This is to certify that the work in this Thesis Report entitled "Secure Fisheye State Routing Algorithm Against Data Packet Dropping by Malicious Nodes in MANET" by Mr. Securing FSR Against Data Packet Dropping by Malicious Nodes in MANET 3 1.2 Basic concepts in MANET.

Dynamic Topology
There is no central governing body in a MANET, so nodes act as hosts and routers. Antennas can be omnidirectional or broadcast, highly directional or point-to-point, steerable, or a combination of these.
Bandwidth Constrained applications
Energy Constrained Operations
A mobile ad hoc network is more vulnerable to security threats than a traditional wired network. Some of the security techniques available for a wired network are also applied to MANETs to reduce threats, and the decentralized nature of the network topology in a MANET helps the network to be more robust against a single point of failure than in the case of a wired network.
Organization of the Thesis
The task of making a network scalable and at the same time preventing it from the security threats is very difficult.
Introduction
- Based on Communication Model
- Based on the Structure
- Based on State Information
- Based on type of Cast
- Based on Scheduling
FSR protection against data packet drops by malicious nodes in MANET 6. Classification of routing algorithms in MANET. Based on the state information that nodes share about the network, protocols can be divided into two categories. i) Topology-based protocols follow the principle that each node in the network maintains large-scale topology information, as in the case of the link-state routing algorithm. Topology-based protocols are GSR (proactive) and DSR (reactive). ii) Destination-based protocols use the principle that each node only keeps information about its neighbors, as in the case of the distance vector routing algorithm.
Based on scheduling, routing protocols can be divided into three categories. i) Proactive (ii) Reactive (iii) Hybrid. Ensuring FSR against data packet dropping by malicious nodes in Manet 8 In proactive routing protocols, the route discovery process is performed at the beginning and maintained using the periodic route update process.
Proactive Routing Protocols
- Destination Sequenced Distance Vector (DSDV)
- Wireless Routing Protocol (WRP)
- Global State Routing (GSR)
- Fisheye State Routing (FSR)
- Cluster-head Gateway Switch Routing (CGSR)
- Optimized Link State Routing (OLSR)
Securing FSR from dropping data packets by malicious nodes in Manet 9 GSR is based on the traditional link state routing algorithm, but it differs in the way it limits the update messages to neighbors only. FSR scales well in a large network as it reduces the frequency of sending the update message to the remote nodes and sends the messages at a higher frequency to the nearby nodes in the fisheye scope. This can be remedied by matching the frequency of sending messages to the distant destination with mobility.
The path overhead is minimized since nodes only need to maintain the path to the cluster heads. Ensuring FSR against data packet dropping by malicious nodes in Manet 10 The characteristics and performance comparison of the above proactive protocols are given below in Table - 2.1 adapted from [3].
Reactive Routing Protocols
- Ad hoc On-demand Distance Vector (AODV)
- Dynamic Source Routing (DSR)
- Light Weight Mobile Routing (LMR)
- Zone Routing Protocol (ZRP)
- Zone-based Hierarchical Link State (ZHLS)
The advantage of this protocol is that it can store multiple routes in the nodes route cache. The characteristic feature and performance comparison of the algorithms discussed above are given in Table – 2.2 below, as adapted from [3]. In the route discovery process, the packet needs to carry only two addresses, the node ID and the area ID of the destination node.
The downside of this protocol is that all nodes must have a static zone map at boot time to work well. The characteristic features and performance of the above discussed two protocols [3] are given in the table – 2.3.
Summary
Securing FSR from dropping data packets by malicious nodes in Manet 14 Table – 2.3 Characteristic and Performance Comparison of Hybrid Routing Protocols.
Introduction
Representation of Network Topology in FSR
The topology table contains the most recent information about the topology of the network from the link state message. FSR is based on the link state routing protocol, but it differs in the way it distributes route update information or the link state information. In LS, each node sends the link state packet by flooding when a topology change is detected by a node.
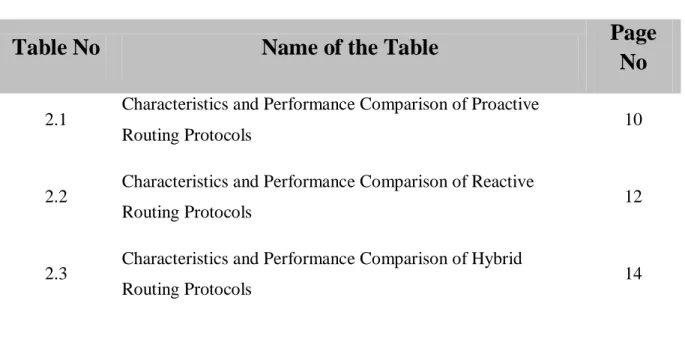
5] The number of levels and the size of the scope depends on the size of the network. GSR can be seen as a special case of FSR with only one level and radius of the scope.
Link State Message Processing
But in FSR, the nodes maintain a connection state table and periodically exchange only this table with the neighbors. The choice of the frequency with which the LS table is sent to the neighboring nodes depends on the distance between the two nodes. A fish eye captures in high detail pixels near the focal point of the fish eye.
In FSR, a complete topological map is maintained at each node and the shortest path is calculated using Dijkstra's algorithm. The range of a fisheye is defined as a set of nodes that can be reached in a certain number of hops, and the range is shown in Figure - 3.1.
Routing Table Calculation
Data Packet Forwarding
Complexity of FSR
Securing FSR Against Data Packet Dropping by Malicious Nodes in Manet 21 required to detect a change and the CT for FSR is the same as that of LS which is O(D.I) where D is the maximum hop distance, i.e.
Advantages of FSR Protocol
Introduction
Internal Threats
These can be divided into three categories: failed nodes, severely failed nodes, selfish nodes or malevolent nodes (here in this thesis the terms selfish and evil have been used synonymously where they may differ in some way in the actual context). The main attack by selfish nodes is packet dropping, with most routing protocols having no mechanism to detect if data packets have been forwarded, DSR being the only exception [14]. Another type of misbehavior by the selfish nodes is partial dropping, which can be difficult to prevent and detect.
These selfish nodes fall under the category of passive attacks, but sometimes they can also be part of some of the active attacks such as denial of service, integrity of the network. Most of the selfish nodes act maliciously because they save their battery power, which is one of the limited resources in MANET.
Types of Attacks on FSR
Severely faulty nodes are as severe as faulty nodes that exhibit characteristics such as not sending or forwarding data packets or routing messages. In addition, they can also send fake routing messages that are still properly formatted but may contain incorrect information and compromise the integrity of the network. Selfish nodes do not cooperate as required by the protocol whenever personal costs are involved, and will behave the same as failed nodes depending on which operations they choose not to perform.
Passive attacks are done by some of the malicious nodes selfishly to save power by not forwarding the packets to the destination. One type of such attacks is known as the black hole attack or the wormhole attack that causes data packets to be dropped.
Black hole attack
Proposed Solution to minimize black hole attacks in FSR
In the modified version proposed here, a weight list is maintained in each node in addition to the previous list and the three tables. The weight is assigned based on the number of times a node has acted maliciously. Instead of taking the number of intermediate hop counts for calculation as in the case of the FSR algorithm, the actual link cost is taken into account.
The weight function has been adjusted to account for the allocated link cost based on the number of malicious behavior rather than the number of hop counts. The route calculated by this algorithm may not be the shortest, but it always provides the optimal route that contains the fewest number of malicious nodes.
Work out Example
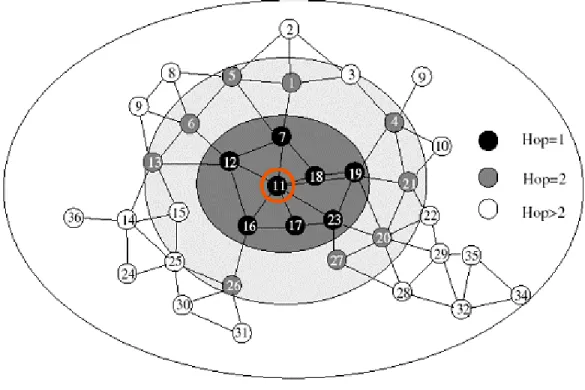
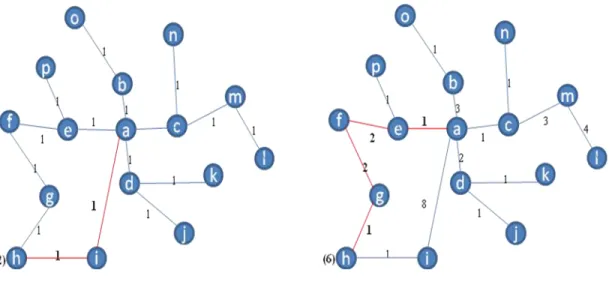
Suppose, initially when node "a" wants to send a data packet to node "h", node "a" checks its routing table for a valid from path. So node „a‟ sends the data packet to node „i‟ to forward it to node „h‟ along with a time stamp for node „h‟ which is enclosed in the data packet. If after a certain time interval node "h" does not respond to the timestamp in "a", then node "a" will understand that node "i" has not forwarded the data packet to node "h" and it writes 1 in the list of weights held at the node "a" corresponding to "i".
In this process, node „i‟ has behaved maliciously 8 times after some time and the next data packet has to be sent or forwarded so that the optimal route to the destination is searched or calculated using Dijkstra's shortest path algorithm. The edge connecting node 'a' and 'i' got weight 8 that means node 'a' sent many data packets of which node 'h' didn't receive 8 data packets so couldn't reply timestamp to node 'a ‟, hence „i‟ behaved maliciously 8 times.
Summary
- Introduction
- Simulation Environment and parameters
- Performance Metrics
- Packet Delivery Ratio: The packet delivery ratio (PDR) is defined as the ratio of the total number of data packets received by the destinations over the total number of
- Simulation Results
- Summary of the thesis work
- Future Research Direction
In both cases, the number of malicious nodes is approximately 1/3 of the total number of nodes. As the number of nodes increases, the packet delivery ratio in the secured FSR graph decreases, but the degradation is graceful when the number of nodes increases so on. However, in the case of the traditional FSR as shown in Figure - 5.1, the packet delivery ratio deteriorates more as the number of nodes increases.
One scheme is proposed to reduce the number of black holes or malicious nodes or selfish nodes in the path to destination, thus the number of dropped data packets can be minimized. The scheme can also be applied to reduce the number of control packets in the proactive routing algorithms available for MANET.
Bibliography
14] Po-Wah Yau; Mitchell, C.J., "Reputation methods for routing security for mobile ad hoc networks" Mobile Future and Symposium on Trends in Communications, 2003. 15] IEEE Computer Society LAN MAN Standards Committee, “Wireless LAN Medium Access Protocol (MAC) and Physical Layer ( PHY) Specification”, IEEE Std. 16] Mohammed, A.K., “A custom arbitrary waypoint model equalized for node crowding effect,” Proceedings of 14th International Conference on Computer Communications and Networks, ICCCN, pp.
20] Cheng Yong; Huang Chuanhe; Shi Wenming, "Trusted Dynamic Source Routing Protocol", International Conference on Wireless Communications, Networking and Mobile Computing, WiCom, pp. Sept. Ydeevneevaluering: kører DSR- og TORA-routingprotokoller samtidigt", i Proceedings of the 2007 Summer Computer Simulation Conference, San Diego, Californien, juli.