w w w. s y n g r e s s . c o m
Syngress is committed to publishing high-quality books for IT Professionals and delivering those books in media and formats that fi t the demands of our cus tomers. We are also committed to extending the utility of the book you purchase via additional materials available from our Web site.
SOLUTIONS WEB SITE
To register your book, visit www.syngress.com/solutions. Once registered, you can access our [email protected] Web pages. There you may fi nd an assortment of valueadded features such as free e-books related to the topic of this book, URLs of related Web sites, FAQs from the book, corrections, and any updates from the author(s).
ULTIMATE CDs
Our Ultimate CD product line offers our readers budget-conscious compilations of some of our best-selling backlist titles in Adobe PDF form. These CDs are the per-fect way to extend your reference library on key topics pertaining to your area of expertise, including Cisco Engineering, Microsoft Windows System Administration, CyberCrime Investigation, Open Source Security, and Firewall Confi guration, to name a few.
DOWNLOADABLE E-BOOKS
For readers who can’t wait for hard copy, we offer most of our titles in downloadable Adobe PDF form. These e-books are often available weeks before hard copies, and are priced affordably.
SYNGRESS OUTLET
Our outlet store at syngress.com features overstocked, out-of-print, or slightly hurt books at signifi cant savings.
SITE LICENSING
Syngress has a well-established program for site licensing our e-books onto servers in corporations, educational institutions, and large organizations. Contact us at [email protected] for more information.
CUSTOM PUBLISHING
Jesse Varsalone
Robert J. Shimonski
Kelly Brown
(collectively “Makers”) of this book (“the Work”) do not guarantee or warrant the results to be obtained from the Work.
There is no guarantee of any kind, expressed or implied, regarding the Work or its contents. The Work is sold AS IS and WITHOUT WARRANTY. You may have other legal rights, which vary from state to state.
In no event will Makers be liable to you for damages, including any loss of profi ts, lost savings, or other incidental or consequential damages arising out from the Work or its contents. Because some states do not allow the exclusion or limitation of liability for consequential or incidental damages, the above limitation may not apply to you.
You should always use reasonable care, including backup and other appropriate precautions, when working with computers, networks, data, and fi les.
Syngress Media® and Syngress® are registered trademarks of Elsevier, Inc. Brands and product names mentioned in this book are trademarks or service marks of their respective companies.
KEY SERIAL NUMBER
The Real MCTS/MCITP Exam 70-620 Prep Kit
Copyright © 2008 by Elsevier, Inc. All rights reserved. Printed in the United States of America. Except as permitted under the Copyright Act of 1976, no part of this publication may be reproduced or distributed in any form or by any means, or stored in a database or retrieval system, without the prior written permission of the publisher, with the exception that the program listings may be entered, stored, and executed in a computer system, but they may not be reproduced for publication. Printed in the United States of America
1 2 3 4 5 6 7 8 9 0 ISBN 13: 978-1-59749-233-1
Tony Piltzecker (CISSP, MCSE, CCNA, CCVP, Check Point CCSA, Citrix CCA), author and technical editor of Syngress Publishing’s MCSE Exam 70-296 Study Guide and DVD Training System and How to Cheat at Managing Microsoft Operations Manager 2005, is an independent consultant based in Boston, MA. Tony’s specialties include network security design, Microsoft operating system and applications architecture, and Cisco IP Telephony implementations. Tony’s background includes positions as Systems Practice Manager for Presidio Networked Solutions, IT Manager for SynQor Inc., Network Architect for Planning Systems, Inc., and Senior Networking Consultant with Integrated Information Systems. Along with his various certifi cations, Tony holds a bachelor’s degree in business administration. Tony currently resides in Leominster, MA, with his wife, Melanie, and his daughters, Kaitlyn and Noelle.
Contributing Authors
Ron Barrett (MCP, CCNA, Citrix CCA) is a technology professional/ author specializing in network infrastructure and emerging technologies. For the past nine years he has worked in various capacities for several major fi nancial fi rms and dot-coms. Ron has also worked as a technical author the last seven years while holding the post of IT director for a fi nancial services fi rm in Manhattan, NY. He also has been a member of CPAmerica for the past four years, holding the posts of vice-chairman and chairman of the Technology Executive Committee. Now turning his attention full-time to writing and technical education, he is currently developing training clips for ClipTraning.com. Ron is the coauthor of the newly released Administrator’s Guide to Microsoft Offi ce Servers 2007 (Sams, 2007).
“I would like to thank my wife, Alicia, and my children, Ronald and Emma, for all their support and patience.”
Kelly Brown is a CTT+ certifi ed Senior Computer Forensic Profes-sional at Computer Science Corporation with over 9 years’ experience in the information technology fi eld. Mr. Brown is an Instructor and Curriculum Developer at CSC and holds a Bachelor of Science Degree in Computer Networking. Prior to teaching, Mr. Brown worked as an information security professional employed by IBM in the Security, Privacy, and Wireless Division Federal Sector conducting network and database audits, reporting information assurance and compliance activi-ties, and conducting annual security awareness training. Mr. Brown has extensive fi eld experience as a Senior Systems Engineer responsible for the successful development, implementation, and administration of numerous companies’ networks in the private sector.
vii client security, content networking, and wireless. In addition to network design and engineering, Jan’s background includes extensive experience with open source applications and operating systems such as Linux and Windows. Jan has contributed to the following Syngress book titles either as a technical editor or author: Managing and Securing Cisco SWAN, Practical VoIP Security, How to Cheat at Securing a Wireless Network, Micro-soft Vista for IT Security Professionals, and How to Cheat at Microsoft Vista Administration.
In addition to his full-time position at MSN Communications, Jan runs a security portal, www.MakeSecure.com, where he dedicates his time to security awareness and consulting. Jan lives in Colorado, where he enjoys outdoor adventures such as hiking Colorado’s 14ner peaks.
Robert J. Shimonski (MCSE, etc) is an entrepreneur, a technology consultant, and a published author with over 20 years of experience in business and technology. Robert’s specialties include designing, deploy-ing, and managing networks, systems, virtualization, storage-based tech-nologies, and security analysis. Robert also has many years of diverse experience deploying and engineering mainframes and Linux- and Unix-based systems such as Red Hat and Sun Solaris. Robert has in-depth work-related experience with and deep practical knowledge of globally deployed Microsoft- and Cisco-based systems and stays current on the latest industry trends. Robert consults with business clients to help forge their designs, as well as to optimize their networks and keep them highly available, secure, and disaster free.
from Syngress publishing. Robert can be found online at www.shi-monski.com.
xvii This book’s primary goal is to help you prepare to take and pass Microsoft’s exam number 70-620, Confi guring Microsoft Windows Vista Client. Our secondary purpose in writing this book is to provide exam candidates with knowledge and skills that go beyond the minimum requirements for passing the exam, and help to prepare them to work in the real world of Microsoft computer operating systems.
What Is MCTS Exam 70-620?
Microsoft Certifi ed Technology Specialist (MCTS) Exam 70-620 is both a stand-alone test for those wishing to master Windows Vista client confi guration and a requirement for those pursuing certifi cation as a Microsoft Certifi ed Information Technology Professional (MCITP) for Windows Server 2008 or as a Customer or Enterprise Support Technician. Microsoft’s stated target audience consists of IT professionals with at least one year of work experience with Tier 1 or Tier 2 customer support in a variety of environments, including medium-sized or large companies.
Exam 70-620 covers the basics of installing, confi guring, maintaining, and troubleshooting Windows Vista Client, including security, connectivity, mobility, and Vista applications. The book includes the following task-oriented objectives:
■ Installing and Upgrading Windows Vista This includes identifying
hardware requirements, performing clean installations, upgrading to Vista from previous Windows versions, upgrading from one edition of
Windows Vista to another edition, troubleshooting installation issues, and installing and confi guring Vista drivers.
■ Confi guring and Troubleshooting Post-Installation System
Settings This includes troubleshooting post-installation confi guration issues, confi guring and troubleshooting Windows Aero, confi guring and troubleshooting parental controls, and confi guring Internet Explorer.
■ Confi guring Windows Security Features This includes confi guring
and troubleshooting user account control, confi guring Windows Defender, confi guring Dynamic Security for IE7, and confi guring security settings in Windows Firewall.
■ Confi guring Network Connectivity This includes confi guring
networking using the Network and Sharing Center, troubleshooting connectivity issues, and confi guring Remote Access.
■ Confi guring Applications Included with Windows Vista This
includes confi guring and troubleshooting media applications, confi guring Windows Mail, confi guring Windows Meeting Space, confi guring Windows Calendar, confi guring Windows Fax and Scan, and confi guring Windows Sidebar.
■ Maintaining and Optimizing Systems That Run Windows
Vista This includes troubleshooting performance issues, troubleshooting reliability issues using built-in diagnostic tools, confi guring Windows Update, and confi guring Data Protection.
Path to MCTS/MCITP/
MS Certifi ed Architect
Microsoft certifi cation is recognized throughout the IT industry as a way to demon-strate mastery of basic concepts and skills required to perform the tasks involved in implementing and maintaining Windows-based networks. The certifi cation program is constantly evaluated and improved, and the nature of information technology is changing rapidly. Consequently, requirements and specifi cations for certifi cation can also change rapidly. This book is based on the exam objectives as stated by Microsoft at the time of writing; however, Microsoft reserves the right to make changes to the objectives and to the exam itself at any time. Exam candidates should regularly visit the Certifi cation and Training Web site at www.microsoft.com/learning/mcp/ default.mspx for the most updated information on each Microsoft exam.
Microsoft currently offers three basic levels of certifi cation on the technology level, professional level, and architect level:
■ Technology Series This level of certifi cation is the most basic, and it
includes the Microsoft Certifi ed Technology Specialist (MCTS) certifi cation. The MCTS certifi cation is focused on one particular Microsoft technology. There are 19 MCTS exams at the time of this writing. Each MCTS certifi cation consists of one to three exams, does not include job-role skills, and will be retired when the technology is retired. Microsoft Certifi ed Technology Specialists will be profi cient in implementing, building, troubleshooting, and debugging a specifi c Microsoft technology.
■ Professional Series This is the second level of Microsoft certifi cation,
To achieve the Enterprise Administrator MCITP for Windows Server 2008, you must successfully complete four Technology Series exams and one Professional Series exam.
■ Architect Series This is the highest level of Microsoft certifi cation, and
it requires the candidate to have at least 10 years’ industry experience. Candidates must pass a rigorous review by a review board of existing architects, and they must work with an architect mentor for a period of time before taking the exam.
N
OTEThose who already hold the MCSA or MCSE in Windows 2003 can upgrade their certifi cations to MCITP Server Administrator by passing one upgrade exam and one Professional Series exam. Those who already hold the MCSA or MCSE in Windows 2003 can upgrade their certifi ca-tions to MCITP Enterprise Administrator by passing one upgrade exam, two Technology Series exams, and one Professional Series exam.
Prerequisites and Preparation
There are no mandatory prerequisites for taking Exam 70-620, although Microsoft recommends that you meet the target audience profi le described earlier.
Preparation for this exam should include the following:
■ Visit the Web site at www.microsoft.com/learning/exams/70-620.mspx
to review the updated exam objectives.
■ Work your way through this book, studying the material thoroughly
and marking any items you don’t understand.
■ Participate in Microsoft’s product-specifi c and training and certifi cation
newsgroups if you have specifi c questions that you still need answered.
■ Take one or more practice exams, such as the one included on the
Syngress/Elsevier certifi cation Web site at www.syngress.com/certifi cation.
Exam Day Experience
Taking the exam is a relatively straightforward process. Prometric testing centers administer the Microsoft 70-620 exam. You can register for, reschedule or cancel an exam through the Prometric Web site at www.register.prometric.com. You’ll fi nd listings of testing center locations on these sites. Accommodations are made for those with disabilities; contact the individual testing center for more information.
Exam price varies depending on the country in which you take the exam.
Exam Format
Exams are timed. At the end of the exam, you will fi nd out your score and whether you passed or failed. You will not be allowed to take any notes or other written materials with you into the exam room. You will be provided with a pencil and paper, however, for making notes during the exam or doing calculations.
In addition to the traditional multiple-choice questions and the select and drag, simulation, and case study questions, you might see some or all of the following types of questions:
■ Hot area questions, in which you are asked to select an element or
elements in a graphic to indicate the correct answer. You click an element to select or deselect it.
■ Active screen questions, in which you change elements in a dialog box
(for example, by dragging the appropriate text element into a text box or selecting an option button or checkbox in a dialog box).
■ Drag and drop questions, in which you arrange various elements in a
target area.
Test-Taking Tips
In this section, we provide some tips that other exam candidates have found useful in preparing for and actually taking the exam.
■ Exam preparation begins before exam day. Ensure that you know the
concepts and terms well and feel confi dent about each of the exam objec-tives. Many test-takers fi nd it helpful to make fl ash cards or review notes to study on the way to the testing center. A sheet listing acronyms and abbre-viations can be helpful, as the number of acronyms (and the similarity of different acronyms) when studying IT topics can be overwhelming. The process of writing the material down, rather than just reading it, will help to reinforce your knowledge.
■ Many test-takers fi nd it especially helpful to take practice exams that are
available on the Internet and with books such as this one. Taking the practice exams can help you become used to the computerized exam-taking experience, and the practice exams can also be used as a learning tool. The best practice tests include detailed explanations of why the correct answer is correct and why the incorrect answers are wrong.
■ When preparing and studying, you should try to identify the main
points of each objective section. Set aside enough time to focus on the material and lodge it into your memory. On the day of the exam, you should be at the point where you don’t have to learn any new facts or concepts, but need simply to review the information already learned.
■ The value of hands-on experience cannot be stressed enough. Exam
questions are based on test-writers’ experiences in the fi eld. Working with the products on a regular basis—whether in your job environment or in a test network that you’ve set up at home—will make you much more comfortable with these questions.
■ Know your own learning style and use study methods that take
Most of us can learn from all of these methods, but have a primary style that works best for us.
■ Although it may seem obvious, many exam-takers ignore the physical
aspects of exam preparation. You are likely to score better if you’ve had suffi cient sleep the night before the exam and if you are not hungry, thirsty, hot/cold or otherwise distracted by physical discomfort. Eat prior to going to the testing center (but don’t indulge in a huge meal that will leave you uncomfortable), stay away from alcohol for 24 hours prior to the test, and dress appropriately for the temperature in the testing center (if you don’t know how hot/cold the testing environment tends to be, you may want to wear light clothes with a sweater or jacket that can be taken off ).
■ Before you go to the testing center to take the exam, be sure to allow
time to arrive on time, take care of any physical needs, and step back to take a deep breath and relax. Try to arrive slightly early, but not so far in advance that you spend a lot of time worrying and getting nervous about the testing process. You may want to do a quick last-minute review of notes, but don’t try to “cram” everything the morning of the exam. Many test-takers fi nd it helpful to take a short walk or do a few calisthenics shortly before the exam to get oxygen fl owing to the brain.
■ Before beginning to answer questions, use the pencil and paper
pro-vided to you to write down terms, concepts, and other items that you think you may have diffi culty remembering as the exam goes on. Then you can refer back to these notes as you progress through the test. You won’t have to worry about forgetting the concepts and terms you have trouble with later in the exam.
■ Sometimes the information in a question will remind you of another
concept or term that you might need in a later question. Use your pen and paper to make note of this in case it comes up later on the exam.
■ It is often easier to discern the answer to scenario questions if you can
■ When appropriate, review the answers you weren’t sure of. However,
you should change your answer only if you’re sure that your original answer was incorrect. Experience has shown that more often than not, when test-takers start second-guessing their answers, they end up changing correct answers to the incorrect. Don’t “read into” the ques-tion (that is, don’t fi ll in or assume informaques-tion that isn’t there); this is a frequent cause of incorrect responses.
■ As you go through this book, pay special attention to the Exam
Warnings, as these highlight concepts that are likely to be tested. You may fi nd it useful to go through and copy these into a notebook (remembering that writing something down reinforces your ability to remember it) and/or go through and review the Exam Warnings in each chapter just prior to taking the exam.
■ Use as many little mnemonic tricks as possible to help you remember
facts and concepts. For example, to remember which of the two IPsec protocols (AH and ESP) encrypts data for confi dentiality, you can associate the “E” in encryption with the “E” in ESP.
Pedagogical Elements
In this book, you’ll fi nd a number of different types of sidebars and other elements designed to supplement the main text. These include the following:
■ Exam Warning These sidebars focus on specifi c elements on which
the reader needs to focus in order to pass the exam (for example, “Be sure you know the difference between symmetric and asymmetric encryption”).
■ Test Day Tip These sidebars are short tips that will help you in
■ Confi guring & Implementing These sidebars contain background
information that goes beyond what you need to know from the exam, but provide a “deep” foundation for understanding the concepts dis-cussed in the text.
■ New & Noteworthy These sidebars point out changes in Windows
Server 2008 from Windows Server 2003, as they will apply to readers taking the exam. These may be elements that users of Windows Server 2003 would be very familiar with that have changed signifi cantly in Windows Server 2008 or totally new features that they would not be familiar with at all.
■ Head of the Class These sidebars are discussions of concepts and
facts as they might be presented in the classroom, regarding issues and questions that most commonly are raised by students during study of a particular topic.
Each chapter of the book also includes hands-on exercises in planning and confi guring the features discussed. It is essential that you read through and, if possible, perform the steps of these exercises to familiarize yourself with the processes they cover.
Additional Resources
There are two other important exam preparation tools included with this study guide. One is the CD included in the back of this book. The other is the concept review test available from our Web site.
■ A CD that provides book content in multiple electronic
formats for exam-day review Review major concepts, test day tips, and exam warnings in PDF, PPT, MP3, and HTML formats. Here, you’ll cut through all of the noise to prepare you for exactly what to expect when you take the exam for the fi rst time. You will want to use this CD just before you head out to the testing center!
■ Web-based practice exams Just visit us at www.syngress.com/
1
Exam objectives in this chapter:
■ User Interface
■ Networking
■ Windows Imaging
■ Security
■ Search
Microsoft Vista:
An Overview
Exam objectives review:
˛ Summary of Exam Objectives ˛ Exam Objectives Fast Track
˛ Exam Objectives Frequently Asked Questions ˛ Self Test
˛ Self Test Quick Answer Key
Introduction
This chapter will introduce the primary features found in Microsoft Windows Vista, the latest Microsoft desktop operating system. Microsoft released Vista to the general public in early 2007, and today you can find it in many different systems and configurations, including laptops, desktops, tablets, and multimedia systems, among others.
Vista is Microsoft’s first major complete operating system redesign since Windows 95. Many components and features have been completely engineered from the ground up to work only with Vista. Although Microsoft isn’t known for its industry-leading innovations, it is very adept at monitoring the industry and identifying which technologies the IT community is accepting. Then it will either purchase companies for their technologies or engineer competing technologies into its base operating systems. You can find evidence of this throughout Vista.
In the past, Microsoft engineered operating systems that would allow vendors to easily create their own software that would function on several versions of the OS. This practice had many benefits as well as many drawbacks. For instance, it was beneficial in terms of compatibility, but a limitation in terms of security and reliability. As previously stated, Vista is an entirely new product. Therefore, vendors and software manufacturers will have to create new software that is capable of running on Vista. This completely new branch of operating system has allowed Microsoft to implement many needed features and security additions from the start.
User Interface
The user interface, also known as the UI or GUI, is the first obvious change the user will notice about Vista compared to other Windows versions. Microsoft has added many new features and enhanced existing ones to help you maneuver around the system and become more productive.
meet these requirements can still run Vista, but the visual experience will be reduced. Recommendations are lower for the Home Basic version because it doesn’t have the same visual options available as the other versions.
■ 1 GHz 32-bit (x86) or 64-bit (x64) processor
■ 1 GB of system memory
■ 40 GB hard drive with at least 15 GB of available space
■ Support for DirectX 9 graphics with:
■ WDDM driver
■ 128 MB of graphics memory (minimum)
■ Pixel Shader 2.0 in hardware
■ 32 bits per pixel
■ DVD-ROM drive
■ Audio output
■ Internet access
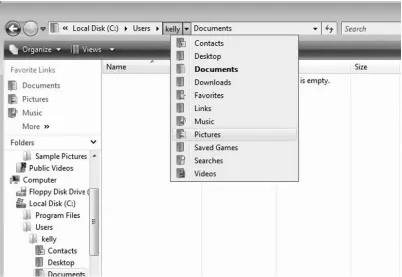
Microsoft has also improved Windows Explorer to provide Vista users with many more options and features for navigating the system. For instance, you can select any of the folders in a path to quickly navigate to other folders (as shown in Figure 1.1).
T
ESTD
AYT
IPWindows Explorer also can dynamically change available options depending on the type of template associated with a folder. For instance, a folder configured with the Pictures and Videos template will provide different options than a folder configured with the Music Icons template. Vista does this via automatic folder type discovery. Vista will attempt to detect what is the best folder type for the files types that are contained within the folder.
Figure 1.1 Navigating with Windows Explorer
EXERCISE 1.1
APPLYING A TEMPLATE TO A NEW FOLDER
This exercise will walk you through applying a Music Details template to a new folder. This allows you to create a music folder anywhere on the system, and can be used to enhance performance on systems with
multiple hard drives. This exercise will assume you have a secondary hard drive installed and configured as the D: drive.
1. Open Windows Explorer and navigate to the D: drive. 2. Click Organize | New Folder.
3. Provide the new folder with a folder name—for example, New Music.
4. Highlight the new folder and click Organize | Properties. 5. Click the Customize tab.
6. From the drop-down menu under “What kind of folder do you want?” select Music Details.
7. Click OK to apply the setting and close the properties windows.
New Look/Feel
The user interface can utilize two different modes depending on the user’s hardware specs: Windows Vista Aero or Windows Vista Basic. Vista will attempt to configure
For instance, sometimes when a user sets his desired folder type, Vista will automatically attempt another discovery on the folder at a later time, and will reset the folder. You can disable automatic folder discovery to prevent this from happening, but you must edit the Registry to do so. Always use caution when editing the Registry because it’s possible to render the system useless.
the Aero Glass effects if the hardware meets the requirements. If the hardware does not meet the minimum required specs to run the Aero Glass effects, Vista will auto-matically scale back its visual effects to give the user the best visual experience possible for the hardware. This ability to scale back allows all users to receive the best user interface possible for their current hardware.
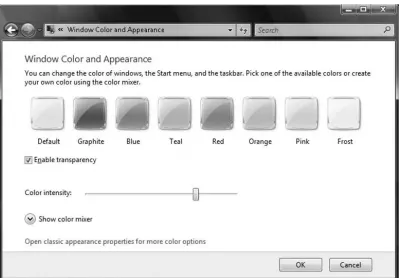
The main feature in Vista’s new look is its transparency. Items behind the windows will show through the outer edges of the windows. Figure 1.2 shows the Window Color and Appearance window. You can easily change these options to meet your preference for visual effects.
Microsoft has changed each component within Vista to match this overall look. Things such as buttons, radio buttons, wizards, task dialogs, the Control Panel, icons, fonts, and user notifications have been synced to give the same overall user experience.
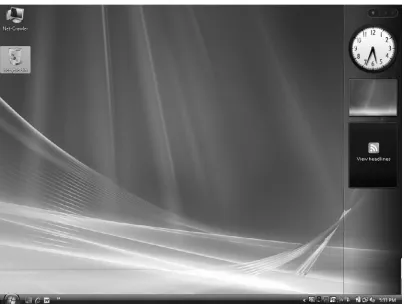
One of the primary new additions to Vista is its sidebar, shown in Figure 1.3, which you can customize to hold whatever gadgets you require. The sidebar is located on the right side of the desktop. Many different gadgets have customizable settings and configurations. You can download new gadgets and install them directly from the Microsoft Web page.
T
ESTD
AYT
IPUse the exam to take the exam. Many topics are covered in each exam. Therefore, it’s not uncommon for a question to have an answer to a question written in the scenario of another question.
User Access Control
User Access Control (UAC) is a new feature in Vista that is aimed at helping to improve security at the desktop level. In previous versions of Windows, local users were added to the local Administrators group. This allowed users to change system settings and install software. The UAC has been implemented by default in Vista. This allows users to run with fewer rights to the system, while also being given the option to override those defaults to allow administrative functions to run on the system.
To help improve compatibility with applications that haven’t been updated with UAC-compatible components, Vista provides the option to run applications as an administrator. To run an application as an administrator, you right-click the applica-tion and then you select Run as Administrator. This is necessary because even when you log on to Vista with an administrator account with UAC enabled, the account is actually running with the same security access rights as a standard user. In previous versions of Windows, the philosophy was that all users were admin-istrators, and software vendors manufactured software that required administrative privileges even if they weren’t conducting any administrative functions. The UAC component is forcing a much needed change in the thought process of many ven-dors by making them update their software to function correctly with the least level of rights necessary.
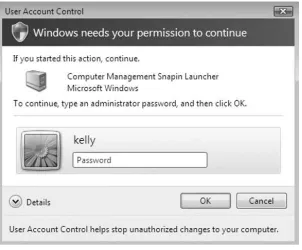
Vista with UAC enabled (the default) responds differently if the logged-on user is an administrator than it does if the logged-on user is a standard user. This is because when you log on to the system with an administrative account, you are actually receiving two different Security Identifiers (SIDs): one with full administra-tive rights and the other with standard user access. Therefore, when an administraadministra-tive task needs to take place, a user logged on with a standard account will have to provide the username and password of an administrator account to complete the task. While logged on under an administrator account, the user only needs to pro-vide consent to pass along the administrator SID for the task to complete. Microsoft still recommends using the more secure method of running Windows primarily with a standard user account.
When you are running Vista with an administrative account with UAC enabled, the elevation component is referred to as the consent prompt (see Figure 1.5). This allows members of the local Administrators group to perform administrative tasks by providing approval for those tasks.
Figure 1.4 The Credential Prompt
Networking
As with nearly every current operating system today, networking capability is essentially a requirement versus a marketable feature. Vista supports the latest in networking technology that provides useful features not found in previous versions of Windows.
Many businesses need to collaborate to be productive. In the past, businesses were required to set up and install expensive systems (such as Microsoft Live Meeting) to accomplish any type of meeting collaboration, or store files on a network-accessible share or use USB thumb drives to share files. To overcome these limitations, Vista offers a feature called Windows Meeting Space, which allows you to create a meeting on Vista at any time that other people can join. This makes it simple to share files and ideas with others throughout the organi-zation’s network, at local hotspots, or even in an ad hoc wireless network. You can use Vista Home Basic Edition to join a meeting, but you can’t use it to create a new meeting.
You can use the Windows Meeting Space peer-to-peer application to share files, programs, and even the entire desktop with up to nine other workstations. Each meeting participant can share files by adding them to the meeting as handouts. As these files are edited, changes are replicated to all users in the meeting. Once the final version of the file is completed, everyone can save a copy to his or her local hard drive. The moderator of the meeting can even delegate control over his or her machine to allow others to take control and make changes, while the other parti-cipants watch from their own screens.
E
XAMW
ARNINGEXERCISE 1.2
C
REATING AW
IRELESSAD HOC MEETING SPACE MEETING
We have discussed some of the primary benefits to using Windows Meeting Space. One of the nice features of Meeting Space is the ability to easily create a wireless ad hoc meeting for others to join. This is a nice added benefit because you can set up a meeting anywhere, without depending on any other networking technologies (although all members joining the wireless ad hoc meeting will need a wireless network device).
To set up a meeting that other wireless-capable Vista users can join, follow these steps:
1. Click Start Menu | All Programs | Windows Meeting Space. The screen shown in Figure 1.6 will be displayed, and Meeting Space will automatically begin to search for available meetings. Automatically searching for available meetings makes it much easier for other people to find and join your meeting.
2. Click Start a new Meeting. Then type in the desired meeting name and a strong password for the new meeting.
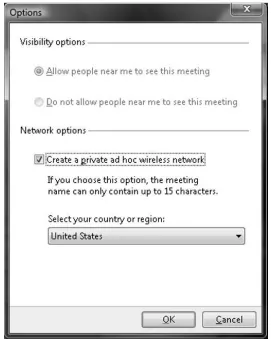
3. Click the Options button to display the screen shown in Figure 1.7. Under Network options, click Create a private
ad hoc wireless network, verify the country or region, and then click OK.
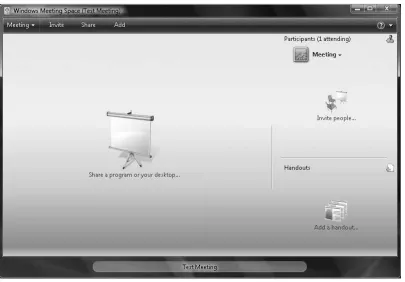
5. Now the meeting will have been created and a screen similar to the one shown in Figure 1.9 will be displayed. From this area, you can share an application or the entire desktop, invite others to the meeting, and add handouts to the meeting.
Figure 1.8 Creating a Meeting
6. To share the entire screen, click Share a program or your desktop. A confirmation window will be displayed (see Figure 1.10). Click OK to continue.
Figure 1.10 The Confirmation Window
7. The next window will allow you to select what you want to share with others in the meeting (see Figure 1.11). Highlight Desktop and click Share. This may cause the background to go black to help increase performance, and the screen to flicker. This is normal and should be expected.
8. Once your entire desktop is shared for others to view, your screen should look similar to the one shown in Figure 1.12. At this point, you have the option to allow others to take control of your desktop and make changes.
Figure 1.12 Sharing a Desktop
IPv6
The next-generation Transmission Control Protocol/Internet Protocol
(TCP/IP) suite, IPv6, overcomes many of the pitfalls of IPv4 and has the following enhancements:
■ Large address space IPv4 addresses are 32-bit, but IPv6 uses a 128-bit
address space to provide a massive increase in available addresses. IPv6 has 340,282,366,920,938,463,463,374,607,431,768,211,456 (3.4 × 1038) avail-able IP addresses that are globally routavail-able.
■ Extension headers IPv6 has streamlined headers that support hierarchical
routing infrastructures and provide faster Internet routing than IPv4.
■ Stateless configuration IPv6 has the built-in ability to
auto-configure network settings. This is not to be confused with IPv4’s Automatic Private IP Addressing (APIPA). APIPA uses only a specific range of
addresses and doesn’t provide any routable information (subnet mask/ gateway). IPv6 is able to get this information from a router on the network or from a Dynamic Host Configuration Protocol (DHCP) v6 service.
■ Enhanced security The standards of IPv6 provide protection against
address and port scans as well as higher security by supporting Internet Protocol Security (IPSec) for protecting network traffic with encryption.
When IPv4 and IPv6 are both enabled and configured, IPv6 is the preferred TCP/IP suite. This is important to note because this means that when making a network query, the next-generation TCP/IP stack will try to communicate first and then fall back to IPv4 if it fails. The IPv6 preference allows applications that are IPv6-enabled to take advantage of the features and benefits of IPv6.
EXERCISE 1.3
CONFIGURING IPV6 IN VISTA
This exercise will walk you through manually configuring IPv6 on a Vista machine using the GUI.
The screen shown in Figure 1.14 will be displayed. This screen will allow you to manually configure all IPv6 settings for this network connection. Multiple IPv6 addresses, gateways, and DNS settings can be configured on each network device.
4. Click Organize | Properties.
5. Highlight Internet Protocol Version 6 (TCP/IPv6) and click Properties (see Figure 1.13).
Figure 1.14 TCP/IPv6 Properties
Wireless Improvements
In the past, it was thought that one of the steps in securing a wireless network was to configure the wireless access point (WAP) to not broadcast the wireless network Service Set Identifier (SSID). The reasoning behind this idea was that if a network was hidden, it would be harder to find and exploit. This is a common misconception, and Microsoft recommends not using this method because other software tools can easily be used to discover all necessary information about a “hidden” access point anyway. Also, the clients that are configured to connect to the non-broadcasting access point are much more vulnerable. This is because for a client to connect to a non-broadcasting (hidden) WAP, it must search for the SSID by broadcasting the network name and other configuration information. Therefore, broadcasting the SSID is actually more secure than not broadcasting it. The major risk in this scenario is that an attacker could set up a workstation to pretend to be the WAP to which the client is trying to connect. Once the victim in connected to the attacker, the attacker would serve as a proxy by sending and receiving data that is requested from the victim system. This would make it nearly impossible for the victim to know that he or she is even connected to the attacker. Then the attacker could capture all unencrypted data passing through the system: Web pages, pass-words, e-mails, IM chats, and so on.
Microsoft has responded to this threat by changing the way Vista finds and con-nects to wireless networks. It designed Vista to be as passive as possible. This means Vista prevents any information from being broadcast that doesn’t specifically need to be to function effectively.
Another important option is “Connect automatically when this network is in range”. Because you can configure Vista not to automatically connect to the network when in range, Vista will not send out probe requests searching for the nonbroadcast access point. Therefore, Vista’s wireless auto-configuration will send probe requests only for access points that are configured with both options: connect automatically and nonbroadcast. This greatly reduces the potential for valuable information to be disclosed to possible attackers.
The next major improvement is that Vista will never automatically connect to an unencrypted network. Each time Vista is to be connected to an unsecured network, you must manually select the unsecured network, and you will be prompted with the dialog box shown in Figure 1.17, alerting you of the security risks associated with connecting to that particular wireless network. Each time you want to connect to the unsecured wireless network, you will have to accept the risk and click Connect Anyway to make the connection.
Figure 1.16 Connecting to a Network
In a domain environment, it is possible for the administrator to push out wire-less policy configurations to the workstations using Group Policies. These policies contain settings for the SSID, whether the WAP is set to broadcast, security con-figurations, and more. It is much easier for administrators to utilize Group Policies than to configure each workstation individually.
Windows Imaging
Deploying a new operating system can be a daunting task for many administra-tors. The complexity of creating, managing, and testing individual images for each deployment platform can drastically add to the time and cost of deploying the new
Improved Deployment
Vista’s major goal was to vastly reduce the required number of images and to better assist in maintaining those images. To help with this, Microsoft modularized Vista to make it easier to customize and deploy by basing the installation on a file-based disk imaging format called Windows Imaging Format (WIM) as well as making deployment enhancements to the core operating system.
Vista has been designed to be more modular than previous systems. Even the English language is considered an optional component separated from the core operating system. This prevents the need for individual images for each language that may be required for global corporations, thus vastly lowering the cost. This modular method also allows for easier additions of device drivers, service packs, and updates. Also, it makes it easier to enable optional Windows components. The greater reliability is enhanced because making changes to certain modules won’t affect or interfere with the other modules.
The new WIM is another great improvement and provides many benefits to administrators. The new image is hardware–independent, so organizations can use only one image for many different hardware requirements. Another great benefit is that this file format can be mounted and edited using Windows Explorer to add, change, and edit files and folders from within the image. Also, the images can be serviced offline for adding and removing optional components, drivers, and updates without the need to create a whole new image. These improvements greatly reduce the time necessary to create and manage images that are to be used to deploy Vista.
Configuring & Implementing…
Imaging Vista 32-Bit and 64-Bit Operating Systems
Even though WIM can support many different hardware requirements in a single image file, the 32-bit and 64-bit images are not compatible with each other. Therefore, the two different platforms will require separate image files.
compared to previous methods that required the use of multiple files for unattended installs. This also provides the ability to automate more of the desktop and deploy-ment process.
Vista is designed to perform faster installations than previous versions of Windows by using a new image-based operating system setup. Another improvement is the upgrade process. When possible, it’s a best practice to perform a completely new installation versus and an upgrade procedure. However, Vista provides a cleaner upgrade by basically performing a new full operating system installation that is followed with a migration of user settings, applications, and documents.
ImageX is the new Vista tool used to create and manage actual WIM files. ImageX is a command-line utility that is used to mount the images for offline editing, pre-venting the need to create a new image from the source system. The image file can be shared from a distribution point and either invoked by the user or pushed to the desktop by administrators.
Vista uses the Windows System Image Manager to make customizing and auto-mating the installation process much easier and more reliable. Users can add, delete, or modify optional components including service packs, updates, device drivers, and languages in an already-existing image file, simply by creating or editing the XML-based unattended configuration file.
Now that we have discussed some of the tools used to create and customized the installation process, let’s look at some technologies that you can use to deploy the Vista desktop operating system:
■ Multiboot options You have many boot options, such as CD/DVD, hard
disk, and the Preboot eXecution Environment (PXE) boot.
■ Secure remote deployment options Vista can be remotely installed
onto a desktop.
■ Windows Deployment Services (WDS) WDS is the new name
for the updated version of the Microsoft Remote Installation Service (RIS) and will provide for the management, storage, and deployment of the images. This method uses the PXE boot option.
■ The upgrade This method will upgrade to the Vista desktop while
never have the time to do, so we just put it off until later. Backing up data never seems important until your life depends on it. Only then do you realize that the last time you successfully completed a backup was when you first got your shiny new system.
Microsoft has tried to alleviate some of the pain of doing backups by making the process much less complicated and very streamlined. Microsoft provides a few ways to help you safeguard your data and Complete PC Backup is one of the main features. This backup solution is available in the Business, Enterprise, and Ultimate versions of Vista. Figure 1.18 displays the Backup and Restore Center found in the Control Panel, which is where the Complete PC Backup can be created or restored.
T
ESTD
AYT
IPDon’t waste time on questions to which you do not know the answers. Use the mark option and come back to such questions after you’ve completed the exam. If you still don’t have any idea how to answer them, simply give it your best guess. Never leave any questions blank.
You can use Complete PC Backup to back up the whole system in case of a hardware failure. This backup method includes all user settings, installed applica-tions, Registry settings, files, and so on. When a backup is performed, the data will be stored in a virtual hard disk (.vhd) image to the destination drive. You can then save the backup to CDs/DVDs, attached storage (external USB hard drives), and network shares.
The first time Complete PC Backup runs, it does a full backup. Every backup after that is differential. This means all backups after the first backup will back up only the changes that have been made to data since the previous backup, making backups much faster. This doesn’t mean that any information from the first backup is lost, because it’s still backing up all the data on the system. You can still restore data from the first full backup or any other backup. This is because Microsoft uses the Volume Shadow Copy Service to complete PC backups. The data that changed will be backed up and the delta data will be moved to the shadow copy storage area.
Great effort has also gone into restoring data. You can easily restore data by using the Windows Recovery Environment (Windows RE), which you can find by booting to the installation CD.
Vista’s Complete PC Backup does not back up Microsoft Outlook .ost files in the backup image. Sometimes restoring .ost files can be problematic. Because you can regenerate .ost files from the Exchange server, Microsoft decided to omit this file type from the Complete PC Backup process.
Security
Security is always a huge issue for individuals, small companies, and large organiza-tions. With new threats and vulnerabilities constantly changing, Microsoft has made many improvements to Vista’s security features to help overcome these concerns.
BitLocker
Enterprise and Ultimate versions of Vista. This new security feature in Vista goes a long way toward helping users and organizations protect their data.
You can set up BitLocker in the following configurations:
■ TPM only In this configuration, only the hardware microchip is used to
protect the data stored on the drive. The Trusted Platform Module (TPM) stores the encryption key and verifies that there have been no changes to the hard drive.
■ TPM and USB flash drive In this configuration, the TPM will still
verify the validity of the hard drive, but in addition, part of the encryption key is stored on the USB flash drive. The USB flash drive is required each time the computer starts.
■ TPM and PIN This configuration is also a two-layer security approach.
After successful verification of the drive, you will be required to enter the correct PIN for the start process to continue.
The default configuration for BitLocker is to be used in conjunction with a TPM. The TPM is a hardware microchip embedded into the motherboard that is used to store the encryption keys. This protects the hard drive even if it has been removed from the computer and installed into another computer. You can also use BitLocker on systems that don’t have the TPM hardware manufactured on the motherboard. You can do this by changing the BitLocker’s default configurations with either a Group Policy or a script. When you use BitLocker without a TPM, you must store the key on a USB flash drive and insert the USB flash drive into the computer for the system to boot.
N
OTENew & Noteworthy…
BitLocker Vulnerabilities
BitLocker is a new security feature in Vista. As with all security technology, some people are working on creating vulnerabilities or ways around this security, so you must always be aware that new threats are coming out all the time. Therefore, BitLocker is just another technical challenge to many hackers in the world.
To use a BitLocker-enabled system, the key must be stored in RAM while the system is up and running. Universities have found that when a system is shut down, it’s possible to retrieve the key from RAM for up to several minutes, giving a hacker complete control over the entire system and all files stored on the drive. The main way to avoid this, of course, is to never leave a system unattended in an unsecured area in the first place. The next step is to completely shut down the system so that the RAM can be allowed to fully discharge.
When Vista is used in a domain environment, it is important for the domain administrators to be able to retrieve the information stored on a system in case of any emergency or other type of event. In a case where a user isn’t able to work or is asked to leave the company, the informa-tion on the hard drive still needs to be accessed and recoverable. Active Directory domains in Server 2003 and 2008 provide administrators with the safeguard to set up Group Policies and have the BitLocker key backed up and stored in Active Directory on the servers.
We will cover BitLocker in greater detail later in this book.
PatchGuard
Microsoft discourages vendors from making kernel-level changes in 32-bit systems, but does not programmatically prevent this. This is because 32-bit software has been around for a long time and is already fully entrenched in the market. Making this change to these systems would break many of the software packages in use today because of compatibility issues. The introduction of 64-bit systems provided Microsoft with an opportunity to introduce this new security feature with much less impact on the community.
Previously in 32-bit system, vendors would use these undocumented means to replace or extend the functionality of the kernel. This could potentially have a nega-tive effect on the system by reducing its reliability, performance, and stability. With the virus, Trojan, and malware communities always becoming more advanced in their techniques, this isn’t an optimal configuration for system security or reliability. By allowing the kernel to be updated only by its tested and approved code, Microsoft has greatly improved system security.
Some of the system structures PatchGuard prevents include the following:
■ Changing the system service tables
■ Changing the interrupt descriptor table (IDT)
■ Changing the global descriptor table (GDT)
■ Using kernel stacks not allowed by the kernel
■ Patching any part of the kernel
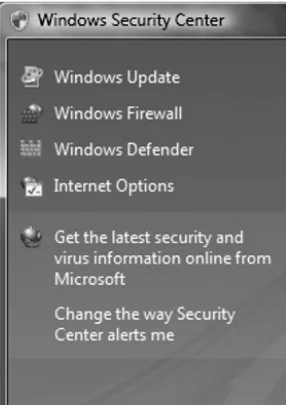
Security Center
The Windows Security Center in Vista puts some of the primary security settings into one easy-to-use and manage window. Figure 1.19 shows the Windows Security Center windows. The Windows Security Center can monitor third-party soft-ware and alert you when a security setting should be adjusted or if softsoft-ware is out-of-date.
Vista usability. You are no longer required to manually check the status in each software package.
The Windows Security Center is capable of monitoring the following components (see Figure 1.19):
■ Firewall settings
■ Vista Automatic Updates settings
■ Antivirus software status
■ Antispyware or malware protection
■ Internet Explorer 7 security settings
■ UAC settings
Figure 1.19 The Windows Security Center
The firewall is used to prevent network access to local ports on your system. The firewall settings built into Vista (see Figure 1.20) allow you to customize fire-wall rules to your needs or requirements. The Windows Security Center monitors the status and settings of the firewall and is capable of monitoring not only the Vista firewall but also third-party software firewalls. The Windows Security Center will notify you if there are any issues with your firewall that you may need to address.
Figure 1.20 The Vista Firewall Settings
EXERCISE 1.4
VERIFYING THAT THE FIREWALL
ALLOWS FILE AND PRINTER SHARING
is enabled in the Vista firewall configurations. This will allow others on the network access to these ports.
1. Open the Windows Security Center by navigating to Start | Control Panel | Security Center.
2. Click on Windows Firewall on the left-hand side of the screen. 3. In the next screen, click Change Settings.
4. Click on the Exceptions tab.
5. Search for File and Printer Sharing and verify that the item is checkmarked.
System and application updates are just another critical component to ensur-ing the security and reliability of any system. New vulnerabilities are constantly being discovered and released to the public. All applications from all vendors (Word, Adobe Acrobat, Mozilla Firefox, etc.) are affected by these security risks. Therefore, continuous monitoring of system and application updates is critical throughout the lifespan of a system.
In the older days of system maintenance, each patch or update had to be manu-ally downloaded and installed and many of these patches had to be installed in a certain order to be fully effective. Microsoft has designed the Windows Update Service to help take the manual work out of maintaining and updating a system, thus allowing anyone to be able to easily and effectively keep his or her system updated and protected from emerging threats.
The Windows Update Service can also monitor, download, and install updates for other common software packages. Therefore, it manages not only key system updates, but also applications such as Microsoft Office and Internet Explorer.
bet-patches and service packs in a testing environment before implementing them in a production systems.
The next option, “Check for updates but let me choose whether to download and install them”, is good for areas that may have less bandwidth (see Figure 1.21). Then you can see what’s available and choose whether to download and install them individually. The setting that is not recommended is “Never check for updates”. This option will fully disable the Windows Update Service.
Figure 1.21 Checking for Updates
Figure 1.22 shows that avast! antivirus software is installed, activated, and currently up-to-date. Figure 1.22 also shows the status of the Windows Defender spyware and malware protection.
Figure 1.22 Malware Protection
The “Other security settings” area provides information about the current secu-rity settings of Internet Explorer and the UAC, as shown in Figure 1.24. Selecting “Internet security settings” as displayed in Figure 1.24 will take you to the Security tab of the Internet Options for Internet Explorer. Here you can accept the default security setting or adjust the settings to your needs.
The Windows Security Center also lets you configure the way you are notified of any security issues. After clicking “Change the way Security Center alerts me”, as in Figure 1.25, you are taken to a screen that allows you to choose the way you prefer to be notified.
Figure 1.24 Other Security Settings
Figure 1.25 Security Notification Options
Digital Rights Management
Digital Rights Management (DRM) is a technology that media content providers can use to ensure that their media is protected. These providers can choose to add DRM protection to their media to help prevent their content from being used illegally.
Digital content providers can use Microsoft Windows Media Rights Manager to create content that is securely encrypted. When a customer purchases a file, he or she must also get the license that contains the key to unlock the file. If the user doesn’t have a valid license for the media, the user will be directed to a site where he or she can purchase a valid license. This doesn’t prevent the content from being transferred, but it does prevent it from being utilized by unauthorized users.
Content providers can not only protect their content from being played but also set some rules regarding how the content can be used. Here are some of the restriction options that are available to these providers:
■ The number of times the content can be played (from one to unlimited)
■ The license start and expiration dates
■ Whether the content can be burned to a CD
■ The required security level of the software playing the media
DRM provides many benefits to content providers as well as their customers. The provider has a tool he or she can use to help fight against content piracy and illegal distribution. The user is assured that the content is in its original form, as intended by the provider, and has the satisfaction of knowing that he or she has legally purchased the media.
New & Noteworthy…
Companies Dropping DRM
Many digital content management companies have began to offer DRM-free content because consumers have made it clear that they simply prefer unprotected media over protected media.
Search
Your computer system can be an excellent tool to accomplish many personal and business tasks—anything from creating and editing images and video for pleasure to creating spreadsheets or custom applications for business purposes. Over time, a system naturally stores all these valuable files and resources. But how much value does a file hold if it can’t be found? Microsoft has added a very valuable user feature in Vista: the dynamic search capabilities called Instant Search.
menu will display results that are found in the Start menu with a higher priority, shown at the top of the list, and then will expand to other files as the search criteria entered are more specific.
Figure 1.27 Vista’s Instant Search
Figure 1.29 shows Instant Search in Windows Explorer. This search capability allows you to search for documents within the current folder quickly and easily. It’s important to note that the searches are based on the contents in the file. For example, if a Word document or text file also contains the search criteria in the
After you click Start | Search, the next screen shown in Figure 1.30 will be displayed. This allows you to edit your search based on more advanced criteria and other options. You can also get to these advanced options in any other Windows Explorer window by starting a search in the Instant Search bar; simply click Search Tools | Select Search Pane. The Search pane is the toolbar that holds the
Advanced Search button. Then click the down arrow to display the advanced search options. You can choose to quickly search indexed locations (discussed later in this section), or select a custom location or any other available options.
Figure 1.29 Windows Explorer’s Instant Search
Vista also makes it easy to add other information to a file to help find impor-tant files. Depending on the type of file, the available editable options will change. All file types will allow you to add tags, as shown in Figure 1.31. To add this infor-mation, or to edit any other inforinfor-mation, simply highlight the file and make the desired changes to the tag. Once the information is entered, click the Save button to commit the changes to the file. If you want to make the same change to multiple files, simply highlight all the files you want to change, make the change, and then click Save. This makes it easy to change information on multiple files in one quick and easy step.
Figure 1.31 Vista’s Available Editable Options
We’ve taken a look at some of the options available for searching files, folders, and applications in Vista. Now let’s take a look at what makes all of this possible. This key ingredient in Vista is its use of indexing. Indexing is what makes all of these searches able to provide fast and reliable results. Indexing not only saves the file-names and locations, but also indexes the contents within all the files in the folder selected to be indexed. To open the indexing options go to Start | Control Panel | Indexing Options. Figure 1.32 will be displayed, showing the default indexed locations.
T
ESTD
AYT
IPBe cautious when changing your answers. Statistically, your first answer is most likely to be the correct answer.
EXERCISE 1.5
R
EBUILDING THES
EARCHI
NDEX INW
INDOWSV
ISTAIndexing is a great way to speed up local searches. It also lets you quickly find files based on the files’ contents. Over time, the speed of the
searches may naturally degrade or the results may become less accurate. To solve these problems it may be necessary to regenerate the search index. This will cause the data currently in the index to be flushed out and a new, fresh index will be populated. This may not be a mandatory task, but is a good idea for regular PC maintenance. Depending on many factors, system performance may be degraded during index regeneration. Therefore, you may want to start this process at the end of the day so that it can run while the system isn’t in use.
1. Navigate to Start | Control Panel | Indexing Options. Figure 1.32 will be displayed.
2. Click the Advanced tab and then click Continue to any User Access Control windows. The next screen will be displayed (see Figure 1.33).
3. Click the Rebuild button.
4. A confirmation pop-up box will be displayed (see Figure 1.34). Carefully read this message and click OK when finished. The index rebuilding process will be started and will run in the background. It’s possible to continue working while the index is running, but performance may be degraded.
Summary of Exam Objectives
Windows Vista is the latest of the Microsoft desktop operating systems, and it fea-tures many new and useful tools not found in any previous version of Windows. The hardware requirements to take full advantage of the features built into Vista have increased like never before. Many systems in use today will simply not be able to utilize all of the features or will need to be upgraded.
Vista has improved the functionality found in Windows Explorer to help users maneuver folders and find files much more quickly and easily. The automatic index-ing of files and folders has made it possible for results to be dynamically displayed as the user inputs the search criteria. Vista also automatically determines what tem-plates to use for each folder by assessing what type of files are contained within each folder. This makes it possible for Windows Explorer to dynamically change its buttons depending on the content in the folder. This means that a folder with images will have different options than a folder that holds videos.
Vista provides two different visual modes, which the system determines auto-matically based on its hardware capabilities. The available modes are Vista Aero and Vista Standard. This allows systems that have older hardware to be able to still load and use Vista. At the same time, it allows systems with more powerful hardware to utilize the more advanced Aero effects. Both modes provide a customizable sidebar that offers many features directly on the desktop.
Vista has introduced User Access Controls (UAC) to improve desktop security. The UAC has helped to increase overall security by forcing the way developers integrate software into the system. Vendors need to create software that will run with only the level of access rights that are required to successfully accomplish their tasks. Another great security improvement is that even administrator accounts run using standard user rights by providing the account with an administrative key and a standard user key. When an administrative task needs to be performed under an administrator account, the UAC notifies the user with a pop-up message requesting the user to allow the use of the administrative key to accomplish the task. When a standard user requests an administrative task, the user must provide credentials for an administrator account before the task will be completed.