MADIS SARALITA - 5112100038 Keamanan Informasi dan Jaringan (C)
PART 1: SYMMETRIC CIPHERS
CHAPTER 4
BASIC CONCEPTS IN NUMBER THEORY AND FINITE FIELDS
CHAPTER 5
ADVANCED ENCRYPTION STANDARD
CHAPTER 6
BLOCK CIPHER OPERATION
CHAPTER 7
CHAPTER 4
BASIC CONCEPTS IN NUMBER THEORY AND FINITE FIELDS
4.1 DIVISIBILITY AND THE DIVISION ALGORITHM
DIVISIBILITY
Rules of divisibility for integers If a|1, then a = ± 1.
THE DIVISION ALGORIT HM
a = qn + r where
0 ≤ r < n;
4.2 THE EUCLIDEAN ALGORITHM
Relatively prime : If the common factor is 1.
GREATEST COMMON DIVI SOR
In general, gcd(a, b) = gcd(|a|, |b|).
Example : gcd(48, 36) = gcd (|48|, |36|) = 12
If relatively prime, gcd(a, b) = 1. Example : 8 and 15
The positive divisor of
So, the only integer of both is 1.
FINDING THE GREATEST COMMON DIVISOR
Example : gcd(30, 24)
PROPERTIES OF CONGRU ENCES
Rules :
a ≡ b (mod n) if n|(a – b)
a ≡ b (mod n) implies b ≡ a (mod n)
a ≡ b (mod n) and b ≡ c (mod n) imply a ≡ c (mod n) MODULAR ARITHMETIC O PERATIONS
Rules :
[(a mod n) + (b mod n)] mod n = (a + b) mod n
[(a mod n) - (b mod n)] mod n = (a - b) mod n
POPERTIES OF MO DULAR ARITHMETIC
if (a + b) ≡ (a + c) (mod n) then b ≡ c (mod n)
if (a * b) ≡ (a * c) (mod n) then b ≡ c (mod n) if a is relatively prime to n
EUCLIDEAN ALGORITHM REVISITED
gcd(a, b) = gcd(b, a mod b)
THE EXTENDED EUCLIDE AN ALGORITHM
ax + by = d = gcd(a, b)
ri = ri-2 - ri-1 qi
4.4 GROUPS, RINGS, AND FIELDS
GROUPS
A group is denoted by G
Using multiplication operation that make a pair of each order (a, b) in G.
RINGS
A ring is denoted by R
Using addition and multiplication operation.
There are multiplicative identity and no zero divisors.
FIELD
A field is denoted by F
Same with rings, using addition and multiplication operation. There are multiplicative inverse for each a in f, except 0.
4.5 FINITE FIELDS OF THE FORM GF(P)
GF IS GALOIS FIELD
Finite Fields of Order p
if (a * b) ≡ (a * c)(mod p) then b ≡ c (mod p)
Rules :
GF(p) consists of p elements.
Over the set, binary operation of addition and multiplcation are defined.
We can do addition, subtraction, multiplication, and division without leaving the set. If elemet is not 0, it will have a multiplicative inverse.
4.6 POLYNOMIAL ARITHMETIC
ORDINARY POLYNOMIAL ARITHMETIC
The variable is not evaluated
Polynomial is allowed if the coefficients are elements of a field.
POLYNOMIAL FORM
POLYNOMIAL ARITHMETI C WITH COEFFICIENTS IN ZP
Polynomial addition, subtraction, multiplication, and division are allowed
FINDING THE GREATEST COMMON DIVISOR
We can find the greatest common divisor of two polynomials with Euclidean algorithm if coeffisients are elements of field.
4.7 FINITE FIELDS OF THE FORM GF(2
N)
GF(2n) consists of 2n elements
Over the set, binary operation of addition and multiplcation are defined.
We can do addition, subtraction, multiplication, and division without leaving the set. If elemet is not 0, it will have a multiplicative inverse.
The elements of GF(2n) can be defined as the set of all polynomials of degree n-1 or less with binary coefficients.
SOURCE :
W. Stallings, Cryptography And Network Security Principles And Practice Fifth Edition, New York: Prentice Hall, 2011.
CHAPTER 5
ADVANCED ENCRYPTION STANDARD
5.1 FINITE FIELD ARITHMETIC
Performed on 8-bit bytes.
Arithmetic operations of addition, multiplication, and division are finished with GF(2n) Using ordinary rules of polynomial arithmetic.
Using XOR operation.
Polynomial m(x) is irreducible if and only if m(x) cannot be expressed as a product of two polynomials which both of degree is lower than m(x).
5.2 AES STRUCTURE
GENERAL STRUCTURE
State, defines the current condition (state) of the block. That is the block of bytes that are currently being worked on.
The state starts off being equal to the block, however it changes as each round of the algorithms executes. Plainly said this is the block in progress.
DETAILED STRUCTURE
AES is not a Feistel Structure. AES is symmetric key block cipher. The structure is quite simple.
It uses a fixed 128-bit block cipher and three key lengths supported by AES as this was an NIST design requirement.
The number of internal rounds of the cipher is a function of the key length according to this table.
Key Lengths Rounds = Nr
128 bit 10
192 bit 12
256 bit 14
AES processes the entire block data as a single matrix using substitutions and permutation. To substitute bytes, AES uses S-box.
Shift the rows use simple permutation.
Mix columns use substitution that the aritmetic over GF(2n). Add round key use simple bitwise XOR
The key is just used in AddRoundKey. Easily reversible in each stage.
The decryption algorithmm use expanded key in reverse order. Same state in encryption and decryption.
The final round consists of three stages.
AES is an iterated symmetric block cipher, which means that: o AES works by repeating the same defined steps multiple times.
o AES is a secret key encryption algorithm.
5.3 AES TRANSFORMATI ON FUNCTIONS
SUBSTITUTE BYTES TRA NSFORMATION
Forward substitute byte transformation is called with SubBytes.
The process in forward and inverse transformations, state is mapped into a new byte.
It is a non linear byte Substitution, with the help of a substation table (s-box), which is generated by multiplicative inverse and affine transformation.
S-Box
SHIFT ROWS TRANSFORMATION
Forward shift row transformation is called with ShiftRows. Here, first row of state is not changed.
The next row of state will shift to the left circularly.
The inverse shift row transformation is called with InvShiftRows.
Here, for each the last three rows, the rows will shift circularly in the opposite direction.
It is simple byte transpositions, the bytes in the last three rows of the state, depending upon the row location, are cyclically shifted; the offset of the left shift varies from zero to three bytes.
Shift Row
MIXCOLUMNS TRANSFORM ATION
The forward mix column transformation is called with MixColumns.
The process in forward and inverse transformations, each column is operated individually. Each byte of column is mapped into new value.
Rules for MixColumn transformation on a single column
The inverse mix column transformation is called with InvMixColumns
This round is equivalent to a matrix multiplication of each columns of the states.
A fix matrix is multiplied to each column vector. In his operation the bytes are taken as polynomials rather than numbers.
Mix Column
In standard, MixColumn is defined by ordering each column of state to be four-term-polynomial with coefficient in GF(28).
ADDROUNDKEY TRANSFOR MATION
The forward add round key transformation is called with AddRoundKey. Here, 128 bits of state are bitwise XORed with 128 bits of the round key. The first matrix is state.
The second matrix is round key.
The inverse add round key transformation is forward the round key transformation.
It is a simple XOR between the present state and the round key. This transformation is its own inverse. The encryption process consists of several steps. Initially an addroundkey operation is performed then a round function is applied to the data block (consisting of bytesub, shiftrows, mixcolumns and addroundkey transformation, respectively). This round operation is performed iteratively (Nr times) depending on the length of the key. The decryption operation has exactly the same sequence of transformations as the one in the encryption operation. The transformations Inv-Bytesub, the InvShiftrows, the InvMixcolumns, and the Addroundkey allow the form of the key schedules to be identical for encryption and decryption.
5.4 AES KEY EXPANSIO N
KEY EXPANSION ALGORI THM
The input is a four-word (16-byte) key.
This algorithm produces a linear array of 44 words (176 bytes). The key is copied into the first four words of the expanded key. In four words, remainder of the expanded key is filled at a time. Simple XOR is used in three out of four cases.
Prior to encryption or decryption the key must be expanded. The expanded key is used in the Add Round Key function.
Each time the Add Round Key function is called a different part of the expanded key is XORed against the state. In order for this to work the Expanded Key must be large enough so that it can provide key material for every time the Add Round Key function is executed. The Add Round Key function gets called for each round as well as one extra time at the beginning of the algorithm.
RATIONALE
There are some criteria that used by Rijndae developers to make the key algorithm will be resistant to known by cryptanalytic attacks. The criteria is the following below :
Calculations of many round-key bits is not enabled by the knowledge of the cipher key or round key. An invertible transformation.
Speed of processor. Usage of round constants.
Diffusion round keys from the cipher key differences.
5.5 AN AES EXAMPLE
Key: 0123456789abcdeffedcba9876543210
Plaintext: 0f1571c947d9e8590cb7add6af7f6798 Ciphertext: ff0b844a0853bf7c6934ab4364148fb9
AVALANCHE EFFECT
Avalanche effect is important characteristic for encryption algorithm. This property can be seen when changing one bit in plaintext and then watching the change in the outcome of at least half of the bits in the cipher text. One purpose for the avalanche effect is that by changing only one bit there is large change then it is harder to perform an analysis of cipher text, when trying to come up with an attack. First we start calculate avalanche effect for AES S-box.
Avalanche Effect in AES: Change in Plaintext
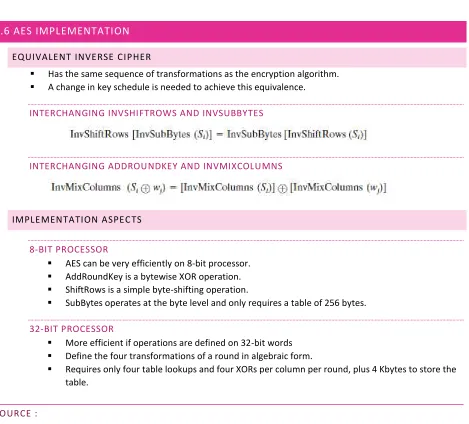
5.6 AES IMPLEMENTATION
EQUIVALENT INVERSE C IPHER
Has the same sequence of transformations as the encryption algorithm. A change in key schedule is needed to achieve this equivalence.
INTERCHANGING INVSHIFTROWS AND INVSUBBYTES
INTERCHANGING ADDROUNDKEY AND INVMIXCOLUMNS
IMPLEMENTATION ASPEC TS
8-BIT PROCESSOR
AES can be very efficiently on 8-bit processor. AddRoundKey is a bytewise XOR operation. ShiftRows is a simple byte-shifting operation.
SubBytes operates at the byte level and only requires a table of 256 bytes.
32-BIT PROCESSOR
More efficient if operations are defined on 32-bit words Define the four transformations of a round in algebraic form.
Requires only four table lookups and four XORs per column per round, plus 4 Kbytes to store the table.
SOURCE :
[1] W. Stallings, Cryptography And Network Security Principles And Practice Fifth Edition, New York: Prentice Hall, 2011.
[2] M. N. T. Amish Kumar, “Effective Implementation and Avalanche Effect Of AES,” International Journal of Security, Privacy and Trust Management (IJSPTM), vol. 1, pp. 3-4, 2012.
[3] E. K. Kavitha, “Performance Evaluation of Cryptographic Algorithms: AES and DES for Implementation of Secured Customer Relationship Management (CRM) System,” IOSR Journal of Computer Engineering (IOSRJCE), vol. 7, no. 4, pp. 1-7, 2012.
[4] A. Berent, “Advanced Encryption Standard by Example”.
[5] D. P. N. C. Jayant P. Bhoge, “Avalanche Effect of AES Algorithm,” (IJCSIT) International Journal of Computer Science and Information Technologies, vol. 5, no. 3, pp. 3101-3103, 2014.
CHAPTER 6
BLOCK CIPHER OPERATION
6.1 MULTIPLE ENCRYPTION AND TRIPLE DES
DOUBLE DES
P = Plaintext
K1, K2 = Keys C = Ciphertext
TRIPLE DES WITH TWO KEYS
Triple encryption that use three keys. Encrypt – decrypt – encrypt (EDE) sequence :
3DES single key, to decrypt data encrypted by users of the older single DES.
TRIPLE DES WITH THRE E KEYS
3DES three key, has an effective key length of 168 bits
6.2 ELECTRONIC CODE BOOK
Electronic code book (ECB) is a simplest mode. Here, one block handles plaintext at a time.
Using the same key while encrypting each block of plaintext. There is a unique ciphertext in every b-block of plaintext.
In decryption, one block will be performed at a time and using the same key. Each block encrypted independently.
Identical plaintexts encrypted similarly. No chaining, no error propagation.
Does not hide data patterns, unsuitable for long messages. Example: pixel map using ECB
Susceptible to replay attacks.
Example: a wired transfer transaction can be replayed by resending the original message) Define ECB mode
6.3 CIPHER BLOCK CHAINING MODE
Input to the encryption algorithm is the XOR of the current plaintext block. Each block use the same key.
Input to the encryption function no fixed relationship for each plaintext block. Allows random access to ciphertext.
Decryption is parallelizable.
Plaintext block xj requires ciphertext blocks cj and cj-1
Identical messages: changing the first plaintext block results in different ciphertext.
Chaining: Ciphertext block cj depends on xj and all preceding plaintext blocks (dependency contained in c j-1).
Error propagation: Single bit error on cj may flip the corresponding bit on xj+1, but changes xj significantly. Initialization Vector need not be secret, but its integrity should be protected.
Define CBC mode
CBC is an appropriate mode for encrypting messages of length greater than b bits because the chaining mechanism.
CBC mode can be used for authentucation.
6.4 CIPHER FEEDBACK MODE
To convert a block cipher into a stream cipher, we can use : Cipher feedback (CFB) mode
Output feedback (OFB) mode Counter (CTR) mode
Allows random access to ciphertext. Decryption is parallelizable.
Plaintext block xj requires ciphertext blocks cj and cj-1 Identical messages: as in CBC.
Chaining: Similar to CBC.
Error propagation: Single bit error on cj may flip the corresponding bit on xj, but changes xj+1 significantly. Initialization Vector need not be secret (XORed with x1).
Define CFB mode
6.5 OUTPUT FEEDBACK MODE
Identical messages: same as CBC No chaining dependencies
Error propagation: Single bit error on cj may only affect the corresponding bit of xj
Initialization Vector need not be secret, but should be changed if a previously used key is to be used again. Define OFB mode
6.6 COUNTER MODE
Preprocessing possible (inc/decrement and enc/decrypt counter). Allows random access.
Both encryption & decryption are parallelizable. Encrypted counter is sufficient to enc/decrypt.
Identical messages: changing nonce results in different ciphertext. No chaining dependencies.
No error propagation.
Nonce should be random, and should be changed if a previously used key is to be used again. Define CTR mode
6.7 XTS-AES MODE FOR BLOCK-ORIENTED STORAGE DEVICES
The XTS-AES mode is base concept of a tweakable block cipher.
STORAGE ENCRYPTION R EQUIREMENTS
1. The ciphertext is freely available. 2. No change of data layout.
3. Data can be accessed in fixed size blocks. 4. Performing 16-byte block in encryption. 5. No metadata used.
6. Same plaintext is encrypted to different ciphertext at different locations.
OPERATION ON A SINGL E BLOCK
Encrypt and decrypt a single block
DEFINE XTS-AES MODE
SOURCE :
[1] W. Stallings, Cryptography And Network Security Principles And Practice Fifth Edition, New York: Prentice Hall,
2011.
[2] M. Kantarcioglu, “Modes of Operation”.
CHAPTER 7
PSEUDORANDOM NUMBER GENERATION AND STREAM CIPHERS
7.1 PRINCIPLES OF PSEUDORANDOM NUMBER GENERATION
THE USE OF RANDOM NU MBERS
Many uses of random numbers in cryptography
o nonces in authentication protocols to prevent replay o keystream for a one-time pad
These values should be
o statistically random, uniform distribution, independent o unpredictability of future values from previous values True random numbers provide this
Psuedo => Deterministic, reproducible, generated by a formula
RANDOMNESS
To validate that a sequence of numbers is random : 1. Uniform distribution
Sum of frequency of ones and zero should be approximately equal. 2. Independece
No subsequence can be inferred from the others in the sequence.
UNPREDICTABILITY
Each number is statistically independent of other numbers with ‘true’ random sequences, so this sequence will be unpredictable.
TRNGS, PRNGS, AND PR FS
TRUE RANDOM NUMBER GENERATOR (TRNG)
Takes input from a source that is effectively random. The sources is referred to entropy source.
There are conversion process of an analog source to a binary output. There are additional processing to overcome any bias in the source.
PSEUDORANDOM NUMBER GENERATOR (PRNG)
Takes input from a fixed value that called by seed.
With deterministic algorithm, a sequence of output bits is produced. Input value determine the output of bit stream.
Have two different forms :
o Pseudorandom number generator
An algorithm that is used to produce an open-ended sequence of bits.
o Pseudorandom Function (PRF)
PRNG REQUIREMENTS
PRNG generates numbers that have the characteristic of randomness as following below : o Uniformity
o Scalability o Consistency
Basic knowledge of statistical analysis
o Frequency test
To determine number of ones and zeros in a sequence, it should be same for a truly random sequence.
o Runs test
To determine number of runs of ones and zeros of various length for a random sequences. Two forms of unpredictability :
o Forward unpredictability o Backward unpredictability
ALGORITHM DESIGN
Purpose-Built Algorithms
Purpose : to generate pseudorandom bit streams. Algorithms based on existing cryptographic algorithms
o Three broad categories of cryptographic algorithms to create PRNGs :
o Symmetric block ciphers o Asymmetric ciphers
o Hash functions and message authentication codes
7.2 PSEUDORANDOM NUM BER GENERATORS
LINEAR CONGRUENTIAL GENERATORS
Parameter :
Three test to evaluarte a random number generator :
T1 : The function sholud be a full-period generating function. T2 : The generated sequence should appear random. T3 : The function is 32-bit in arithmetic.
BLUM BLUM SHUB GENER ATOR
The BBS is referred to as a cryptographically secure pseudorandom bit generator (CSPRBG). Use least significant bit from iterative equation:
xi = xi-12 mod n
where n=p.q, and primes p, q=3 mod 4 Unpredictable, passes next-bit test.
Security rests on difficulty of factoring N. Is unpredictable given any run of bits. Slow, since very large numbers must be used. Too slow for cipher use, good for key generation.
There is a proof reducing its security to the computational difficulty of computing modular square roots, a problem whose difficulty is equivalent to factoring.
The main difficulty of predicting BBS's output lies in the intractability of ``quadratic residuosity'' problem.
7.3 PSEUDORANDOM NUM BER GENERATION USING A BLOCK CIPHER
PRNG USING BLOCK CIP HER MODES OF OPERATI ON
Can use a block cipher to generate random numbers for cryptographic applications, For creating session keys from master key
CTR
Xi = EK[Vi] OFB
Xi = EK[Xi-1]
Input : Two pseudorandom inputs drive the generator.
Keys : The generator makes use of three triple DES encryption modules.
Output : The output consists of a 64-bit pseudorandom number and a 64-bit seed value.
7.4 STREAM CIPHERS
Process message bit by bit (as a stream)
A pseudo random keystream XOR’ed with plaintext bit by bit Ci = Mi XOR StreamKeyi But must never reuse stream key otherwise messages can be recovered
7.5 RC4
A proprietary cipher owned by RSA DSI.
Another Ron Rivest design, simple but effective. Variable key size, byte-oriented stream cipher. Widely used (web SSL/TLS, wireless WEP/WPA). Key forms random permutation of all 8-bit values.
Uses that permutation to scramble input info processed a byte at a time.
INITIALIZATION OF S
Start with an array S of numbers: 0..255 Use key to well and truly shuffle S forms internal state of the cipher
swap (S[i], S[j])
STREAM GENERATION
• Encryption continues shuffling array values.
• Sum of shuffled pair selects "stream key" value from permutation. • XOR S[t] with next byte of message to en/decrypt.
i = j = 0
for each message byte Mi i = (i + 1) (mod 256) j = (j + S[i]) (mod 256) swap(S[i], S[j])
t = (S[i] + S[j]) (mod 256) Ci = Mi XOR S[t]
STRENGTH OF RC4
7.6 TRUE RANDOM NUMBER GENERATORS
ENTROPY SOURCES
Nondeterministic source is used by TRNG to produce randomness. The following possible sources of randomness
o Sound/video input o Disk drives
SKEW
Deskewing algorithms, using hash function.
An n-bit output from an input of arbitrary length is produced by the hash function.
For deskewing, blocks of m input bits, with m ≥ n , can be passed through the hash function.
SOURCE :
[1] W. Stallings, Cryptography And Network Security Principles And Practice Fifth Edition, New York: Prentice Hall, 2011.
[2] R. Jain, “Pseudorandom NumberGeneration and Stream Ciphers,” Washington University in Saint Louis, Saint Louis, 2011.
[3] F.-X. S. O. P. T. G. M. M. Y. Christophe Petit, “A Block Cipher based Pseudo Random Number Generator Secure Against Side-Channel Key Recovery,” Dept. of Computer Science, Columbia University.
[4] [Online]. Available: http://en.wikipedia.org/wiki/Blum_Blum_Shub. [Diakses 8 March 2015].
[5] [Online]. Available: http://www.cs.indiana.edu/~kapadia/project2/node11.html. [Diakses 8 March 2015].