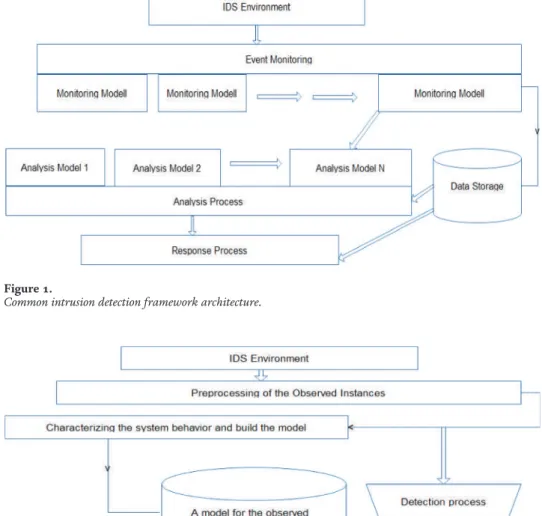
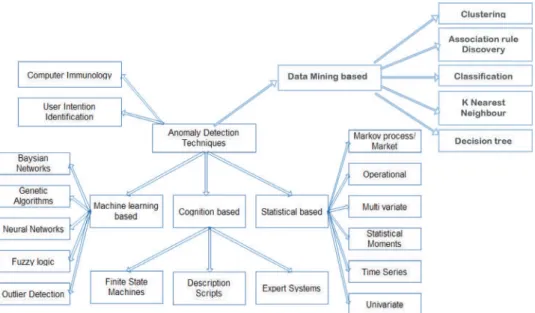
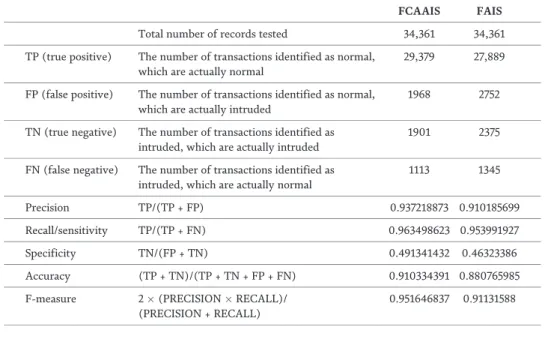
The biggest advantage of the anomaly-based detection system concerns the possibilities for the detection of new attacks. Developing an intrusion detection system independent of the environment is another challenging task for the network anomaly-based intrusion detection system development community [9-13].
Analysis of experimental results
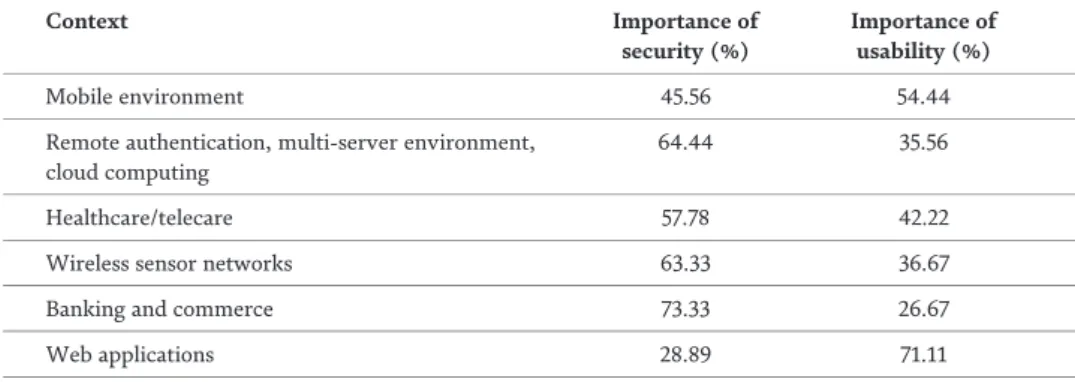
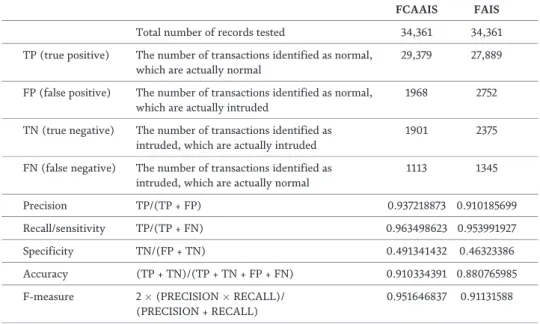
The records identified as normal are 19.8% of the total test data records, with observations of 4.7% of them as "false negatives" and 15.1% of them as "true negatives." The cumulative number of records detected as "intrusion transactions" is 80.2%, with 75.3% of them being "actually intruded transactions" of test data records and the "false positive" percentage of 4.9% of test data records. It is observed that the application of canonical correlation after optimized feature selection leads to 3% improvement in the accuracy of FAIS [14]. Table 3 indicates precision, recall and F measure values calculated under divergent canonical correlation threshold values (Figure 7).
Conclusion
It is desirable that an anomaly-based network intrusion detection system achieves high classification accuracy and reduces the process complexity of extracting the rules from training data. Anomaly Detection and Machine Learning Methods for Network Intrusion Detection: An Industry Focused Literature Review.
Introduction
Important research domains in WLAN security include: access control and data frame protection, lightweight authentication and secure handover. CAPWAP (Control and Provisioning of Wireless Access Points), HOKEY (Hand Over Keying) and IEEE 802.11r are important protocols for performing the secure handover.
Access control
Comparisons of various WLAN access control mechanisms
The KHC scheme uses an interesting methodology that differs from other access control protocols. Thus, the fewest messages are required to refresh the key among all WLAN access control security mechanisms. In most WLAN access control mechanisms (except KHC), data frame authenticity is usually ensured by the MIC.
-in-middle attack Yes No Yes No No. Repeat Attack Yes No Yes No No. Reduce DoS attacks No No No Yes Yes.
Frame authentication
Comparisons of various lightweight authentication mechanisms
Therefore, it is suggested that light authentication and cryptographic measures based on symmetric key per frame should be used. For providing individual frame-level protection, there are two types of per-frame authentication in WLAN: MIC-based authentication and lightweight authentication. Although KHC is considered in this chapter primarily under access control mechanisms, it also includes lightweight per-frame authentication and needs a special mention in this sub-section.
KHC also has higher memory requirements, but fulfills important security features such as secrecy forwarding, key refresh, lightweight per-frame authentication, per-frame encryption, etc.
Secure handoff
Comparisons of various handoff mechanisms
Conclusions
Network steganography methods
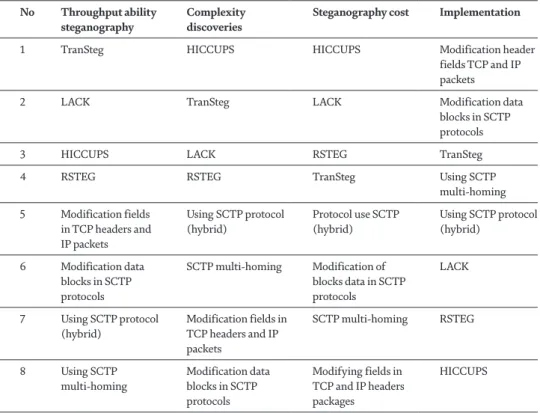
The value of the "Identification" field of the IP packet is generated on the sender's side. However, the frame analysis does not include a checksum and may lead to the discovery of the use of the Nogo method. The complexity of detection and throughput is directly related to the use of the method's implementation mechanism.
The implementation of the method is too complex, but may not be possible within certain operating systems.
The combined method using modification of the fields IP and TCP As mentioned earlier, the methods for modifying the IP and TCP header
- Intercomputer exchange
- IPv4
- Header of IPv4
- Injection’s result
- IPv6
This condition is necessary so that the value of the "Sequence Number" field does not look suspicious. The next step is to add the C-media value in the "Sequence number" field of the TCP header. Next, you need to enter the value of the encrypted key (inv(z)) 16 in the IP header field.
So the next step is to enter (inv(z)) 16 in the "Identifier" field of the IP header.
Result of injection
In this protocol, you can use the IPv6 "Destination Address" field in the IPv4 encapsulation header to load information into it. As a result of the manipulations described above, it is possible to use 284 bits, which is 88.75% of the total number of bits. Because of the change that had occurred on the source device, the receiving PC cannot build the original packages correctly.
Due to the tampering that takes place at the source, the receiving party cannot properly collect packets.
Result of injection
The processed piece of information was included in the next 8 bits of the transmitted symbol. Due to the manipulation that has taken place on the source device, the receiving party cannot properly assemble the original packets. Due to the tampering of the device generating the packets, the receiving party cannot correctly assemble the source packets.
Increasing the value of this field also increased the packet size, so we can modify the data octet fields by appending them to the end of the datagram.
Result of injection
Conclusion
The main part of the software model is a detector program for analyzing network traffic to find possible hidden transmissions. The analysis is performed by checking the header according to the standards, which is necessary to identify illegal values for certain fields of the PDU. Thus, thanks to the proposed manipulation, the programming model uses 603 bits, which is 74.04% of the total number of bits in the order of three heads.
However, the experience of the developers involved may vary from team to team, which may influence the decision on which authentication technique to implement.
Methodology
To distinguish between single-factor and multi-factor authentication techniques, the former will be referred to as authentication schemes in this book chapter, while the latter will be referred to as multi-factor authentication methods. Today, the decision about which authentication scheme or method to implement in a software application rests with the software development team. Some frameworks in the literature partially help with this [14, 15]; however, they do not provide the appropriate features for their application in different application contexts or do not take into account all authentication techniques or multi-factor authentication.
This action research was carried out in collaboration with a multinational software development company and envisages the use of other research methodologies to support it.
Identification of the knowledge base
Systematic literature review
In this case, the critical reference group is composed by the employees of the partnered software development company (PSDC). The aim of the first cycle was to obtain the required knowledge base for creating the framework. Subsequently, a short summary of the most important results of the SLR is given for each research question.
Moreover, it could be observed that most of these articles highly regarded the importance of the context of use for the comparison and selection of schemes and methods.
Survey and interviews
Out of the 57 respondents, more than two thirds of them held a senior position in the PSOS, as well as more than 6 years of work experience. For the last question of the S&I, clear strategies were applied between the interviewers and the survey respondents. In the case of the former, they were asked directly what criteria they use for the comparison and selection of authentication schemes and methods.
In the case of the latter, the responses of the interviewees, together with the results of the previously conducted SLR, were used to generate a list of comparison and selection criteria that respondents were asked to rate from 1 to 5.
Short survey
The respondents were then asked which authentication techniques they have implemented in applications developed by them and what kind of application this is. These employees are selected from the most experienced developers of the company, based on their years of experience and positions. The values obtained were then used as input for the decision framework.
Multifactor Authentication Methods: A Framework for Their Comparison and Selection DOI: http://dx.doi.org/10.5772/intechopen.89876.
The framework
Tool prototype
To facilitate the use of the framework in software development environments, a tool prototype was created that enables its use in a semi-automatic way. They show procedures for criteria selection, context selection, and framework recommendation. After calculating the SUV and taking into account the average value given by C, the framework can make a suggestion about which authentication schemes or methods should be implemented in the evaluated application.
Thus, for each Ct, the framework will give six possible recommendations based on the calculated SUV and C. Table 10 illustrates the above framework for the context of mobile environment.
Validation through the industry
Expert panel
The prototype tool also has additional features that facilitate its use in software development companies. Specifically, it has a user registration feature that allows keeping a record of its usage and a functionality to customize its preferences based on the needs of the software development company.
Case studies
Through the creation of the framework, its adequacy was repeatedly validated using strategies associated with the application of the action research method. The first session consisted in the presentation of the first draft of the framework with the aim of helping the experts to have a general idea of the purpose of this research. After its construction, the validation of the framework's recommendations was realized through the application of a case study methodology in collaboration with Computer and Network Security.
Specifically, the framework's recommendations were compared with the authentication schemes or methods implemented in existing applications developed by the PSDC or with the recommendations their experts would give for hypothetical situations.
Conclusions
This framework helps to compare and select the most appropriate authentication schemes or multifactor authentication methods for applications created by software developers. On the other hand, an expert panel and several case studies were conducted to validate the adequacy of the framework. This allowed feedback from the end users of the framework to be obtained so that it would provide an appropriate authentication scheme or method recommendations and have appropriate usability.
Finally, the last cycle of action research, i.e. the realization of case studies, could be replicated in other software development companies to further confirm the relevance of the framework.