Zoheb Hassan University of British Columbia, Canada Fang Fang University of British Columbia, Canada Website Committee Chair. China Yuan Luo University of Hong Kong, PAR China Wen Ji Institute of Computer Technology,.
1 Introduction
However, if the dynamics are allowed to evolve for a sufficient amount of time such that consensus is reached between all the nodes, then the existence of a pure Nash equilibrium can be guaranteed. In our competition model, the players' utilities are defined to be a function of each node's relative opinions to the players at the end of the dynamic process.
2 Model
Influence
The resulting consensus is described by the weighted sum of the nodes' initial opinions (at time t = 0), where the weights given by the entries in the eigenvector Γ correspond to the eigenvalue 1. However, if Ti is not large enough to obtain consensus, sus, then the centrality of a node's eigenvector no longer corresponds to the influence they have on the average opinions after the end of the dynamic.
3 On the Existence of Pure Nash Equilibrium
At Consensus
Since|VC|=μ=m(b+ 1) + 1 and the total seed budget among all players is bm, it will always be the case that a player's best response will not include nodes already included in another player's strategy is not, and exactly m+ 1 of the central nodes will not be. The dark nodes are the "central nodes" and the white nodes are the "petals".
4 Computational Properties of Best Response
A playeri with a seed node v ∈ si that is a successor of u can always improve their utility by switching to a strategisi={u} ∪(si\ {v}). Proof (Sketch). The submodularity and monotonicity follow immediately from establishing that (7) is increasing and (6) is submodular, and the fact that since πi(·) is a function defined by a linear combination of submodular functions (cf. , Eq.
5 Discussion and Future Work
In a competitive extension of the probabilistic independent cascade model of Kempe et al. [5] show that competitive extensions of the threshold diffusion model do not share the (1−1/e) approximation guarantee established in [14] for the “single player” optimization institution.
Similar (1−1/e) approximation guarantees have recently been established in competitive impact maximization models by Goyalet al. Our analysis in Sect.3 highlights the importance of the length of the diffusion process, T, to guarantee the existence of pure strategy Nash equilibrium.
Networks: A Game Theoretic Approach
There are two fundamental assumptions required for the optimal data preservation algorithm in Tang et al. Such mendacious behavior of the storage nodes out of their selfishness makes it clear that the data preservation path in Tang et al.
2 Data Preservation Problem
Second, based on the reported cost of each node, the payment can sufficiently motivate each node involved in the optimal data preservation path shown in Tang et al. The centralized algorithm can only determine the minimum cost data storage path based on the assumption that data storage cost of each storage node is observed.
3 Algorithmic Mechanism Design (AMD) Approach
Node i is on the storage path to transmit the data packet when it reports oseci or ˜ci. Node i is on the storage path to store the data packet when it reports oseci or ˜ci.
4 Conclusion and Future Work
To solve it efficiently, the problem is divided into two subproblems, i.e., the clustering problem and the energy-efficient beamforming problem. Then, the problem of energy-efficient beamforming and gathering is formulated and efficiently solved in Section 3 .
2 System Model
Signal Model
Power Consumption Model
MCT introduces additional operation on each BS, the signal to be transmitted must be exchanged by BS via the backhaul and the joint signal processing is necessary to enable joint transmissions. Therefore, we refer to the energy consumption model in [9] and the signal processing power is modeled as a quadratic function of the cooperative cluster size as follows.
3 Energy Efficient Clustering and Beamforming
Problem Formulation
Energy Efficient Beamforming
Applying the Lagrangian dual theory and the Karush-Kuhn-Tucker (KKT) conditions, the optimal beamformer is given by. Hkik)Huik (16) The optimal Lagrange multipliers {λ∗qk} can be obtained using the gradient method. Then we develop Algorithm1 as below to numerically find the optimal value of θ and{vik}.
Energy Efficient Clustering as a Coalition Formation Game We define the energy efficient cluster forming game (EECFG) as a triplet,
At each iteration, the proposed algorithm for energy-efficient beamforming (Algorithm1) is used to determine the cooperative transmission strategy and calculate the achieved EE. Since the total number of partitions is finite, i.e. Bell number and clustering history information are fed into the algorithm to avoid repeated deviations, the proposed clustering algorithm always converges to any initial partition.
4 Numerical Results
In addition, the EE can be further improved by 20.5% when the CFG-based clustering algorithm is also exploited. When ICI is severe, BSs will cooperate with aggressor BSs to improve EE.
5 Conclusion
It can be seen that when using the proposed energy-efficient beamforming algorithm, the EE can be significantly improved compared to the MRT case, and the gain can be up to 104%. In addition, we can see that with the increase of the transmission power limitation, the EE first increases and then decreases.
Context-Aware Placement of Services with Information Producers and Consumers
But both the cloud and the delivery of services and content are also important in wireless networks, and in those networks entities have only limited knowledge about the topology. The next section provides our model and assumptions, as well as definitions of cost-sharing games and requirements.
2 Related Work
This was our motivation to develop a self-organizing algorithm that addresses the challenges outlined in the abstract.
3 System Model and Requirements
Typically, the agent has an incentive to cover the cost of investing in cost shares. The agent's income/profit must be greater than his investment in cost shares.
4 Cross-Monotonic Semi-cost Recovering Game
Consumers in a service instance offset the costs incurred by receiving updates. In Eq. 2, the valueαv(S, i, t) indicates the fraction of the agent cost that must be paid in each waiting for a context update and is described in Eq. 4.
5 Evaluation
In our simulation, the multi-server cost is well above the single-server approach, in the range of read/write ratios between 0.35/0.65 and 0.5/0.5. Before the operating point, line 10 in Algorithm 1 guarantees that the cost is slightly above the single-server approach.

6 Conclusion
Game in Heterogeneous and Small Cell Networks
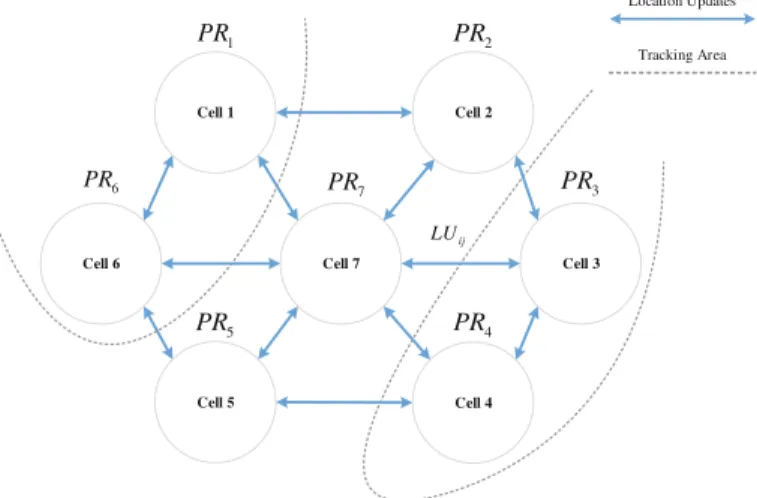
In each TA, the LTE core network sends the paging request (PR) to idle users while the call arrives, and the mobility management unit (MME) is responsible for location update (LU) while the users move out of the TA. The application of the corresponding location area concept, this area is called tracking area location.
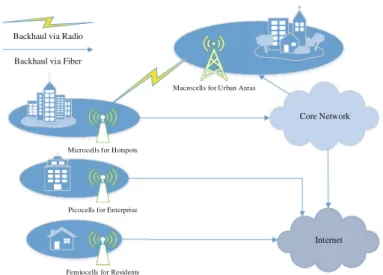
3 Proposed TA Planning Algorithm Based on Cooperative Game
EPC for the UE is an idle state and connection state, and has their registered TA management, exchanging the registration information of the UE. Therefore, the community detection model based on cooperative game can be expressed as CG = (N,Eigen), denoted as.
4 Performance Evaluation
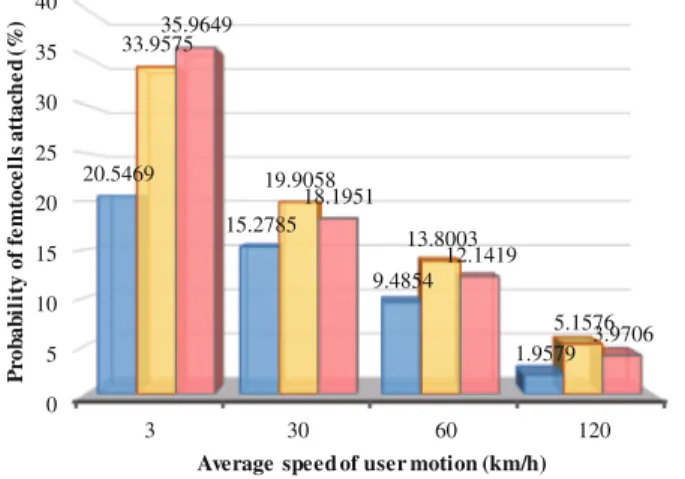
Due to the extremely dense placements of femtocells in this circumstance, the probability increases slowly as the femtocell dwell rate increases. In contrast to YU 2013, the proposed algorithm and TORIL 2013 have a better performance of using femtocells.
Maximization
Initially, each agent does not have a membership, and an agent can have at most one membership, which cannot be revoked or changed later. Define the membership function mem : A → P ∪ {U} which takes an agent and returns the principal from which the agent is infected, or U if the agent is uninfected.
3 Analysis
Uninfected nodes that have received proposals can accept at most one of the referrals or remain uninfected. We relate the size of an agent's neighborhood in the network to the parameter perturbations α and β in a director's stimulus package.
Optimization for Device-to-Device Networks
As a useful tool to model the complex interactions between users while taking into account the inherent benefit-cost trade-off in [12], coalition formation game theory can be well qualified to design the resource sharing scheme for D2D communication [13]. And the proposed scheme is more flexible for the data requesting users than other schemes like in [18].
2 Network Model
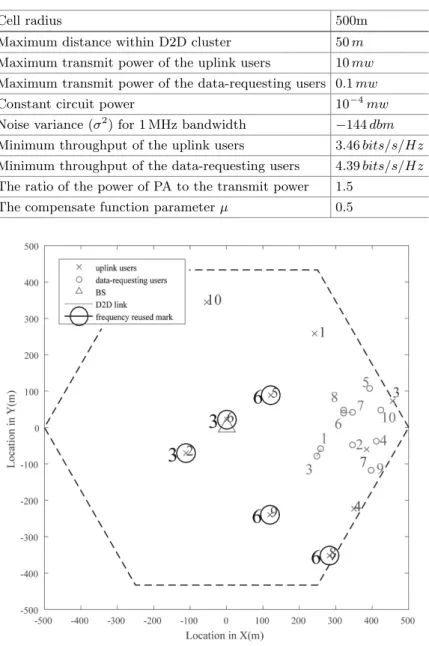
Similarly, the transmit power of an uplink user sharing a resource is Pt,u, and the channel gain from an uplink user to a single tail is Hu,tail, and the product of the two values is the per-user interference. The transmit power of the connection of the user requesting data is equal to the transmit power from the cluster head to the farthest user on the tail.
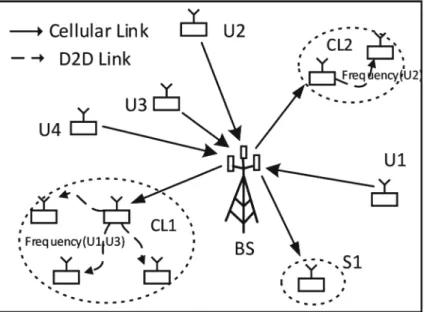
3 Coalition Formation Game and the Solution
System Model
Network and BS sharing service. We consider a setM of multiple MNOs, and each of them has operational BSs denoted by a setBm respectively. Traffic, capacity and load. We assume that users in a classq have identical independent Poisson arrival traffic with rateλq, and that the file size is independently distributed with an average of 1/μq. Therefore, the unit mass in classq generates γq = λq/μq traffic intensity, and the class q generates γqdq traffic intensity in total.
3 Problem Formulation: Game
Social Objective
In (c), for a given BSb, the function gb(yqb) represents the sum of load and energy consumption of the BS, where the original subscription of classq is not the MNO that owns the BSb (ie, roaming traffic in classuq), as follows. A large η means that MNOs give higher priority to BS energy consumption than flow-level capacity in mobile network operation.
Payoff Function
4 Equilibrium Analysis
Price-of-Anarchy and Existence of Equilibrium
Since the potential function (6) is exactly the same as the social goal as described in (1), and the KKT conditions are a necessary and sufficient condition for a global maximizer in a concave function, the NE satisfying the KKT conditions must be a global maximizer of the social goal. Note that our game and the game played by mobile operators have exactly the same potential function (i.e. equivalent game) for any roaming cost per unit.
Evolutionary Dynamics and Distributed Association Algorithm Developing a distributed algorithm for user association is important in prac-
Dynamics of the best response. In best-response dynamics, each user chooses his strategy that maximizes his payoff function for a given social state as follows. In detail, the best response dynamics require only the social state, while others require additional information such as the average payoff and the opponent's payoff.
5 Numerical Analysis
We consider the case where all MNOs adopt the same roaming unit price (i.e., km = kn) for roaming traffic due to the symmetry property in the roaming unit price under the symmetric BS deployment and the identical characteristics of users. In Fig. 1 (b), (c) and (d), we show the impact of our algorithm in terms of potential function, flow rate performance and BS energy consumption under the given roaming price per unit k.
6 Conclusions
The result in Fig.1(b) shows that social objective is maximized when each MNO assigns zero unit roaming price and it decreases as k increases due to the increased roaming price. As shown in Fig. BS part, since no one is interested in roaming when highly expensive roaming price (eg km=kn ≥150) is applied.
Managemnet in VANETs
Although game theory has been used to optimize the vehicle choice, the definition of Nash equilibrium point for cooperation is lacking. We propose an algorithm based on Weighted Voting Game to select fair and optimal relay vehicles for anchor vehicles.
2 Network Architecture
3 System Model
- Scanning
- Connection Attempt
- Forming Coalition
- Voting
- Packet Dissemination
In CoMP, a number of TX (transmit) points provide coordinated transmission on the DL, and a number of RX (receive) points provide coordinated reception on the UL. CoMP cooperative sets (macrocell, microcell) can be configured according to the location of the UE.
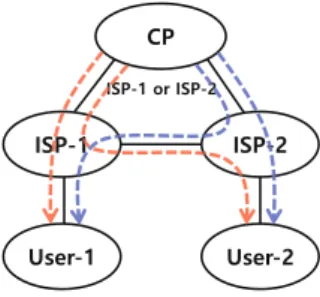
In our model, we assume that only one of the ISPs provides the piracy monitoring service, while the other does not, to understand the effects of competition on profit-sharing behavior. CP profit: The CP profit depends on the content price, the profit sharing ratio γ, the content of the easiest access unit and the protection level β.
3 Analysis of Best Responses and Equilibrium
- User Behaviors
- Strategy of CP
- Strategy of ISP
- Negotiation of Profit Sharing Rate
Otherwise, we can always find a monitoring level with which contracting with ISP-1 is more beneficial. For the former, although the profit sharing rate is small, the monitoring level is bounded below by ˇβ so that ISP-1 can be selected.

4 Numerical Study
5 Conclusions
Otherwise (either the access price is high or the revenue distribution is low enough) there exists a monitoring level at which ISP and CP can work together. Further characterization of the level of piracy monitoring remains a future work, as does that of the revenue distribution relationship.
Using Accumulated-Payoff Based Snowdrift Game Model
Snowdrift Game
If they both remove the snow from opposite sides, which means they both choose the cooperative strategy, they can both get the wage R by driving home and sharing the labor cost of clearing the snow. If one of them chooses to stay in the car and the other sinks into the snow, the cooperative receives a payment and the deserter pays the higher wage. However, if they both stay in the car, they cannot go home and receive the minimum payment. Thus, we have T > R > S > P, and the defect payment and cooperation behaviors can be formulated in a payoff matrix as follows:
Topological Characteristic of P2P Network
3 Cooperation Incentive Mechanism
Assumption
Accumulated-Payoff Based Snowdrift Game
The payoff matrix thus satisfies the aforementioned snowdrift game model, since b > b−c/2 > b−c >0. Without loss of generality, we normalize the payoff matrix by defining b−c/2 = 1 andr =c/2, where the payoff ratio holds.
4 Simulation
APBSG on Small World Network
The increase ofr leads to a high payoff when the defect strategy is chosen, so the value represents the degree of a rational selfish individual. A rational individual's selfishness is to maximize his compensation as far as possible, and a unilateral defect always brings a greater payoff.
APBSG on Scale-Free Network
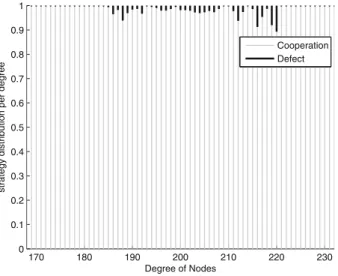
Due to the fact that a strong penalty will be received when the single node chooses to defect, although one may receive a temporarily high payoff in one round, it will immediately change its strategy from defect to cooperation to win. a maximum salary. In contrast, those with higher degrees tend to adhere to cooperative behavior, regardless of what strategy their neighbors adopt.
Allocation for D2D Communications Underlaying Cellular Networks
A Coalitional Game Perspective
The authors in (Wang et al.2013) assumed that a D2D pair can reuse the channels of multiple CUEs. For example, let us consider a case where the first and second D2D pairs share the same subchannel with CUE c1.
3 Interference Mitigation as a Coalition Formation Game
Coalitional Game in Partition Form
We allow multiple D2D pairs operating on the same subchannel of a CUE to form cooperative group, i.e. coalition. 1 We use the same set of D2D pairs that join all the D2D pairs in the formulated game.
Power Control Within a Specific Coalition
A D2D pair that joins a coalition with the following constraint met will receive a unique payout in the coalition. 9) For detailed proof, see Appendix. When the maximum number of iterations is reached, the players in the same coalition use their throughput as a payout.
Coalition Formation Algorithm for Joint Power and Subchannel Allocation
Starting from any initial network partition π0, the coalition formation stage of the proposed algorithm always converges to a final Nash Stable paritionπ∗. Since the total number of partitions is limited (MN in our setting) and the proposed algorithm prohibits D2D pairs from revisiting previous coalitions, all D2D pairs will finally converge to a Nash-stable network partition.
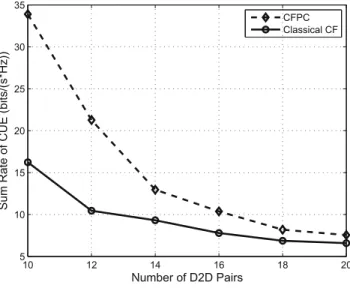
4 Simulation Results
We find that the Classic CF algorithm provides improved system fairness compared to the proposed scheme when the number of D2D pairs is small. However, the proposed scheme provides better system fairness compared to the classical CF algorithm when the no.
A The Proof of Proposition 1
Xu, S., Wang, H., Chen, T., Huang, Q., Peng, T.: An efficient interference cancellation scheme for device-to-device communication underlying cellular networks. Yu, C.-H., Doppler, K., Ribeiro, C.B., Tirkkonen, O.: Resource sharing optimization for device-to-device communication under cellular networks.