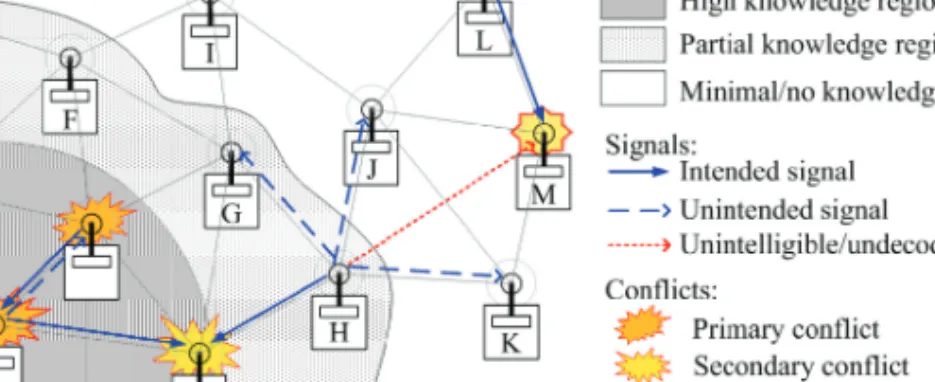
This helps maintain the bandwidth of a network with a limited number of channels and prevents congestion [Kyasanur et al. In addition, multichannel scheduling [So and Vaidya 2004], multiradio scheduling [Raniwala and Chiueh 2005; Kyasanur et al.

Common Assumptions in Simulation Studies
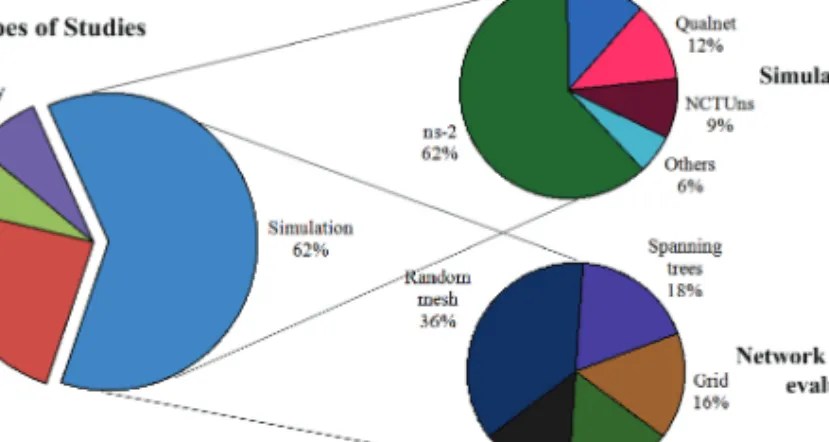
As shown in Figure 5, 62% of the research papers selected for this study are based on simulation studies. Specifically, 52% of research work involves a multitude of complexities, such as varying degrees of networking (i.e., number of neighbors), multi-hops, and loop connectivity using arbitrary mesh and/or grid topologies. On the other hand, 48% of studies lack full investigation of the complexity of WMN, as stated in RFC 2501 of the Internet Engineering Task Force for Mobile Ad Hoc Networks (MANETs) [Corson and Macker 1999].
Theoretical studies, including graph theory-based studies, statistical models and/or derivations of upper and lower bounds, constitute almost a quarter of the research work. All testbeds included in this study were built using ubiquitous IEEE 802.11-based wireless WiFi interfaces.
RANDOM ACCESS SCHEMES
Contention-Based Access
In addition to the previous list of assumptions, slot time-based scheduling schemes have further assumptions such as: (i) all nodes are equipped with perfect time synchronization or have a global clock, and (ii) a message sent by a node. is correctly received by all neighbors within a limited time, and propagation delay is less than the waiting band. These schemes mainly depend on protocols that determine which packet should be sent next and when it can be sent based on the events observed. Algorithms are used in the secondary areas, such as adjustments of the size of the battle window [Kim et al.
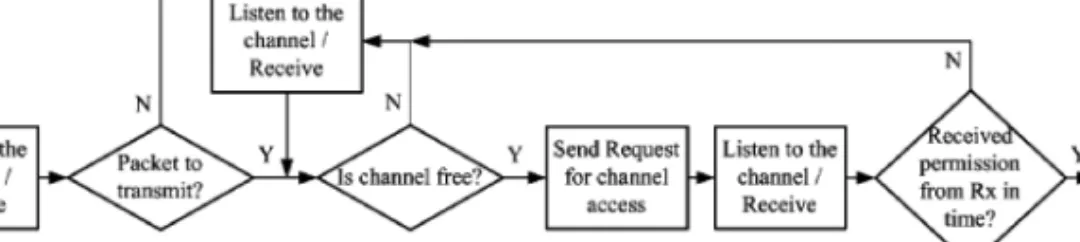
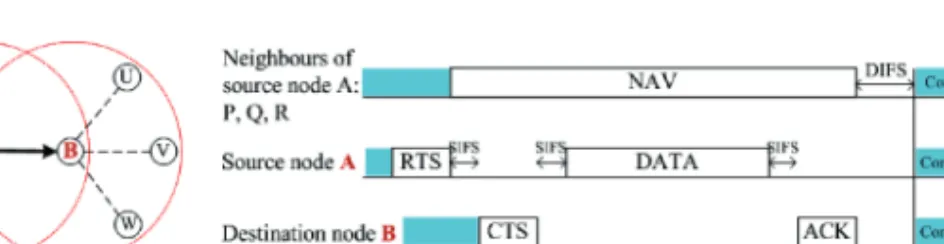
The Distributed Coordination Function
The backoff period is calculated in a way that minimizes the collisions through an adaptive contention window calculation scheme and the equation used is. Backo f T ime=Random[0,CW]×aSlotT ime, (1) where Random[0,CW] is a random integer generated from a uniform distribution of 0 to CW, where Contention Window -CW adapts itself with number of previous attempt failed, and aSlotT ime based on physical layer properties.
Progress in the Research of Random Access Schemes Asynchronous random access schemes
Findings include how the physical layer, MAC layer, and network layer behave differently and how they affect traffic flow in WMNs based on random access schemes. The authors discuss advances in a random access scheme to improve delay and service level guarantees and throughput measurement in pro-type 802.11s-based nodes. 2006] on DCF-based media access control (MAC) protocols provides a very good insight into early random access solutions.
While the vast majority of random access-based research work has focused on adding some advancements on top of asynchronous DCF schemes that are readily supported by WiFi devices, some research is also being conducted on time-based random access schemes for WMNs [ Zhu and Corson 1998; Navy etc. A similar contention-based synchronous and distributed random access scheme was proposed in Ju and Li [1998].
PSEUDO-RANDOM ACCESS SCHEMES
Continuous Distributed Prediction
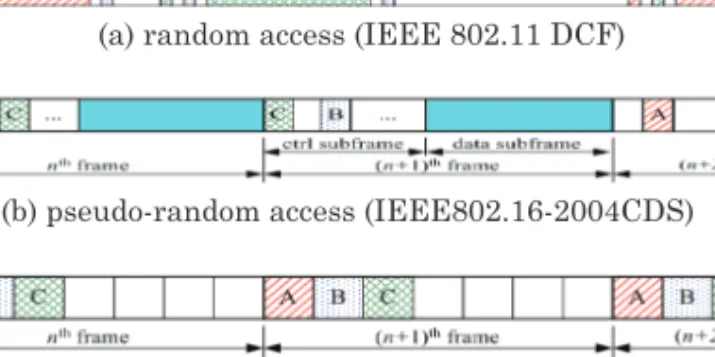
Thereby, contention is limited to reservation subframes and slots within user data subframes are broadcast in a collision-free manner. While Zhu and Corson [1998] use an adaptation mechanism, based on the number of contending neighbors, to limit the probability of a node accessing a slot within the reservation subframe to minimize collisions, Marina et al. 2001] propose repeated transmissions of request messages to improve the probability that a request message is received by the intended node. These schemes, intended for control message exchange to achieve cyclic access within a user data subframe, pave the way for further research on the number of reservation subframes required for different neighborhood densities.
The proposal improves the throughput lower bound and requires the network size and maximum degree of a node in the network in advance for its operation. Another prominent example of the use of synchronous random access schemes exists within the IEEE Coordinated Scheduling Framework, where MSH-NENT messages in network control subframes are randomly scheduled. 2007] succinctly identifies potential deadlocks caused by the hidden terminal problem in the network establishment processes involving MSH-NENT and MSH-NCFGMAC management messages that affect autonomous operation.
Mesh Election-Based Coordinated Distributed Scheduling
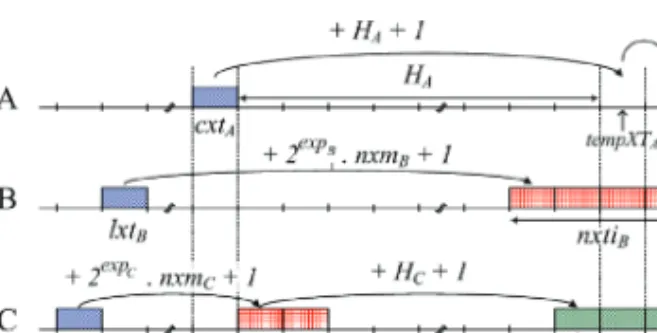
In pseudo-random access, while distributed algorithms play a primary role in determining the transmission opportunities, protocols such as three-way handshakes of request-grant-acknowledge messages can be used for secondary slot assignments. In addition, the node must transmit its first-hop neighbors' next transmission timings within each MSH-DSCH message. The relationship between parameters Xmt Holdoff Time (H), Next Xmt Mx (nxm), and Xmt Holdoff Exponent (exp) is defined in the standard as.
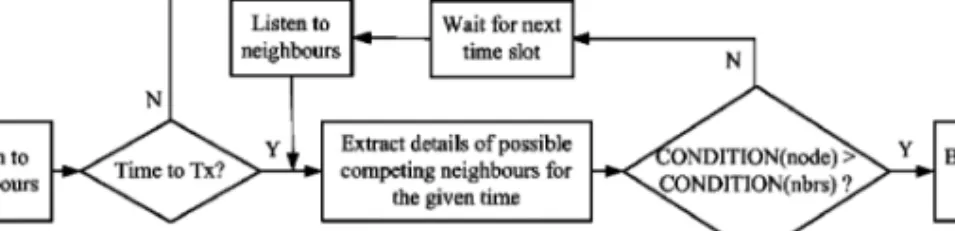
Neighbors are considered competitors in the following scenarios: if (i) node B, whose next transmission time interval (nxtiB) includes txtA, (ii) node C, whose earliest subsequent transmission time, esxtC≤txtA, or (iii) node D, whose next transmission time interval is unknown . Note that unlike random access schemes, pseudo-random access schemes rely primarily on algorithms such as hashing sequences and mesh selection to determine which node should access the channel.
Progress in the Research of Pseudo-Random Access Schemes
The standardization of network operation and the strength of certified WiMAX devices in terms of bandwidth and coverage have attracted considerable research interest in this channel access framework [Ali et al. Moreover, the two-sided study of Cao et al. [2005] evaluate the delay performances using a stochastic model and simulation results. Accelerating the three-way handshakes of MSH-DSCH messages is considered as a way to speed up the allocation of data slots and thus reduce the end-to-end delay [Vijayalayan et al.
Some of the MSallocation solutions that emerged after some preliminary publications on TO scheduling, such as Mogre et al. The following are the general assumptions made in many of the pseudo-access-based simulation studies, in addition to the lists of assumptions given in Section 2.6: (i) all nodes use the same set of algorithms in random number generation, seed value exchange and comparison, (ii) nodes know the identities of their two-hop neighbors (the minimum), (iii) network changes are learned by some other mechanisms, and (iv) the strongest modulation and coding schemes are used for control messages and modulation and coding schemes with the highest possible bitrate are used for user data (in the case of IEEE.
CYCLIC ACCESS SCHEMES
Achieving the Lowest Cycle Length
2010] summarizes some of the distributed planning proposals in addition to the centralized proposals. The study categorizes the proposals on distributed scheduling schemes into Election-Based Transmission Timing (EBTT) proposals and MS allocation algorithms.
Node-Id-Based Cyclic Access Scheme
Progress in the Research of Cyclic Access Schemes
Cunningham and Cahill [2002] propose a combined solution of random access and cyclic access to guarantee end-to-end delays. The network coverage area is divided into cells, and nodes within a cell access the channel in a contention-free and cyclical manner using random access-based negotiations over the contention period. The solution has a prerequisite of knowing the number of nodes in the network and geographic location of nodes at each node.
The solution supports multiple slot allocations to meet bandwidth requirements and an asynchronous random access scheme is incorporated to negotiate the scheduling cycle. In addition, a priori knowledge of global network parameters, such as the number of nodes in network and the maximum number of neighbors a node has, are difficult to predict and can change over time [Chlamtac et al.
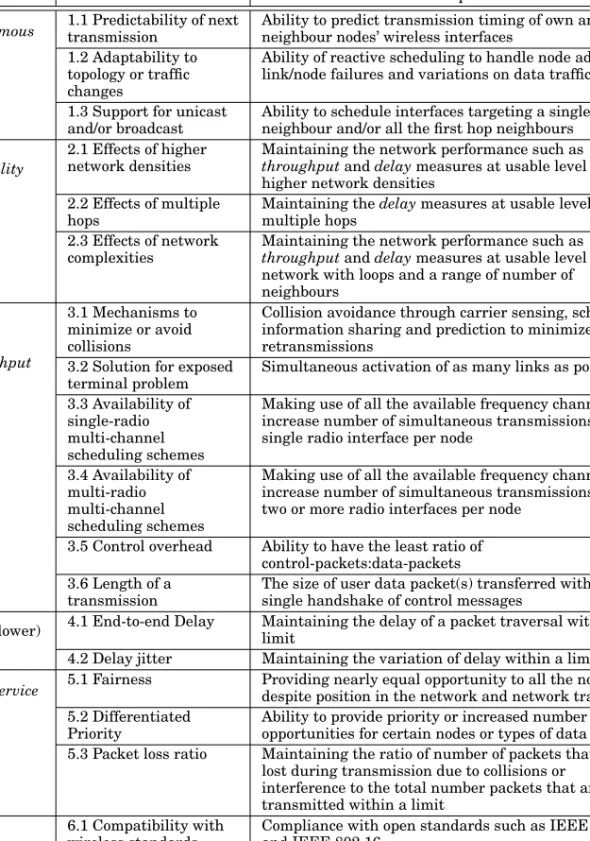
COMPARISON OF MAJOR TYPES OF DISTRIBUTED SCHEDULING SCHEMES
Research Focus of the Selected Literature
In addition to the comparison provided in Table II, we also quantitatively compared the research focus given on the eight main attributes for the main planning schemes. This process was carried out on the literature referred to in this survey that were selected based on the criteria given in section 1.5. Based on this, the mean values and standard deviations of the signs in each attribute were obtained for each large distributed scheduling solution.
From the web maps in Figure 12, it is clear that in random access and pseudo-accessible access schemes more focus is given to autonomous operations, interoperability and throughput while cyclic access schemes pay more attention to delay. Furthermore, there appears to be room for more energy efficiency contributions from pseudo-random access solution designs.
DEVELOPMENTS IN WIRELESS STANDARDS 1. IEEE 802.11 Family Standards
IEEE 802.16 Family Standards
A discussion thread from the IEEE 802.16 Working Group (IEEE C802.16maint-07/042) indicates that a mesh operation map is being dropped due to its incomplete status and that the change-based IEEE 802.16j framework can be considered as an alternative solution in the meantime. Despite the changes in the IEEE 802.16 standard, researchers continue to work on Mesh Election subroutine-based scheduling to make it a complete channel access solution. Furthermore, the IEEE 802.16j-2009 framework only supports a tree topology-based multihop relay network and not the general mesh topologies [Ghosh et al.
IEEE 802.16m-2011 provides enhancements for higher throughput air interfaces to match the International Telecommunication Union's advanced IMT specifications. Therefore, it can be concluded that IEEE 802.16-based WiMAX technology will continue as a potential fourth-generation wireless interface, and a complete planning framework to turn them into component nodes for WMNs remains an interesting research topic.
Other IEEE 802 Family Standards
This means that the Mesh Elections subroutine, the basis of the widely researched pseudo-random channel access scheme, will not be part of the newer version of WiMAX equipment. IEEE 802.16h-2010 proposes cognitive radio (CR) capabilities, i.e., operational environment and internal state awareness and timely decision making on IEEE 802.16-based wireless units, for improved coexistence mechanisms in license-free operation.
IETF’s Mobile Ad Hoc Network (MANET)
EMERGING TRENDS AND KEY RESEARCH PROBLEMS
For example, IEEE 802.11s is developed with time synchronization, and IEEE 802.11y serves greater coverage distances up to 4.5 km previously found in IEEE 802.16 solutions. Therefore, these performance metrics must be evaluated for different network topologies and traffic patterns. In addition, the continuous receiver uptime for carrier sensing must be minimized to improve energy efficiency while keeping delays within acceptable limits.
Investigations into the optimal amount of seed data to share is another open challenge for researchers. Detailed message patterns serving WMN control and user data packets are another critical shortcoming of round-robin access schemes that must be addressed.
CONCLUSION