This is because the IoT has become an integral part of everyday life and has the potential to collect and distribute massive amounts of (generally sensitive) data. Devices in the IoT are capable of producing, processing and exchanging not only a huge amount of security-related data, but also sensitive information concerning privacy. The first is a data-based privacy threat, and the second is a location-based privacy threat.
Data privacy issues arise when secret information is leaked during data collection and transmission. This part covers the location privacy of each node in the IoT and the location privacy of the IoT to provide various location services such as RFID reader location privacy, the user location, sensor node location, and location-based privacy issues. The technique proposed in this research work is based on the threshold and monitor mode for the detection of malicious nodes.
I would like to express my gratitude to my supervisor Professor Chong, UiPil for the helpful comments, remarks and involvement throughout the learning process of this master's thesis. Furthermore, I would like to thank Prof. Surinder Sharma for introducing me to the subject as well for the support along the way.
- Introduction to IoT (Internet of Things)
- IoT Layered Architecture
- Security in IoT
- Location Privacy in IoT
In particular, the determination that the recipient of the data will not forward this data to other entities and then attention to data management. Malicious code attack: This attack is present in the form of code in any piece of software that can be used to cause unwanted effects and damage to the system. A malicious code attack can activate itself or pretend to be a program that required the user's attention to run [13].
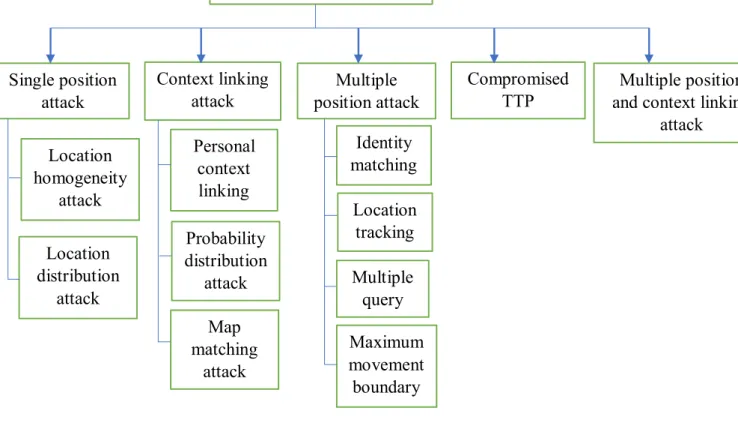
Location data significantly affects the management or processing of IoT (Internet of Things) data, which in turn greatly affects its location privacy. In this attack, the attacker tries to determine the probability distribution function of the user's location around the masking area. As a result, the attacker continuously monitors updates or queries and the associated members of the k-anonymity set.
The attacker can use these interactions to determine the user's privacy sensitive areas or the user's location. Combination of multiposition attack and context linking: An attacker can integrate or use multiple presented attacks or use them sequentially instead of using only a single attack to destabilize the user's location privacy [18]. A location server can resolve queries without learning or releasing any information about the query based on PIR.
Location sharing: This concept is used to perform queries, such as nearest neighbor or range queries based on the location, when the user's location protection is protected.
Literature Review
Donghe Li, et.al (2019) designed a novel reliable online dual auction system where multi-unit energy trading was performed among electric vehicles (EVs), routing optimization was adopted to charge the EV charging, and privacy was protected [27]. Guangjie Han, et.al (2018) designed a KCLP (k-means cluster-based location protection) technique to protect location privacy for Internet of Things (IoT) [29]. Mengmeng Yang, et.al (2018) intended a data release system for crowdsensing methods where differentiated privacy was used to protect workers' location [32].
Guangjie Han, et.al (2018) designed a CASLP (Confused Arc-Based source location privacy) protection method in wireless sensor networks for the Internet of Things (IoT) [34]. ShathaAlarabi, et.al (2018) proposed a two-level scheme to protect the location privacy of Internet of Things (IoT) users [35]. Yan He, et.al (2020) designed a strong identity verification system to ensure the security of system authentication at the beginning [38].
Defeng Li, et.al (2020) recommended a location chain storage system for blockchain-based Internet of Things devices and simulated the system [39]. Yu He, et.al (2019) established an SRR (sector-based random routing) method for addressing the source location privacy (SLP) issue and mitigating energy consumption [40]. Guangjie Han, et.al (2017) aimed a SLP (source location protection) protocol based on dynamic routing for location privacy protection [41].
Gang Sun, et.al (2016) proposed an approach named ADLS (Attack algorithm based on dummy location selection) for privacy protection to test the security of the Internet of Things (IoT) [42] . RômuloMeiraGóes, et.al (2018) introduced a discrete-event control-theoretic method for opacity enforcement in which the output events were inserted and deleted to preserve privacy in an indoor environment where IoT devices were implemented to monitor the users [43 ] . Gang Sun, et.al (2016) presented a location tag-based algorithm for preserving location privacy in which three key protocols existed, known as the user request aggregation protocol, the pseudo-ID exchange protocol, and the improved PLAM- protocol [44] .
Mengmeng Yang, et.al (2018) developed a blockchain crowd sensing privacy preservation system for dealing with privacy concerns [45]. Sridhar, et.al (2017) formulated an Intelligent Security model for the IoT (Internet of Things) devices [53]. Kalyani, et.al (2018) projected the IDS (Intrusion Detection System) for Internet of Things (IoT) detecting the rank attack and the attacker node [57].
Daemin Shin, et.al (2019) presented a secure route optimization protocol for DMM-based smart home systems in IoT [62]. ZieEyaEkolle, et.al (2018) introduced an approach to the security of IoT networks with the implementation of a hybrid security strategy [65].
Problem Formulation
Objectives
Research Methodology
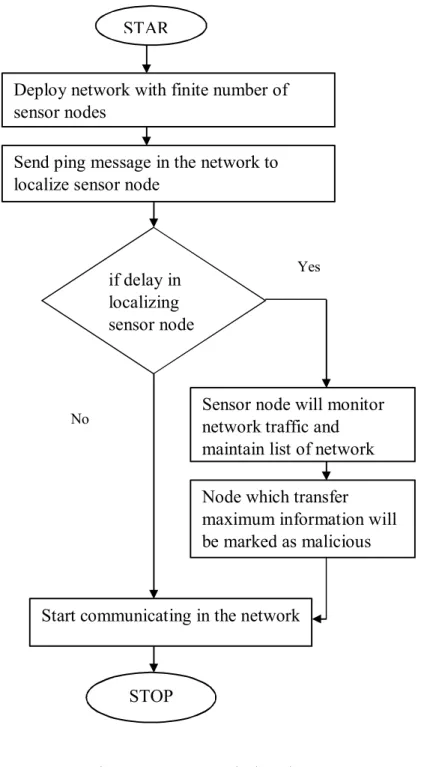
Sensor nodes will monitor network traffic and keep a list of network nodes that transmit maximum information will be marked as malicious.
Tool and Technologies
- Deployment of Network
- Division of Network in Clusters
- Aggregation of sensed information
- Location Protection Number Attack
- Proposed Methodology
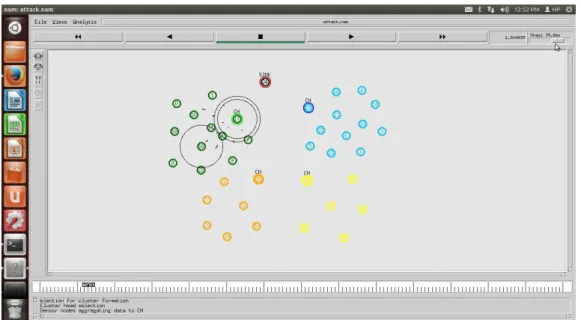
As shown in Figure 4.1, an IoT network is deployed with a finite number of sensor nodes. The sensor node with the highest energy and the lowest distance to the base station is selected as the cluster head. The data detected by the sensor nodes is transmitted to the cluster head.
The cluster head will pass the information to the base station and is shown in Figure 4.3. The version number attack is launched in the DODAG protocol shown in Figure 4.4. As a result, malicious nodes will create a loop and data will be transmitted in this loop, leading to packet loss in the network. A trust-based mechanism technique is implemented, and sensor nodes with the least trust are detected as malicious nodes from the network.
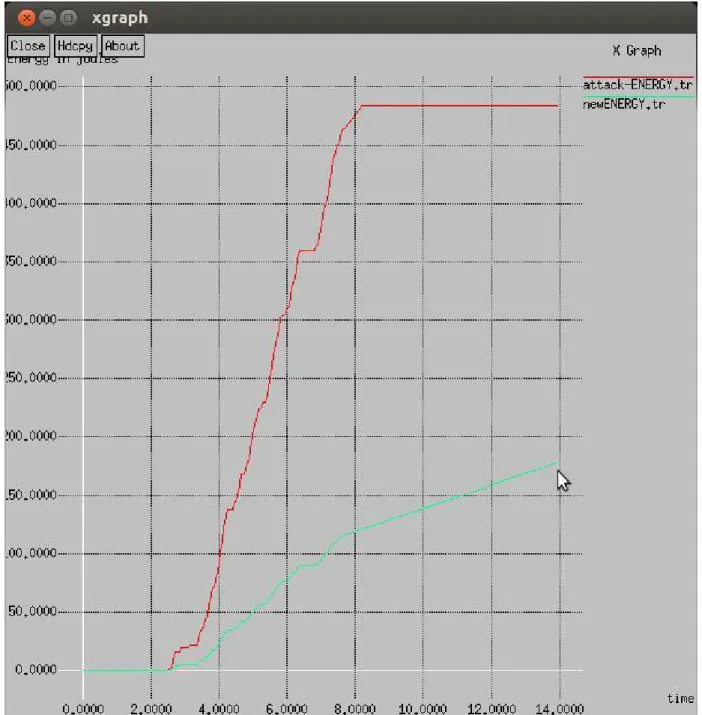
This research work is based on detection and isolation of malicious nodes from IoT. The performance of the proposed model is tested in terms of energy consumption, throughput and delay. As shown in Figure 4.6, the energy consumption of the proposed method is compared with the attack scenario.
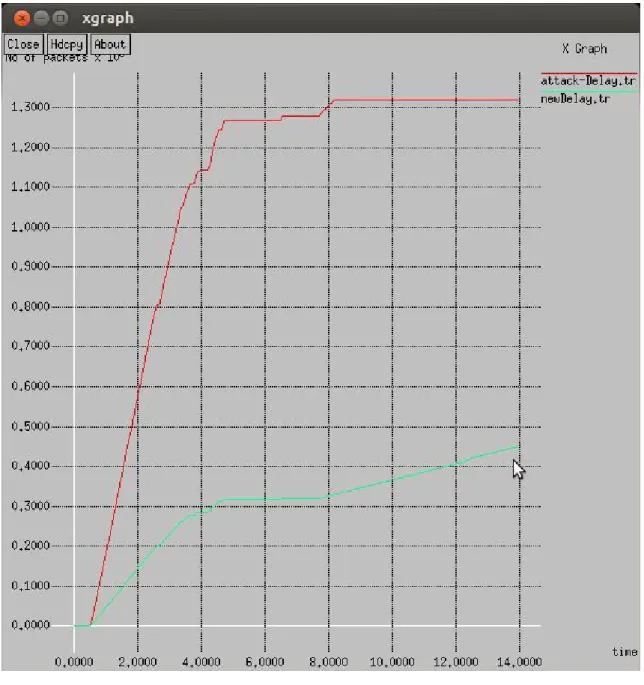
The proposed method provides low energy consumption compared to the existing method, which improves the performance of the model. As shown in Figure 4.7, the delay of the proposed method is low compared to the existing technique. The proposed method detects malicious node in the least time due to which delay is reduced in the network.
As shown in figure 4.8, the throughput of the proposed technique is high compared to the existing technique.
Conclusion
Future Work
Joshi, “Comprehensive Assessment of Security Attack Detection Algorithms in the Internet of Things”, 2018, Fourth International Conference on Computer Communication Control and Automation (ICCUBEA). 21] Chunyong Yin, Jinwen Xi, Ruxia Sun, Jin Wang, “Location Privacy Protection Based on Differential Privacy Strategy for Big Data in Industrial Internet of Things”, 2018, IEEE Transactions on Industrial Informatics. 22] Zainab Waleed Hussien, Doaa Sami Qawasmeh, Mohammad Shurman, “MSCLP: Multi-Sinks Cluster-Based Location Privacy Protection scheme in WSNs for IoT’, 2020, 32nd International Conference on Microelectronics (ICM).
23] Amani Abuladel, OmaimahBamasag, "Data Privacy and Location Issues in IoT Applications", 2020, 3rd International Conference on Computer Applications and Information Security (ICCAIS). 31] Thu Le, Isao Echizen, "Lightweight Semantic Collaborative Scheme for Generating a Fuzzy Region to Ensure Location Privacy", 2018, IEEE International Conference on Systems, Man and Cybernetics (SMC). 36] Wei Wu, Erwu Liu, Xinglin Gong, Rui Wang, "Blockage-Based Zero-Knowledge Location Proof in IoT", 2020, IEEE International Conference on Communications (ICC) [37] Hao Wang, Guangjie Han, Wenbo Zhang, "A source location privacy protection scheme based on ring routing for IoT", 2018, Computer Networks.
40] Yu He, Guangjie Han, Whenbo Zhang, "A Sector-Based Random Routing Scheme for Protecting Source Location Privacy in WSNs for the Internet of Things", 2019, Next Generation Computing Systems. Thorat, “Improving location privacy and energy saving technique for sensors in Internet of Things domain”, 2016, International Conference on Global Trends in Signal Processing, Computing and Information Communication (ICGTSPICC). 49] Mahmoud Elkhodr, SeyedShahrestani, Hon Cheung, "A Contextual-Adaptive Location Discovery Agent for General Devices in the Internet of Things", 2013, 38th Annual IEEE Conference on Local Area Networks - Workshop.
56] Seungyong Yoon, Jeongnyeo Kim, "Remote security management server for IoT devices", 2017, International Conference on Information and Communication Technology Convergence (ICTC). Vydeki, “Survey of Rank Attack Detection Algorithms in Internet of Things”, 2018, International Conference on Advances in Computing, Communication and Informatics (ICACCI). Gutierrez, Sayan Kumar Ray, "SecTrust-RPL: A Trust-Aware RPL Secure Routing Protocol for the Internet of Things", 2018, Next Generation Computing Systems.
Malik, "Proposing a Rank and Wormhole Attack Detection Framework using Machine Learning", 2019, 13. internationale konference om matematik, aktuarvidenskab, datalogi og statistik (MACS). 61] Dong Seong Kim, Kok Onn Chee, Mengmeng Ge, "A Novel Graphical Security Model for Evolving Cyber Attacks in Internet of Things", 2020, 50. årlige IEEE-IFIP International Conference on Dependable Systems and Networks-Supplemental Volume (DSN-S) ). 74] Yusuf Muhammad Tukur, DhavalkumarThakker, Irfan-Ullah Awan, "Multi-layer Approach to Internet of Things (IoT) Security", 2019, 7. internationale konference om fremtidens internet af ting og cloud (FiCloud).