerce Sites (N=116)
n %
Privacy and security policy status
A privacy policy link available on e-commerce homepage 112 97 A security policy link available on e-commerce homepage 102 88 A proper-use note attached to the security policy or
disclaimer
66 57
A no-liability note attached to the security policy or disclaimer
54 47
Security measures
Encryption: using secure socket layer (SSL) encryption to protect data transmissions
83 72
Authentication: using username and password to protect for account privacy and security
64 55
Monitoring: using software programs to monitor Internet traffic
49 42
Auditing: identifying unauthorized attempts to upload or change information
42 36
Investigation: investigating improper activities to identify individual persons
30 26
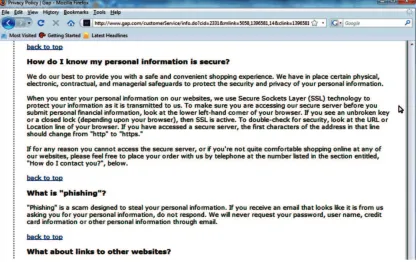
the e-commerce sites use the appropriate physical, electronic, and managerial measures to safeguard the data collected on-line and to prevent unauthorized access (see, for example, Figure 1).
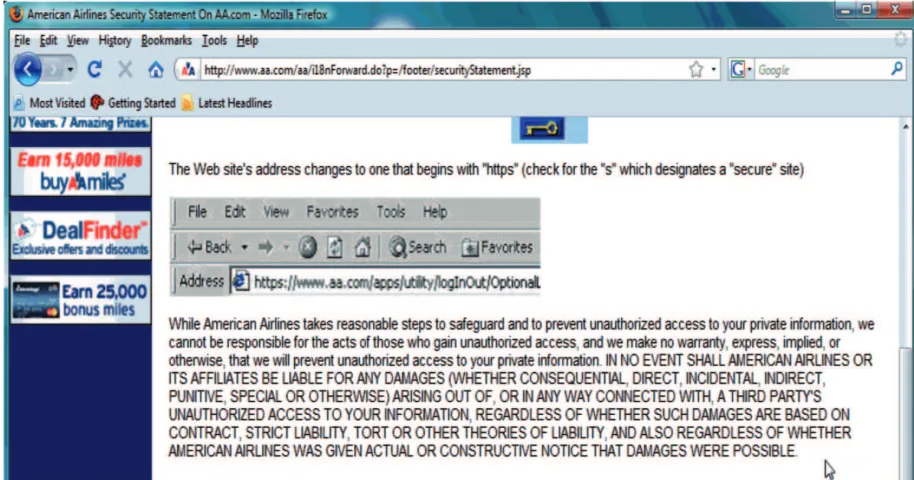
More than half (57%) of sites also included a proper-use statement in their security policy for enforcing users’ proper online behaviors. However, nearly half (47%) of sites also
included a no-liability note in their security policy to avoid any legal liability if their sites were attacked and consumer accounts were stolen (see, for example, Figure 2).
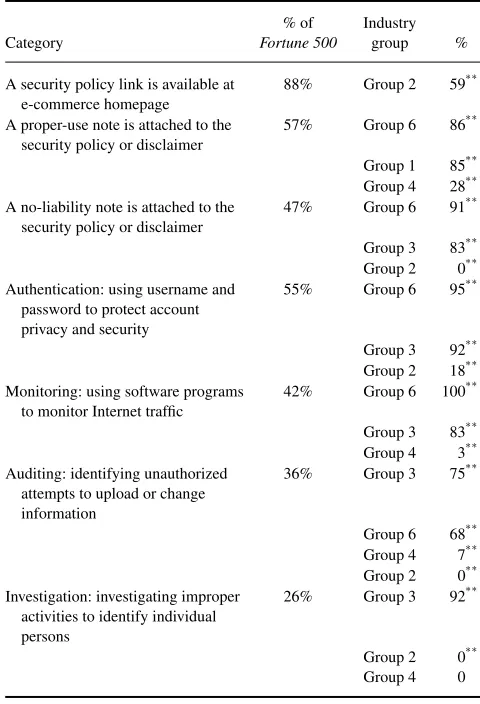
Regarding the security measures, most of the sites clearly stated using SSL encryption to protect data transmission (73%) and using username and password to protect account privacy and security (55%). However, only around one third of the sites stated how they monitor Internet traffic (42%), how they audit unauthorized attempts to upload or change in-formation (36%), and how they investigate improper online activities (26%).
Protection of Personal Information
Research Question 2 asked the following: How doFortune 500 corporations’ e-commerce sites protect customer and employee information? As Table 3 illustrates, 100% of the sites securedMy Accountlogin pages with SSL encryption for data transmission. However, only 16% of the sites lim-ited a user to have a maximum of three access attempts to log in as a security measure to prevent hackers’ guessing of usernames and passwords guessing. Obviously, the majority (84%) of My Account login pages required only the basic security measures of username and password for accessing such private and personal accounts. This login practice was vulnerable to hacker intrusion because hackers could easily get into an account by using the software tools for automati-cally and repeatedly guessing usernames and passwords.
Regarding weather the e-commerce site’s search tools would reveal employee and customer information, the test
FIGURE 1 Security statement on Gap.com e-commerce site (color figure available online).
FIGURE 2 No-liability notice on AA.com e-commerce site (color figure available online).
results indicated that only a minority of their search tools would generate some results of company employees’ infor-mation such as their name (33%), job title (32%), affiliation (5%), and salary (4%). No customer information could be generated through the search with the e-commerce site search tools.
The Google search also generated little to no informa-tion of the companies’ employees. Only two companies’ em-ployee names and one company’s emem-ployee job titles were searchable from Google. The search did not generate any in-formation of the companies’ employee affiliation and salary.
TABLE 3
Customer and Employee Information Security on E-Commerce Sites (N=116)
Category n %
My Accountpage secured with SSL encryption 116 100 My Accountlogin limiting 3 access attempts 18 16 E-commerce site search results
Employee name 38 33
Employee job title 37 32
Employee’s affiliation 6 5
Employee salary 5 4
Customer information 0 0
Google.com search results
Employee name 2 2
Employee job title 1 1
Employee’s affiliation 0 0
Employee salary 0 0
Security Status of E-Commerce Network Systems
Research Question 3 asked the following: How secure are the computer network systems ofFortune 500corporations’ e-commerce sites? Computer network systems connect to the Internet through communication ports. The ports of an Internet-connected computer are classified into the well-known ports, the registered ports, and the dynamic or private ports. The numbers of the well-known ports range from 0 to 1023, those of the registered ports are from 1024 to 49151, and those of the dynamic or private ports range from 49152 to 65535. If the ports are open on the Internet without fire-walls or filters, they are very vulnerable to cyber intrusions and attacks.
As Figure 3 shows, of the 116 sites scanned byNmap, 112 sites (97%) revealed 1,705 Internet ports at each of their network; only four sites showed 1,680 ports per each. The scan report also indicated that most of these ports were fil-tered, behind firewalls, or closed, and only very few ports were open. As Figure 4 shows, among 112 sites that revealed 1,705 ports at each of their network, 108 sites filtered, fire-walled, or closed most of their ports, ranging from 1,701 to 1,704 ports at each site. Similarly, among the four sites that revealed 1,680 ports (see Figure 3), two sites had all their ports filtered, firewalled, or closed, whereas the other two had 1,679 ports filtered, firewalled, or closed (see Figure 4). However, three sites only filtered, firewalled, or closed 1,695 of their 1,705 ports. Only one site just secured 1,680 of its 1,705 ports.
The scan report also presented the network vulnerabil-ity from the open ports. Of the 116 sites, 113 (97%) had
RETAIL E-COMMERCE SECURITY 141
FIGURE 3 Number of Internet ports scanned atFortune 500e-commerce sites (color figure available online).
port 80/tcp open for the web or http service. Web servers frequently disclosed via port 80/tcp were Apache, Microsoft IIS, and Netscape servers. In addition, 92 sites (79%) had port 443/tcp open for the https service of encrypted data transmis-sion. Only 15 sites (13%) had port 22/tcp open for the secure shell (ssh) communication. However, from the open ports, the network scanner detected information of nearly one third of the sites’ computer operating systems, such as Windows IE7/XP/2003 Server, Sun Solaris 8, Linux 2.6.8–2.6.9, and IBM AIX 4.3.2.0–4.3.3.0 on IBM RS/x. A follow-up anal-ysis found that these sites did not include any commercial bank sites. Finally, the scanner did not identify any of the following ports open: port 21/tcp for file transfer protocol (FTP) service, port 23/tcp for telnet remote access, and port 53/tcp for domain name server (DNS) service of mapping domain names. These ports are usually the primary targets for cyber attacks and intrusions if they are open.
Differences Among Industry Groups
Research Question 4 asked the following: Are there any sig-nificant differences among industry groups of the Fortune 500corporations’ e-commerce sites? As Table 4 shows,
sig-FIGURE 4 Number of ports filtered, firewalled, or closed atFortune 500 e-commerce sites (color figure available online).
nificant differences existed among the six industry groups on privacy and security protection. Significantly fewer sites in the apparel and shoes industry (Group 2, 59%) posted a security policy link on their home pages in comparison with 88% of theFortune 500sites. Regarding the proper-use note, significantly more sites in the general merchandisers and spe-cialty retailers industry (Group 6, 86%) and the airlines and hospitality services industry (Group 1, 85%) attached such a note to the security policy, whereas significantly fewer sites of the computer, telecommunications, and electronic tools industry (Group 4, 28%) did so. In addition, although signif-icantly more sites of the general merchandisers and specialty retailers industry (Group 6, 91%) and the commercial banks (Group 3, 83%) attached a no-liability note to their security policy, no site of the apparel and shoes industry (Group 2, 0%) posted such a note.
Regarding the implementation of security measures, sig-nificantly more sites of Group 6 (95%) and Group 3 (92%) stated using username and password authentication for se-curity protection, when compared with 55% of theFortune
TABLE 4
Pearson Chi-Square Test of Significant Differences Among Industry Groups
A security policy link is available at e-commerce homepage
88% Group 2 59∗ ∗
A proper-use note is attached to the security policy or disclaimer
57% Group 6 86∗ ∗
Group 1 85∗ ∗ Group 4 28∗ ∗ A no-liability note is attached to the
security policy or disclaimer
attempts to upload or change information
500as a whole. In contrast, Group 2 (18%) did significantly less. For monitoring the Internet traffic, significantly more sites of Group 6 (100%) and Group 3 (83%) stated using software programs to monitor the traffic than did theFortune 500(42%). But significantly fewer sites of Group 4 (3%) did so. Concerning the audit of user activities, significantly more sites of Group 3 (75%) and Group 6 (68%) stated auditing and identifying unauthorized attempts to upload or change information when compared with theFortune 500(36%) as a whole. However, significantly fewer sites of Group 4 (7%) and Group 2 (0%) did so. Finally, regarding the investiga-tion of improper user activities, significantly more sites of Group 3 (92%) stated so when compared with the Fortune 500(26%) as a whole. Nevertheless, no single site of Group 2 and Group 4 did so.
SUMMARY AND DISCUSSION
Most of theFortune 500retail e-commerce sites posted pri-vacy policies (97%) and security policies (88%) on the home pages and described ways of handling and protecting the pri-vacy and personal data in compliance with pripri-vacy laws. The policies clearly stated using SSL encryption to protect data transmission and using username and password to protect account privacy. These findings indicate that the large U.S. corporations’ sites did much better than other companies in privacy protection, as the 2009 InformationWeek analytics survey of 430 business technology professionals found so little encryption on so much enterprise data (Davis, 2009).
However, improvement is needed because only around one third of the sites stated how they monitor Internet traffic, audit unauthorized attempts to upload or change information, and investigate improper online activities. Clearly, the other two-thirds of the sites have to review their policies and assure to include needed security measures to protect consumers’ sensitive information from hacker attacks. Otherwise, if data breach happened to their sites, the companies would face the legal charges by the law enforcement authorities as shown in the CVS Caremark case (Farrell et al., 2009).
Nearly half of sites included a no-liability note in their security policies to avoid any legal liability if their sites were attacked and consumer accounts were stolen. Obviously, this no-liability note would very likely stop cautious online shop-pers from buying anything at these sites (Yang, Chandlrees, Lin, & Chao, 2009). Furthermore, whether a site is liable to a data breach is not up to the no-liability statement, but up to the law enforcement authorities’ examination of the site’s privacy compliance (Kaplan, Kresses, & Marcus, 2008; Lordan & Crawford, 2009).
All of the sites securedMy Accountlogin pages with SSL encryption for data transmission. However, 84% of the sites failed to limit a maximum of three access attempts for login. The failure to set this second security defense has made the login vulnerable because hackers could easily get into
an account by guessing username and password (Ciampa, 2009). Obviously, these 84% of the sites need to improve their login pages by limiting the number of login attempts.
No site’s search tools generated any customer informa-tion. When searching for employee information, one third of the sites revealed some employee names and job titles. The Google search generated little to no information of the companies’ employees. These findings indicate that the large U.S. corporations’ sites in general are secure in protecting employee and consumer information.
Moreover, the sites had most of their Internet ports fil-tered, behind firewalls, or closed, with only very few ports open, such as port 80/tcp and port 443/tcp. From the open ports, the network scanner detected nearly one third of the sites’ computer operating systems information. These find-ings indicate that the sites still had a few spots vulnerable to cyber intrusions, as the open ports would enable cyber intruders to detect the ports’ detailed information such as server names and versions, service status, and computer op-erating systems. Knowing such detailed information, cyber intruders would be able to find their ways to intrude into and hack at those open, vulnerable ports. As a consequence, web services could be paralyzed by the denial of service (DoS) attacks (Symantec, 2007), important data could be changed, stolen, or deleted by cross site scripting and Structured Query Language (SQL) code injection (Moen, Klingsheim, Simonsen, & Hole, 2007), and computer operating systems could be impaired (Halcnin, 2004), if the website has no 24 hr/day, 7 days/week security surveillance for monitoring the web traffic.
Significant differences existed among the six industry groups on e-commerce privacy and security protection. Com-mercial banks, general merchandisers, and specialty retailers did significantly better than other industry groups in imple-menting security measures of authenticating username and password, monitoring Internet traffic, and auditing unautho-rized attempts to upload or change information. In addition, the commercial banks’ sites were significantly more active than other industries in investigating improper online activi-ties to identify individual persons.
Furthermore, theNmap scanner did not detect any op-erating systems information from the sites of the commer-cial banks. Obviously, the findings of the commercommer-cial banks in this study did not support the 2006 survey results of Hovanesian (2008) that 75% of bank websites were vul-nerable to hacking. This could mean that banks had made continuous improvement in securing their sites. The findings would also enable other industry groups to benchmark com-mercial banks, general merchandisers, and specialty retailers in implementing their e-commerce security measures.
Practical and Pedagogical Implications
The findings of this study identified strengths and weaknesses of theFortune 500retail e-commerce sites. These findings
RETAIL E-COMMERCE SECURITY 143
would not only enable e-commerce administrators to learn from the other sites’ strengths and improve over their own weaknesses, but also assist business and information tech-nology educators in advising their students in internship and job searches.
First, because two-thirds of the sites failed to state the security measures in their policies, it is necessary for the ad-ministrators of these sites to consider including the following security measures in their security policies and implement-ing them immediately: monitorimplement-ing Internet traffic, auditimplement-ing unauthorized attempts to upload or change information, and investigating improper online activities to identify individual persons and report them to the law enforcement authorities.
Second, because only 16% of the sites set the limit to a maximum of three access attempts to My Accountlogin to prevent hackers’ guessing of usernames and passwords, the administrators of the other 84% of sites should consider the need for limiting a maximum of three login access attempts as a security measure.
Furthermore, the administrators of the sites should con-sider following theFortune 500commercial banks’ examples and filtering or firewalling ports 80/tcp and 443/tcp. There-fore, the internal hosts’ server names and versions, service status, and computer operating systems would not be detected by port and network mapping scanners.
Finally, around two-thirds of the sites need to improve their privacy and security policies and technologies. Such needs appear to imply opportunities for student internships and jobs at theFortune 500retail e-commerce sites. There-fore, business and information technology educators should consider contacting the administrators of these sites for cre-ating internships or job positions for students specialized in e-business or Internet security.
REFERENCES
Boggs, R. A., & D. Walters. (2006). A longitudinal look at e-government in practice.Issues in Information Systems,7, 161–164.
Ciampa, M. (2009).Security+guide to network security fundamentals(3rd ed.). Boston, MA: Cengage Learning.
Children’s Online Privacy Act of 1998, Pub. L. 105–277, 112 stat. 2581-728 (1998).
Cochran, W. G. (1977).Sampling techniques(3rd ed.). New York, NY: Wiley.
Davis, M. A. (2009, November 23). What will it take? So much data, so little encryption.InformationWeek,1249, 23–31.
Farrell, C. B., Sheer, A., & Garrison, L. (2009, February 18).CVS Caremark settles FTC charges: Failed to protect medial and financial privacy of customers and employees[Press release]. Retrieved from http://www.ftc. gov/opa/2009/02/cvs.shtm
Federal Trade Commission Act of 2006, 15 U.S.C.§§42–58 (2006). Fortune. (2009, May). The Fortune 500 largest U.S. corporations.Fortune,
159(9), F-34–45.
Fossi, M., Johnson, E., Mack, T., Blackbird, J., Low, M. K., Adams. T.,... Samnani, A. (2009, April).Symantec global Internet security threat re-port: Trends for 2008(Vol. 14). Retrieved from http://eval.symantec.com/ mktginfo/enterprise/white papers/b-whitepaper internet security threat report xiv 04-2009.en-us.pdf
Garcia, R. C. (2004). Network security: Mapping intrusion and anomaly detection to very-high-degree polynomials.Signals, Systems, and Com-puters,2, 1449–1452.
Gorman, S. (2010, February 18). Hackers attack 2.411 firms.Wall Street Journal, p. A3.
Greene, T. (2008, August). Business hacks reap money from e-commerce sites.Network World,25(30). Retrieved from http://www.networkworld. com/news/2008/080808-business-hacks.html
Halcnin, L. E. (2004). Electronic government: Government capability and terrorist resources.Government Information Quarterly,21, 406–419. Hovanesian, M. D. (2008, August 11). Security holes at the online bank.
Business Week, p. 16.
Hurley, E. (2002, April 3). Audits confirm enterprise security. Tech Target. Retrieved from http://searchsecurity.techtarget.com/news/ article/0,289142,sid14 gci814796,00.html
Jamieson, S. (2002).The ethics and legality of port scanning. Bethesda, MD: SANS Institute. Retrieved from http://www.sans.org/reading room/whitepapers/legal/the ethics and legality of port scanning 71? show=71.php&cat=legal
Kaplan, P., Kresses, M., & Marcus, P. (2008, December 11). Sony BMG Music settles charges its music fan web sites violated the Chil-dren’s Online Privacy Protection Act[Press release]. Retrieved from http://www.ftc.gov/opa/2008/12/sonymusic.shtm
Lordan, B., & Crawford, M. (2009, February 5).Consumer electronics company agrees to settle date security charges[Press release]. Retrieved from http://www.ftc.gov/opa/2009/02/compgeeks.shtm
Moen, V., Klingsheim, A. N., Simonsen, K. F., & Hole, K. J. (2007). Vulnerabilities in e-governments.International Journal of Elec-tronic Security and Digital Forensics, 1, 89–100. Retrieved from http://www.inderscience.com/storage/f125431610811792.pdf
Mookhey, K. K. (2004, April 26). Common security vulnerabilities in e-commerce systems. Security Focus. Retrieved from http://www. securityfocus.com/infocus/1775
Privacy Act of 1974, Pub. L. 93-579, 88 stat. 1896 (1974).
Schuman, E. (2007, October 24). TJX breach more than twice as bad as reported.eWeek. Retrieved from http://www.eweek.com/print article2/ 0,1217,a=217939,00.asp
Symantec. (2007, September). Symantec internet security threat report. Symantec Enterprise Security,12, 1–30.
U.S. Census Bureau. (2009).The 2007 e-commerce multi-sector “E-Stats” report. Measuring the electronic economy. Washington, DC: Author. U.S. Census Bureau. (2010). Quarterly retail e-commerce sales: 2nd
quarter 2010. E-stats—measuring the electronic economy. Washington, DC: Author. Retrieved from http://www.census.gov/retail/mrts/www/ data/pdf/10q2.pdf
U.S. Department of Justice. (2003). Fraud and related activity in connec-tion with computers. In the United States Code Annotated Title 18, Chapter 47, Section 1030. Washington, DC: Author. Retrieved from http://www.justice.gov/criminal/cybercrime/patriot redline.htm U.S. Safe Web Act of 2006, Pub. L. No. 109-455, 120 stat. 3376 (2006). Vijayan, J. (2007, January 19). Breach at TJX shows IT security still
lacking in retail industry.Computer World. Retrieved from http://www. computerworld.com/action/article.do?command=viewArticleBasic& articleId=9008599
Wilkinson, V. O., & Cappel, J. J. (2005). Impact of economic prosperity and population on e-government involvement.Issues in Information Systems, 6, 204–209.
Winkler, I. (2004, July 19). What is a security audit? Tech Target. Retrieved from http://searchcio.techtarget.com/sDefinition/0,,sid182 gci955099,00.html
Yang, M., Chandlrees, N., Lin, B., & Chao, H. (2009). The effect of perceived ethical performance of shopping web sites on consumer trust.Journal of Computer Information Systems,50(1), 15–24.
Zhao, J. J., & Zhao, S. Y. (2004). Internet technologies used by INC. 500 corporate web sites. Issues in Information Systems, 5, 366– 372.
APPENDIX—Security Audit of Retail E-Commerce Sites
Company Name: URL: http:// Auditing Date: / / Auditor Name:
Directions:Please read each of the following questions carefully and audit the site meticulously. You must save each of your search results digitally, print out a hard copy, and attach it to its audit instrument for double-check.
PART I. E-Commerce Privacy and Security Policy Status
1. Is there a Privacy Policy statement or disclaimer on the company e-commerce homepage? Yes
No
2. Is there a Security Policy statement or disclaimer on the company e-commerce homepage? Yes
No (please skip Question 3 and continue on Question 4).
3. Which of the following security measures were stated in use? (Please check all that apply.) a. Monitoring: using software programs to monitor traffic
b. Auditing: identifying unauthorized attempts to upload or change information or otherwise cause damage c. Investigation: investigating improper activities to identify individual persons
d. Authentication: using username and password to protect for account privacy and security e. Encryption: using secure socket layer (SSL) encryption to protect data transmissions
f. Other (Please specify: .)
4. Does the security/privacy statement provide ano-liabilitynote similar to the following?
“The information contained in this policy should not be construed in any way as giving business, legal, or other advice, or warranting as fail proof, the security of information provided via this website.”
Yes No
5. Is there a Proper Use or Anti-Hacking statement on the e-government homepage? Yes No
PART II. Customer Account Security Status on E-Commerce Sites
6. Does My Account link usehttps://(SSL) encryption? Yes No
7. Does My Account Login page limita maximum of three access attemptsof typing usernames and passwords? Yes No
8. Does e-commerce site’s Search tool reveal sensitive information of company top executives? Yes. No
If yes, which of the following information are revealed? (Please check all that apply.) a. Executive’s name b. Executive’s job title
c. Executive’s annual salary d. Executive’s other compensation e. Executive’s phone number f. Executive’s email address
f. Other (Please specify: .)
9. Does e-commerce site’s Search tool reveal sensitive information of company employees? Yes. No
10. If yes, which of the following information are revealed? (Please check all that apply.) a. Employee name b. Employee job title
c. Employee salary d. Employee’s affiliation/employer e. Employee’s home address
f. Other (Please specify: .)