Before using this information and the product it supports, please read the general information in Appendix A, “Special Notices” on page 673. When you submit information to IBM, you grant IBM a nonexclusive right to use or distribute the information. in any way it sees fit without incurring any obligation to you.
Preface
The Team That Wrote This Redbook
He has two years of experience in the MVS TCP/IP area with a focus on FTP and Sockets. He has five years of experience supporting IBM network hardware products focusing on TCP/IP and SNA connectivity.
Comments Welcome
Architecture and Core Protocols
- Internet History - Where It All Came From
- Internetworks
- The Internet
- ARPANET
- NSFNET
- Commercial Use of the Internet
- Information Superhighway
- Internet2
- The Open Systems Interconnect (OSI) Model
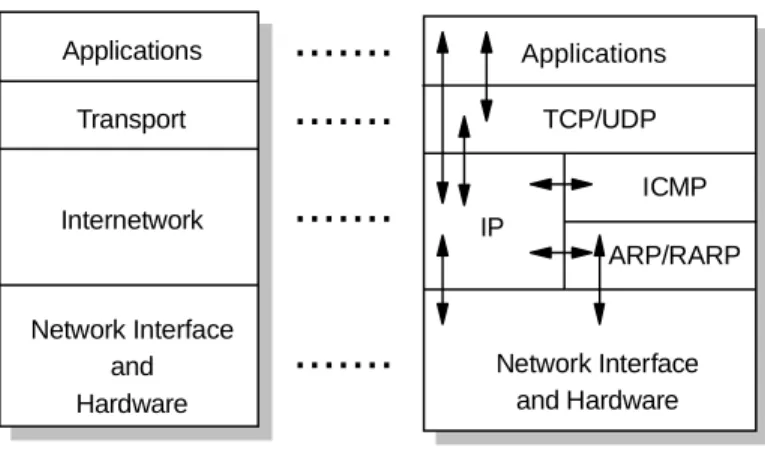
- TCP/IP Architectural Model - What It Is All About
- Internetworking
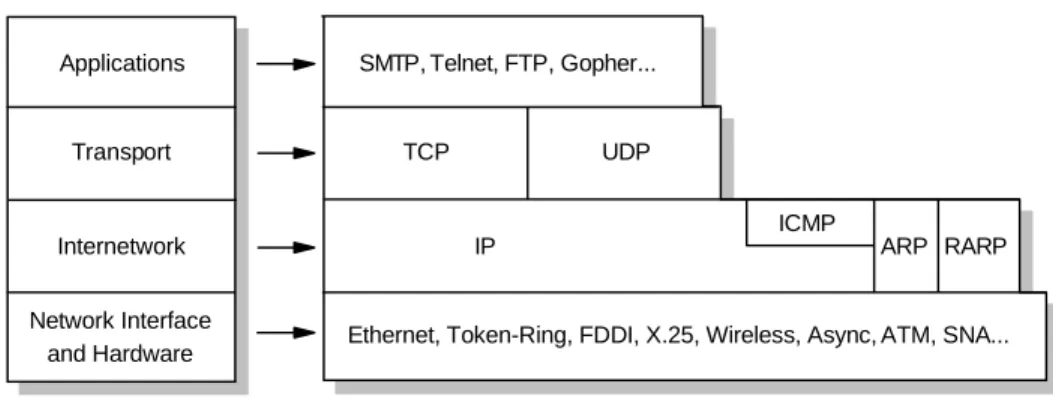
- The TCP/IP Protocol Stack
- TCP/IP Applications
- Bridges, Routers and Gateways
- Finding Standards for TCP/IP and the Internet
- Request For Comments (RFC)
- Internet Standards
The term IP router is also used because the routing function is part of the IP layer of the TCP/IP protocol suite (see 1.2.2, “The TCP/IP Protocol Stack” on page 12). New protocols (mostly application protocols) are designed and implemented by researchers and are brought to the attention of the Internet community in the form of an Internet Draft (ID).1 The largest source of IDs is the Internet Engineering Task Force (IETF). ), which is a subsidiary of the IAB.

Internet Official Protocol Standards
Assigned Internet Numbers
Host Requirements
Router Requirements
- For Your Information (FYI)
- Obtaining RFCs
- Major Internet Protocols
- Future of the Internet
- IBM and the Internet
- The Network Computing Framework
In fact, IBM has been practically involved in the development of the Internet for a long time, providing software and hardware for, for example, NSFNET. Database services that integrate the properties and functions of an object-relational database with those of the web application server.
Internetworking and Transport Layer Protocols
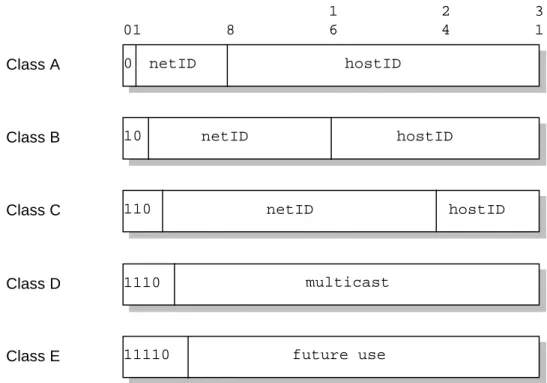
- Internet Protocol (IP)
- IP Addressing
- IP Subnets
- IP Routing
- Methods of Delivery - Unicast, Broadcast, Multicast and Anycast
- The IP Address Exhaustion Problem
- Intranets (Private IP Addresses)
- Classless Inter-Domain Routing (CIDR)
- IP Datagram
- Internet Control Message Protocol (ICMP)
- ICMP Messages
- ICMP Applications
- Internet Group Management Protocol (IGMP)
- Address Resolution Protocol (ARP)
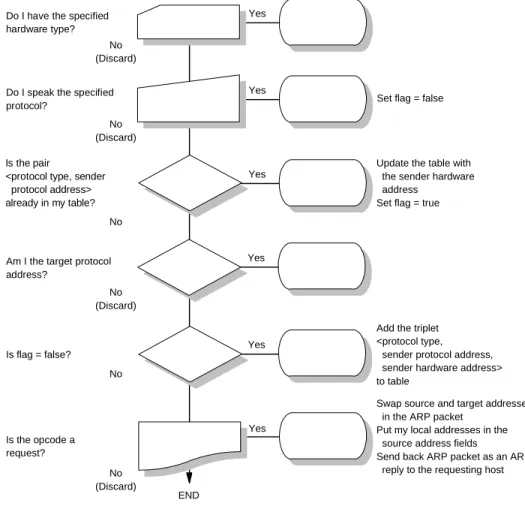
- ARP Overview
- ARP Detailed Concept
- ARP and Subnets
- Proxy-ARP or Transparent Subnetting
The problem and how to solve it is discussed in 2.1.5, “The IP Address Exhaustion Problem” on page 42. The host number part of the IP address is again split into a network number and a host number. The address of the first of these gateways (the first hop) is called an indirect route in the context of the IP routing algorithm.
The format for each depends on the value of the option number in the first byte. Take the following IP address in the route data field (the one indicated by the pointer field) and place it in the destination IP address field of the datagram. Checks the operation of the name server (or the flat namespace resolver, depending on the installation).
Therefore, a module (ARP) is provided that will translate the IP address to the physical address of the destination host. Both this address and the source route information are stored in the requesting host's ARP cache.
IP subnet routing
Reverse Address Resolution Protocol (RARP)
- RARP Concept
Host A receives this ARP reply, places it in its cache, and will forward future IP packets for host B to router R. And of course the physical header of the frame will now indicate RARP as the higher level protocol (8035 hex) instead of ARP (0806 hex) or IP (0800 hex) in the EtherType field. Because of the size this database can take, part of the server function is usually implemented outside the adapter's microcode, with optionally a small cache in the microcode.
The microcode portion is then solely responsible for receiving and transmitting the RARP frames, with the RARP mapping itself being handled by server software running as a normal process on the host machine. The nature of this database also requires some software to manually create and update the database. In case there are multiple RARP servers on the network, the RARP requester will only use the first RARP response received on its broadcast RARP request and ignore the others.
Ports and Sockets
- Ports
- Sockets
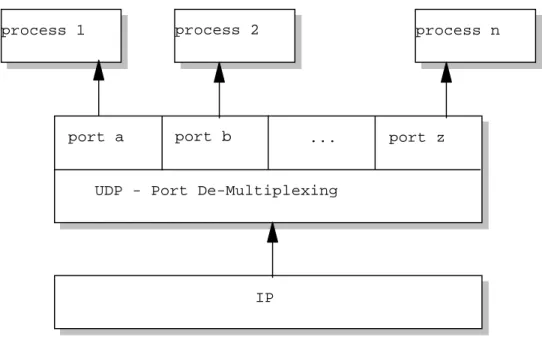
Well-known ports are controlled and assigned by the Internet Central Authority (IANA) and on most systems can only be used by system processes or by programs run by privileged users. Each client process is assigned a port number as long as it needs it from the host it is running on. UDP, TCP, and ISO TP-4 all use the same port principle (see Figure 50 on page 78).
As far as possible, the same port numbers are used for the same services over and above UDP, TCP and ISO TP-4. Each side of a TCP connection has a socket that can be identified by the triple
User Datagram Protocol (UDP)
- UDP Datagram Format
- UDP Application Programming Interface
That is, a socket is an endpoint for communication that can be named and addressed in a network. The application need not concern itself with the management of this stream; these facilities are provided by TCP. The UDP layer can be considered extremely thin and therefore has low overhead, but it requires the application to take responsibility for error recovery and so on.
Applications that send datagrams to a host must identify a target that is more specific than the IP address, since datagrams are usually directed to specific processes rather than the system as a whole. It is an optional 16-bit complement of the complement sum of a pseudo-IP header, UDP header, and UDP data. Note that UDP and IP do not provide guaranteed delivery, flow control, or error recovery, so these must be provided by the application.
Transmission Control Protocol (TCP)
- TCP Concept
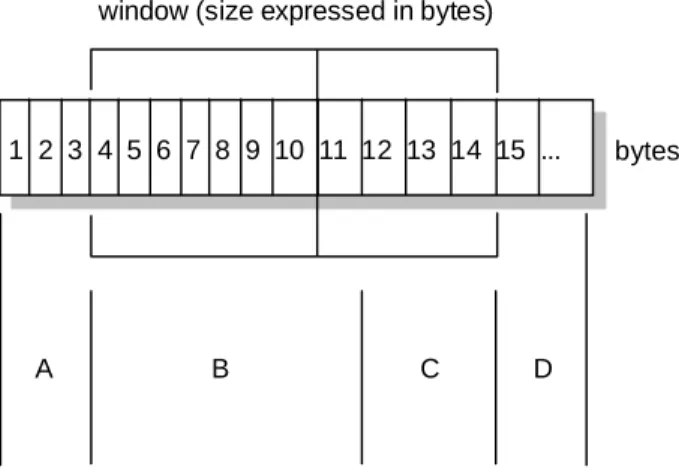
- The Window Principle
Sometimes, an application needs to be sure that all data passed over TCP has actually been transmitted to the destination. Since data is transmitted in blocks (TCP segments), only the sequence number of the first byte of data in the segment is sent to the destination host. The receiving TCP, when sending an ACK back to the sender, also tells the sender the number of bytes it can receive beyond the last TCP segment received, without causing overruns and overflows in its internal buffers.
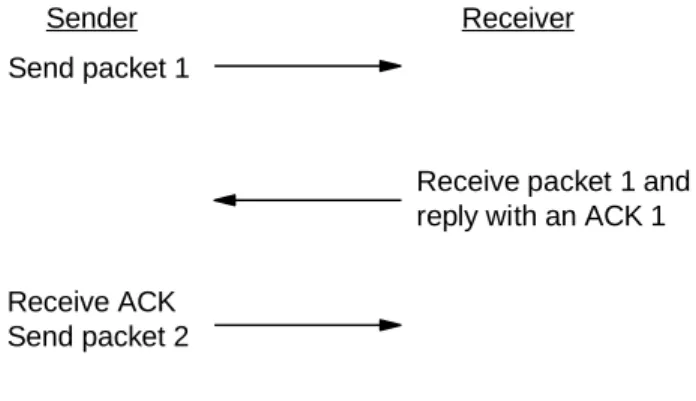
A simple transport protocol can use the following principle: send a packet and wait for an acknowledgment from the receiver before sending the next packet. The sender can send all packets within the window without receiving an ACK, but must initiate a timeout timer for each packet. The recipient must confirm each package received and indicate the tracking number of the last package received successfully.
- The Window Principle Applied to TCP
- TCP Segment Format
- Acknowledgments and Retransmissions
- Establishing a TCP Connection
- TCP Application Programming Interface
- TCP Congestion Control Algorithms
- Slow Start
- Congestion Avoidance
- Fast Retransmit
Remember that TCP will block bytes into segments, and a TCP segment only carries the sequence number of the first byte in the segment. If the ACK control bit is set, this field contains the value of the next sequence number that the receiver expects to receive. It specifies the number of data bytes beginning with that specified in the Acknowledgment Number field that the receiver (= the sender of this segment) is willing to accept.
Acknowledgments indicate the sequence number of the next byte that the receiver expects to receive. The TCP congestion algorithm prevents a sender from exceeding network capacity (eg slower WAN links). The sender may transmit the lower value of the congestion window or the advertised window.
- Fast Recovery
- References
The purpose of this duplicate ACK is to tell the other end that a segment was received out of order, and what sequence number to expect. Since TCP does not know whether a duplicate ACK is caused by a lost segment or just a reordering of segments, it waits to receive a small number of duplicate ACKs. When the third double ACK in a row is received, set ssthresh to half of the current congestion window, cwnd, but not less than two segments.
It inflates the congestion window with the number of segments that have left the network and cached the other side (3). When the next ACK arrives acknowledging new data, set cwnd to ssthresh (the value set in step 1). In addition, this ACK must acknowledge all the intermediate segments sent between the lost packet and the receipt of the first duplicate ACK.
Routing Protocols
- Basic IP Routing
- Routing Processes
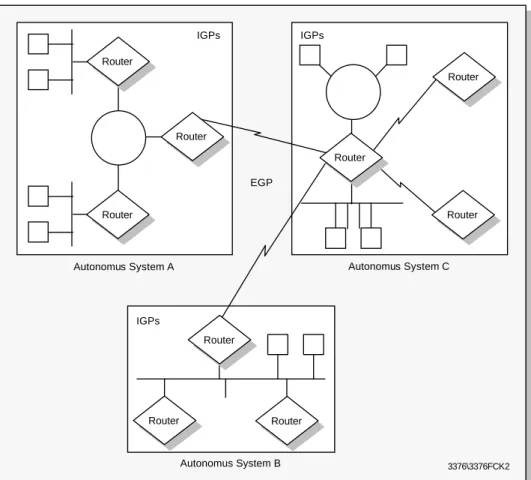
- Autonomous Systems
- Routing Algorithms
- Static Routing
- Distance Vector Routing
- Link State Routing
- Interior Gateway Protocols (IGP)
- Routing Information Protocol (RIP)
- Routing Information Protocol Version 2 (RIP-2)
- RIPng for IPv6
- Open Shortest Path First (OSPF)
- Exterior Routing Protocols
- Exterior Gateway Protocol (EGP)
- Border Gateway Protocol (BGP-4)
- OPEN 7 2. UPDATE
- References
Link state information is sent in the form of link state packets (LSPs), also known as link state advertisements. The flooding process ensures that all routers in a network have the same link state information. The resolution of the loop will take much more time (see counting to infinity in 3.2.2.1, "The counting to infinity problem" on page 101).
It is created based on the link status ads generated by the routers in the area. Shortest-Path First (SPF)' on page 105) algorithm against the link state database to obtain the shortest path tree. It consists of the exchange of a number of database description packages that define the set of link status information present in each router's database.
Each packet is identified by a sequence number and contains a list of the link status headers in the master's database. Connection status advertisements are exchanged between neighboring routers in the form of connection status update packages, the format of which is shown in Figure 88 on page 126.
Application Protocols
- Characteristics of Applications
- Client/Server Model
- Domain Name System (DNS)
- The Hierarchical Namespace
- Fully Qualified Domain Names (FQDNs)
- Generic Domains
- Country Domains
- Mapping Domain Names to IP Addresses
- Mapping IP Addresses to Domain Names — Pointer Queries
- The Distributed Name Space
- Domain Name Resolution
- Domain Name System Resource Records
- Domain Name System Messages
- A Simple Scenario
- Extended Scenario
- Transport
- DNS Applications
- References
- TELNET
- TELNET Operation
- Terminal Emulation (Telnet 3270)
- TN3270 Enhancements (TN3270E)
- References
- File Transfer Protocol (FTP)
- Overview of FTP
- FTP Operations
- Reply Codes
- FTP Scenario
- A Sample FTP Session
- Anonymous FTP
- Remote Job Entry Using FTP
- Trivial File Transfer Protocol (TFTP)
- TFTP Usage
- Protocol Description
- TFTP Multicast Option
This section explains the implementation of the domain name system, and the implementation of name servers. The division of the domain name space into zones is accomplished using resource records stored in the domain name system. This will either be a name server with authority for the domain given in the query, or it will be one of the root name servers.
Authority for the zone comprising the root of the namespace is assigned to a set of root name servers.8. 00 X'00' indicates the end of the domain name and represents the zero mark of the root domain. Assume that the domain name of the second network is tt.ibm.com and its name server is located in VM9.