Informasi Dokumen
- Penulis:
- Abraham Silberschatz
- Peter Baer Galvin
- Greg Gagne
- Sekolah: Yale University
- Mata Pelajaran: Computer Science
- Topik: Operating System Concepts
- Tipe: textbook
- Tahun: 2018
- Kota: Hoboken, NJ
Ringkasan Dokumen
I. Overview
This section introduces the fundamental concepts of operating systems, their role in computer systems, and their diverse applications across various computing environments. It establishes the context for subsequent chapters by highlighting the interaction between hardware, software, and users. The section emphasizes the operating system's role as a resource allocator, managing CPU time, memory, storage, and I/O devices to ensure efficient and fair system operation. It also touches upon the different user interfaces and computing environments, such as traditional PCs, mobile devices, and embedded systems, showcasing the adaptability of operating systems.
1.1 What Operating Systems Do
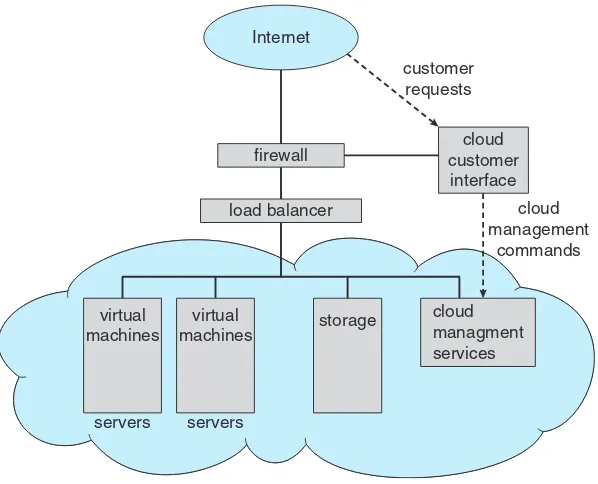
This subsection explores the operating system's role from both the user's and the system's perspectives. From the user's standpoint, the operating system provides a user-friendly interface for interacting with the computer, tailored to different types of devices (desktops, laptops, mobile devices, etc.). From the system's perspective, the operating system acts as a resource allocator, managing various system resources like CPU time, memory, and I/O devices to optimize efficiency and fairness among competing applications and users. The figure (Figure 1.1) illustrating the interaction between user, applications, operating system, and hardware visually reinforces these key concepts.
1.2 Computer-System Organization
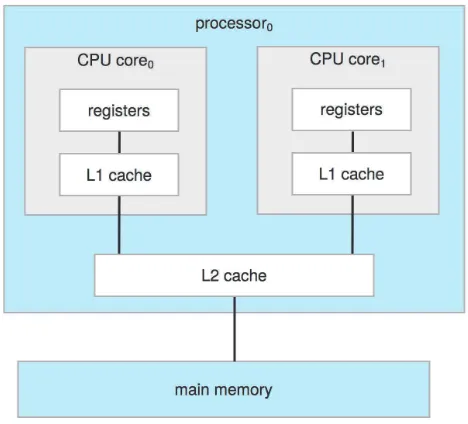
This subsection delves into the hardware components of a computer system, including the CPU, memory, and I/O devices. It explains how these components interact and cooperate to execute programs. The role of interrupts in managing and coordinating the system’s activities is also explained, highlighting their importance in achieving efficient resource utilization and responsiveness. The importance of understanding computer organization as a foundation for studying operating systems is stressed. The discussion provides a solid groundwork for understanding how the OS interacts with and manages hardware components.
1.3 Computer-System Architecture
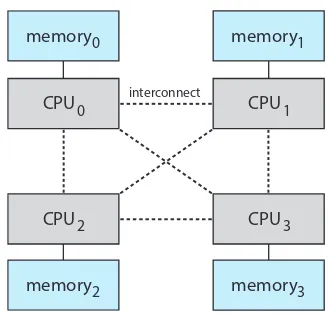
This section examines various architectural aspects of computer systems, emphasizing the importance of understanding how they affect the design and implementation of operating systems. This includes discussion of multiprocessor systems, their organization, and the challenges and opportunities they present in terms of resource management and concurrency. Key architectural elements like the CPU, memory hierarchy, and I/O buses are explained, with emphasis on their role in overall system performance. The importance of architectural considerations in developing efficient and scalable operating systems is highlighted.
1.4 Operating-System Operations
This subsection focuses on the mechanisms by which operating systems manage the transition between user mode and kernel mode, emphasizing the critical role of system calls. It explains how user processes request services from the operating system kernel and how the kernel responds to these requests. The importance of protecting the operating system kernel from malicious or erroneous user-level code is highlighted. The different ways an operating system handles the transition between different execution modes are also explained.
1.5 Resource Management
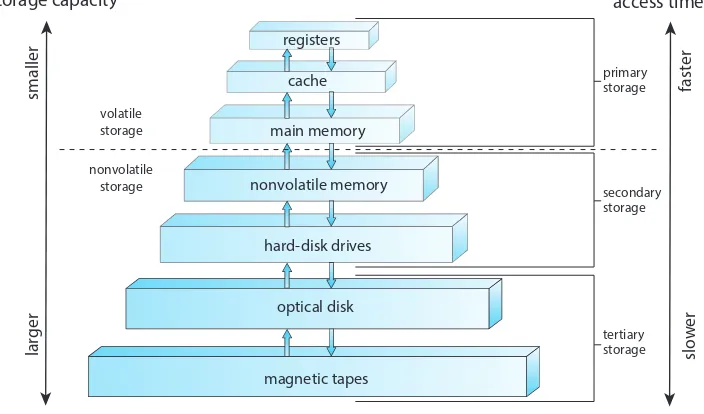
This subsection discusses the core function of an operating system as a resource manager. It details how the OS allocates and manages various resources, including CPU time, main memory, secondary storage, and I/O devices. The challenges of efficient resource allocation in the presence of concurrent processes are examined, including the concept of resource contention and the strategies the OS uses to address this. The fairness and efficiency requirements of resource management are emphasized.
1.6 Security and Protection
This subsection provides a preliminary overview of the crucial role of security and protection in operating systems. It introduces the fundamental principles of ensuring that processes and users only access the resources they are authorized to use. This section highlights the importance of protecting the system from unauthorized access, malicious attacks, and accidental data corruption. The basic concepts lay the groundwork for more in-depth discussions in later chapters.
1.7 Virtualization
This subsection offers an introductory look at virtualization—a crucial aspect of modern operating systems. It explains the concept of creating virtual machines that allow multiple operating systems to run concurrently on a single physical machine. The advantages of virtualization, such as improved resource utilization and isolation, are discussed. This prepares the reader for a more detailed discussion in a later chapter dedicated solely to this topic.
1.8 Distributed Systems
This brief introduction to distributed systems sets the stage for later chapters. It touches upon the concept of operating systems spanning multiple computers and the challenges and opportunities this presents. The advantages of distributed systems, such as increased scalability and fault tolerance, are briefly discussed. This section emphasizes the increasingly important role of distributed systems in contemporary computing.
1.9 Kernel Data Structures
This subsection introduces some of the fundamental data structures commonly used within operating system kernels, providing a glimpse into the internal workings of the OS. It might briefly mention examples such as linked lists, trees, and hash tables, explaining how they are employed for managing system resources or tracking processes. This section provides a basic level of understanding of the underlying data structures crucial to OS functionality, laying groundwork for later, more detailed discussions.
1.10 Computing Environments
This subsection expands on the diverse computing environments in which operating systems operate, highlighting differences and similarities in design considerations. It revisits the examples of traditional PCs, mobile devices, and embedded systems, providing more specific examples and discussing how OS design adapts to the unique needs of each environment. The section underscores the diversity of contexts in which OS principles are applied.
1.11 Free and Open-Source Operating Systems
This final subsection of the introductory chapter highlights the significance of free and open-source operating systems (FOSS), such as Linux. It discusses their impact on the computing landscape and their relevance to both academic study and practical application. The advantages of open-source systems—including their transparency, community support, and adaptability—are discussed. This sets the stage for the later detailed case study of the Linux operating system.
II. Operating-System Structures
This chapter delves into the architectural aspects of operating systems, examining their design and implementation strategies. It explores the services provided by operating systems, the interface between users and the OS, the crucial role of system calls, and the internal structure of the kernel. The chapter also addresses the operating system boot process, detailing how the OS loads and initializes the system. Additionally, it covers system debugging, emphasizing how to identify and resolve issues within the OS.
2.1 Operating-System Services
This subsection details the various services provided by an operating system to users and applications. These services might include program execution, I/O operations, file system management, communication, error detection, and resource allocation. Each service is explained with regards to its importance to the overall functionality of the system, and its implementation within the OS kernel.
2.2 User and Operating-System Interface
This subsection focuses on the various ways users interact with the operating system. It examines different types of user interfaces, such as command-line interfaces, graphical user interfaces (GUIs), and API calls. The discussion explores the trade-offs and advantages of each type of interface in relation to user experience, efficiency, and system security. The subsection highlights how the interface influences the design and implementation of OS functions.
2.3 System Calls
This subsection dives into the details of system calls, the primary mechanism by which user-level programs request services from the operating system kernel. It explains the process of making a system call, the parameters involved, and how the operating system handles the request. Examples of different system calls and their functionalities are provided, underscoring the critical role of system calls in OS-level functionality. The architectural considerations for efficient system call implementation are also discussed.
2.4 System Services
Building upon the discussion of system calls, this subsection expands on the specific system services provided by the OS kernel. These services might include file manipulation, process management, memory allocation, inter-process communication (IPC), and network access. Each service’s functionality is elaborated, along with its underlying implementation, highlighting the different ways the services are provided across different operating systems. The key to providing efficient and reliable services is also discussed.
2.5 Linkers and Loaders
This section details the role of linkers and loaders in the context of operating system functionality. It explains how linkers combine different parts of a program into an executable file and how loaders subsequently load these executables into memory for execution. The significance of this process in the overall system functionality is discussed, including its importance in system security and reliability. The process is elaborated upon in relation to efficient memory management and the implementation of dynamic linking.
2.6 Why Applications Are Operating-System Specific
This section explains why applications often require specific operating systems, exploring the reasons behind this dependency. This discussion highlights the role of system calls, hardware dependencies, and the differences in API calls across various operating systems. It also touches on library dependencies and how differences in the underlying OS architecture constrain application portability and compatibility. The section emphasizes the interconnectedness of applications and OS environments.
2.7 Operating-System Design and Implementation
This subsection explores different approaches to operating system design and implementation. It discusses various design goals, such as modularity, efficiency, security, portability, and extensibility. Different design principles, such as layered, microkernel, and monolithic architectures, are compared and contrasted. The relative merits and drawbacks of each design philosophy are considered in the context of specific system requirements. The importance of a well-defined design process is highlighted.
2.8 Operating-System Structure
This section provides a detailed overview of the internal structure of an operating system. It discusses various structural components such as the kernel, system calls, libraries, and user-level programs. The way these components interact is described in detail, with specific examples illustrating the relationships between the different parts. The internal structure is described in the context of efficient resource management and system stability.
2.9 Building and Booting an Operating System
This section explains the process of building and booting an operating system, tracing the steps from compilation to execution. It discusses the roles of various tools and processes involved, such as compilers, linkers, loaders, and boot loaders. Specific examples are provided to illustrate the different steps. The boot process is described in detail, highlighting its crucial role in initializing the system and loading the OS into memory.
2.10 Operating-System Debugging
This subsection discusses methods for debugging operating systems. It covers different techniques and tools used to identify and resolve errors in OS code. It may include examples of debugging tools and techniques commonly used, such as system logs, debuggers, and trace tools. The specific challenges involved in debugging a complex system like an OS are also explored, along with techniques to efficiently find and correct errors.
2.11 Summary
This concluding subsection summarizes the key concepts and principles presented in the chapter. It reinforces the essential aspects of operating system structures and provides a concise overview of the material covered. It serves as a useful reference point for reviewing the key ideas and their interconnections, preparing the reader for subsequent chapters.