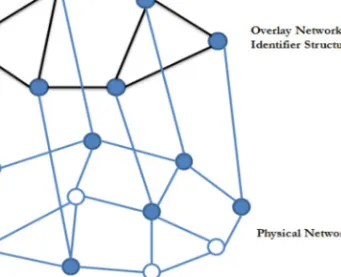
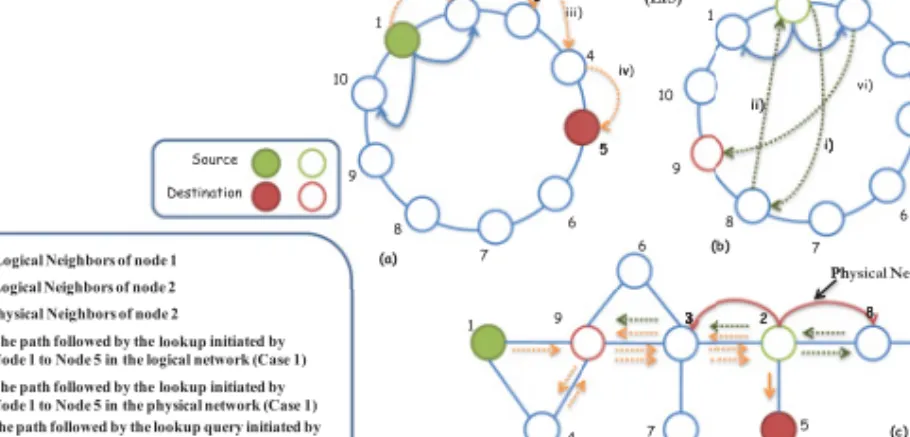
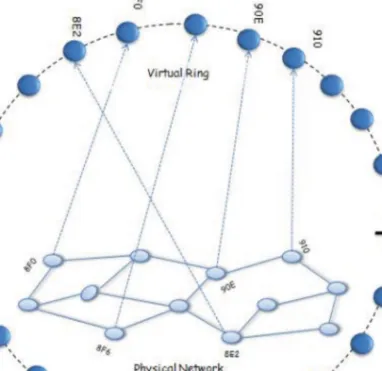
This lookup is accomplished inO(f(n))logical hops, wheref(n) is a function of the number of neighbors a node has in the LIS. 2012] mainly focuses on the location of the node and ensures that neighbors in the overlay network are physically close. Packet forwarding is determined using only logical neighbors of the node in the LN.
Such protocols only use DHT to locate the geographic coordinates of the destination on the network. We assume that each node in the LIS stores information about its one-hop logical neighbors. Node4 has node5 as its logical neighbor in the LIS, which is the final destination of the query.
High maintenance overhead. The DHT maintenance procedure ensures routing convergence and efficiency in terms of the number of hops in the LIS. For reactive routing protocols, the overhead is at most O(n), where is the number of nodes in the network [Shen et al. Selection of LIS. The structure connecting the nodes in the LS is another challenge to the performance of DHT-based routing protocols in MANETs.
Address space utilization Efficient utilization of the LS is one of the major concerns in the design of a large-scale, DHT-based routing protocol. Forwarding in KDSR is based on XOR distance to the cover of the destination, which can incur a high path-stretch penalty in the worst case. L+nodes are arranged in a tree-based LIS, and the cover of a node describes its relative position in the LIS.
The LID of a node reflects the relative position of the node with respect to its neighbors in the LN. DART proactively stores routing information and incurs O(logn) routing table complexity for the number of nodes in the network. Each node in the ATR maintains a subset of pairs in the form of (identifier (UID), network address (LID)) that is assigned to the node based on the hash function.
The cover of a node shows its relative position with respect to the root node in the LDAG structure. To forward a packet, the node searches the list of its one-hop neighbors to find a node whose cover shares the longest prefix to the cover of the destination node in the packet. When the parent of a node in EMP is lost or fails, the node gets a new cover from one of the available one-hop neighbors in the network.
Therefore, the routing table size is O(log n), where is the number of nodes in the network.
FUTURE TRENDS AND DHT-BASED ROUTING
- Content-Centric Networking
- Device-to-Device Communication
- Integrated MANET and Internet
- Internet of Things
- Machine-to-Machine Communications
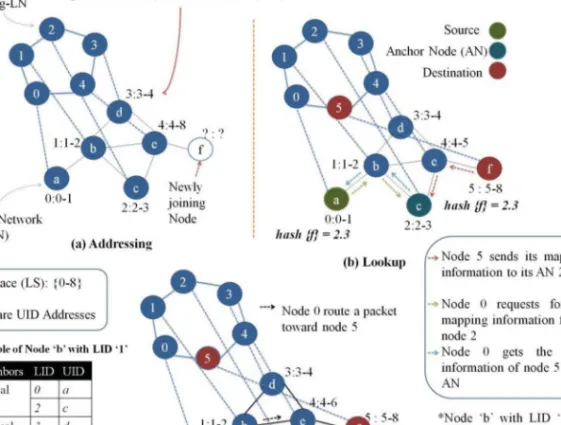
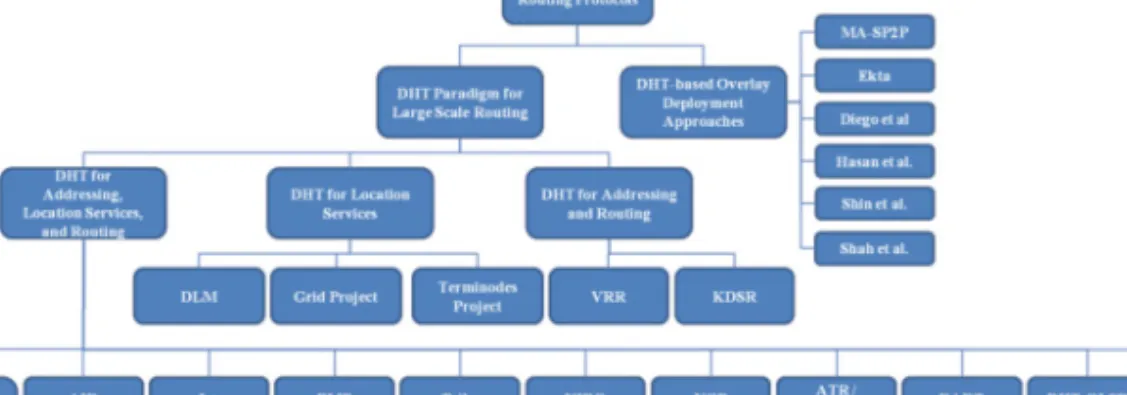
Similarly, 3D-RP introduces a concept of secondary AN that stores the replica of the map information stored on the primary AN. In a nutshell, in this section we discuss in detail the basic concepts related to DHT and identify the key challenges and requirements as a guideline for researchers planning to design a DHT-based routing protocol. Furthermore, we classify DHT-based routing into two main categories, namely DHT-based overlay deployment approaches and DHT paradigms for large-scale routing in MANETs, followed by an explanation of the criteria that distinguish them.
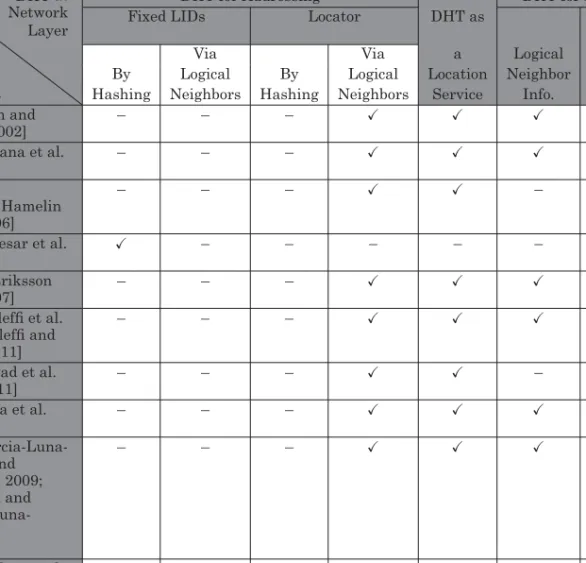
Finally, the features of the protocols discussed are summarized in Table III, where each protocol is analyzed against key metrics that could be useful to those working in this field. Fourth-generation (4G) wireless systems connect mobile users to the Internet through heterogeneous connection technologies (e.g., cellular, wireless LAN, MANETs) [Al Shidhani and Leung 2010; Cavalcanti et al. Second, in the MANET, a mobile user can access the Internet through another user connected to the Internet [King 2011; Reporter 2011].
Existing traditional routing protocols for MANETs are not scalable because these protocols are based on the flooding mechanism [Caleffi and Paura 2011; Eriksson et al. IoT refers to an intelligent world of identifiable objects, such as devices, sensors, actuators and mobile phones with ubiquitous computing and networking, and that cooperate with their neighboring objects to provide value-added services [Atzori et al. Scalable identification, naming, name resolution and addressing space and structure, due to the large size of the resulting system, and scalable data communication and networking, due to the high level of interconnection between a large number objects, there are several. the main concerns related to scalability in IoT [Chaouchi et al.
IoT analysis and planning cannot overlook aspects related to network technologies such as routing protocols, flow control robustness, and synchronization. Distributed implementation of routing protocols is a key issue for all network systems and especially for IoT [Chaouchi et al. DHT-based lookup and routing technologies can be used for short-range communication whenever possible in case of large deployments in IOT.
Machine-to-machine (M2M) communication refers to data communication between autonomous machines without human intervention [Ant´on-Haro et al. IoT concepts can be seen as a superset of functions necessary for the design of M2M, as IoT involves other technologies such as nanotechnology, robotics and artificial intelligence [Bourgeau et al. This can be reduced by carefully applying algorithmic and distributed computing techniques to design efficient communication protocols, such as routing protocols [Chang et al.
CONCLUSIONS
InProceedings of the 5th IEEE International Conference on Mobile Ad Hoc and Sensor Systems (MASS. Distributed hashing for scalable multicast in wireless ad hoc networks. IEEE Transactions on Parallel and Distributed Systems. DART: Dynamic address routing for scalable ad hoc and mesh networks.IEEE /ACM Transactions on Network.
A Survey on QoS Routing Solutions for Mobile Ad Hoc Networks. IEEE Communications Surveys and Tutorials9, 2, 50–70. DSR: Dynamic Source Routing Protocol for Multihop Wireless Ad Hoc Networks. Ad Hoc Network 5, 139–172. A Survey on Multicast Routing Protocols for Mobile Ad-Hoc Networks. IEEE Communications Surveys and Tutorials.
Scalability study of the ad hoc on-demand distance vector routing protocol.International Journal of Network Management. Efficient use of route requests for loop-free on-demand routing in ad hoc networks. Computer networks. Proceedings of the 1st Annual IEEE Communications Society Conference on Sensor and Ad Hoc Communications and Networks (SECON.
Proceedings of the IEEE Communications Society 6th Annual Conference on Sensor, Mesh, and Ad Hoc Communications and Networks (SECON'09). Proceedings of the 7th International IEEE Conference on Mobile Ad-Hoc and Sensor Networks (MSN. A survey on adaptive congestion routing protocols for mobile ad-hoc networks. International Journal of Computer Theory and Engineering3, 2, 189–.
A peer-to-peer file discovery and transfer protocol for wireless ad-hoc networks. Computer communications. Self-Organization in Spontaneous Networks: A DHT-Based Routing Protocols Approach. Ad hoc networks. An overview of clustering schemes for mobile ad hoc networks. IEEE Communications Surveys and Tutorials7, 1, 32–48.