Carlos Becker Westphall, Pederal nga Unibersidad ti Santa Catarina, Brasil Carlos Calafate, Unibersidad ti Politekniko ti Valencia, Espania. Dimitrios Vergados, Unibersidad ti Siensia ken Teknolohia ti Norway, Norway Ding-Zhu Du, Unibersidad ti Texas, Dallas, E.U.A. Ibrahim Ghareeb, Unibersidad ti Siensia ken Teknolohia ti Jordan, Jordan Ibrahim Habib, Unibersidad ti Siudad ti Nueva York, E.U.A.
János Tapolcai, Universidade de Tecnologia e Economia de Budapeste, Hungria Javier Gozalvez, Universidad Miguel Hernandez de Elche, Espanha. Jorge Sá Silva, Universidade de Coimbra, Portugal José de Souza, Universidade Federal do Ceará, Brasil. Jussi Haapola, Centro de Comunicação Sem Fio, Universidade de Oulu, Finlândia Jyoti Singh, Instituto Nacional de Tecnologia de Patna, Índia.
Krzysztof Szczypiorski, Warsaw University of Technology, Poland Krzysztof Walkowiak, Wroclaw University of Technology, Poland Kui Ren, State University of New York at Buffalo, USA. Mariofanna Milanova, University of Arkansas at Little Rock, USA Mariusz Glabowski, Poznan University of Technology, Poland Mariusz Zal, Poznan University of Technology, Poland. Mohammad Banat, Jordan University of Science and Technology, Jordan Mohammad Taghi Hajiaghayi, University of Maryland, College Park, USA.
Rajib Ghosh, National Institute of Technology Patna India, India Rajkumar Buyya, The University of Melbourne, Australia. Reaz Ahmed, Bangladesh University of Engineering and Technology, Bangladesh Roberto Beraldi, "Sapienza" Università di Roma, Italy. Sergey Andreev, Tampere University of Technology, Finland Seshan Srirangarajan, Cork Institute of Technology, Ireland Seung-Jong Park, Louisiana State University, USA.
Snehanshu Saha, PES Institute of Technology, Bangalore South Campus, Indien Sonali Agarwal, Indian Institute of Information Technology, Allahabad, Indien Song Guo, University of Aizu, Japan. Zbigniew Dziong, École de technologie supérieure, University of Quebec, Canada Zhang Jin, Beijing Normal University, P.R.
Additional Re
Additional Revie vie wers w ers
Ziqian Dong, New York Institute of Technology, USA Zoubir Mammeri, Paul Sabatier University, France Zubair Fadlullah, Tohoku University, Japan. Indrajit Banerjee, Bengal University of Engineering & Science, Shibpur, India Jacques Facon, PUCPR Pontificia Universidade Católica do Paraná, Brazil Jeeva Jacob, Rajagiri School of Engineering & Technology, India. Juluru Tarunkumar, Jawaharlal Nehru University of Technology, India Kamalanathan Kandasamy, Amrita Vishwa Vidyapeetham, India Kamil Dimililer, Middle East University, Cyprus.
కీర్తి ప్రసాద్ జి., విశ్వేశ్వరయ్య టెక్నలాజికల్ యూనివర్శిటీ, ఇండిజా కౌశిక్ మజుందార్, వెస్ట్ బెంగాల్ యూనివర్శిటీ ఆఫ్ టెక్నాలజీ, ఇండిజా కృష్ణన్ కుట్టి, కెపిఐటి కమ్మిన్స్ ఇన్ఫోసిస్టమ్స్ లిమిటెడ్, ఇండిజా. మీనా మరలప్పనవర్, బి.వి. భూమరద్ది కాలేజ్ ఆఫ్ ఇంజిన్ అండ్ టెక్నాలజీ, ఇండిజా మీనల్ బోర్కర్, ఆమ్రపాలి ఇన్స్టిట్యూట్, ఉత్తరాఖండ్ టెక్నికల్ యూనివర్శిటీ, ఇందీజా మేఘా చాకోలే, RT M నాగ్పూర్ విశ్వవిద్యాలయం, ఇందీజా. Mohamad Zoinol Abidin Aziz, Universiti Tehnical Malaysia Melaka, Malaysia Mohammad Farhatullah, Dr L Bullayya College of Engineering for Women, Indija Mohammad Rasmi, Universiti Sains Malaysia (USM), మలేషియా.
మోనిరుల్ ఇస్లాం, అహ్సానుల్లా యూనివర్శిటీ ఆఫ్ సైన్స్ అండ్ టెక్నాలజీ (AUST), బంగ్లాదేశ్ మోనోవర్ భుయాన్, డిపార్ట్మెంట్ ఆఫ్ కంప్యూటర్ Sc & Engg, తేజ్పూర్ యూనివర్సిటీ, ఇండీజా. రాజేష్ కన్నన్ మేగలింగం, అమృత విశ్వ విద్యాపీఠం విశ్వవిద్యాలయం, ఇండిజా రాకేష్ మిశ్రా, ఫిరోజ్ గాంధీ ఇన్స్టిట్యూట్ ఆఫ్ ఇంజనీరింగ్ & టెక్నాలజీ, ఇందీజా రోహిత్ థాంకీ, సి యు షా విశ్వవిద్యాలయం, ఇండీజా. సతీష్ చంద్ర, జేపీ ఇన్స్టిట్యూట్ ఆఫ్ ఇన్ఫర్మేషన్ టెక్నాలజీ, ఇండిజా సెల్వరాజ్ అనంతి, SNS కాలేజ్ ఆఫ్ టెక్నాలజీ, ఇండీజా.
Thakur, MCKV Institute of Engineering, India Sunita Aher, Solapur University, Solapur, Maharashtra, India Susant Jena, KNS Institute of Technology, Bangalore, India Syed Ibrahim, VIT University, India. Vikrant Chauhan, Jaypee Institute of Information Technology University, India Vimal Pandey, Dehradun Institute of Technology, India.
Second International
ADM: Second International
ADM: Second International Workshop on W orkshop on Adv Advances in Data Management ances in Data Management (ADM’13)
ADM’13)
Abstract - A combination of One Time Password (OTP), SMS gateway and MD5 Hash encryption algorithm is used to develop a more secure login process to access an online academic information system. But in the second place, while connected to the Internet, there are many vulnerable. Gammu SMS Gateway is installed in the server to automatically send OTP via SMS to the authenticated user.
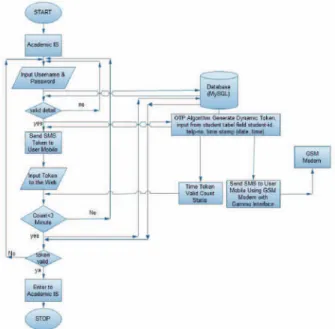
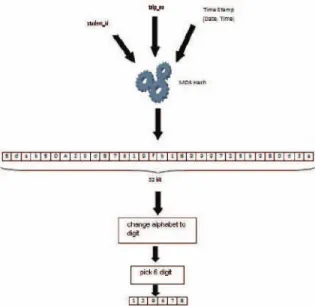
A message that has been converted to a message summary cannot be reverted back. While the SMS arrives in the SMS device, gammu moves it to the Inbox of the database. The student ID, phone number, and timestamp (date and time of access) are encrypted using an MD5 hash. 2) The hashed value obtained is 32 hexadecimal digits.
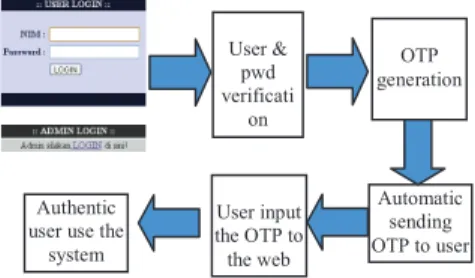
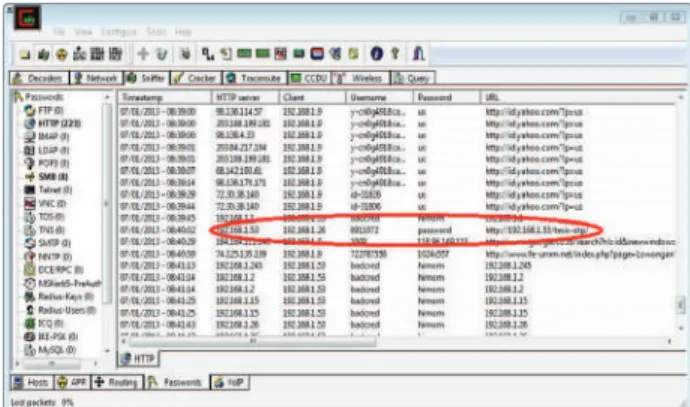
We run this tool in the background, while we manage the system and users start logging into the system. While the user logs into the system without extended security (OTP), CA records the username and password input by the user. If the username and password are valid, the system sends the OTP via SMS to the number previously registered with the system.
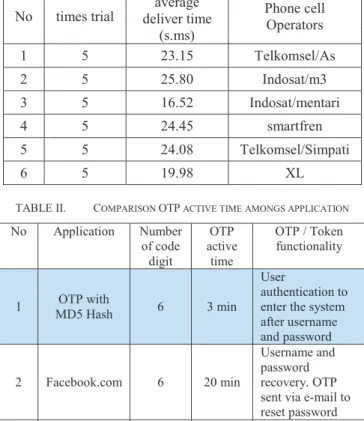
If the user does not enter the OTP within the allowed time, the system will be reset and back to the original state. This table shows that among the mobile phone operators used in this experiment, the average time to deliver the OTP to the user is no more than half a minute. As it is too shoot a time for hackers to break the code and infiltrate to the system.
We have developed a security login system using OTP which is encrypted with MD5 Hash and OTP is automatically sent to the registered user's phone number. Compared to an OTP generated with a pseudo random number generator (PNRG), it can generate the same codes. With this condition, it is impossible for a hacker to break the code and infiltrate the system.